Multi-party collaborative EdDSA digital signature generation method and medium
A digital signature and multi-party technology, applied in the field of information security, can solve problems such as threats to security and fairness, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0043] This scheme contains two algorithms: Key Generation Algorithm and Cooperative Signature Algorithm.
[0044] 1. Key generation algorithm
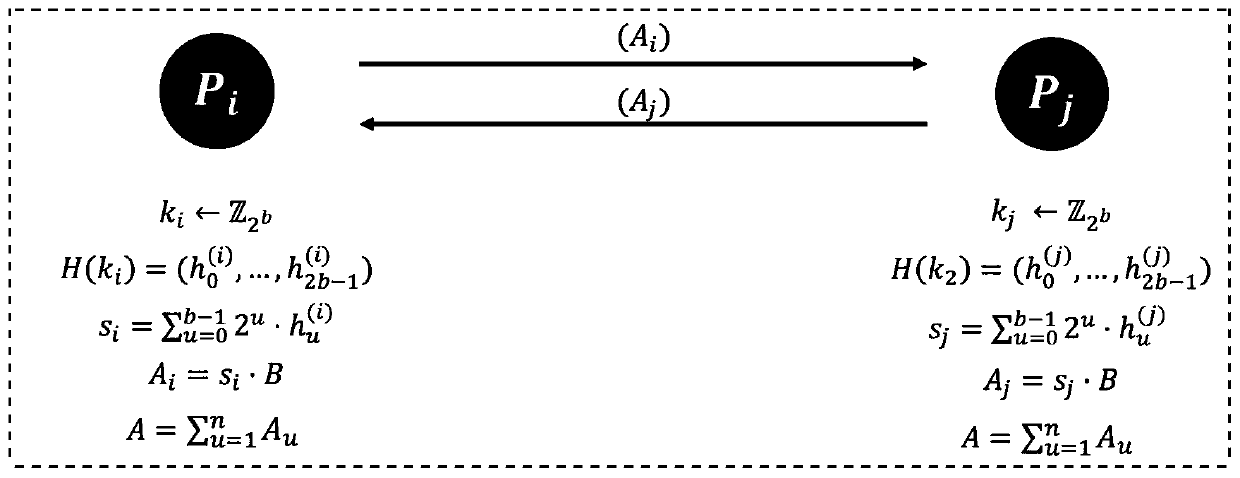
[0045] The EdDSA key generation algorithm is jointly participated by multiple parties, In order to calculate the partial signature private key, each participant performs the following operation steps (order denote each party that performs the following steps, let Expressed with P i other parties involved in the interaction):
[0046] a. Generate the first b-bit random number k i As part of the private key, for k i Perform a hash operation to get the first hash value Computes the first public key scalar And thus calculate the first part of the public key A i =[s i ] B. Last P i send a i To all other parties P j .
[0047] b. When receiving A from all other participants j , P i Computing the collaborative public key
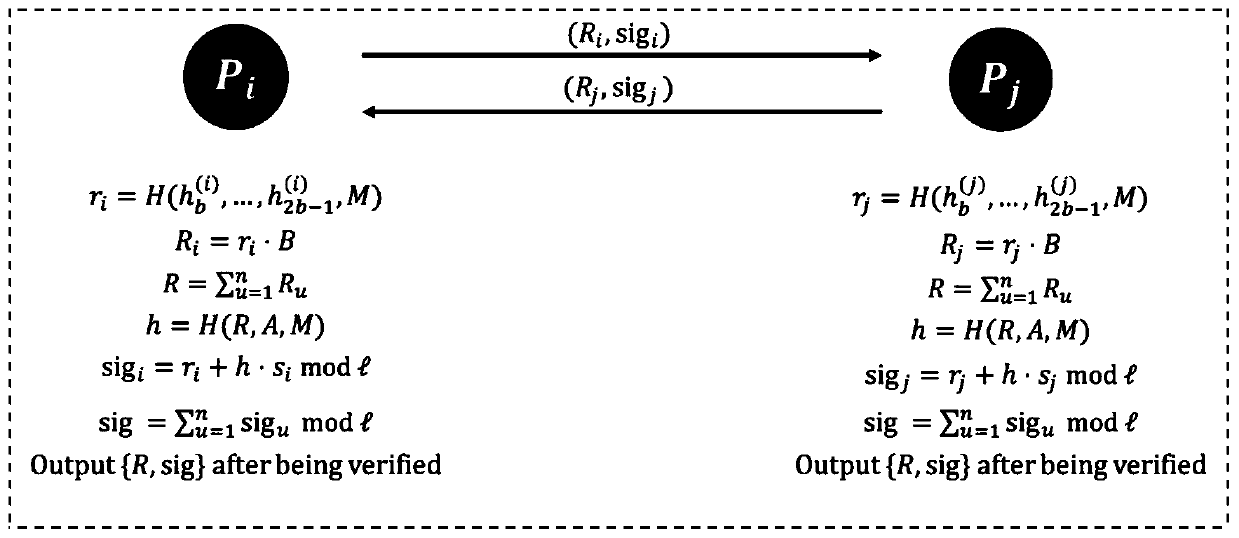
[0048] 2. Collaborative signature algorithm
[0049] participant collection At this stage, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com