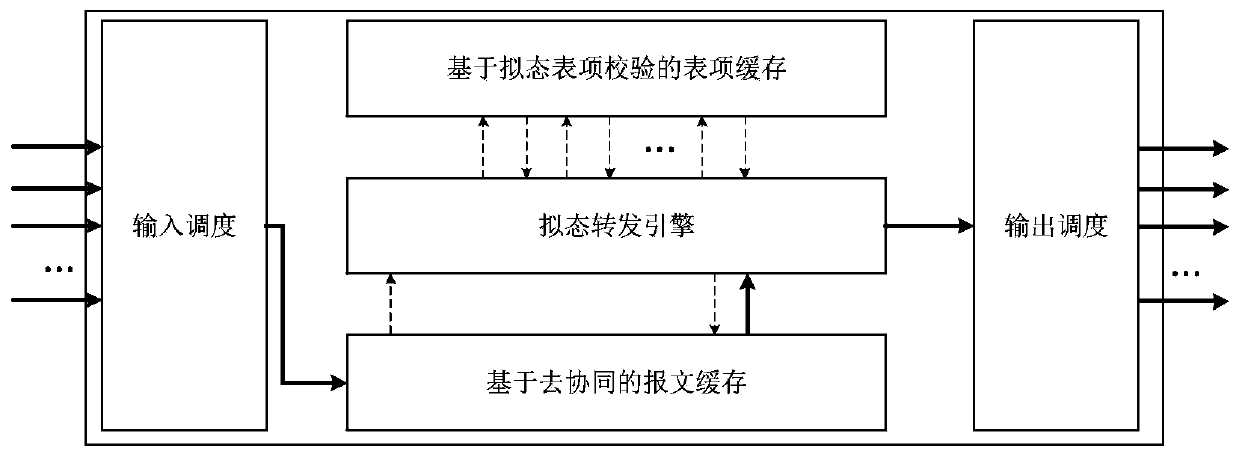
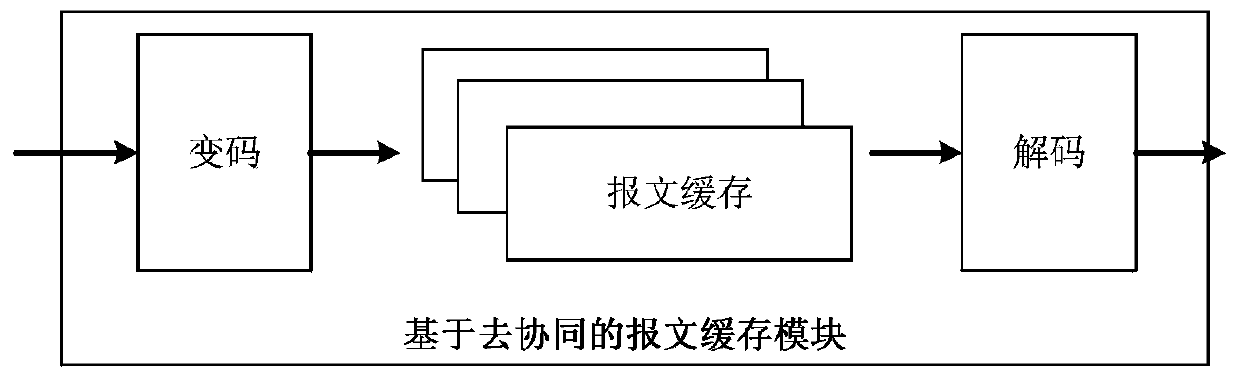
Mimicry thought-based security exchange chip, implementation method and network exchange equipment
A technology of secure exchange and thought, applied in the field of network exchange, can solve the problems of shortening the research and development cycle, changing the data flow, tampering or destroying, etc., to achieve the effect of increasing difficulty, enhancing reliability, and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
[0051] Network exchange refers to a form of exchange that converts different signals or signal forms into signal types recognizable by the other party through switches and other equipment to achieve communication purposes. The common ones are: data exchange, line exchange, message exchange, and packet exchange. . In a computer network, according to different switching levels, network switching can be divided into physical layer switching (such as telephone network), link layer switching (two-layer switching, changing the MAC address), network layer switching (three-layer switching, Change the IP address), transport layer switching (four-layer switching, port changes, relatively rare) and application layer switching (i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com