Fragmentation-based content authentication method
An authentication method and content technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as low authentication efficiency, not supporting media content fragmentation authentication, etc., to reduce authentication overhead and improve response speed. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
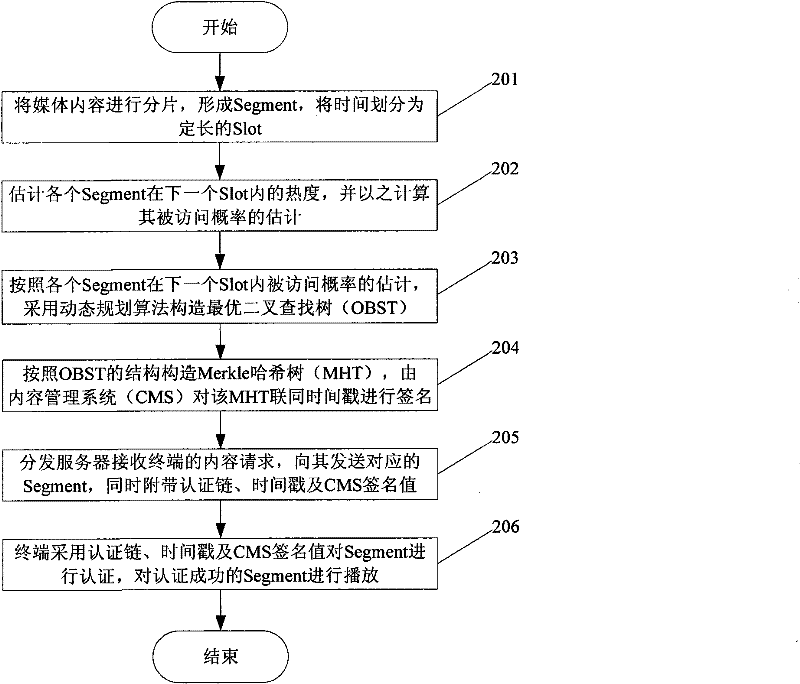
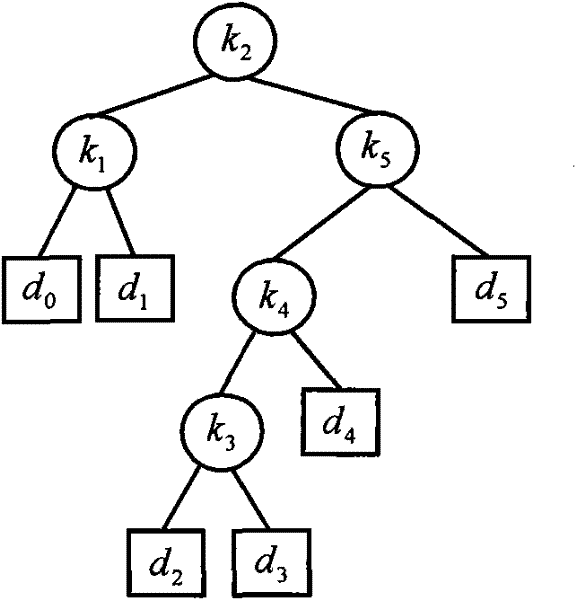
[0032] The present invention will be further described below in conjunction with accompanying drawing:
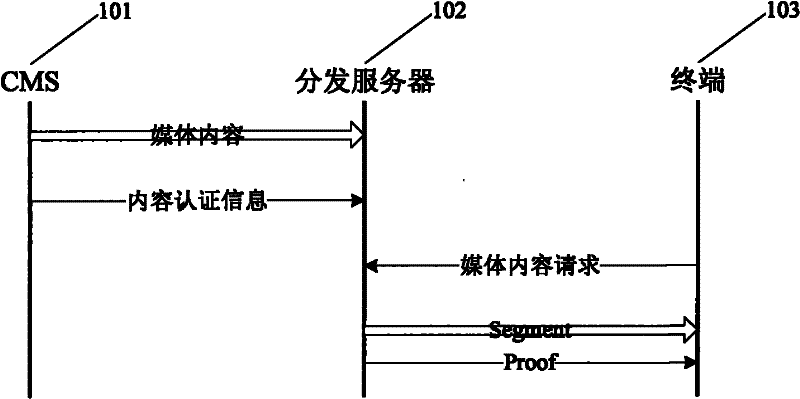
[0033] figure 1 It is the content authentication entity model diagram of the content service system, including the following three entities:
[0034] Content management system CMS 101: source of media content, CMS pushes media content to distribution server, and provides content authentication information at the same time. The CMS is trusted to the terminal.
[0035] Distribution server 102: an untrusted storage server, distributed and deployed at the edge of the network, to store media content from the CMS. In response to the media content request from the terminal, the distribution server provides the media content and the corresponding "Proof", which is used for the terminal to authenticate the media content.
[0036] Terminal 103: the consumer of the media content, applies for the media content from the distribution server, and after obtaining the media content and "...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com