User behavior clustering analysis method and terminal, and computer readable storage medium
A cluster analysis and behavior technology, applied in computer parts, computer security devices, computing, etc., can solve problems such as inability to accurately and quickly distinguish user types, and low accuracy of user behavior clustering.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
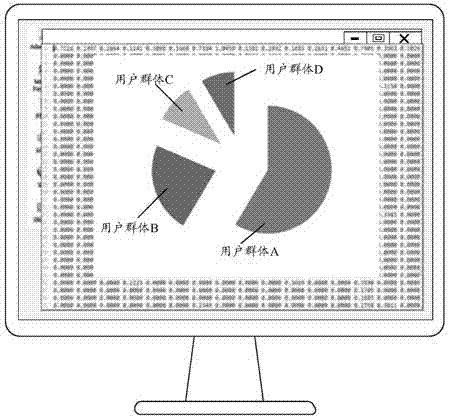
[0066] In the traditional user behavior analysis, it is judged through the pre-established user behavior model, and only the user's behavior operation is the same or similar to the operation specified by the user behavior model, then the user behavior operation is considered to be legal, but this It is only to judge the operation itself, and there is no corresponding induction for the user behavior operation after the judgment is completed, or the corresponding user is classified, which leads to the need for repeated comparison operations in the prior art, and The accuracy rate of the judgment is not high. In order to solve the above problems, the embodiment of the present invention provides a user behavior cluster analysis method. The category of user groups is convenient for quickly locating bad users.
[0067] Such as figure 2 as shown, figure 2 It is a flow chart of the user behavior cluster analysis method provided by this embodiment of the present invention, which is...
no. 2 example
[0116] Such as image 3 As shown, it is another flow chart of the user behavior clustering analysis method provided by Embodiment 2 of the present invention. This method is based on the operation plan proposed by the specific website, for example, the Alibaba sales platform, which specifically includes the following steps:
[0117] S301. The system collects user behavior. Develop a user behavior recording module to record the behavior of all users on the website and record these behaviors to the database.
[0118] S302, extracting user behavior. Analyze the user behavior in the database and extract various behaviors of the user. For example, user A's behavior includes: whether to log in from another place, log in time, log in location, stay time, query sales data, change password, etc.
[0119] S303, feature item extraction. Based on the feature item extraction algorithm, the behavior that best represents a certain user is extracted to form a feature item. For example, in...
Embodiment 3
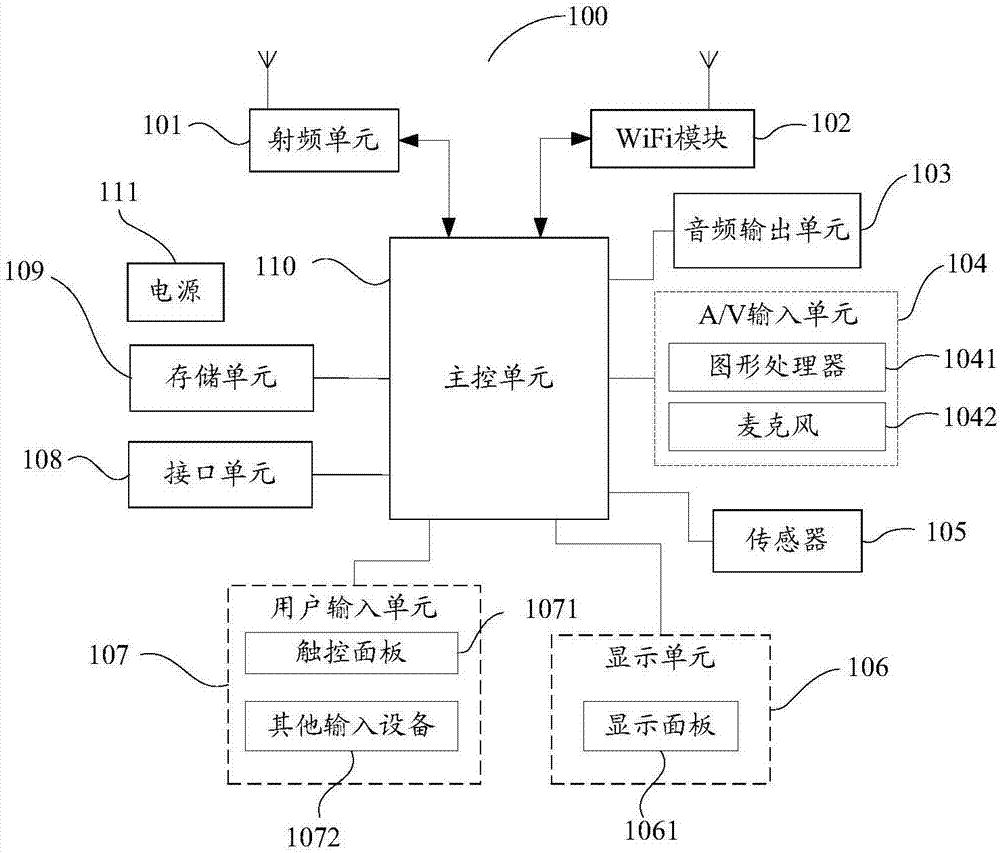
[0142] refer to Figure 7 , Figure 7The structural block diagram of the user behavior distance analysis terminal provided in Embodiment 3 of the present invention, the device provided in this embodiment includes: a processor 71, a memory 72, and a communication bus 73, wherein:
[0143] The communication bus 73 is used to realize the communication connection between the processor 71 and the memory 72;
[0144] The processor 71 is configured to execute the user behavior cluster analysis program stored in the memory 72, so as to realize the following steps:
[0145] Obtain user data of all users operating on the website, where each user data includes at least one user behavior operation;
[0146] Extracting at least one valid user behavior operation from the at least one user behavior operation to form a feature item set;
[0147] Converting feature item sets of all users into vector space model data, the vector space model data is a multi-dimensional data table;
[0148] C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com