Power distribution terminal authentication method, system and device, computer equipment and storage medium
A power distribution terminal and authentication method technology, which is applied in the field of power grids, can solve the problems of invalid authentication system, long time consumption, and low efficiency of power distribution terminal identity authentication, so as to improve the efficiency of identity authentication, increase the speed of authentication, and prevent authentication systems. The effect of aging
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application.
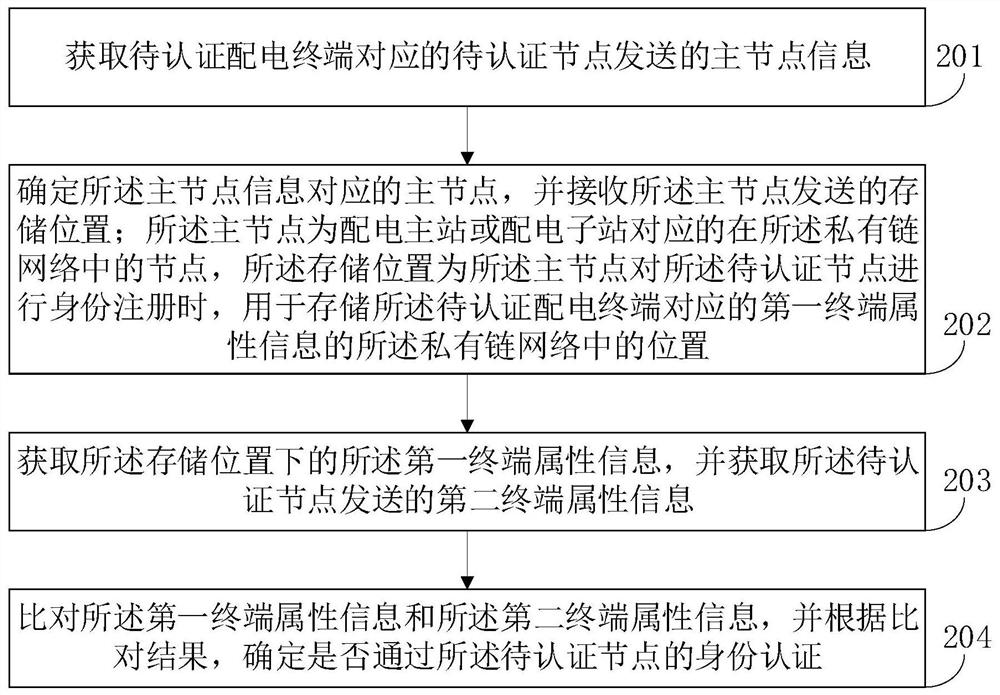
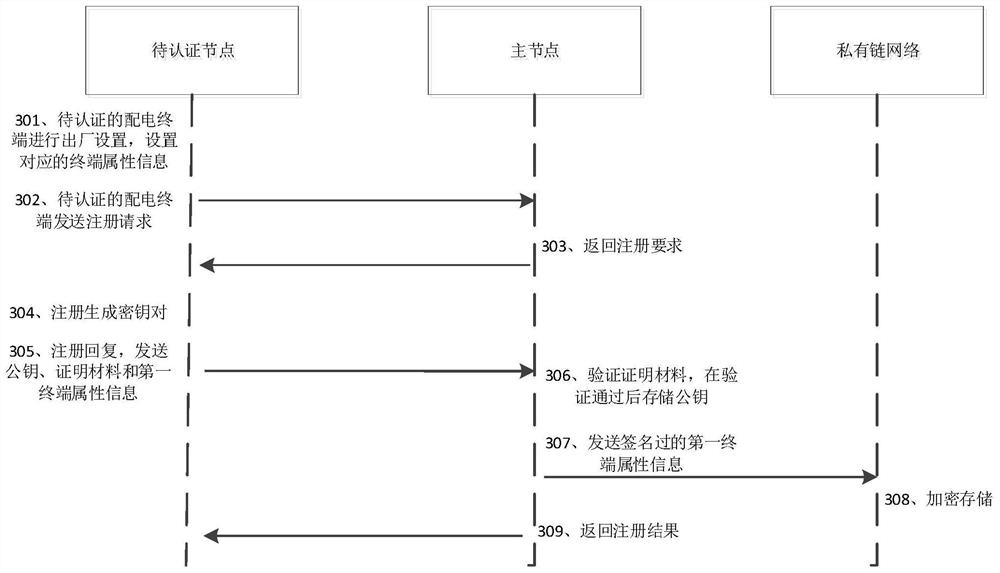
[0046] With the development of power grid technology and the continuous advancement of distribution automation construction, the number of power distribution terminals put into operation has exploded, and the covered area has expanded rapidly. brought hidden dangers.
[0047]Specifically, power distribution terminals can be connected to the master station of power distribution automation through optical fiber or wireless networks. Due to the wide distribution characteristics, attackers can maliciously destroy and attack the main station of distribution automation through ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com