Parent-child card authentication system
An authentication system, mother-child technology, applied in user identity/authority verification, key distribution, can solve problems such as no consideration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0073] (Embodiment 1 (mainly explain claims 1 and 10))
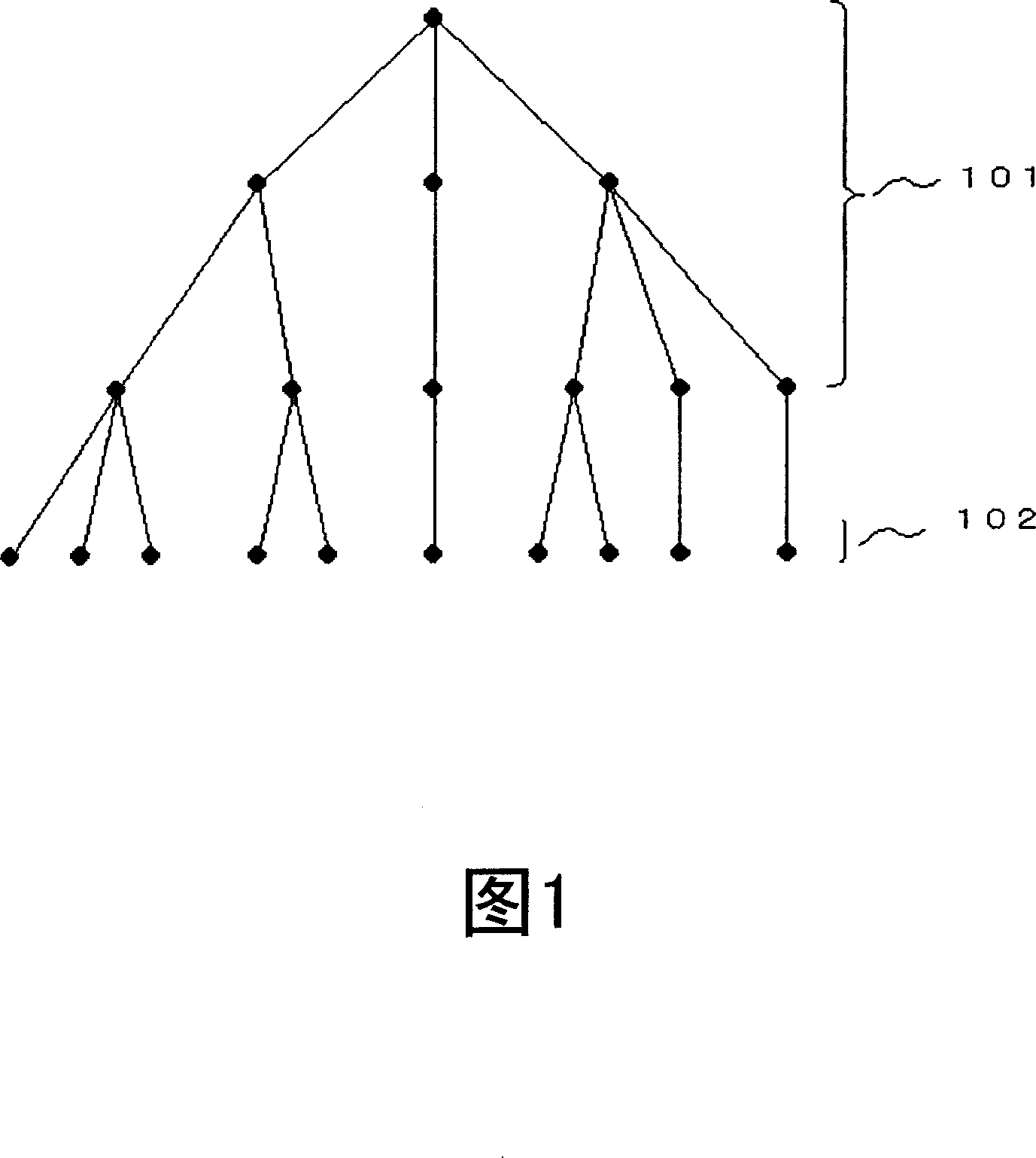
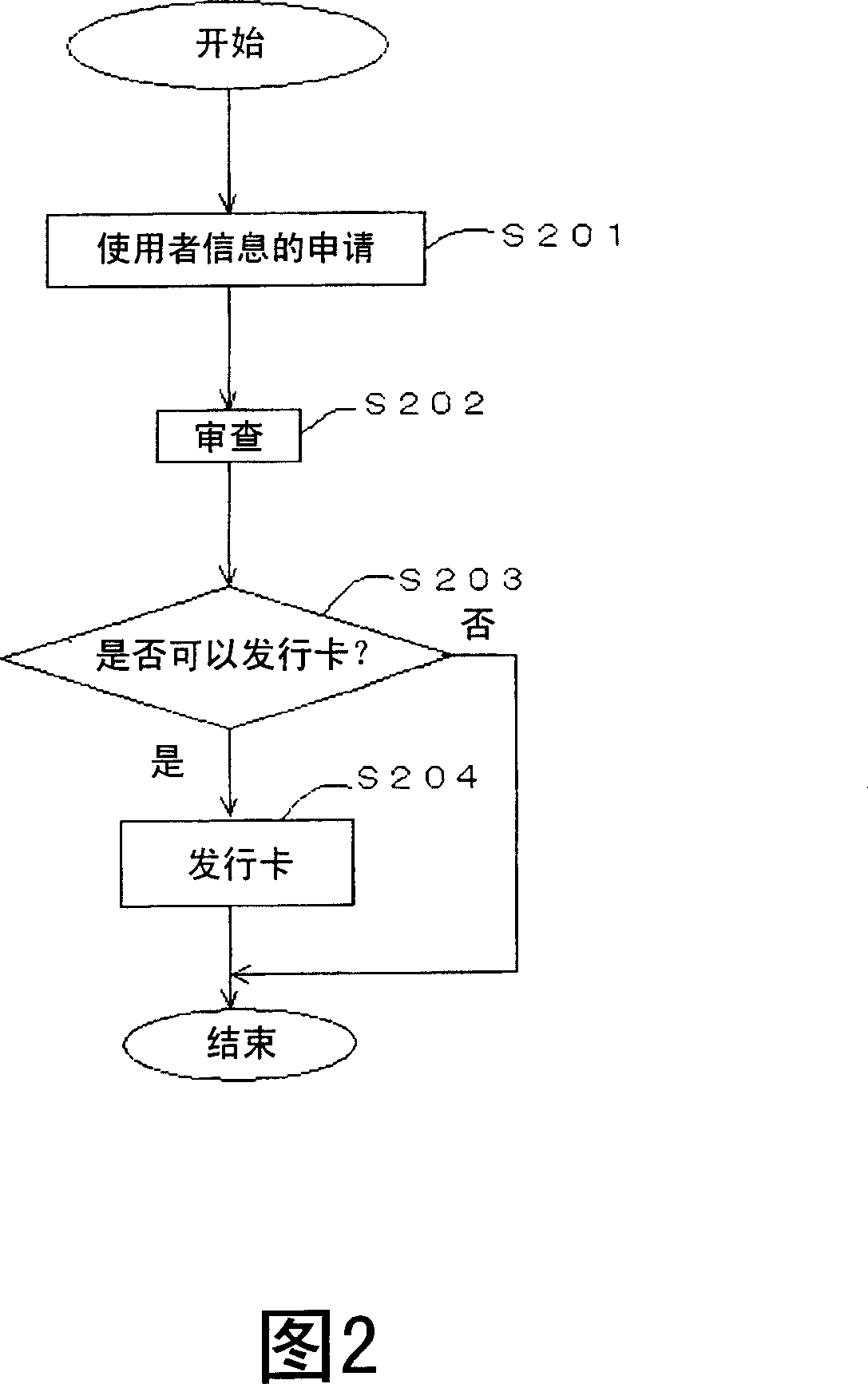
[0074] As the first embodiment, a parent-child card authentication system that uses the first-generation card certified by the root certification authority as the original card and inherits its authentication from generation to generation to generate descendant cards will be described.
[0075] FIG. 6 is a conceptual diagram of the parent-child card authentication system in Embodiment 1. FIG. The upper part of Fig. 6 depicts the classification of certification authorities. These accreditation bodies have the relationship that the accreditation body located above certifies the accreditation body directly below it. The root certification authority may also be the certification authority located at the root of FIG. 6 . Alternatively, it could be the Certification Authority directly above the Generation 1 card. When the root certification authority is located at the root of Figure 6, the first generation card certified by...
Embodiment approach 2
[0100] (Embodiment 2 (mainly explain claim 2))
[0101] The parent-child card authentication system in which the N+1th generation card existence proof information includes information uniquely identifying the N+1th generation card as Embodiment 2 will be described.
[0102] (Embodiment 2: Structure)
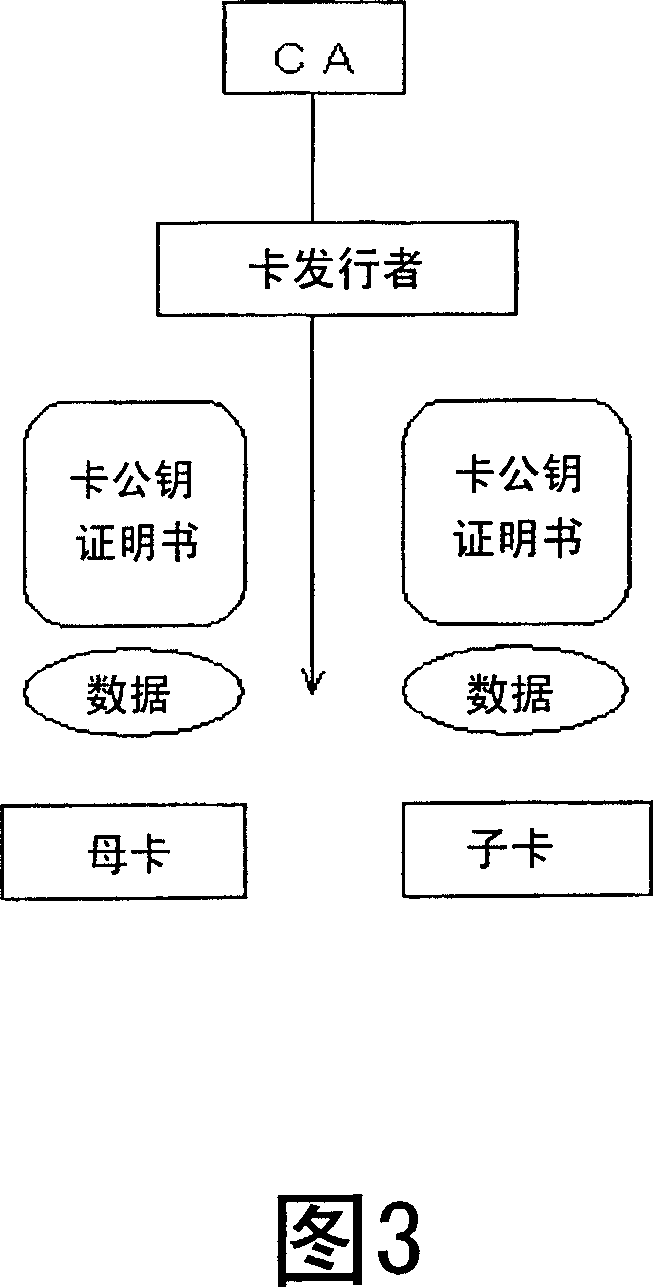
[0103] Embodiment 2 is a form in which in the mother-child card authentication system of Embodiment 1, self-identification information as information for uniquely identifying the N+1th generation card is included in the N+1th generation card existence proof information. "Unique identification" means to uniquely designate the N+1th generation card.
[0104] As an example of including self-identification information, the value stored as the target in FIG. 8 is a value obtained by combining the name or logo of the N+1th generation card manufacturer with the manufacturer's manufacturing number. Alternatively, such a value may be replaced with the name or the like of the N+1th gener...
Embodiment approach 3
[0107] (Embodiment 3 (mainly explain claim 3))
[0108] A parent-child card authentication system in which the N+1th generation card existence proof information of the third embodiment includes information uniquely identifying the Nth generation card will be described.
[0109] (Embodiment 3: Structure)
[0110] Embodiment 3 is a form in which in the mother-child card authentication system of Embodiment 1 or 2, the N+1th generation card existence proof information includes the mother card identification information as information for uniquely identifying the Nth generation card. "Unique identification" means to uniquely designate the Nth generation card.
[0111] As an example of including the master card identification information, the value stored as the issuer in FIG. 8 is a value obtained by combining the name or logo of the Nth generation card manufacturer with the manufacturer's serial number. Alternatively, such a value may be replaced with the name of the Nth generat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com