Majority consistent escape error processing device based on mimicry security defense zero-day attack and method thereof
A security defense and error handling technology, applied in the field of network security, to achieve the effect of ensuring robustness and survivability, reducing defense costs, and ensuring robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
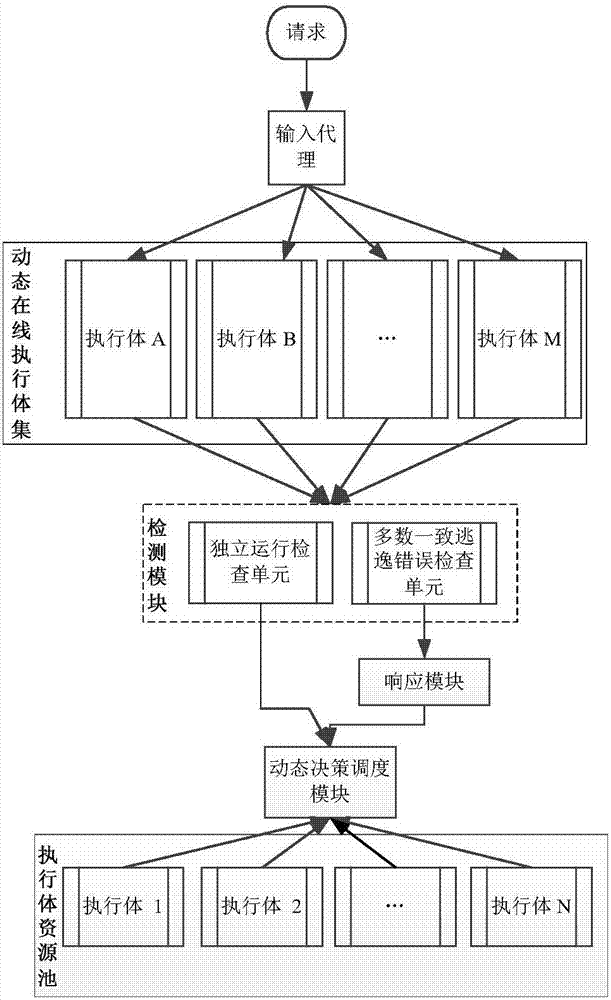
[0032] Embodiment one, see figure 1 As shown, a majority consensus escape error processing device based on mimic security defense zero-day attack, a majority consensus escape error processing device based on mimic security defense zero-day attack, including dynamic online execution body set, execution body resource pool, detection module, response module and dynamic decision-making scheduling module, the dynamic online execution body set contains M dynamic online execution heterogeneous execution bodies, the execution body resource pool contains N heterogeneous execution bodies with meta-functional equivalents, and the M dynamic Heterogeneous execution bodies executed online include at least new online execution bodies and online majority consistent execution bodies;
[0033] The detection module is used to detect the operation result of the request received by the input agent according to the heterogeneous execution body in the dynamic online execution body set, including an in...
Embodiment 2
[0037] Embodiment 2 is basically the same as Embodiment 1, except that the response module includes a record analyzer, an attack response unit, and an output alarm unit, wherein the record analyzer feeds back to most consistent escape error checking units. Record and analyze the inconsistent results, and feed back the analysis results to the attack response unit and the output alarm unit; the attack response unit is used to respond to the attacker and establish a zero-day attack related database; the output alarm unit issues an alarm and determines The operation output of the new online executive is the final output, and the majority of the original online consistent executives are abnormal output executives. The multi-mode ruling is suspended, and the executive switching request is sent to the dynamic decision-making scheduling module.
[0038] Preferably, the response module further includes: a vulnerability repair unit, which receives the analysis result of the record analyz...
Embodiment 3
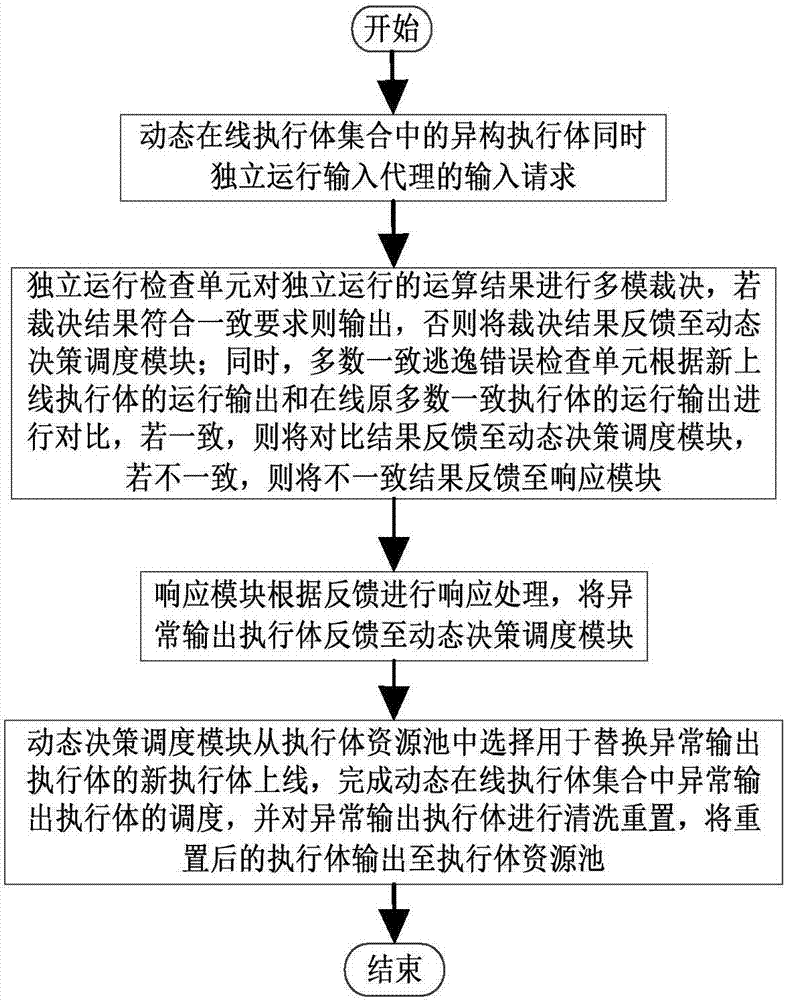
[0040] Embodiment three, see Figure 1~2 As shown, a majority consistent escape error processing method based on mimic security defense zero-day attack is realized based on the majority consistent escape error processing device based on mimic security defense zero-day attack described in Embodiment 1, comprising the following steps:
[0041] Step 1. The heterogeneous executors in the dynamic online executor set independently run the input request of the input agent at the same time;
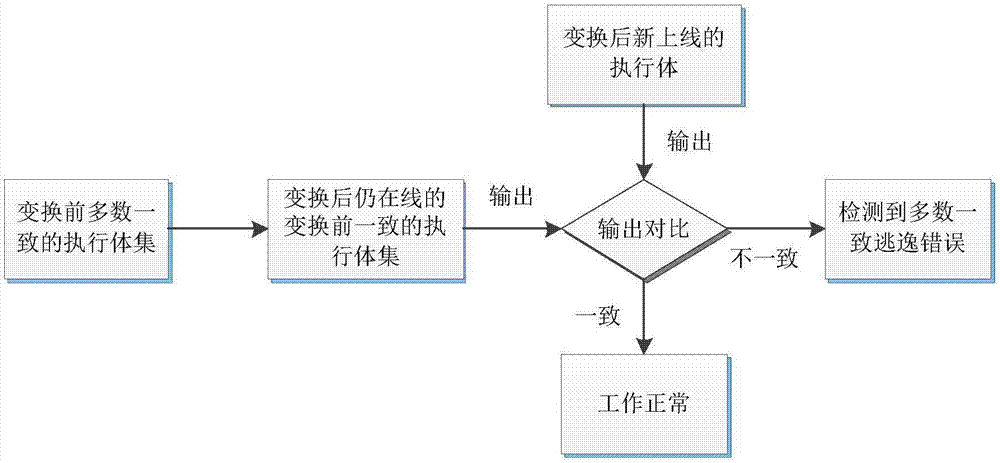
[0042] Step 2. The independent operation check unit conducts multi-mode judgment on the calculation results of independent operation. If the judgment result meets the consistent requirements, it will output, otherwise, the judgment result will be fed back to the dynamic decision-making scheduling module; at the same time, most of the consistent escape error check units execute according to the new online Compare the operation output of the entity with the operation output of the online majority o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com