Image encoding method for preventing and identifying image tamper
An image coding and coding technology, applied in image communication, image data processing, image data processing, etc., can solve problems such as difficulty, not allowing images, and generating noise, and achieve the effect of ensuring security and authenticity and preventing malicious tampering.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
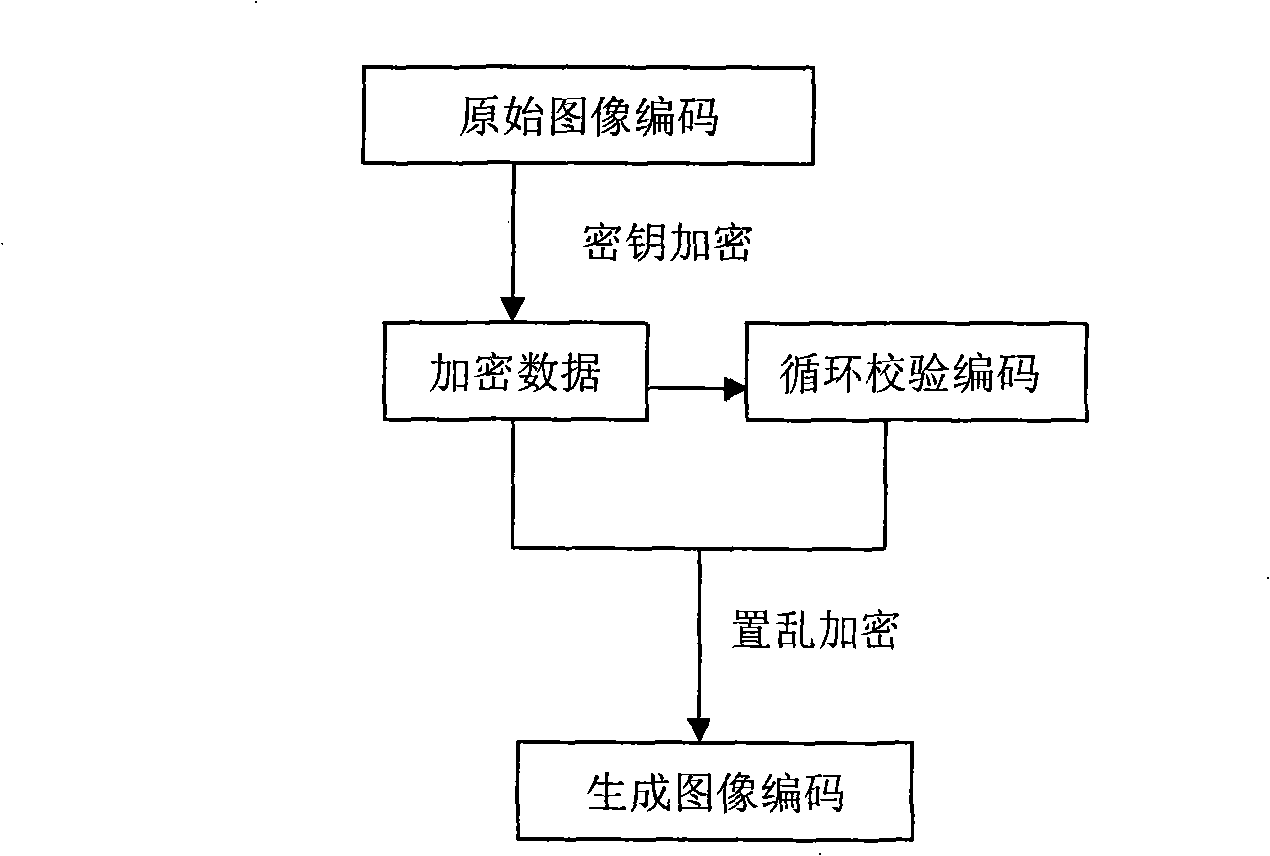
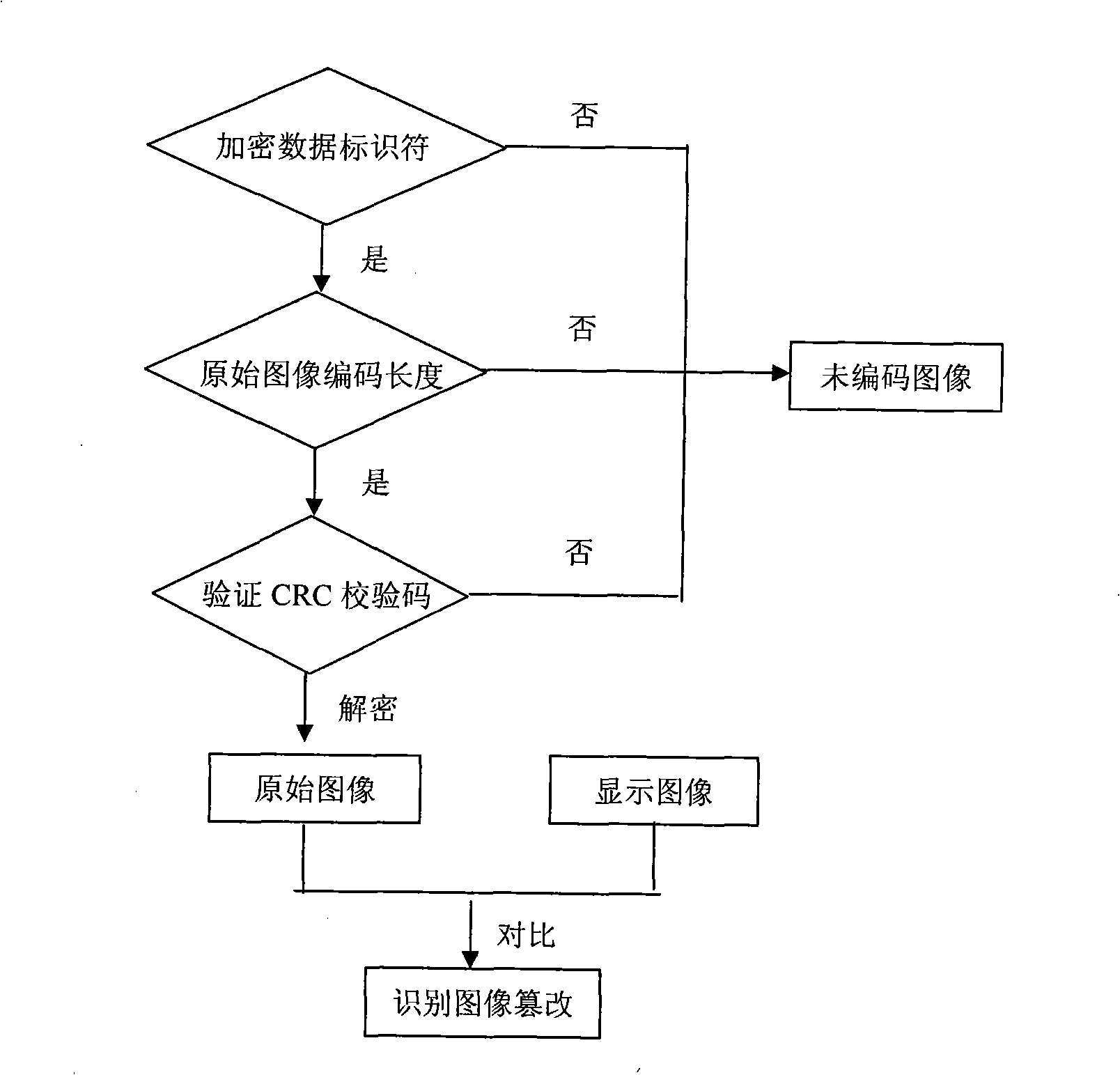
[0022] An image encoding method for preventing and identifying image tampering, comprising the following steps:
[0023] 1. Encrypted original image encoding:
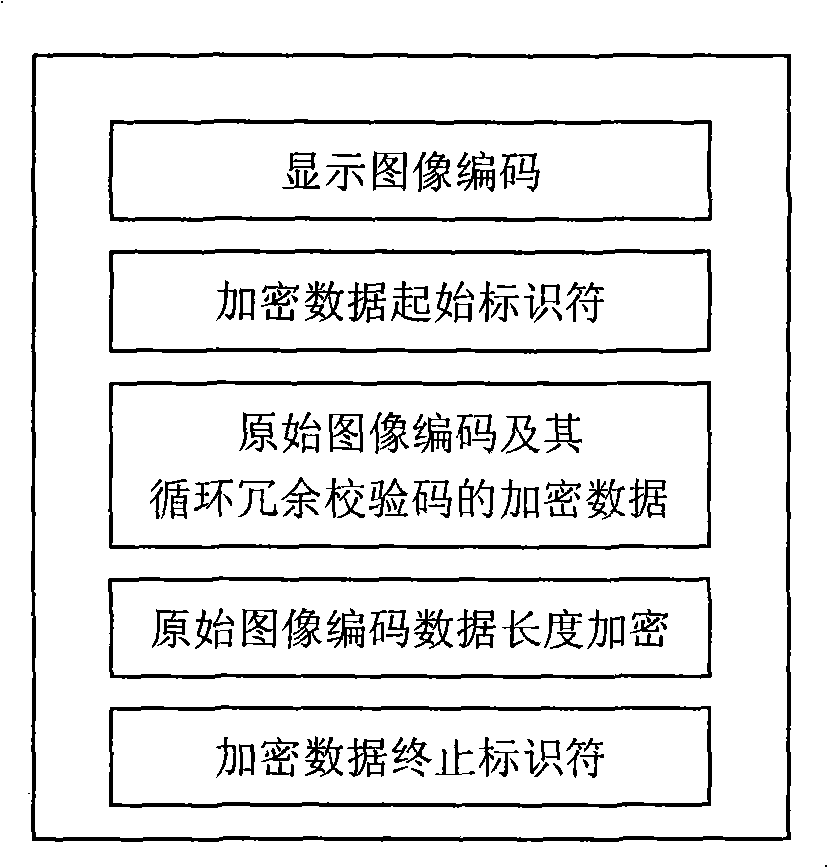
[0024] Such as figure 2 To generate the encoded file structure shown in the figure, firstly, the encoding of the displayed image must be completed. The encoding of the displayed image can be encoded in any format, such as BMP, JPEG, JPEG2000, PNG, RAW, etc., and then set the start identifier of the encrypted data. As a starting sign for decoding encrypted data, the sign can be defined by characters composed of multiple bytes, such as defining 4 bytes in C++ language (hereinafter, C++ language is used to represent the operation of data) and performing the following arrangement : BYTE(19), BYTE(82), BYTE(11), BYTE(24). When setting the first encoding, the display image is the original image, so the original image encoding is the same as the display image encoding, and the original image encoding uses the key K 1 Encr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com