Identity-based anonymous authentication method and system
An anonymous authentication and identity technology, applied in the field of information security, can solve problems such as system security that threatens the rights and interests of other users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
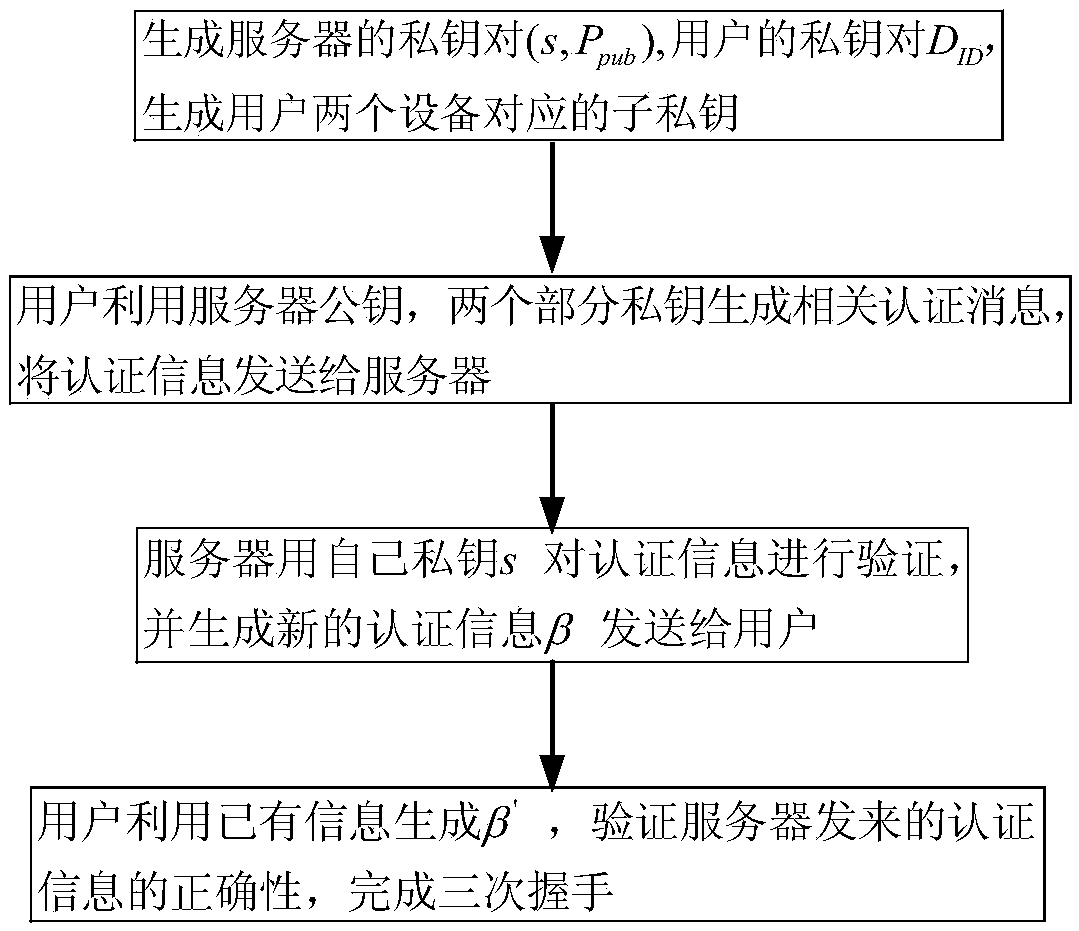
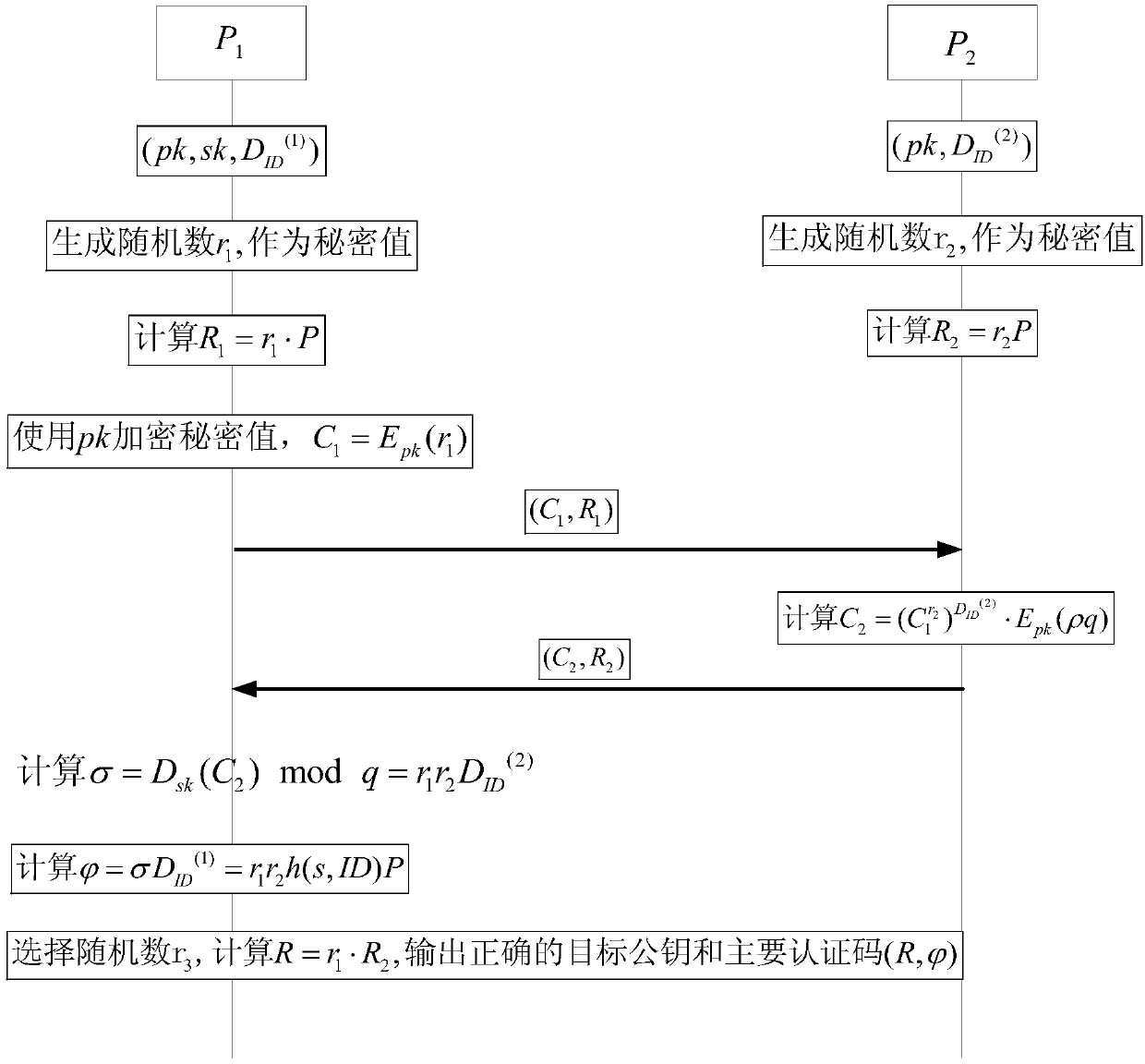
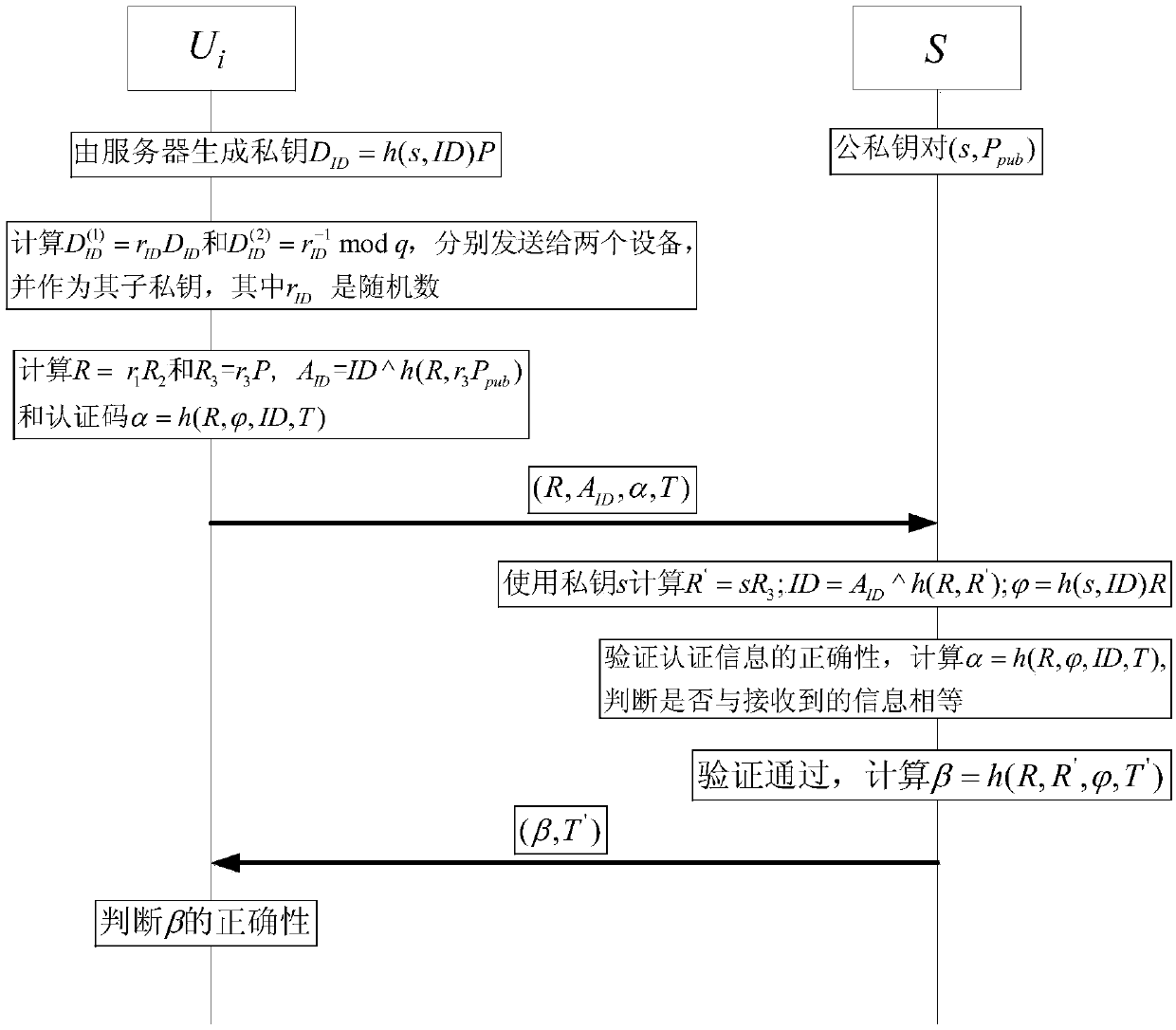
[0040] The present invention will be described in detail below in conjunction with examples. The following embodiments only show that the present invention is a possible implementation, not all possible implementations, and are not intended to limit the present invention.
[0041] In the following description of the present invention, the authenticated party is referred to as the user for short, and the authenticating party is referred to as the server for short. When two integers are multiplied (or integer symbols multiplied), if there is no ambiguity, the multiplication sign "·" is omitted, for example, a·b is simplified to ab. mod n means modulo n operation, and the priority of modulo n operation is the lowest. For example, a+b mod n is equivalent to (a+b) mod n, and ab mod is equivalent to (ab) mod n. "≡" represents a congruence formula, that is, a≡b mod n is equivalent to a mod n=b mod n. gcd(a, b) means finding the greatest common factor of integers a and b, if gcd(a, b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com