Wireless security access authentication method
An access authentication and wireless security technology, applied in security devices, wireless communication, wireless network protocols, etc., can solve the problems of attack authentication overhead, public key certificate authentication system denial of service attack domino effect, etc., to reduce authentication overhead, The effect of maintaining the security of public key authentication and eliminating the cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
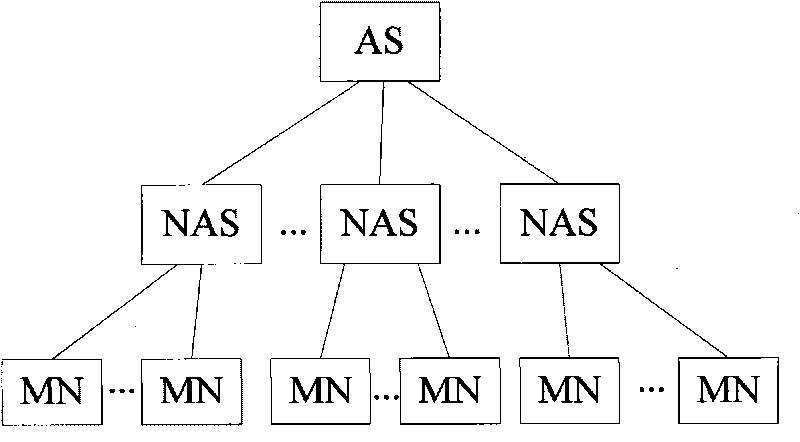
[0030] The inventive method comprises an EBAF initialization protocol, an EBAF authentication protocol and an optional EBAF revocation protocol, wherein: an elliptic curve is generated in the EBAF initialization protocol, the key of the resource owner is generated and the key of the terminal is distributed; in the EBAF authentication protocol In EBAF, the authenticating parties use their own Diffie-Hellman key pair to authenticate each other's messages; in the EBAF revocation protocol, the group administrator generates a new key pair, and the terminals that cannot pass the key pair authentication will be revoked.
[0031] The detailed steps of the present invention are as follows:
[0032] (1) EBAF initialization protocol
[0033] AS initializes the parameters of the EBAF field, in the finite field F p Generate an elliptic curve T in which there is a field base point G and a prime order n, and then AS generates the first and second random numbers M nas and M mn ,M nas and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com