Non-contact processor card based on combined public key authentication and use method
A combined public key, non-contact technology, applied in the direction of digital data authentication, user identity/authority verification, digital transmission system, etc. The effect of the ability to attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
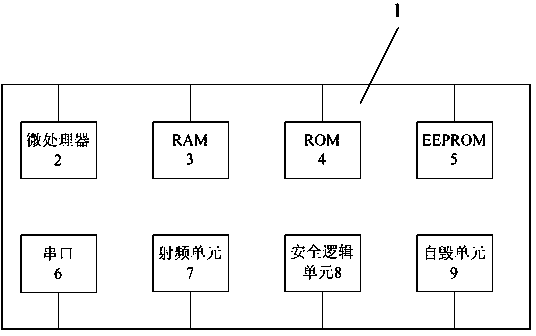
Image
Examples
Embodiment 1
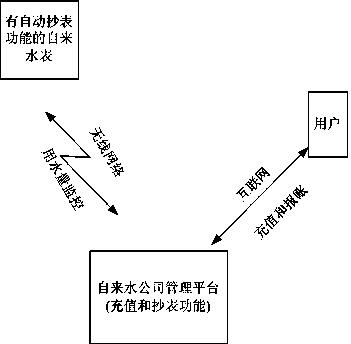
[0073] figure 2 It is a flow chart of the present invention applied to a tap water meter with an automatic meter reading function.
[0074] like figure 2 As shown, the CPU card based on combined public key identification proposed by this patent invention is built in the water meter with automatic meter reading function, which can uniquely identify the automatic water meter, and has encryption and decryption functions. Because the information is encrypted, It is impossible to modify and decipher these water consumption information, so as to prevent water stealing; at the same time, users can obtain water consumption in real time through the Internet and recharge in real time. The specific steps are as follows:
[0075] Step 1: The user recharges the water fee through the Internet;
[0076] Step 2: After obtaining the recharge fee, the management platform of the water company notifies the built-in CPU card based on combined public key identification through the wireless netw...
Embodiment 2
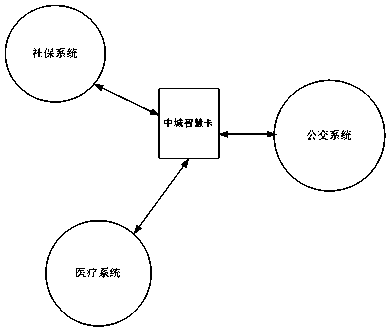
[0081] image 3 It is a flowchart of the application of the present invention on the Midtown Smart Card, such as image 3 , the Midtown smart card adopts the CPU card based on combined public key identification proposed by the present invention, through the new and old card number mapping and the new and old card key conversion, to realize the interaction and connection of information. The social security card, medical insurance card, and bus card in the figure are shown as For example, multiple cards in one are realized.
[0082] The current traditional method is that different departments issue different cards, such as social security cards, medical insurance cards, bus cards, etc., which are troublesome to carry, inconvenient to use, and easy to lose. In case of loss, you need to go to different departments to report the loss. The original intention of issuing cards has not been achieved.
[0083] The available resources of the present invention are very huge, and the sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com