Virtual machine load balancing security dispatching method in cloud environment
A scheduling method and load balancing technology, applied in software simulation/interpretation/simulation, multi-program device, program control design, etc., can solve problems such as failure to make, being attacked, and different levels of security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
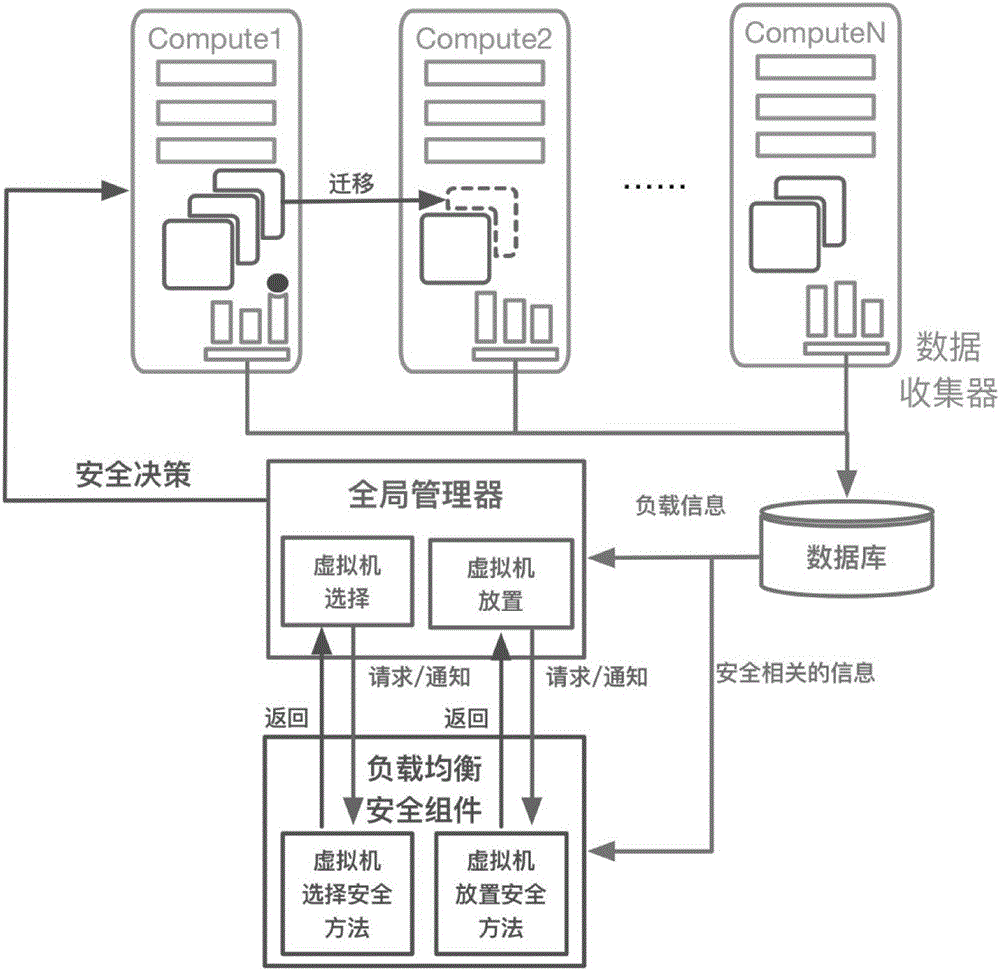
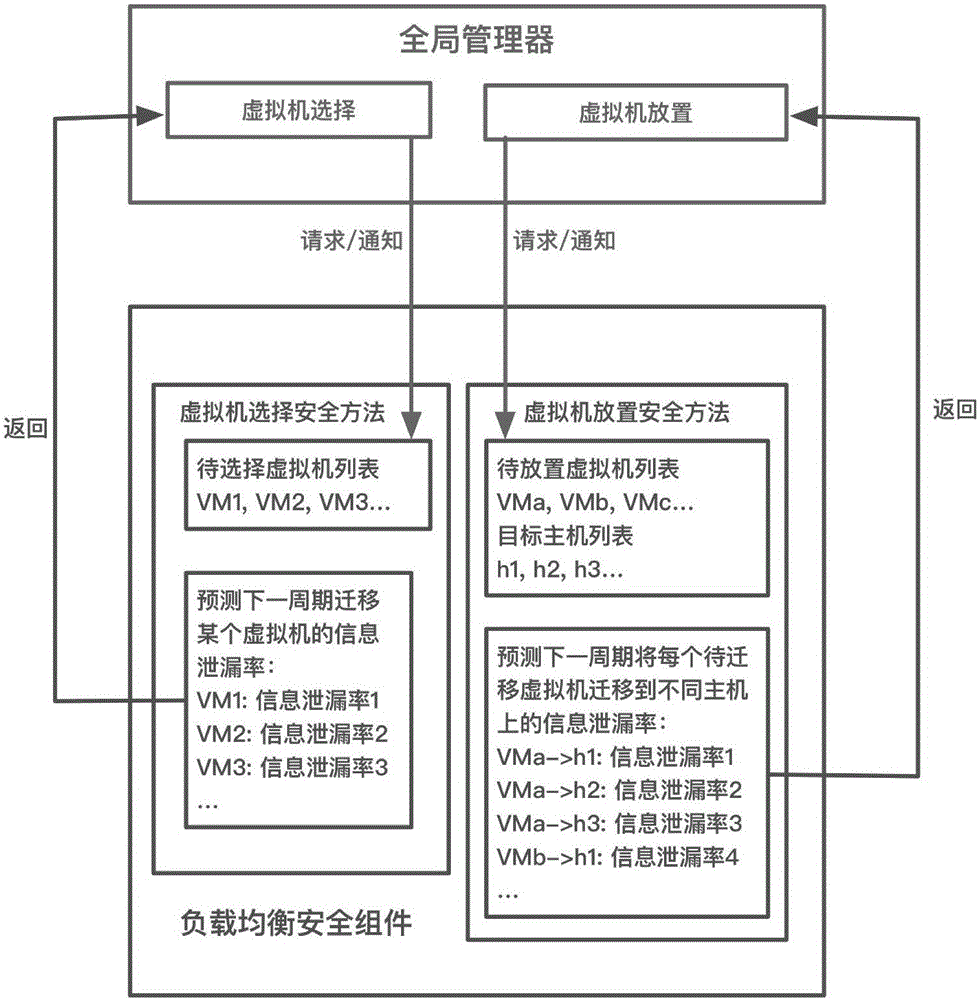
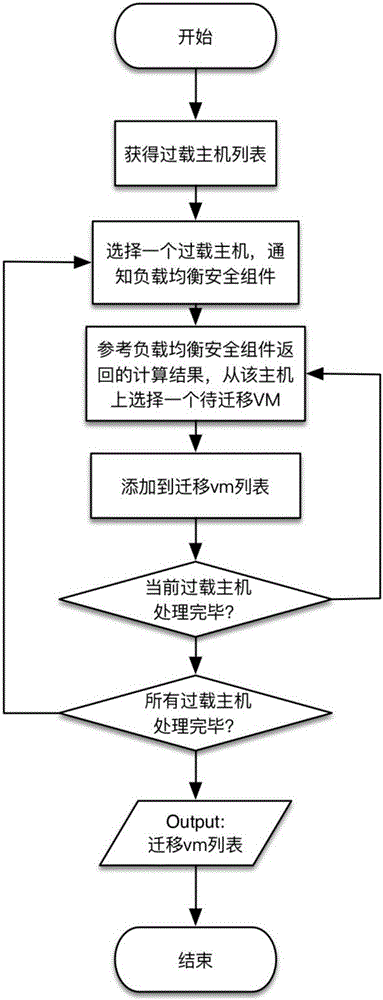
[0060] Take the host overloading of OpenStack as an example, where OpenStack Neat is selected as the load balancer.
[0061] 1) Suppose there are 3 hosts in the cloud environment in the initial state, that is, H={h 1 、h 2 、h 3}, there are 3 users, namely C={c 1 ,c 2 ,c 3}, user c 1 Have a virtual machine VM 1,1 、VM 1,2 , user c 2 Have a virtual machine VM 2,1 、VM 2,2 , user c 3 Have a virtual machine VM 3,1 、VM 3,2 、VM 3,3 . In the initial state h 1 VM 1,1 、VM 2,1 、VM 3,2 , h 2 VM 1,2 、VM 2,2 , there is a virtual machine VM on h3 3,1 . VM 3,3 . The security component receives the creation and placement information of all the above hosts, users, and virtual machines. set another x 1 =x 2 = 1, the information leakage rate of the virtual machine to the friendly virtual machine is 0, and the information leakage rate of the virtual machine to the trusted host is 0. If the system detects the current time h 1 Overload, assuming that user c at this time ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com