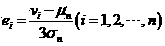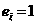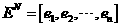Trojan horse detection method based on communication behavior clustering
A detection method and clustering technology, applied in the field of information security, can solve the problems of improper selection of feature clustering algorithm, unsatisfactory detection effect, and inability to detect TCP sessions in real time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with accompanying drawing.
[0035] according to figure 1 Organize the process of the embodiment step by step, and divide the embodiment into several modules, such as figure 2 shown. The embodiment includes a TCP session reorganization module, an abnormal feature extraction module, a communication behavior feature vector generation module, a Gaussian normalization module, an LSH-based real-time incremental clustering module and a TCP session discrimination module.
[0036] Among them, the TCP session reorganization module is used to capture network traffic data packets, and perform TCP session reorganization on it, so as to facilitate the subsequent acquisition of TCP session information; the abnormal feature extraction module performs statistics on the data flow of the TCP session according to the characteristics of the Trojan horse communication behavior Analysis; the communication behavior featu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com