Harass call identification and interception method
A technology of harassing calls and identification factors, applied in the field of harassing calls identification and interception, which can solve problems such as flooding and limited coverage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] Hereinafter, the preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings.
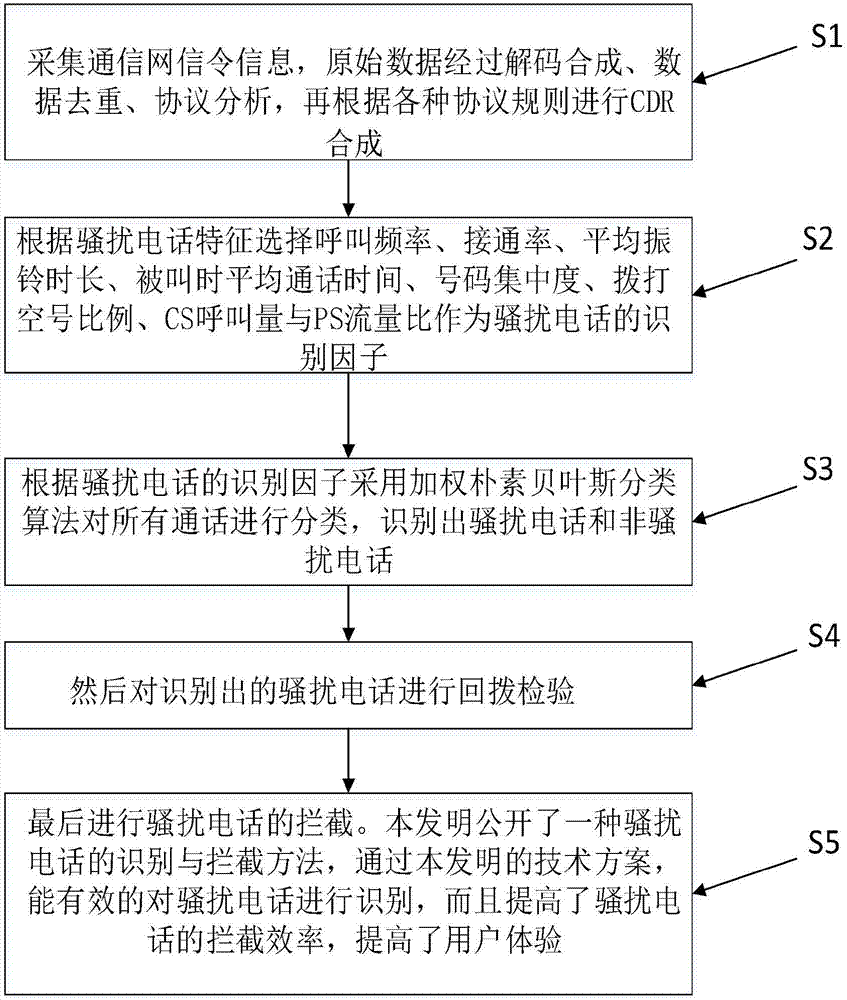
[0067] Such as figure 1 As shown, this embodiment includes the following steps:
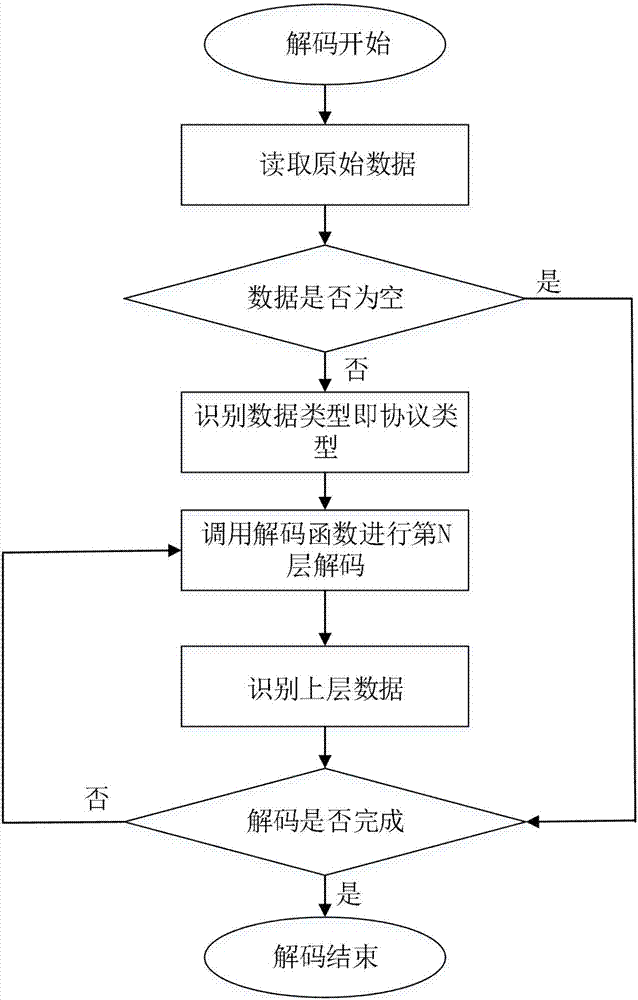
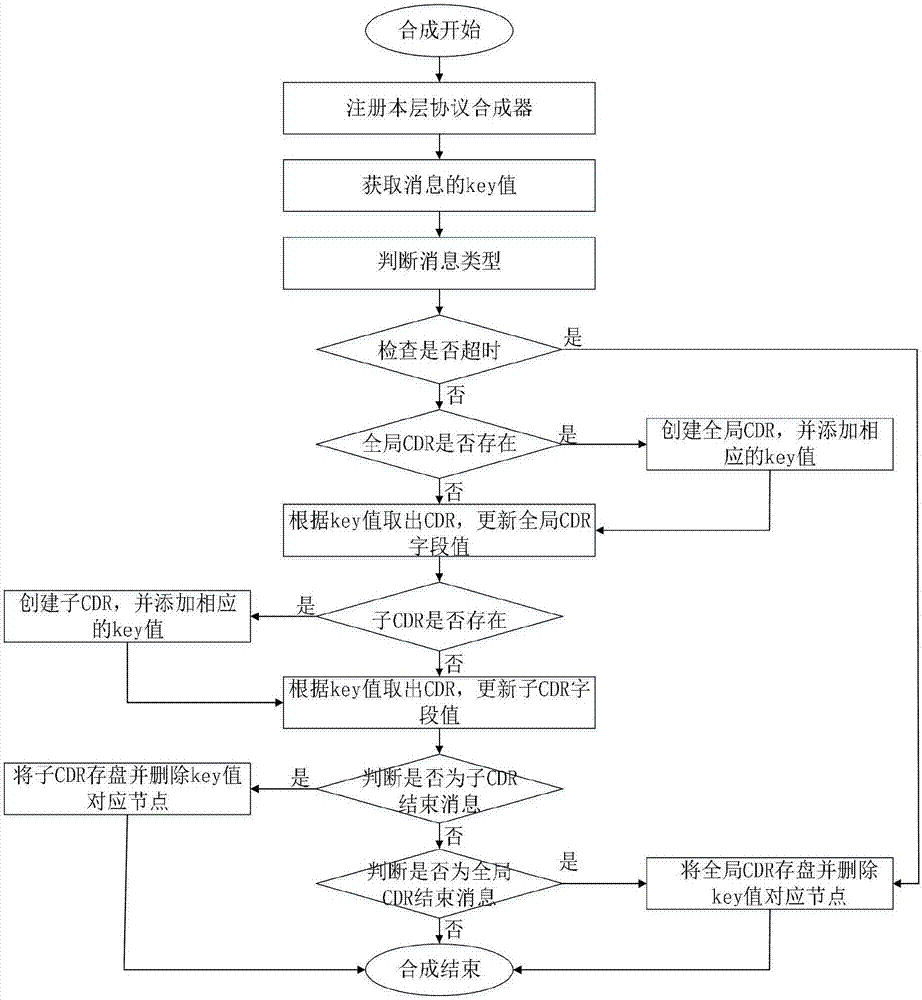
[0068] S1: Collect the signaling information of the communication network, the original data is decoded and synthesized, data deduplication, protocol analysis, and then CDR synthesis is performed according to various protocol rules;
[0069] S2: According to the characteristics of harassing calls, select calling frequency, connection rate, average ringing duration, average call time when called, number concentration, ratio of empty numbers, ratio of CS call volume and PS traffic as the identification factor of harassing calls;
[0070] S3: Use weighted naive Bayes classification algorithm to classify all calls according to the identification factor of harassing calls, and identify harassing calls and non-harassing calls;
[0071] S4: Then perform a callback chec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com