Mobile device secure binding method based on quick response code identification and application system
A mobile device and application system technology, which is applied in the field of computer technology and information security, can solve the problems of not using two-dimensional codes and mobile device identity security verification, and achieve the effects of flexible use, cost reduction, convenient maintenance and use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the purpose, technical solution and advantages of the present invention more clear, the present invention will be further described in detail through examples below.
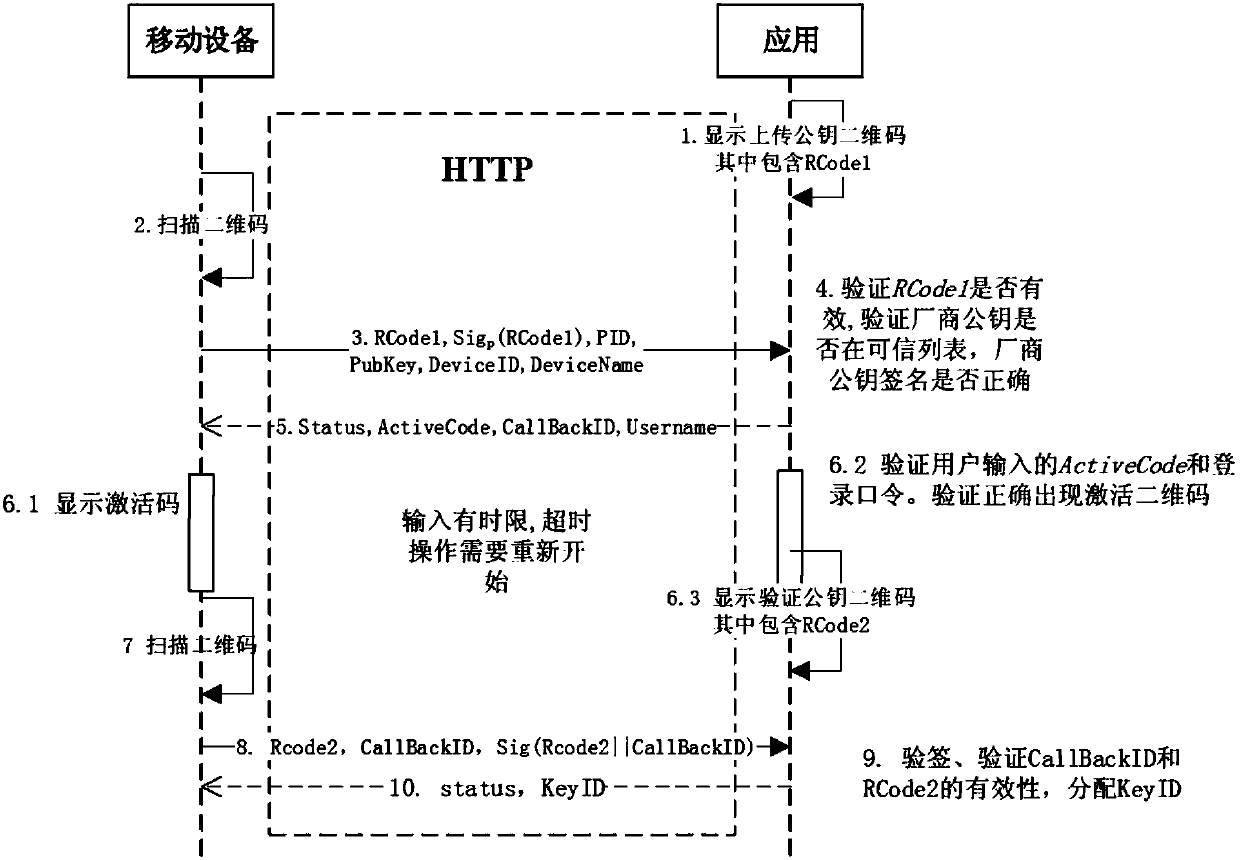
[0026] Such as figure 1 As shown in the figure, it is a schematic flowchart of the mobile device secure binding method based on two-dimensional code identification of the present invention. The figure schematically shows the relationship between the mobile device and the application system and the data interaction verification between the two. In a nutshell, the mobile device transmits its stored public key and related evidence to verify the validity of the public key to the application system; after the application system verifies the validity of the public key, it will bind the mobile device with the identity of the current account, And persist the data of the binding relationship.
[0027] Among them, the mobile device supports the safe storage function of public and private keys and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com