Disk array and its access right control method and device, server and server system
A technology of access rights and disk arrays, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve the problems of inflexibility, inability to prevent viruses from invading disk arrays, and inability to guarantee data security on disk arrays. Achieve the effects of improving security, avoiding malicious tampering, and preventing viruses from invading disk arrays
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
[0052] Table 4 Permission relation table between access permission table and permission permission table
[0053]
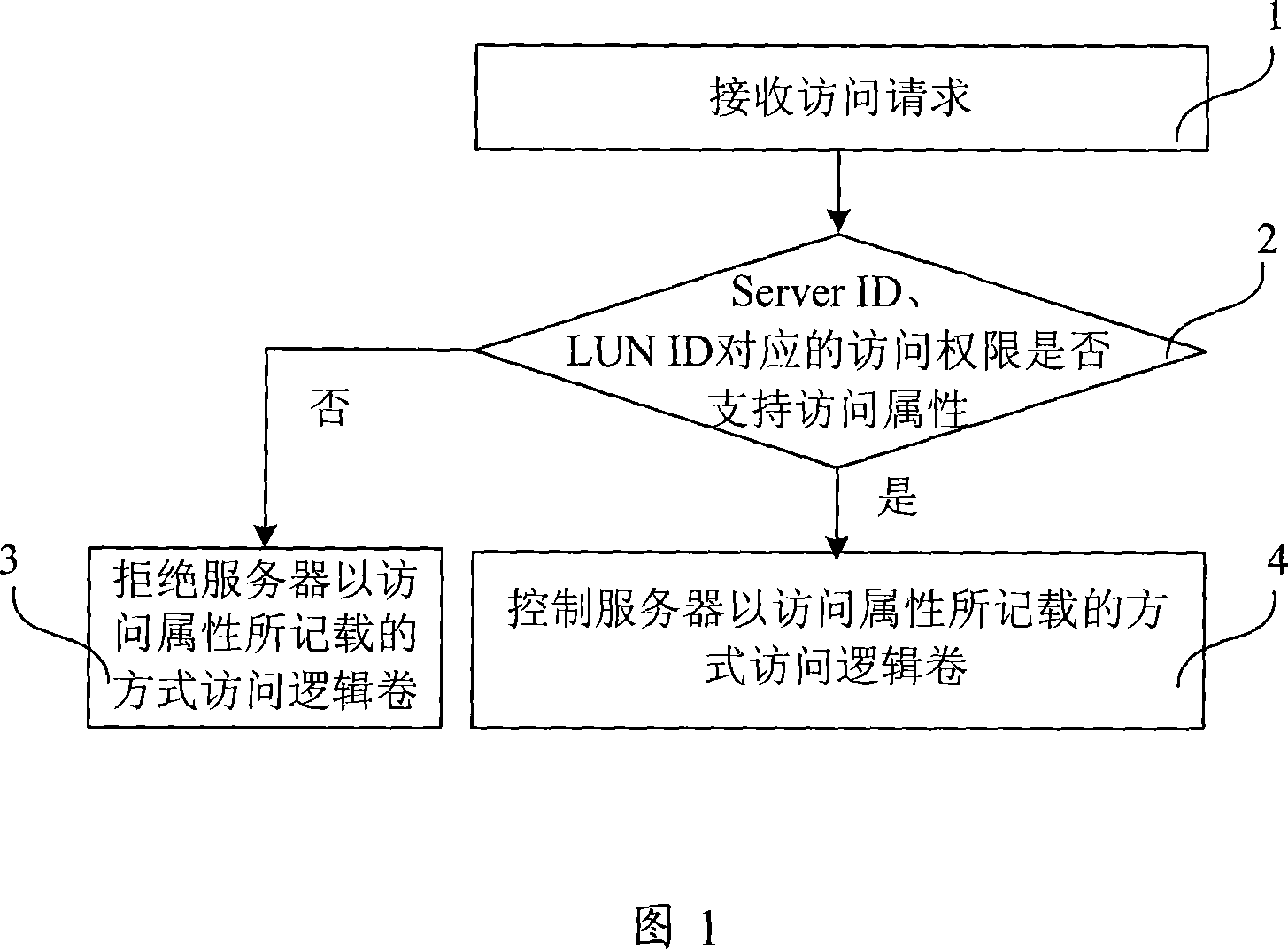
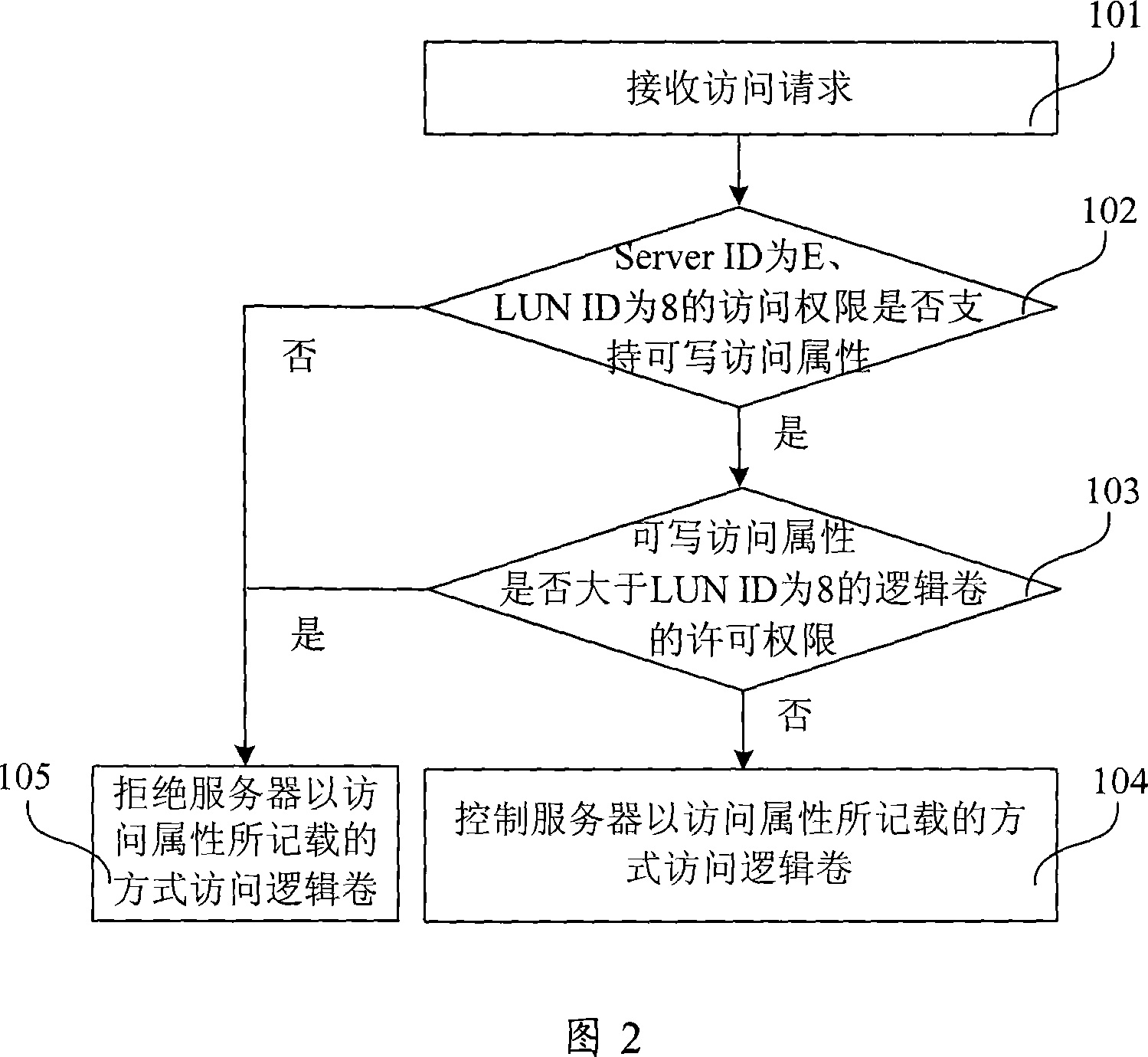
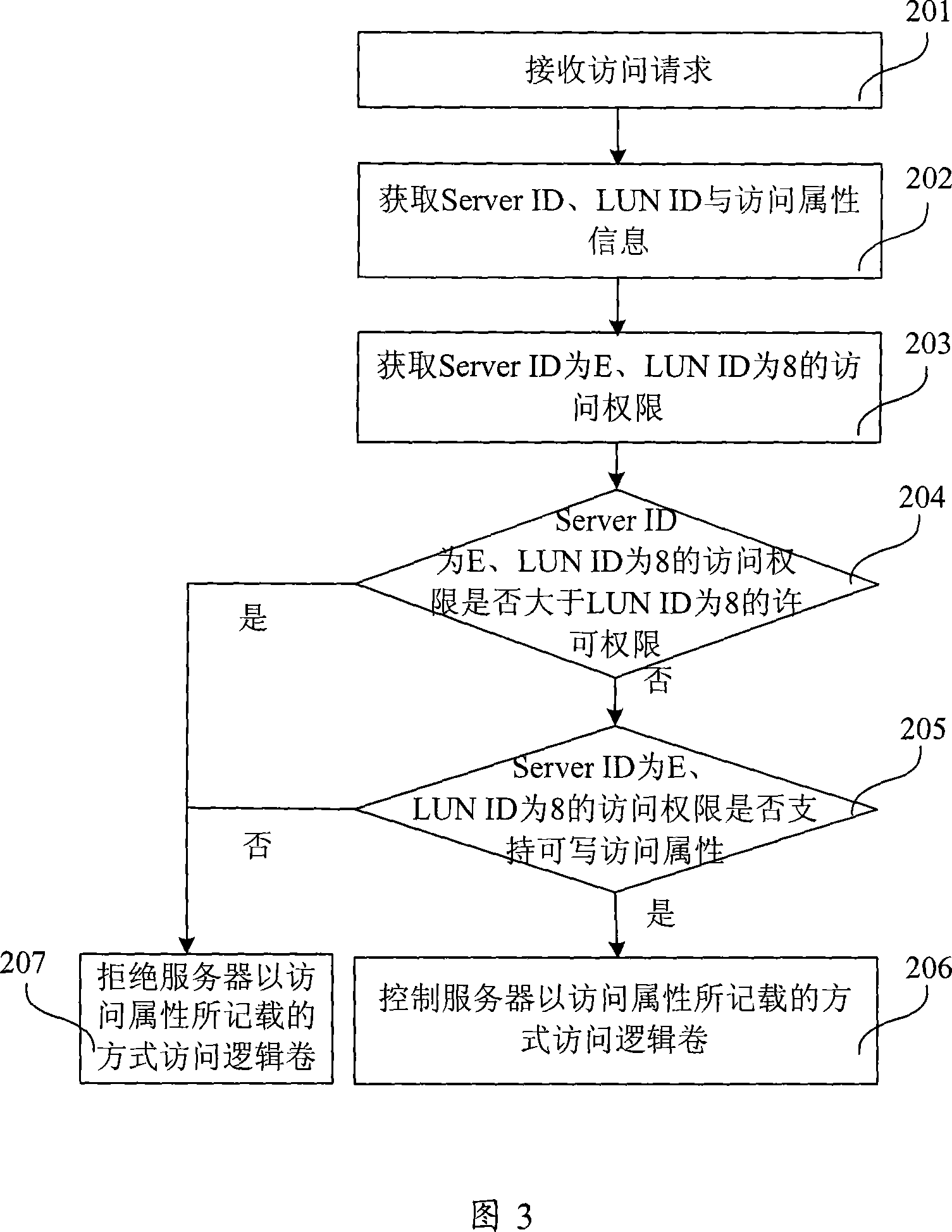
[0054] The access rights of the logical volume corresponding to the same LUN ID should be within the scope of its permission rights, and the setting of the access rights table should be subject to the permission table. According to the above table 4, if the permission permission of the logical volume with LUN ID 3 is set to read and write, the access permission of the server to it can be set to read-only, read-write, and inaccessible; if the set logical volume If the permission permission of the logical volume is read-only, the server's access permission to it can be set to read-only or inaccessible; if the permission permission of the logical volume is set to inaccessible, the server's access permission to it can only be set to inaccessible. When modifying the access permission table, the access permission of the logical volume corresponding to the sa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com