Authentication method and system using portable terminal
A technology of an authentication system and an authentication method, which is applied in the field of authentication and system using portable terminal devices, can solve the problems of weak security, leakage of user information, fragile malicious code, etc., and achieves the effect of improving convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Hereinafter, it demonstrates in detail with reference to drawings.
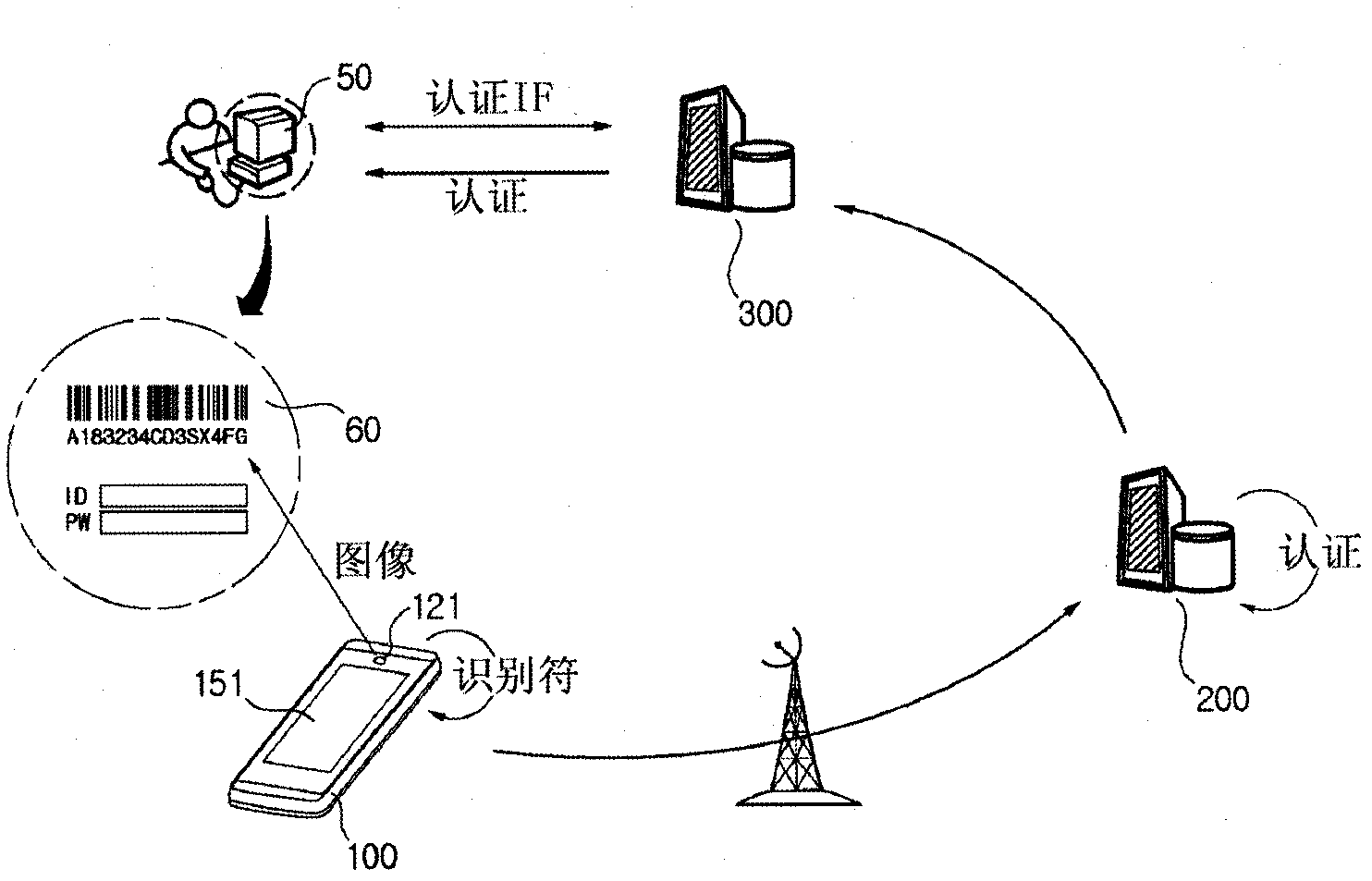
[0025] figure 1 A schematic diagram is shown for explaining the authentication system and the authentication method using the authentication system of the present invention.
[0026] in the description figure 1 Previously, the designation "50" indicated "user terminals" such as personal computers and notebook computers,
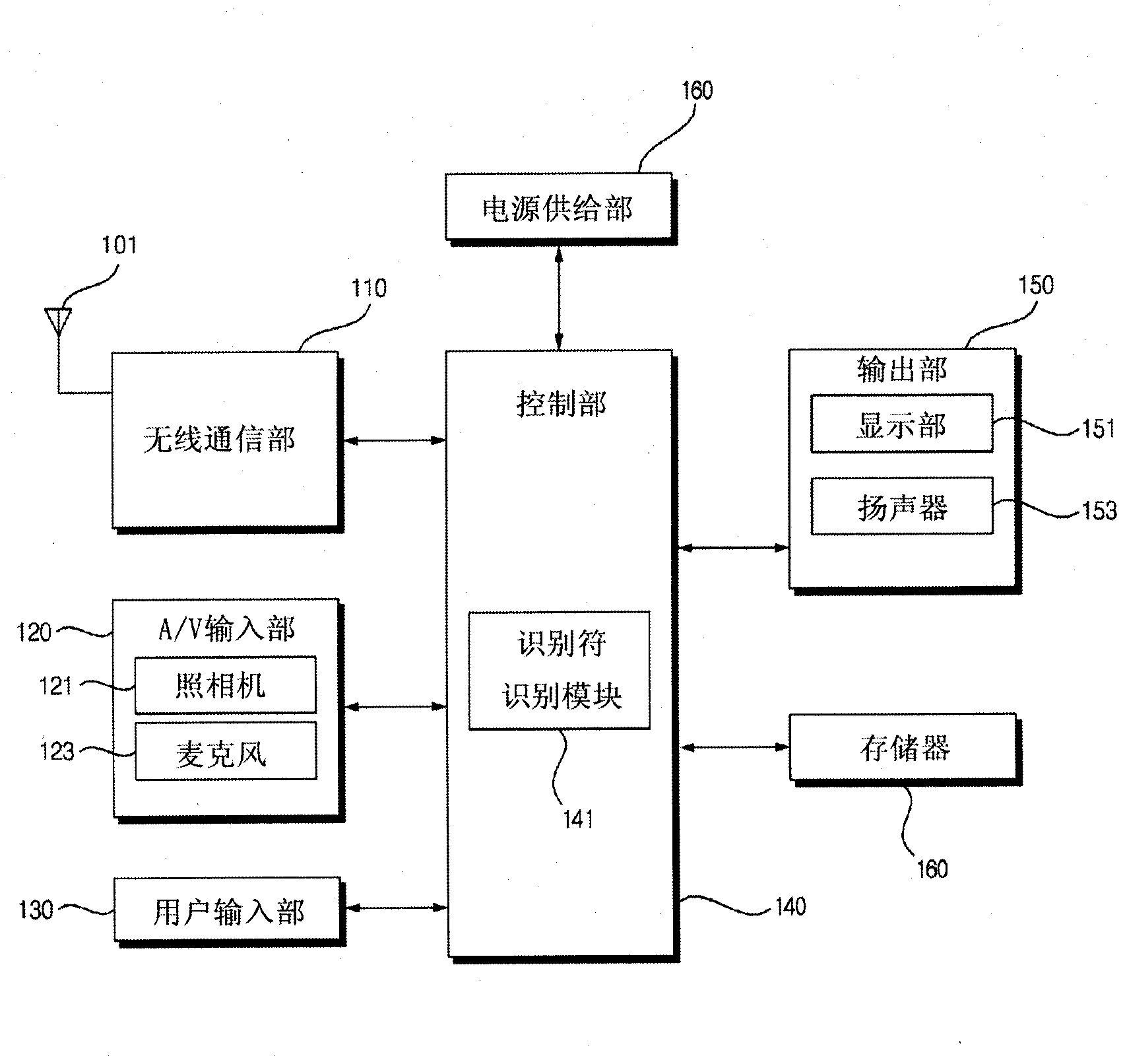
[0027] Reference numeral "100" denotes "portable terminal devices" such as mobile phones, smart phones, and PDAs,
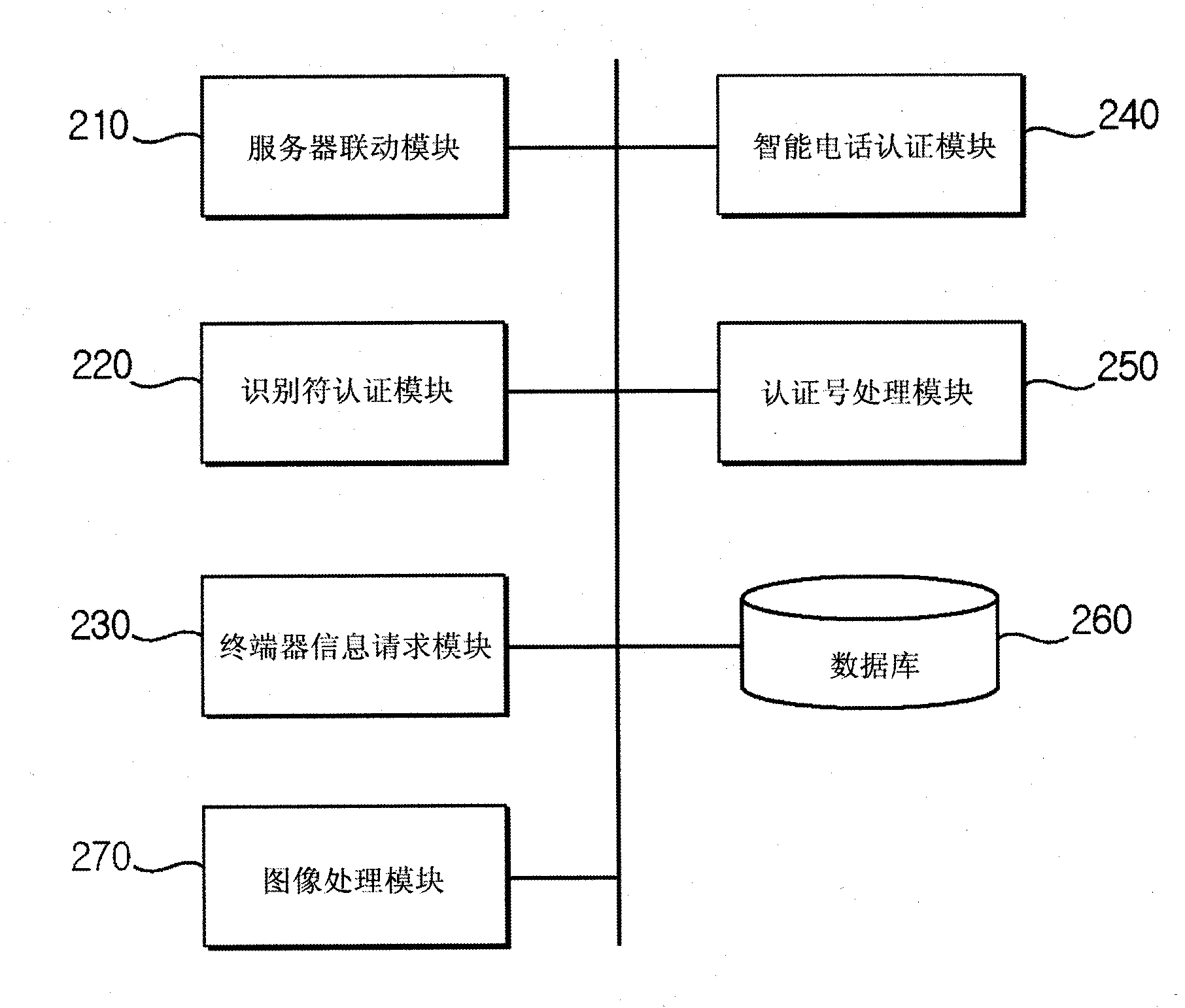
[0028] Reference numeral "200" represents the authentication system of the present invention,
[0029] Reference numeral "300" denotes a server that provides various services to users such as a portal site, a general site (web site), a blog, a site of a public institution, and a site of a financial institution such as a bank. In addition, the server may be various forms of sites that provide information to users, may be a personal homepage, and other various sites th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com