Security protection method and system for widget application
A safe and secure technology, applied in the field of Internet applications, can solve problems such as user terminal interface security, user personal data security and network security risks, and achieve the effect of ensuring interface security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
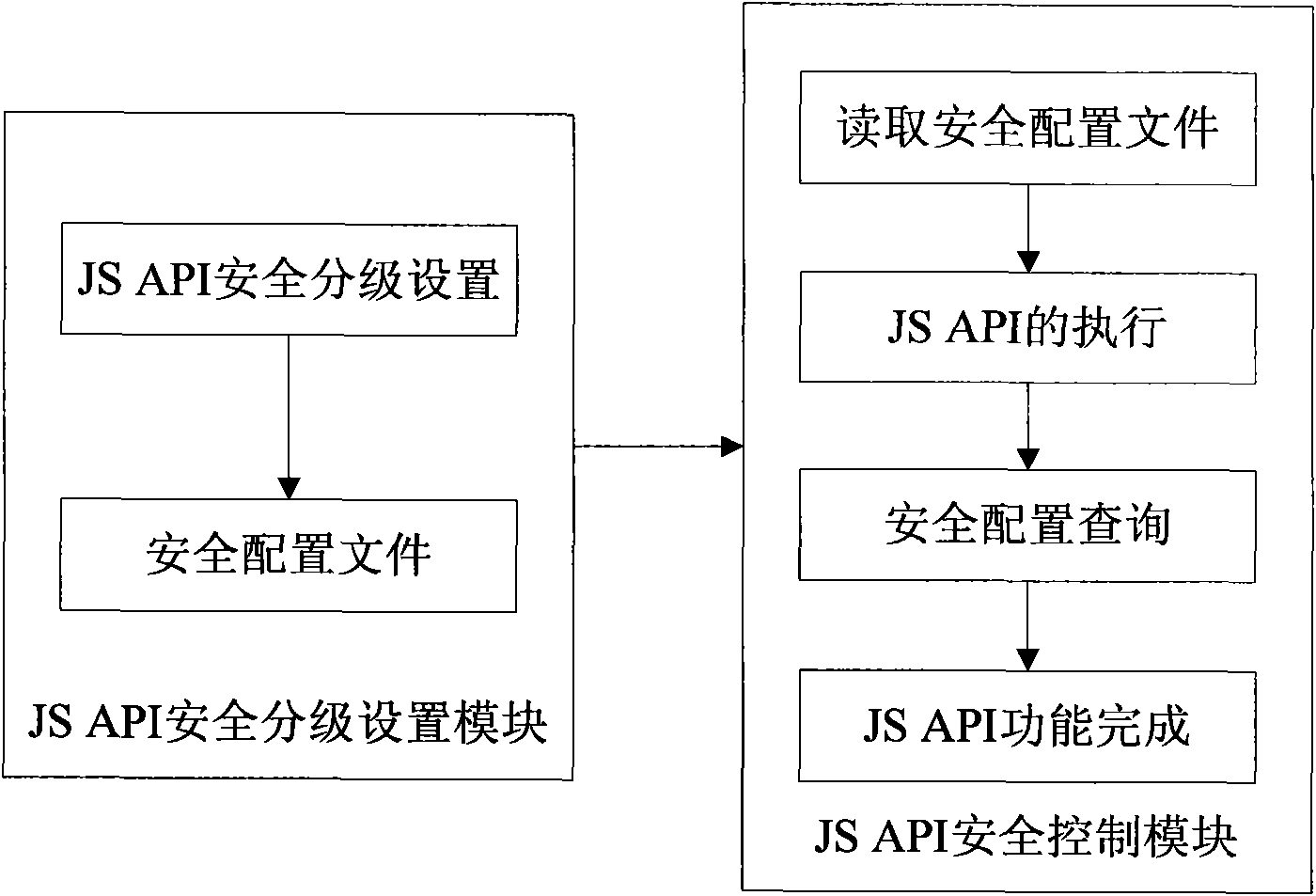
[0026] Follow the widget system framework defined by standards such as W3C, JIL and BONDI, and add a sub-system for security classification of JavaScript API to the widget engine under the framework defined by the standards. Such as figure 1 As shown, this subsystem contains JS API security classification setting module and JS API security control module, among which:
[0027] ●JS API security level setting sub-module, used to configure the security level of JS API, and save the configuration results in the security configuration file;
[0028] The configured security level can be: no trust, partial trust, and full trust. The specific meaning of each security level is as follows:
[0029] A. No trust: At this time, every JS API related to the terminal's local function is unavailable, that is, it is invalid to call the terminal's local function through the JS API in the widget application;
[0030] Part B trust: At this time, set whether the JS API related to the terminal local functi...
Embodiment 2
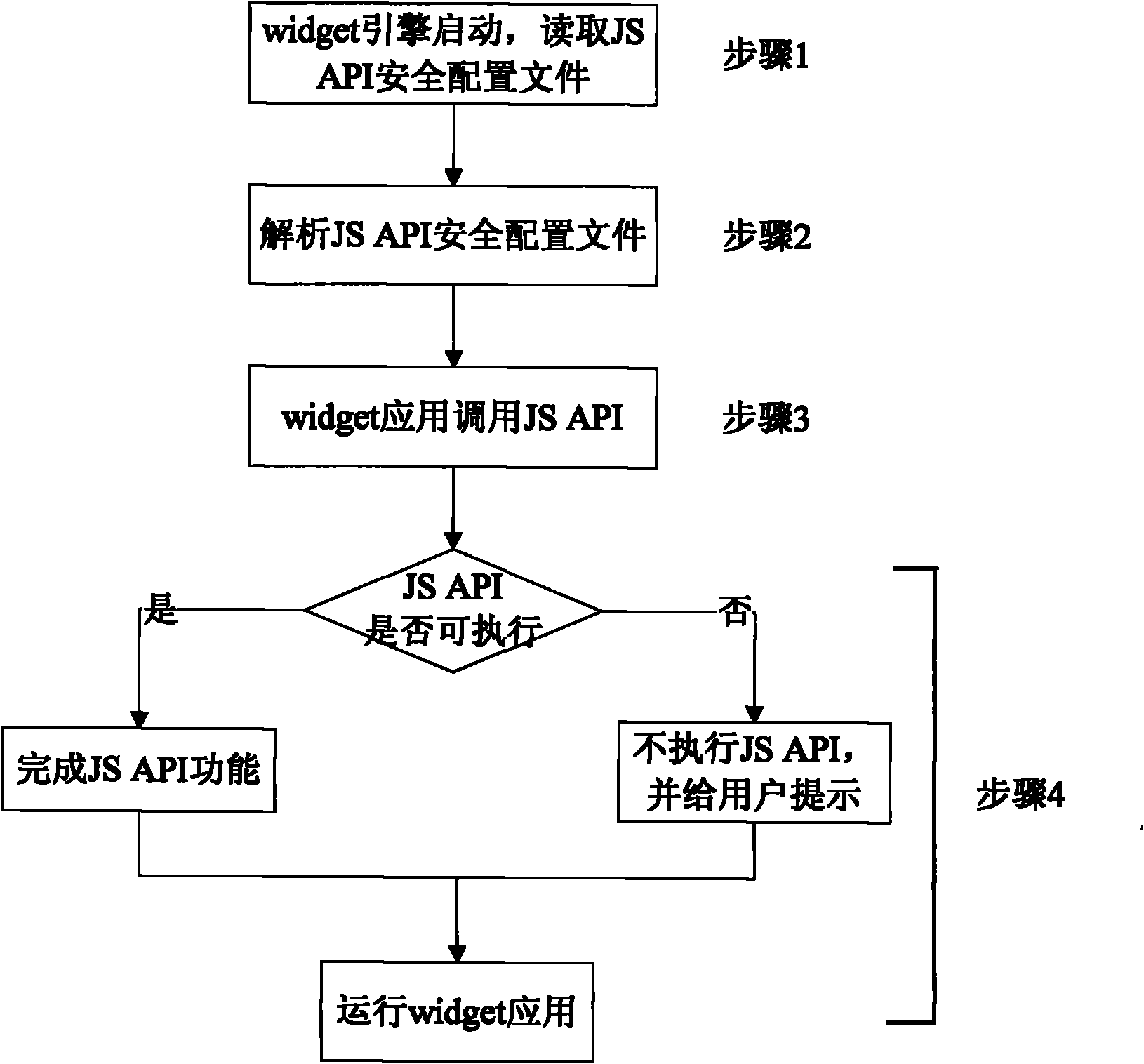
[0037] This embodiment introduces a security protection method for widget applications, including:
[0038] Step 1: Configure the security level of the JS API and save the configuration result in the security configuration file;
[0039] Step 2: Read the security configuration file when the widget engine starts. When the widget application calls the terminal local functions through the JS API, control the JS API according to the configuration in the security configuration file, that is, determine whether the JS API can call the terminal local Features.
[0040] The following is a step-by-step introduction.
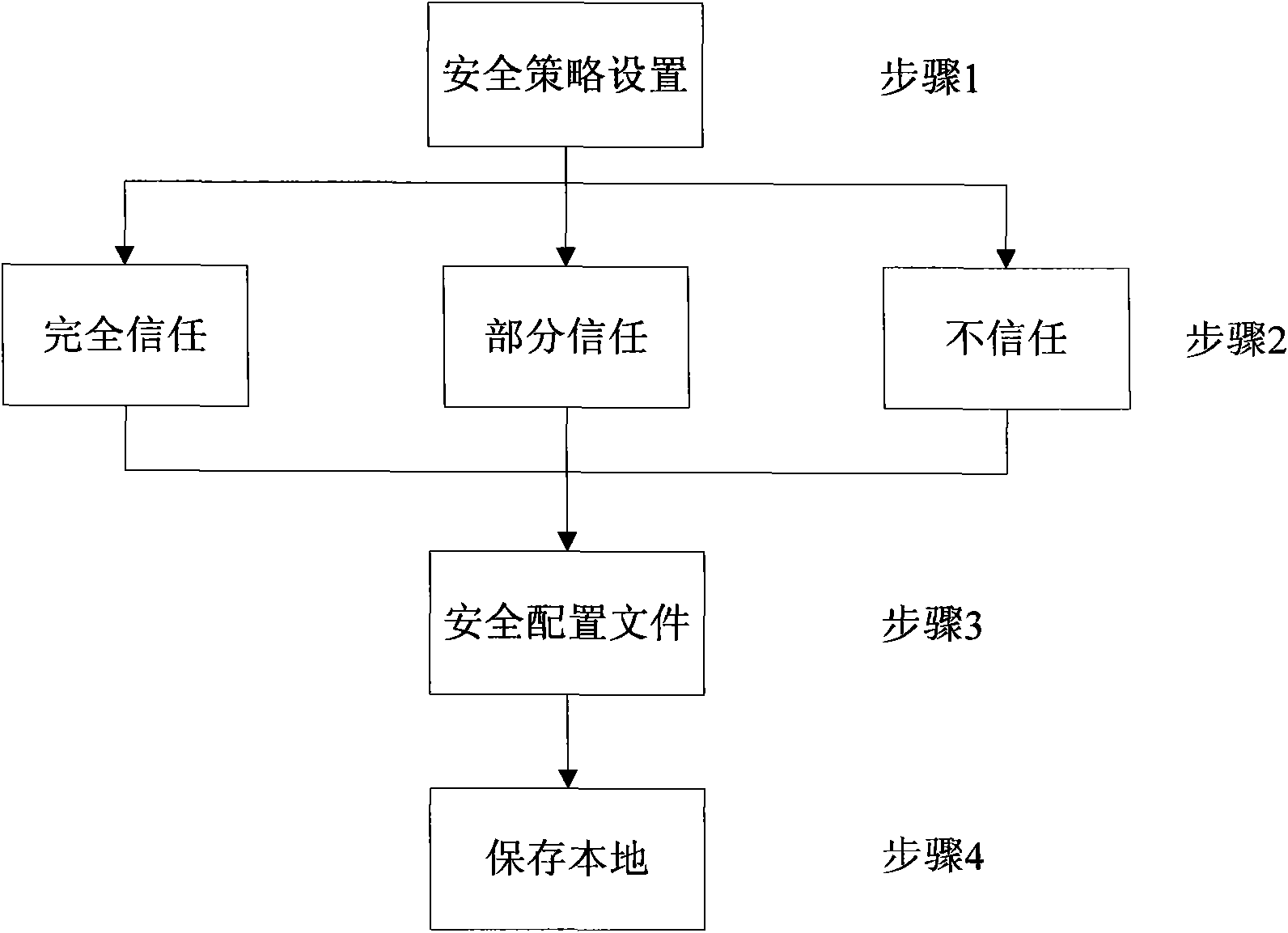
[0041] Such as figure 2 As shown, the above step one specifically includes the following steps:
[0042] Step 1: The user starts the security policy setting;
[0043] Step 2: The user sets the security level, and can set the JS API to be fully trusted or partially trusted or not trusted;
[0044] In this step, if the user chooses a fully trusted security level, all JS APIs that call...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com