Cross-domain identity authentication method based on block chain certificate
A technology of identity authentication and authentication method, which is applied in the direction of user identity/authority verification, digital transmission system, electrical components, etc., can solve the problems of inconvenient use, achieve the effects of ensuring security, improving identity authentication efficiency, and reducing communication overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
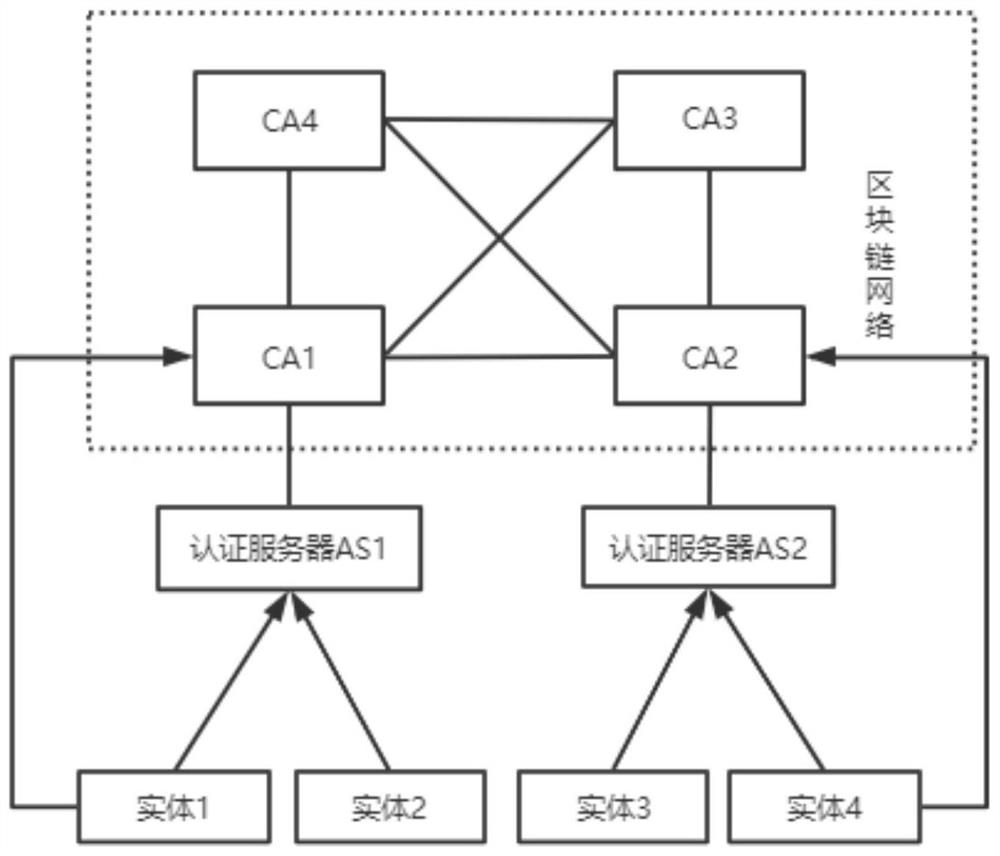
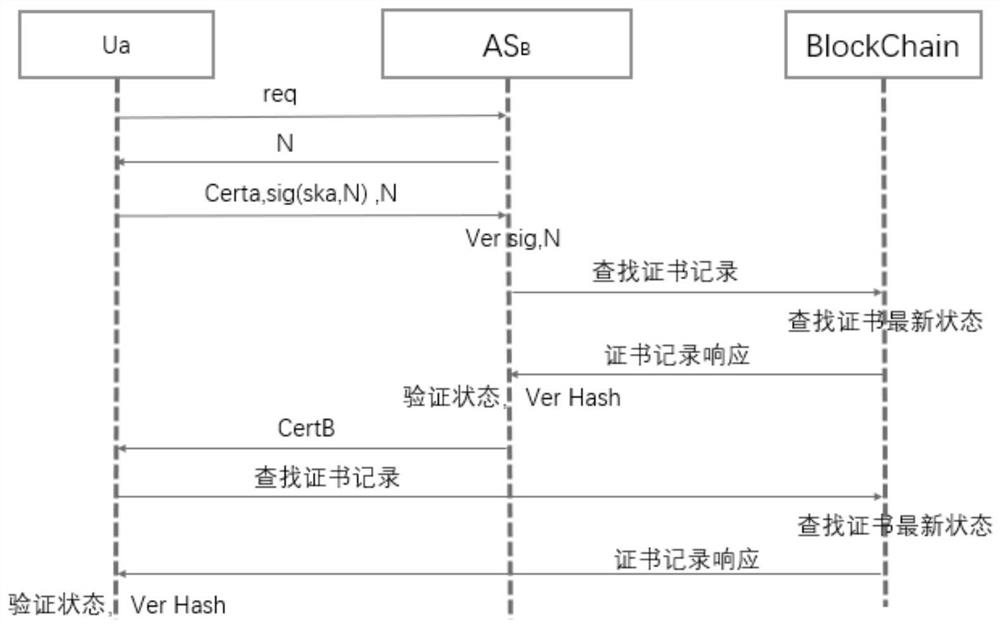
[0048] 1) Design of blockchain certificate:
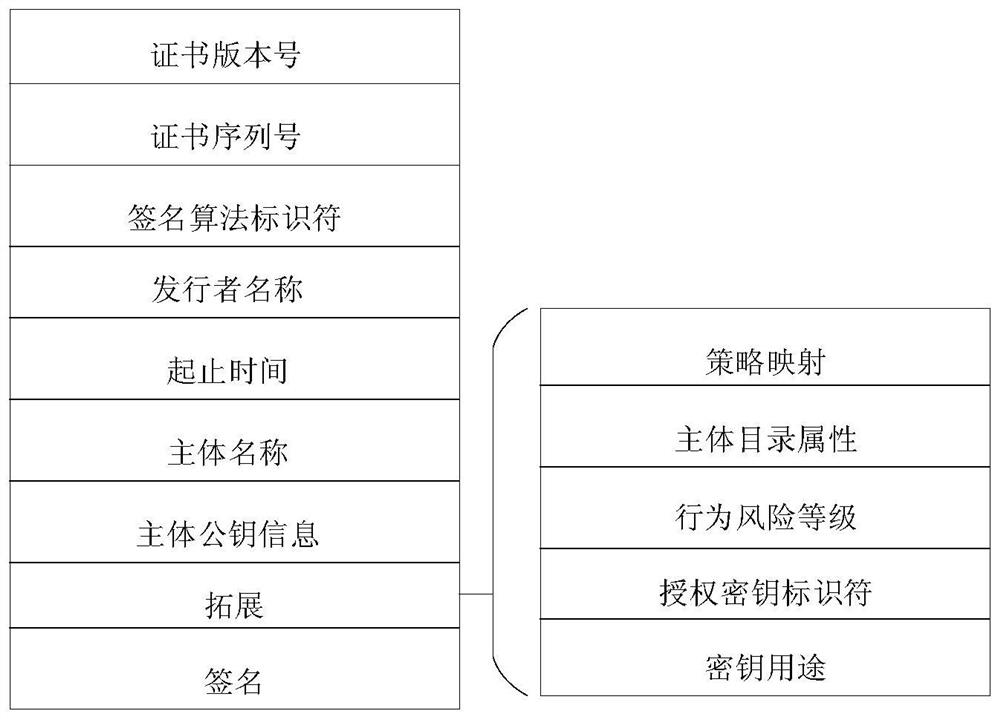
[0049] The traditional PKI-based identity authentication process is realized through digital certificates, and the most common version of digital certificates is the X.509v3 version, which is characterized by strong stability, not easy to tamper, and has high safety.
[0050] In the X509v3 version of the digital certificate, there are several parts that need to be explained: Issuer Unique Identifier and Subject Unique Identifier are optional, and they are only available in X.509v3 and X. There are requirements in 509v2; the signature (Signature) is mainly used to prove the correctness of the public key contained in the certificate. Generally, the issuer of the certificate uses its private key to sign according to the agreed signature algorithm. In the extended part, the policy mapping generally only appears in the CA certificate, which contains the equivalence relationship between multiple policies in different domains; the CRL di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com