Method and device for abnormity detection and processing of log files
A log file and anomaly detection technology, applied in digital data processing, error detection/correction, hardware monitoring, etc., can solve inaccurate analysis, affect website analysis effect and even operation effect, and log file integrity and accuracy cannot be obtained Guarantee and other issues to achieve the effect of analysis improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
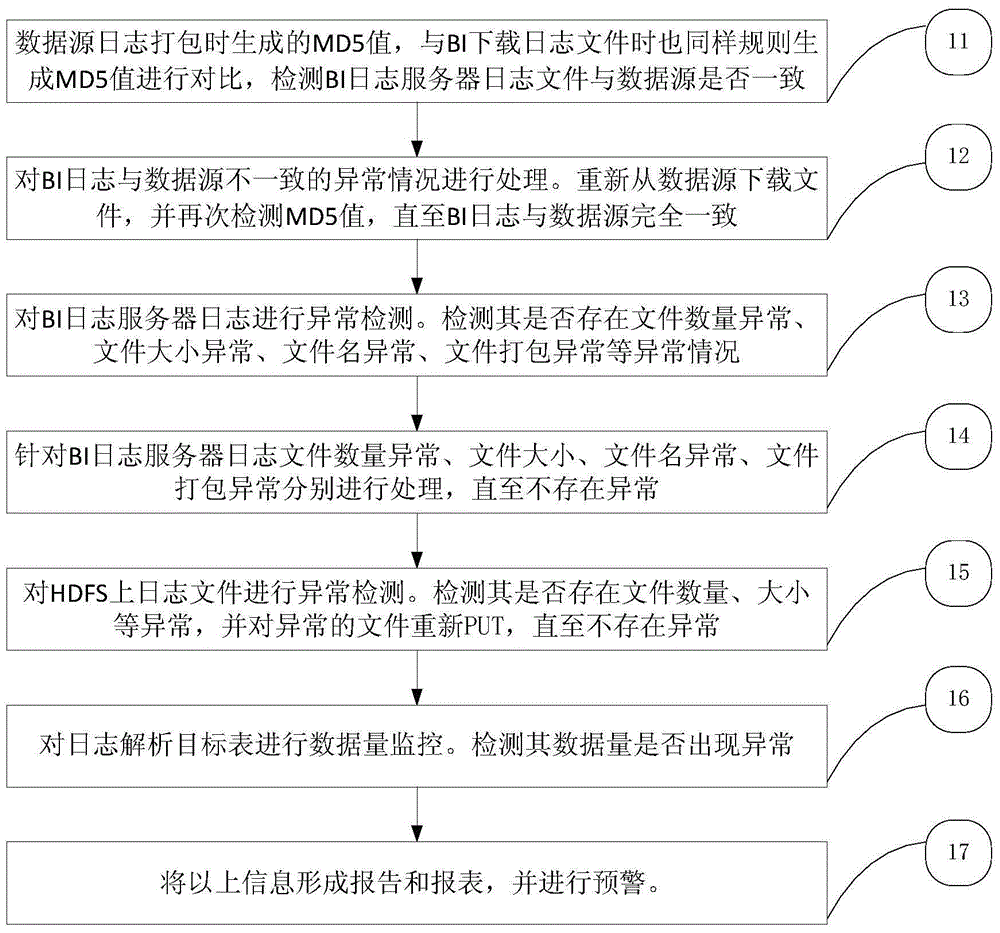
[0034] figure 1 A flowchart showing a log file abnormality detection and processing method according to an embodiment of the present invention.
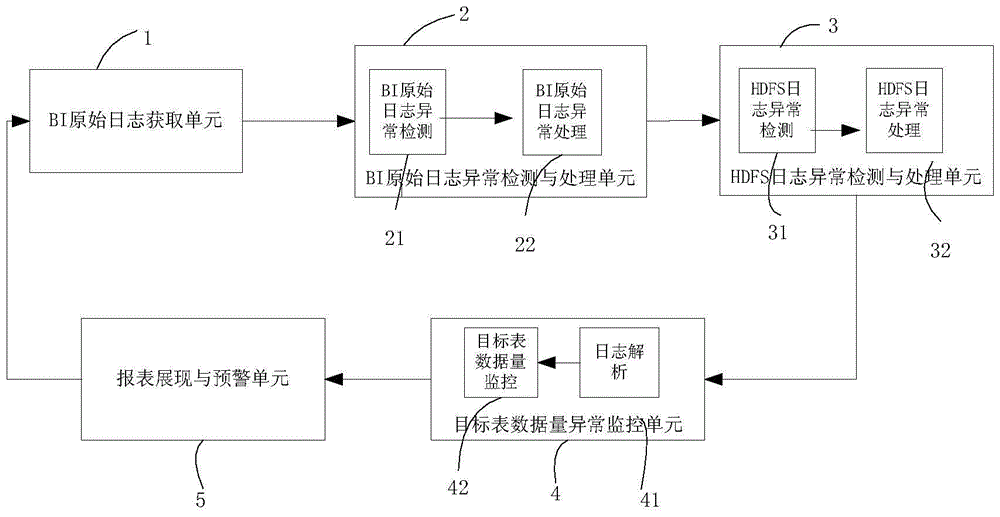
[0035] A method and device for abnormal detection and processing of log files, comprising:
[0036] 1), BI log server log and data source MD5 exception monitoring and processing
[0037] (1) Compare the BI log server log with the MD5 of the data source to detect whether it is abnormal
[0038] When the operation and maintenance package mounts the data source log file and the BI log server downloads the log, the MD5 value is generated for each file with the same MD5 encryption method and stored in two tables respectively. The MD5 value of the data source file and the original BI log server By comparing the MD5 value of the log file, you can judge whether the BI log server log is consistent with the data source file, and give corresponding warnings for abnormal situations.
[0039] (2) Handle the abnormal situation that the log file...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com