Printing security monitoring and auditing system based on virtual printing technique
A technology of virtual printing and security monitoring, which is applied in the direction of transmission system, digital output to printing unit, electrical components, etc. It can solve the problems of printing behavior and difficult monitoring of content, so as to provide traceability, prevent malicious tampering, and solve the problem that cannot be prevented The effect of unauthorized printing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
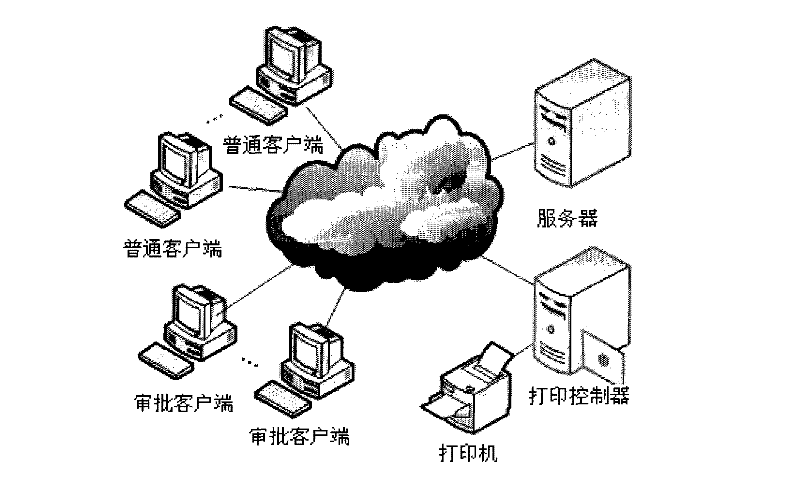
[0019] Such as figure 1 As shown, the printing security monitoring and auditing system based on virtual printing technology provided by the present invention includes a server, at least one common client, at least one approval client, a print controller, and a printer; the common client and the approval client are collectively referred to as Clients; all common clients and all approval clients are connected to the server, the print controller is connected to the server, and the printer is connected to the print controller.
[0020] The common client consists of a single PC and the common client software installed in the PC. Common client software includes virtual printers, common client network communications, and common client man-machine interfaces.
[0021] The approval client consists of a single PC and the approval client software installed in the PC. Approval client software includes approval client network communication, approval client man-machine interface.
[0022...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com