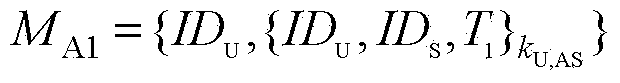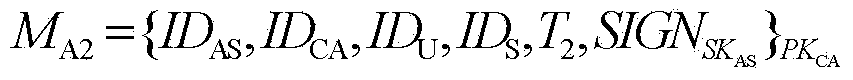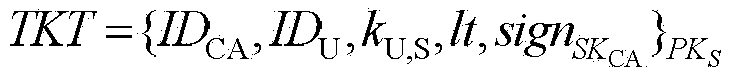Method for cross-isomerism domain identity authentication and session key negotiation based on access authorization ticket
A session key and domain identity technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of Kerberos domain user difficulty, large communication volume, low efficiency, etc., to reduce computational complexity, guarantee safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0123] A cross-heterogeneous domain identity authentication and session key negotiation method based on access authorization tickets, the steps of which include: first, the certification center CA in the PKI (public key infrastructure) domain and the Kerberos (private key authentication system) domain The authentication server AS performs interactive authentication through public key certificates; then, users in the Kerberos domain and resources in the PKI domain perform interactive authentication and session key negotiation through access authorization tickets.
[0124] In this example, users in the Kerberos domain and resources in the PKI domain perform mutual authentication and session key negotiation through access authorization tickets as follows:
[0125] A1. Access Authorization Ticket Request
[0126] The user in the Kerberos domain submits an authentication request for cross-domain resource access to the authentication server AS, and the authentication server AS authe...
Embodiment 2
[0171] A cross-heterogeneous domain identity authentication and session key negotiation method based on access authorization tickets, the steps of which include: first, the certification center CA in the PKI (public key infrastructure) domain and the Kerberos (private key authentication system) domain The authentication server AS performs interactive authentication through the public key certificate; then, users in the PKI domain and resources in the Kerberos domain perform interactive authentication and session key negotiation through access authorization tickets; it is characterized in that:
[0172] In this example, users in the PKI domain and resources in the Kerberos domain perform interactive authentication through access authorization tickets:
[0173] B1. Note granting note request
[0174] Users in the PKI domain submit a request for cross-domain access to resources to the certification center CA. After authenticating the identity of the user in the PKI domain, the ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com