Uniform intimidation managing device and loading method of intimidation defense module
A technology for managing equipment and equipment, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as random packet discarding, hardware acceleration, and software that cannot meet equipment processing performance, and achieve the effect of ensuring throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
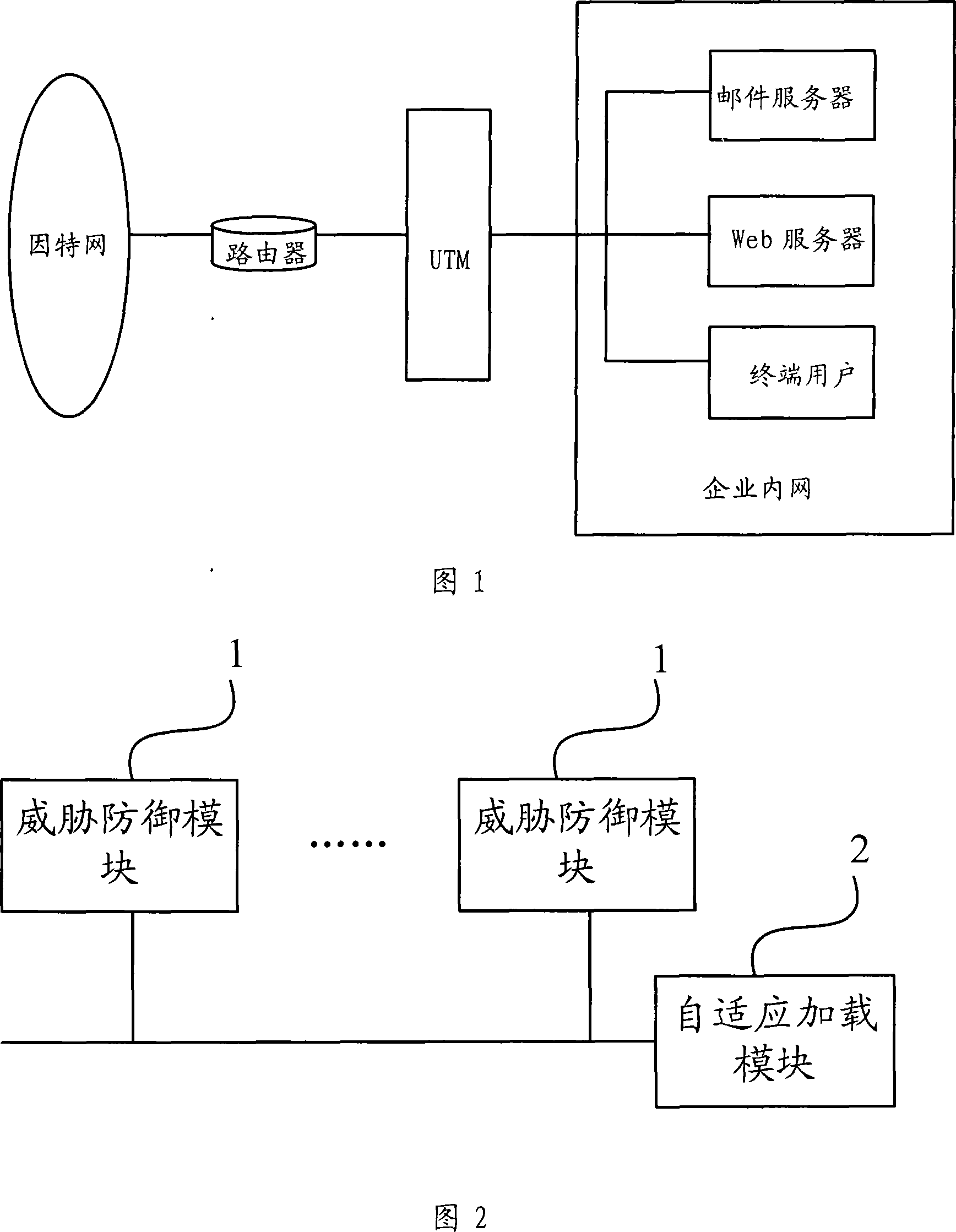
[0023] The unified threat management device in the embodiment of the present invention will be described below with reference to the accompanying drawings.
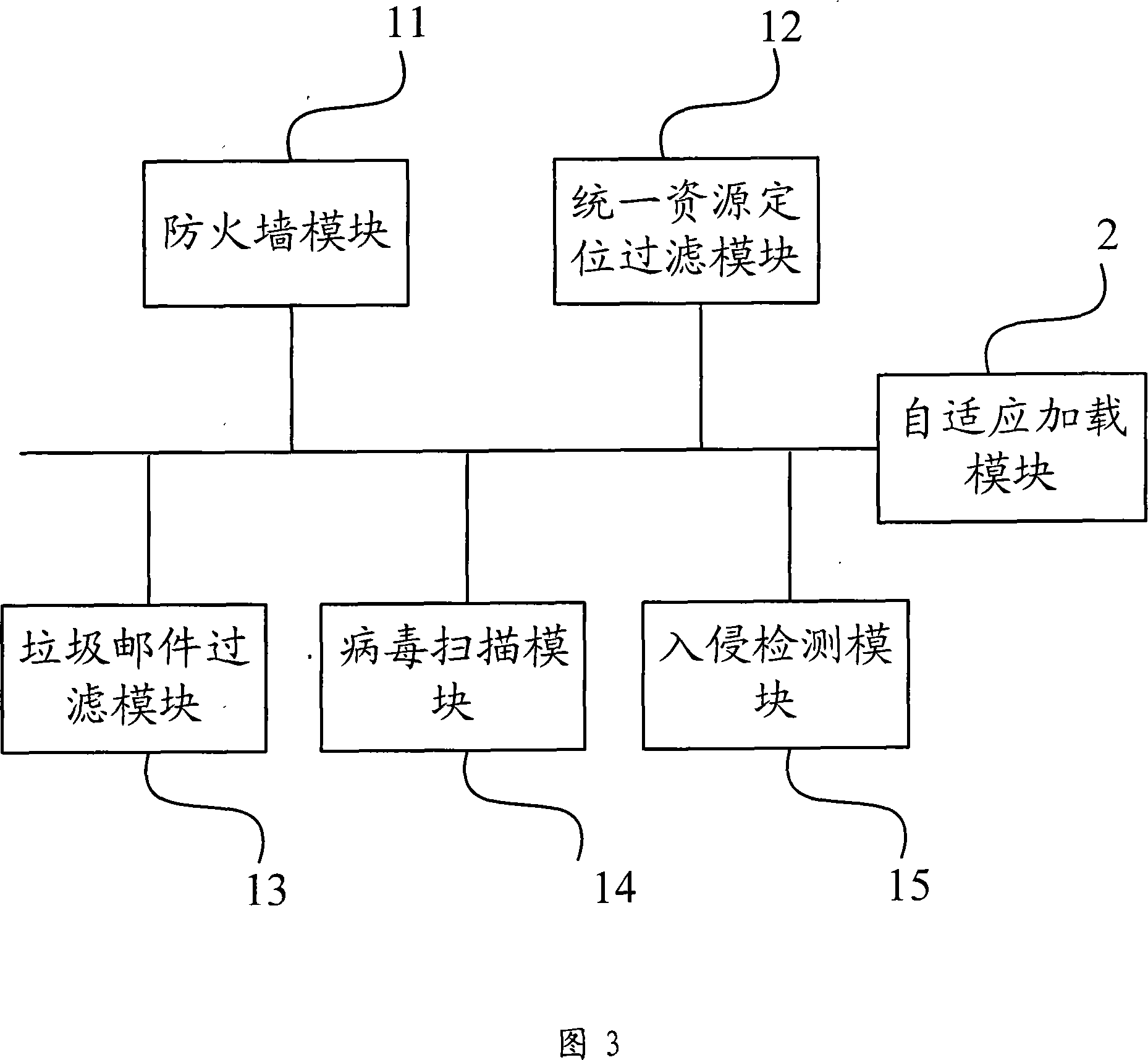
[0024] FIG. 2 is a schematic structural diagram of a unified threat management device according to an embodiment of the present invention. include:
[0025] At least one threat defense module 1 is used to perform security detection on the message;
[0026] The adaptive loading module 2 is configured to dynamically load the threat defense module 1 according to the processing performance information of the unified threat management device.
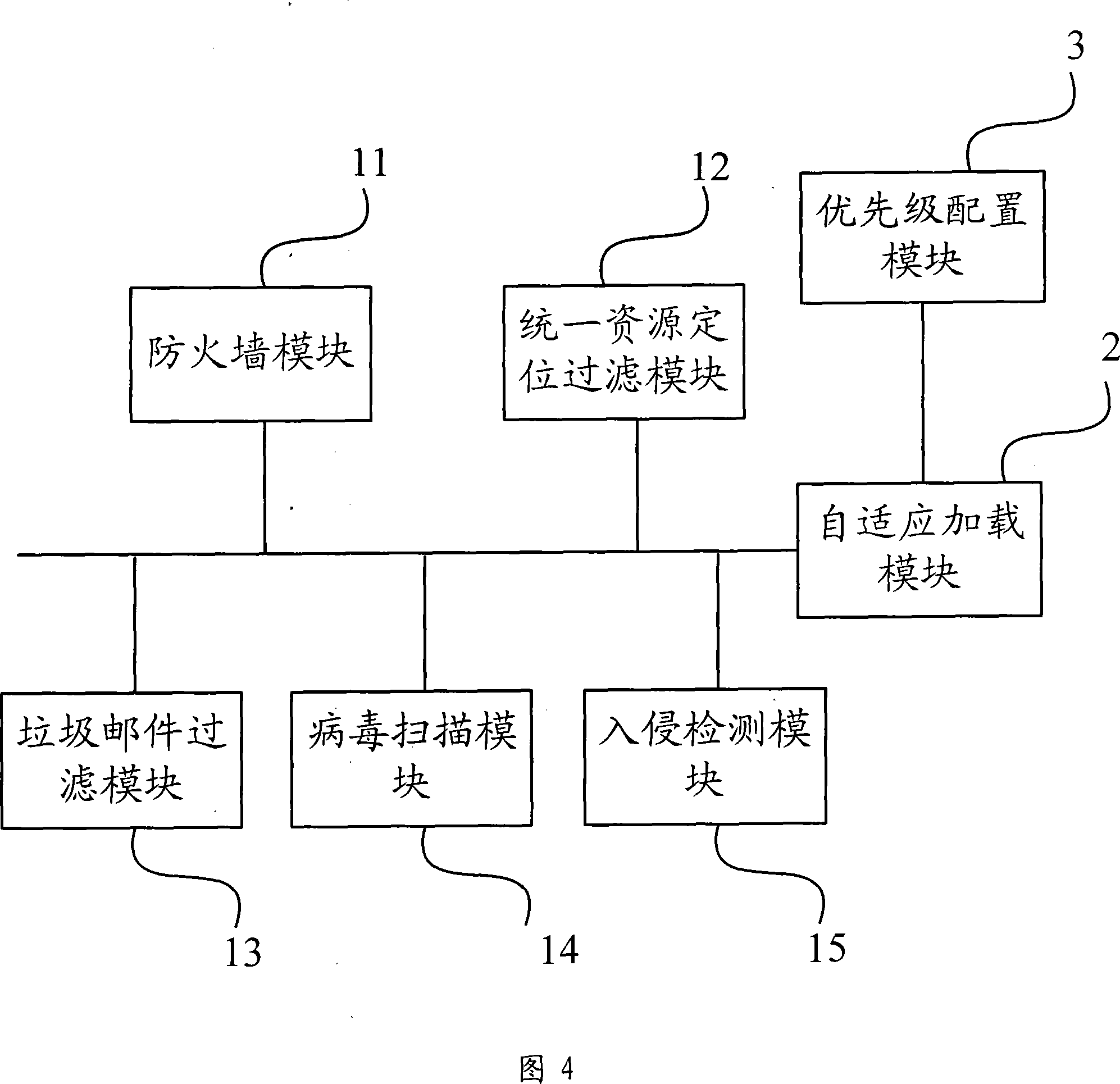
[0027] As shown in FIG. 3 , the threat defense module 1 in the embodiment of the present invention can be any multiple of a firewall module 11 , a URL filtering module 12 , a spam filtering module 13 , a virus scanning module 14 , and an intrusion detection module 15 . The types and combinations of threat defense modules can be loaded according to actual needs, and this embodiment onl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com