Unified authentication method for simulation identity
An authentication method and identity technology, applied in transmission systems, electrical components, etc., can solve problems such as the inability to quickly determine the responsible person, the inability to track users, the lack of user identification and authentication mechanisms, etc., and achieve the effect of improving the ability to guarantee services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
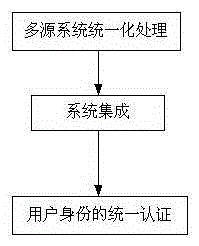
[0085] figure 1 A schematic flow chart of the unified authentication method for simulated identity provided in this embodiment, as shown in figure 1 As shown, a unified authentication method for simulated identity, the method includes the following steps:
[0086] Step 1, unified processing of multi-source systems: transform the interfaces of application systems and / or business systems on multiple different platforms with unified functions to form a unified login authentication method;
[0087] Step 2, system integration: centrally manage all application systems and / or business systems after functional transformation, and provide a unified login platform for visiting users;
[0088] Step 3, unified authentication of user identity: the unified authentication platform conducts unified user authentication for all application systems and / or business systems.
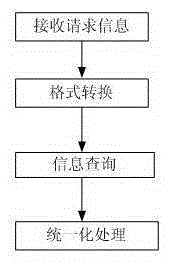
[0089] Such as figure 2 A unified authentication method for simulating identity is shown, wherein, the specific steps ...
Embodiment 2
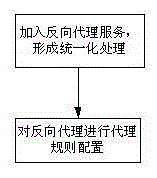
[0136] Figure 9 A schematic flow chart of the unified authentication method for simulated identity provided in this embodiment, as shown in Figure 9 As shown, a unified authentication method for simulated identity, the method includes the following steps:
[0137] Step 1, unified processing of multi-source systems: transform the interfaces of application systems and / or business systems on multiple different platforms with unified functions to form a unified login authentication method;
[0138] Step 2, system integration: centrally manage all application systems and / or business systems after functional transformation, and provide a unified login platform for visiting users;
[0139] Step 3, unified authentication of user identity: the unified authentication platform conducts unified user authentication for all application systems and / or business systems;
[0140] Step 4, multi-user system login processing: When multiple users log in to the system at the same time, the unif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com