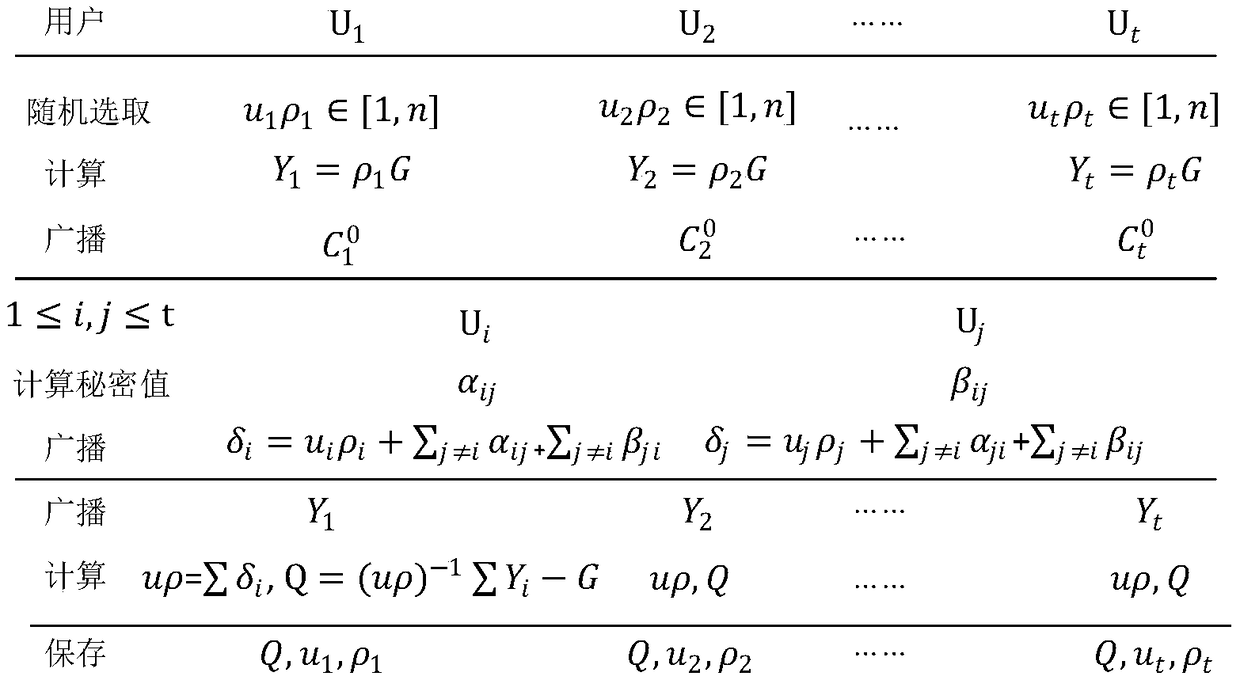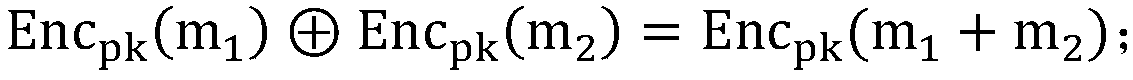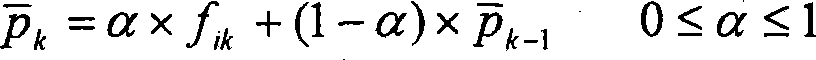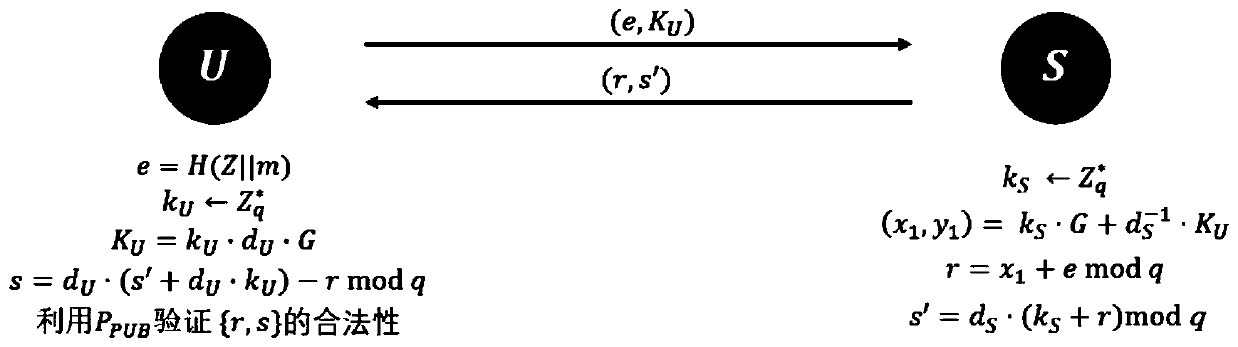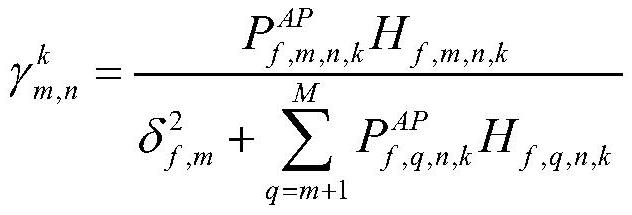Patents
Literature
46results about How to "Less fairness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Intelligent teaching system
InactiveCN107230403AEasy to useReduce manufacturing costData processing applicationsElectrical appliancesMan machineComputer terminal
The invention discloses an intelligent teaching system, which includes a teacher terminal and a plurality of student module terminals connected through a communication module. Communication module, sign-in module, class and teacher selection module, on-site teaching scene simulation module, man-machine operation module, touch display screen, central processing unit; the teacher terminal includes lesson preparation module, electronic teaching plan database, material database, and data sharing module , homework arrangement module, homework correction module, evaluation and lesson coin distribution module, and man-machine operation module; the intelligent teaching system disclosed by the present invention is easy to operate, easy to interact and score between teachers and students, and between students and students, and in the student The terminal can switch to the on-site teaching scene simulated with real pictures of students, which can enhance students' teaching interest and students' sense of recognition for intelligent teaching.
Owner:成都优瑞商务服务有限公司
Method for multi-party associated generation of SM2 digital signature
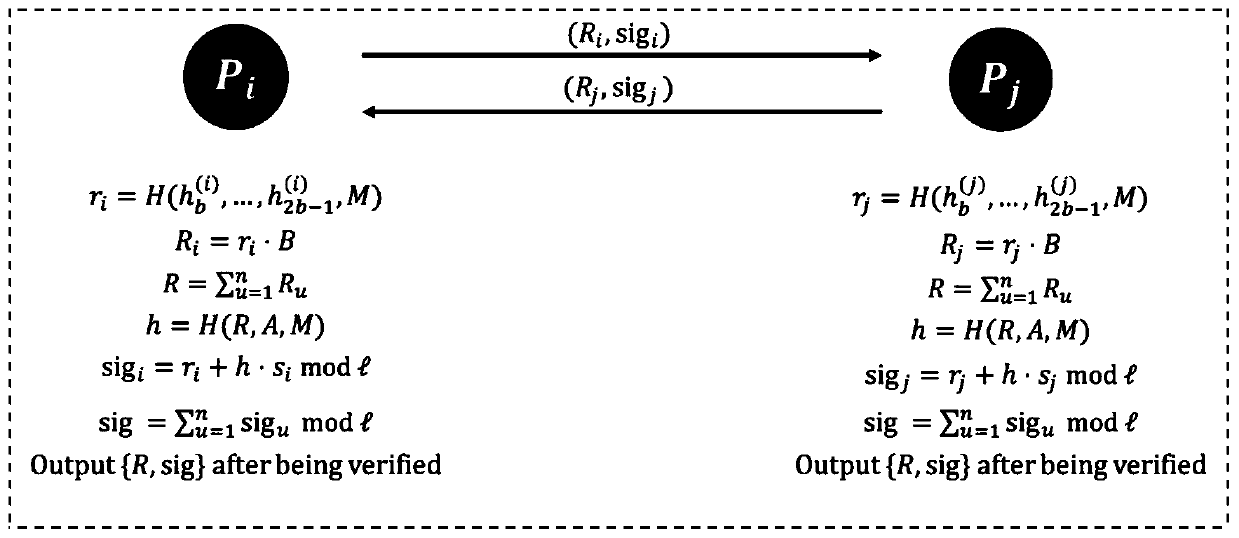
ActiveCN109474422AImprove securityLess fairnessKey distribution for secure communicationPublic key for secure communicationDigital signatureComputer security
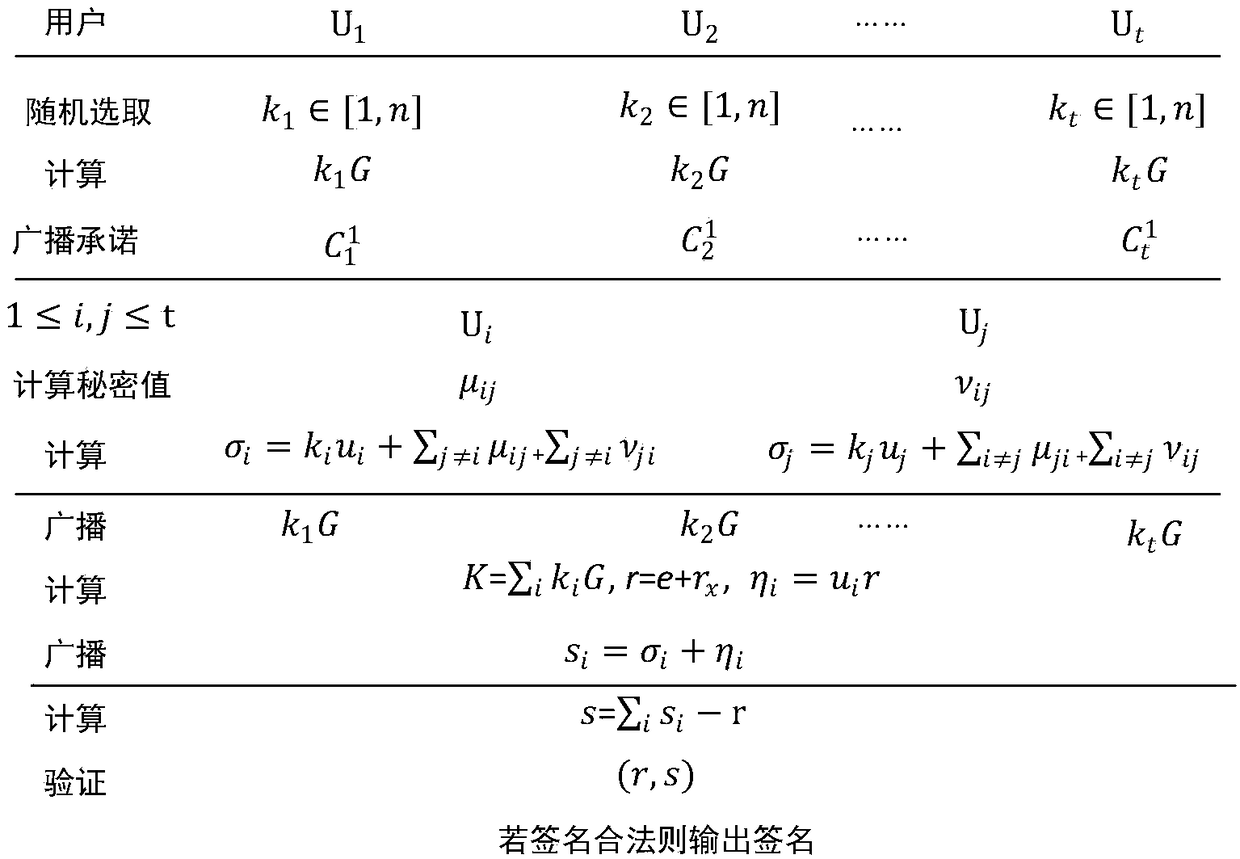
The invention discloses a method for multi-party associated generation of a SM2 digital signature, which comprises the following steps: t participants generated by participating in an algorithm randomly select two numbers ui and pi in a set {1-n}, and a public key Q of the SM2 digital signature is interactively generated. The t participants randomly select ki from {1-n}; a first part r of the signature is first calculated through interaction; the t participants interactively calculate a second part s of the signature again through the r; and finally, the complete SM2 digital signature (r, s) is published. The method for multi-party associated generation of a SM2 digital signature in the invention realizes the function of multi-party associated generation of the SM2 digital signature; during signature generation, users in the set are required to participate at the same time; meanwhile, the safety and high efficiency of the signature private key are ensured.
Owner:WUHAN UNIV
Medical equipment anti-counterfeiting and traceability system based on block chain technology
InactiveCN107679876ASolve counterfeit and shoddy productsReduce execution time and fairnessCommerceMedical equipmentSmart contract
The invention relates to a medical equipment anti-counterfeiting and traceability system based on the block chain technology. The system comprises a circulating module, an authentication module and aquerying module; participants comprises an authentication node, a manufacture node, a transaction node and a querying node. The medical l equipment anti-counterfeiting and traceability system adds allcirculating information of the medical equipment from leaving factory to waste in an information traceback chain, the life cycle data is real and queryable; two anti-counterfeiting chips are designedfor the disposable and reusable medical equipment, thereby thoroughly solving the trouble of the counterfeiting and shoddy products; the management method on the medical equipment market by the government offices is written in the intelligent contract, the execution time of the management flow is greatly shortened, the fairness and the judicial efficiency are improved, and the judicial transparency is increased.
Owner:SHANGHAI WEILIAN INFORMATION TECH CO LTD
RSA digital signature generation method and system based on identity
ActiveCN107733648AImprove securityLess fairnessKey distribution for secure communicationPublic key for secure communicationCiphertextDigital signature
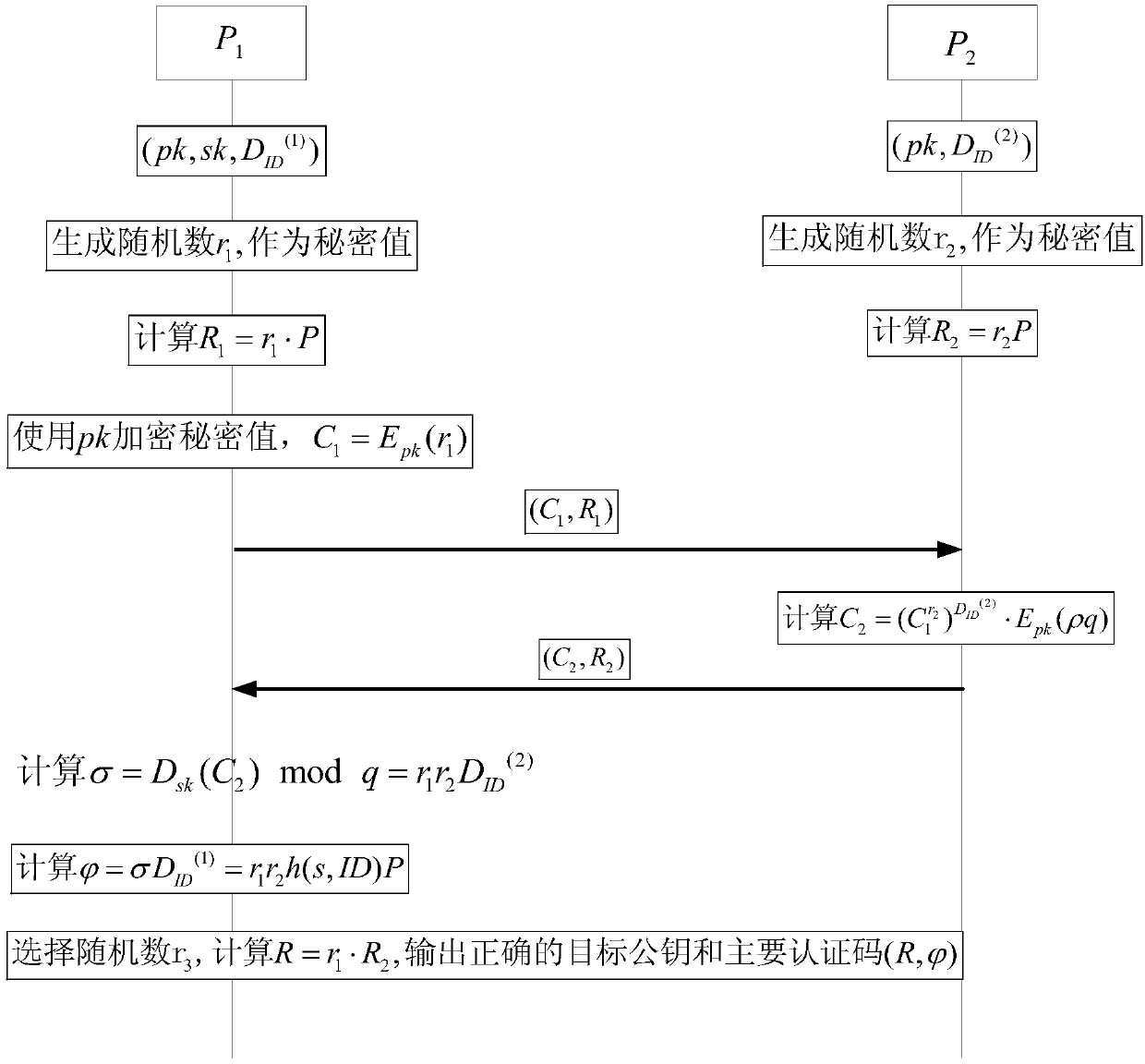
The invention relates to a RSA digital signature generation method and a RSA digital signature generation system based on an identity. The method specifically comprises the steps as follows: a secretkey generation center generates a public and secret key pair of a pair of RAS and a pair of random numbers; one part of a signature secret key is sent to P1, and the other part of signature secret keyis sent to P2; the two parties P1 and P2 participating into generation of a digital signature separately generate a random number r1 and a random number r2; the P1 firstly computes r1, encrypts the r1 to acquire C1, and then sends the C1 and r1 to the P2; the P2 computes r2 and returns the same to the P1; meanwhile, the P2 a ciphertext C2; the P2 sends the ciphertext C2 to the P1; And the P1 decrypts the C2, and computes to acquire signatures S and R by using one part of own signature secret key, and after the signatures pass authentication, the P1 publishes the complete RAS digital signature(R, S) based on the identity. According to the method and the system provided by the invention, security of the signature secret key is ensured, and the fairness of the two parties participating intothe digital signature is improved.
Owner:WUHAN UNIV
Identity-based anonymous authentication method and system
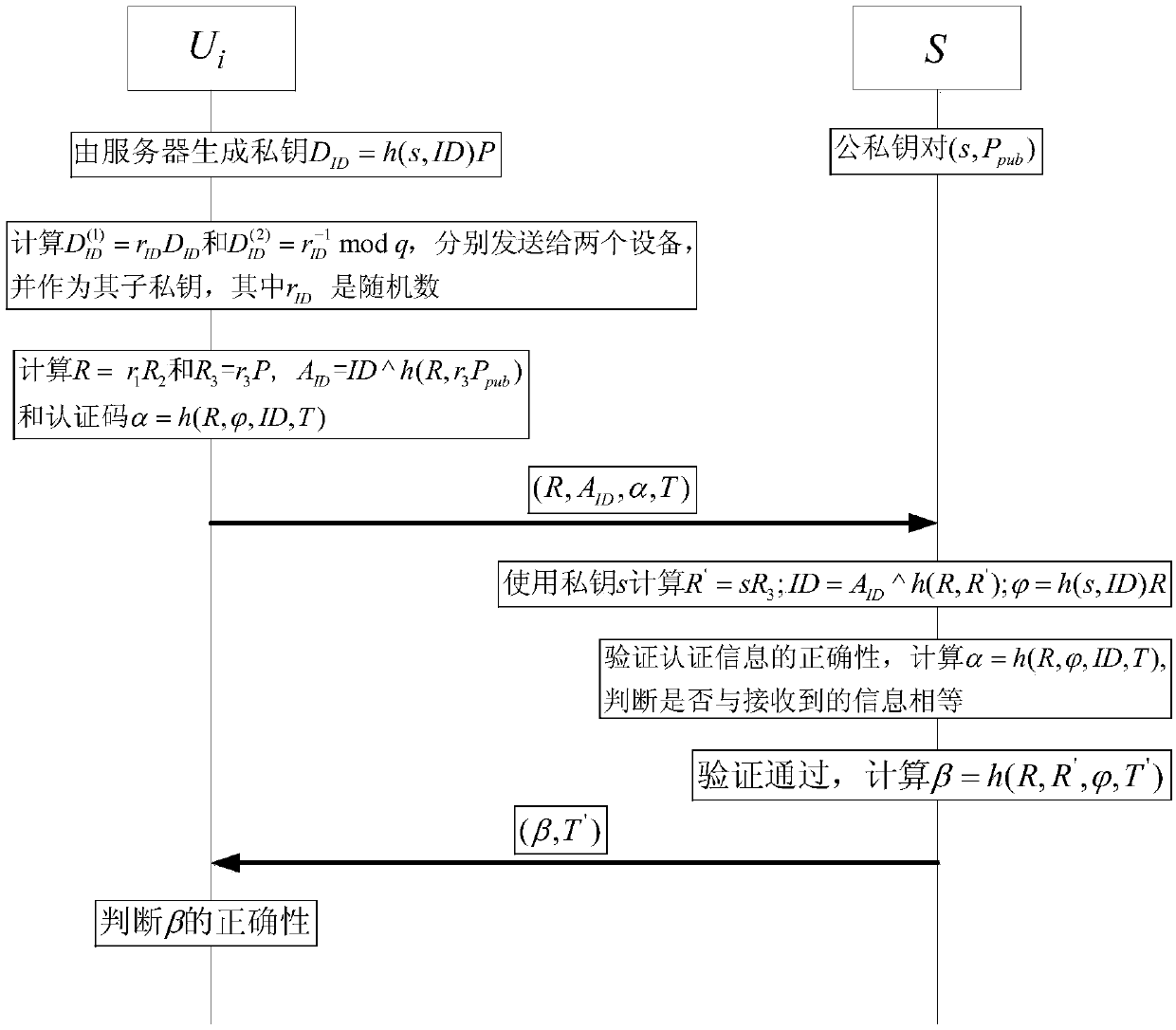
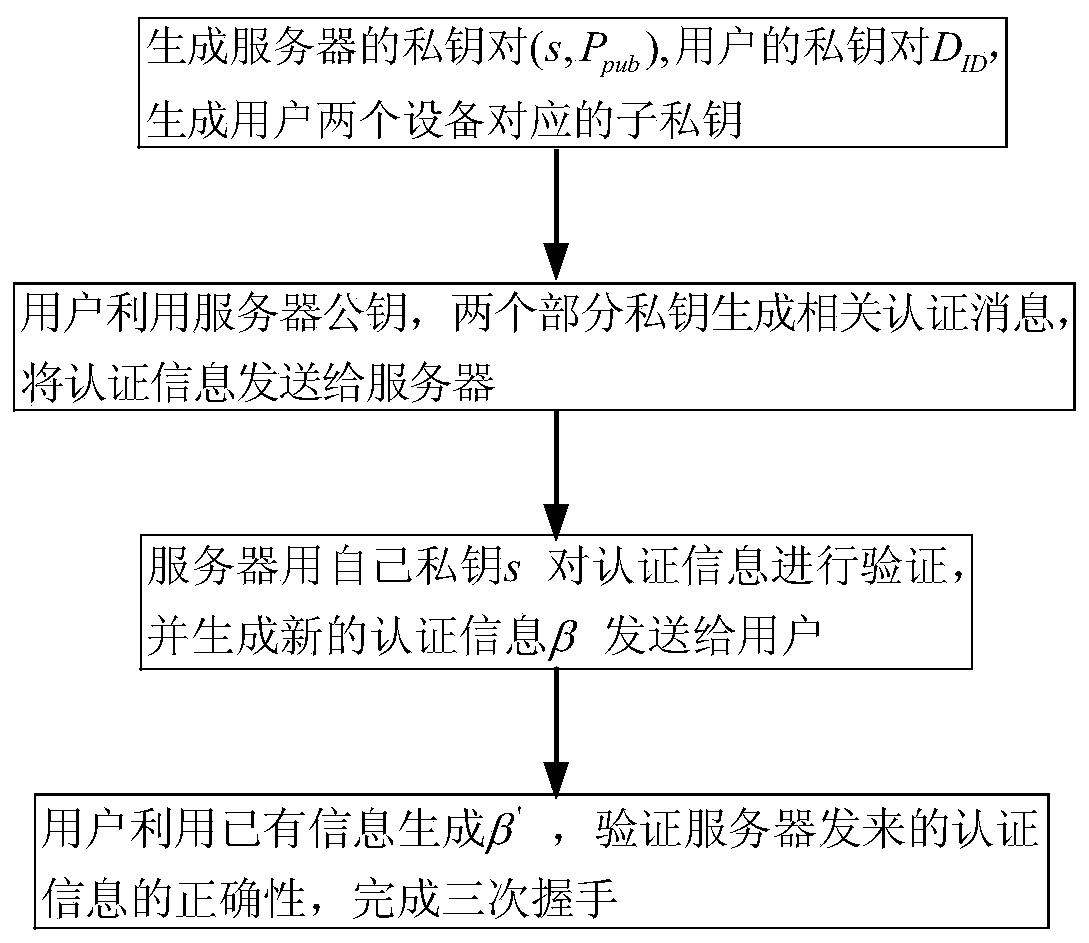
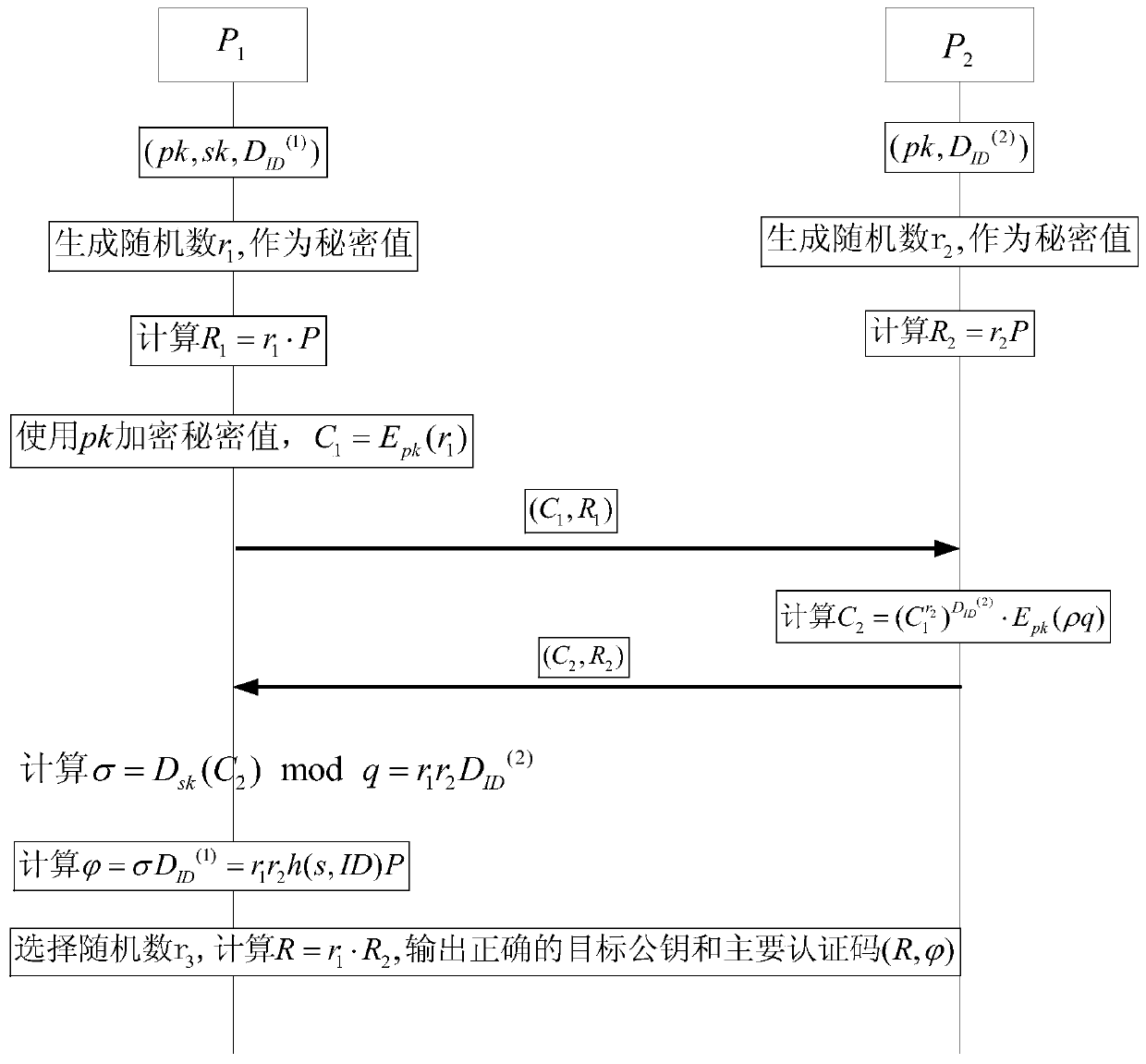
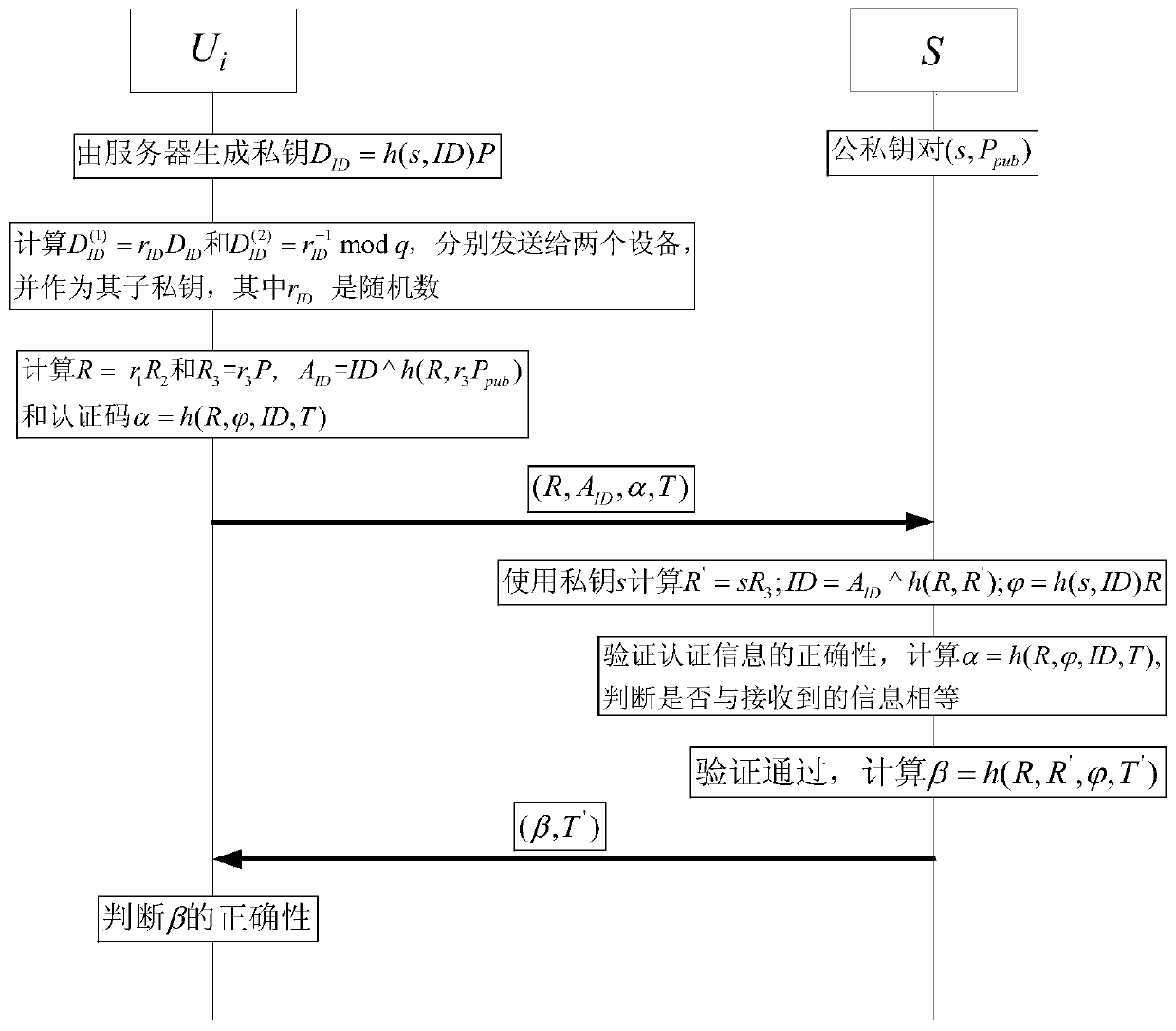
ActiveCN107947913AImprove securityLess fairnessKey distribution for secure communicationUser identity/authority verificationZero-knowledge proofSecure communication
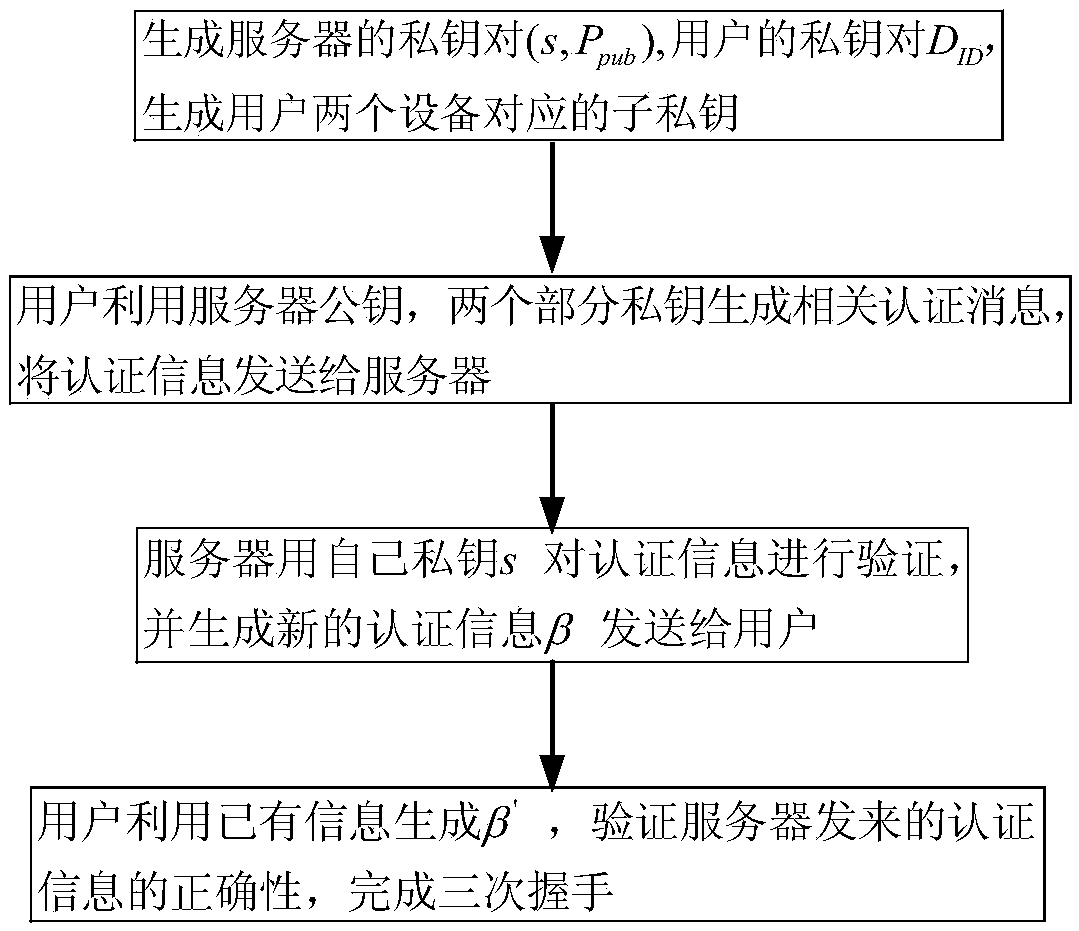
The invention relates to an identity-based anonymous authentication method and system. The method comprises the following steps: a server generates two partial private keys and sends the same to double parties P1 and P2 participating in the authentication respectively, wherein P1 and P2 generate a main authentication code (the formula is described in the specification) and R in an authentication process, and the privacy and reliability of the interactive information between P1 and P2 are ensured by using zero knowledge proof; after the P1 obtains the main authentication code, the P1 generatesa pseudo-address AID, generates a third temporary public key R3, calculates a final authentication code alpha, and sends the authentication information (AID, R, R3, alpha, T) the server, and the server verifies the authentication information and feeds back the authentication information to a user, after the successful completion of three times of handshake, the server can establish secure communication with the user. The identity-based anonymous authentication method and system are suitable for jointly completing identity-based distributed anonymous authentication without exposing the respective partial authentication private keys of the both parties together, the both parties holding the partial private keys must participate in the authentication at the same time, and the complete authentication private key does not need to be restored.
Owner:WUHAN UNIV
Random draw-off method, apparatus and system
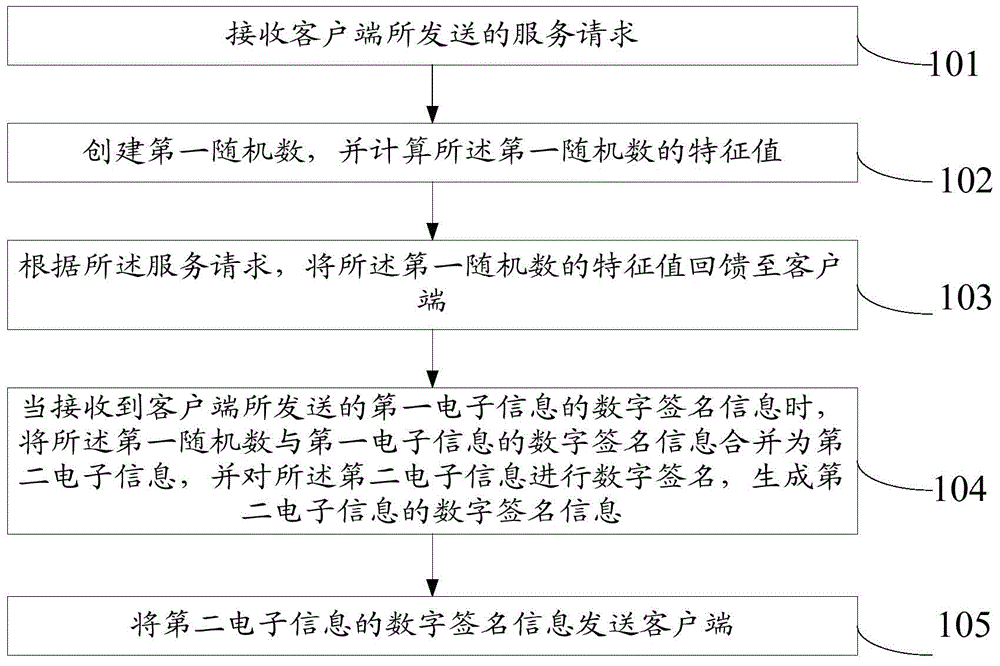
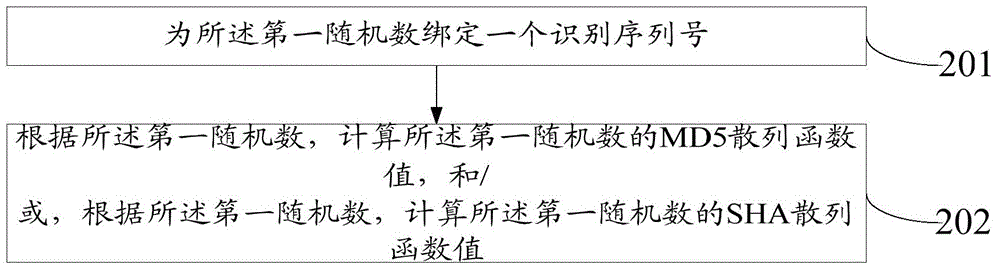
ActiveCN105162760ALess fairnessReduce the impact of fairnessEncryption apparatus with shift registers/memoriesUser identity/authority verificationDigital signatureElectronic information
The invention relates to the technical field of communications, and specifically relates to a random draw-off method, apparatus and system. The method comprises the following steps: receiving a service request sent by a client; creating a first random number, and calculating a feature value of the first random number; feeding the feature value of the first random number back to the client; when digital signature information of first electronic information sent by the client is received, combining the first random number with the digital signature information of the first electronic information to form second electronic information, and carrying out digital signing on the second electronic information; and feeding digital signature information of the second electronic information back to the client. According to the invention, through superposed digital signing for two times, it is difficult to tamper the first random number and a second random number on nodes of data transmission or calculation, it can be ensured to a greater degree that a final draw-off result is not manually interfered, and accordingly, the influence exerted by manual factors on fairness of a probability event is reduced.
Owner:郝孟一
Upstream bandwidth allocation scheduling algorithm of O-OFDM (optical orthogonal frequency division multiplexing) access system
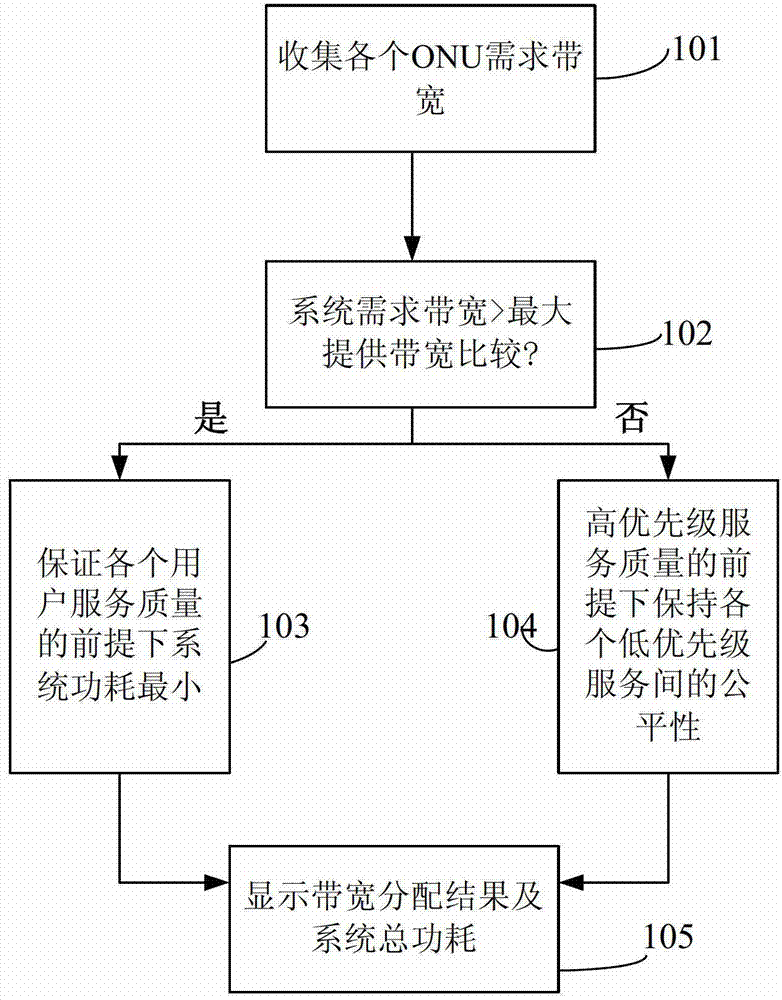
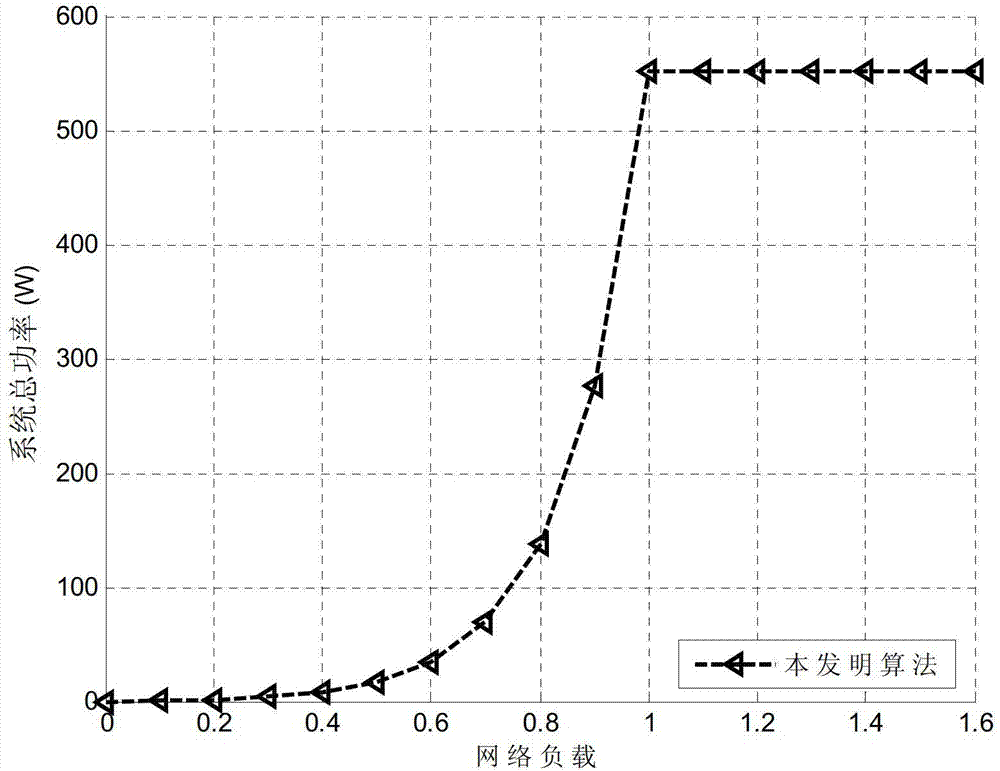
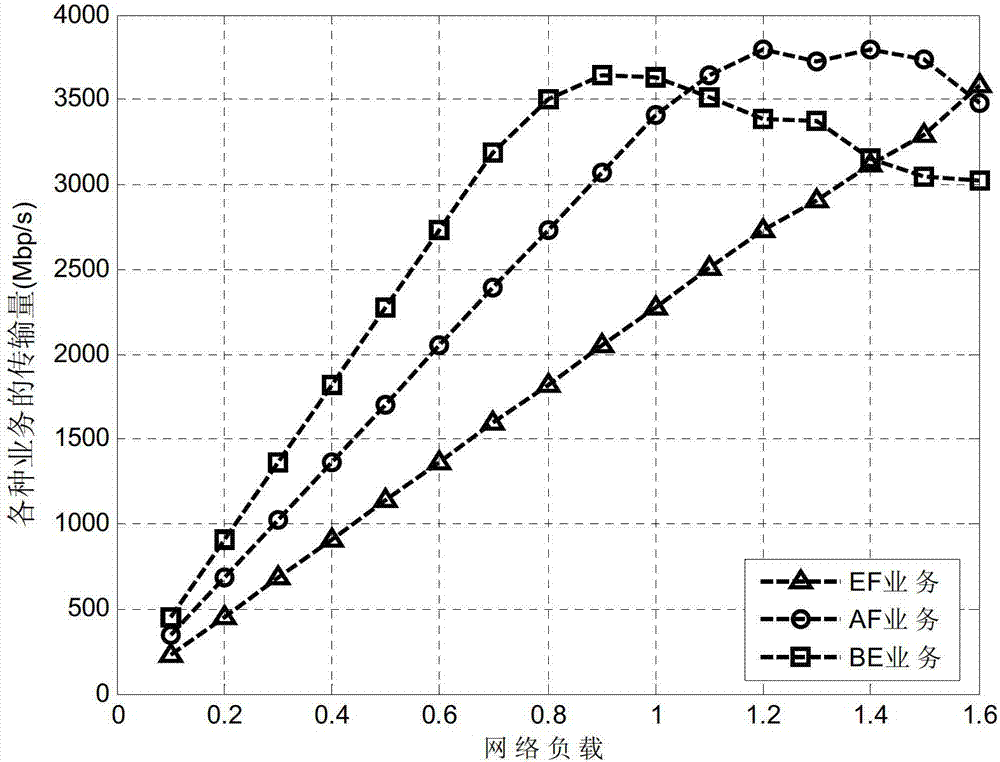
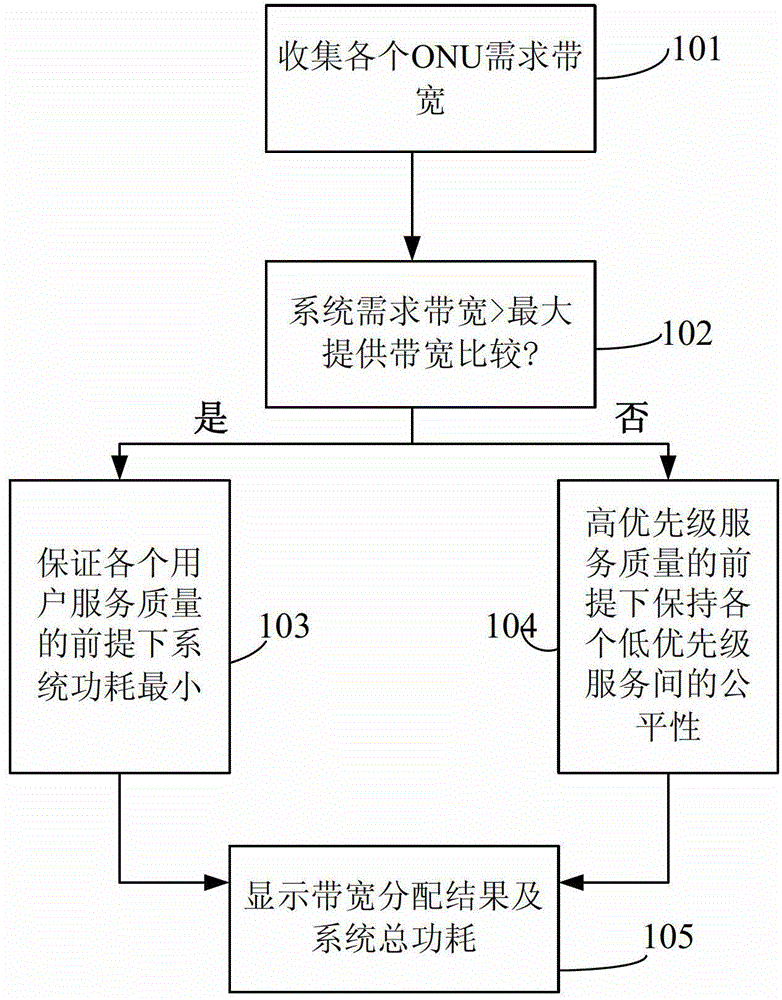
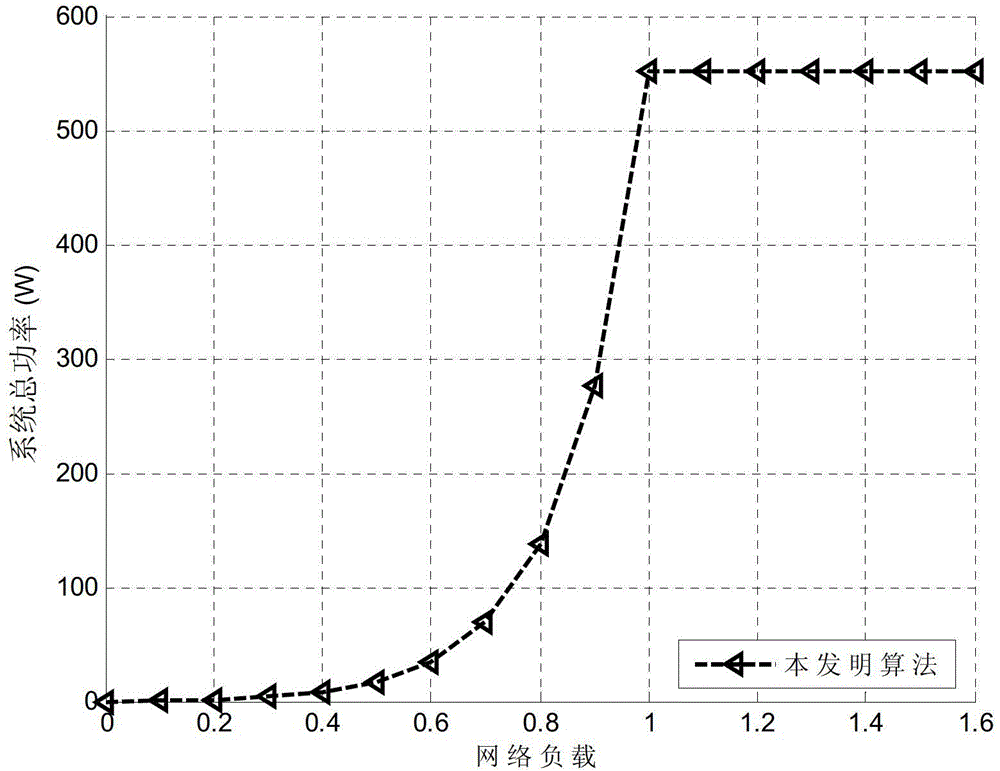
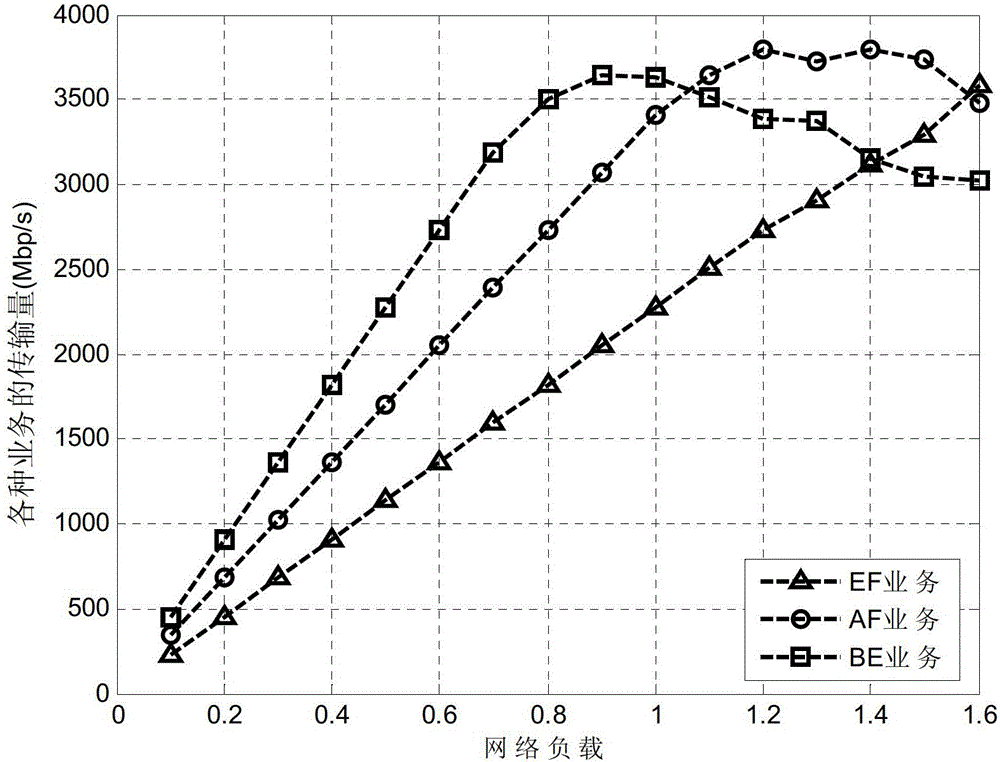
InactiveCN103051563ALow powerReduce energy consumptionMultiplex system selection arrangementsMulti-frequency code systemsOptical network unitBandwidth requirement
The invention discloses an upstream bandwidth allocation scheduling algorithm of an O-OFDM (optical orthogonal frequency division multiplexing) access system. The upstream bandwidth allocation scheduling algorithm comprises the following steps of collecting a bandwidth requirement of each user; comparing whether bandwidth required by the system is larger than the maximum bandwidth capable of being provided by the system or not; if yes, enabling the power consumption of the system to be minimum on the premise of ensuring the service quality of each user; otherwise, keeping the fairness of each low-priority service on the premise of ensuring the high-priority service quality; and displaying a bandwidth allocation result and the total power consumption of the system. When the bandwidth requirements of the system are smaller than the maximum bandwidth capable of being provided by the system, the upstream bandwidth allocation scheduling algorithm disclosed by the invention can try hard to reduce the power consumption of the system on the premise of ensuring the bandwidth requirement of each ONU (optical network unit) so as to realize the purpose of energy saving; and when the bandwidth requirements of the system are larger than the maximum bandwidth capable of being provided by the system, the upstream bandwidth allocation scheduling algorithm can effectively allocate the bandwidth resource so as to be capable of ensuring that the system has the high-priority service quality and also to be capable of ensuring the fairness of the low-priority services.
Owner:SHANGHAI JIAO TONG UNIV
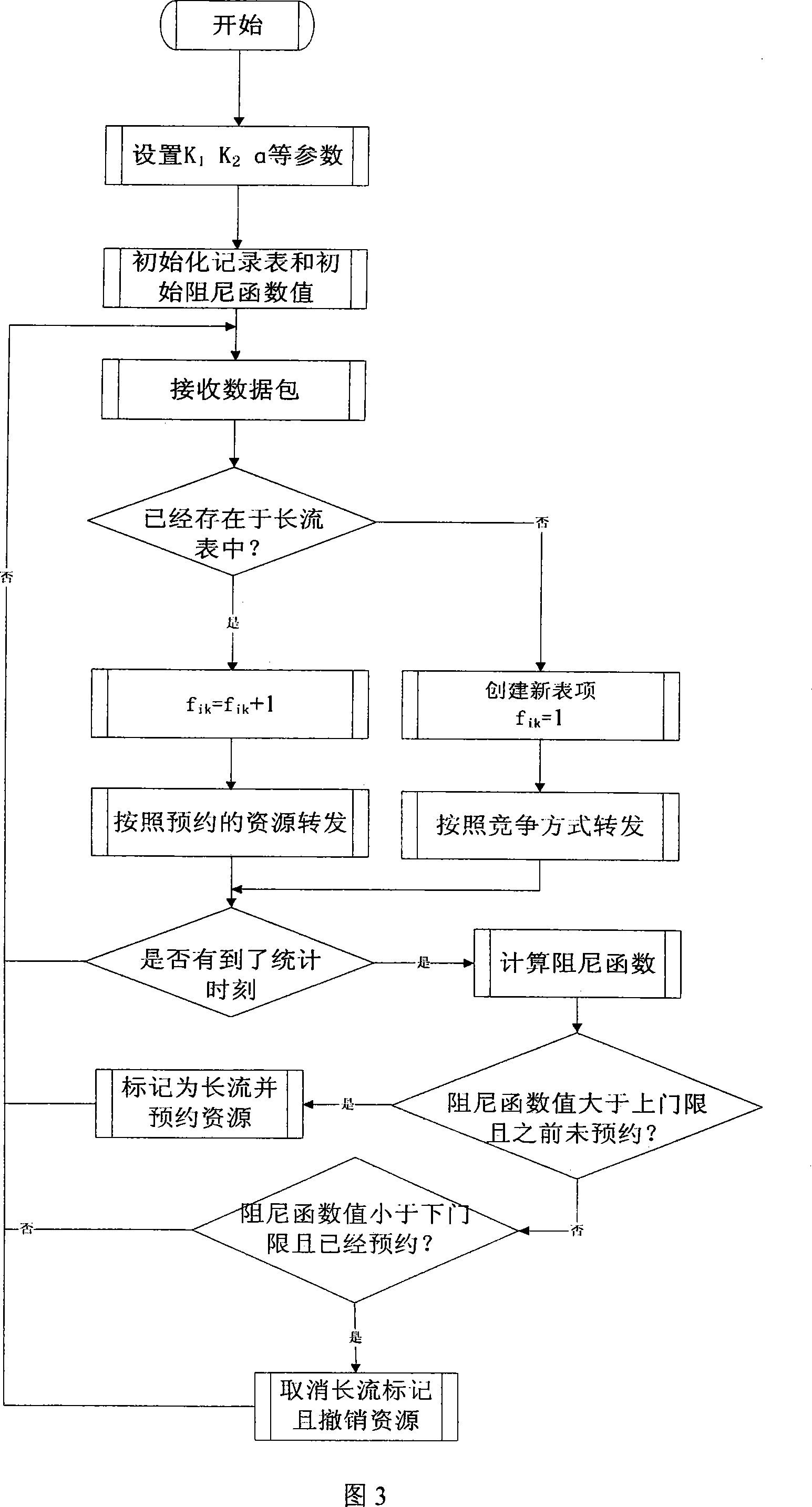
Method for implementing dynamic resource obligation of wireless self-organizing network by elephant flow detection
InactiveCN101247327AReduce utilizationLess fairnessData switching by path configurationDynamic resourceSelf-organizing network
The invention relates to a method for achieving dynamic resources obligating of a self organization network by using long traffic detection. The method avoids a traditional mechanism of a network node channel competition, and an important transaction and a high priority transaction can be forwarded in high reliability, the method for the dynamic resources obligating is recommended in Ad hoc network, and a channel distributed according to need is inserted into a control protocol, and network resource distribution is achieved to dynamic, and a goal for providing different resource to a different upper transaction is furthest achieved, meanwhile, the highest network transmission efficiency is kept in a station of lower network load and higher network load. The method can dynamically identify and distinct different characteristic transaction traffic in real time, and then the resource is directly obligated, and an operating factor of the channel is improved, and has high utility value.
Owner:PLA UNIV OF SCI & TECH
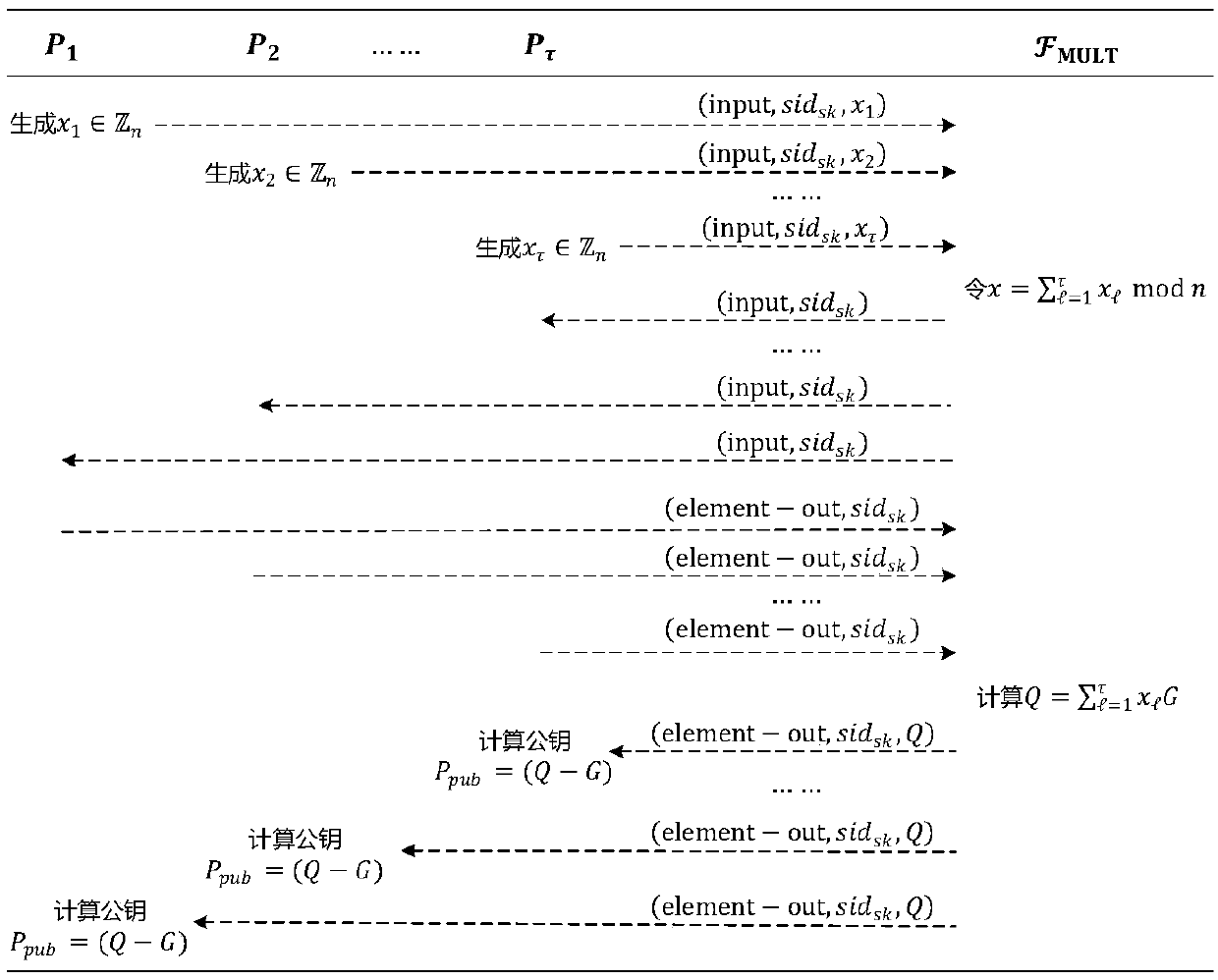
Method for jointly generating SM2 digital signature by multiple parties
ActiveCN109547199AImprove securityLess fairnessKey distribution for secure communicationPublic key for secure communicationGreek letter betaDigital signature
The invention discloses a method for jointly generating SM2 digital signature by multiple parties. The method comprises following steps that all parties P1, P2, ... , P<Tau> joining digital signaturerandomly select partial private keys x1, x2, ... , x<x>(belonging to Zn), and two partial random numbers k1, k2, ... , k<x>(belonging to Zn) and Rho1, Rho2, ... , Rho<x>(belonging to Zn); then all parties calculate through an interactive ideal function F<MULT> to obtain a public key P<pub>=(Q-G)=(Sigma<lota=1><Tau>x<lota>G-G) of SM2, and two intermediate variables R=Sigma<lota=1><Tau>k<lota>G=(r<x>,r<y>) and alpha =xRhomode n; for a message m, all parties separately calculate a hash value e=h(m) and a first signature r=r<x>+e mod n, and calculates through the interactive ideal function F<MULT>to obtain a third intermediate variable beta=Rho(k+r)mod n; and finally, all parties separately calculate a second signature s=min{alpha<-1>beta-r, n-alpha<-1>beta+r}, and outputs complete SM2 digital signature (r,s) after signature verification succeeds. Through adoption of the method, an SM2 digital signature is generated by multiple parties jointly, it is ensured that all parties do not disclose partial private keys in signing, and digital signature involves all parties, so that multi-party signature is safe and fair.
Owner:WUHAN UNIV
Two-party distributed identity-based RSA digital signature generation method and system
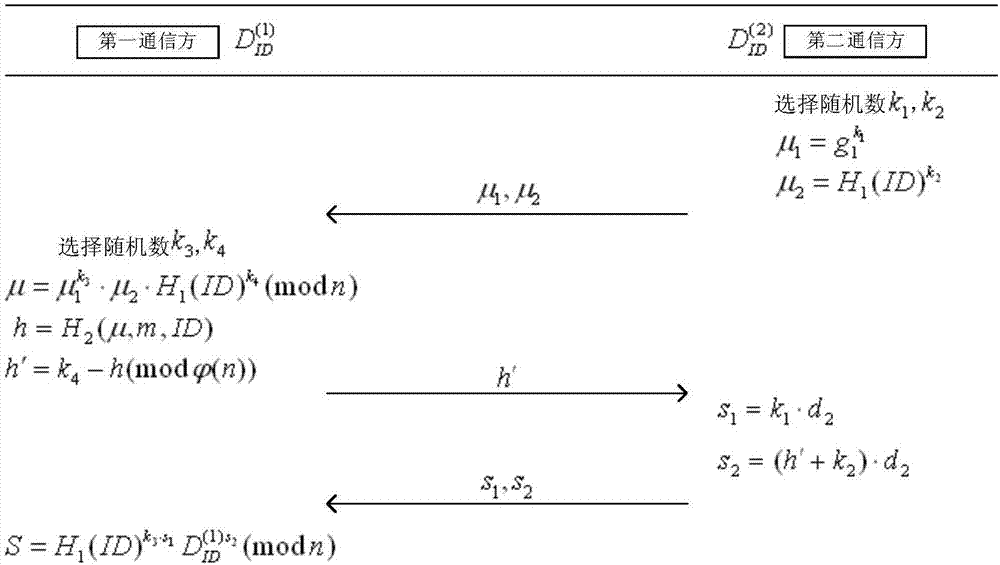
InactiveCN107888380ALess fairnessImprove fairnessPublic key for secure communicationUser identity/authority verificationDigital signatureComputer security
The invention relates to a two-party distributed identity-based RSA digital signature generation method and system. The method and system are implemented through the following technical schemes: a KGCgenerates partial signature keys FORMULA 1 and FORMULA 2 (as shown in the original document) for two communication parties A and B that participate in a digital signature respectively, after the partial signature keys are received, B firstly selects two random numbers k1, k2, calculates the formulas of mu1=g1k1 and mu2=H1(ID)k2, and sends mu1 and mu2 to A; and then A selects two random numbers k3, k4, calculates a first partial signature h, and sends FORMULA (as shown in the original document) to B; B calculates s1, s2 by using the own partial signature key, and sends s1, s2 to A; and after receiving s1, s2, A calculates a second partial signature FORMULA (as shown in the original document) by using the own partial signature key, and after the signature verification is successful, A publishes a complete RSA digital signature (h, S). According to the scheme of the invention, the security of the signature keys can be improved, and the fairness of signature schemes can also be ensured.
Owner:WUHAN UNIV
Digital supply chain purchasing platform
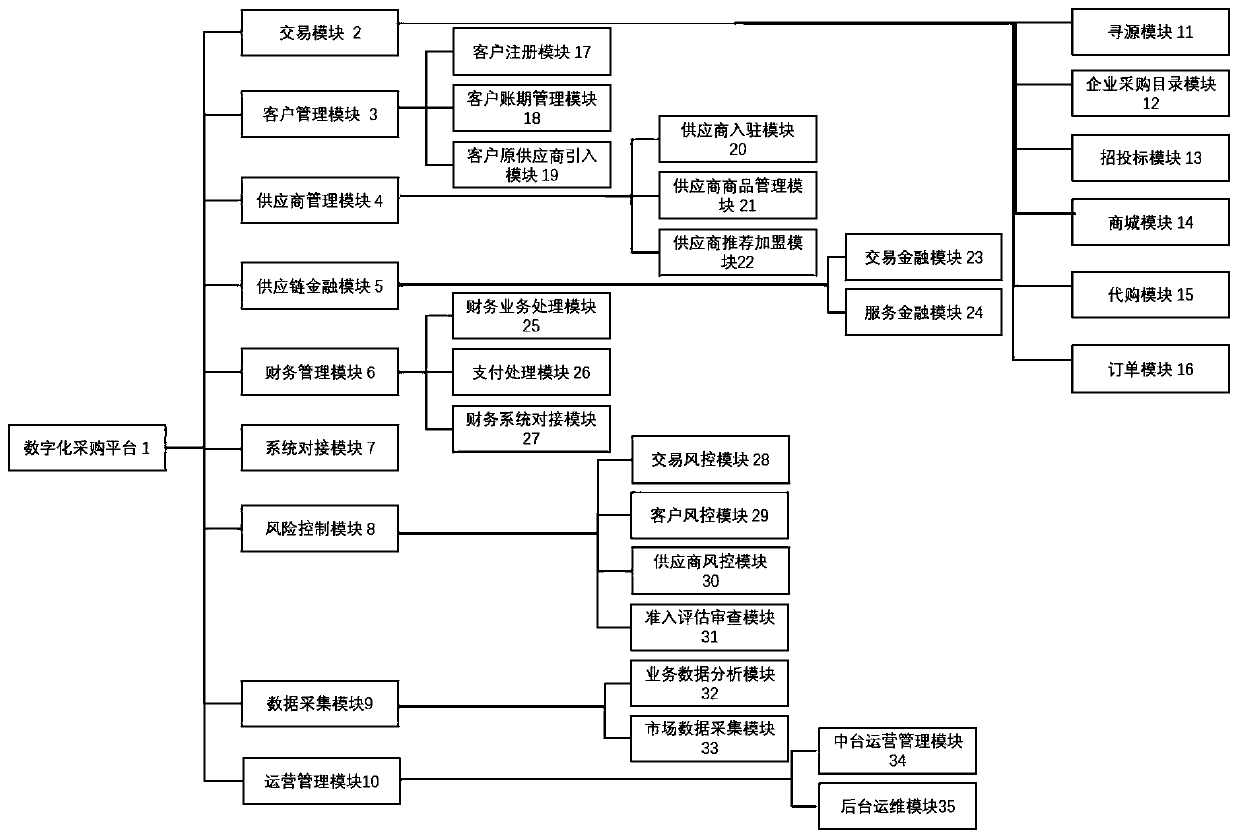
InactiveCN111461845AReduce operating costsReduce procurement costsBuying/selling/leasing transactionsFinancial transactionData profiling
The invention relates to the technical field of supply chains, in particular to a digital supply chain purchasing platform which comprises a transaction module, a customer management module, a supplier management module, a supply chain financial module, a financial management module, a system docking module, a risk control module, a data analysis module and an operation management module. The transaction module is used for performing process control and continuous tracking management on supply chain purchasing transaction behaviors. According to the digital purchasing platform, a customer supply chain enters platform type digital purchasing from single-point management, the labor cost of a customer purchasing link and a financial link is reduced, the purchasing cost of customers is reducedthrough a transparent and compliant purchasing process, and the purchasing efficiency is improved through real-time and rapid data transmission.
Owner:上海固买供应链管理有限公司
Virtual machine task scheduling method and system
ActiveCN103870313ARaise priorityImprove performanceProgram initiation/switchingSoftware simulation/interpretation/emulationVirtual machine
The invention discloses a virtual machine task scheduling method and system. The method includes the steps: detecting whether a current task belongs to a virtual machine set or not; processing the current task when the current task belongs to the virtual machine set; selecting a next task according to a default algorithm when the current task does not belong to the virtual machine set. Existence of a virtual machine can be perceived when the task is scheduled, the task belonging to the virtual machine set is preferentially selected, the priority of the virtual machine is equivalently improved, and performances of the virtual machine are improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Method for expanding capacity of Ad Hoc network through mitigating interference using multiple antennas MAC (MIMO-MAC) optimization
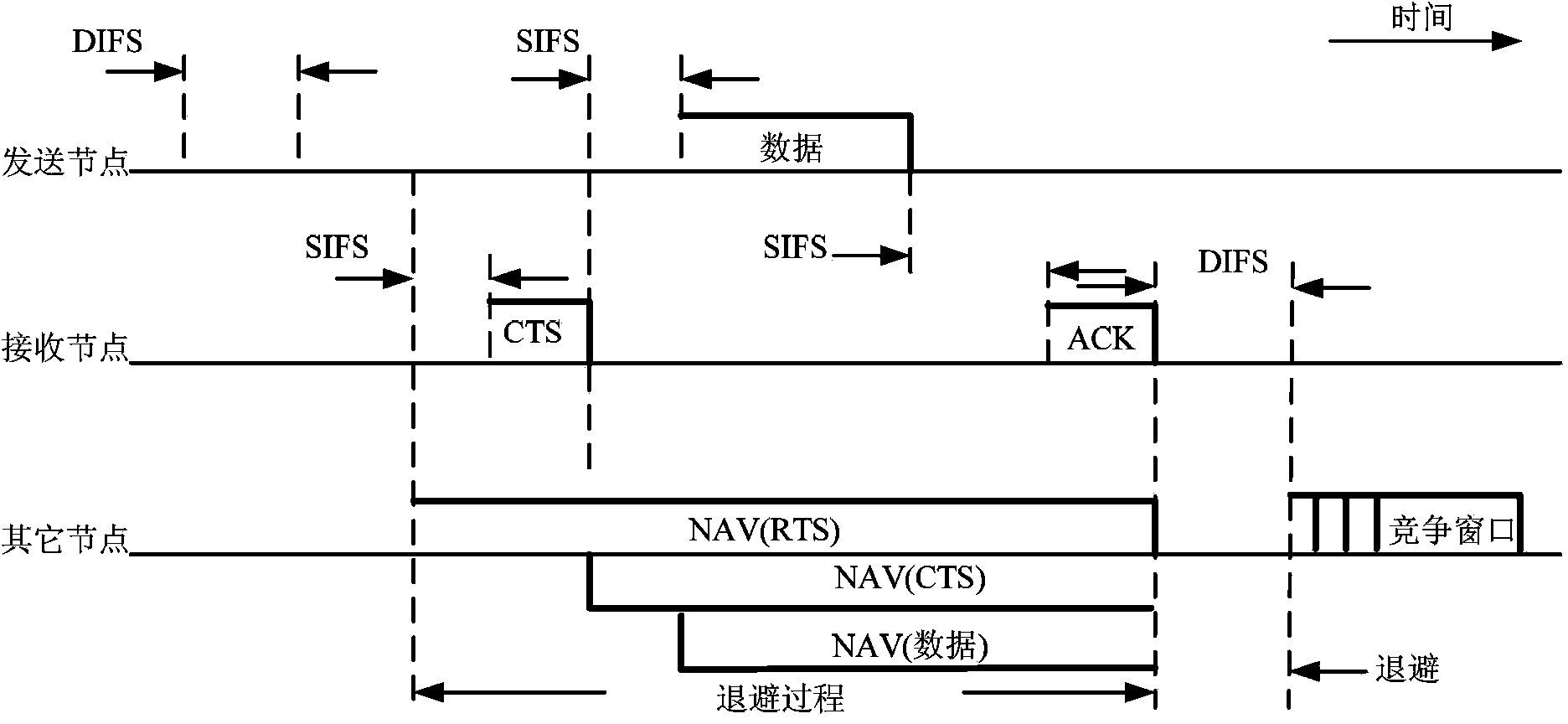
InactiveCN102137506AReduce interaction timeIncrease capacityError prevention/detection by using return channelWireless communicationHidden node problemClear to send
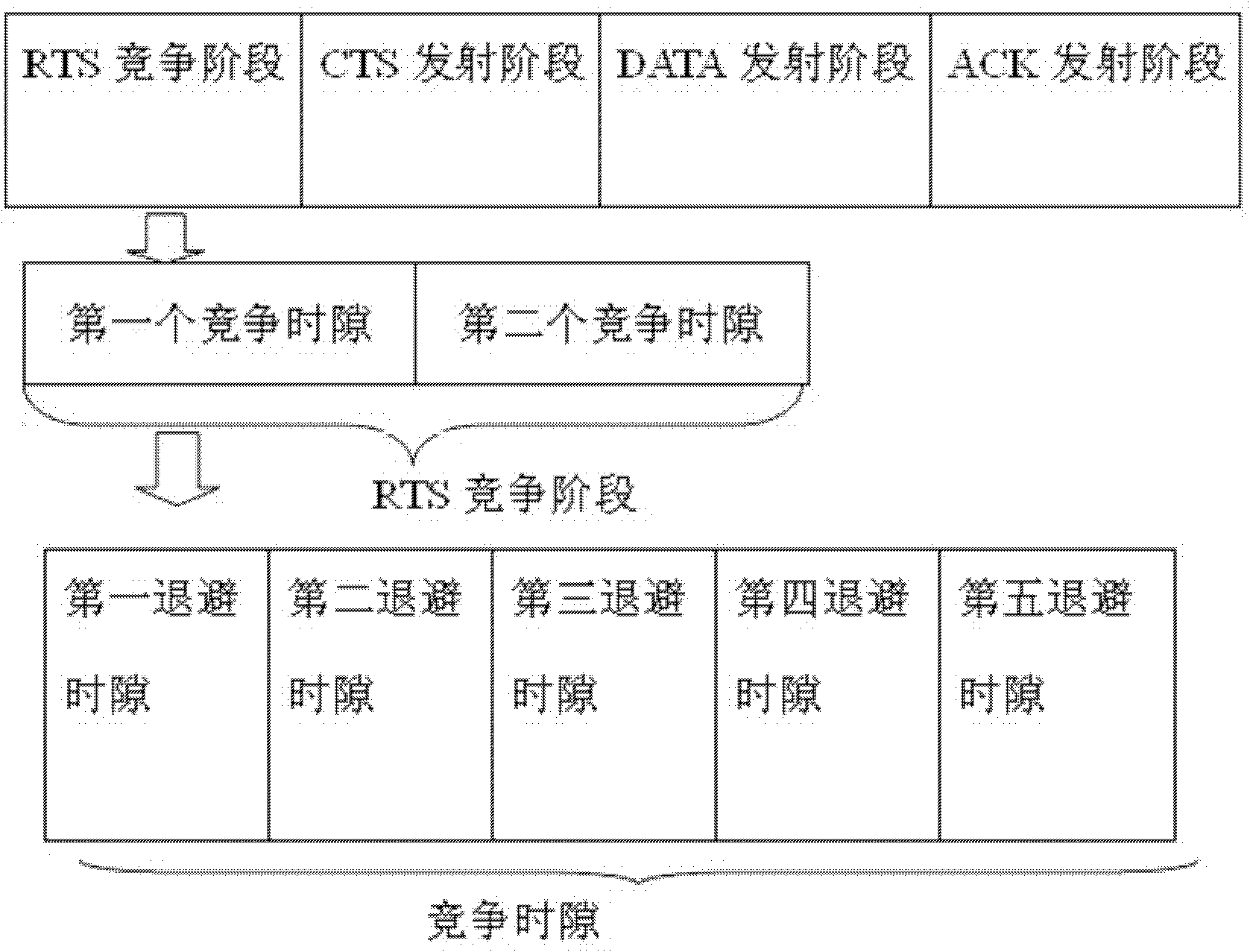
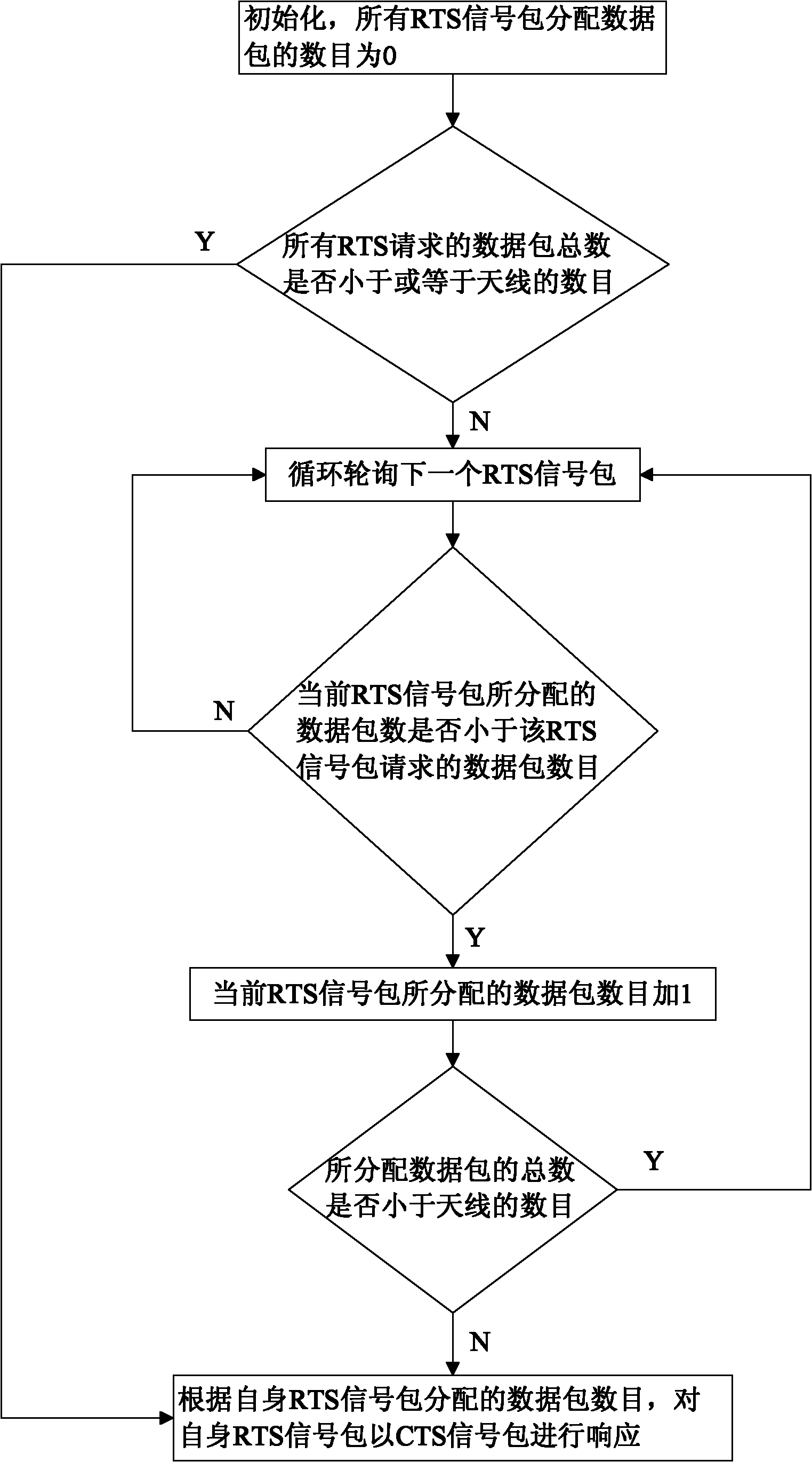
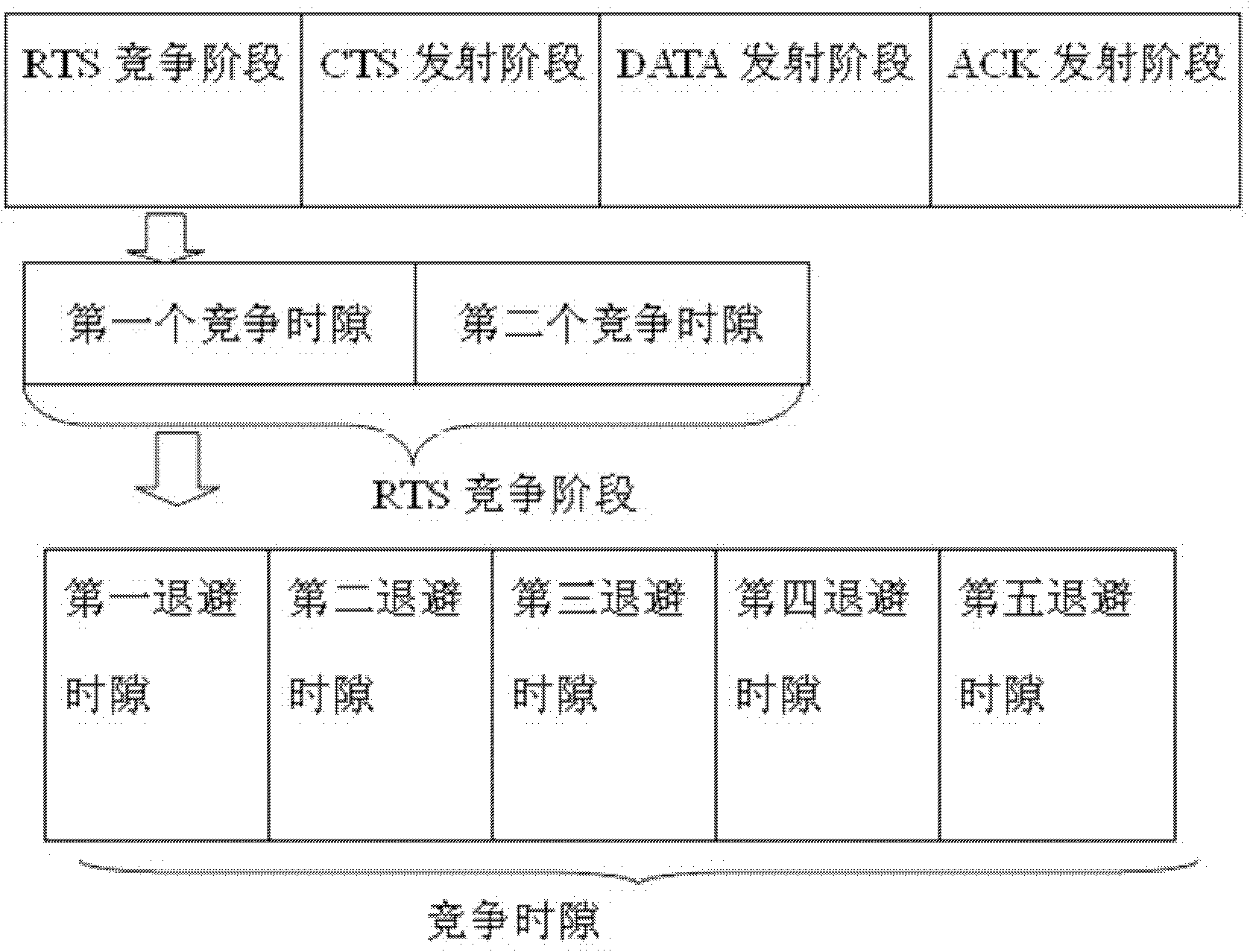
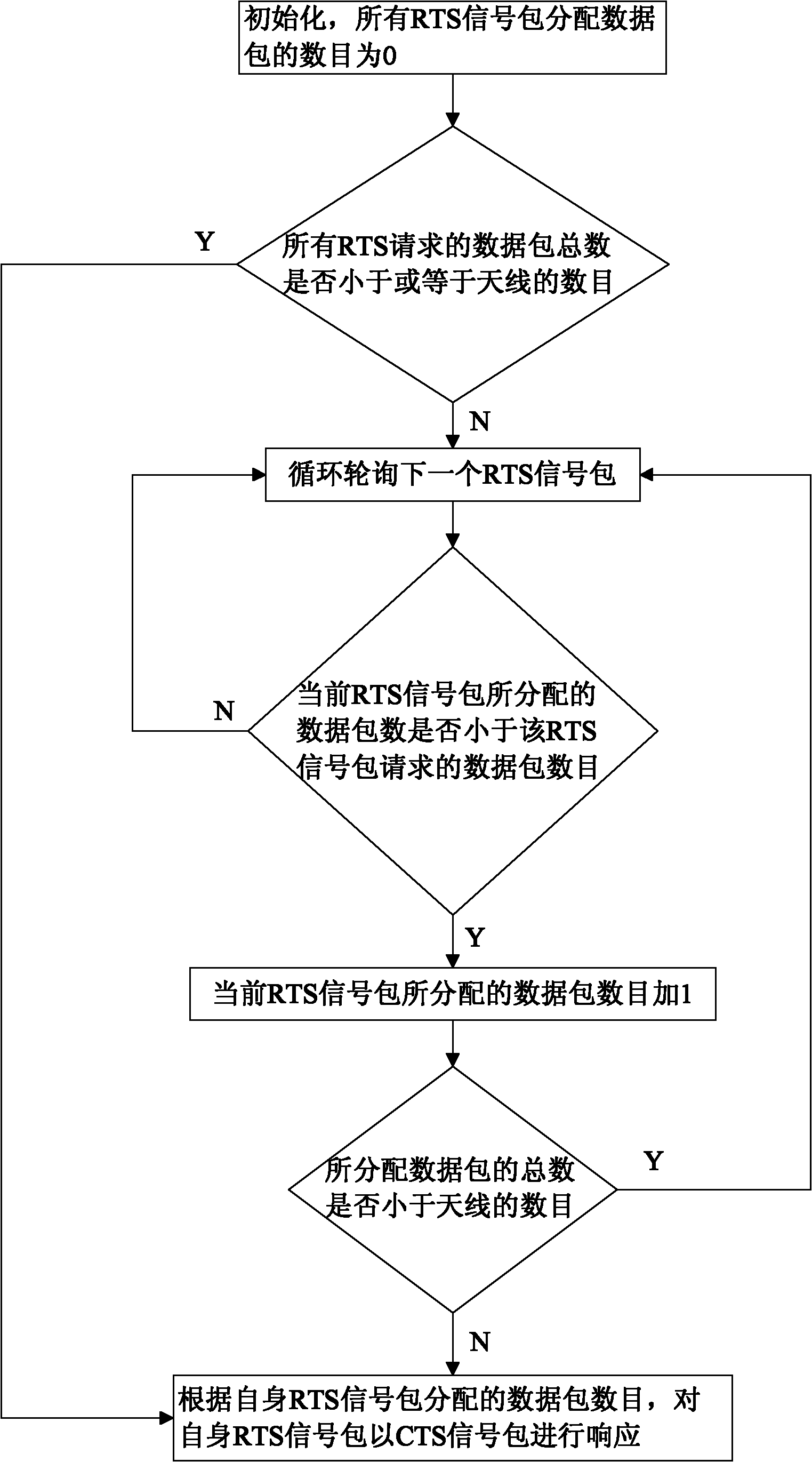
The invention discloses a method for expanding capacity of Ad Hoc network through mitigating interference using multiple antennas MAC (MIMO-MAC) optimization. The method comprises the following step that: each node is provided with a plurality of antennas, and the number of the antennas on each node is the same. Data frames of the MAC layer are synchronized and have four stages: namely a request to send (RTS) competing stage, a clear to send (CTS) emitting stage, a data (DATA) emitting stage and an acknowledgement (ACK) emitting stage, which are closely associated and cannot be separated. RTS signal packets in the method are emitted in a competition manner and CTS signal packets are synchronously emitted so as to shorten interactive time for RTS and CTS. The number of the data packets which can be emitted by each node is derived by a method for bilaterally allocating the data packets, so the problem of node hiding is solved and the capacity of the network is greatly expanded.
Owner:SOUTH CHINA UNIV OF TECH
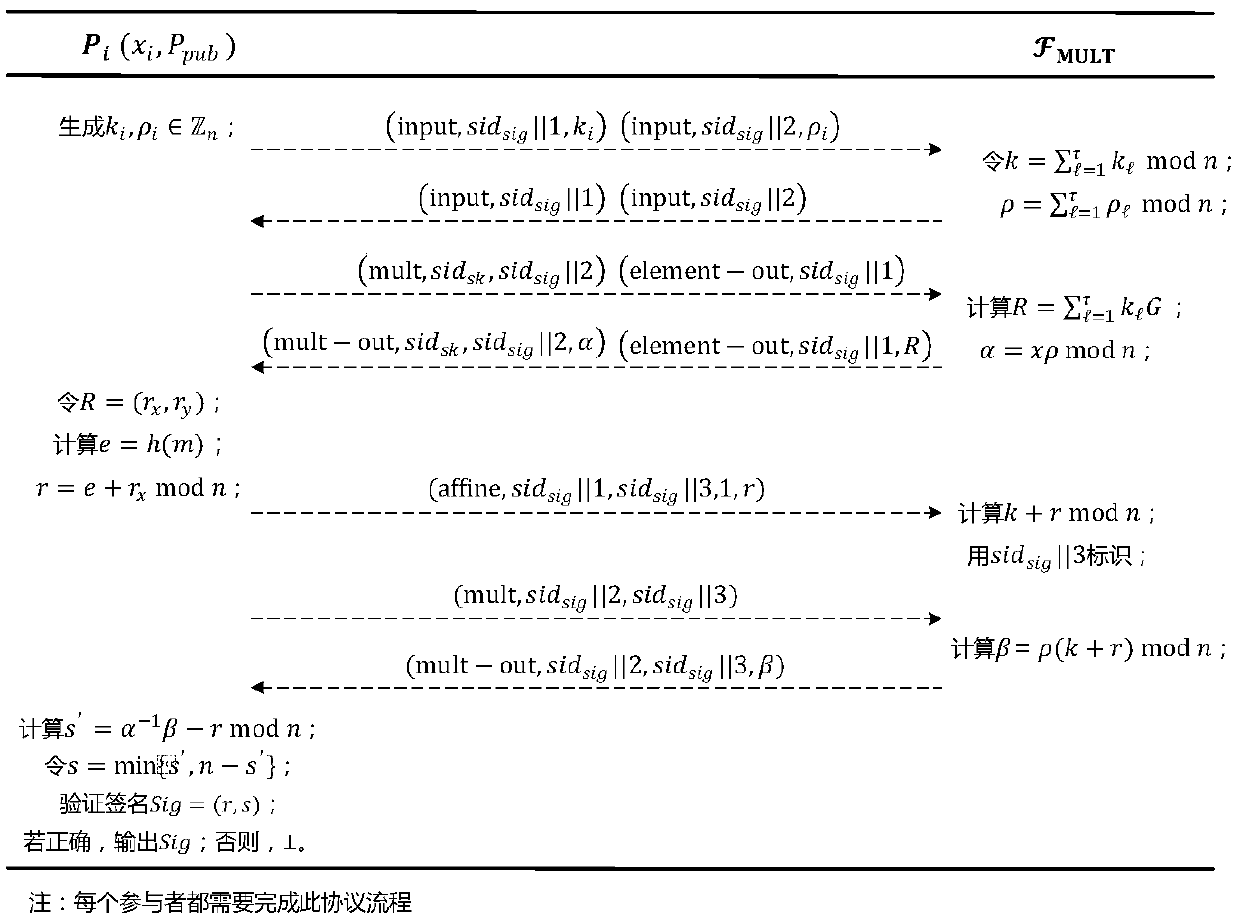
SM2 two-party collaborative signature method suitable for lightweight client and medium
ActiveCN111010285AEnsure safetyImprove securityUser identity/authority verificationHigh level techniquesDigital signatureNetwork architecture
The invention provides a network architecture for an unbalanced client / server. The invention relates to a scheme for generating an SM2 digital signature through cooperation of two parties, in particular to an SM2 two-party cooperative signature method suitable for a lightweight client and a medium, and in the scheme of the invention, when an SM2 digital signature is generated, the two parties participate together, one party is a client U, and the other party is a server S. And the client U and the server S cooperatively generate an SM2 signature about the message m by using respective partialprivate keys at the current stage. The method has the advantages of being high in safety, easy to implement and easy to verify.
Owner:WUHAN UNIV
Ultra-dense network wireless resource allocation method based on NOMA and beam forming
ActiveCN111615202AEnsure fairnessLess fairnessSpatial transmit diversityHigh level techniquesInterference (communication)Signal quality
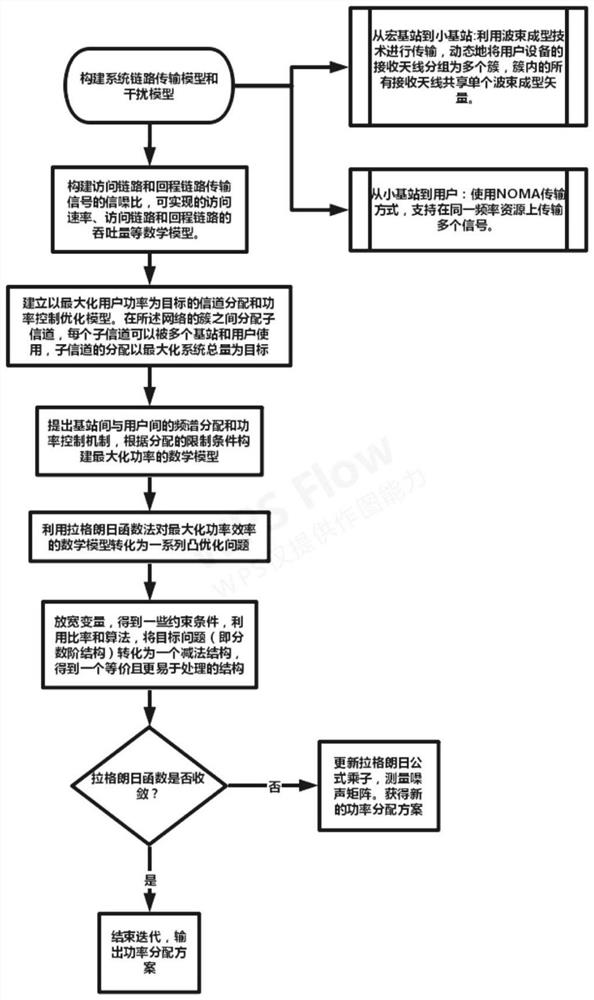
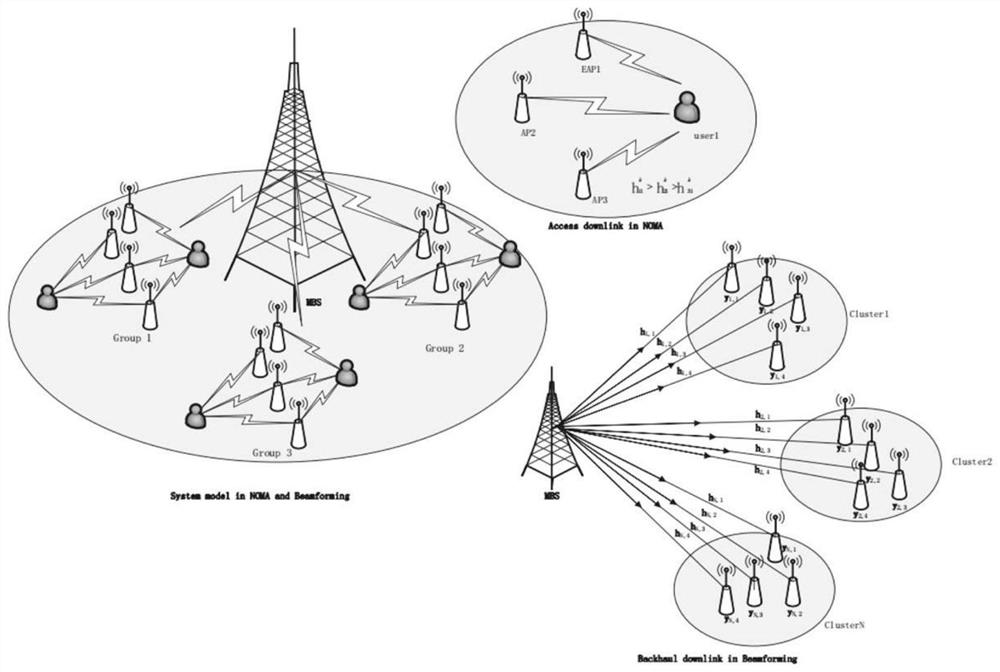
The invention discloses an ultra-dense network wireless resource allocation method based on NOMA and beam forming. The method comprises the steps: combining beam forming and NOMA; enabling a base station equipped with multiple antennas to communicate with user equipment equipped with multiple single antennas; employing beam forming to improve the coverage rate and the signal to noise ratio of signals from a macro base station to a small base station; adopting NOMA in the process that the small base station transmits the signals to users, and distributing different transmission powers to the different users so as to adapt to the situation that the users cannot feed back effective network state information according to the change of the network environment. According to the invention, inter-cluster interference and intra-cluster user interference are effectively suppressed; moreover, the fairness among users is ensured to a certain extent, the throughput performance of the system is improved, and power distribution is fairly and effectively carried out, so the system has the advantages of high throughput, high signal quality and high power efficiency, simultaneous communication of alarge number of users is supported, and the system performance and the spectrum utilization rate are greatly improved.
Owner:DONGGUAN UNIV OF TECH
Real-time low-packet-loss service scheduling method in TD-LTE
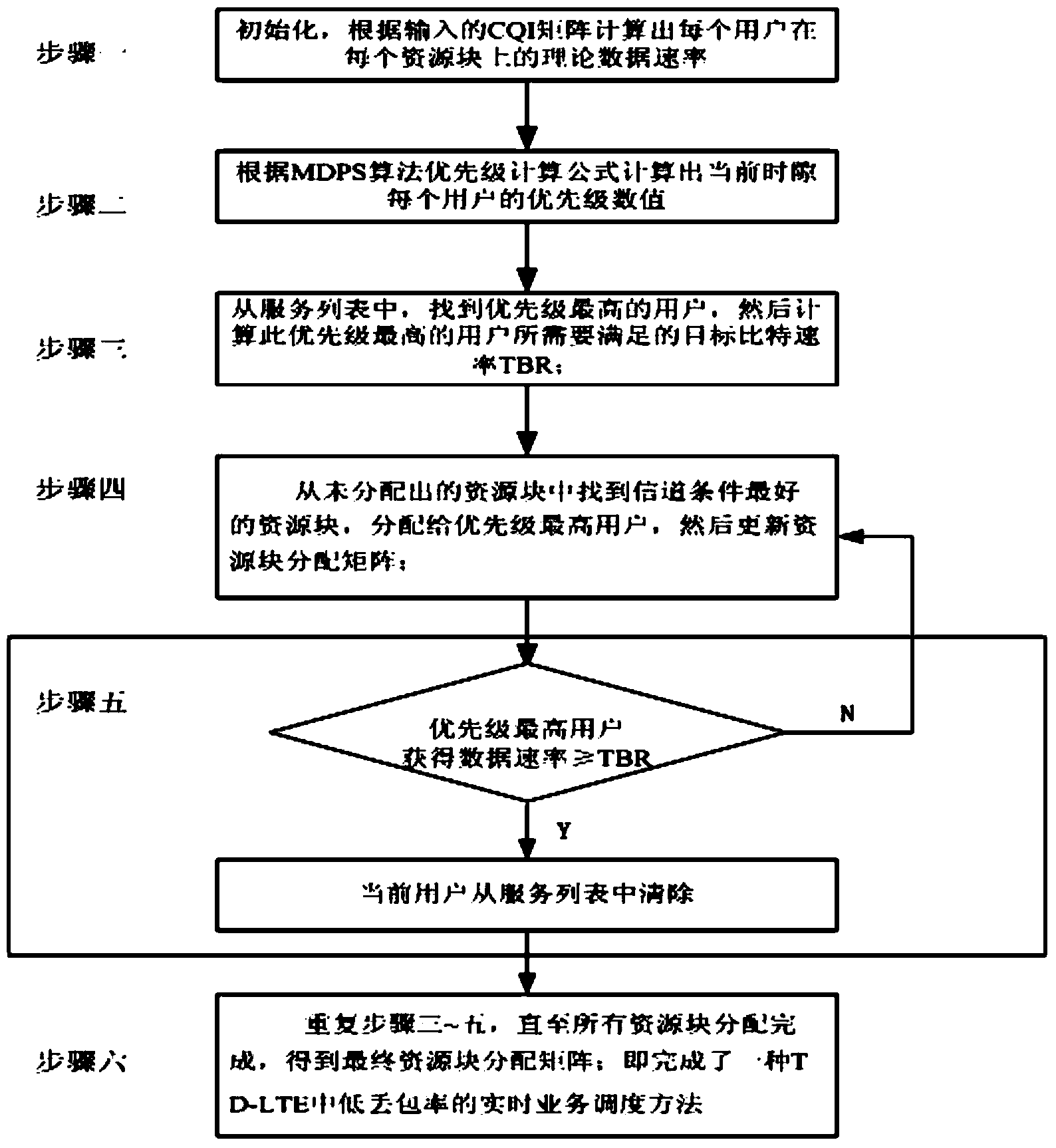
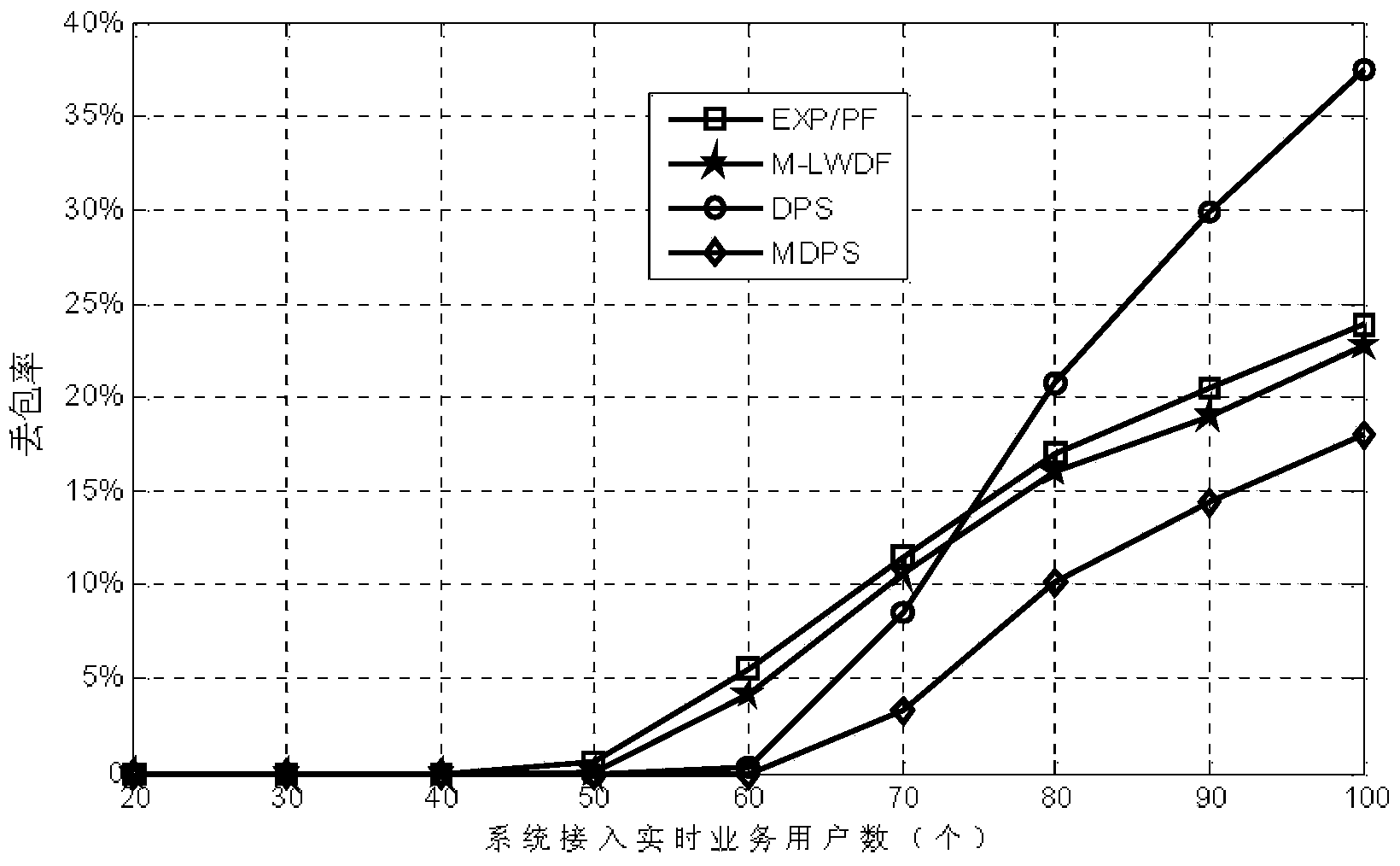
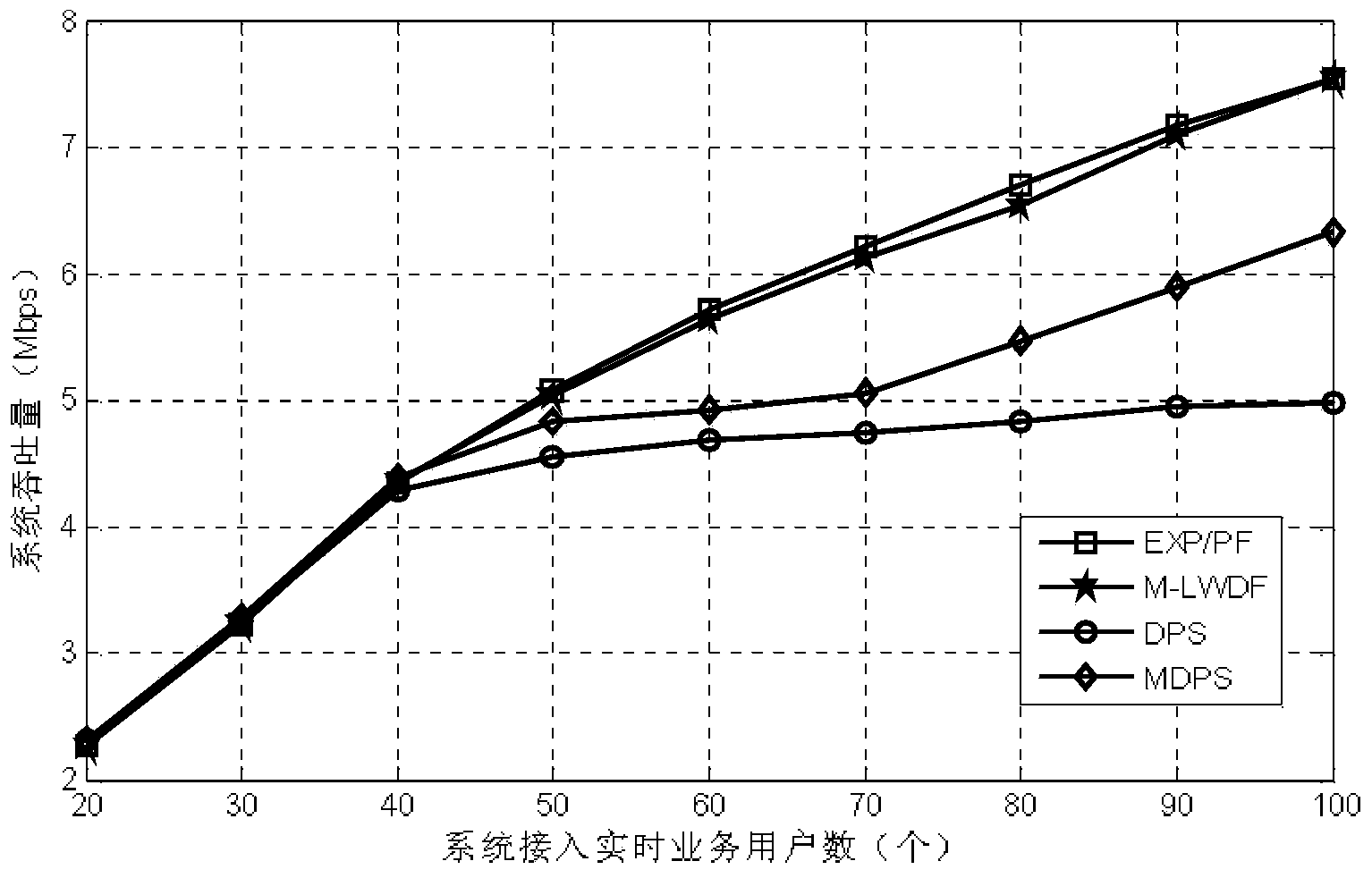
ActiveCN104066197AHigh packet loss ratePacket Loss GuaranteeError preventionWireless communicationRound complexityPacket loss
The invention relates to a real-time low-packet-loss service scheduling method in TD-LTE to solve the problems that in an existing TD-LTE system, the user packet loss is high, the throughput is low, the user delay situation, channel state and scheduling algorithm complexity is high, and the computing amount is large. The method comprises the steps that firstly, initializing is carried out; secondly, priority values of all users are worked out according to the MDPS algorithm; thirdly, the user with the highest priority is found out, and the met target bit rate is calculated; fourthly, a resource block with the best channel condition is found out and allocated to the user with the highest priority, and updating is carried out; fifthly, whether the data rate of the user with the highest priority is larger than or equal to TBR or not is judged; sixthly, the steps from the third to the fifth are repeatedly executed until all resource blocks are allocated to obtain a final resource block allocation matrix. The real-time low-packet-loss service scheduling method is applied to the mobile communication field.
Owner:HARBIN INST OF TECH
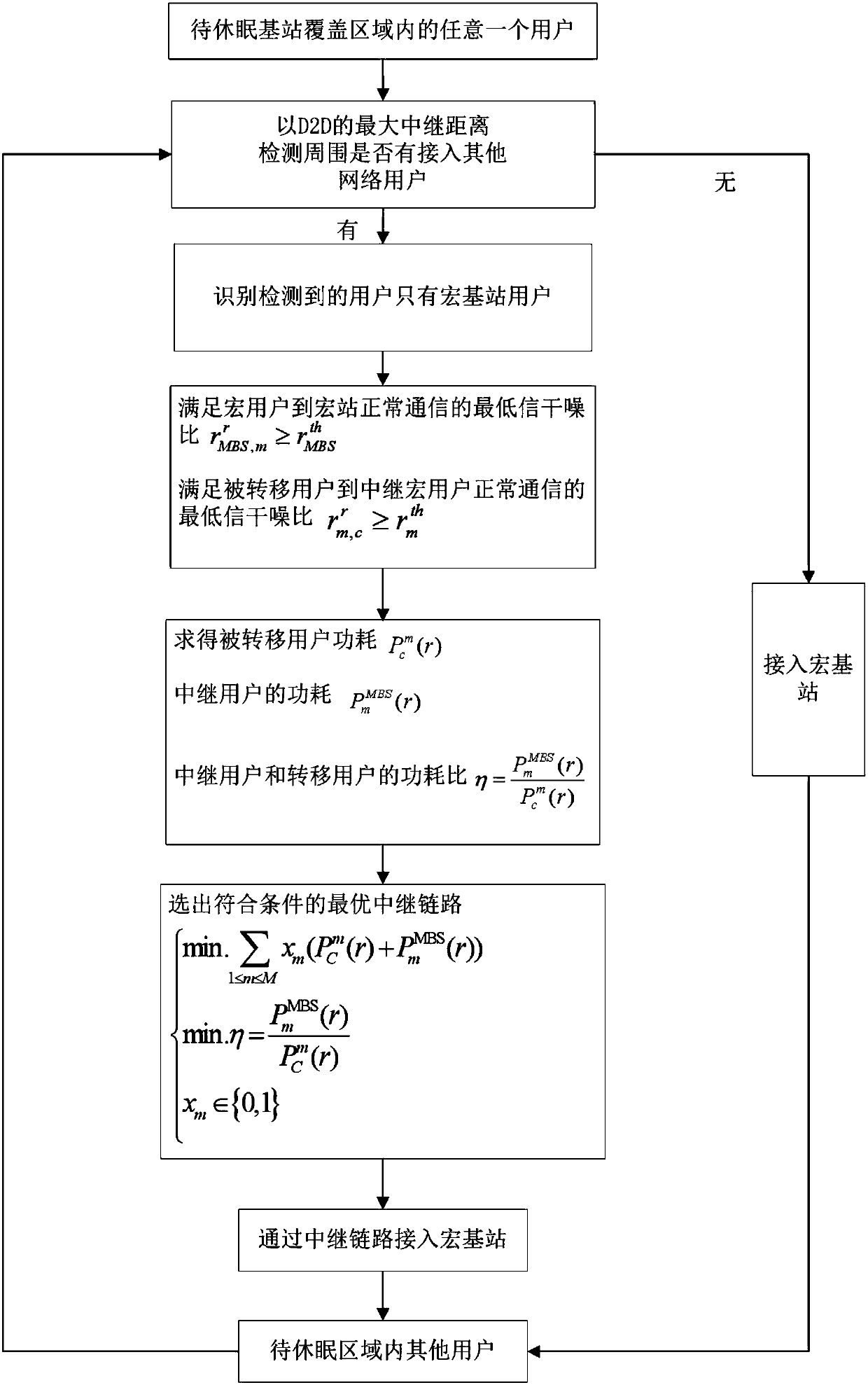
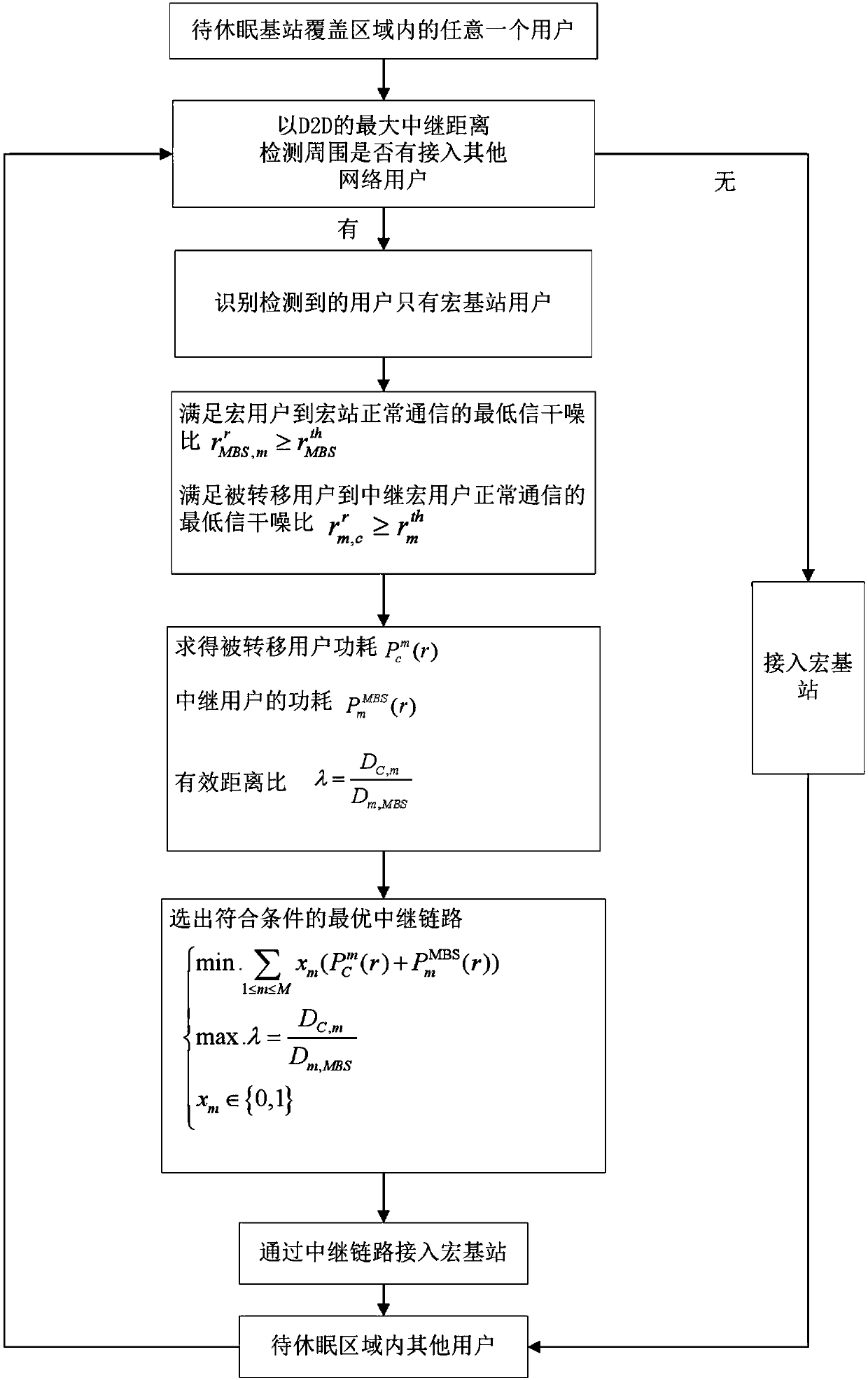
Energy-saving transfer path selection method for user side in heterogeneous network based on D2D relay
ActiveCN108337714AReduce power consumptionEnsure fairnessPower managementHigh level techniquesMacro base stationsReal time communication systems
The invention discloses an energy-saving transfer path selection method for a user side in a heterogeneous network based on a D2D relay. A relay link is selected in a classification manner by distinguishing a network type of a relay user. When a macro base station user is selected as the relay, the power consumption proportion of the macro relay user is controlled by adopting a minimum relay powerconsumption proportion method under the condition that the total power consumption of the relay link is ensured to be minimum; and when a small base station user is selected as the relay, the power consumption of the relay user is reduced by adopting the minimum relay power consumption proportion method under the condition that the lowest energy consumption required for normal communication of the link is ensured, at the same time, the effective rate of an uplink of the small base station relay user is adjusted, and the load of the relay user accessing the surrounding small base station is balanced. The method controls the total power consumption of the relay link, reduces the power consumption of the user terminal and balances the load of the surrounding receiving base station while meeting normal communication of the user, and is suitable for a real-time communication system.
Owner:江苏三台山数据应用研究院有限公司
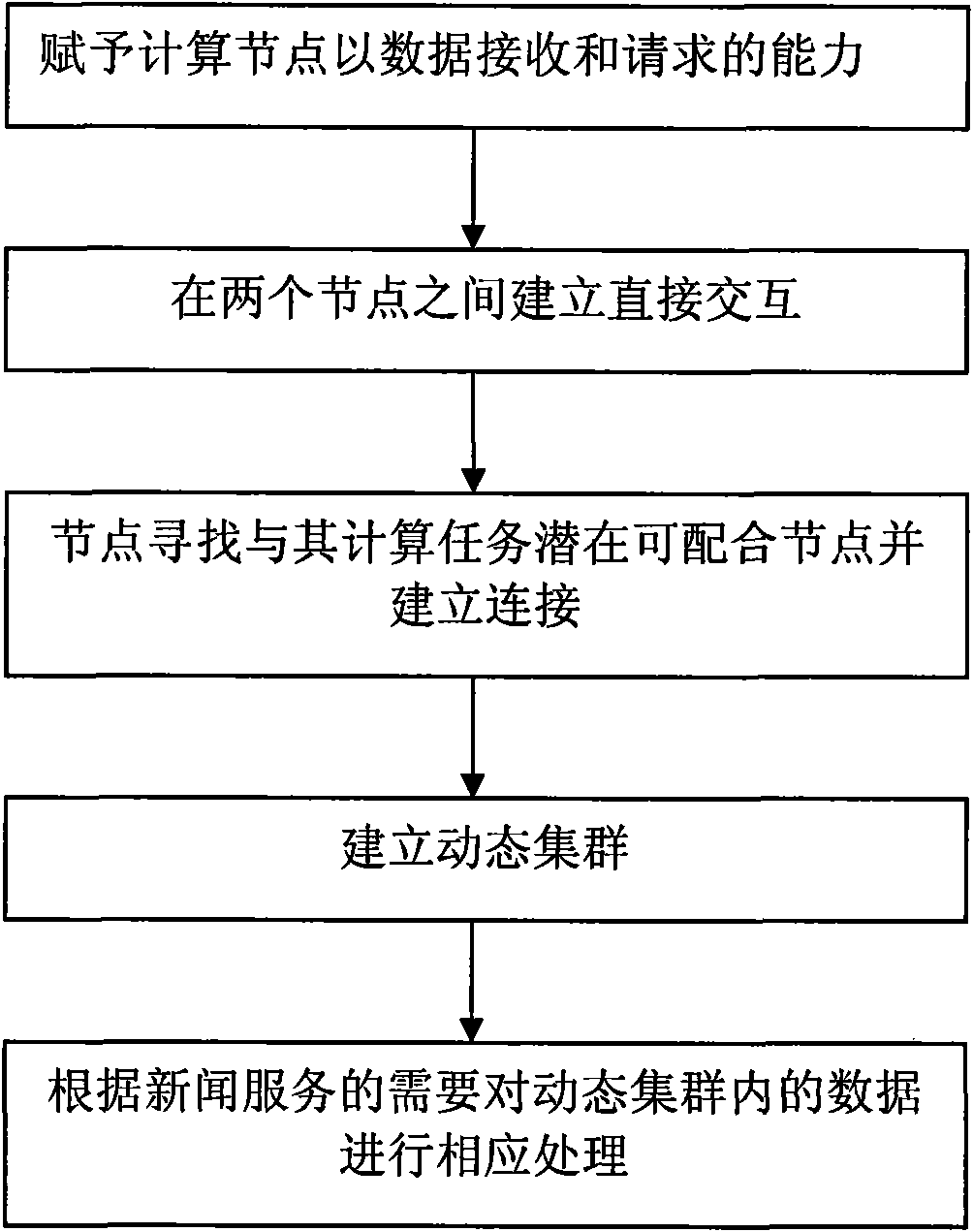
Dynamic cluster-based news service method
InactiveCN101645911AEnsure fairnessPlay value effectivelyData switching networksThe InternetCluster based
The invention discloses a cluster-based news service method and belongs to the field of Internet application and development. The method comprises: firstly, establishing data receiving and request mechanisms at computing nodes; secondly, establishing direct interaction between any two nodes to allow the nodes to find potential nodes that can be matched with the computing tasks of the nodes and establishing connection between the nodes and the potential nodes; and finally, establishing a dynamic cluster according to a stream network protocol, wherein a news system performs corresponding processing of data in the dynamic cluster according to the needs of news service. The news service method can grasp the change of news timely and accurately for providing various news services such as effective news sequencing and interaction function supply timely and effectively.
Owner:PEKING UNIV
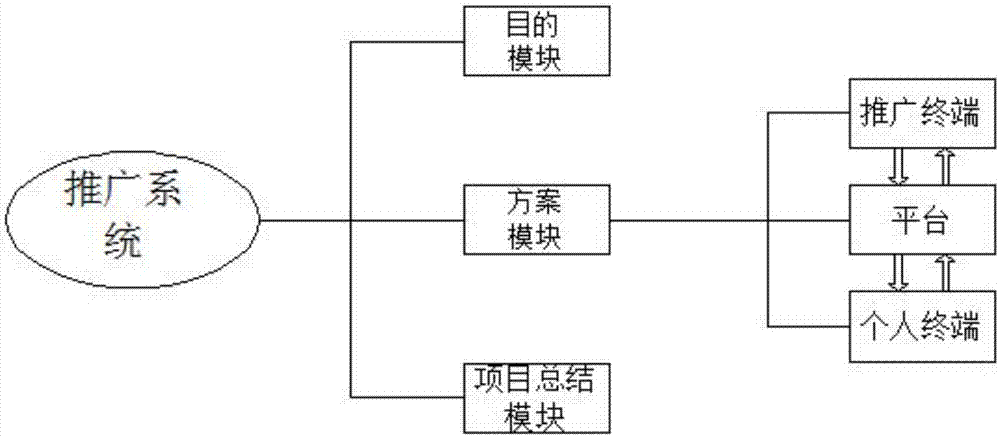
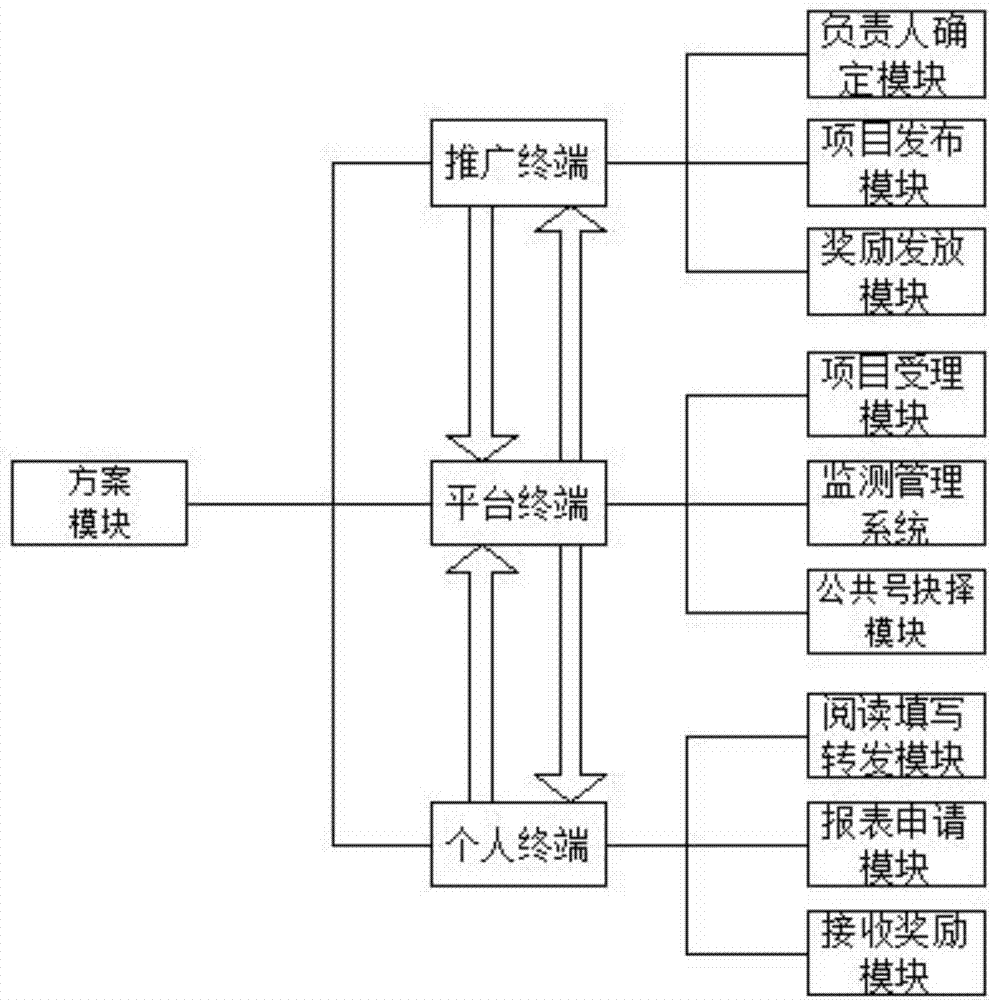
Internet-based promotion system and method
InactiveCN107346500AReasonable designEasy to operateDiscounts/incentivesAdvertisementsPublic accountComputer terminal
The invention discloses an Internet-based promotion system and method, belonging to a promotion system. The promotion system comprises a target module, a plan module and a project summary module. A release mode of a plan is formed by a promotion terminal, a platform terminal and a personal terminal, and the platform terminal is connected to the promotion terminal and the personal terminal through a data transmission unit. The promotion terminal comprises a responsible person determination module, a projection release module and a reward releasing module. The platform terminal comprises a projection acceptance module, a monitoring and management system and a public account selection module. The personal terminal includes a reading, filling and forwarding module, a report application module and a reward receiving module. The project promotion is carried out through a credit platform terminal, the reward promotion is carried out in a fair and impartial way, all the people involve, and a promotion effect can be obtained in a very short time.
Owner:合肥左成传媒科技有限公司
Receding method based on physical layer channel quality estimation constraint
ActiveCN103441827AAchieve protectionData flowError prevention/detection by using return channelBaseband system detailsChannel dataData stream
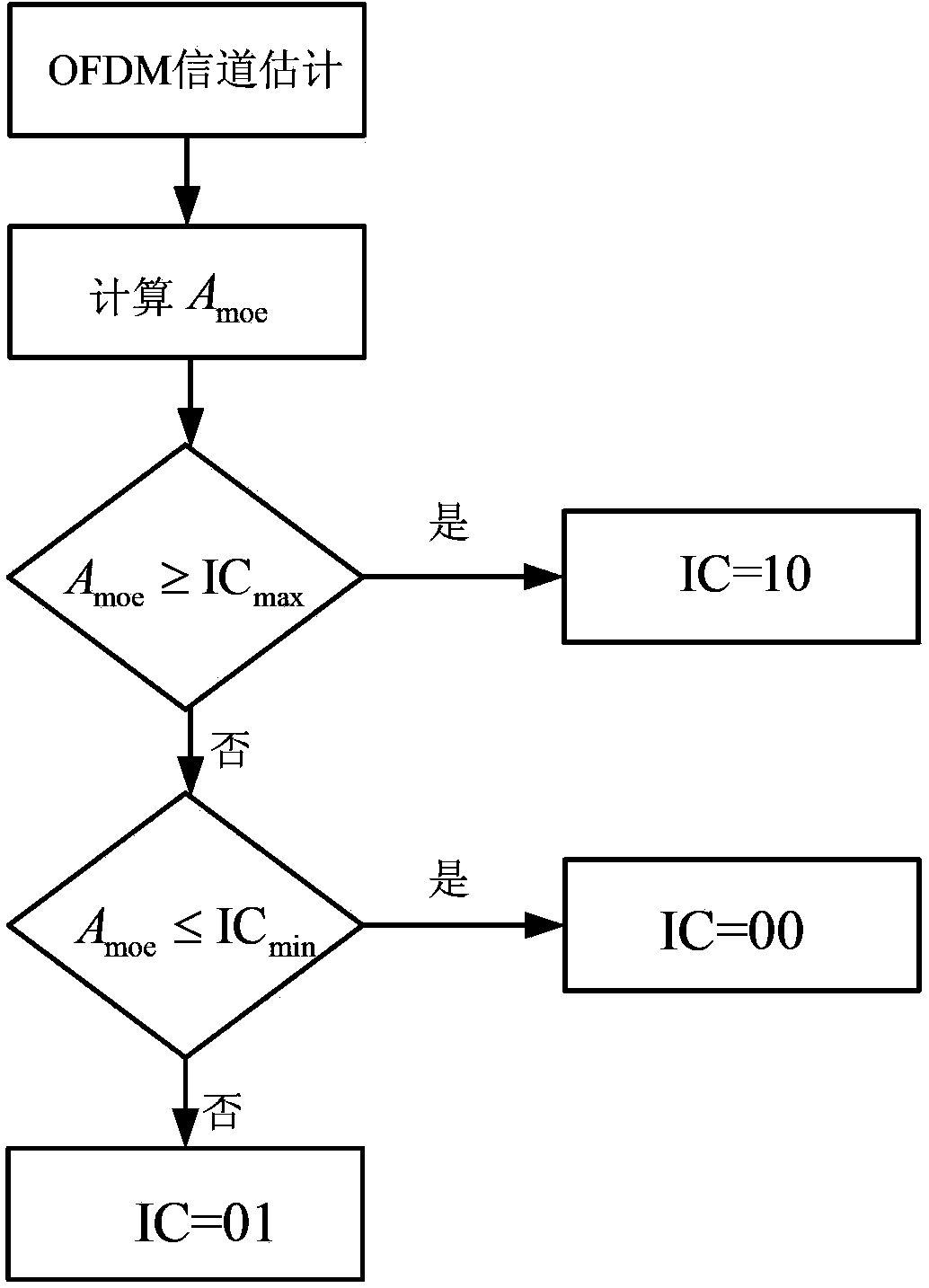
The invention discloses a receding method based on physical layer channel quality estimation constraint, and relates to an MAC layer receding method which is based on the physical layer channel quality estimation constraint and suitable for being used on the premise of MPSK modulation. The significance of the receding method is to provide a capacity for a wireless local area network system, and the capacity includes obtaining channel quality information between receiving nodes and sending nodes in real time through training data by the utilization of a network physical layer, handing over the channel quality information to an MAC layer, moreover, duly adjusting receding parameters and modifying values of a receding counter through the channel quality information, and thereby providing appropriate competition channels for the nodes. An OFDM system blind equalization technology of a PHY layer is used for obtaining channel quality estimation criterions, then the criterions are applied to the receding method, and the receding method finally achieves protection of high-quality channel data flows.
Owner:WENZHOU UNIVERSITY
Coal on-line transaction platform and using method thereof
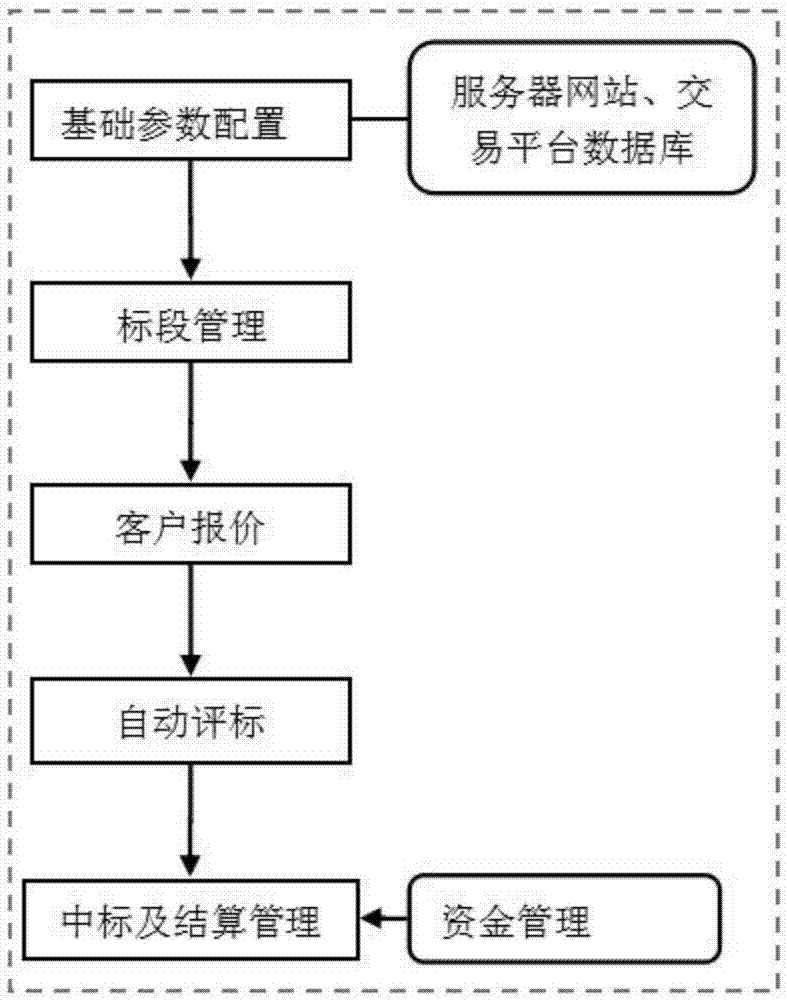
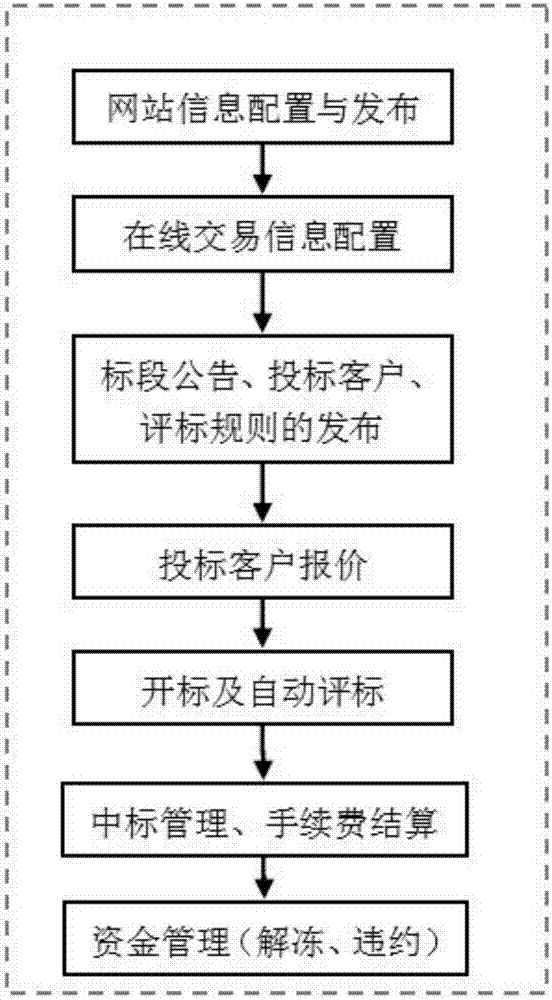
PendingCN107480905ALess fairnessAvoid influenceBuying/selling/leasing transactionsResourcesData centerLibrary science
The invention discloses a coal on-line transaction platform and a using method thereof. The platform includes a website configuration module, a data center module, a basic parameter configuration module, a tender management module, a customer quotation module, a bid opening and evaluation module, a successful bid management module, a fund management module and a server database. The using method includes issuing website information configuration and website data; configuring coal on-line transaction basic data; processing businesses such as tender announcement, tender information, and bidding client screening; starting the bidding quotation after qualified bidding clients pay the corresponding guarantee funds; performing bid opening and evaluation on the clients who participate the biding quotation after the quotation is closed and automatically generating the pre-bidding according to the evaluation rules; confirming the successful bid information and deducting the corresponding fees and converting the fees into a performance bond; and managing the funds of the clients who win the bidding. The platform provided can reduce the influence on the fairness and impartiality of the bid evaluation results due to human factors.
Owner:合肥明信软件技术有限公司
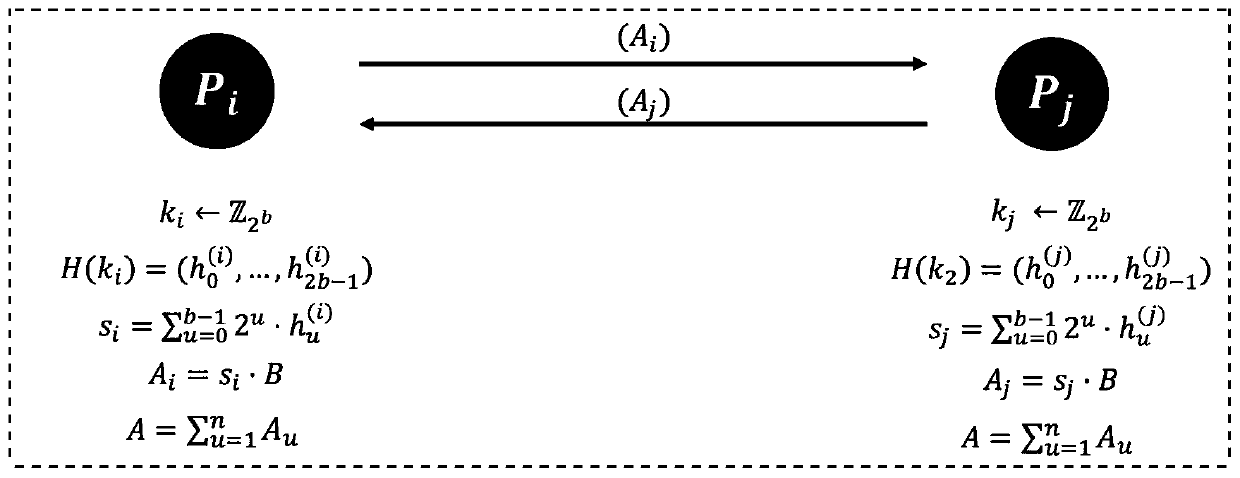
Multi-party collaborative EdDSA digital signature generation method and medium
PendingCN110995441AImprove securityLess fairnessUser identity/authority verificationEdDSAInternet privacy
The invention relates to a multi-party collaborative EdDSA digital signature generation method and a medium. The method comprises the following steps of: generating a secret key, specifically, cooperatively generating an EdDSA signature about a message M by a participant set by utilizing secret key information of a secret key generation stage in the stage in order to calculate a part of signatureprivate keys and a cooperative signature by multi-party joint participation. The method is suitable for two-party or more than two-party collaborative signature application scenarios, can prove the security of the collaborative signature application scenarios, and has the characteristics of high security, simplicity in implementation and easiness in verification.
Owner:WUHAN UNIV
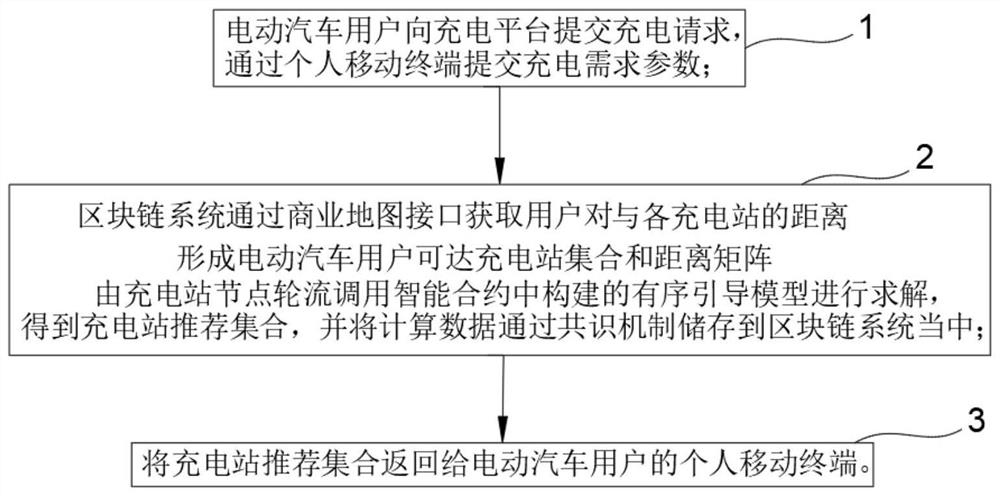
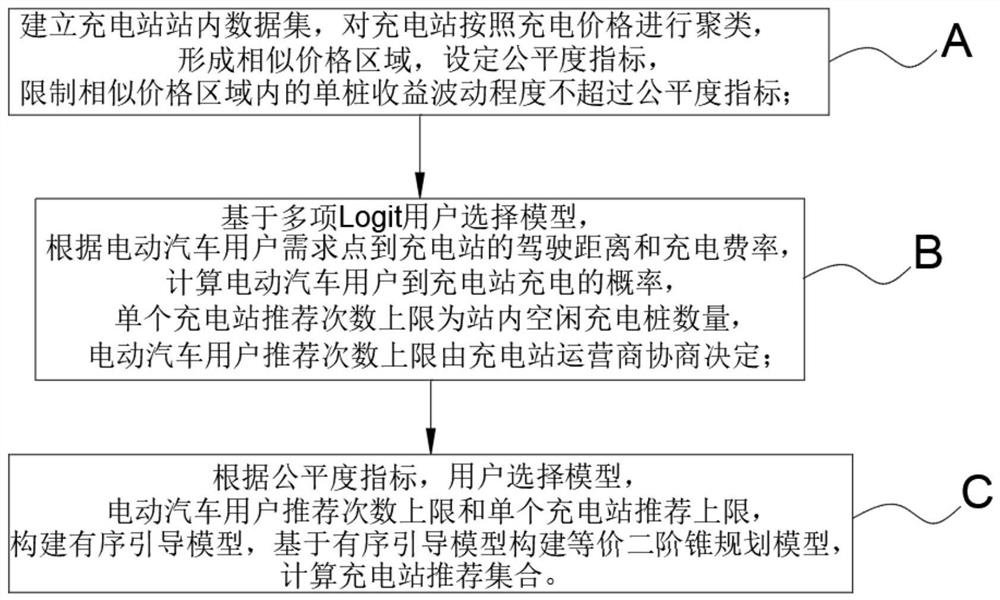
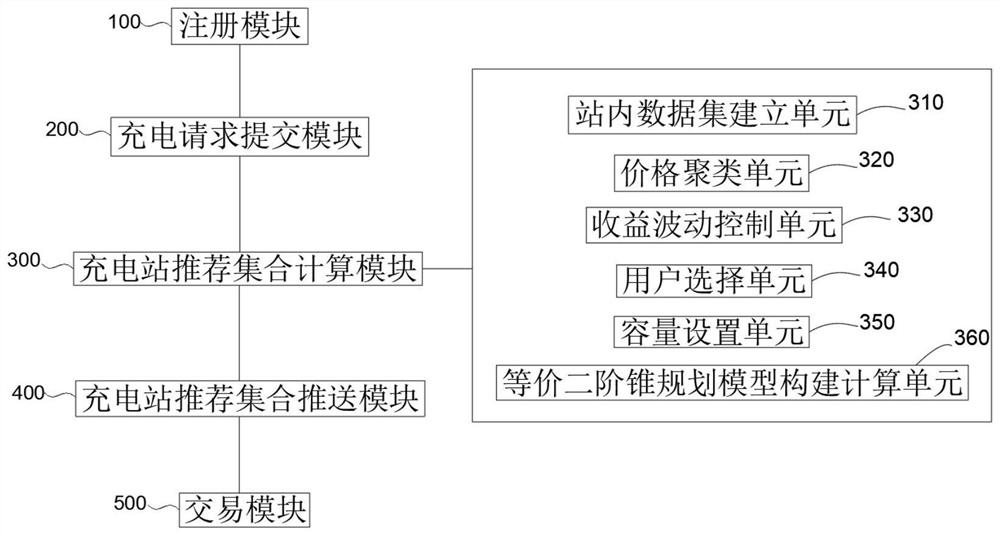
Electric vehicle ordered charging guiding method and system based on block chain smart contract
The invention relates to the technical field of block chain technology and electric vehicle charging scheduling, in particular to an electric vehicle ordered charging guiding method and system based on a block chain smart contract. An electric vehicle user submits charging demand parameters to a charging platform, and a block chain system obtains the distance between the user and each charging station through a commercial map interface to form an electric vehicle user reachable charging station set and a distance matrix. And the charging station nodes call the ordered guidance model constructed in the smart contract in turn for solving, a charging station recommendation set is obtained, and calculation data is stored in a block chain system through a consensus mechanism. According to the method, the block chain technology is combined, the fairness index is introduced, the fluctuation degree of the single pile income is limited, the charging station set is provided for the user through the user selection model and the ordered charging guide model, the fairness of income distribution of a charging station operator is guaranteed, and the charging effectiveness of the user is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
An Identity-Based Anonymous Authentication Method and System
ActiveCN107947913BImprove securityLess fairnessKey distribution for secure communicationUser identity/authority verificationSecure communicationInternet privacy
The invention relates to an identity-based anonymous authentication method and system. The method comprises the following steps: a server generates two partial private keys and sends the same to double parties P1 and P2 participating in the authentication respectively, wherein P1 and P2 generate a main authentication code (the formula is described in the specification) and R in an authentication process, and the privacy and reliability of the interactive information between P1 and P2 are ensured by using zero knowledge proof; after the P1 obtains the main authentication code, the P1 generatesa pseudo-address AID, generates a third temporary public key R3, calculates a final authentication code alpha, and sends the authentication information (AID, R, R3, alpha, T) the server, and the server verifies the authentication information and feeds back the authentication information to a user, after the successful completion of three times of handshake, the server can establish secure communication with the user. The identity-based anonymous authentication method and system are suitable for jointly completing identity-based distributed anonymous authentication without exposing the respective partial authentication private keys of the both parties together, the both parties holding the partial private keys must participate in the authentication at the same time, and the complete authentication private key does not need to be restored.
Owner:WUHAN UNIV
Method for expanding capacity of Ad Hoc network through mitigating interference using multiple antennas MAC (MIMO-MAC) optimization
InactiveCN102137506BReduce interaction timeIncrease capacityError prevention/detection by using return channelWireless communicationHidden node problemClear to send
The invention discloses a method for expanding capacity of Ad Hoc network through mitigating interference using multiple antennas MAC (MIMO-MAC) optimization. The method comprises the following step that: each node is provided with a plurality of antennas, and the number of the antennas on each node is the same. Data frames of the MAC layer are synchronized and have four stages: namely a request to send (RTS) competing stage, a clear to send (CTS) emitting stage, a data (DATA) emitting stage and an acknowledgement (ACK) emitting stage, which are closely associated and cannot be separated. RTS signal packets in the method are emitted in a competition manner and CTS signal packets are synchronously emitted so as to shorten interactive time for RTS and CTS. The number of the data packets which can be emitted by each node is derived by a method for bilaterally allocating the data packets, so the problem of node hiding is solved and the capacity of the network is greatly expanded.
Owner:SOUTH CHINA UNIV OF TECH
Wireless network data transmission method and network node
Disclosed are a data transmission method for a wireless network and a network node, which are used for the network node to configure the time domain length of a wireless frame on an unlicensed spectrum, so that different network nodes can occupy a channel, so as to achieve the fairness of network resource occupancy. The method of the embodiments of the present invention comprises: a network sending node determines the time domain length of the next one or more wireless frames of a current wireless frame on an unlicensed spectrum; the network sending node configures, according to the time domain length of the next one or more wireless frames, the next one or more wireless frames; and when an idle channel is detected via a CCA, the network sending node sends the configured next one or more wireless frames to a network receiving node.
Owner:HUAWEI TECH CO LTD
A virtual machine task scheduling method and system
ActiveCN103870313BRaise priorityImprove performanceProgram initiation/switchingSoftware simulation/interpretation/emulationAlgorithm SelectionVirtual machine
The invention discloses a virtual machine task scheduling method and system. The method includes the steps: detecting whether a current task belongs to a virtual machine set or not; processing the current task when the current task belongs to the virtual machine set; selecting a next task according to a default algorithm when the current task does not belong to the virtual machine set. Existence of a virtual machine can be perceived when the task is scheduled, the task belonging to the virtual machine set is preferentially selected, the priority of the virtual machine is equivalently improved, and performances of the virtual machine are improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Uplink Bandwidth Allocation and Scheduling Algorithm in Optical Orthogonal Frequency Division Multiplexing Access System
InactiveCN103051563BLow powerReduce energy consumptionMultiplex system selection arrangementsMulti-frequency code systemsBandwidth requirementOptical network unit
The invention discloses an upstream bandwidth allocation scheduling algorithm of an O-OFDM (optical orthogonal frequency division multiplexing) access system. The upstream bandwidth allocation scheduling algorithm comprises the following steps of collecting a bandwidth requirement of each user; comparing whether bandwidth required by the system is larger than the maximum bandwidth capable of being provided by the system or not; if yes, enabling the power consumption of the system to be minimum on the premise of ensuring the service quality of each user; otherwise, keeping the fairness of each low-priority service on the premise of ensuring the high-priority service quality; and displaying a bandwidth allocation result and the total power consumption of the system. When the bandwidth requirements of the system are smaller than the maximum bandwidth capable of being provided by the system, the upstream bandwidth allocation scheduling algorithm disclosed by the invention can try hard to reduce the power consumption of the system on the premise of ensuring the bandwidth requirement of each ONU (optical network unit) so as to realize the purpose of energy saving; and when the bandwidth requirements of the system are larger than the maximum bandwidth capable of being provided by the system, the upstream bandwidth allocation scheduling algorithm can effectively allocate the bandwidth resource so as to be capable of ensuring that the system has the high-priority service quality and also to be capable of ensuring the fairness of the low-priority services.
Owner:SHANGHAI JIAOTONG UNIV
Feature selection optimization method and device and readable storage medium
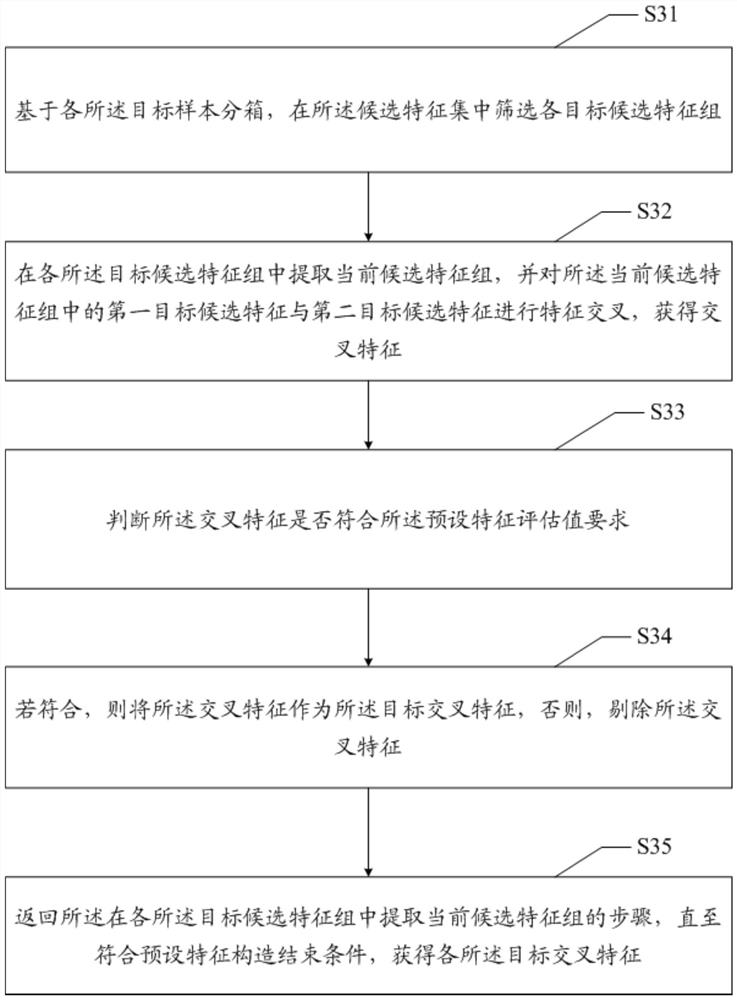
PendingCN112633414ALess fairnessImproved feature selectionEnsemble learningCharacter and pattern recognitionFeature setEngineering
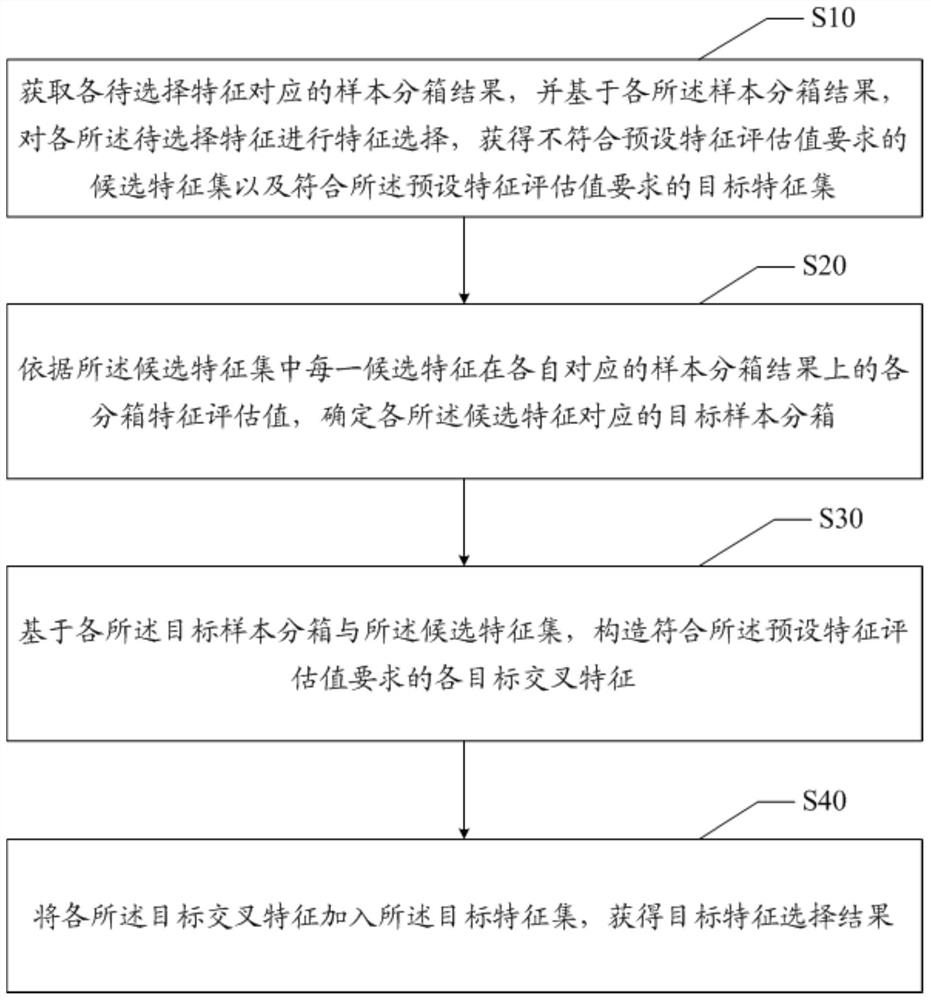
The invention discloses a feature selection optimization method and device and a readable storage medium, and the method comprises the steps: obtaining a sample binning result corresponding to each to-be-selected feature, and carrying out the feature selection of each to-be-selected feature based on each sample binning result, obtaining a candidate feature set which does not meet the requirements of a preset feature evaluation value and a target feature set which meets the requirements of the preset feature evaluation value; determining a target sample binning corresponding to each candidate feature according to each binning feature evaluation value of each candidate feature in the candidate feature set on the respective corresponding sample binning result; based on each target sample sub-box and the candidate feature set, constructing each target cross feature meeting the requirement of the preset feature evaluation value; and adding each target cross feature into the target feature set to obtain a target feature selection result. The technical problem that the feature selection effect is poor is solved.
Owner:WEBANK (CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com