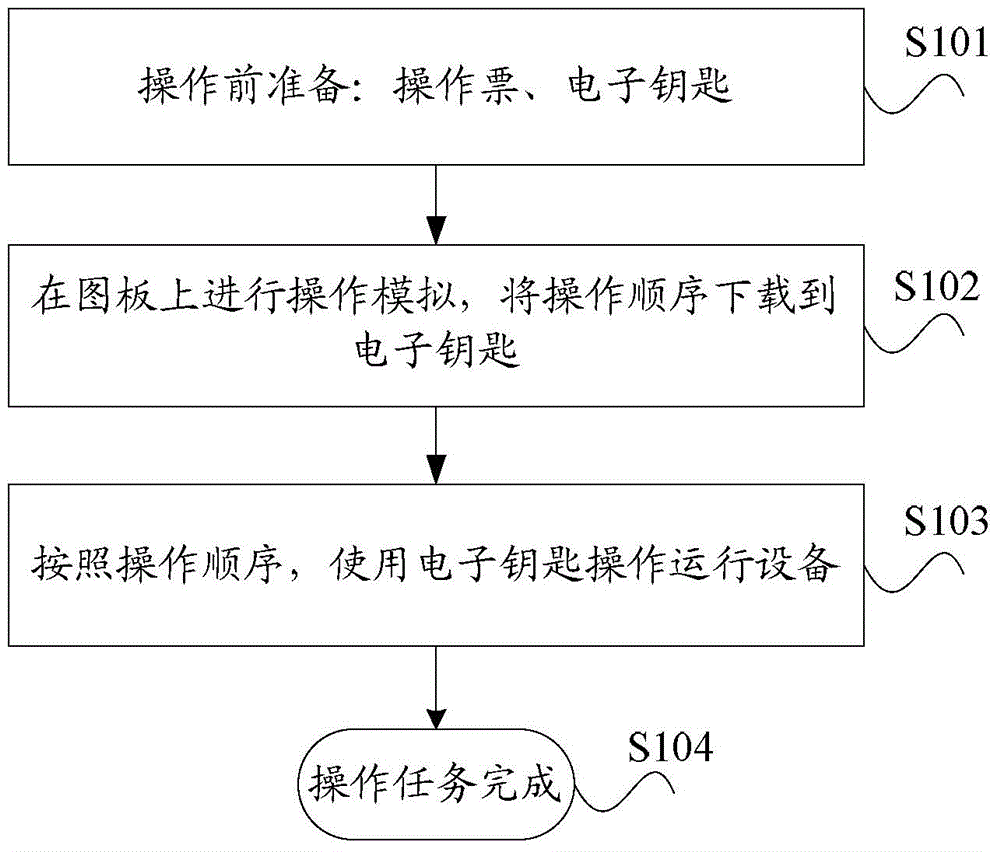
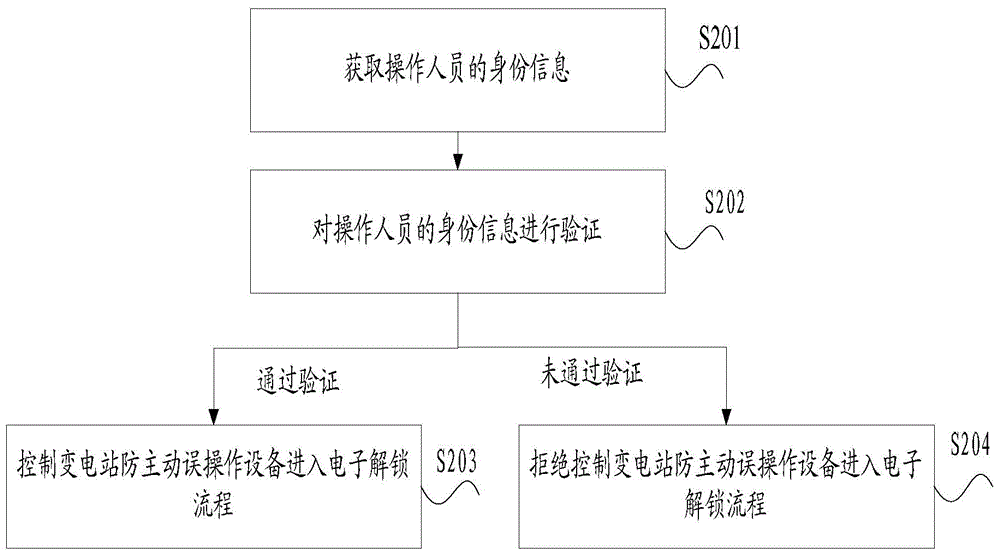
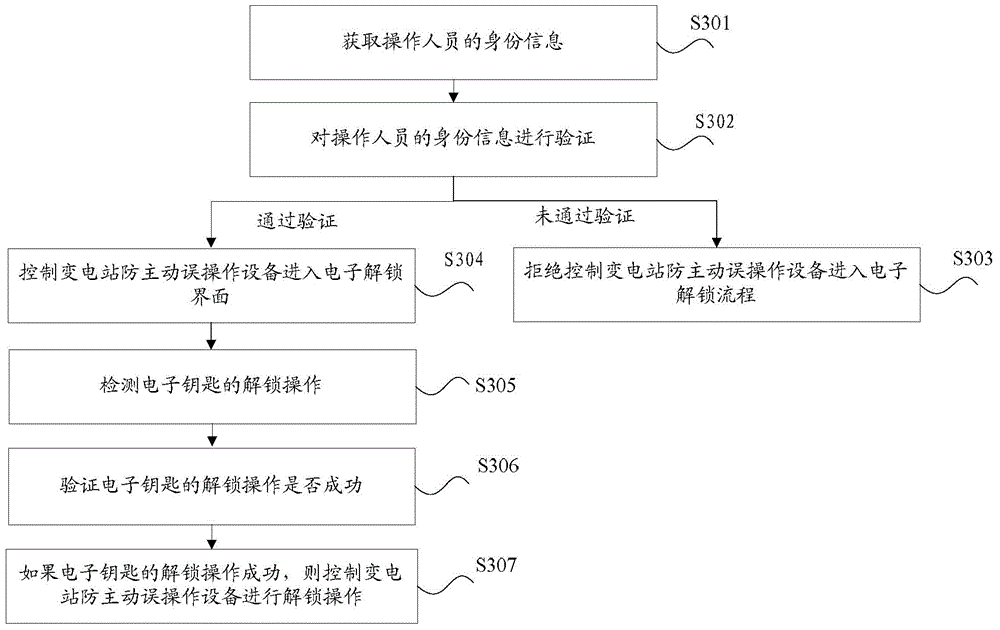
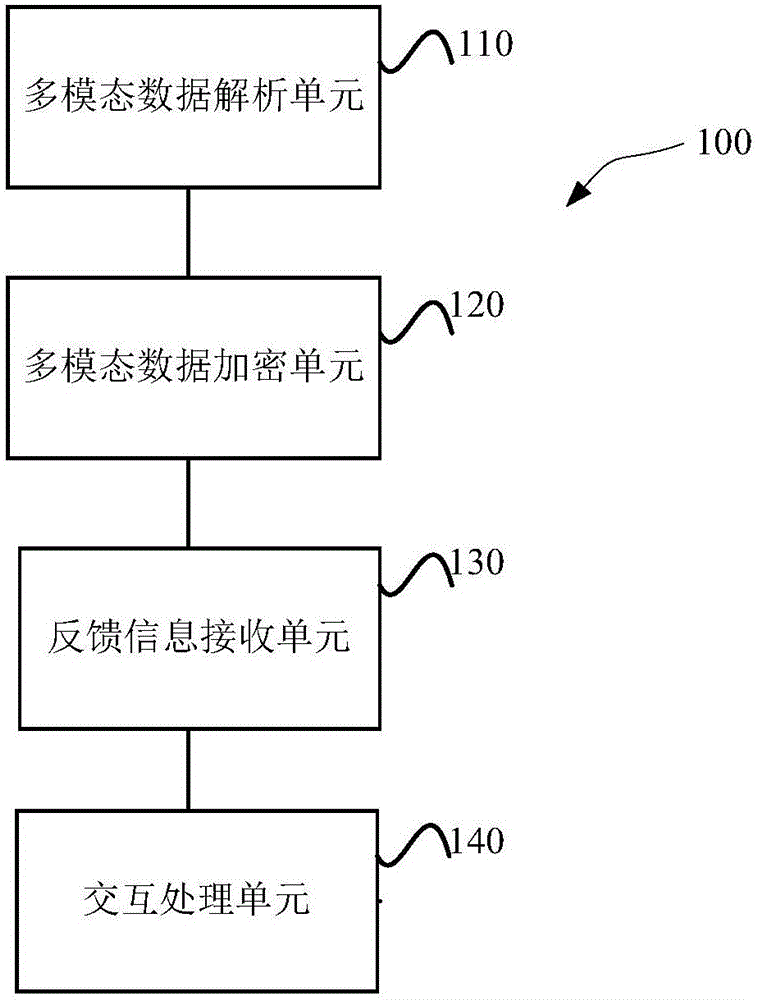
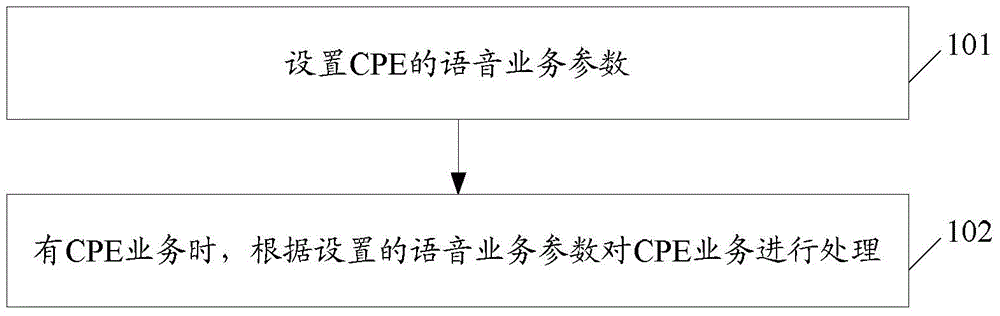
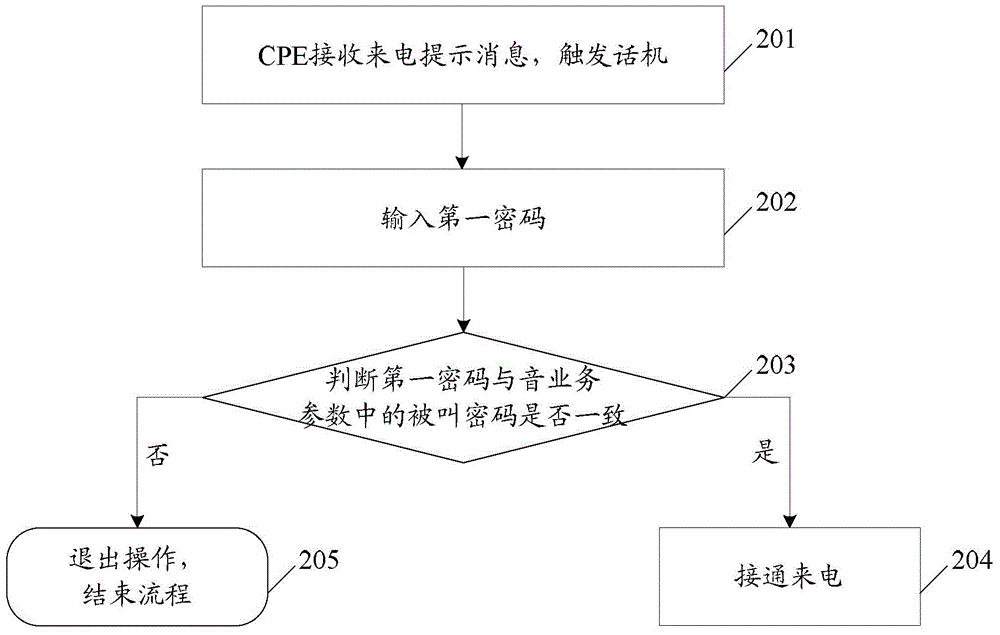
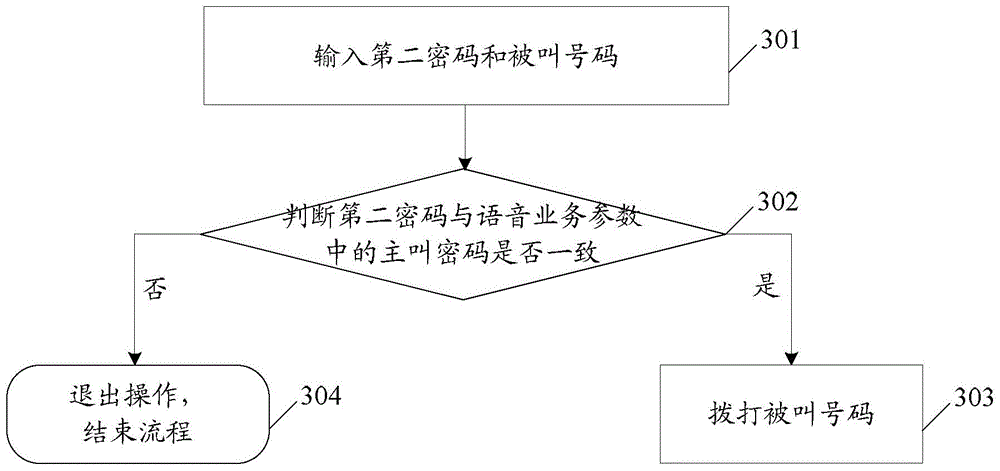
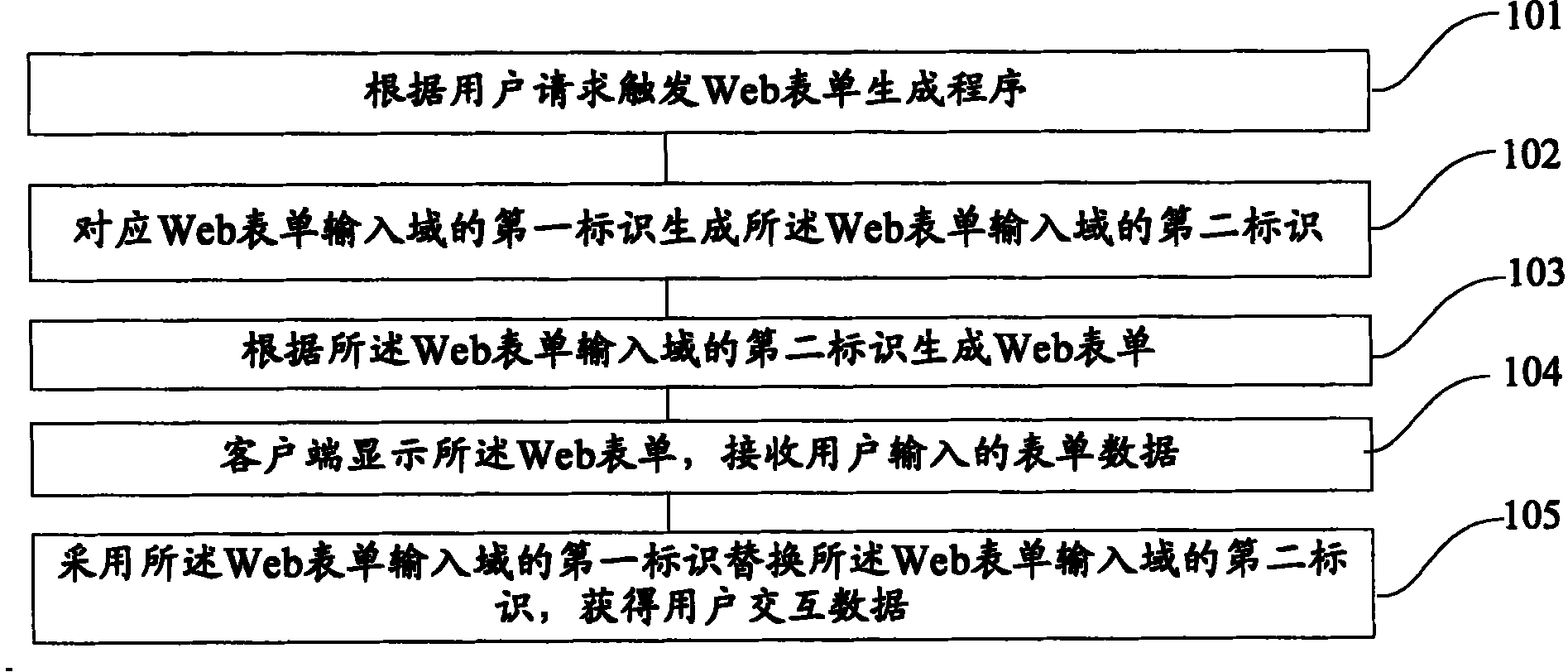
Patents
Literature
76results about How to "Avoid Malicious Operations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
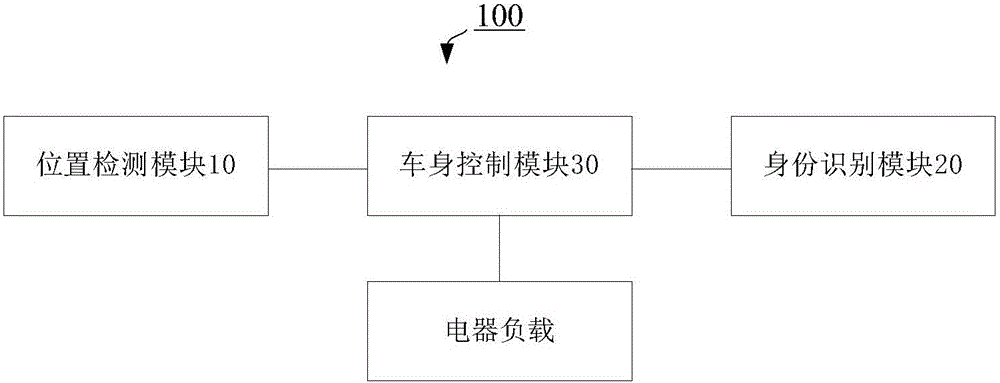
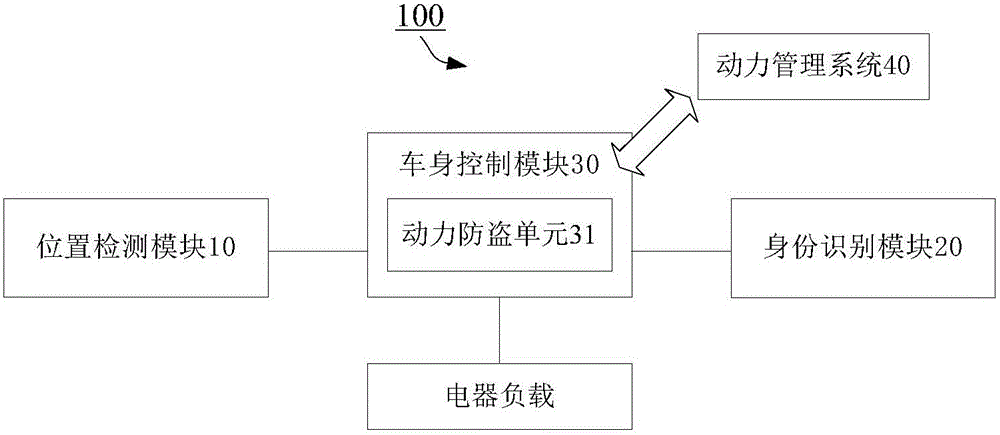
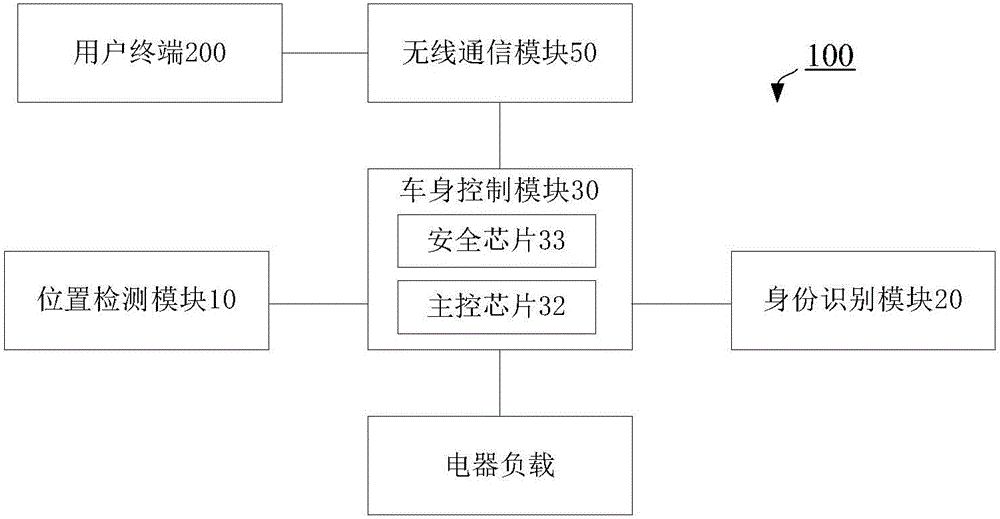
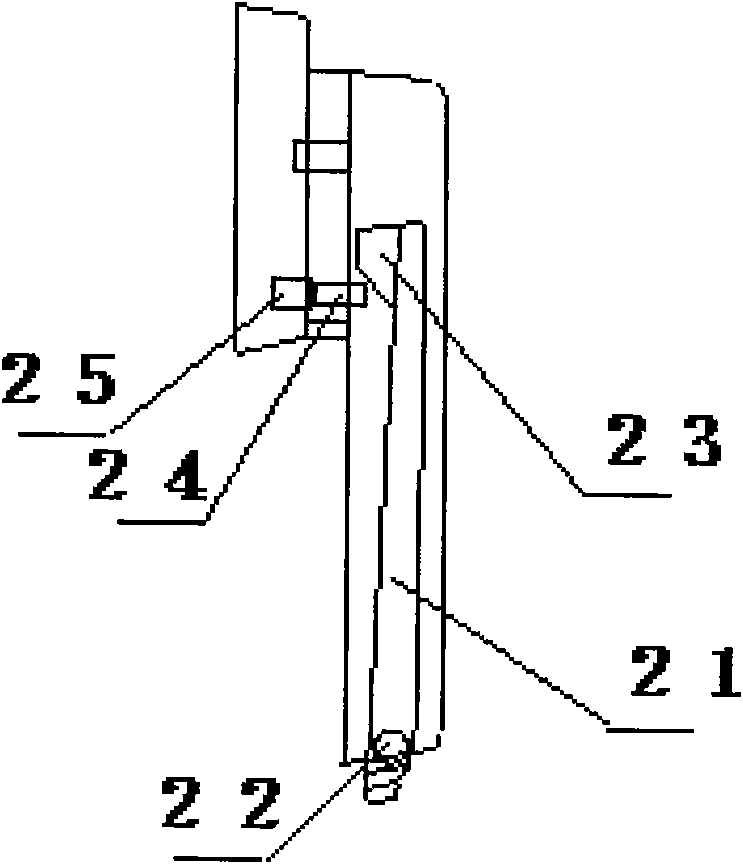
Vehicle body control device and control method thereof, a vehicle body control system and vehicle
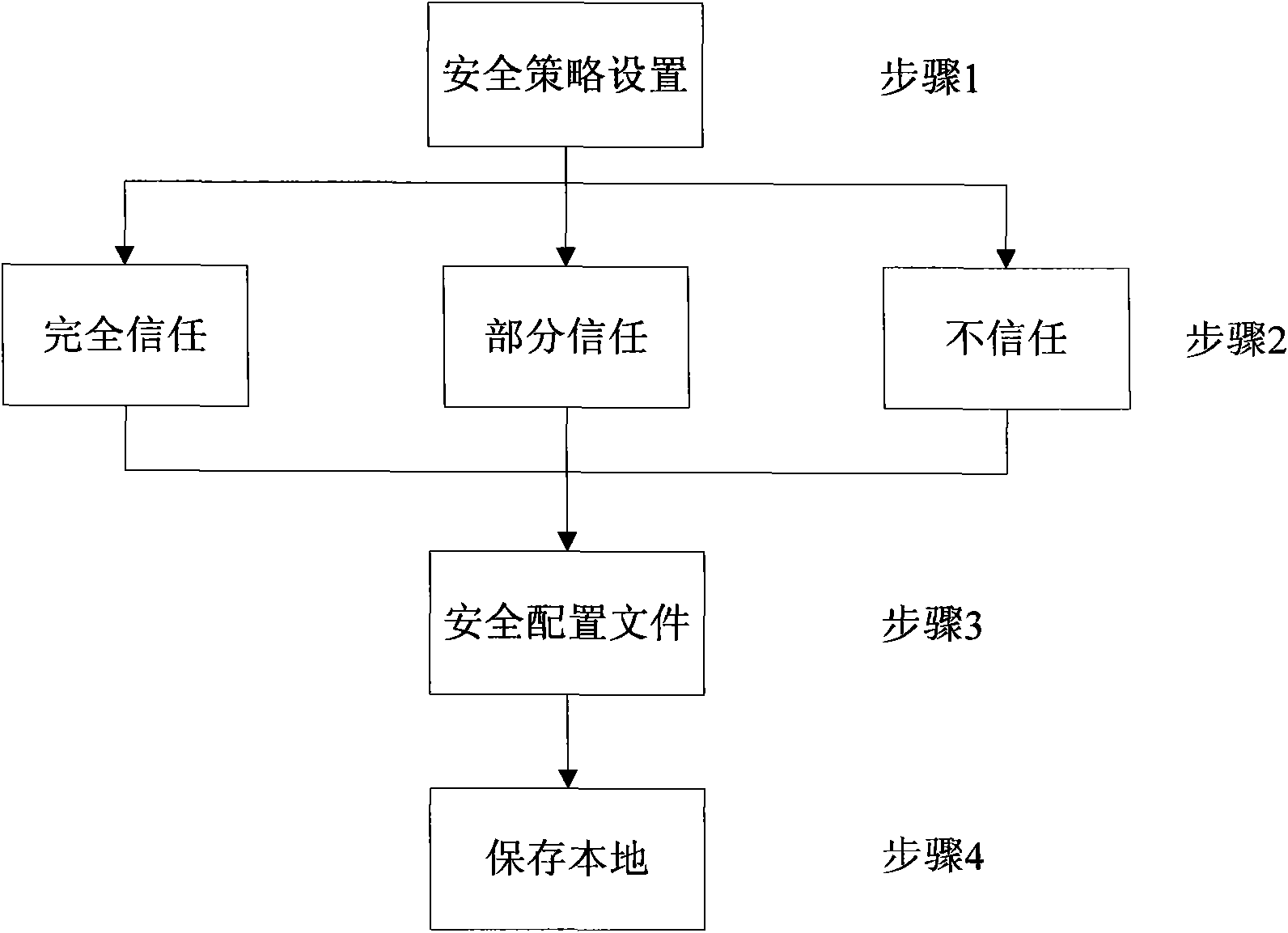
InactiveCN105774709AMeet individual needsImprove ride comfortElectric/fluid circuitControl systemElectrical load
The invention discloses a vehicle body control device, comprising a position detection module, an identification module and a vehicle body control module, wherein the position detection module is used for detecting seat positional information of each passenger in a vehicle; the identification module is used for acquiring identification information of the passenger at each seat position; the vehicle body control module matches the identification module and the positional information, acquires vehicle usage habit information of each passenger according to the identification information of each passenger, and controls electrical load of the vehicle respectively according to the vehicle usage habit information of each passenger and the corresponding positional information. The vehicle body control device can provide personal services for each passenger in the vehicle, meeting the requirement of each passenger for riding comfort. The invention also discloses a vehicle body control system and a vehicle, as well as a control method of the vehicle body control device.
Owner:BEIJING ELECTRIC VEHICLE
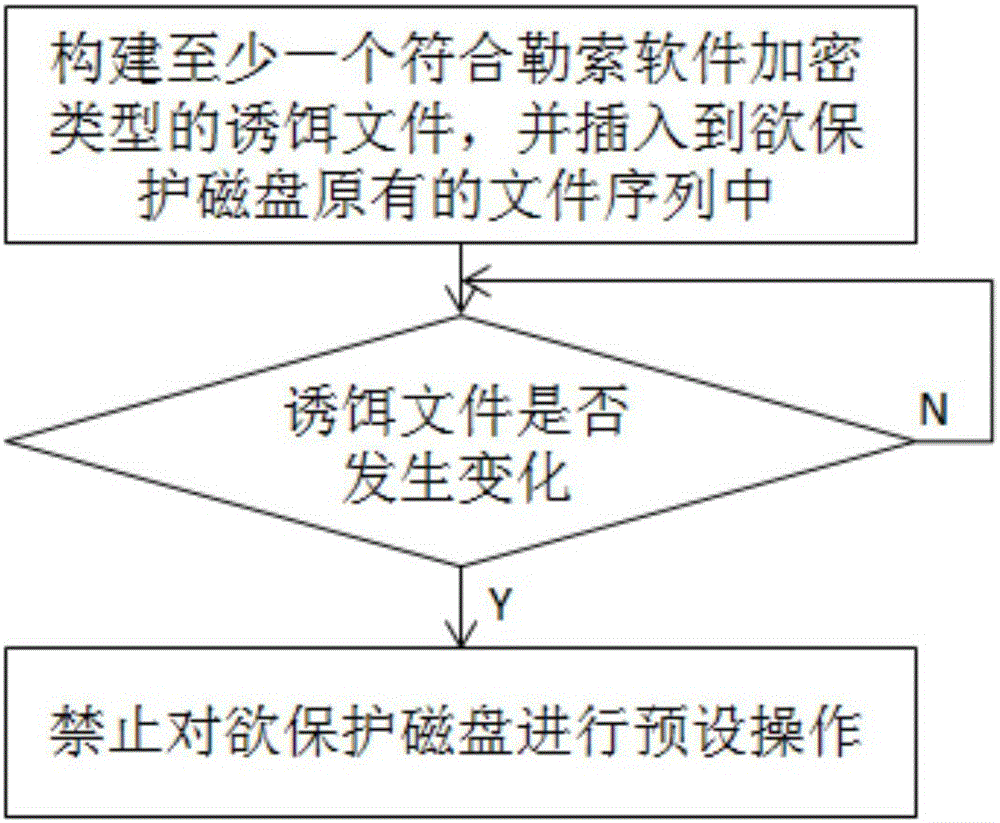
Ransomware prevention method and system
ActiveCN106096397AImprove the accuracy of early warningAvoid Malicious OperationsPlatform integrity maintainanceDecoyRansomware
The invention relates to a ransomware prevention method and system. The method comprises the steps of creating at least one bait file with the type conforming to a ransomware encryption type and inserting the bait file into an original file sequence of a to-be-protected disk; judging whether the bait file is changed or not; and prohibiting the to-be-protected disk to be subjected to a preset operation when the bait file is changed. According to the method and the system, the bait file with the type conforming to the ransomware encryption type is created by utilizing a characteristic that ransomware traverses disk files necessarily to search for a file type suitable for encryption, and the bait file is put in the original file sequence of the to-be-protected disk; the effects of prewarning the ransomware and protecting other disk files are achieved by monitoring the bait file; the prewarning accuracy is high; a targeted scheme is designed based on an inevitable common behavior of the ransomware, so that known and unknown ransomware can be detected; and the disk space occupied by the created bait file nearly can be ignored.
Owner:倪茂志
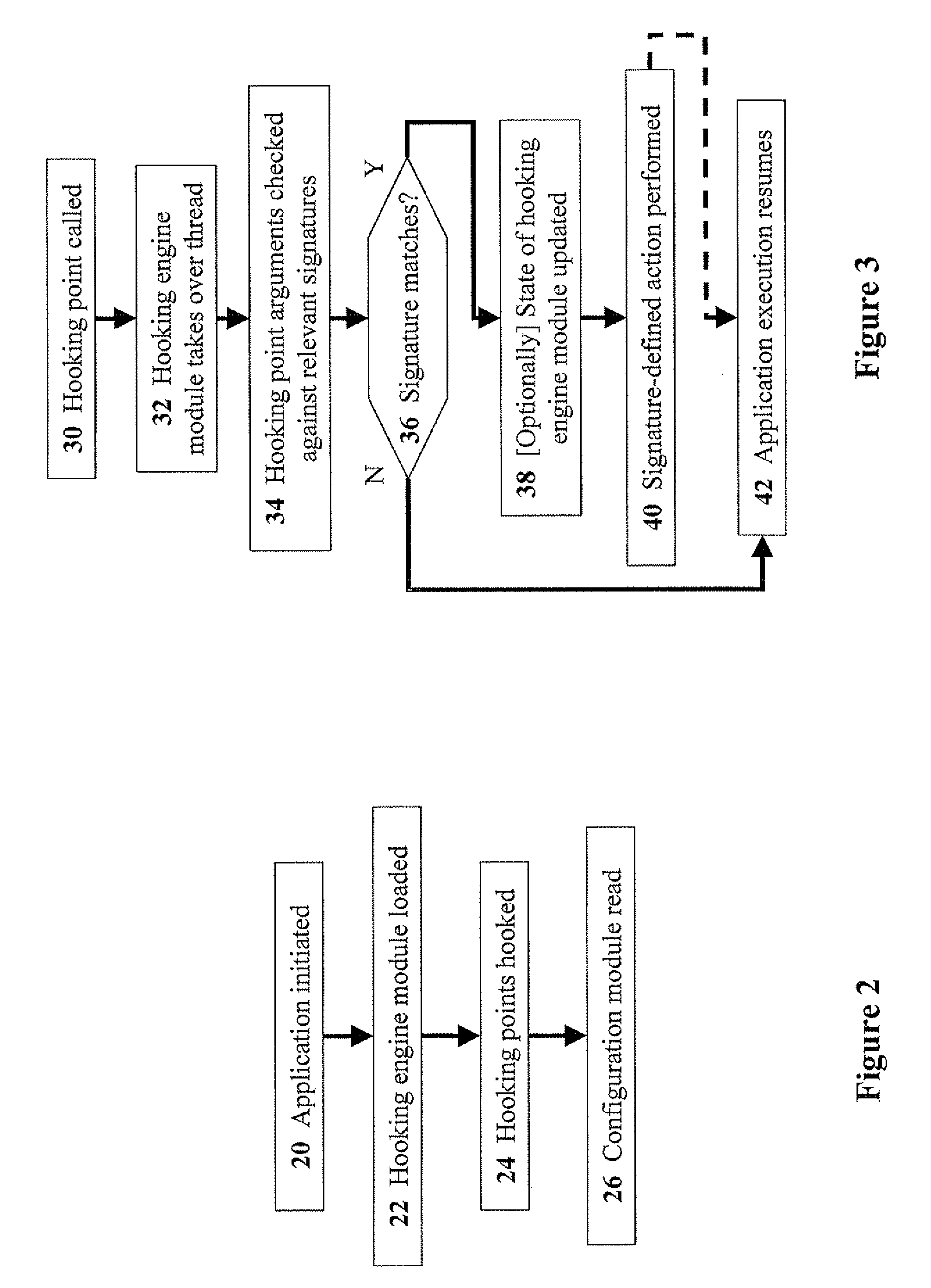
Methods for hooking applications to monitor and prevent execution of security-sensitive operations
ActiveUS20100005528A1Avoid Malicious OperationsMemory loss protectionError detection/correctionApplication softwareOperating system
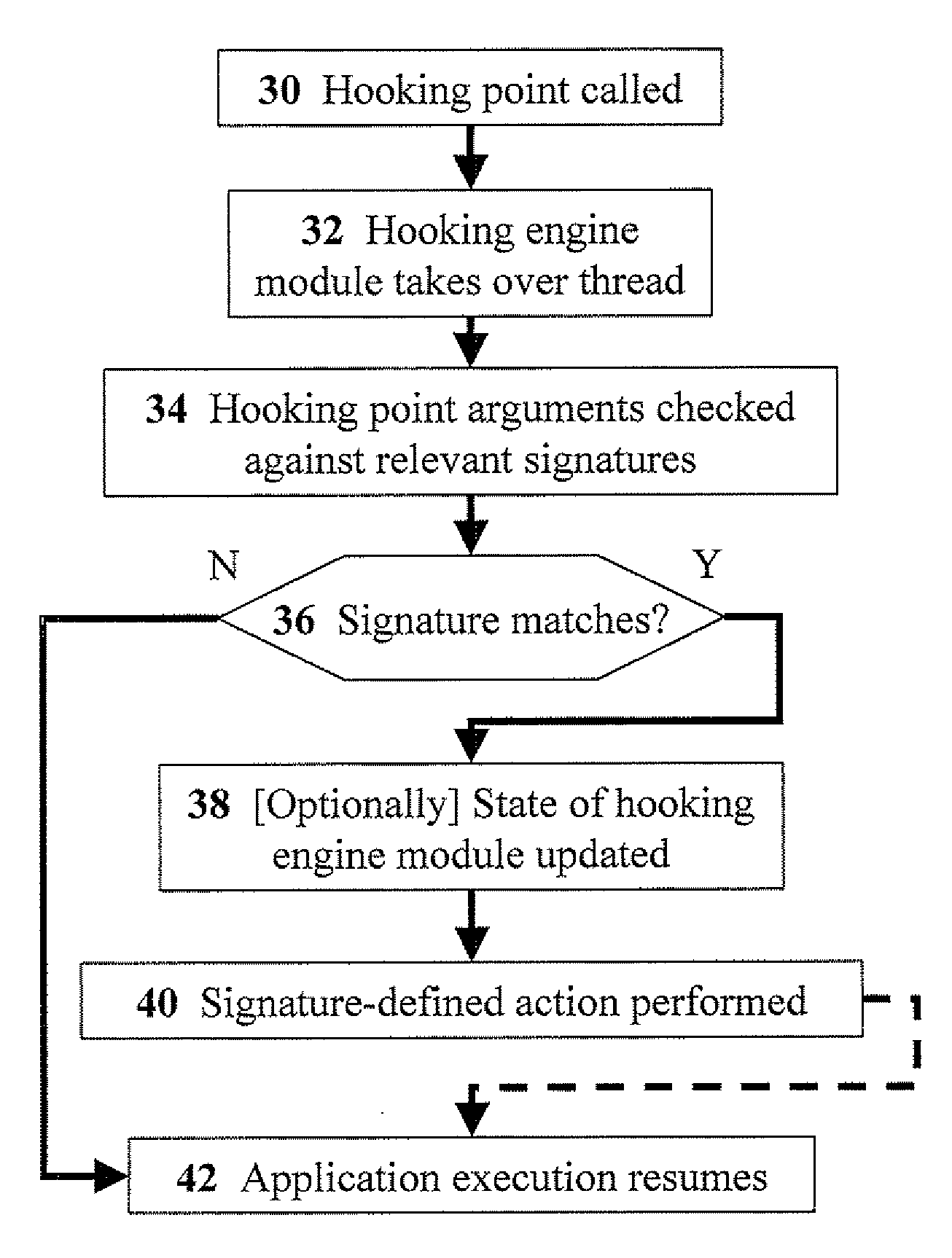
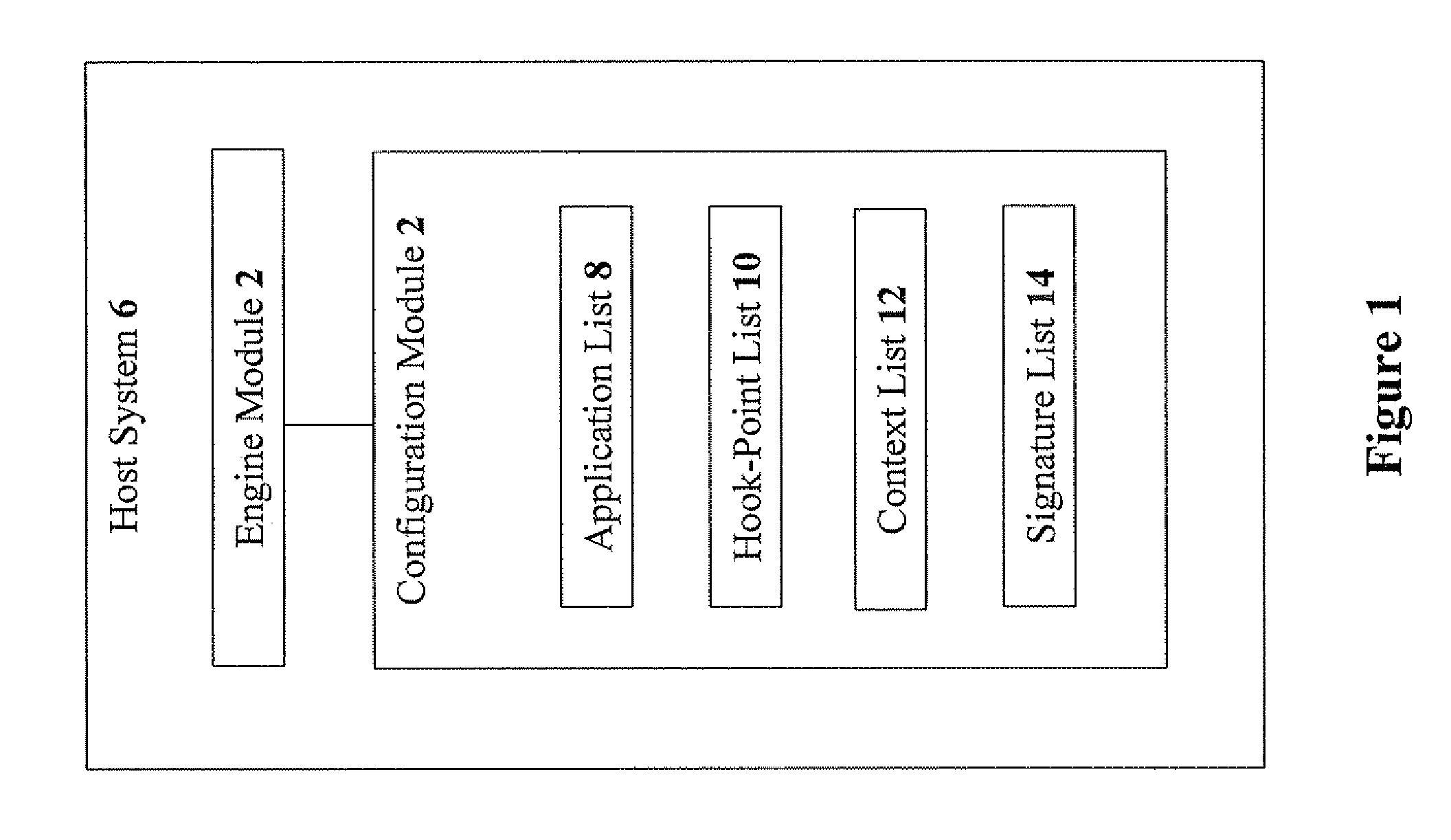
The present invention discloses methods and media for hooking applications to monitor and prevent execution of security-sensitive operations, the method including the steps of: reading at least one configuration parameter list from a configuration module; hooking, by a hooking engine, a hooking point in an application, wherein the hooking point is defined in the configuration module; calling, by the application, the hooking point during operation of the application; matching at least one hooking parameter in the hooking point to at least one configuration parameter in at least one configuration parameter list; and upon detecting a match between the hooking parameter and at least one configuration parameter, performing at least one configuration-defined action. Preferably, the method further includes the step of: updating a state of the hooking engine. Preferably, the hooking engine is operative to prevent malicious operations by obfuscated code.
Owner:CHECK POINT SOFTWARE TECH LTD
User behavior clustering analysis method and terminal, and computer readable storage medium
InactiveCN107426177AImprove performanceAvoid Malicious OperationsCharacter and pattern recognitionPlatform integrity maintainanceComputer terminalAnalysis method
The invention provides a user behavior clustering analysis method and terminal, and a computer readable storage medium. The method includes: obtaining user data operated by all users on a website, extracting effective user behavior operations from the user data to form a characteristic item set, converting the characteristic item set of all the users to vector space model data, performing clustering operation on characteristic items in the vector space model data according to a clustering analysis algorithm, obtaining clustering analysis results, and determining the legality of each user behavior operation according to the clustering analysis results. According to the user behavior clustering analysis method and terminal, and the computer readable storage medium, the legality of the user behaviors operated by the users on the website is analyzed according to the clustering analysis algorithm, whether the user behaviors are legal is determined according to the analysis results, classified display of illegal user behaviors and the corresponding users is realized, the performance of the website is enhanced, interception processing of malicious operations of a certain kind of users is performed, and malicious operations of the website by the users can be solved from the operation source.
Owner:NUBIA TECHNOLOGY CO LTD
Realizing method of synchronous management of DAS (Distributed Antenna System) WEB (World Wide Web) account information of multiple systems
ActiveCN108667809ARealize unified managementRealize unified synchronization managementDiversity/multi-antenna systemsDistributed antenna systemUnit system
The invention provides a realizing method of synchronous management of DAS (Distributed Antenna System) WEB (World Wide Web) interface account information of multiple systems. The method comprises security verification initialization of WEB interfaces during starting of single system equipment in DASs of the multiple systems, synchronization of current inter-system user information of the WEB interfaces in the DASs of the multiple systems and synchronization of key books of inter-system WEB account information in the DASs of the multiple systems. By the method, the synchronous management of DAS WEB interface account information of the multiple systems can be realized, the management mode is simplified, and the management efficiency is improved; the synchronization of the current WEB user information realizes integration and automatic login of WEB user states of the multiple systems, and tedious repeated processes are eliminated; the key books are automatically updated and synchronized,so that the multiple systems use the same account information key book, and a main unit system adds, deletes and alters the key book in a unified way; and therefore, the security, the unicity and thedefiniteness are improved to a certain extent, and overall consideration is realized.
Owner:SUNWAVE COMM
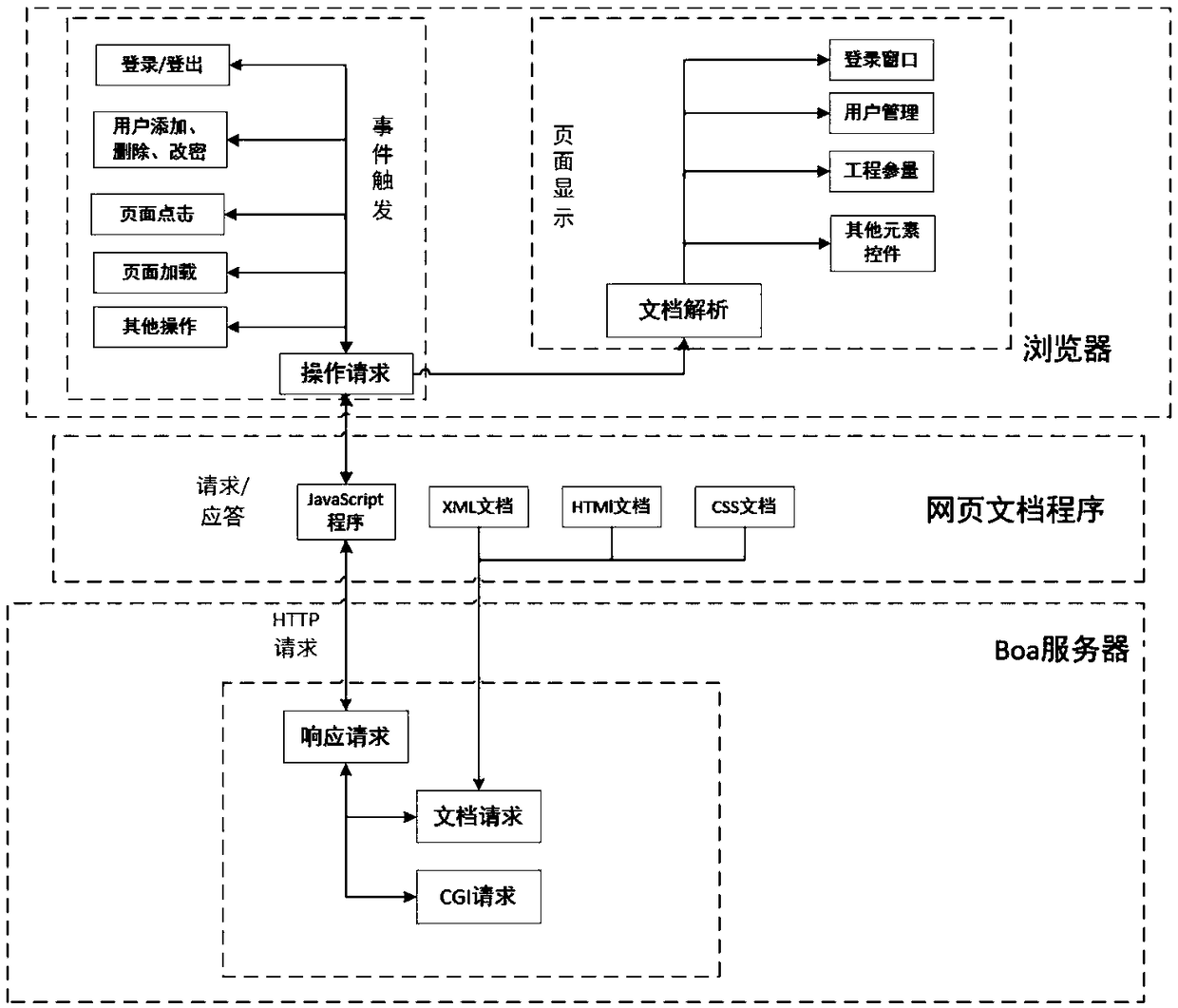
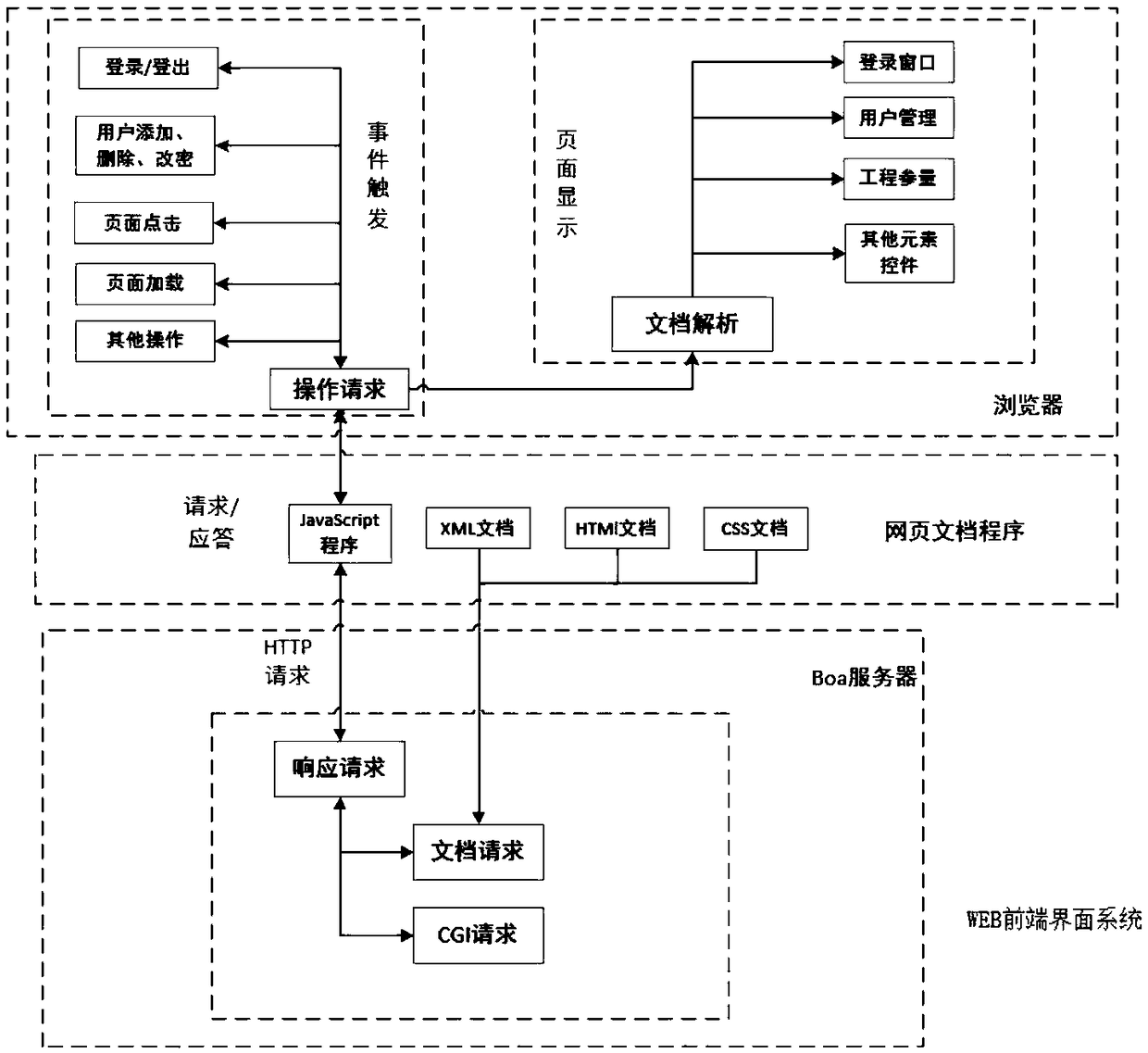
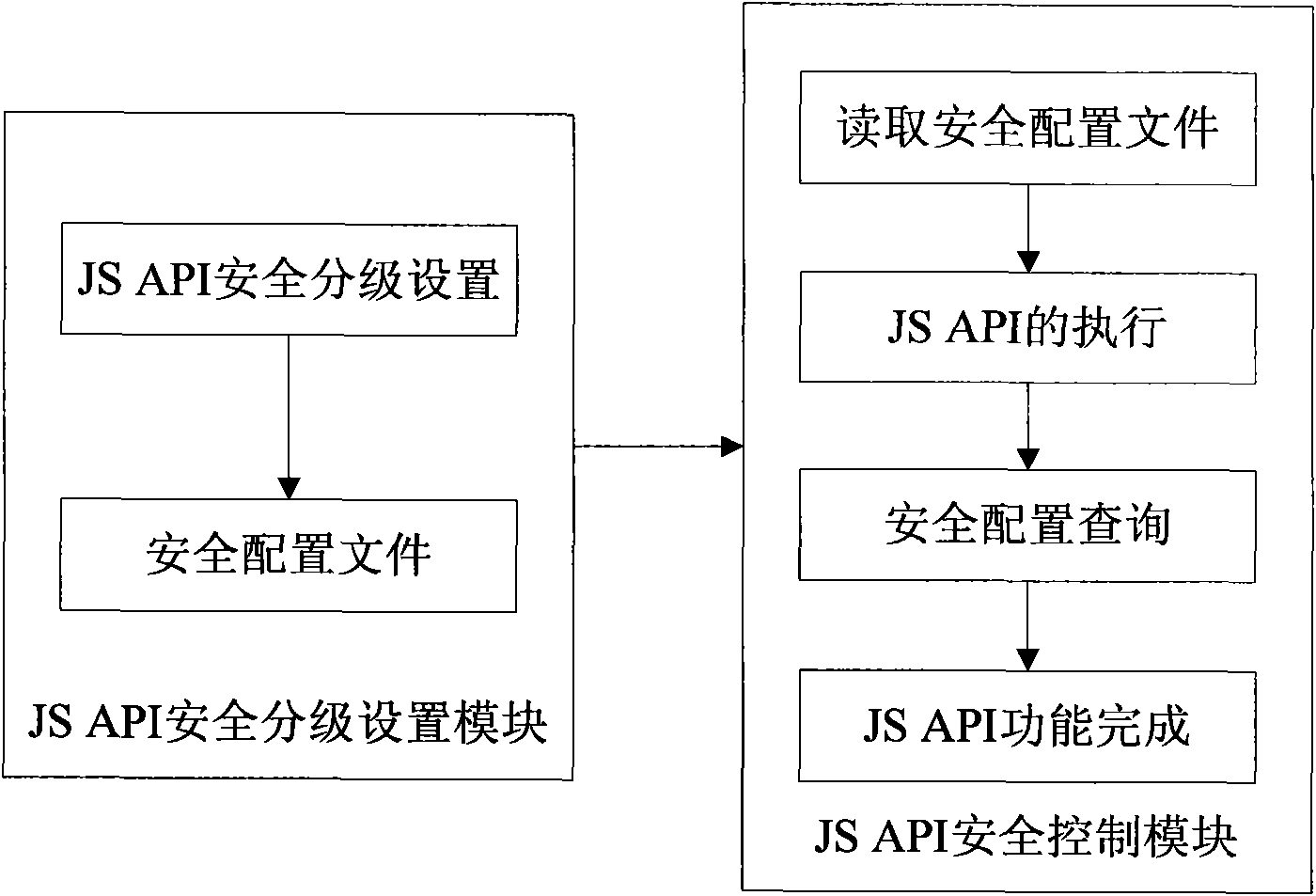
Security protection method and system for widget application
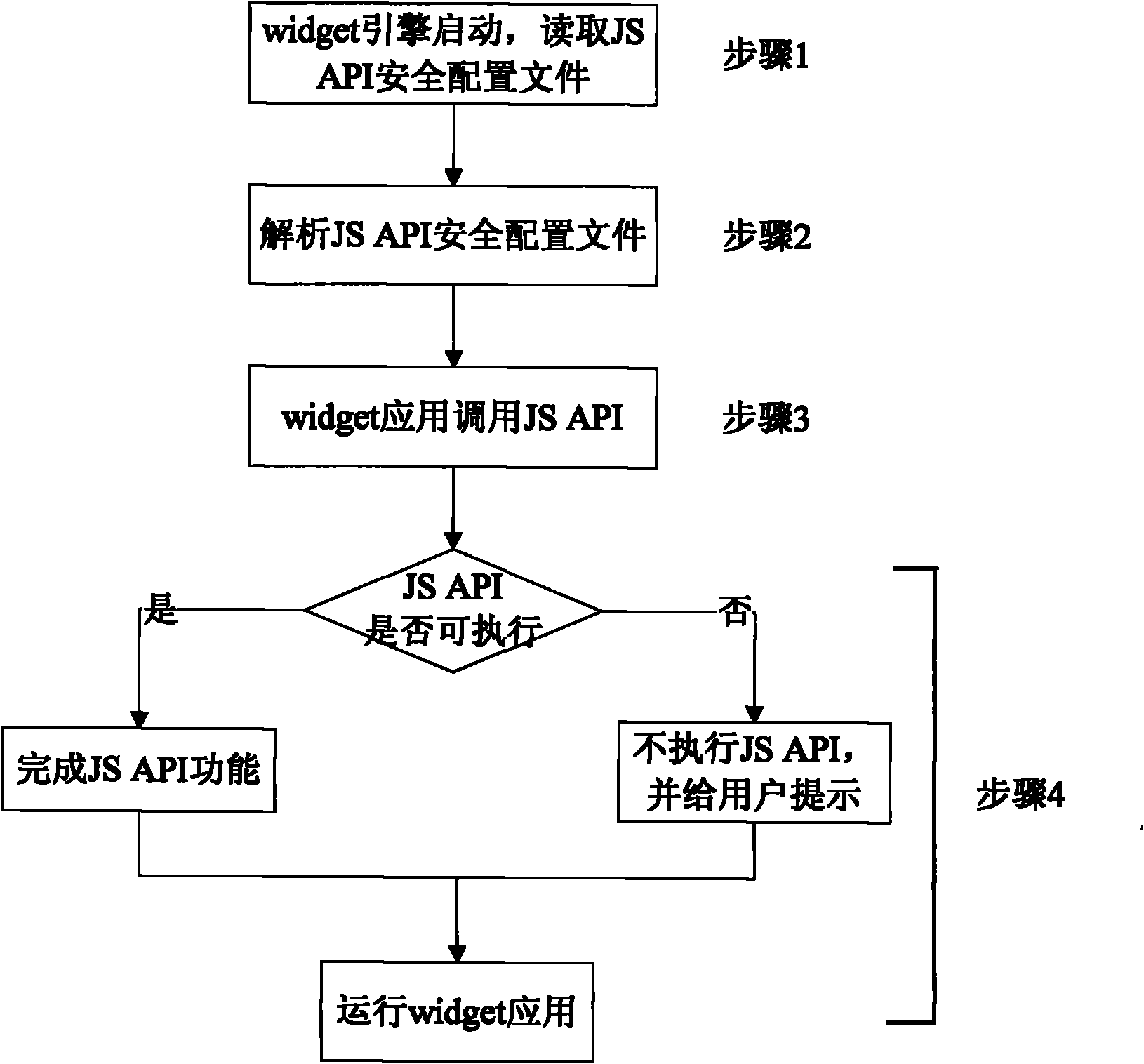
ActiveCN101977230AGuarantee information securityGuarantee data securityTransmissionApplication programming interfaceComputer terminal
The invention discloses a security protection method for widget application and a system, and guarantees the interface security of a user terminal, personal data security of a user and the network security. The method comprises the following steps: performing security level configuration for a JavaScript application programming interface (JS API), and storing the configuration result in a security configuration file; when a widget engine is started, reading the security configuration file; and when the widget application calls the local functions of the terminal through the JS API, controlling the JS API according to the configuration in the security configuration file.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
Verification method and verification device
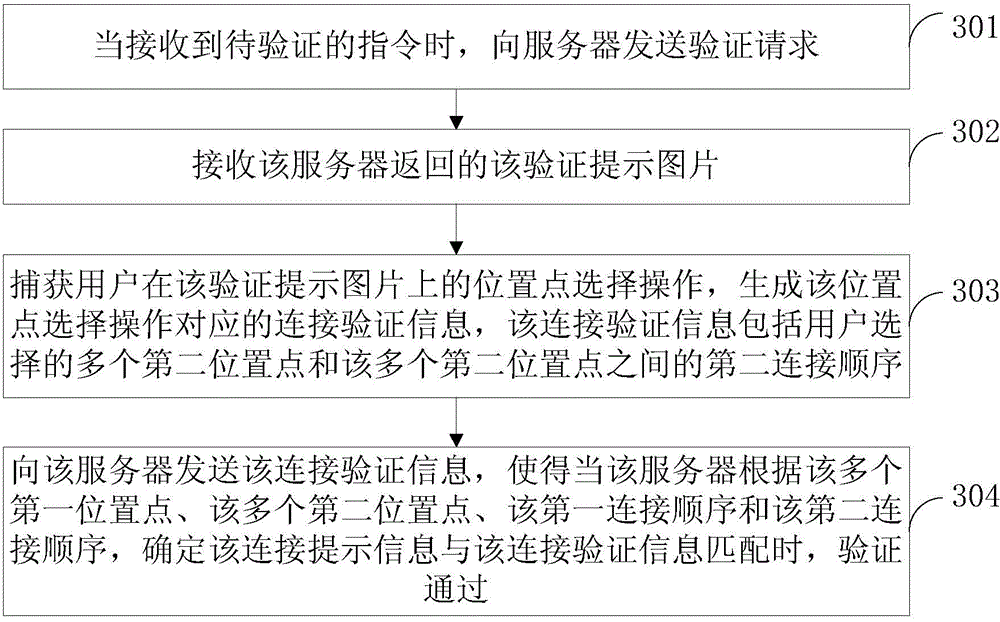
ActiveCN105245489AIncrease the difficulty of crackingAvoid Malicious OperationsDigital data authenticationTransmissionValidation methodsComputer terminal
The invention discloses a verification method and a verification device, and belongs to the technical field of network. The method comprises the steps as follows: generating a verification prompt picture when receiving a verification request sent by a terminal, wherein the verification prompt picture includes multiple first positions and connection prompt information, and the connection prompt information is used for indicating a user to connect the multiple first positions according to a first connection order; sending the verification prompt picture to the terminal to enable the terminal to capture a position selection operation by the user, generating connection verification information which includes multiple second positions selected by the user and a second connection order, and returning the connection verification information; receiving the connection verification information sent by the terminal; and passing verification when determining that the connection prompt information matches the connection verification information. According to the invention, the difficulty in cracking an automat is increased, the security is improved, malicious operation on an automat is avoided, and loss brought to other users is avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Industrial control security defense system
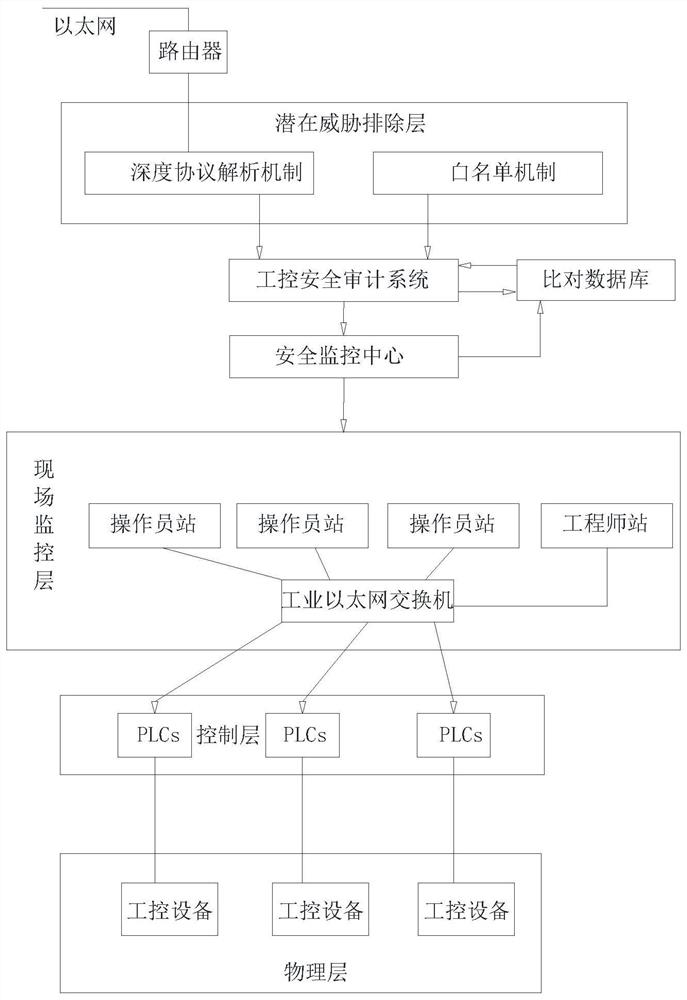
ActiveCN112799358AOccupies less than BillyImprove the protective effectTotal factory controlProgramme total factory controlBehavior controlControl layer
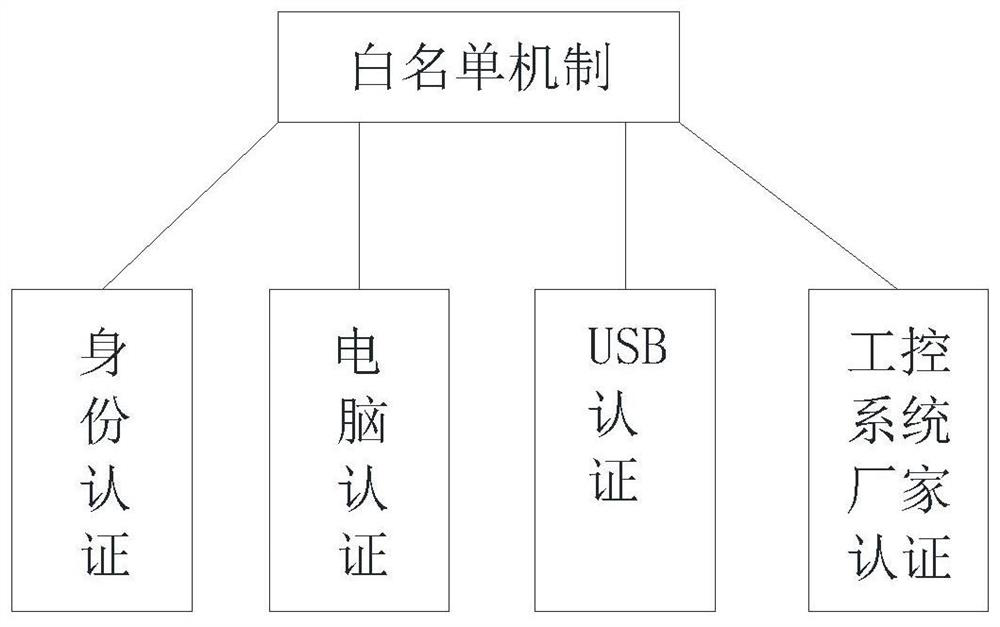
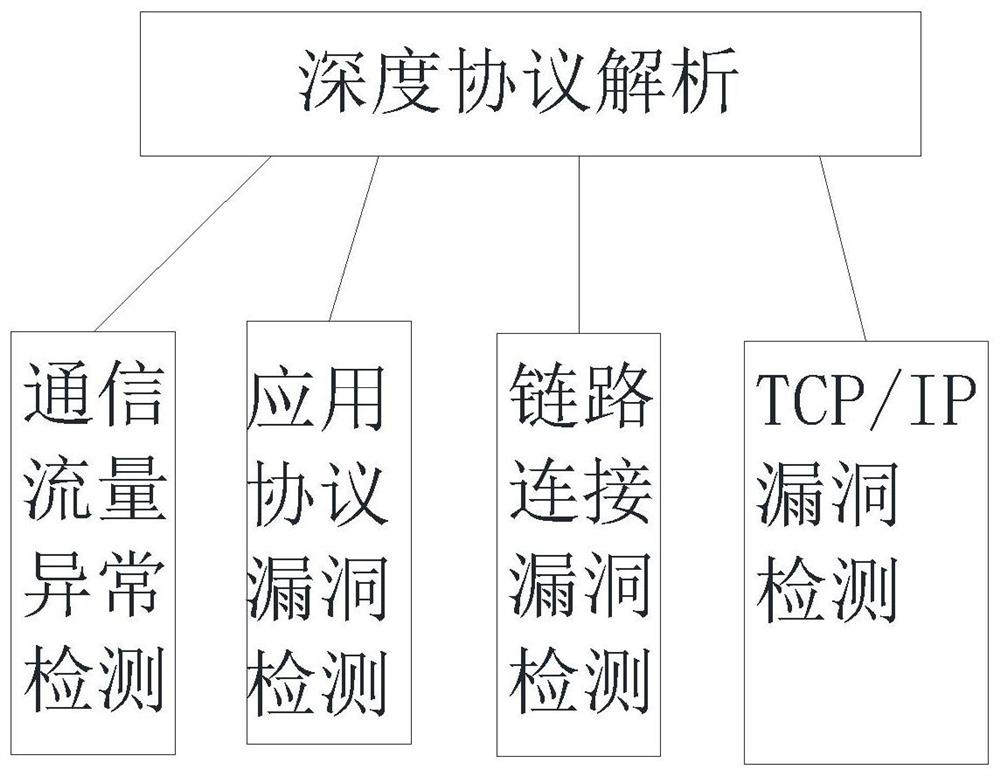
The invention discloses an industrial control security defense system which comprises a potential threat exclusion layer, an industrial control security audit system, a monitoring center, a field monitoring layer, a control layer and a physical layer. The potential threat elimination layer comprises a deep protocol analysis mechanism and a white list mechanism; the field monitoring layer performs data exchange and behavior control on the control layer and the physical layer through an industrial Ethernet; the industrial control security auditing system can analyze and identify illegal operation, abnormal events and external attacks in an industrial control network from multiple angles and give an alarm in real time; identity recognition is carried out through multiple means, system operation authority can be limited, override operation and malicious operation are avoided, it is avoided that external equipment carries viruses to affect system safety, meanwhile, exclusive detection can be carried out on common attack means, and the operation resource occupancy is small. The alarm response time of the whole system can be prolonged through unified monitoring management of the monitoring center, and the accident handling speed is increased.
Owner:上海磐御网络科技有限公司
Method of realizing elevator manual operating platform based on hand-held device
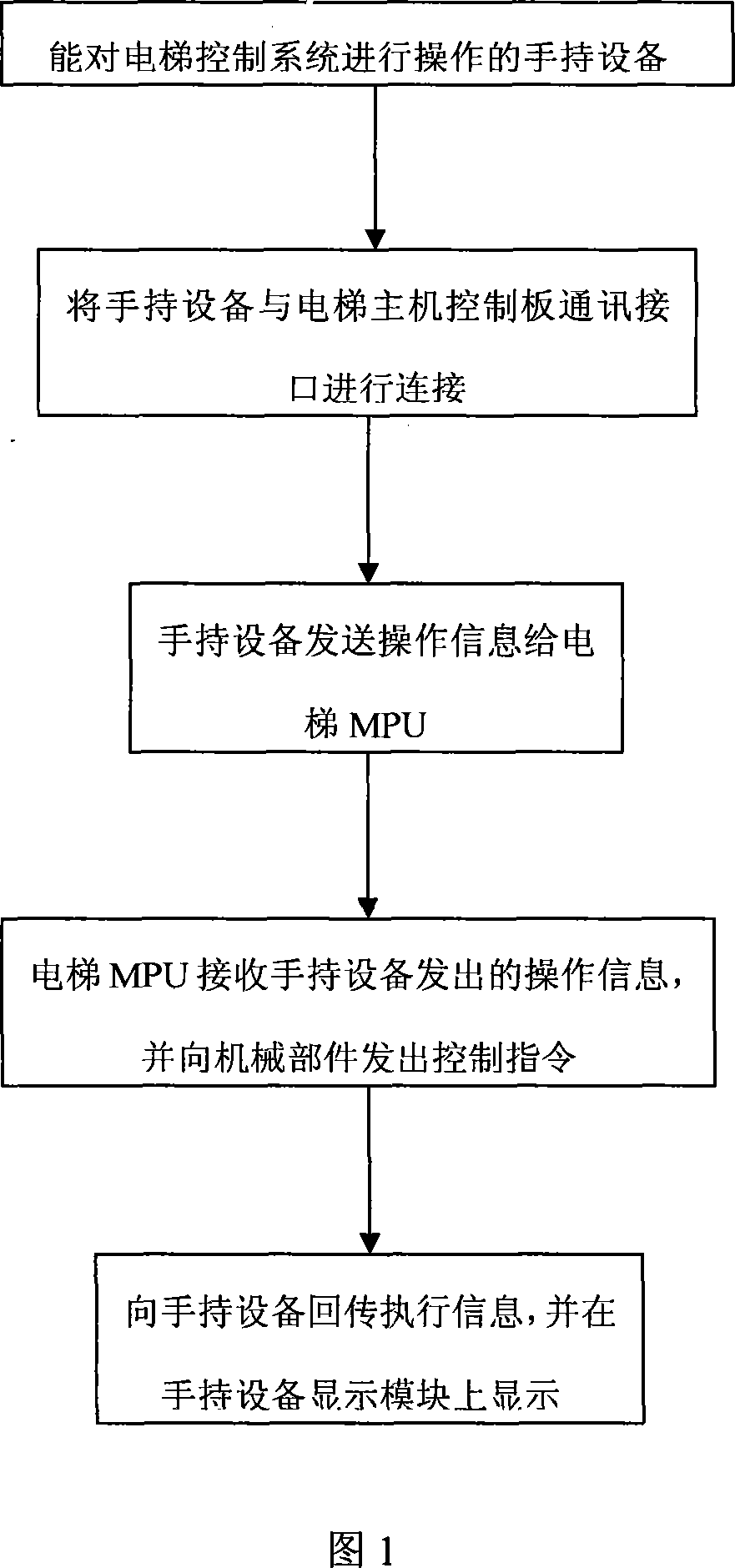
InactiveCN101033046AAvoid Malicious OperationsLow costElevatorsEmbedded systemCommunication interface
This invention provides a method for realizing elevator manual operation platform based on handheld equipment including the following steps: 1, setting a handheld device operating a control system of elevators, 2, connecting the communication interfaces of the handheld device and its master control board by communication cable, 3, the handheld device sends operation information to the elevator MPU, 4, the MPU receives the operation information sent by the handheld device and gives off instructions to mechanical parts.
Owner:YUNGTAY ELEVATOR EQUIP CHINA
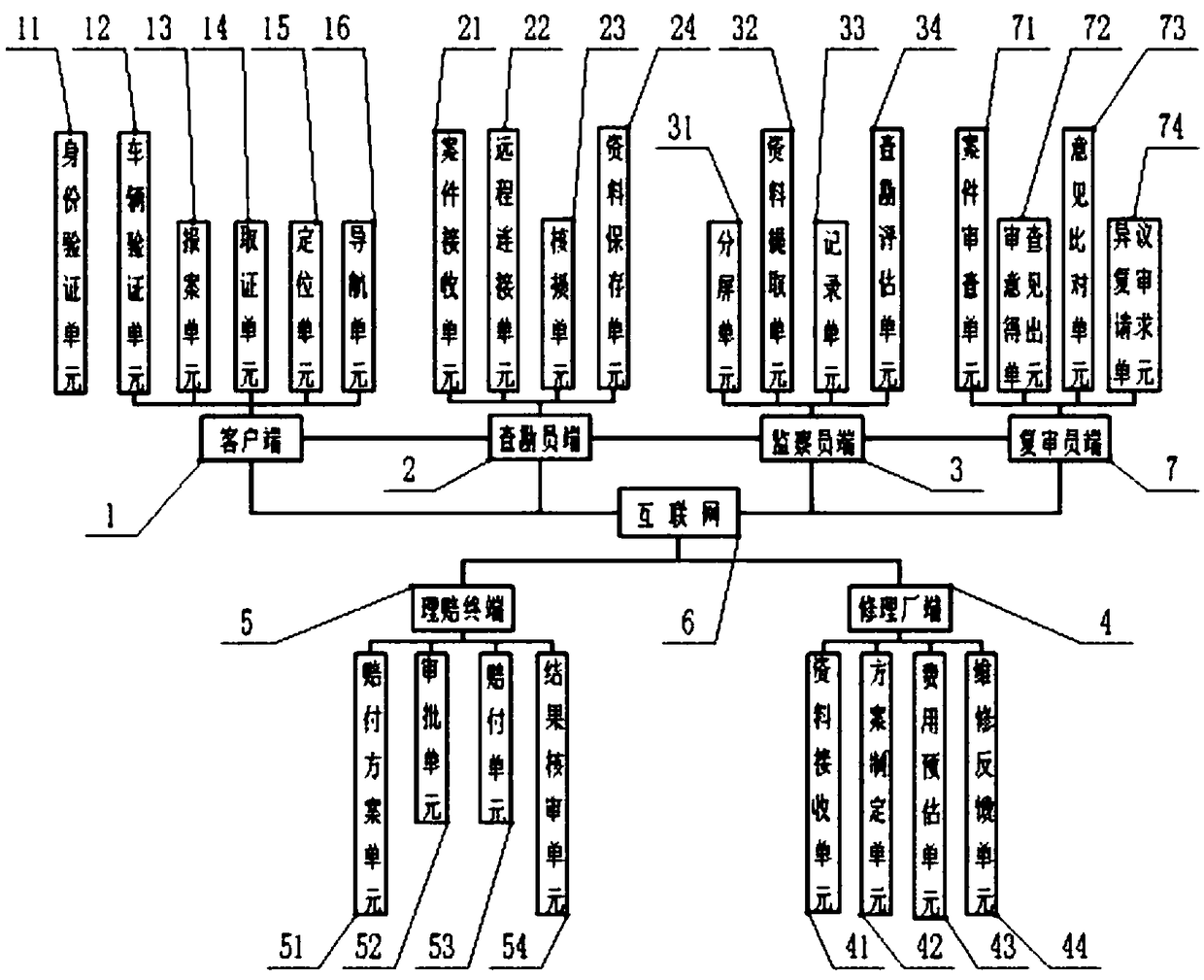
A method and a system for remotely processing automobile insurance claim settlement business
InactiveCN109034734AAvoid Malicious OperationsAvoid Incomplete ForensicsFinanceOffice automationRepair shopThe Internet
The invention relates to a method and a system for remotely processing automobile insurance claim settlement business. The method mainly comprises the following steps: S1, a vehicle owner verifies identity information and vehicle information through a client; S2: after the accident is reported, a surveyoer end is connected to the client end; S3: the surveyor and the owner of the vehicle jointly carry out verification and evidence collection; S4: supervision of forensics process is performed; S5: if the a supervisor objects to the evidentiary process, a review is conducted; S6: a repair shop formulates the maintenance plan and estimates the cost; S7: the claim settlement plan is determined and quickly approved for paying the compensation amount; S8: processing results are fed back for analysis and improvement. The system comprises a client end, a surveyor end, a supervisor end, a reviewer end, a repair shop end, a claim settlement terminal and an Internet. In a word, the invention has the advantages of excellent method, perfect system, safety and high efficiency, etc.
Owner:BEIJING JINGYOU CENTURY SOFTWARE TECH
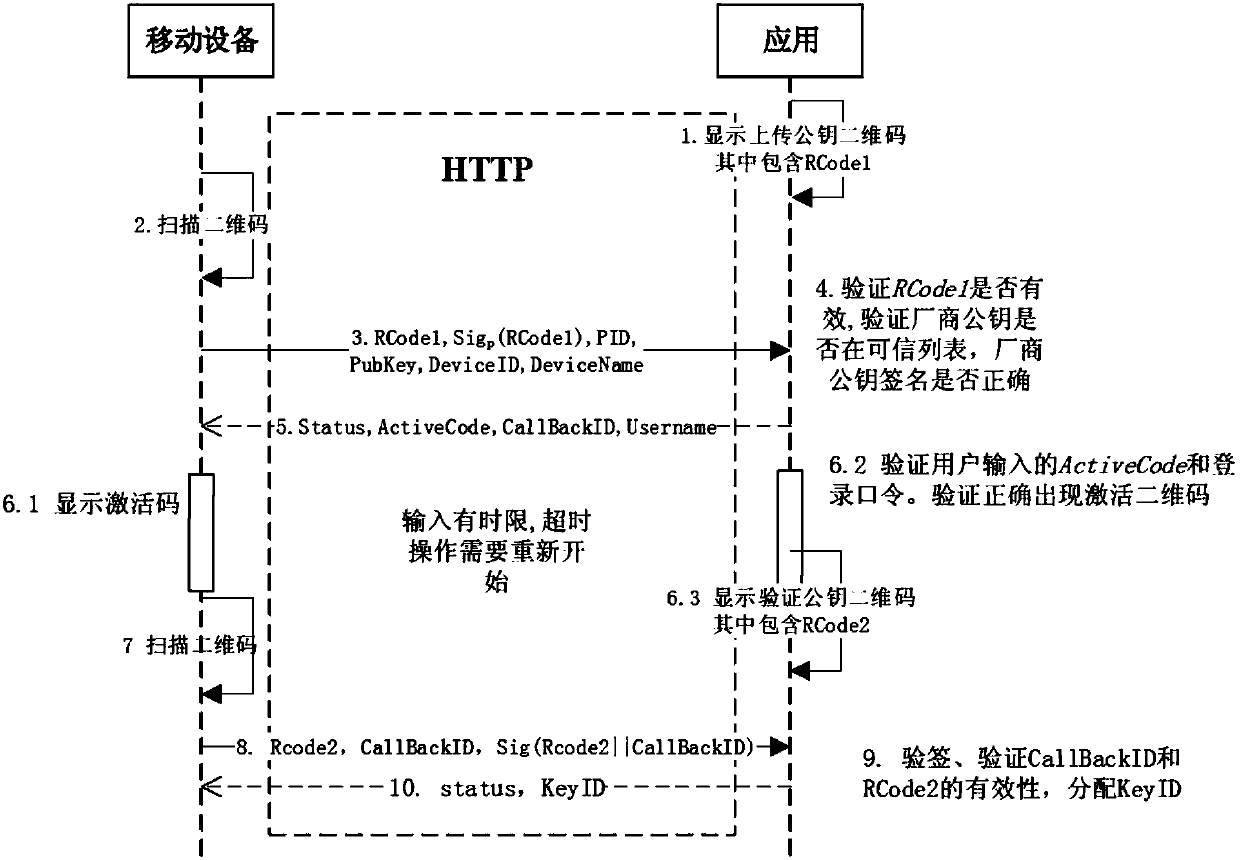
Mobile device secure binding method based on quick response code identification and application system
ActiveCN107707356AFlexible useNo physical costKey distribution for secure communicationUser identity/authority verificationMobile deviceUSB
The invention provides a mobile device secure binding method based on quick response code identification. The method is applied to binding of a mobile device and an identity account of an applicationsystem. The method comprises the following steps that an uploading quick response code generated by the application system is identified by the mobile device and the mobile device uploads a device public key to the application system according to an identification result; and a verification quick response code generated by the application system is identified by the mobile device, whether the mobile device holds a private key corresponding to the public key or not is verified according to the identification result, and the application system binds the identity account with the mobile device ifthe mobile device holds the private key corresponding to the public key. The method is applied to various mobile devices in support of public and private key pair storage; and through repeated quickresponse code identification, the mobile device and a user account identity of the application system providing service are bound, so the limitation and inconvenience of identifying the user identitythrough utilization of a U-key (USB Key) are solved, and the security is ensured. The invention also provides the application system applicable to the method.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
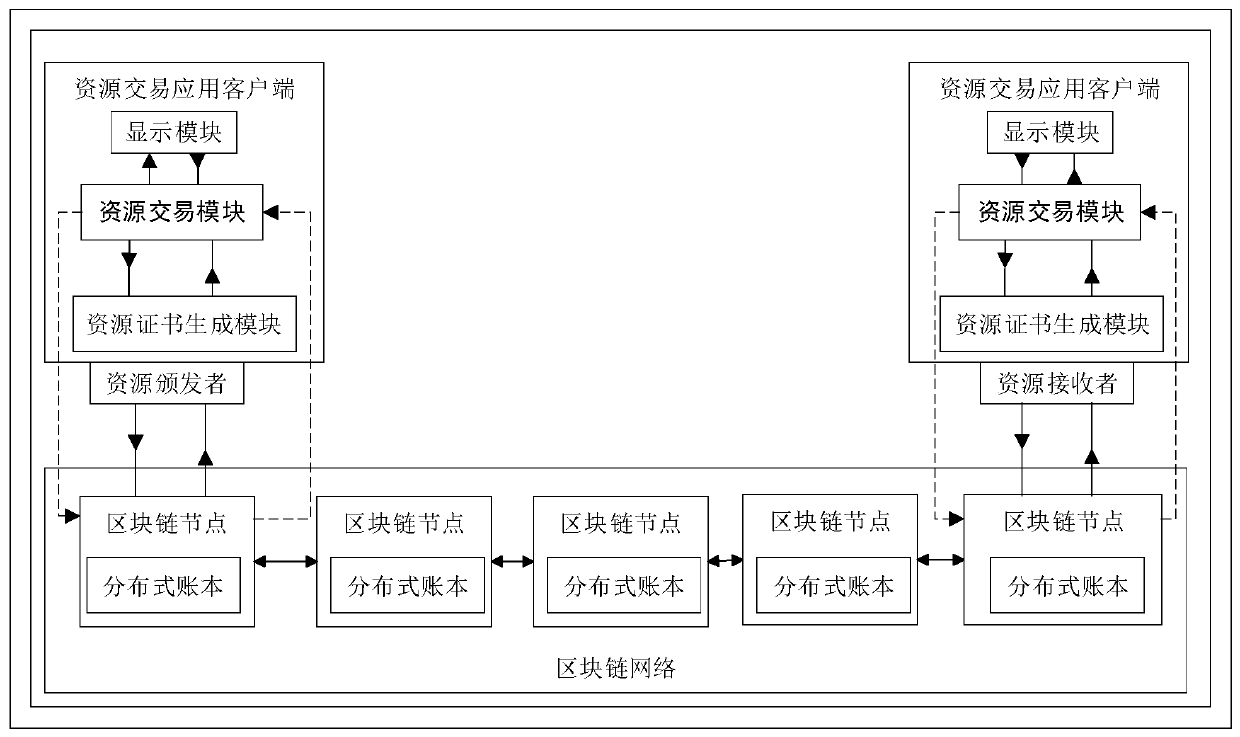
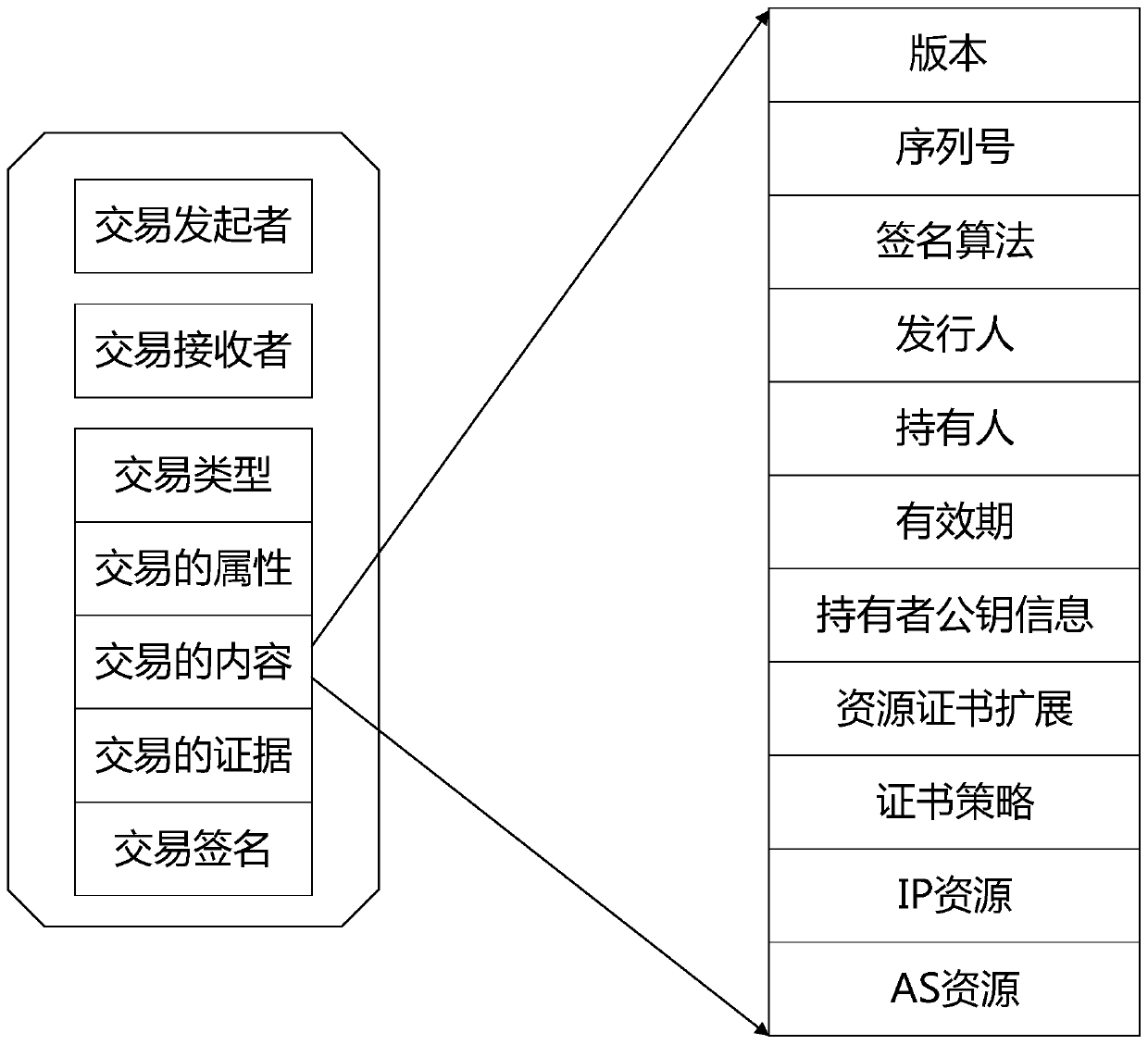
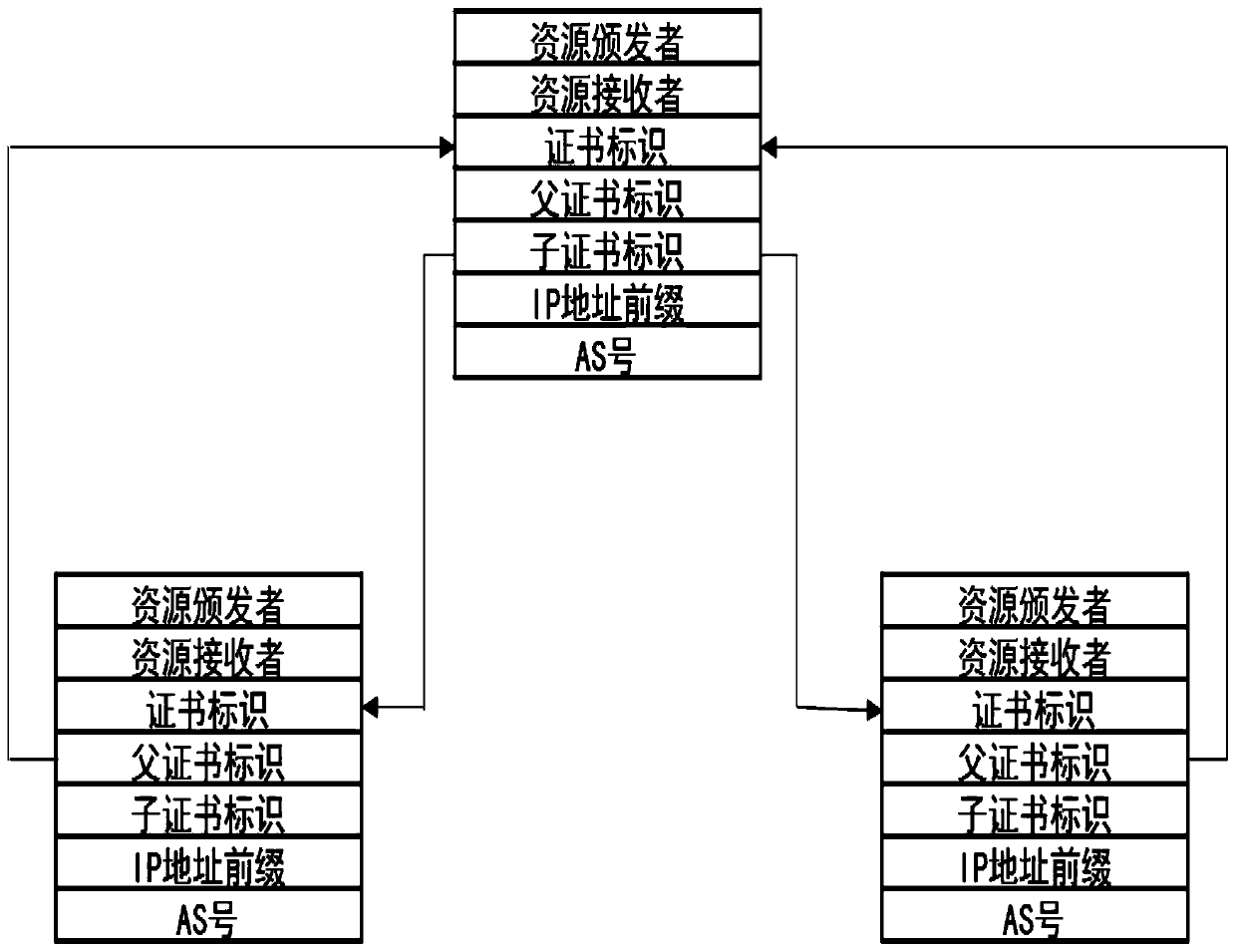
Resource public key infrastructure bidirectional authorization method based on block chain
ActiveCN111130766AAvoid Malicious OperationsAvoid security threatsKey distribution for secure communicationPublic key for secure communicationAuthorization ModeIp address
The invention discloses a resource public key infrastructure bidirectional authorization method based on a block chain, and aims to solve the security threat problems that a legal BGP route is illegal, a legal IP address is blocked and the like caused by malicious operation. The method comprises the following steps: constructing a resource public key infrastructure system RPKIB based on a block chain, wherein the resource public key infrastructure system RPKIB is composed of a resource issuer, a resource transaction application client, a resource receiver and a block chain network; changing any operation of issuing, cancelling, updating and modifying of a resource certificate by the resource issuer into a bidirectional authorization mode, and implementing the operation of the resource certificate only when the issuer and the receiver agree; and carrying out the operations of the resource certificate RC and the route origin authorization ROA as transactions by the issuer through a blockchain network, and distinguishing whether the operations are malicious behaviors or normal operations through bidirectional authorization. The method is adopted to overcome malicious operation facedby the current RPKI, and security threats such as illegal legal BGP routing and legal IP address blocking are effectively avoided.
Owner:GUANGZHOU UNIVERSITY
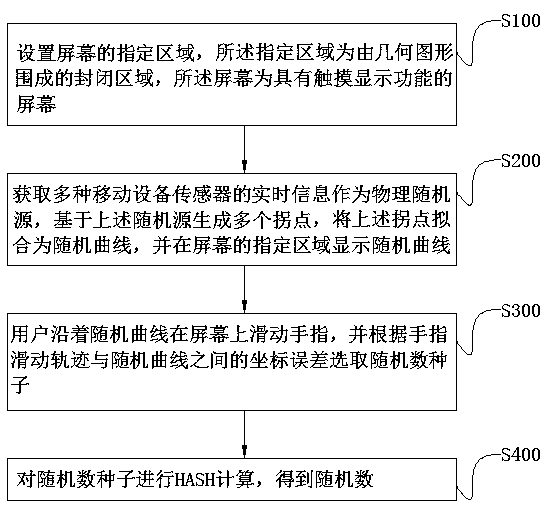
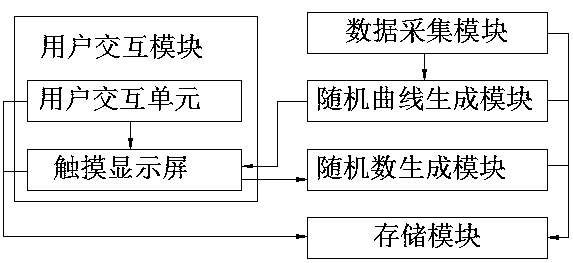
Random number generation method and system based on interactive curve
ActiveCN108804011AAvoid Malicious OperationsRandomKey distribution for secure communicationInput/output processes for data processingData acquisitionMobile device
The invention discloses a random number generation method and system based on an interactive curve, and belongs to the field of information security technology. The technical problem to be solved is how to generate random numbers of mobile equipment on the premise of ensuring security and convenience. The method comprises the following steps: generating a random curve by an acquired physical random source; making a user draw a screen along the random curve; and performing HASH calculation on coordinate errors between a screen drawing track and the random curve to generate a random number. Thesystem comprises a user interaction module, a data acquisition module, a random curve generation module, a random number generation module and a storage module. Through adoption of the method and thesystem, random and unpredictable random numbers of the mobile equipment can be generated.
Owner:北京信任度科技有限公司
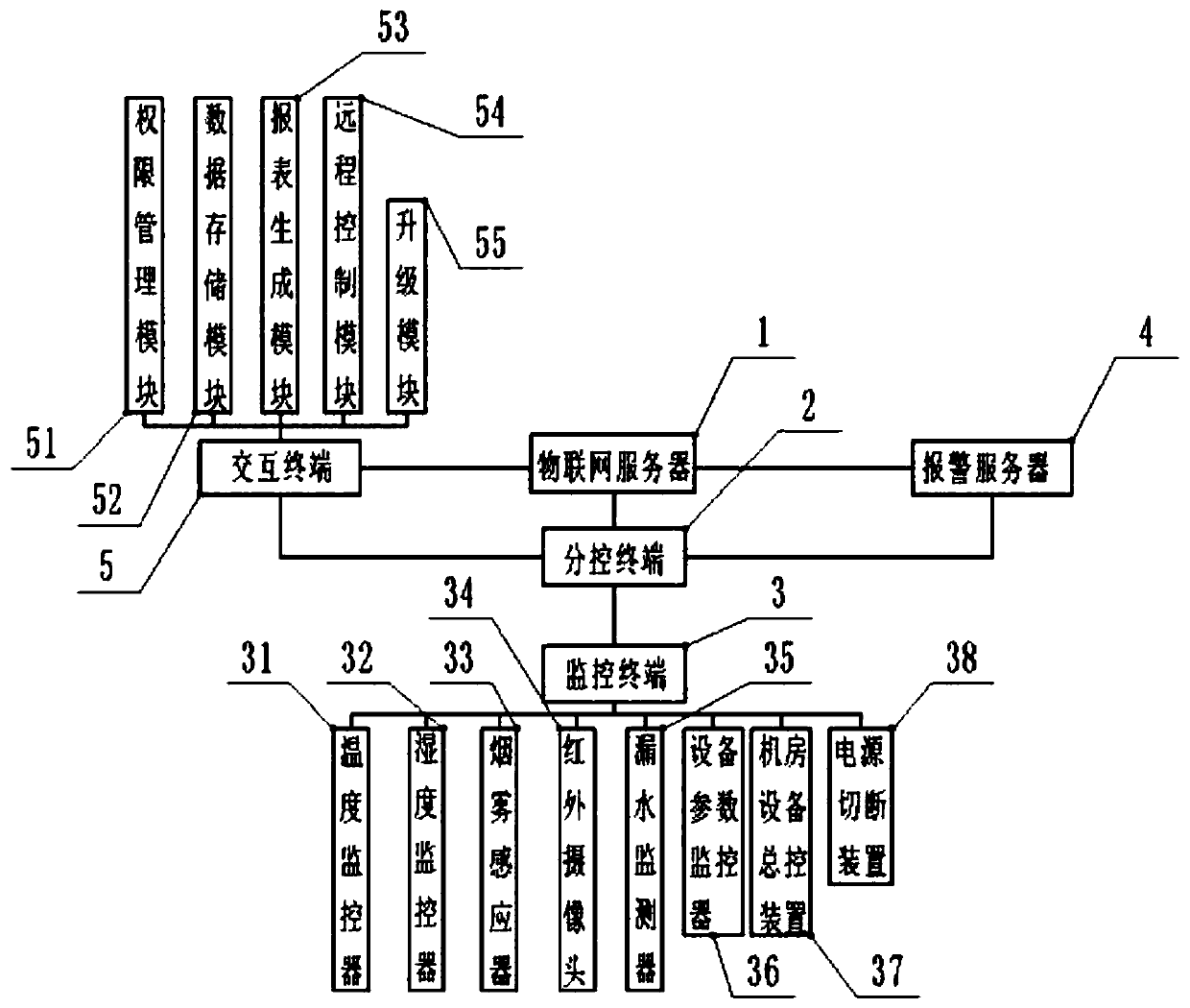
Remote electrical equipment monitoring method based on composite Internet of Things
InactiveCN109900322AFirmly connectedImprove transmission efficiencyMeasurement devicesAlarmsComputer terminalBluetooth
The invention discloses a remote electrical equipment monitoring method based on the composite Internet of Things. The method comprises steps that S1, corresponding monitoring terminals are separatelydistributed at corresponding positions in an electrical equipment room; S2, the monitoring terminals are connected with sub-control terminals through Bluetooth signals, the sub-control terminals, analarm server and an interactive terminal are respectively connected with an IoT server, and debugging of the devices for to normal operation is performed; S3, the monitoring terminals are utilized tomonitor the electrical equipment room, monitoring data are sent to the IoT server through the sub-control terminals, the IoT server is used for sending the monitoring data to the interactive terminal,and abnormal data is sent to the alarm server; S4, the alarm server realizes analysis and ranking according to the abnormal monitoring data received, and the corresponding alarm mode is adopted; andS5, the staff can view and manage the monitoring data on the interactive terminal.
Owner:仁诚建设有限公司
Key instruction processing method and terminal
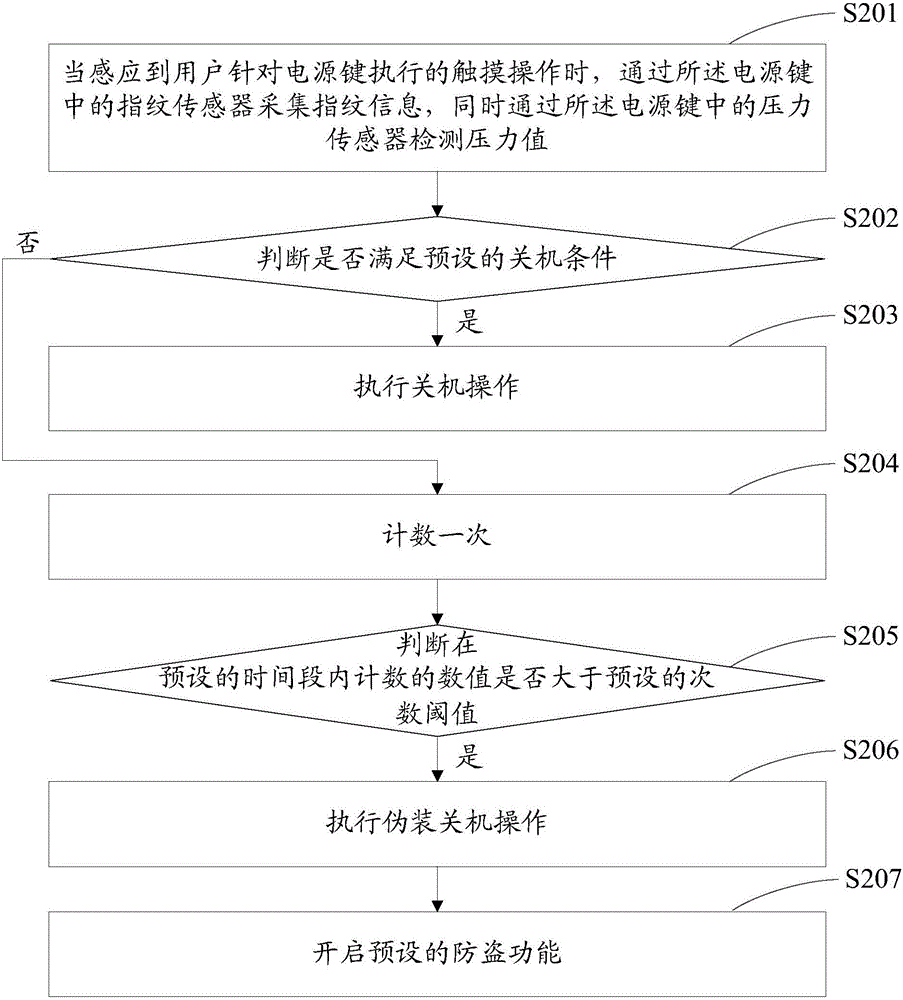
InactiveCN105844181AAvoid Malicious OperationsInternal/peripheral component protectionFingerprintPressure threshold
The embodiment of the invention discloses a key instruction processing method. The method is applied to a terminal. A fingerprint sensor and a pressure sensor are arranged in a key of the terminal. The method comprises the following steps of: acquiring fingerprint information through the fingerprint sensor in the key while inducing touch operation of a user for the key, and simultaneously, detecting a pressure value through the pressure sensor in the key; judging whether pre-set conditions are satisfied or not, wherein the pre-set conditions are as follows: the acquired fingerprint information is matched with pre-set fingerprint information; and the detected pressure value is greater than a pre-set pressure threshold value; and, if the pre-set conditions are satisfied, executing operation corresponding to the key. Correspondingly, the embodiment of the invention further discloses the terminal. By adopting the embodiment of the invention, the key can be prevented from being operated maliciously.
Owner:SHENZHEN GIONEE COMM EQUIP
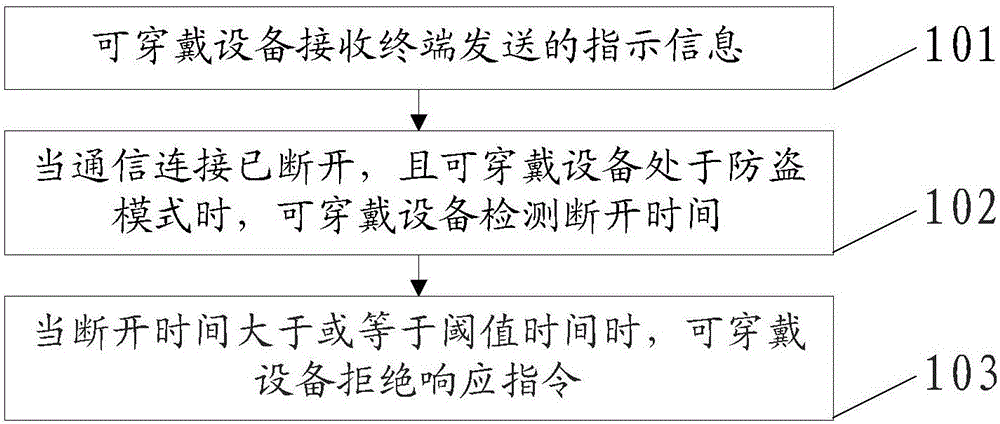
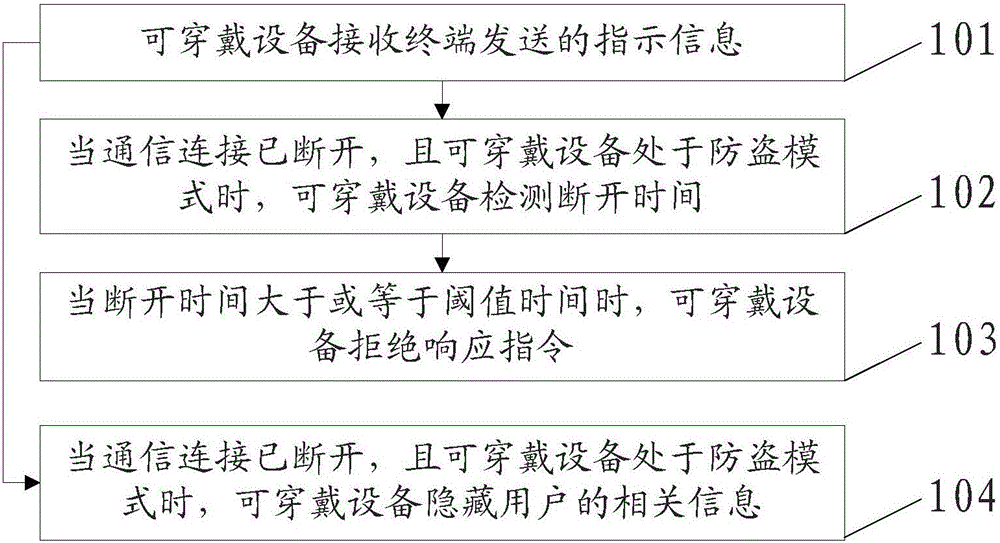
Wearable device-based information anti-theft method, device and apparatus
ActiveCN105812584AImprove securityPrevent leakageSubstation equipmentTransmissionComputer hardwareAnti theft
An embodiment of the invention discloses wearable device-based information anti-theft method, device and apparatus, relates to the technical field of communications and aims to improve usage safety of a wearable device.The method of the embodiment comprises: a wearable device receives an indicative message transmitted by a receiving terminal, the indicative message being useful for indicating whether the wearable device is in an anti-theft mode, wherein the wearable device has been in communication connection with the terminal; in case that the communication connection is broken, the wearable device enters the anti-theft mode and detects disconnection time, wherein a start moment of the disconnection time is the moment when the communication connection is broken, and a stop moment of the disconnection time is a current moment; when the disconnection time is longer than or equal to a threshold time, the wearable device refuses to respond to a command.The invention is suitable for a communication network system.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
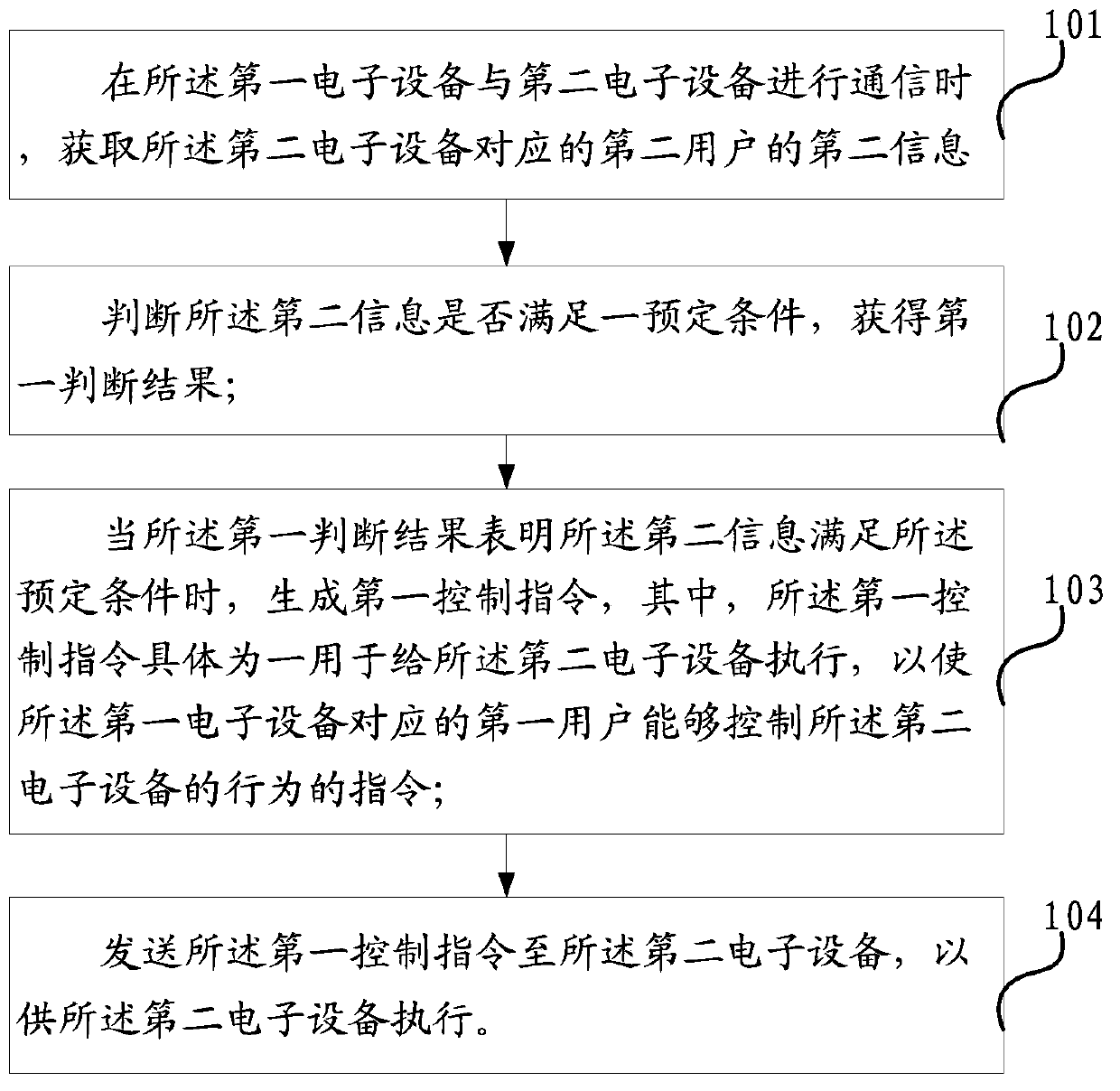
Electronic device control method and electronic device
ActiveCN103873658ASolve the technical problem of not being able to control the other party's mobile phone to store the call contentSolve the technical problem that the other party's mobile phone cannot control the local mobile phone to store the call contentSubstation equipmentControl electronicsReal-time computing
The invention discloses an electronic device control method and an electronic device, solving the technical problem of prior art that a handset can not control the handset of the opposite side to store conversation content. The method is applied to a first electronic device and comprises the steps of: obtaining the second information of a second user corresponding with a second electronic device when a first electronic device and the second electronic device are communicating; determining whether the second information meets a predetermined condition to obtain a first determination result; generating a first control instruction when the first determination result shows that the second information meets the predetermined condition, wherein the first control instruction is concretely an instruction used for the execution of the second electronic device so that the first user corresponding with the first electronic device can control the actions of the second electronic device; and sending the first control instruction to the second electronic device for the execution of the second electronic device.
Owner:LENOVO (BEIJING) LTD
Control method and control apparatus of substation active misoperation prevention equipment
ActiveCN105374088AImprove securityAvoid Malicious OperationsIndividual entry/exit registersComputer sciencePower substation
Owner:STATE GRID CORP OF CHINA +1
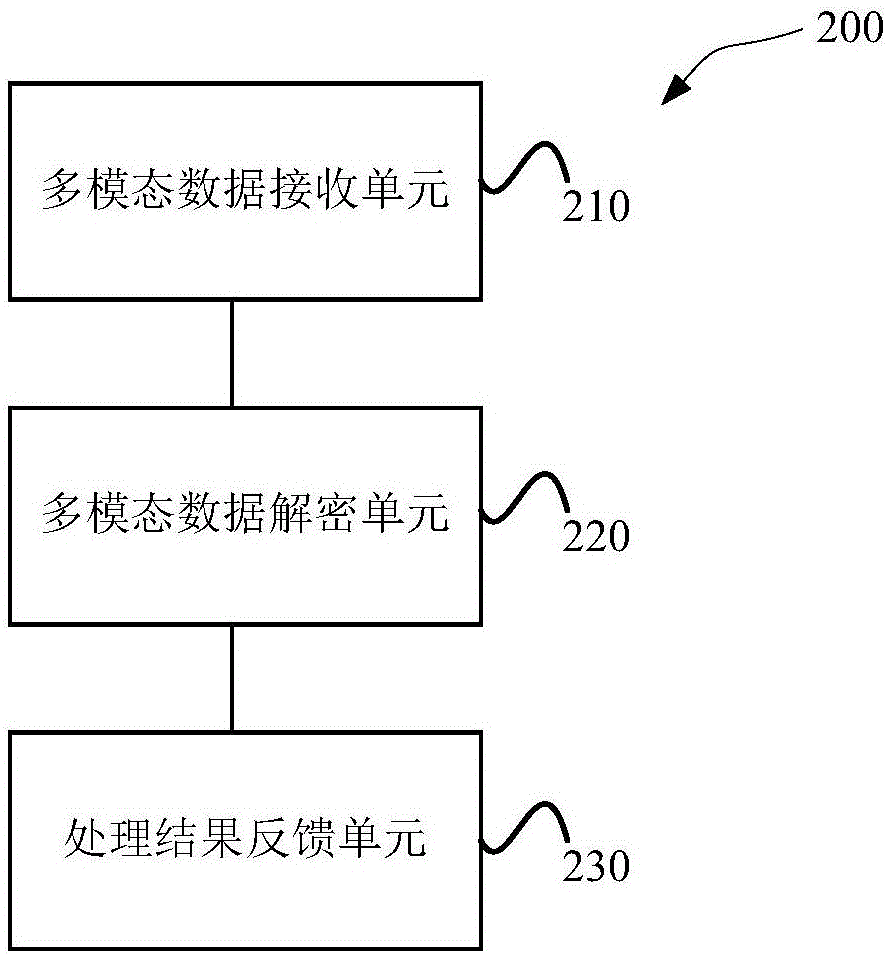
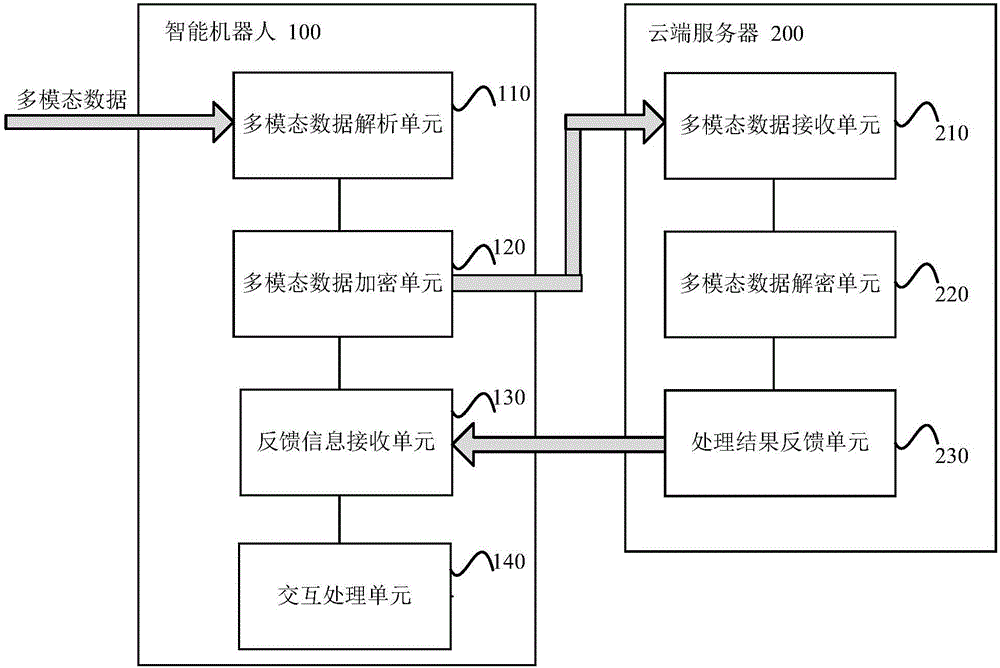
Data interaction method and system based on intelligent robot
InactiveCN106411873AEnsure information securityAvoid Malicious OperationsTransmissionMultimodal dataData needs
The invention discloses a data interaction method and system based on an intelligent robot. The intelligent robot is provided with a robot operating system, and the robot operating system performs control to execute the following steps: receiving multimodal data and analyzing the multimodal data; and when it is determined that the analyzed multimodal data needs to be uploaded to a server, acquiring a preset key, encrypting the analyzed multimodal data, and uploading the analyzed multimodal data to the server. By adoption of the data interaction method and system disclosed by the invention, in an interaction process of a user and the intelligent robot, the information security of the cloud server can improved, and related data of the intelligent robot can be prevented from being stolen.
Owner:BEIJING GUANGNIAN WUXIAN SCI & TECH
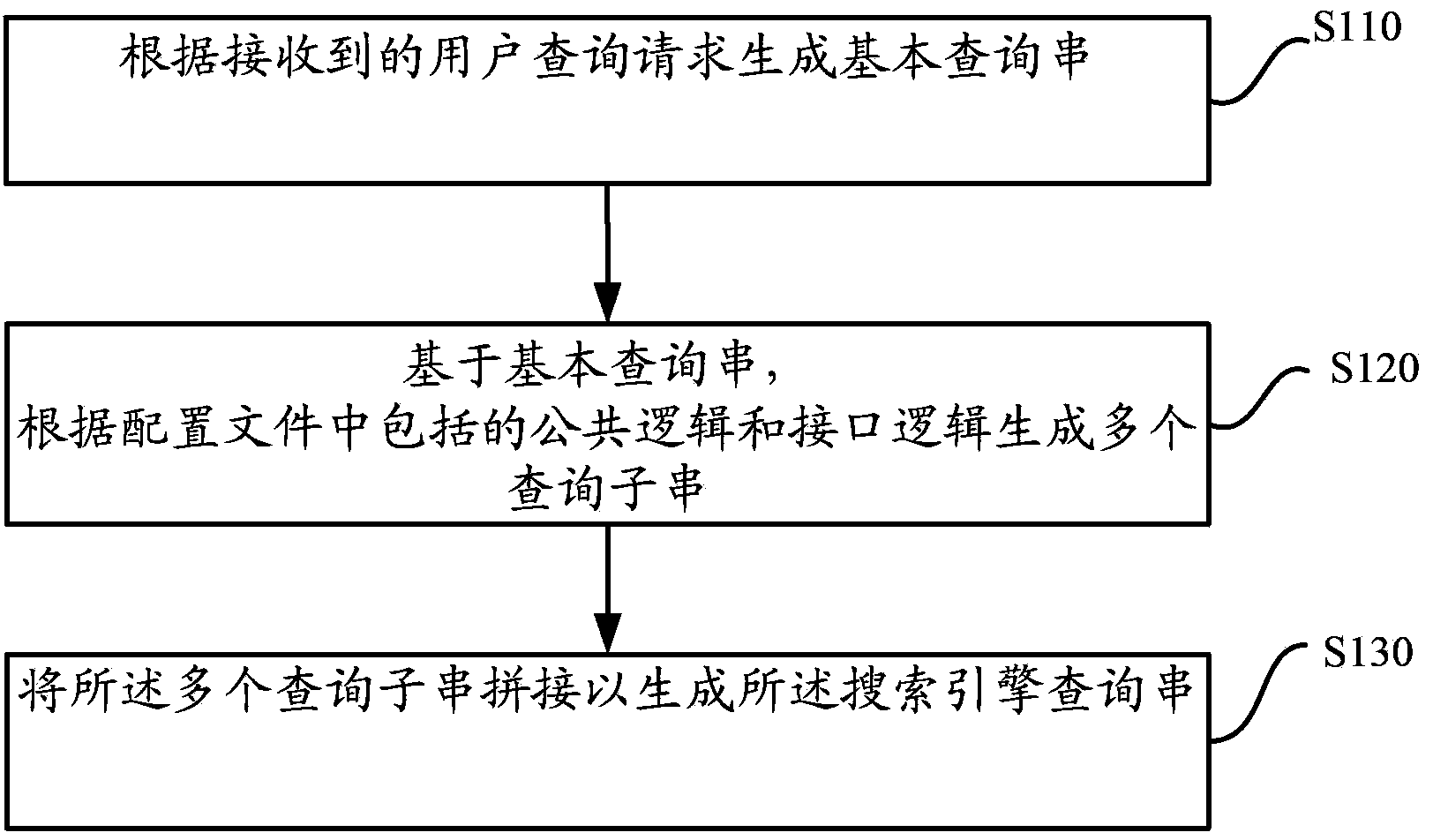
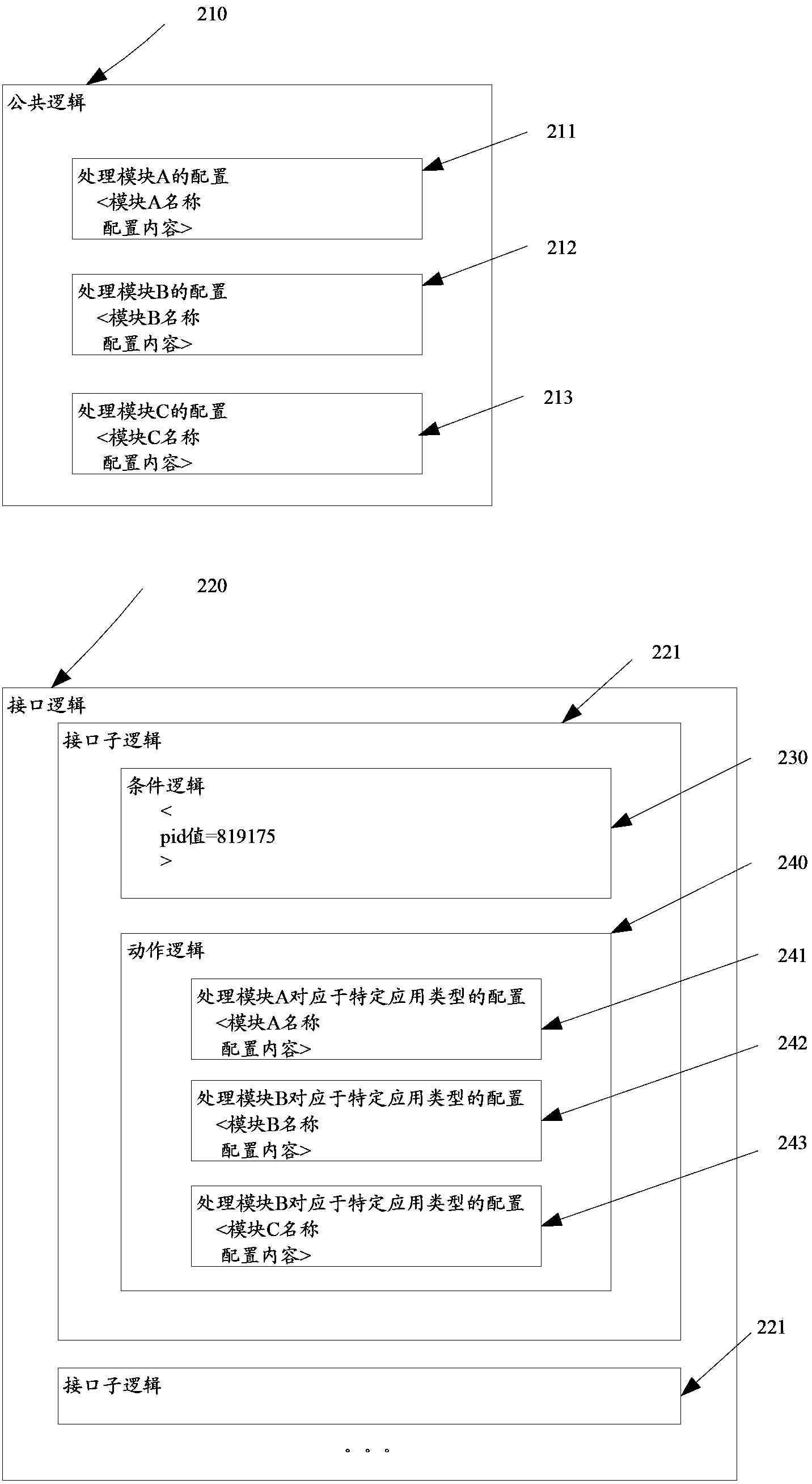
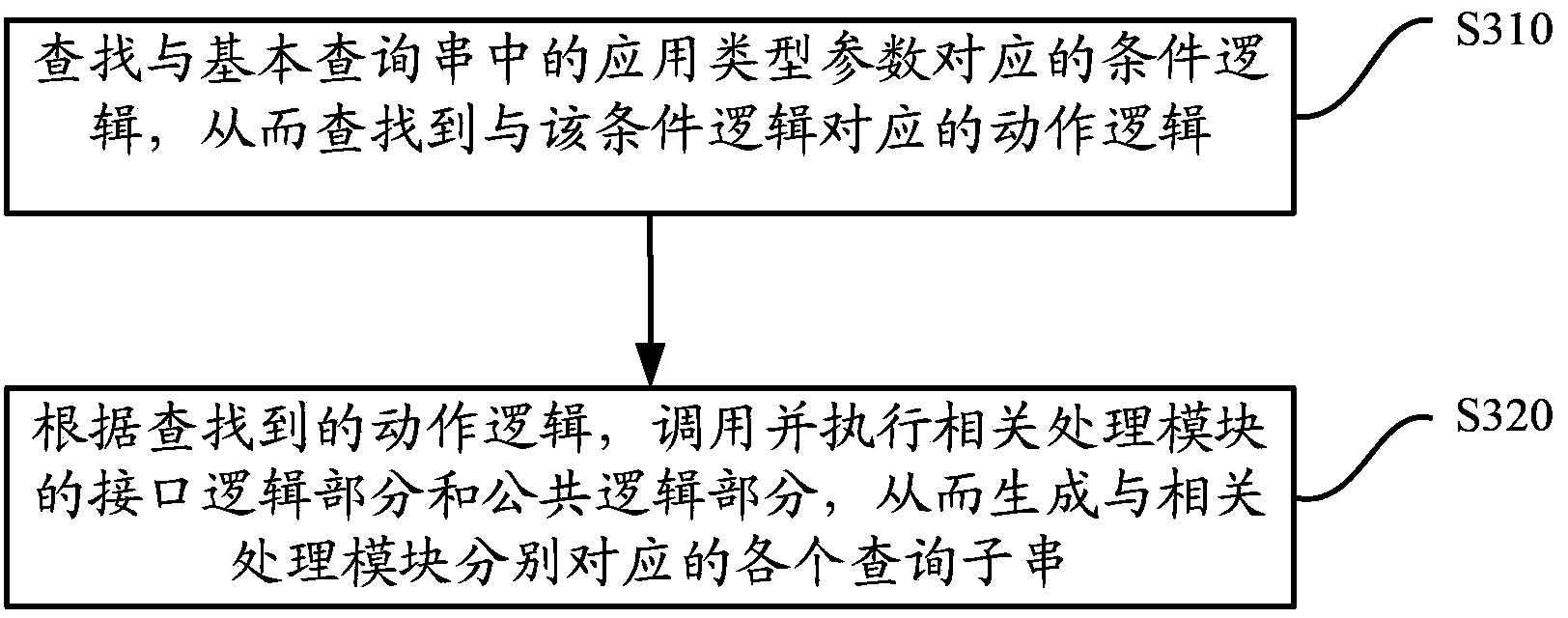
Search engine query string generation method and device and search engine system
ActiveCN104239021AAvoid Malicious OperationsImprove query performanceSpecific program execution arrangementsSpecial data processing applicationsQuery stringSearch engine query
The invention relates to a search engine query string generation method and device and a search engine system. The method includes generating a base query string according to a received user query request; on the basis of the base query string, generating a plurality of sub query requests according to public logic and interface logic of configuration files; connecting the sub query requests to generate a search engine query string. According to the technical scheme, the search engine query string can be generated dynamically, and modification and maintenance can be performed as required by modifying configuration parameters of the configuration files. The engine querying performance is improved, the engine maintaining cost is reduced, and external malicious operations on the search engine can be avoided.
Owner:ALIBABA GRP HLDG LTD
Building intercom indoor unit, control method thereof and storage medium
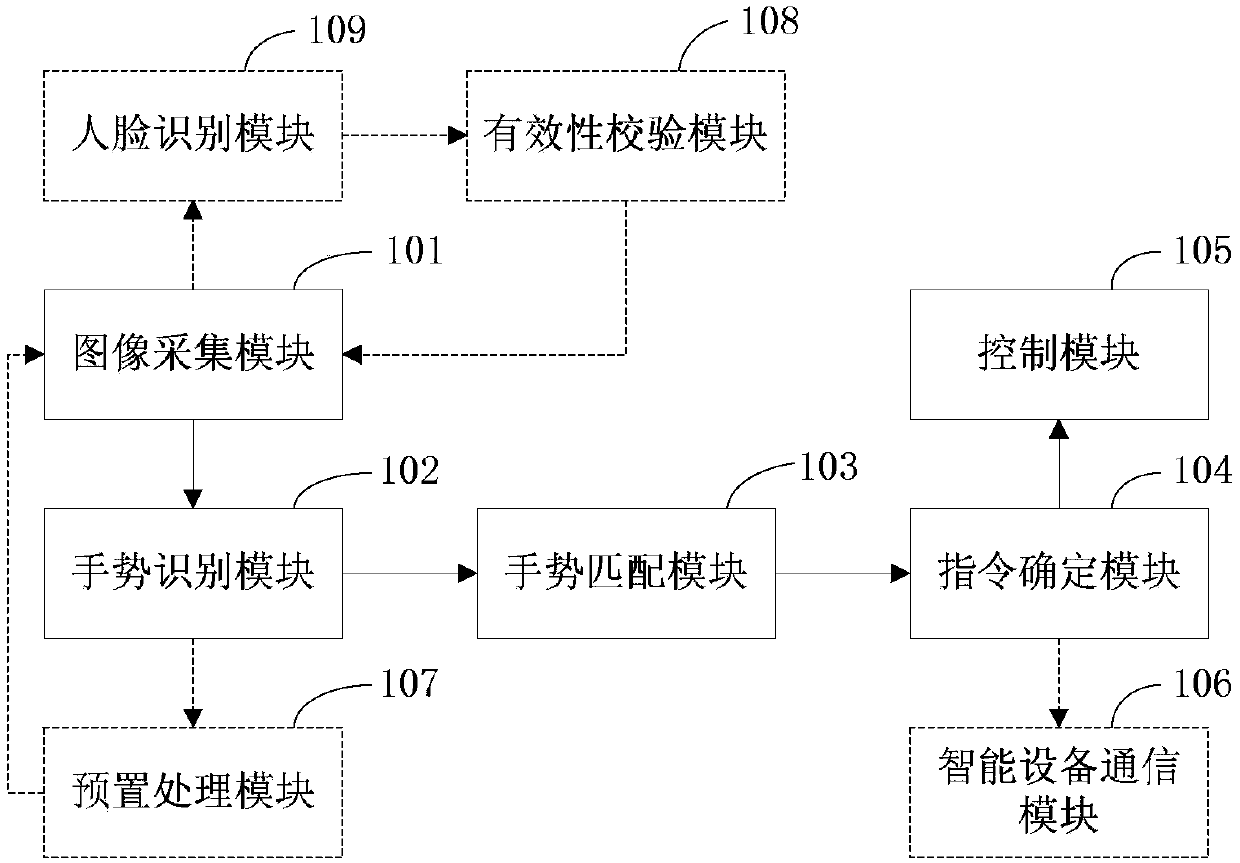
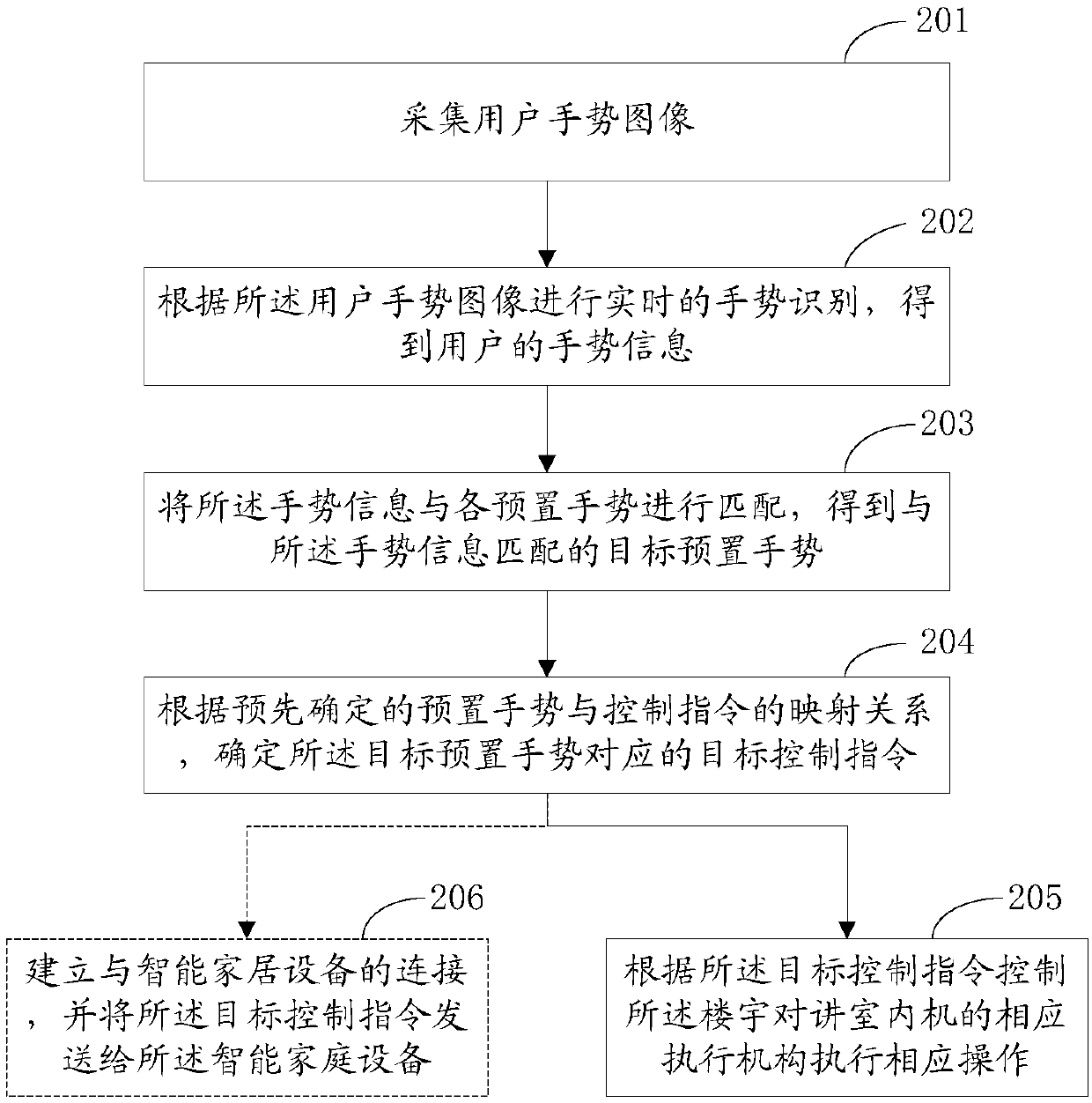
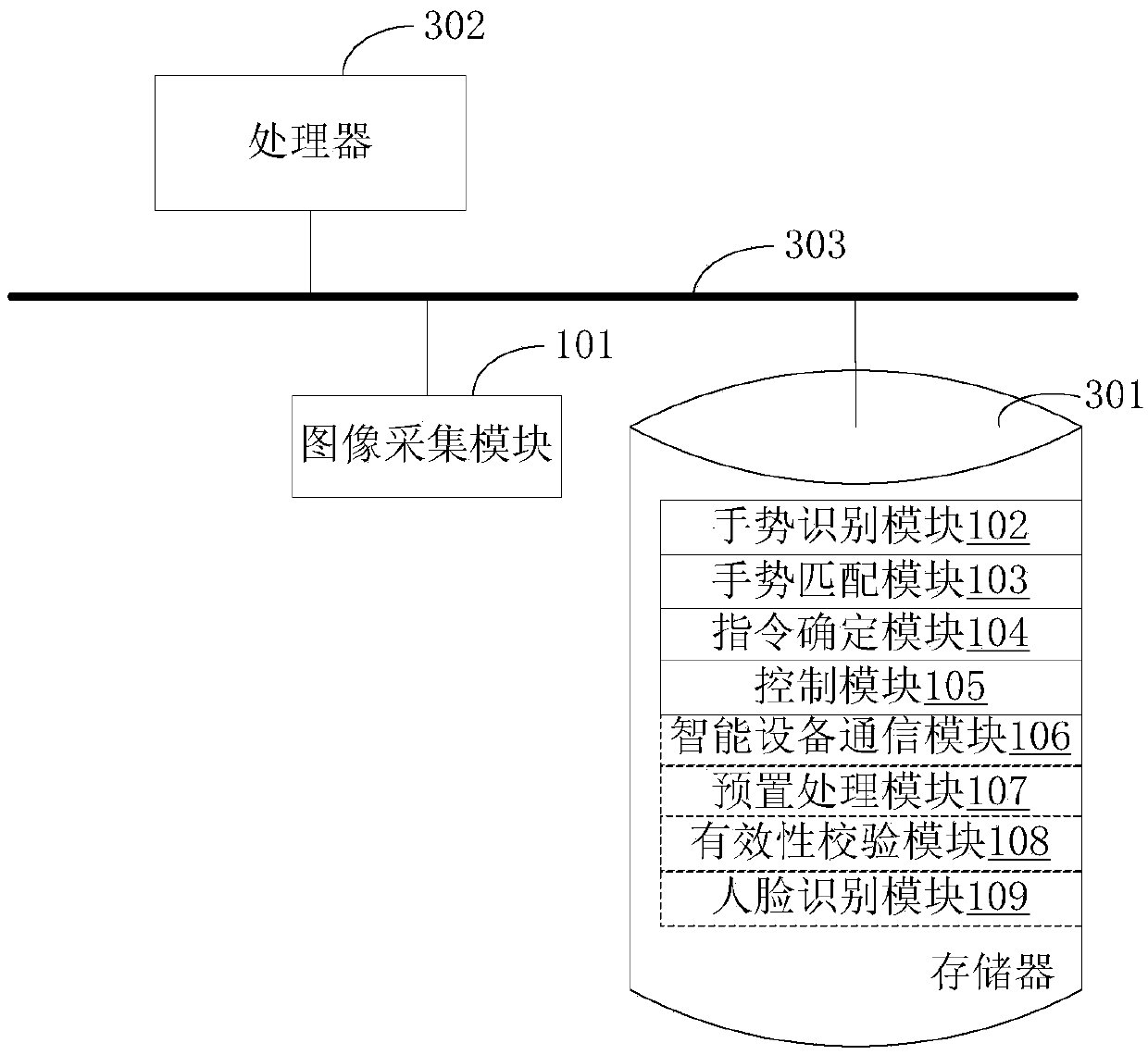
PendingCN110874131AImprove convenienceImprove efficiencyInput/output for user-computer interactionData switching by path configurationComputer hardwareTarget control
The invention discloses a building intercom indoor unit and a control method thereof. The building intercom indoor unit comprises an image collection module used for acquiring a user gesture image; atleast one memory storing a computer program; the at least one processor is used for calling the computer program stored in the at least one memory and interacting with the image collection module soas to execute the following operations: performing real-time gesture recognition according to a user gesture image to obtain gesture information of a user; matching the gesture information with each preset gesture to obtain a target preset gesture; determining a target control instruction corresponding to the target preset gesture according to a predetermined mapping relationship between the preset gesture and the control instruction; and controlling the building intercom indoor unit to execute corresponding operation according to the target control instruction. According to the technical scheme provided by the embodiment of the invention, the control convenience and efficiency of the building intercom indoor unit can be improved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
System lock screen protection method and system
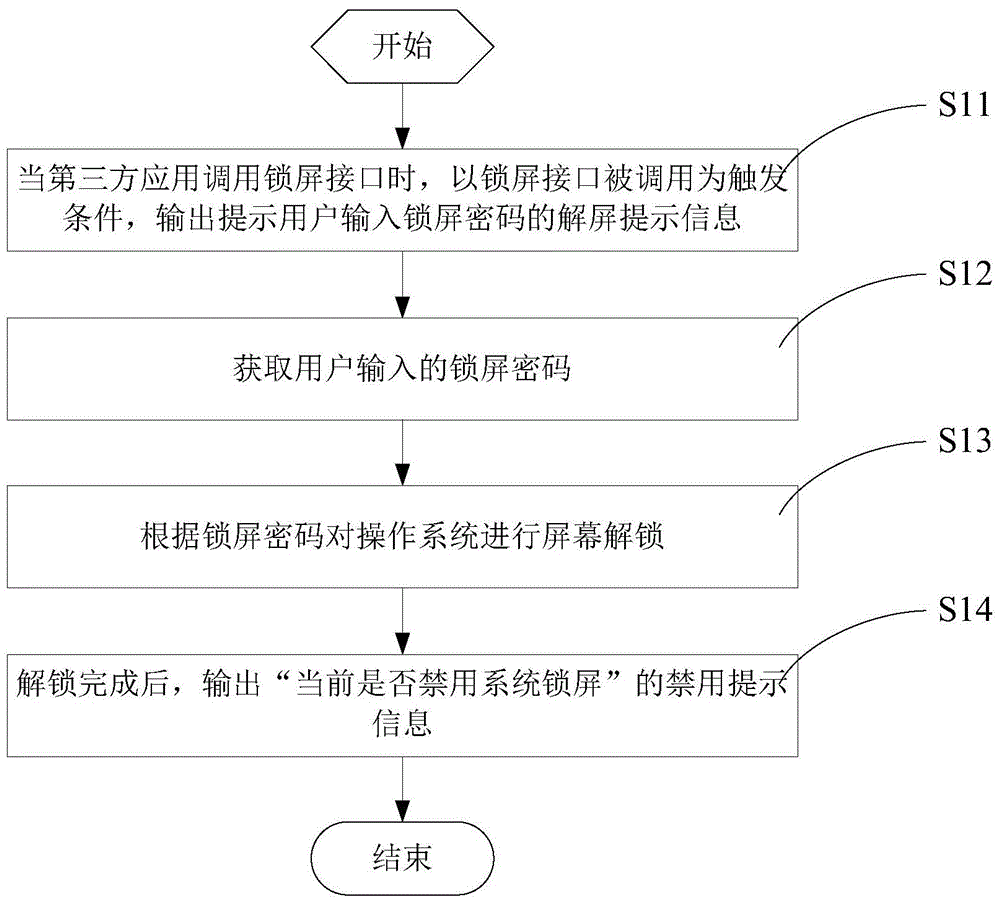
InactiveCN105718786AAvoid Malicious OperationsAvoid malicious program cracking situationsDigital data authenticationPlatform integrity maintainanceThird partySoftware engineering
The invention discloses a system lock screen protection method and system. The method comprises the following steps of when a third-party application calls a lock screen interface, reminding a user of inputting a lock screen password; performing screen unlocking on an operating system according to the screen locking password; and then, telling the user that the third-party application executing the system lock screen function closing operation exists at present through reminding the user of whether to forbid the system lock screen or not at present. The reminding information includes identification information of the third-party application, so that the user can judge whether the third-party application is a rogue program or not according to the identification information, and effective measures can be adopted. The method and the system have the advantages that the lock-screen interface is subjected to real-time monitoring; reminding information is output when the lock screen interface is called; and the system lock screen protection is realized. Meanwhile, the right of an operator is set through enabling the user to input the lock screen password, so that only the user knowing the lock screen password has the right to decide whether to forbid the system lock screen or not; the malicious operation of others can be prevented; and the further protection on the system lock screen is realized.
Owner:THUNDER SOFTWARE TECH
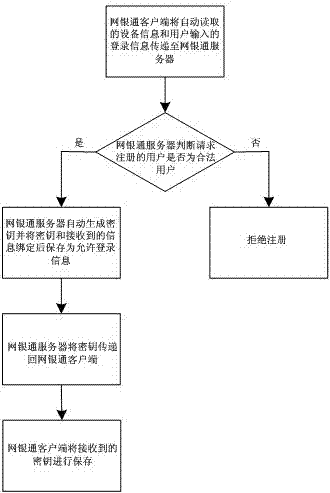
Online bank security protection method
InactiveCN103209182AImprove securityAvoid Malicious OperationsKey distribution for secure communicationFinanceBank accountTerminal equipment
The invention discloses an online bank security protection method which mainly solves the problem of poor online bank login security in the prior art. The online banking security protection method includes downloading an online banking client side to a user terminal device and setting up an online banking server which is used for the supervision of a login prohibition state and a login permission state of an online bank account and the register and login authorization of the online banking client side; registering for the online banking client side on the online banking server through a user; and setting the user who logs in the online banking client side successfully and obtains login authorization as a login permitted user through the online banking server, wherein any online bank login is required to request login authorization authentication from the online banking server and only the online bank login passing through the authorization authentication is allowed. The online bank security protection method is good in security, intelligent and high in practical value and application value.
Owner:上海金融云服务集团安全技术有限公司
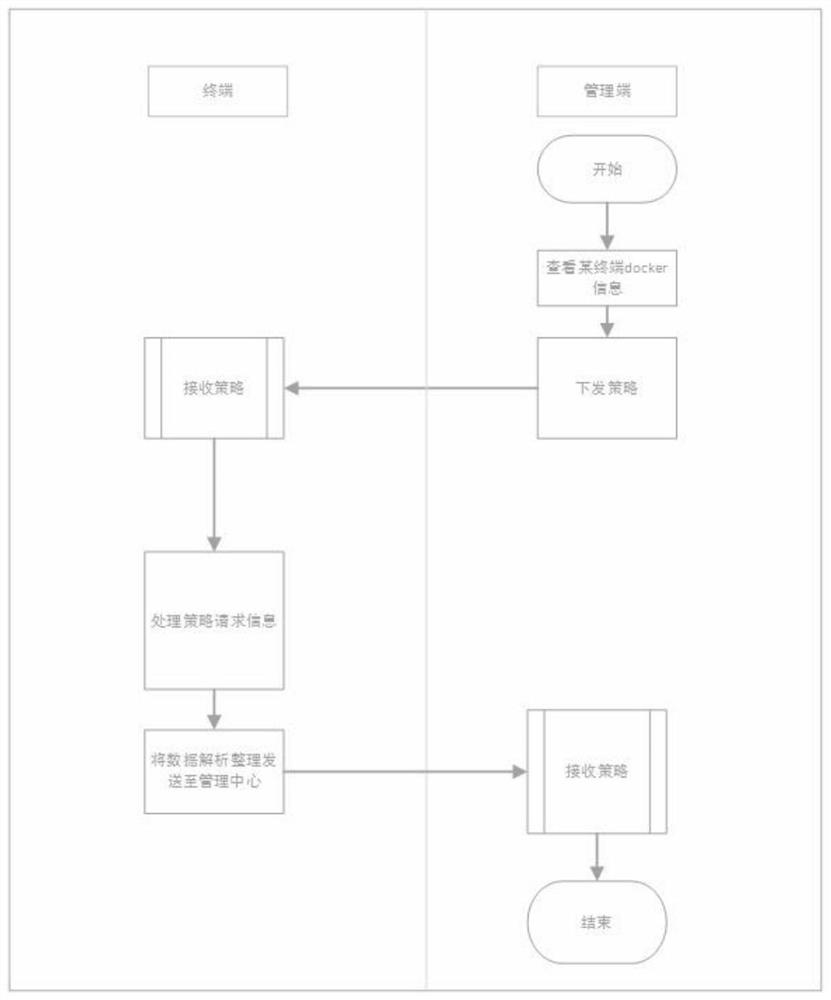
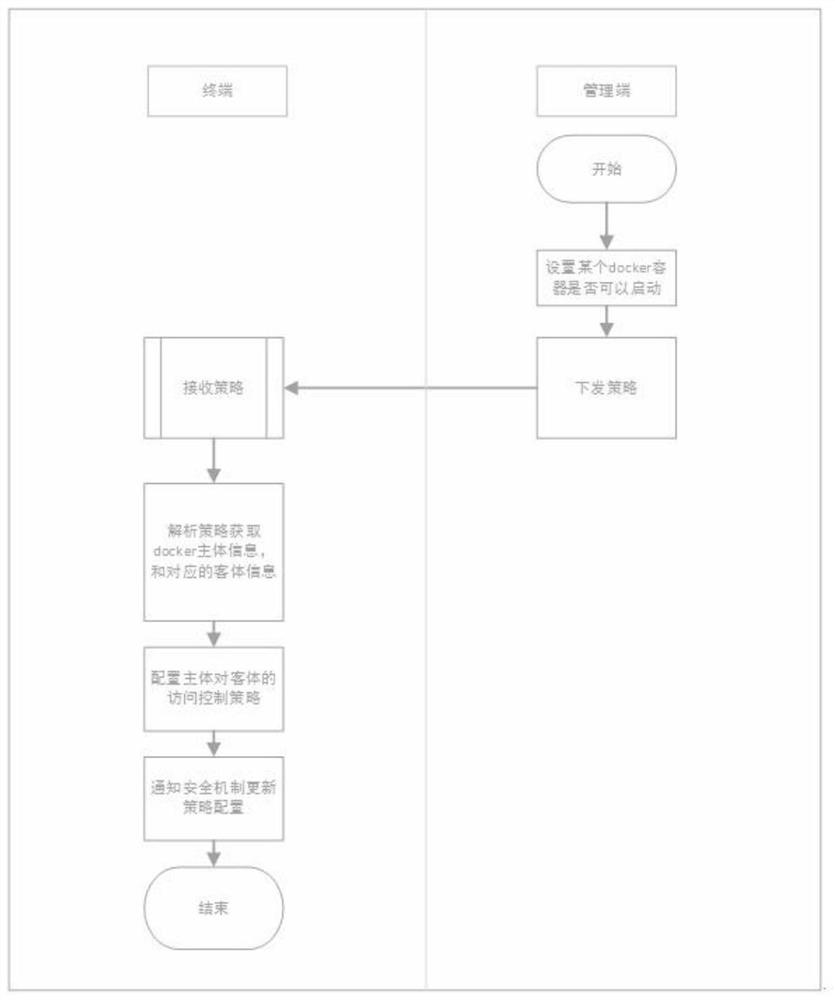
Management and control method for Docker container creation and destruction
ActiveCN114615064AAvoid Malicious OperationsAvoid modificationSecuring communicationContainer statusReliability engineering
The invention provides a management and control method for creating and destroying a Docker container, which comprises the following steps that: a management end initiates a strategy request for acquiring the state of the Docker container to a terminal, and the terminal receives the strategy request, and after the terminal processes the strategy request, information for analyzing the strategy request is analyzed and sent to the management end; when the management end configures whether the docker container can be started or not, the management end sets and issues a starting management and control strategy to the terminal, after the terminal receives the starting management and control strategy, corresponding object information is found out according to subject information of the docker container, and a corresponding access control permission strategy is configured for an object; and when the management end closes the management and control of the docker container, the management end triggers and sends a closing management and control strategy for closing the docker container to the terminal, and after the terminal receives the closing management and control strategy, all docker strategies including the starting management and control strategy are eliminated, and a security mechanism is notified to update the strategy. According to the method and the system, the business service can be effectively prevented from being interfered and damaged, and the safety management and control of Docker container creation and recovery are solved.
Owner:北京旋极安辰计算科技有限公司
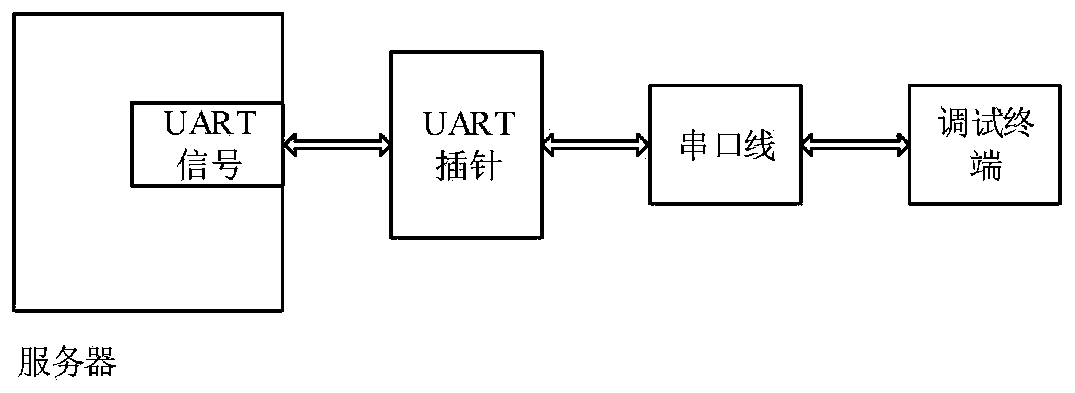
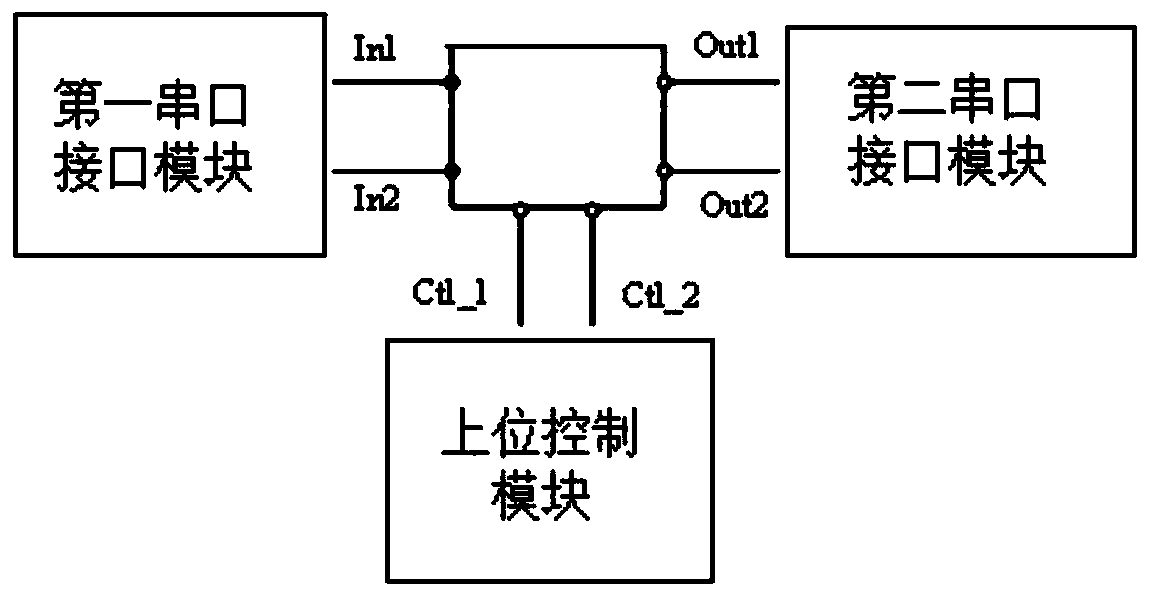
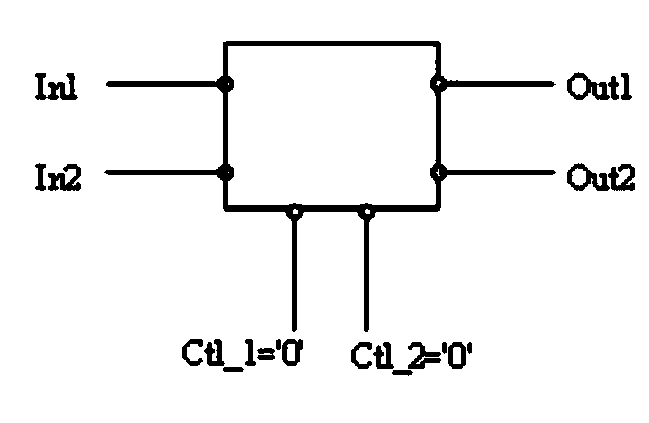
Server serial port disabling protection circuit and method
ActiveCN110378155AImprove securityAvoid Malicious OperationsInternal/peripheral component protectionComputer moduleControl circuit
The invention discloses a server serial port forbidding protection circuit which comprises a logic circuit module, the input end of the logic circuit module is connected with a first serial port interface module, the output end of the logic circuit module is connected with a second serial port interface module, and the control end of the logic circuit module is connected with an upper control module. The logic circuit module comprises a serial port sending end control circuit and a serial port receiving end control circuit, the control end of the serial port sending end control circuit is at ahigh level, the input end of the serial port sending end control circuit is connected with the output end path, the control end is at a low level, and the input end of the serial port sending end control circuit is disconnected with the output end path; the control end of the serial port receiving end control circuit is at a high level, and the input end of the serial port receiving end control circuit is communicated with the output end path; the control end is at a low level, and the serial port receiving end controls the input end and the output end of the circuit to be disconnected. The invention further discloses a serial port protection method, a hardware circuit of the server mainboard does not need to be additionally added, and the design flexibility is improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
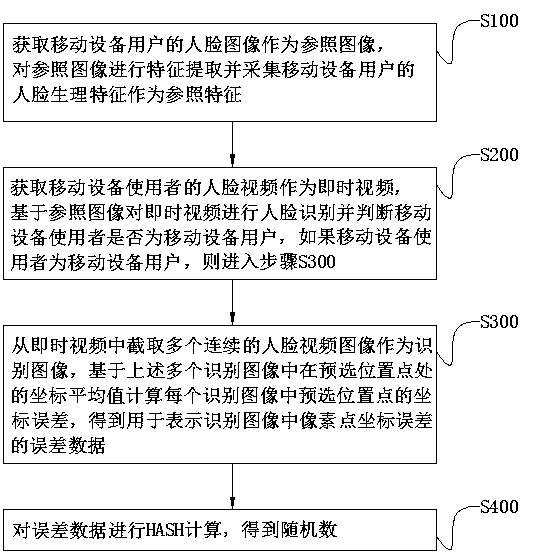
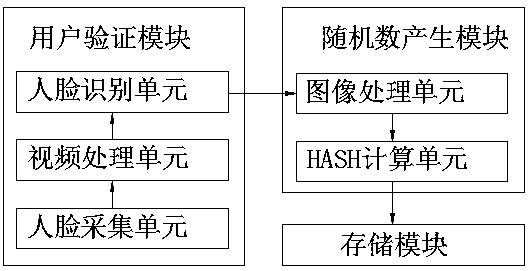
Random number generation method and system based on face image recognition
ActiveCN108921036AAvoid Malicious OperationsAvoid lostRandom number generatorsCharacter and pattern recognitionUser verificationPattern recognition
The invention discloses a random number generation method and system based on face image recognition, belongs to the field of an information security technology and aims to solve the technical problemof how to generate a random number of a mobile device on the premise of guaranteeing security and convenience. According to the method, whether a mobile device user is a mobile device owner or not isconfirmed by acquiring a face video of the mobile device user and performing face recognition, and a random number is generated by performing error calculation on the face video of the mobile deviceuser. The system comprises a user verification module, a random number generation module and a storage module, wherein the user verification module comprises a face collection unit, a video processingunit and a face recognition unit, and the random number generation module comprises an image processing unit and a HASH calculation unit. Through the random number generation method and system, a random and unpredictable random number can be generated, and loss caused by mobile device losing can be avoided.
Owner:北京信任度科技有限公司
Method for improving performance of customer premise equipment, and customer premise equipment
InactiveCN105376424AImprove performanceImprove usabilitySpecial service for subscribersCustomer-premises equipmentTerminal equipment
Owner:ZTE CORP
System and method for obtaining user interactive data by Web table list
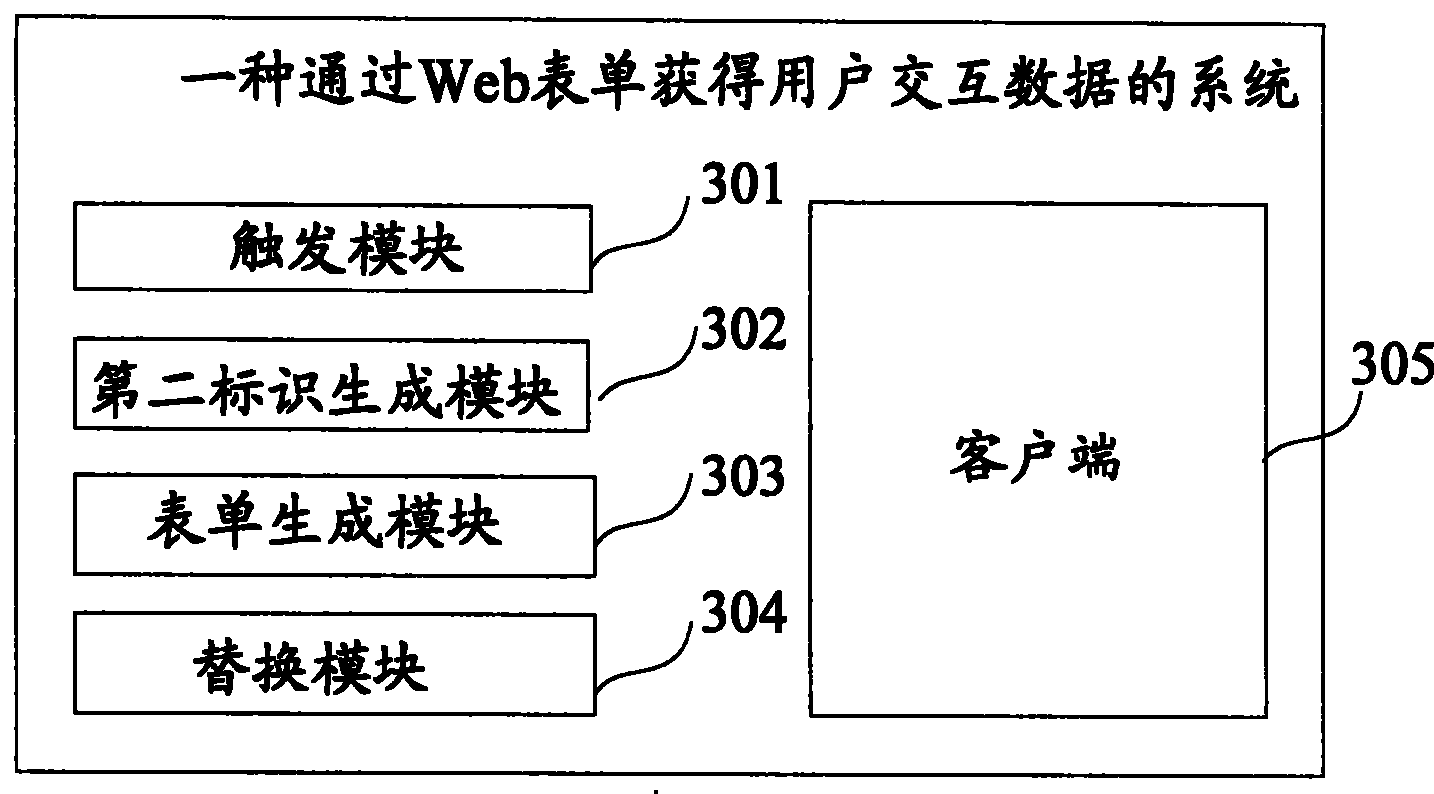
ActiveCN101227451BAutofill implementationAutofill PreventionTransmissionSpecial data processing applicationsUser inputWeb tables
Owner:ADVANCED NEW TECH CO LTD
Misoperation prevention isolating switch
ActiveCN101604584APrevents unintentional misuseEnsure safetyElectric switchesEngineeringHigh pressure
The invention discloses a misoperation prevention isolating switch which relates to an isolating switch, in particular to an isolating switch suitable for a soft starting cabinet of an electric motor. The invention can lock a handle when the handle is switched in a communication position so as to be capable of shutting down in time when an accident to be generated or the accident is generated in the running process of a large-scale electric motor. The invention is provided with cabinet door misoperation prevention systems playing a locking role in a soft starting cabinet door of the electric motor, the cabinet door is locked in the running process of the large-scale electric motor and can not be unlocked so as to prevent equipment damage or electric shock due to electric operation when high voltage is led in the soft starting cabinet of the electric motor. The invention reasonably limits the staring of the large-scale electric motor and the unlocking of the cabinet door by the two misoperation prevention systems with simple operation and ensures the safety of staffs and equipment.
Owner:SHANGHAI RENLE SCI & TECH
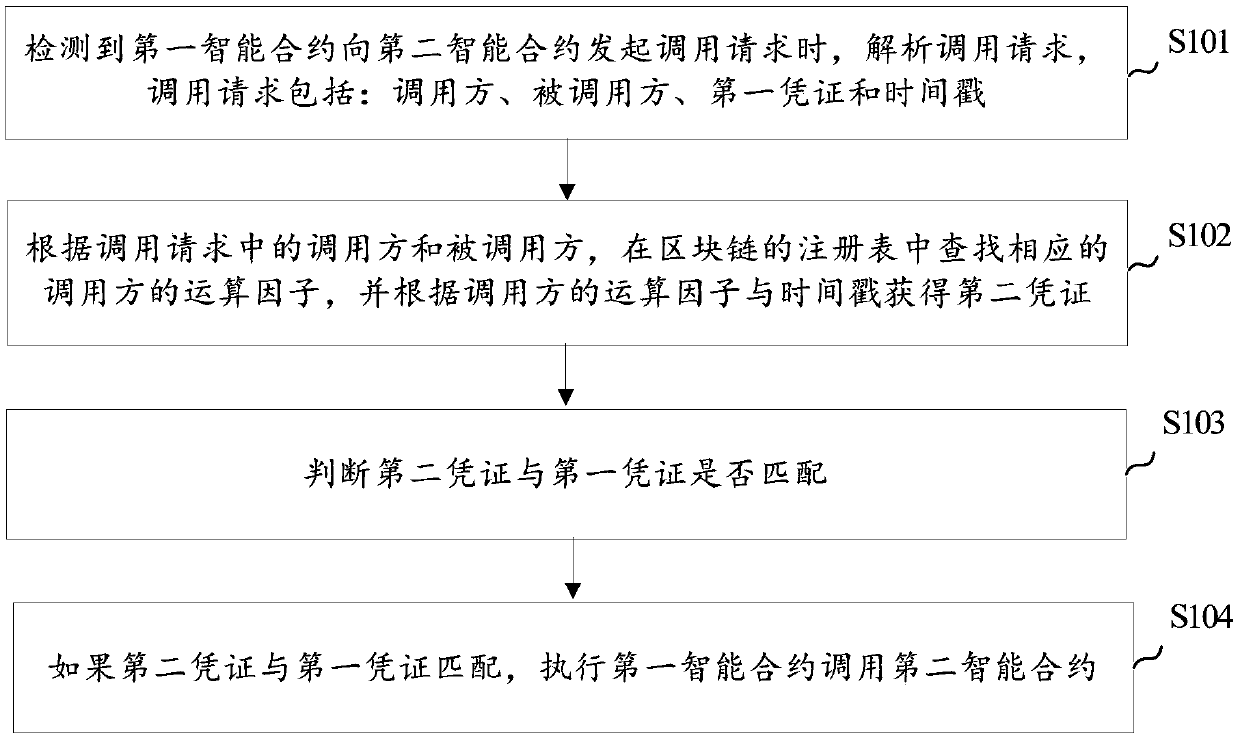
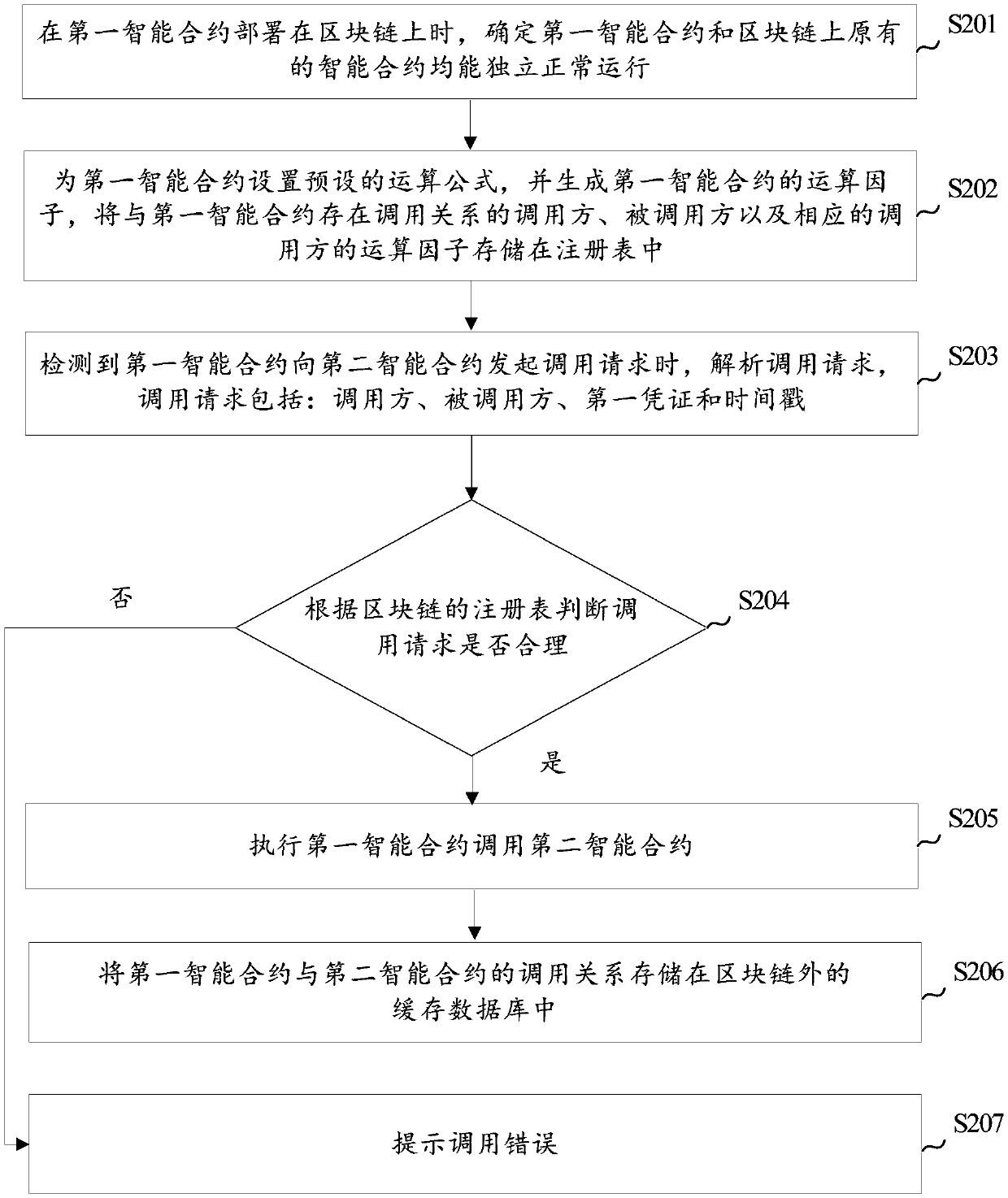
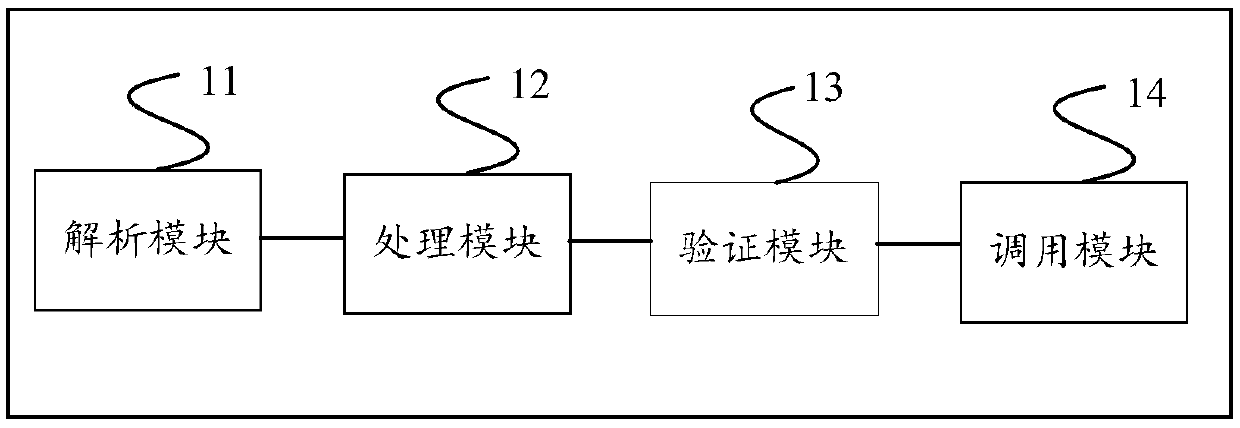
Method and device for managing and controlling invocation between intelligent contracts
ActiveCN109543457AGuaranteed execution securityAvoid Malicious OperationsFinanceDigital data protectionTimestampVoucher
The present application provides a method and apparatus for managing invocation between intelligent contracts. The method comprises the following steps: when detecting that the first intelligent contract initiates the invocation request to the second intelligent contract, analyzing the invocation request, wherein the invocation request comprises a caller, a called part, a first credential and a timestamp; according to the caller and the callee in the call request, searching the operation factor of the corresponding caller in the registry of the block chain, and obtaining the second credentialaccording to the operation factor and the timestamp of the caller; Judging whether the second voucher matches the first voucher; If the second credential matches the first credential, the first smartcontract is executed to invoke the second smart contract. Thus, the invocation between intelligent contracts can be managed, and the invocation between intelligent contracts can be guaranteed to be reliable and safe.
Owner:TAIKANG LIFE INSURANCE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com