Lightweight certificateless authentication method, client and system
An authentication method and a certificate-free technology, applied in the field of information security, can solve problems such as high algorithm complexity, heavy storage space and transmission bandwidth, and difficult implementation, and achieve the effect of low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
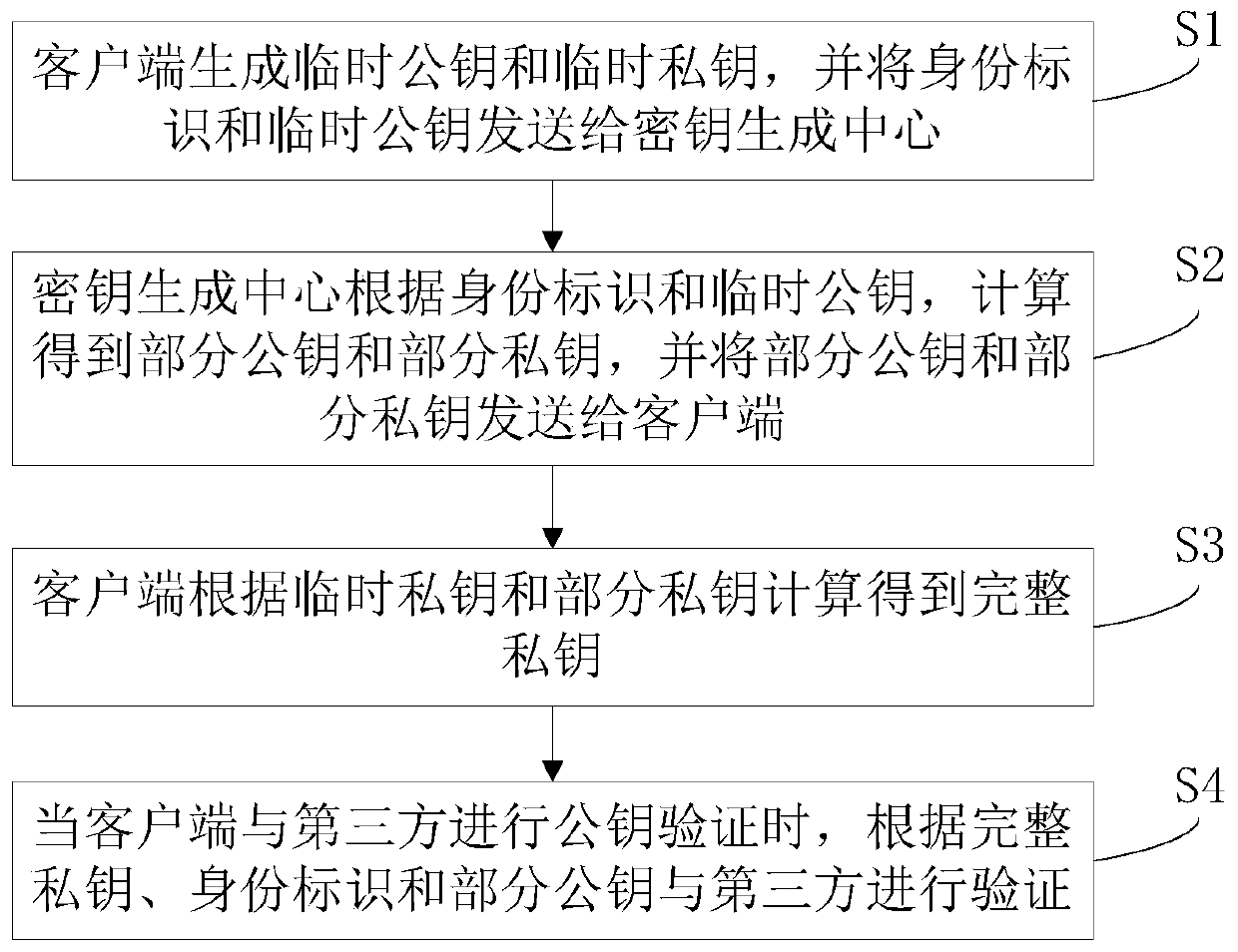
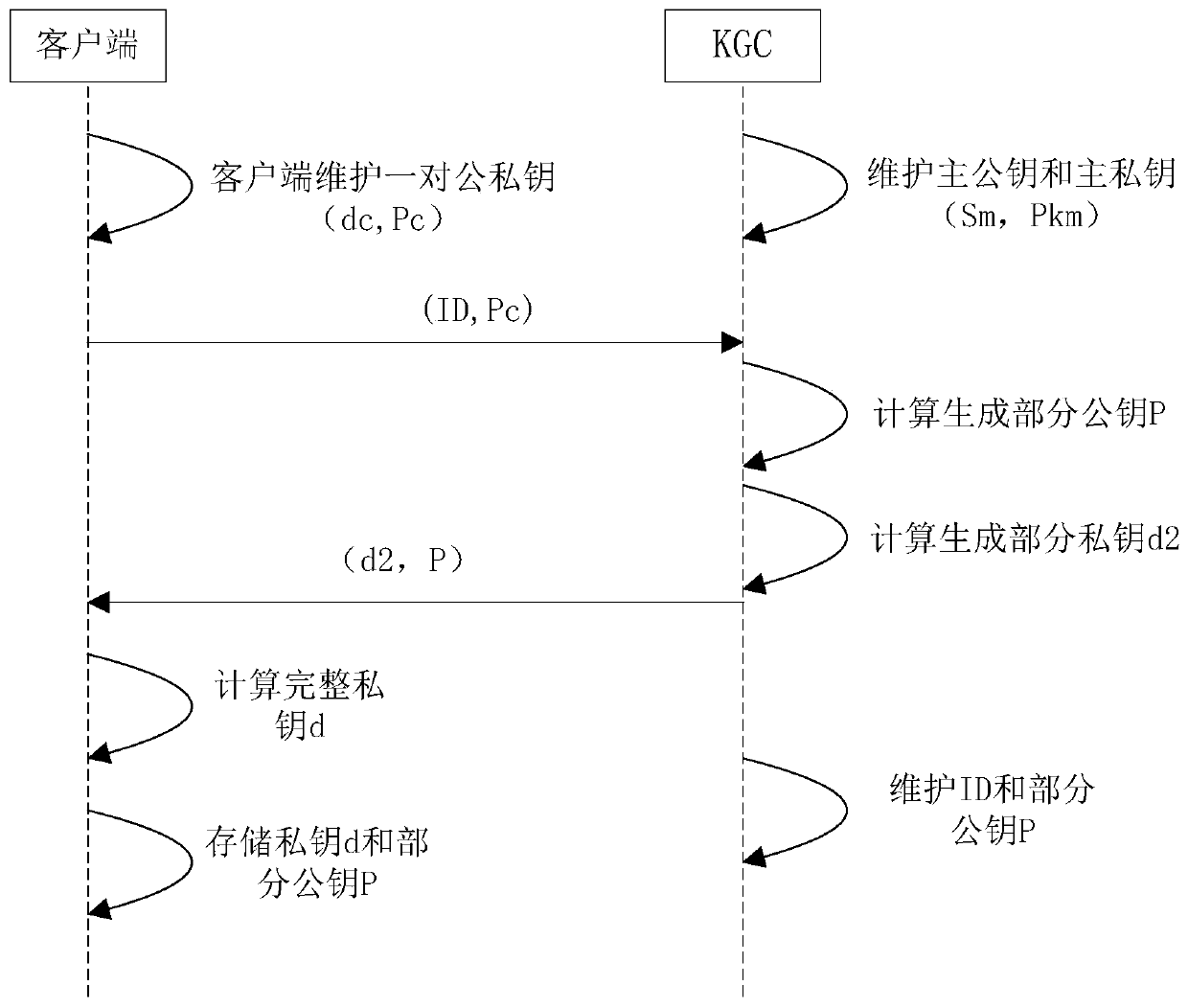
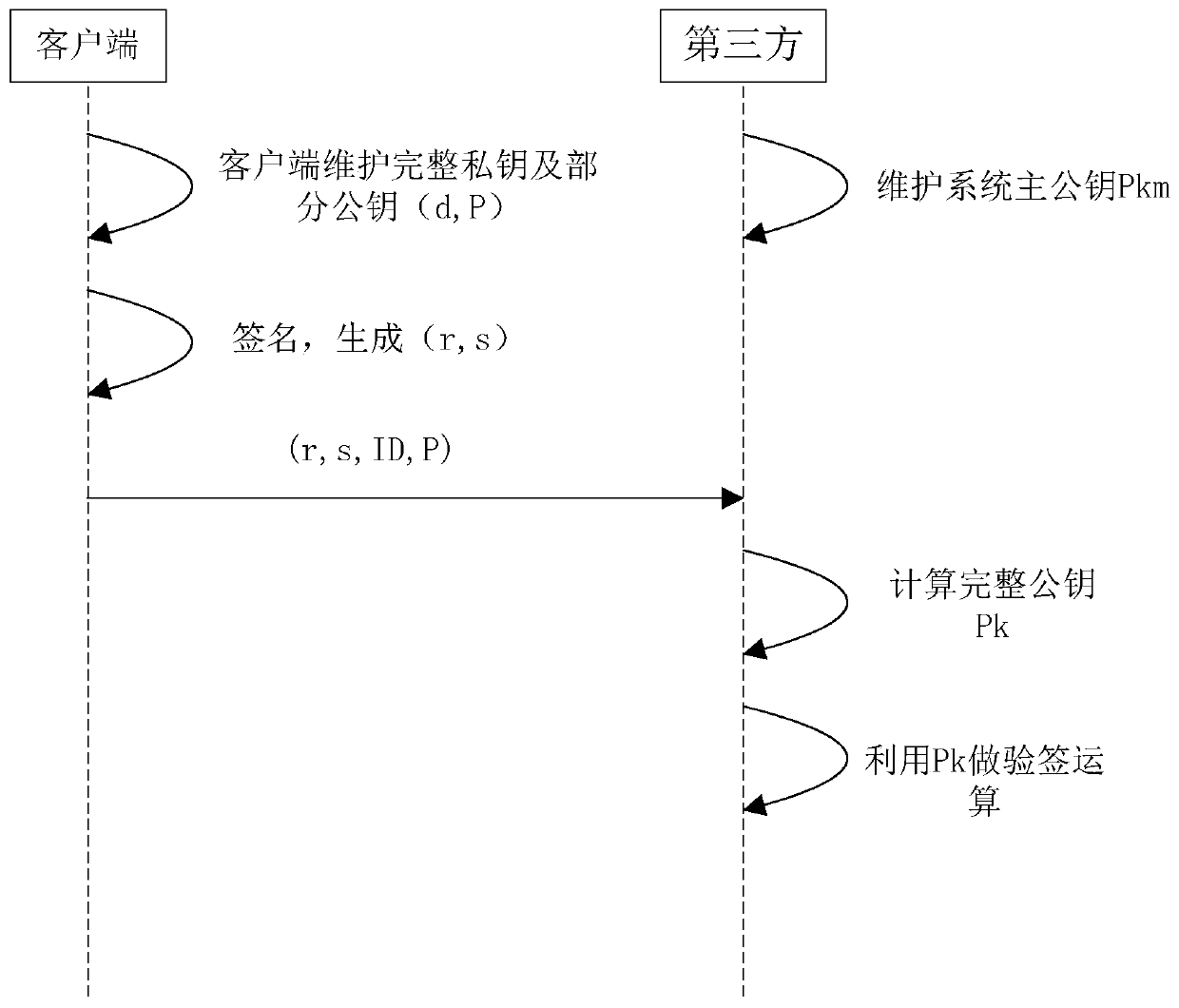
[0030] The principles and features of the present invention will be described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0031] With the rapid development of the Internet of Things, the security issues of the Internet of Things have received more and more attention. The Internet of Things terminal device is the weakest link in the entire Internet of Things security, which brings security risks to all devices connected to the Internet of Things. Therefore, strengthening the security level of IoT terminal equipment has become an urgent problem to be solved in the current development of IoT. However, the bandwidth of the Internet of Things environment is generally low. Therefore, in the current authentication algorithm, the SM2 authentication that needs to use digital certificate parameters and the SM9 authentication with complex alg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com