Mimicry honeypot fingerprint confusion system and method and SDN network architecture thereof
A honeypot and fingerprint technology, applied in the field of mimetic honeypot fingerprint obfuscation system, can solve the problems of difficult to resist fingerprint sniffing and isolated static defense, so as to reduce the fingerprint recognition rate, ensure security and reliability, and avoid impact. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
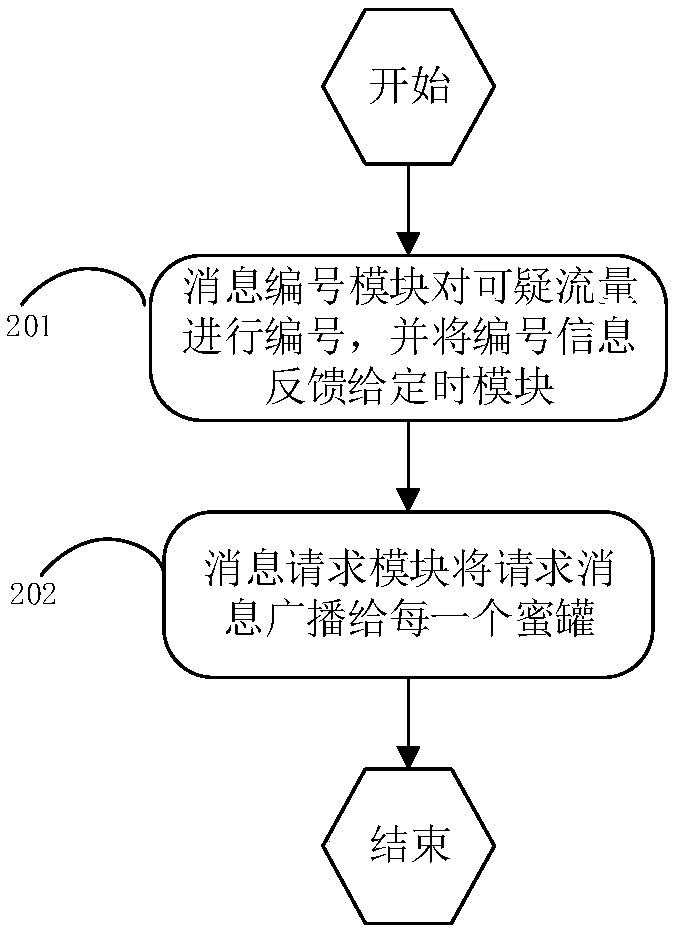
[0028] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
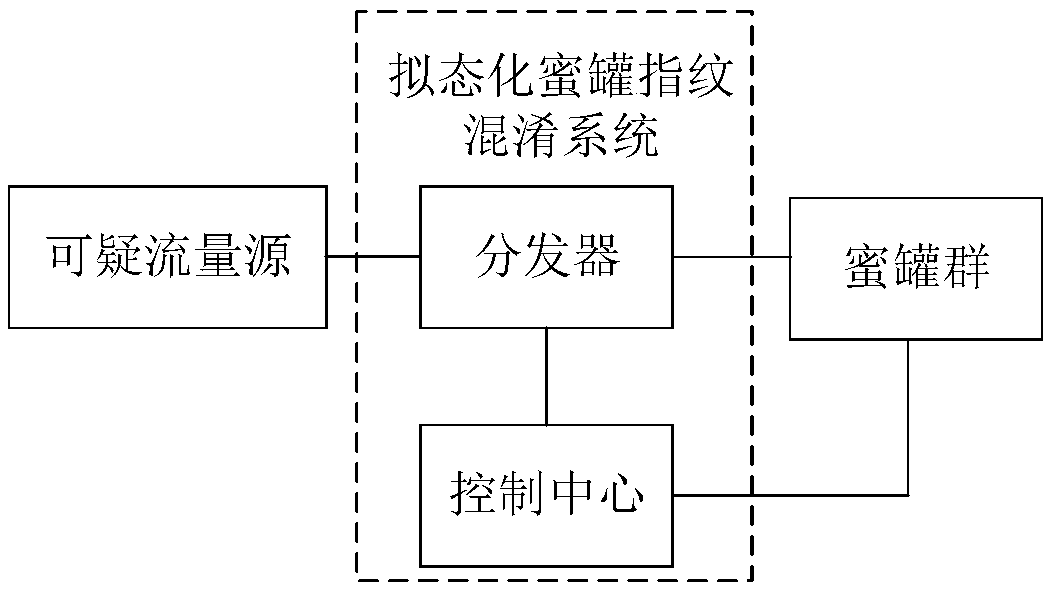
[0029] At present, honeypot fingerprints are difficult to hide, and isolated static defenses are difficult to effectively protect network security. For this reason, embodiment of the present invention, see figure 1 As shown, a mimetic honeypot fingerprint confusion system is provided, including: a distributor and a control center, wherein,
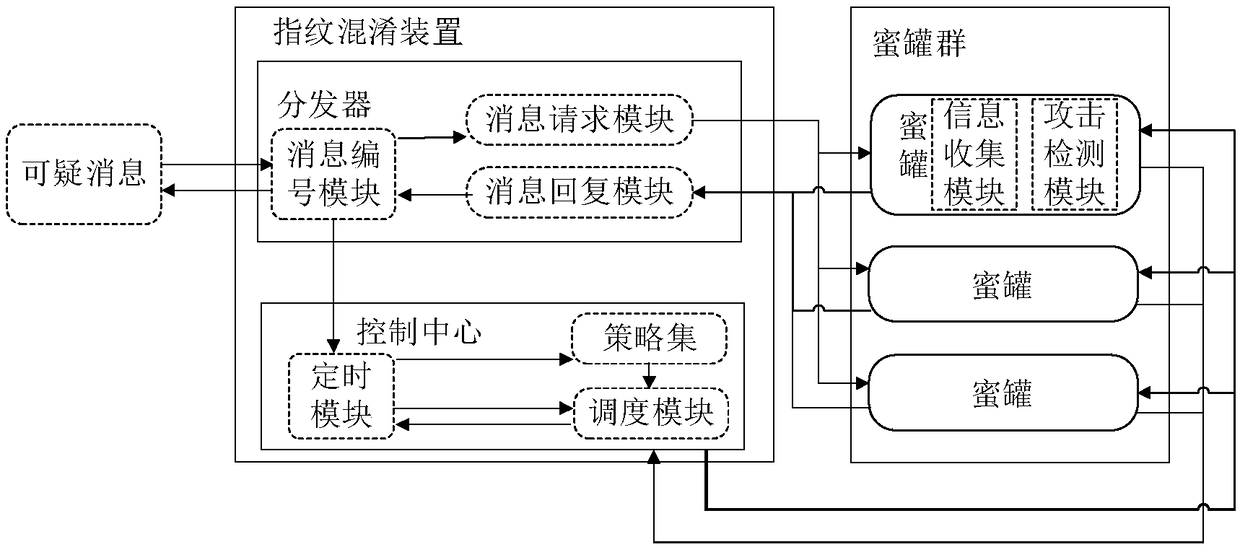
[0030] The control center, deployed on the distributor, is used to maintain the working status of the honeypot, dynamically generate the scheduling rules of the honeypot according to the suspicious traffic behavior characteristics fed back by the honeypot, and start and close the corresponding honeypot according to the scheduling rules;
[0031] Distributor, deployed between the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com