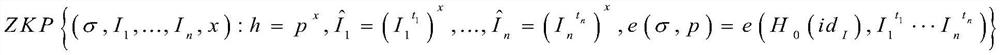Contact person tracking privacy protection method based on aggregation signature
A privacy protection and private key technology, applied in short-distance communication services, user identity/authority verification, security devices, etc., can solve the problems of slow authentication speed, large communication overhead and memory overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
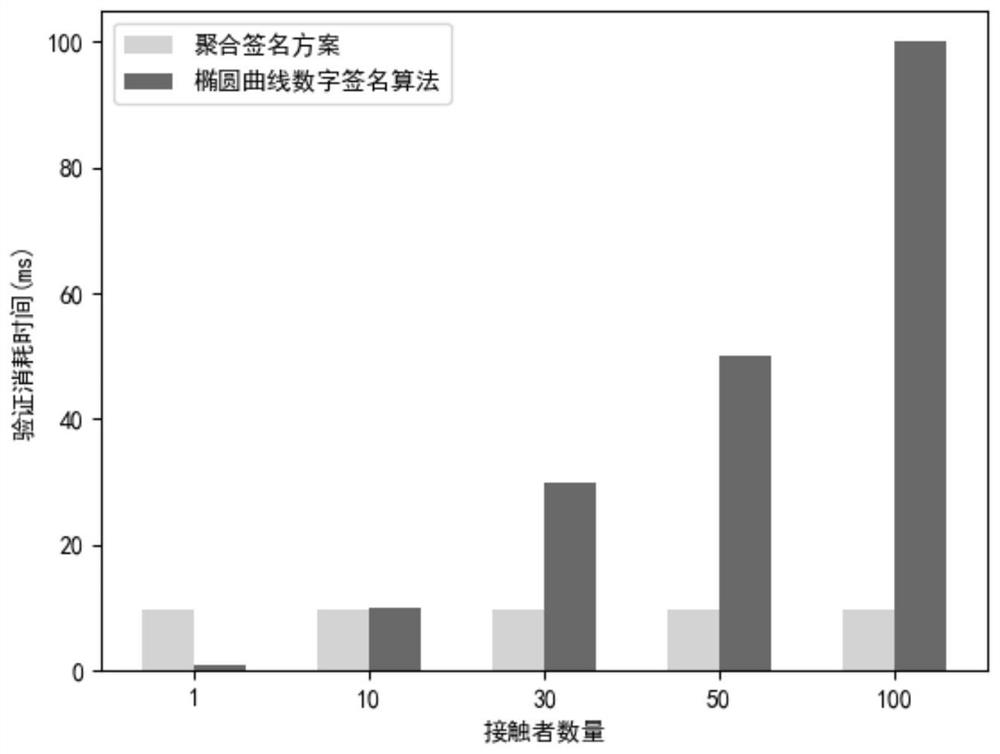
Problems solved by technology
Method used
Image
Examples
Embodiment
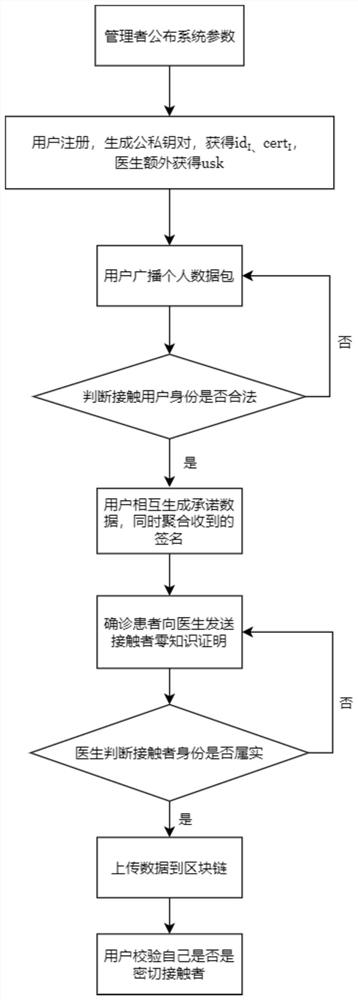
[0072] A method for privacy protection of contact tracing based on aggregated signatures, specifically implemented according to the following steps:
[0073] Step 1, user registration, specifically:
[0074] Step 1.1, the manager runs the key generation algorithm Gen to generate the manager’s public-private key pair (pk,sk)←Gen(λ), λ∈N is the security parameter, and announces the system parameters {λ,q,u,u at the same time 1 ,p,p 1 ,p 2 ,pk,H}, the parameters are initialized in the user's application program;
[0075] Step 1.2, the user registers with the manager and chooses his own private key i=sk I ∈ Z q , automatically calculate the public key The public key and personal information are uploaded to the manager, and the manager generates an anonymous personal id for each registered user I ∈ Z q and manager authentication cert I ←Sign(sk,pk I , time, id I ), the user will id I and cert I Save it locally on your phone. To protect user privacy, this must be done ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com