Mimicry defense architecture based zero-day attack detection, analysis and response system and method thereof
An attack detection and attacker technology, applied in the field of network security, can solve the problems of lack of response means, error consistent output, increase of defense cost, etc., to achieve the effect of reducing defense cost, ensuring robustness, and improving mimic defense efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
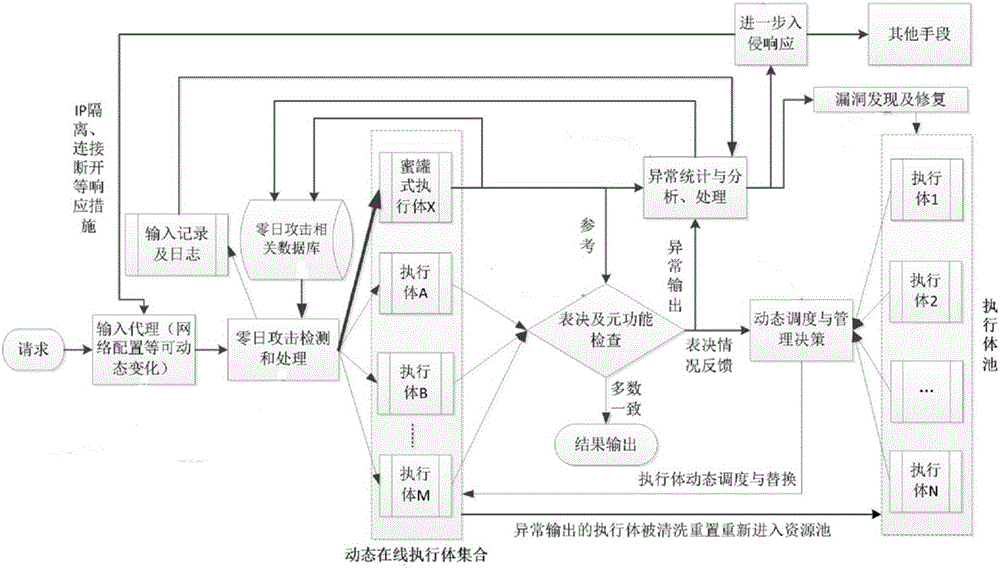
[0037] Embodiment one, see figure 1As shown, a zero-day attack detection, analysis and response system based on the mimic defense architecture includes an input agent unit, a zero-day attack detection unit, a dynamic online execution body set, a voting and meta-function inspection unit, a dynamic scheduling and management unit, Execution body pool, exception statistics and analysis unit, among which,
[0038] The input proxy unit conducts a preliminary inspection of the request data packet, including: processing the request data packet according to the requirements of the intrusion response, and dynamically changing the network attributes and configuration at the same time;
[0039] The zero-day attack detection unit detects, analyzes and abnormally judges the input request data according to the zero-day attack database;
[0040] Dynamic online execution body collection, including honeypot execution body and M heterogeneous execution bodies, M heterogeneous execution bodies i...
Embodiment 2
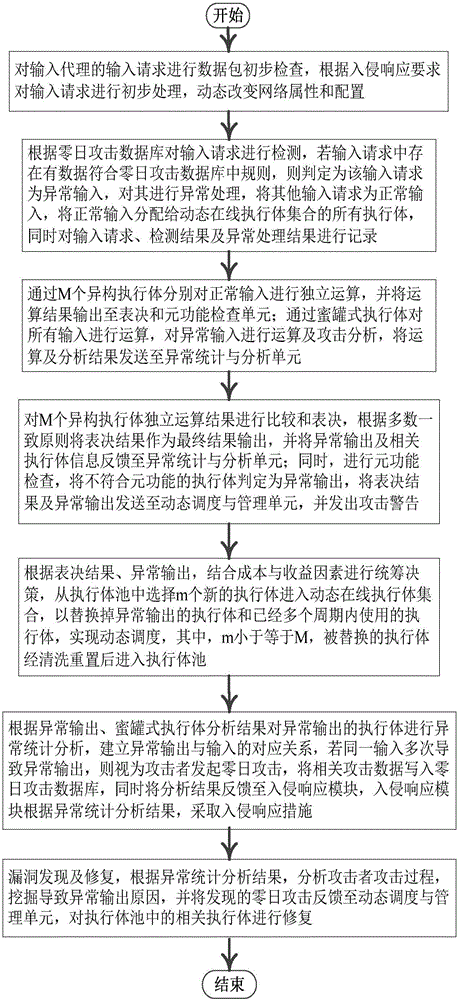
[0047] Embodiment 2 is basically the same as Embodiment 1, the difference is that it also includes a vulnerability discovery and repair unit, which analyzes the attacker’s attack process according to the abnormal statistical analysis results, digs out the cause of the abnormal output, and feeds back the found zero-day attack Go to the dynamic scheduling and management unit, and repair the related execution bodies in the execution body pool.
[0048] As mentioned above, the meta-function inspection checks whether the output of the executive body conforms to its design function, checks and blocks the output of non-meta-functions; the honeypot type executive body intentionally leaks the information of the executive body to lure attackers to attack it, At the same time, the detected abnormal input is analyzed to obtain attacker information.
Embodiment 3
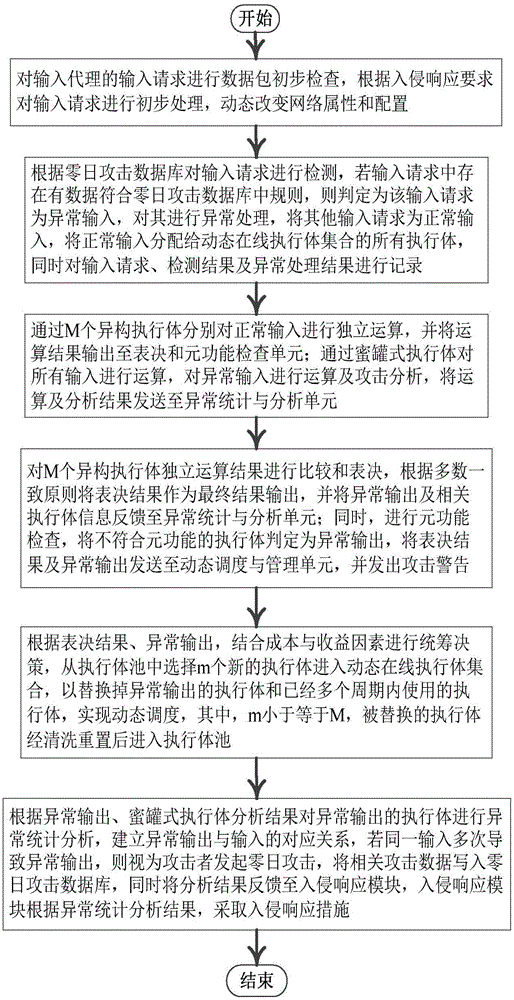
[0049] Embodiment three, see Figure 1~2 As shown, a zero-day attack detection, analysis and response method based on the zero-day attack detection, analysis and response system based on the mimic defense architecture described in Embodiment 1 includes the following steps:
[0050] Step 1. Perform a preliminary inspection of the data packet on the input request of the input agent, including: perform preliminary processing on the input request according to the intrusion response requirements, and dynamically change network attributes and configurations at the same time;
[0051] Step 2. The input request is detected according to the zero-day attack database. If there is data in the input request that conforms to the rules in the zero-day attack database, it is determined that the input request is an abnormal input, and abnormal processing is performed on it, and other input requests are treated as Normal input, assigning normal input to all the execution bodies of the dynamic o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com