Anonymous authentication method and system
An anonymous authentication and authentication information technology, applied in the field of information security, can solve the problems of not meeting the need to protect the authenticator's private information, user privacy leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
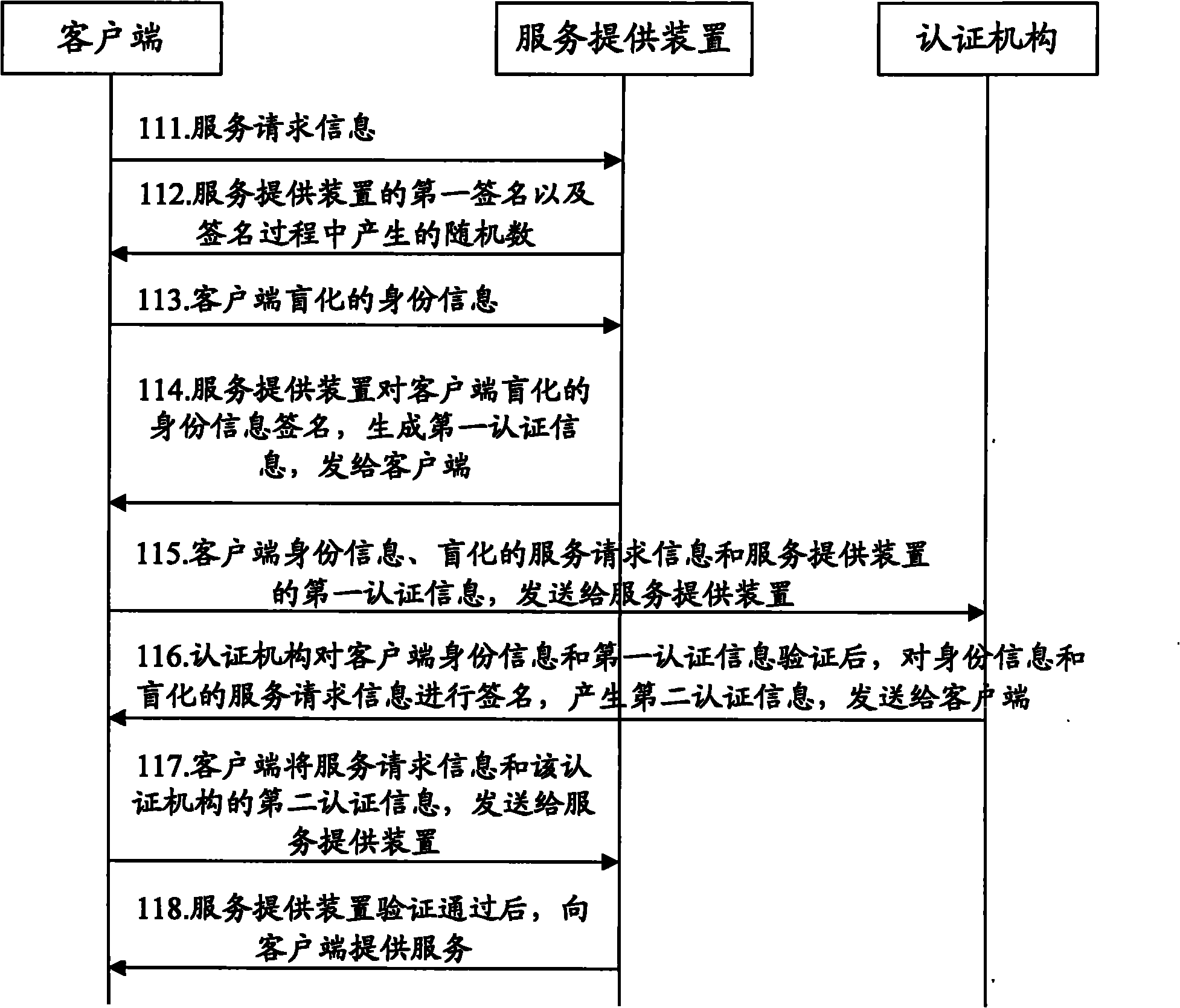
[0126] Taking the electronic ticket reservation system as an example to illustrate the specific implementation of the present invention, the various entities involved in the electronic ticket reservation system: users (equivalent to clients), ticketing institutions (equivalent to service providing devices), banks (equivalent to certification body);
[0127] 1) The user sends the booking information to the ticketing agency;
[0128] 2) The ticketing agency verifies the integrity of the booking information, signs the booking information, and sends the random value generated in the signature to the user;
[0129] 3) The user uses the chameleon hash function in the aforementioned method to generate a message digest of the user's bank account information, user public key and random number, and sends the message digest to the ticketing agency;
[0130] For example, set user bank account information m 2 , the user randomly selects calculate r U = r M g t , let m=m 2 ||r U , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com