Without-trust third party public key authentication method based on speaker voice print
An authentication method and public key technology, applied in the field of network security, can solve the problem of difficult implementation of public key cryptosystem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described below in conjunction with accompanying drawing.
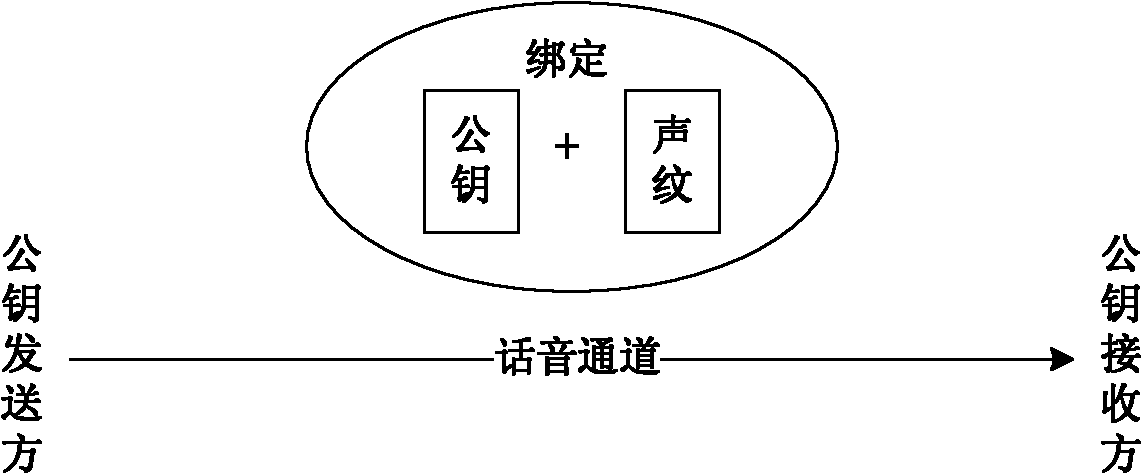
[0018] An important problem that needs to be solved when transferring public keys in a network environment is how to make the recipient of the public key confirm the correspondence between the public key and the private key user who owns the public key. In the present invention, the confirmation of this corresponding relationship is by binding the public key with the unique biometric characteristics contained in the speaker's voice, thereby confirming that the public key is sent by the speaker, that is, confirming that the public key and the owner For the correspondence between the private key users of this public key, see figure 1 . The non-trusted third-party public key authentication method based on the speaker's voiceprint in the present invention follows the steps below:
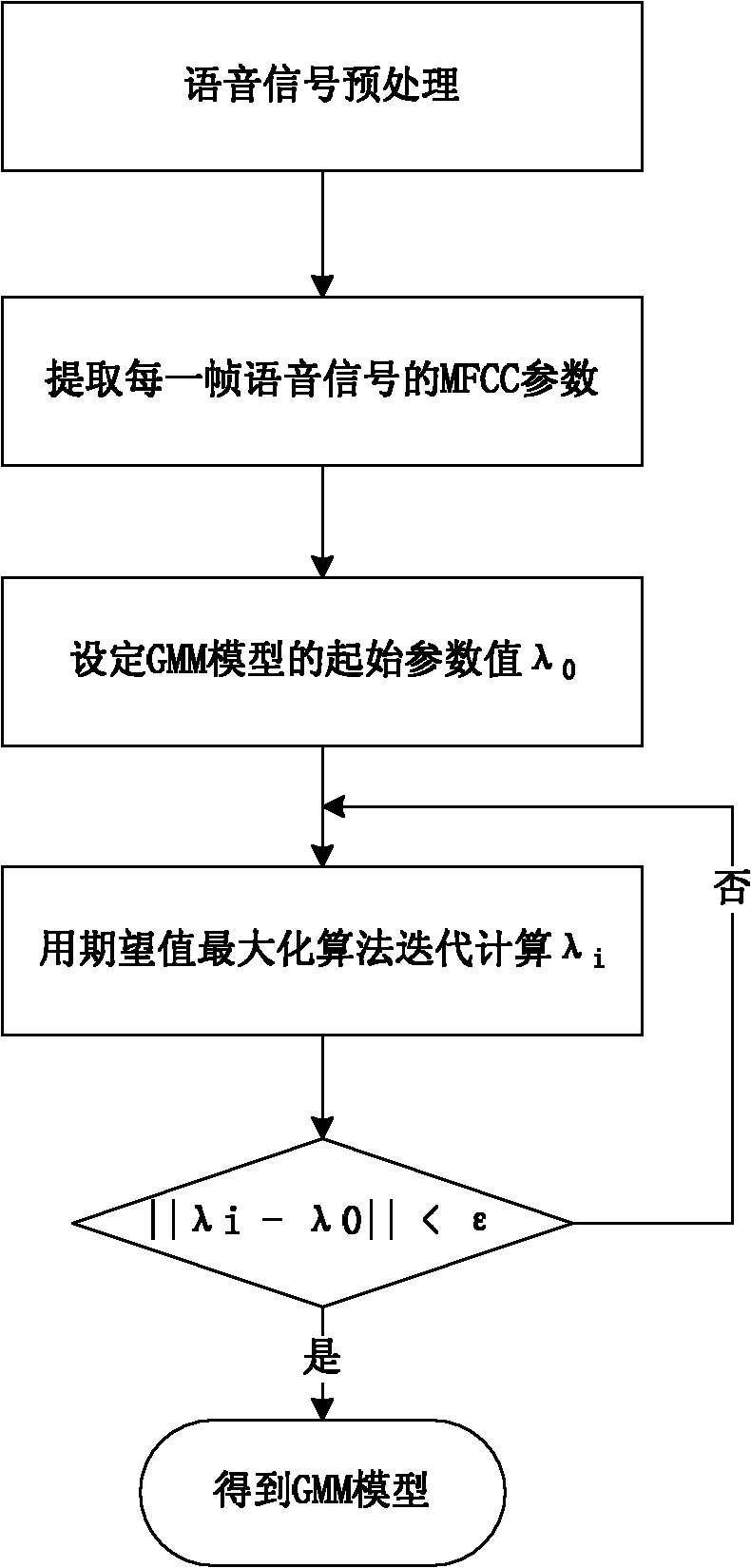
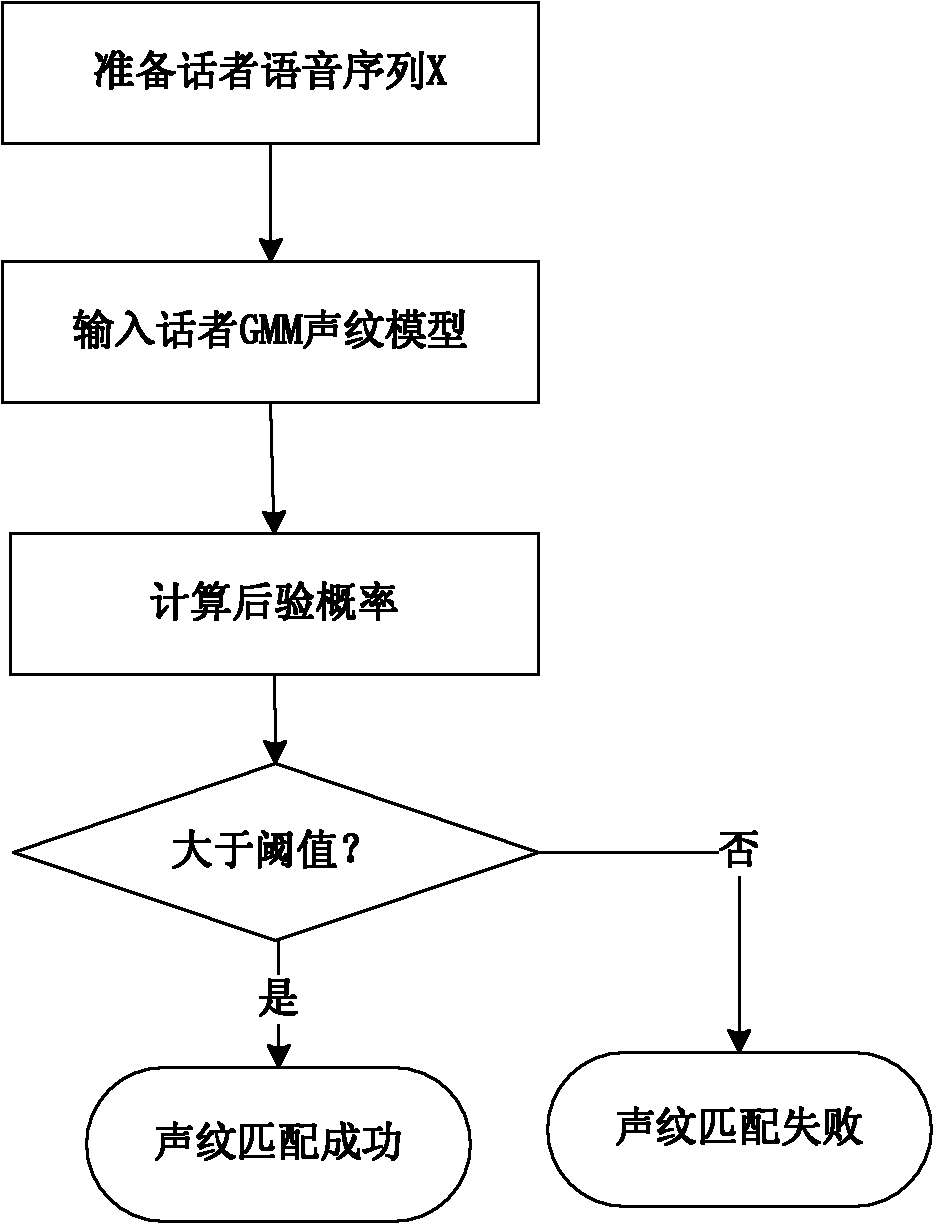
[0019] In the first step, the communication parties determine the voice channel and require dig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com