Controlled secure code authentication
A technology for code and secure storage, applied in the field of code authentication, which can solve problems such as lack of computing power, limited security boot security, and protection restrictions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0010] System Overview
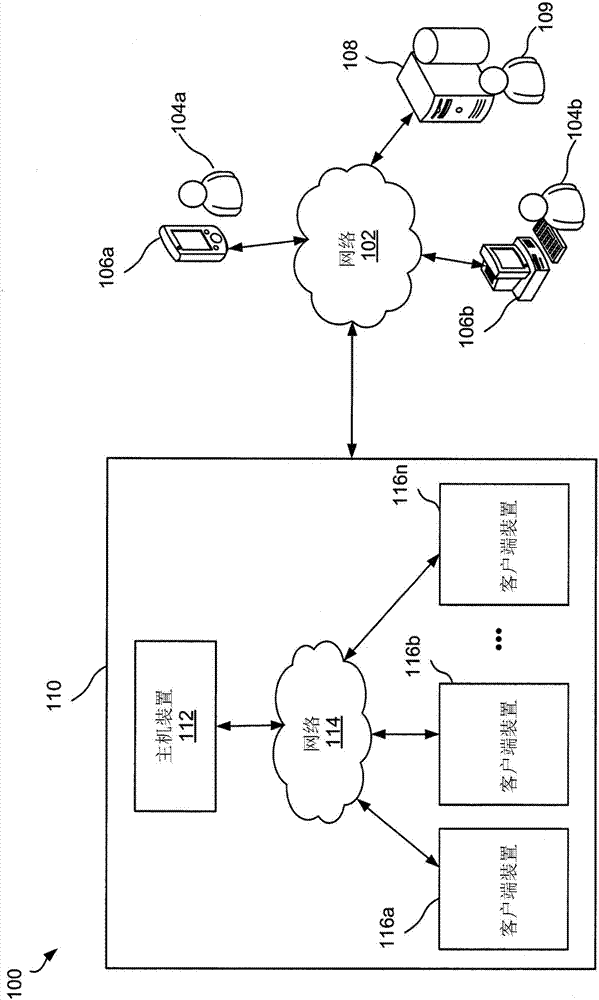
[0011] figure 1 is a block diagram of an example environment 100 according to an implementation. For purposes of illustration, environment 100 includes system 110 having host device 112 and "n" client devices 116a through 116n. Host device 112 communicates with client devices 116 a - 116 n over network 114 , which may be, for example, the local area network of system 110 . It should be noted, however, that the present technology is not limited to the implementation of a local area network; in fact, the network may be other than a local area network, for example, may be a wide area network or a controlled area network (CAN). Additionally, the network 114 may be a wired network, a wireless network, or any combination thereof. The host device 112 is configured to confirm whether the code or program stored in the client device is authorized (or authenticated) code for execution by the client devices 116a-116n. The code of the client device includes at ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com