Mimicry network topology transformation method
A technology of network topology and topology transformation, applied in the field of computer communication, can solve the problems that it is difficult for attackers to observe and predict changes in the target environment, increase the difficulty and cost of attacks, and achieve the goal of reducing network scale, reducing difficulty, and increasing flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
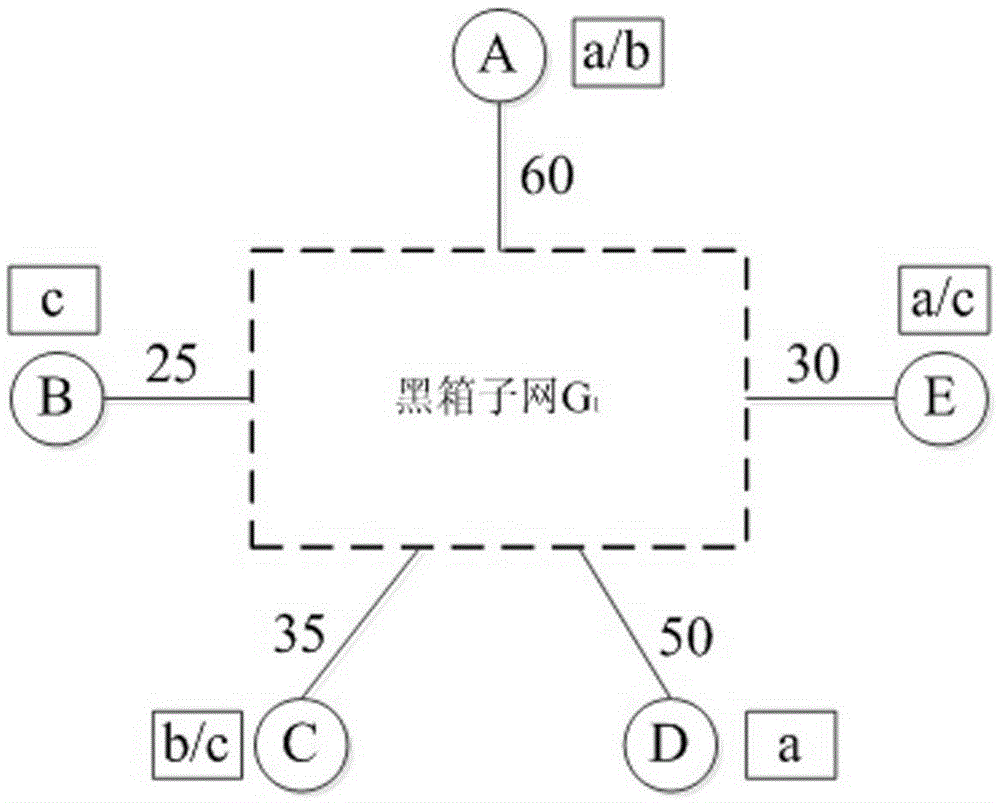
[0029] The following explains the signs appearing in the description of the drawings: represents a node, Indicates the node function, 20 , 25 , 30 , 35 , 40 , 50 , 60 Indicates link bandwidth.
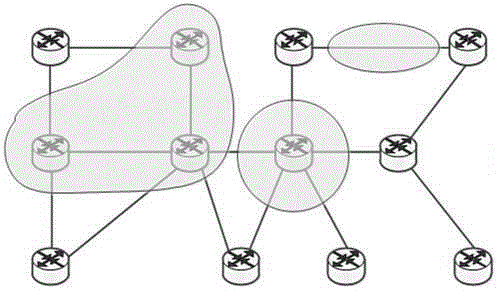
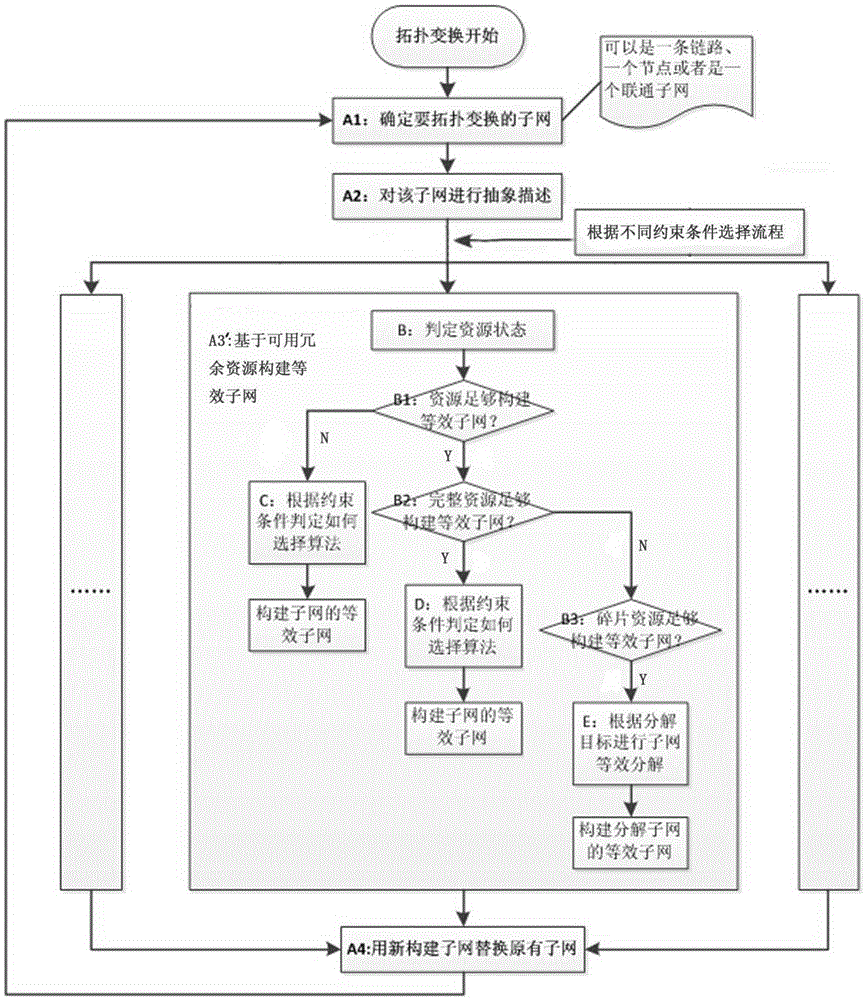
[0030] The method for the topology transformation of the mimic network of the present invention will be further described below in conjunction with the accompanying drawings and specific implementation methods: based on this method, the network can dynamically construct the network topology under equivalent conditions, thereby providing the dynamics, non-determinism, and Heterogeneity implements active hopping or rapid migration between diverse topology environments in a controllable manner by the network builder, making it difficult for attackers to observe and predict topology changes. The network equivalence mentioned here means that the function, performance and other indicators of the network after the topology transformation are consistent with the network before the tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com