Mimicry defense method for deep learning model confrontation attack
A deep learning and model technology, applied in neural learning methods, biological neural network models, character and pattern recognition, etc., can solve problems such as not being universal, achieve good defense effects, reduce training time, and improve defense effects Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further described below in conjunction with the accompanying drawings.
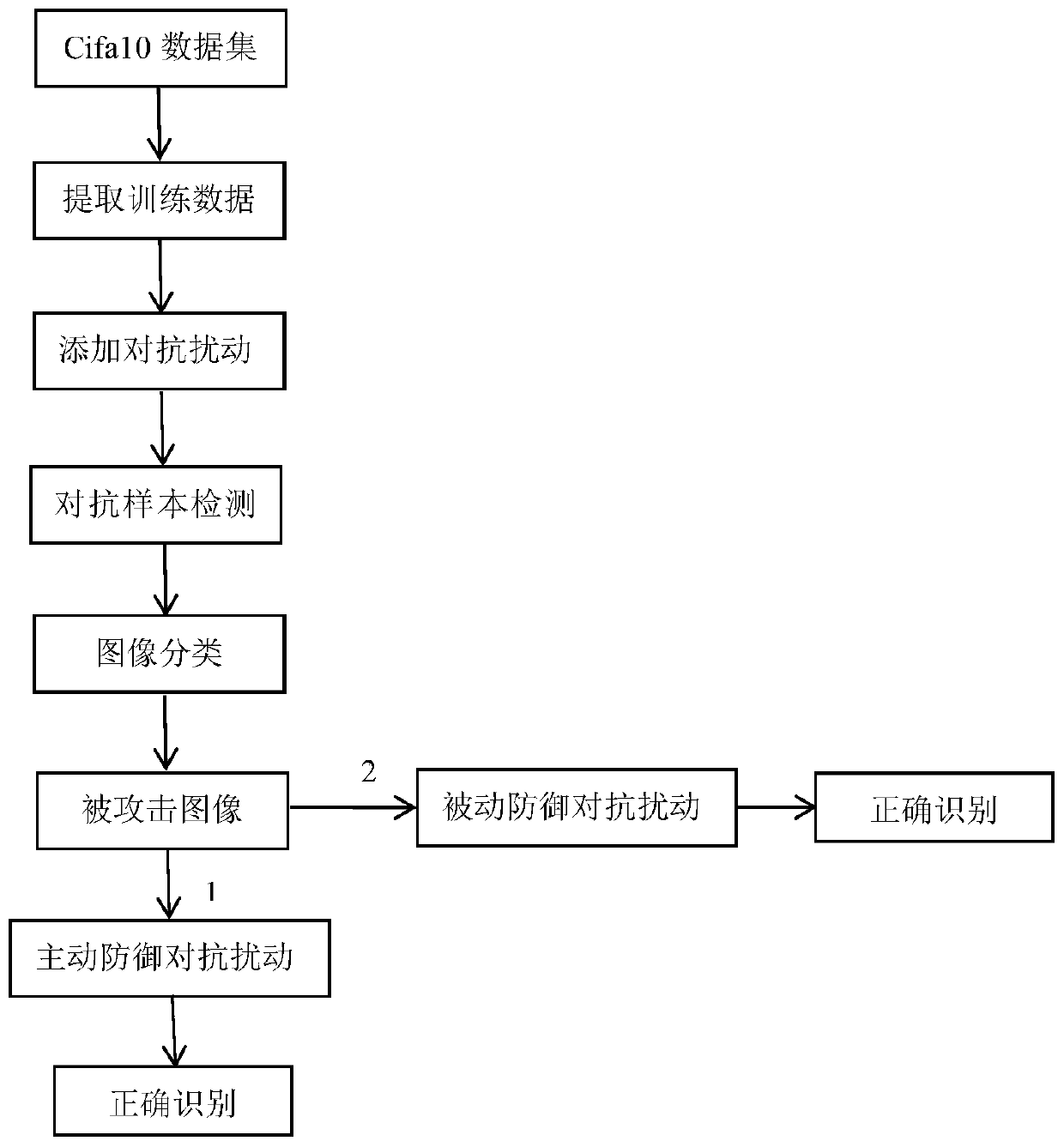
[0048] A mimetic defense method for deep learning model against attacks, including the following steps:
[0049] 1) Randomly take some normal pictures and input them to various attack models A to generate pictures with anti-disturbance, that is, anti-sample s. The present invention takes the cifa10 data set as an example, and the methods for generating adversarial examples include FGSM, JSMA, iterative calculation method, image rotation and the like. Save the adversarial samples generated by different attack methods in batches.
[0050] 2) Training the adversarial example detector, the process is as follows:
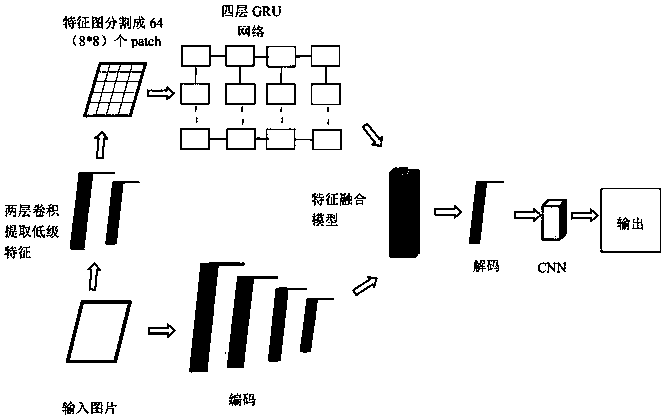
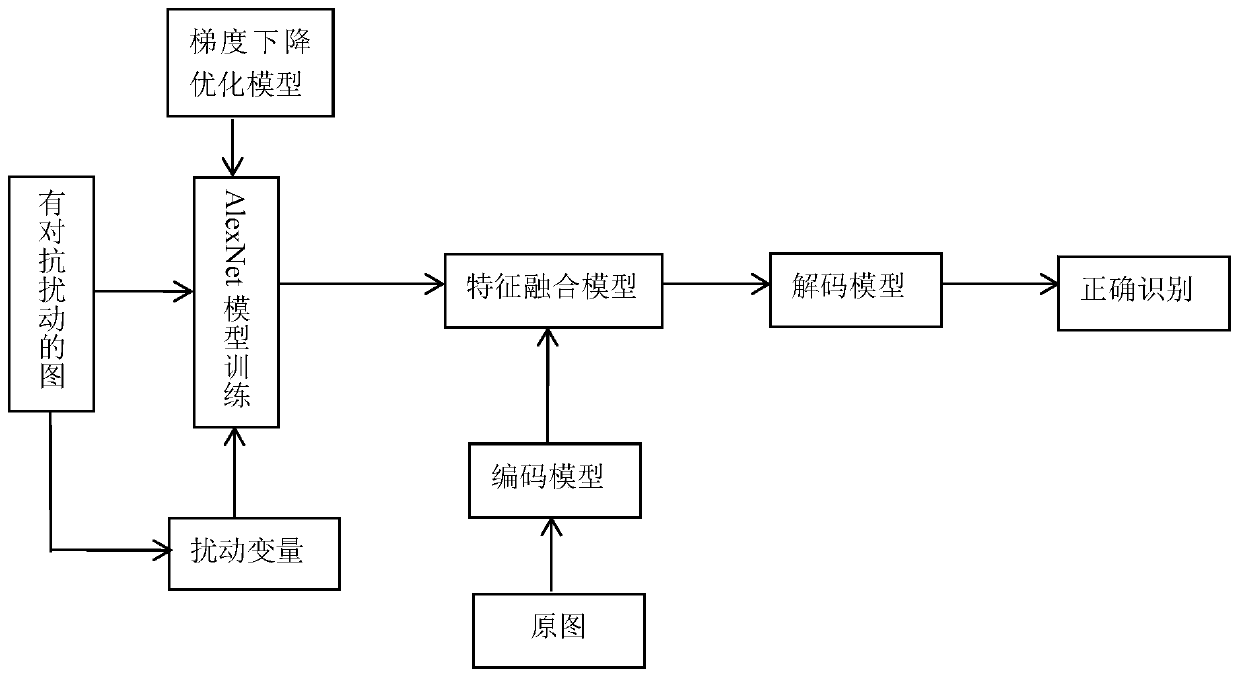
[0051] 2.1) Divide each adversarial sample into 8×8 image blocks (batches) that do not cross and overlap with each other, and extract resampling features for the patches, and then input the resampling features extracted from the image into the GRU network in se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com