Patents
Literature
352 results about "Time rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
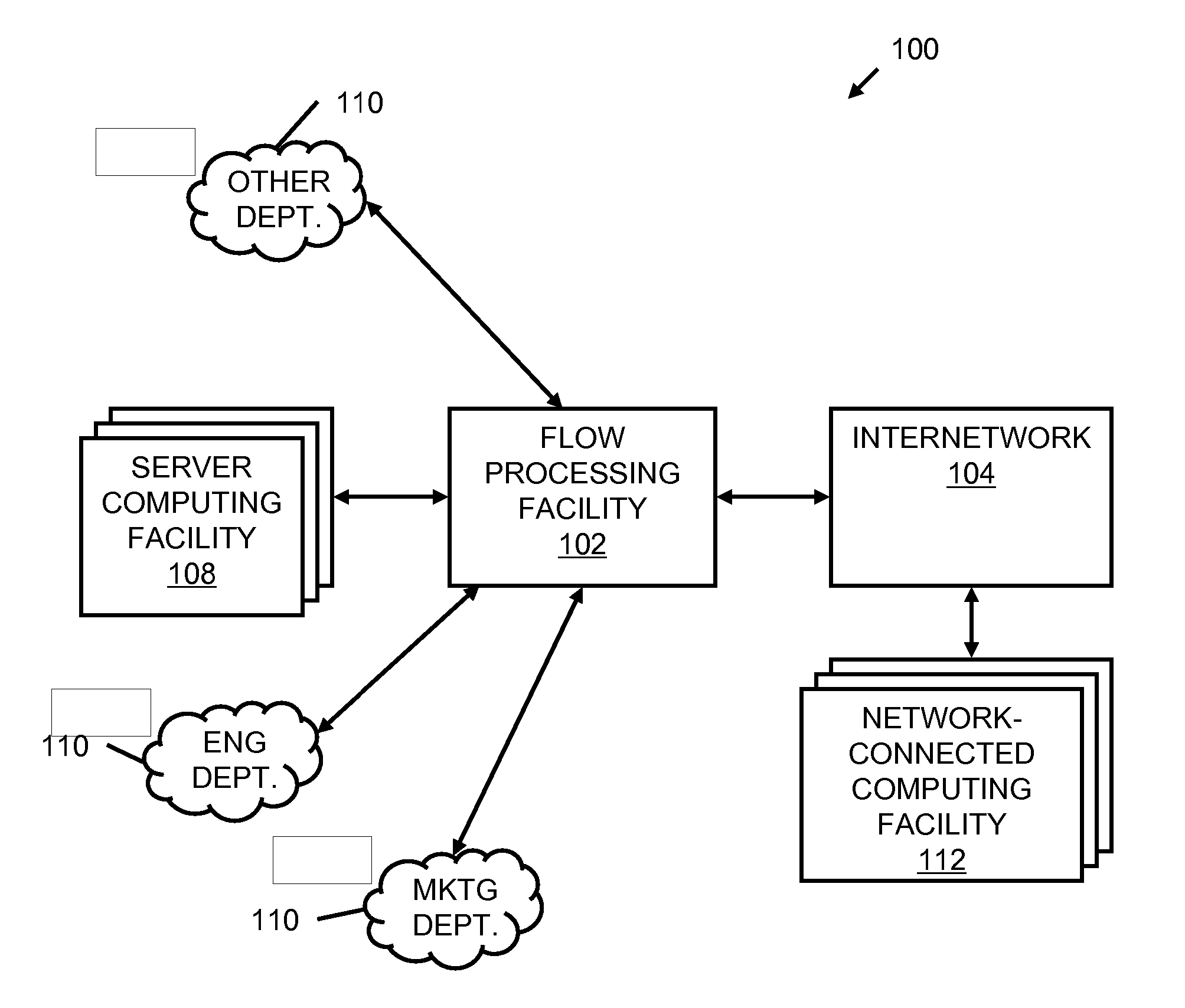
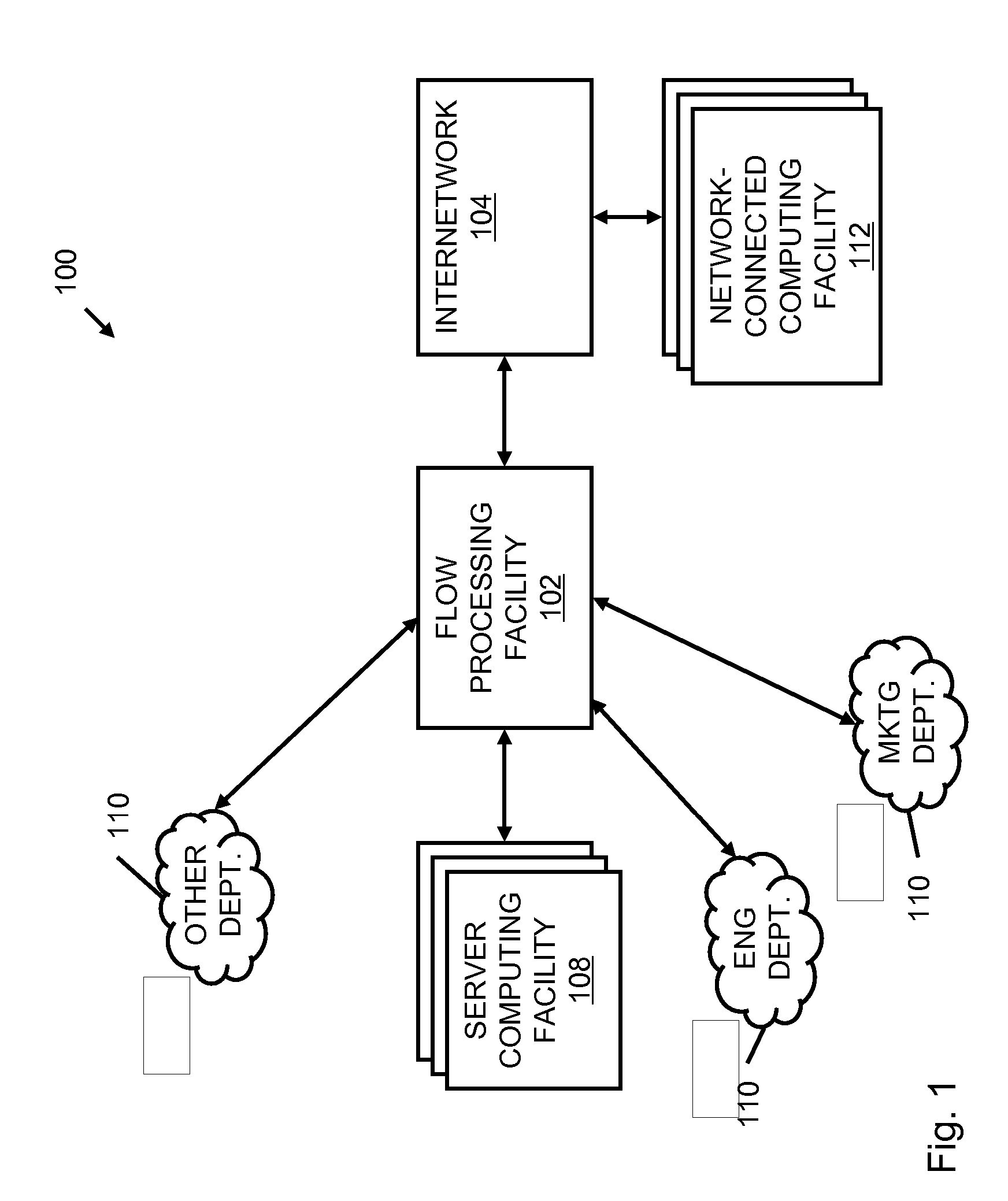
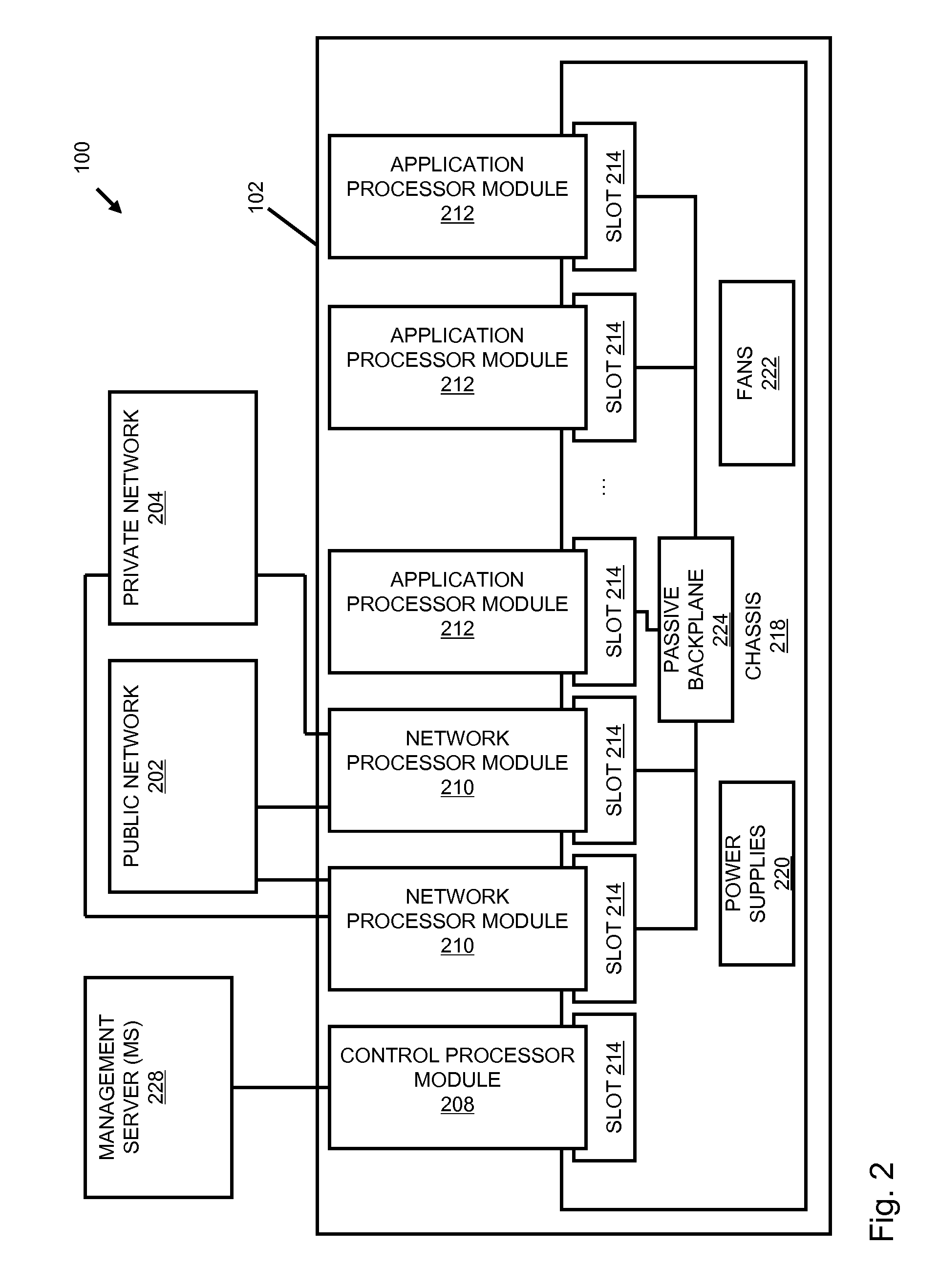
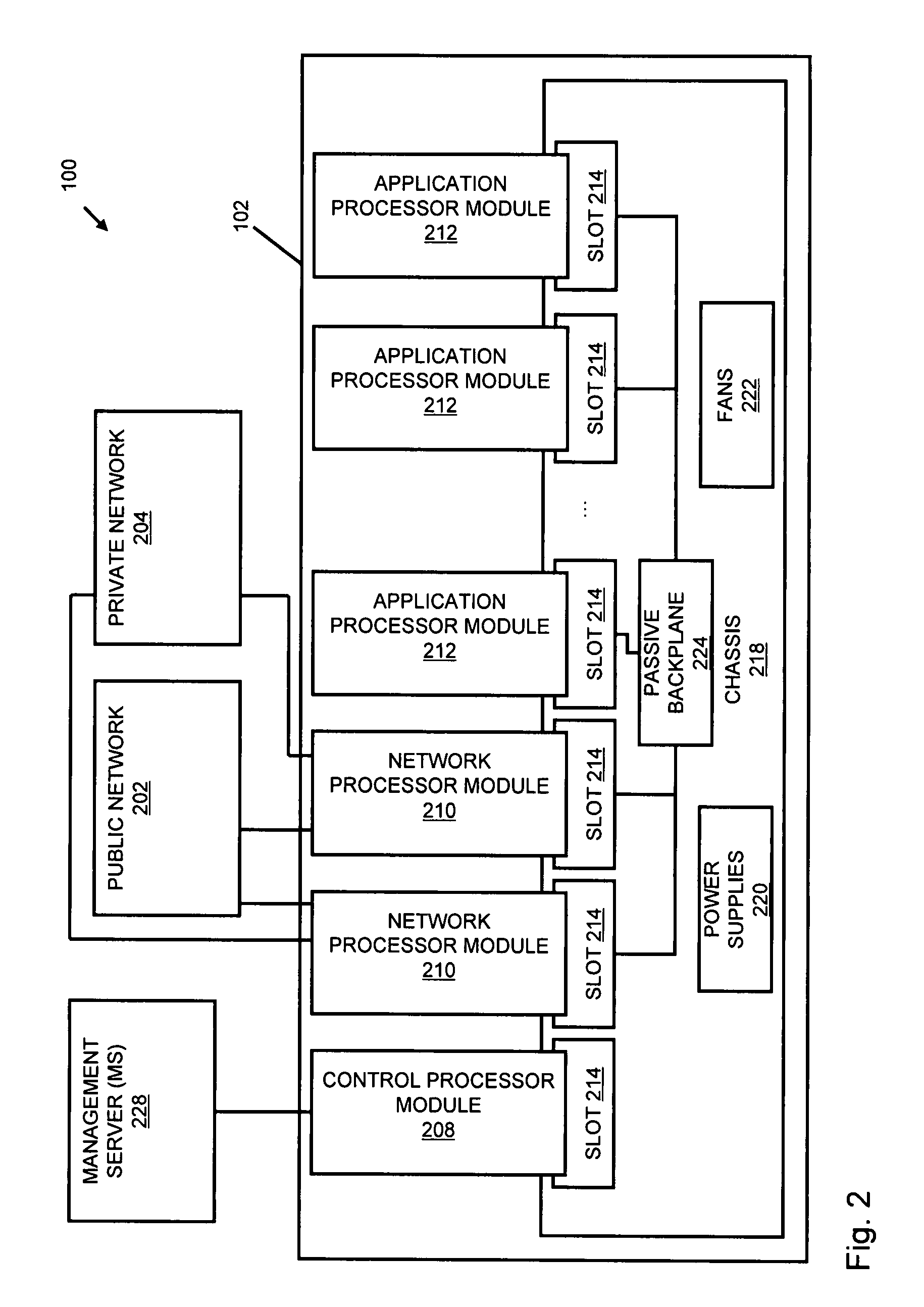
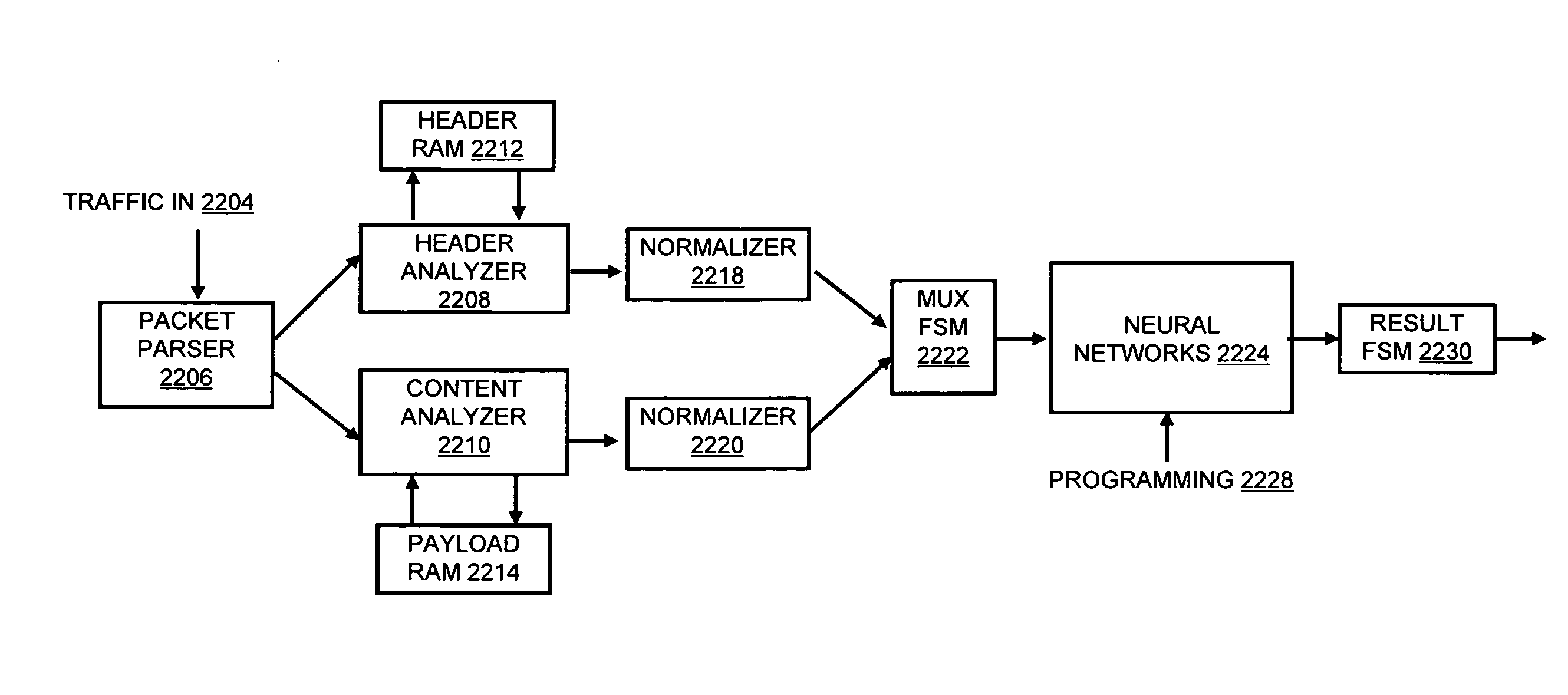
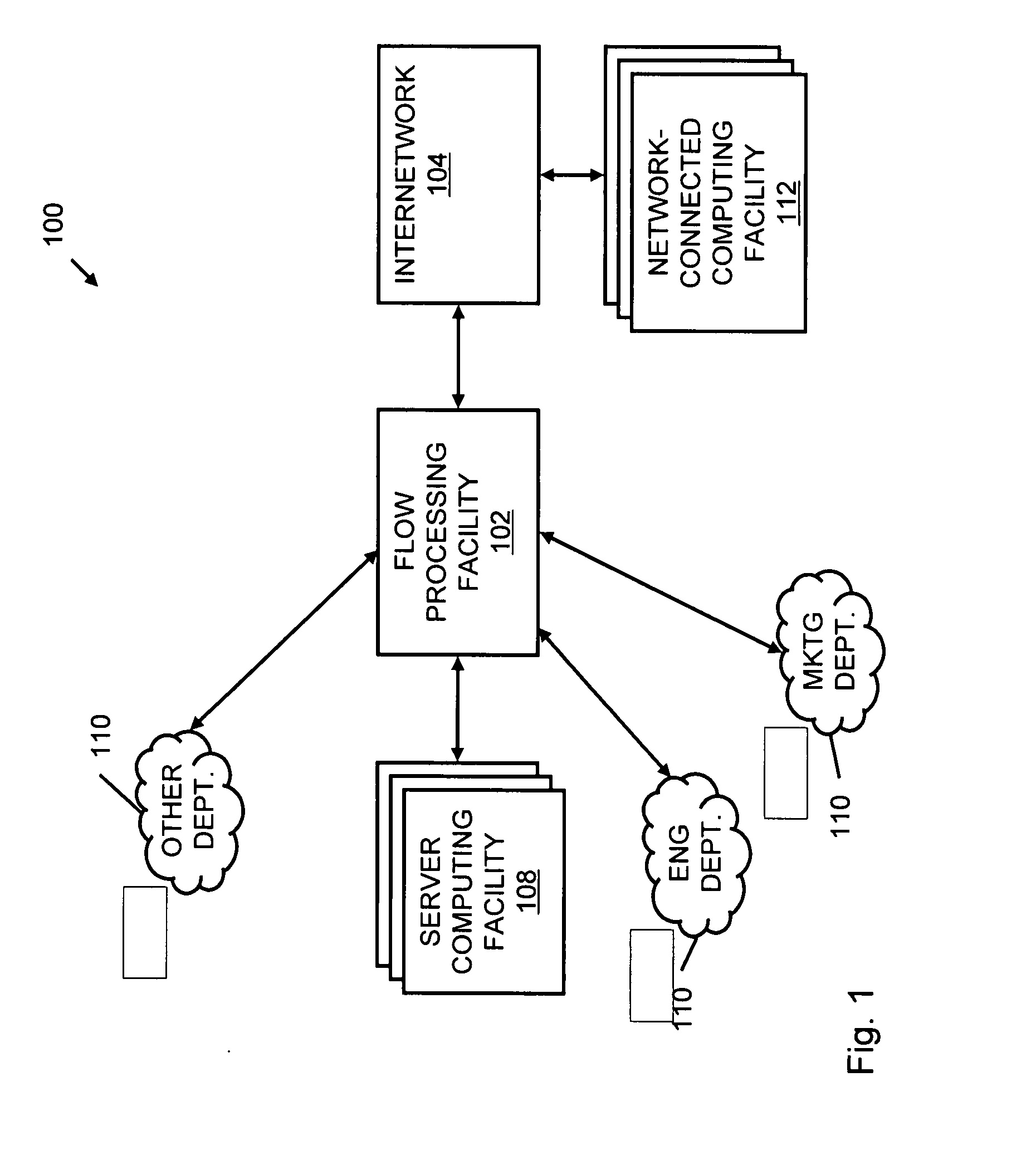
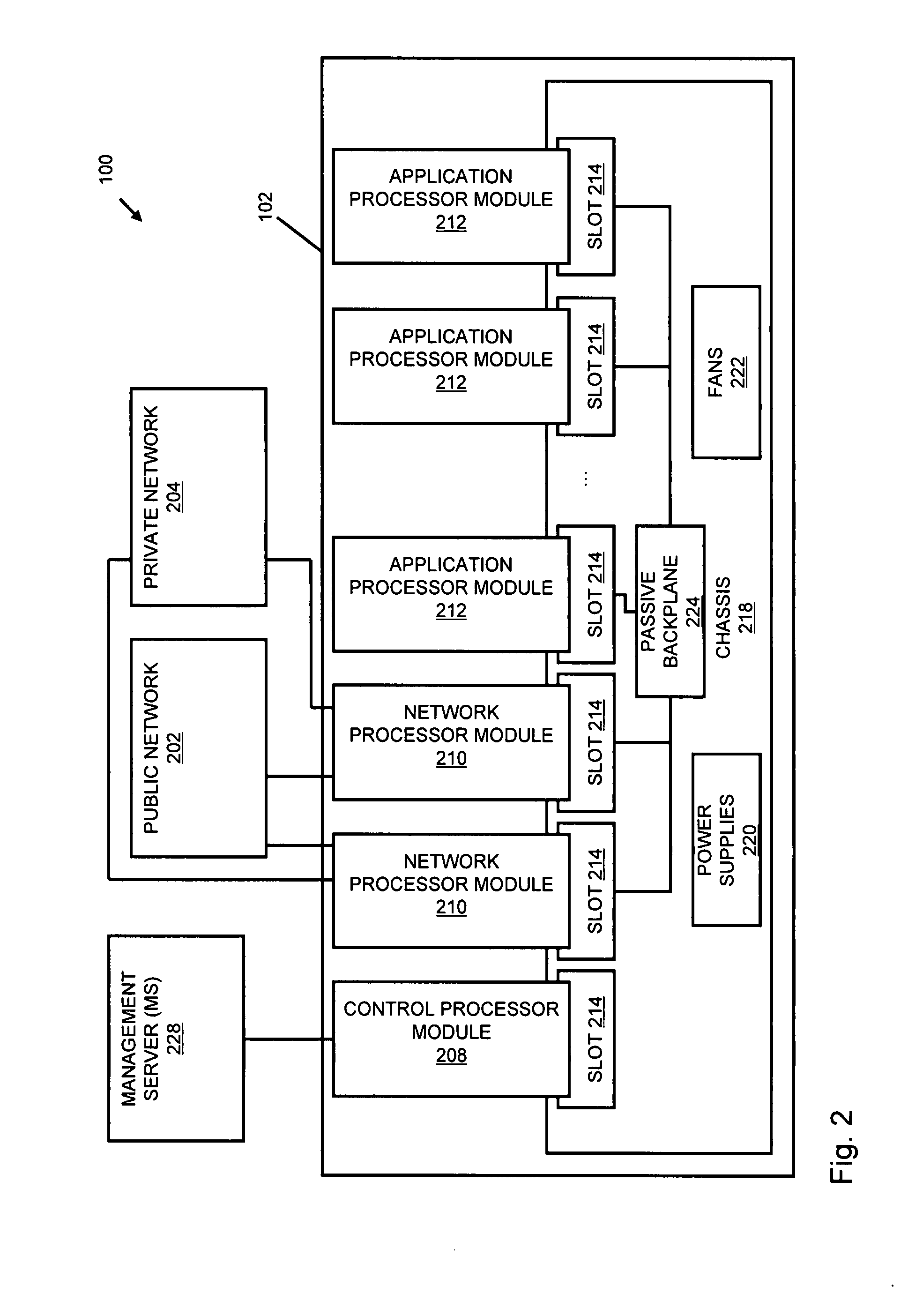
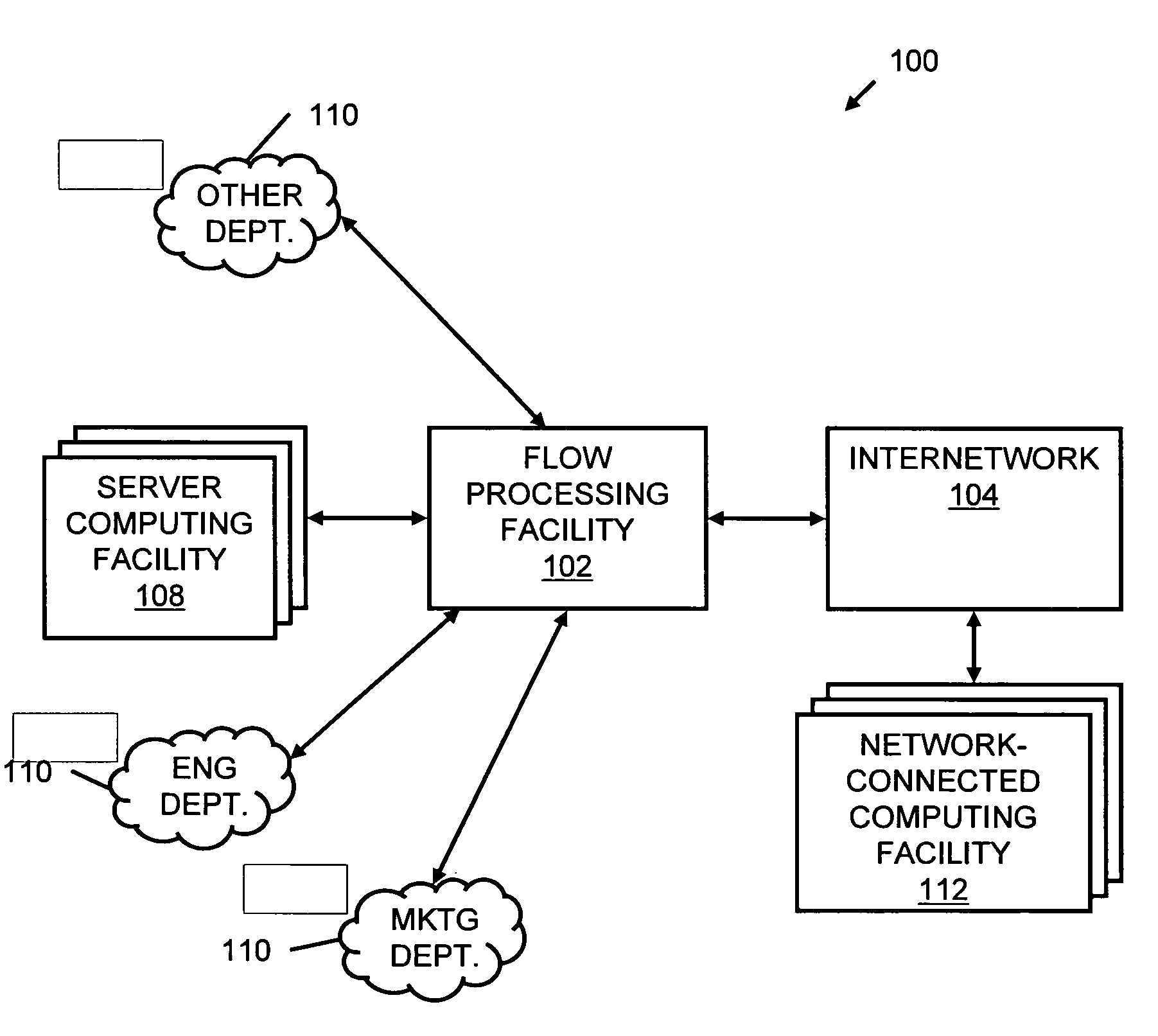
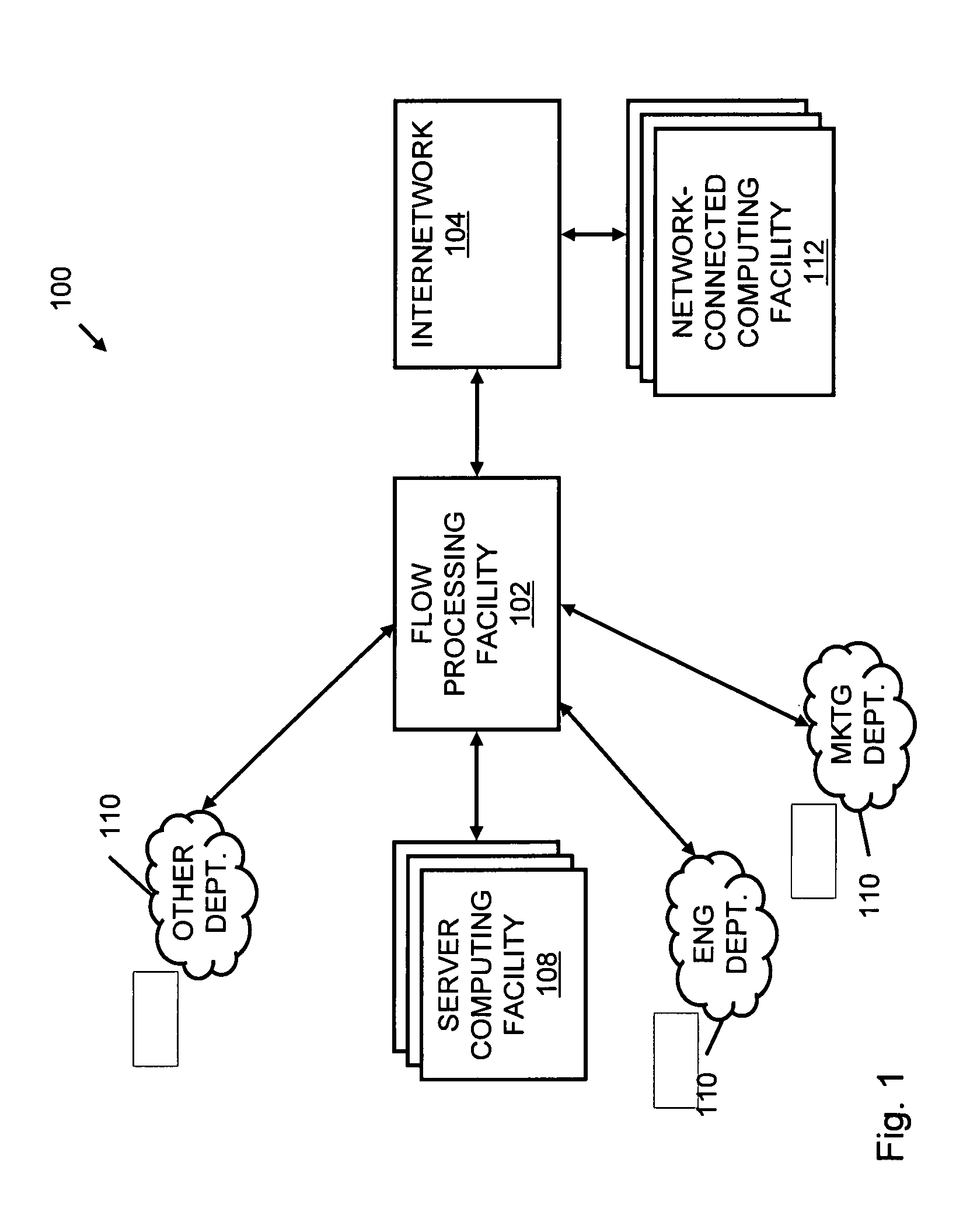
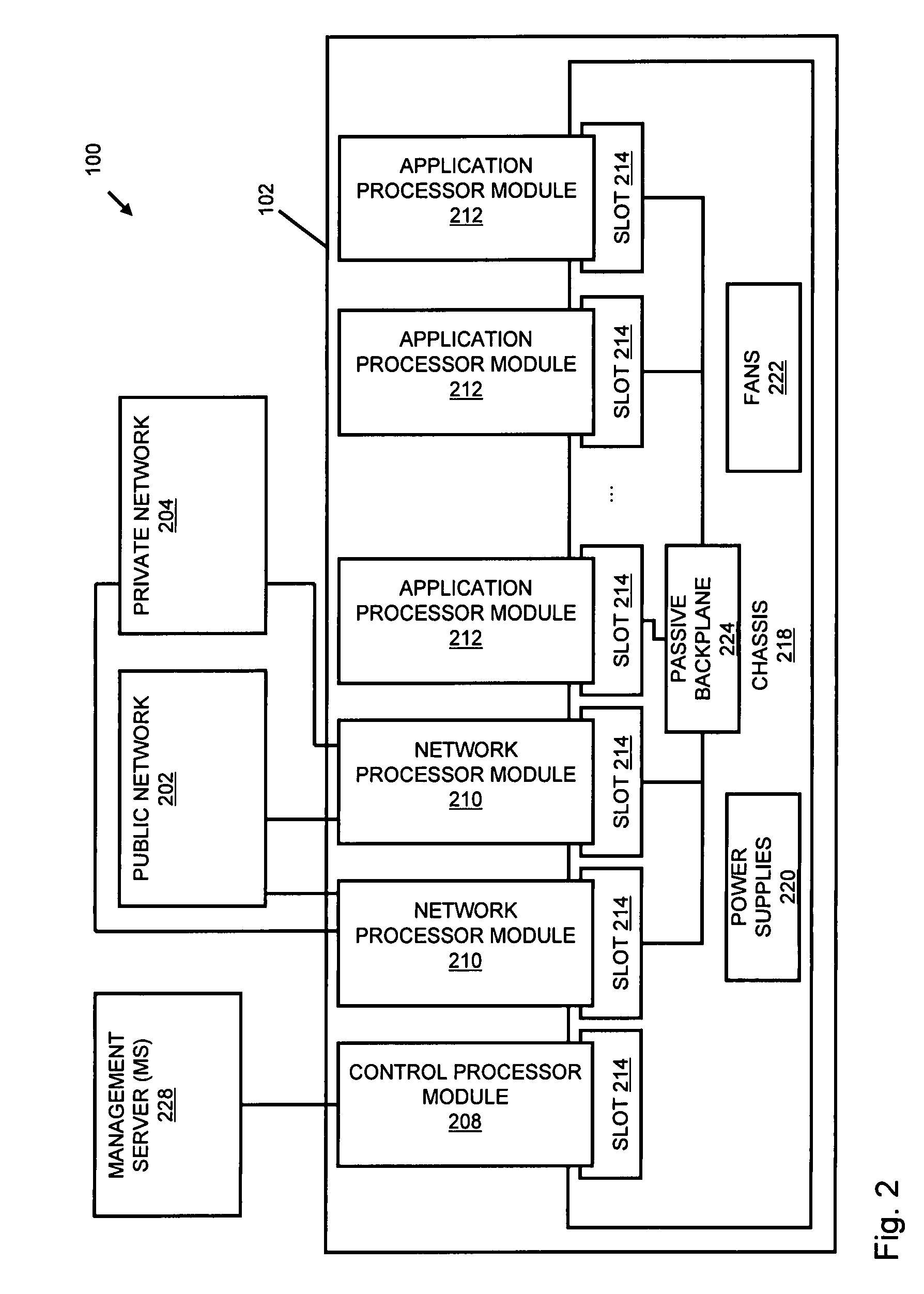
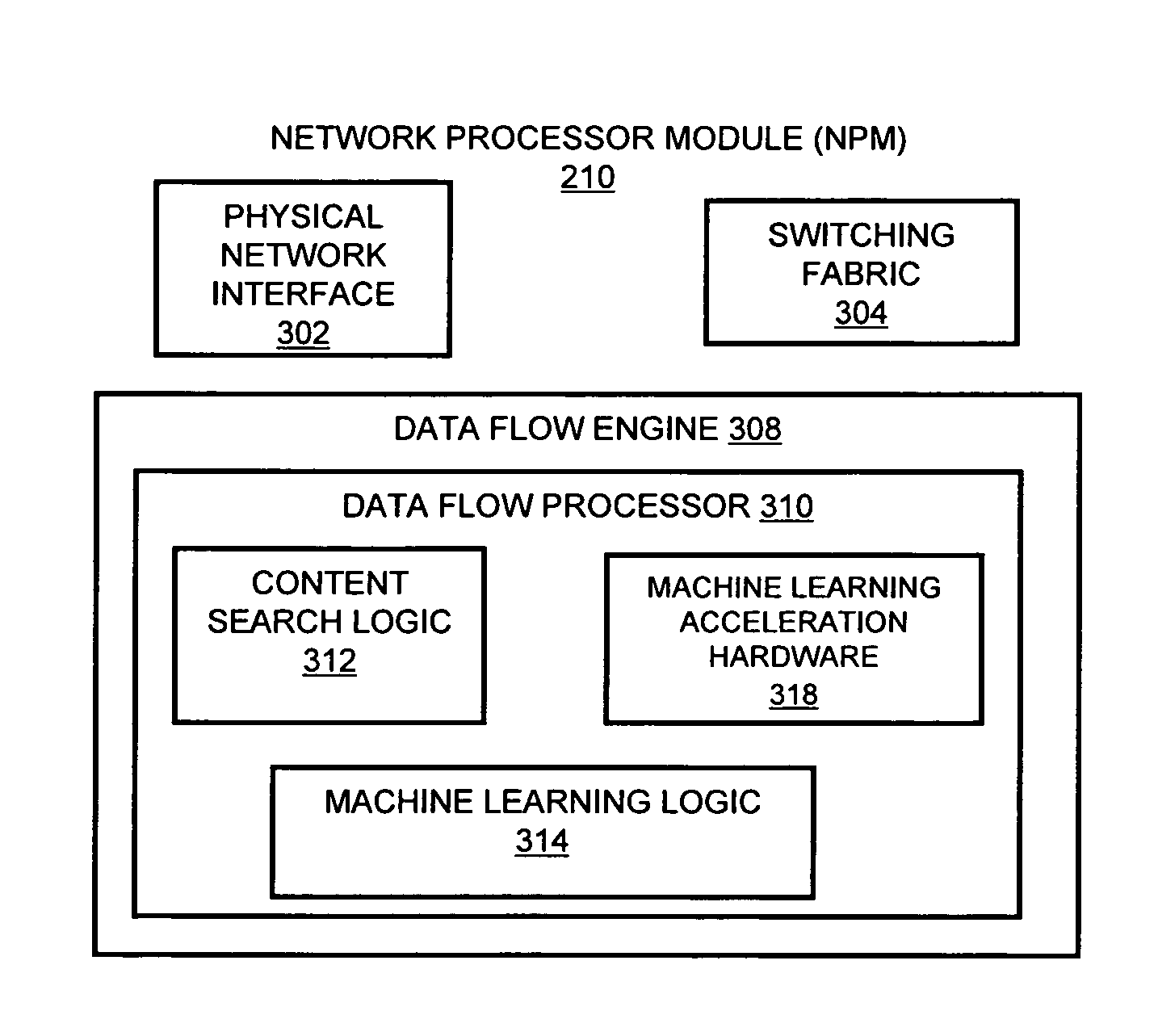
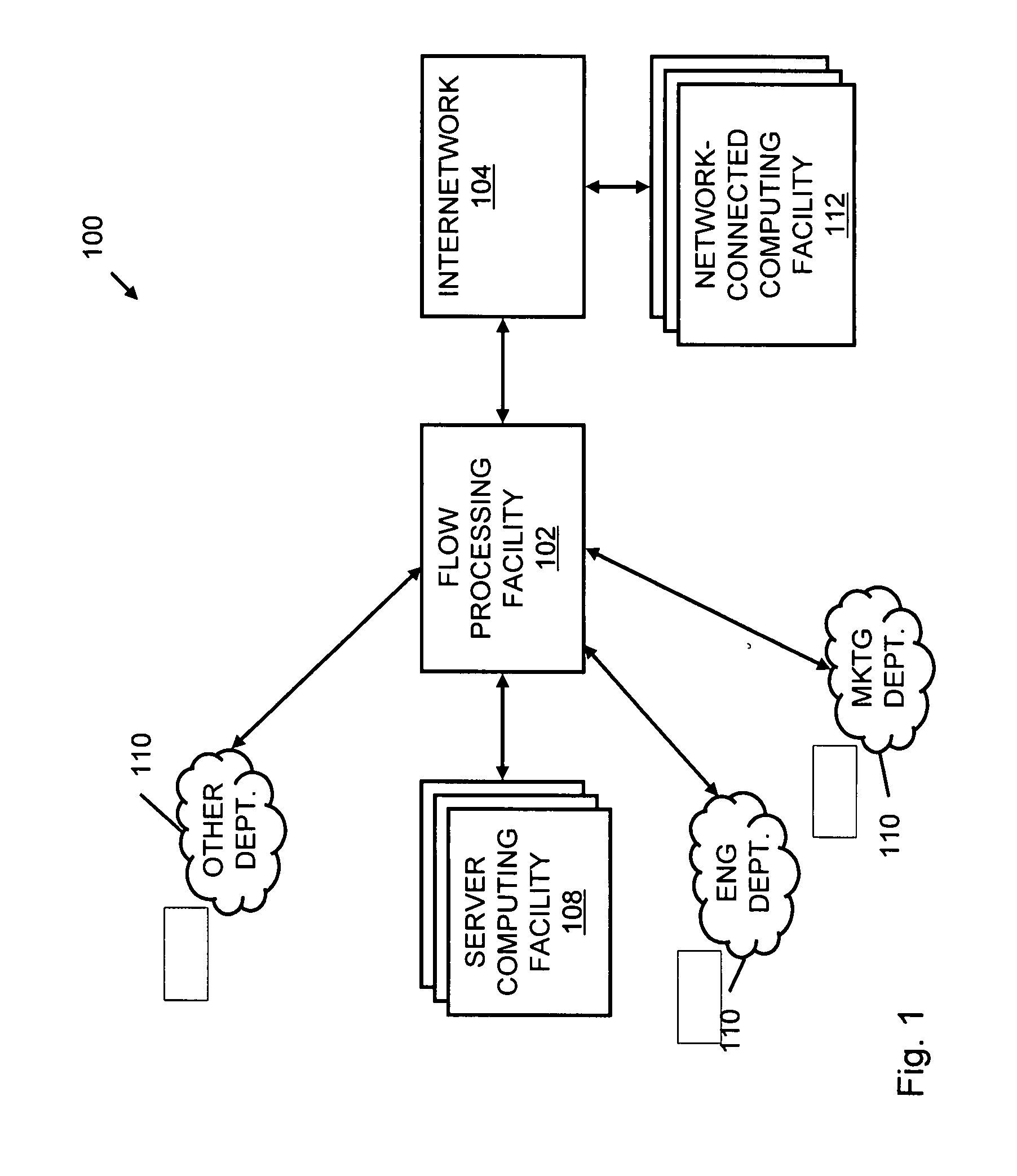
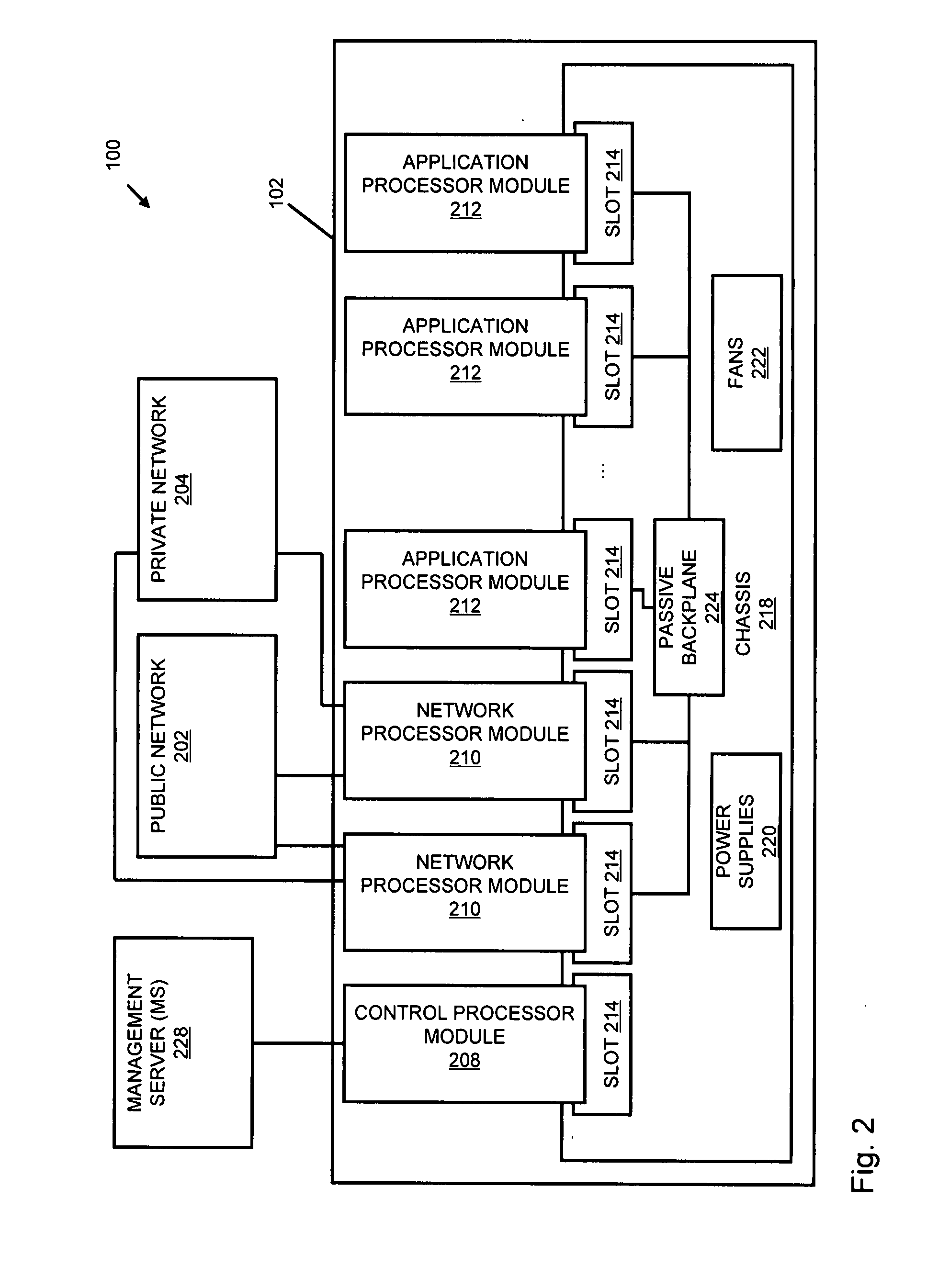
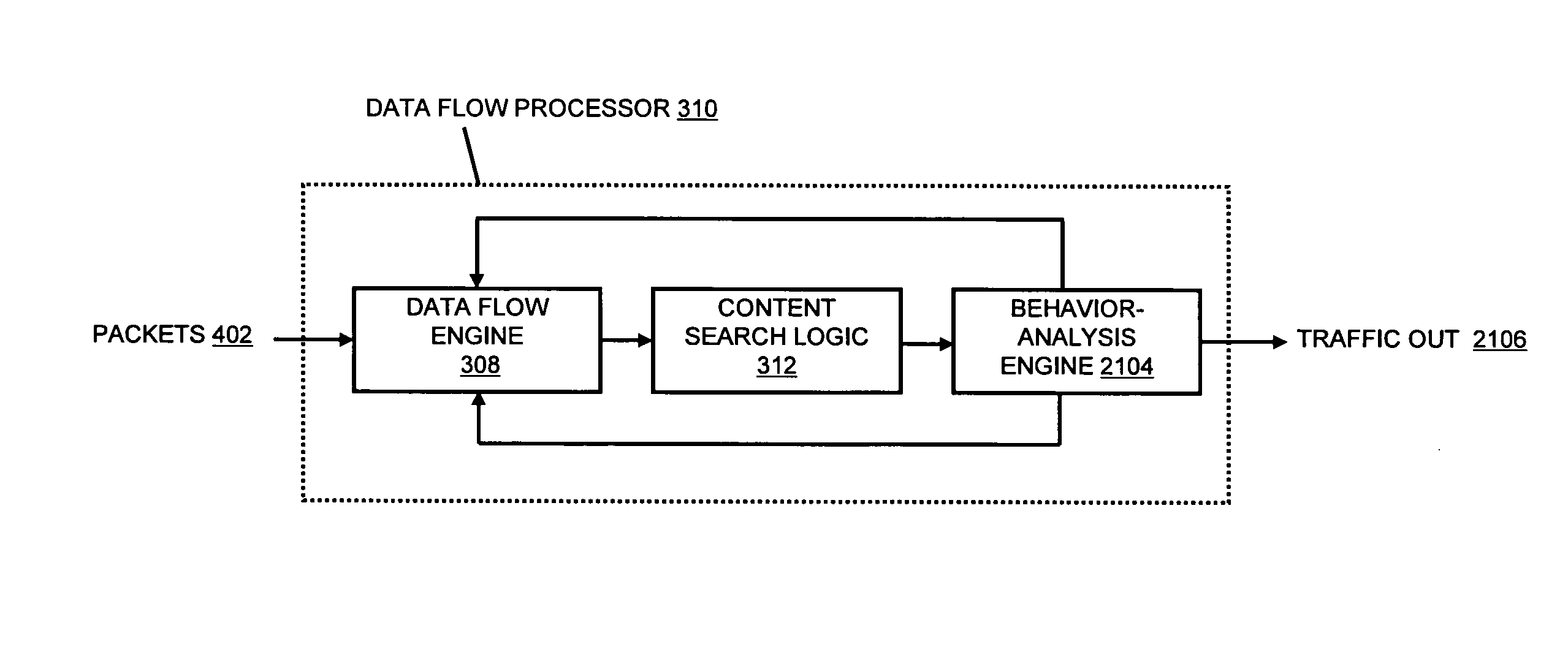
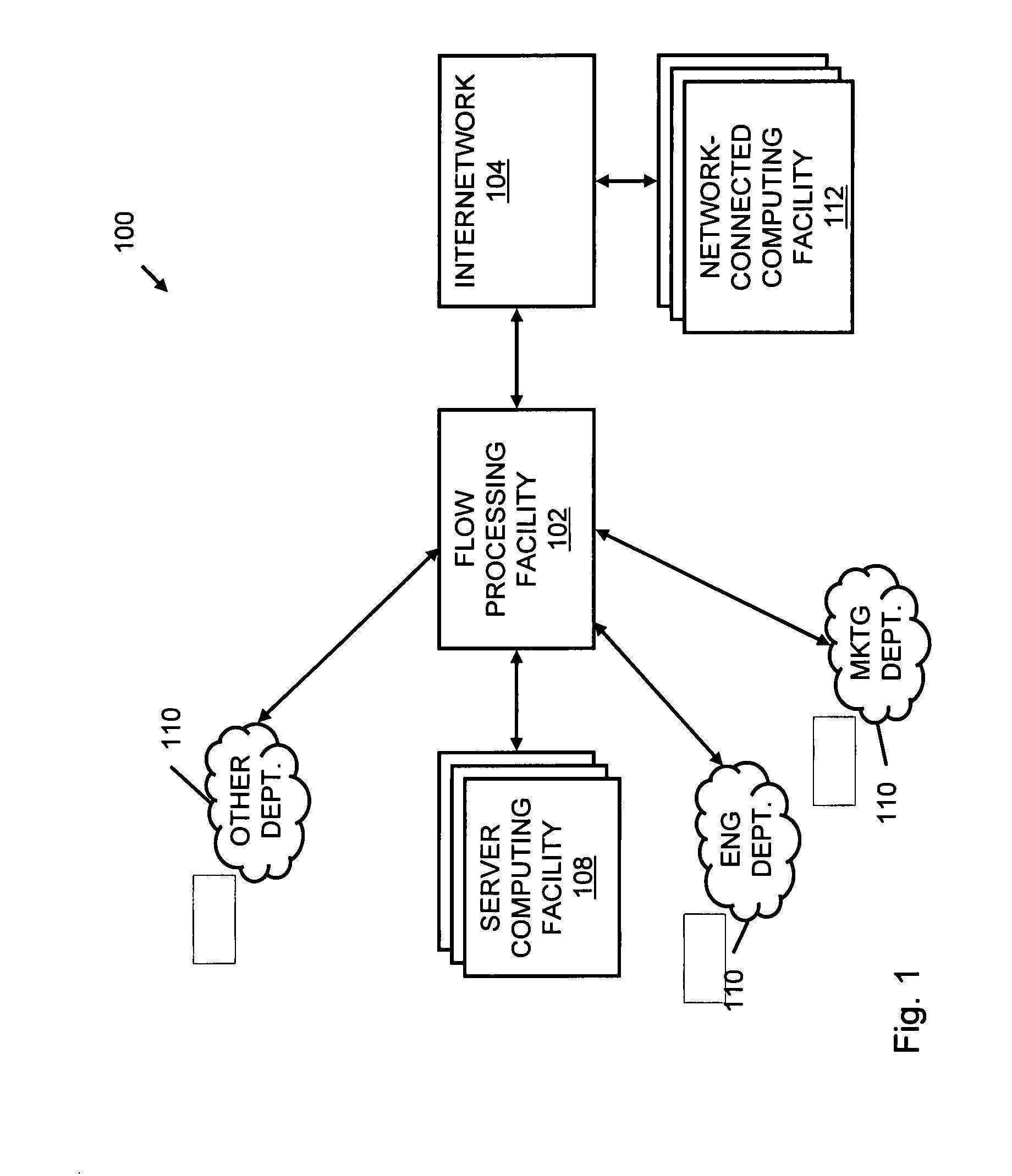
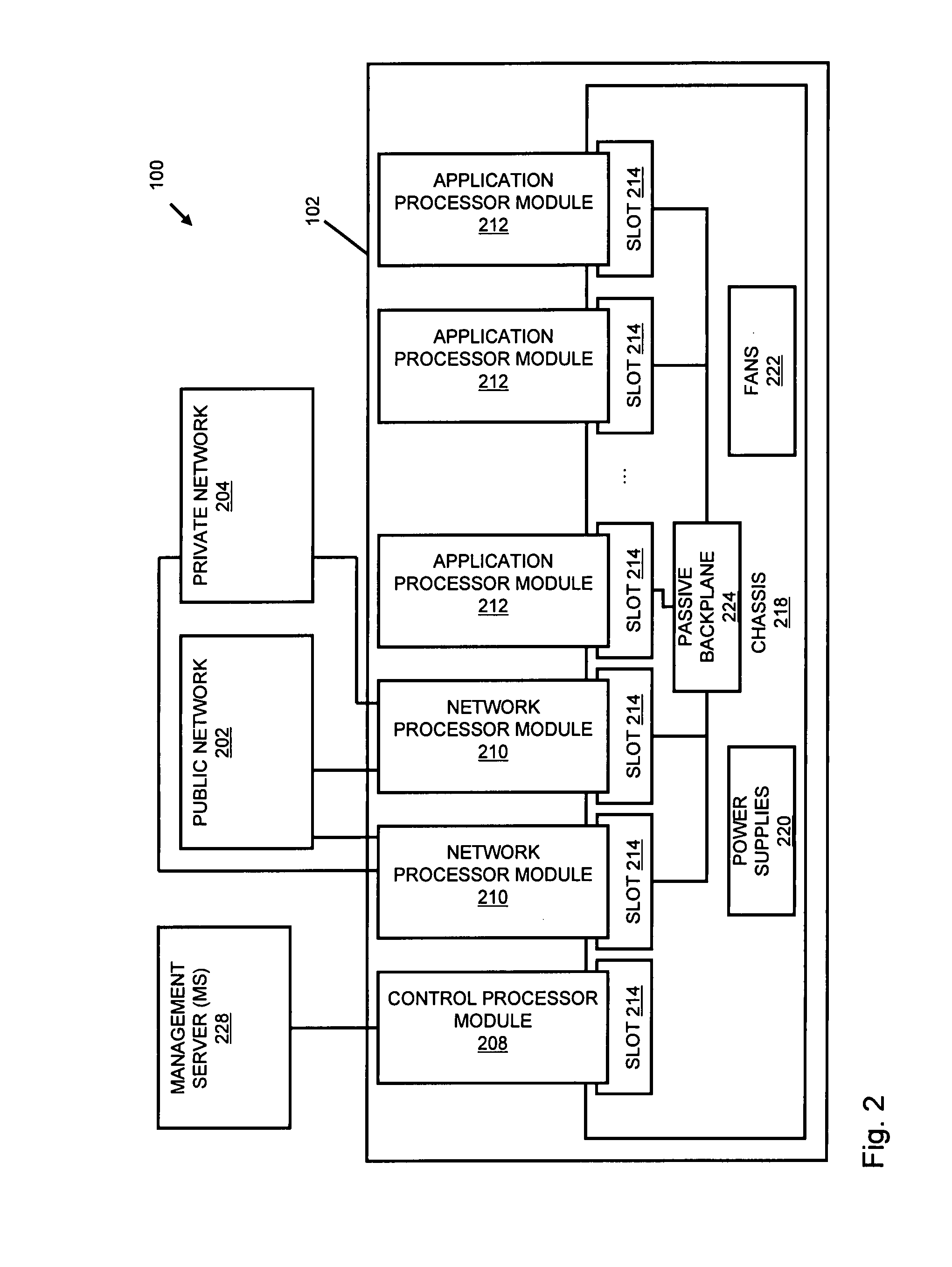
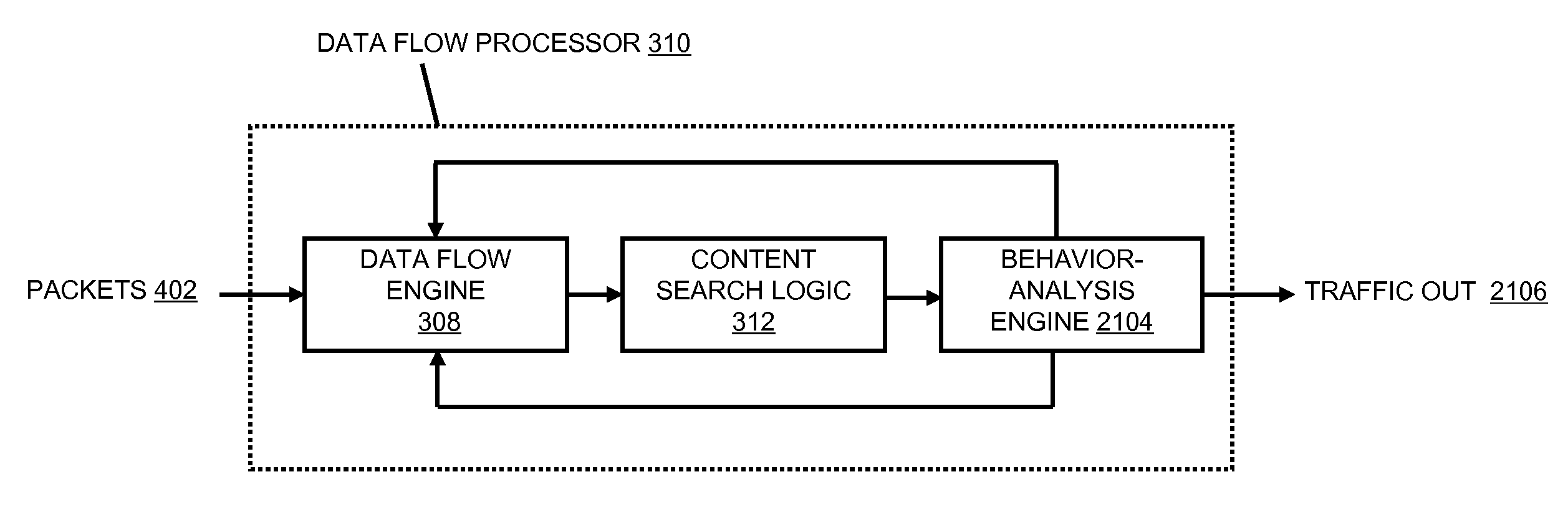
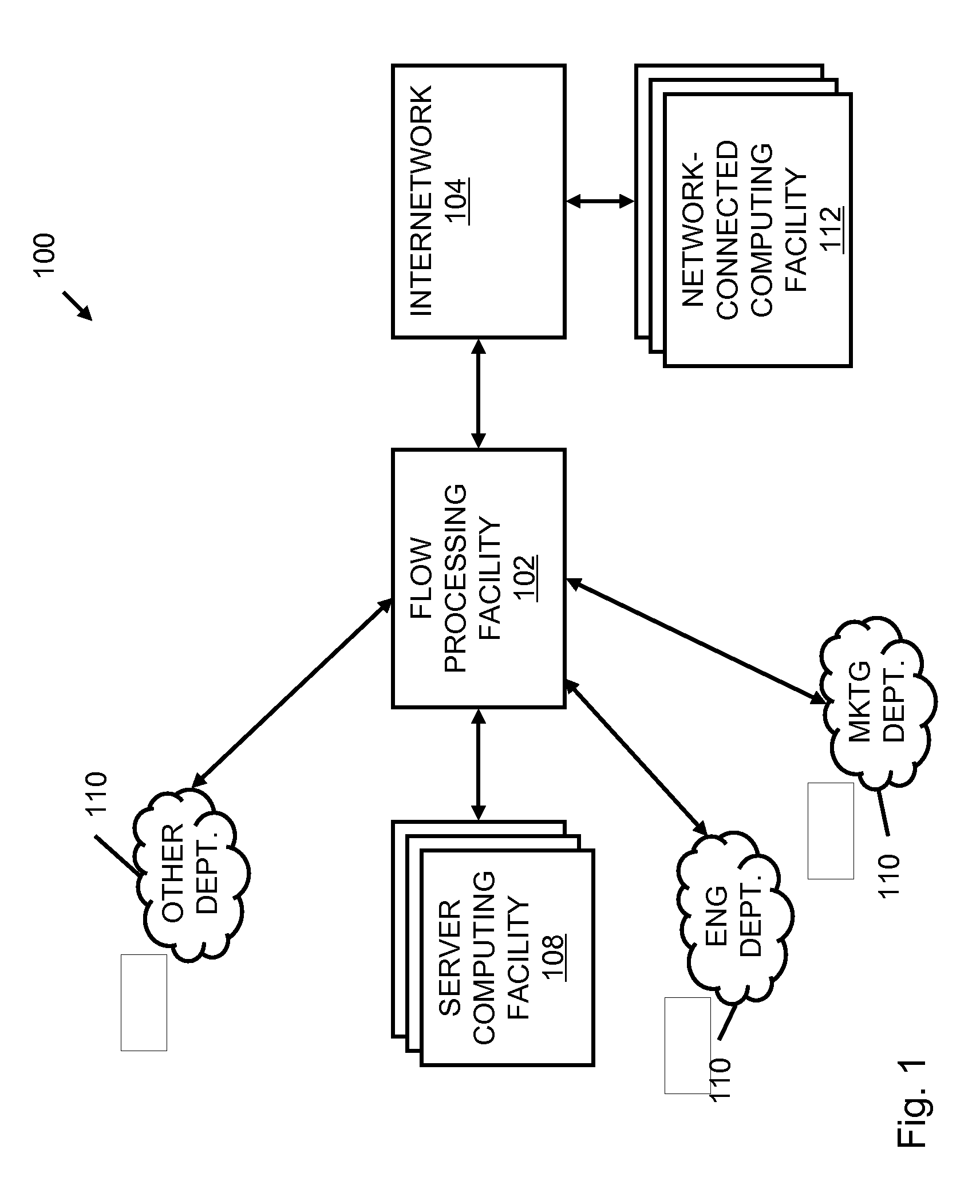
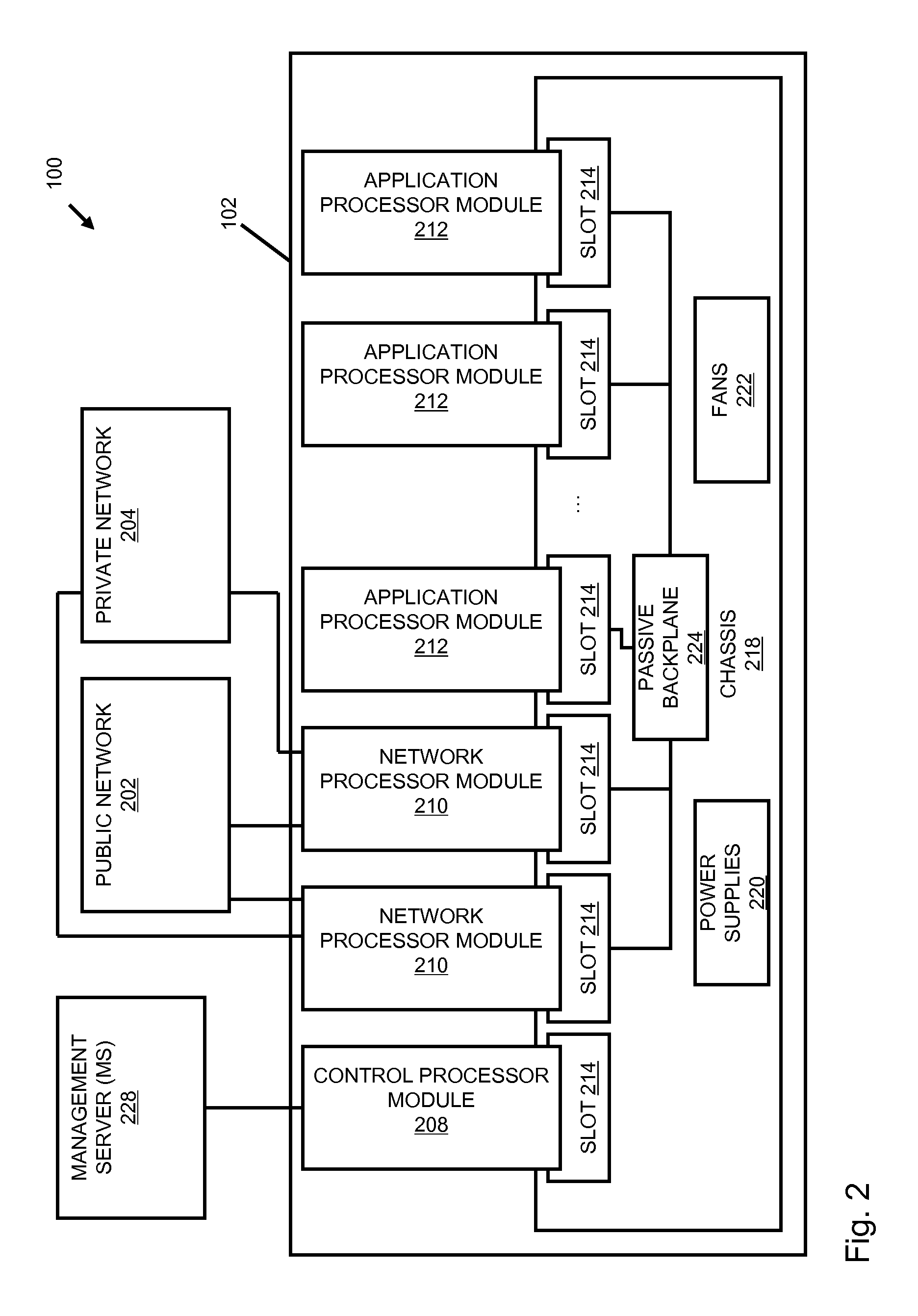
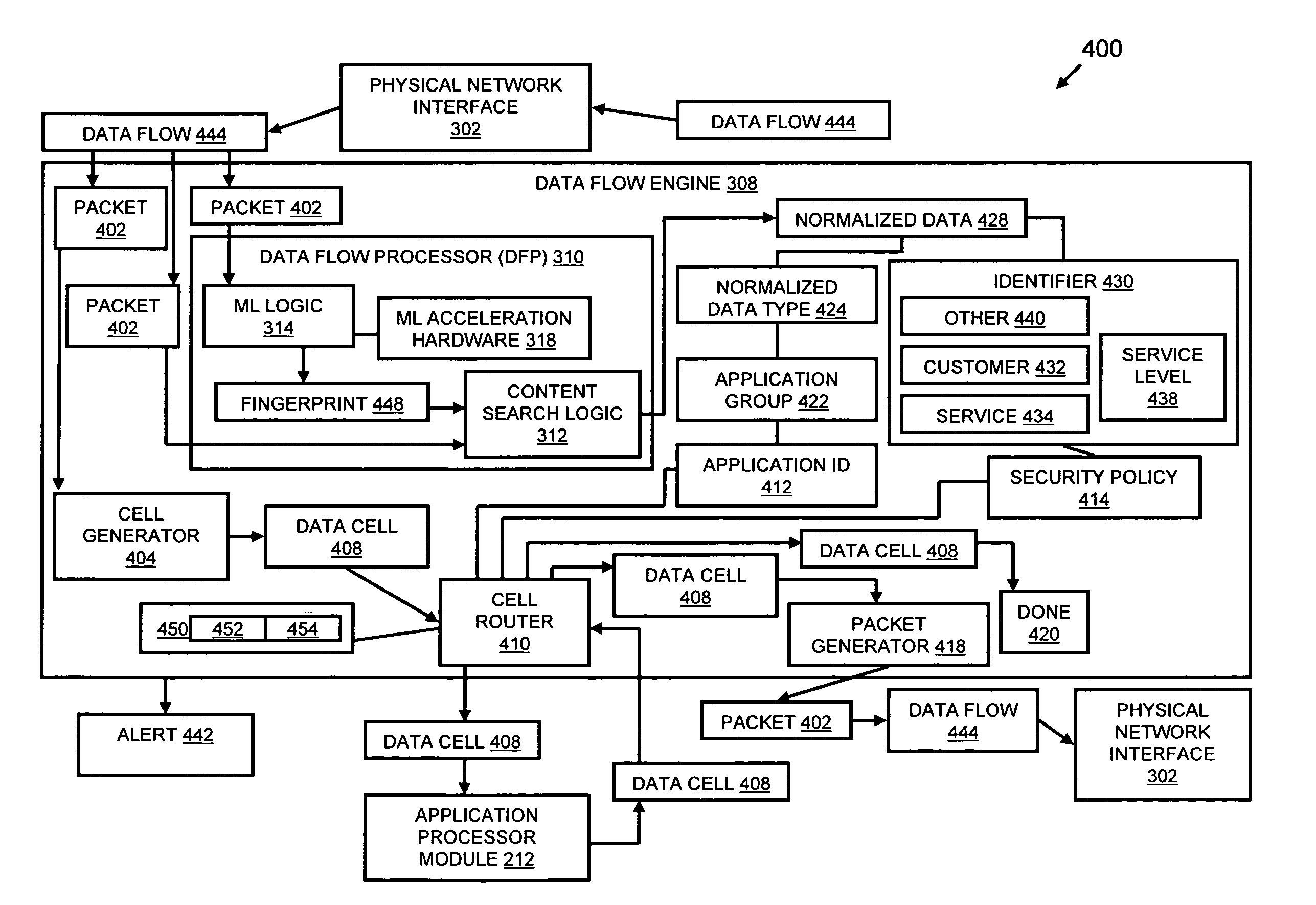
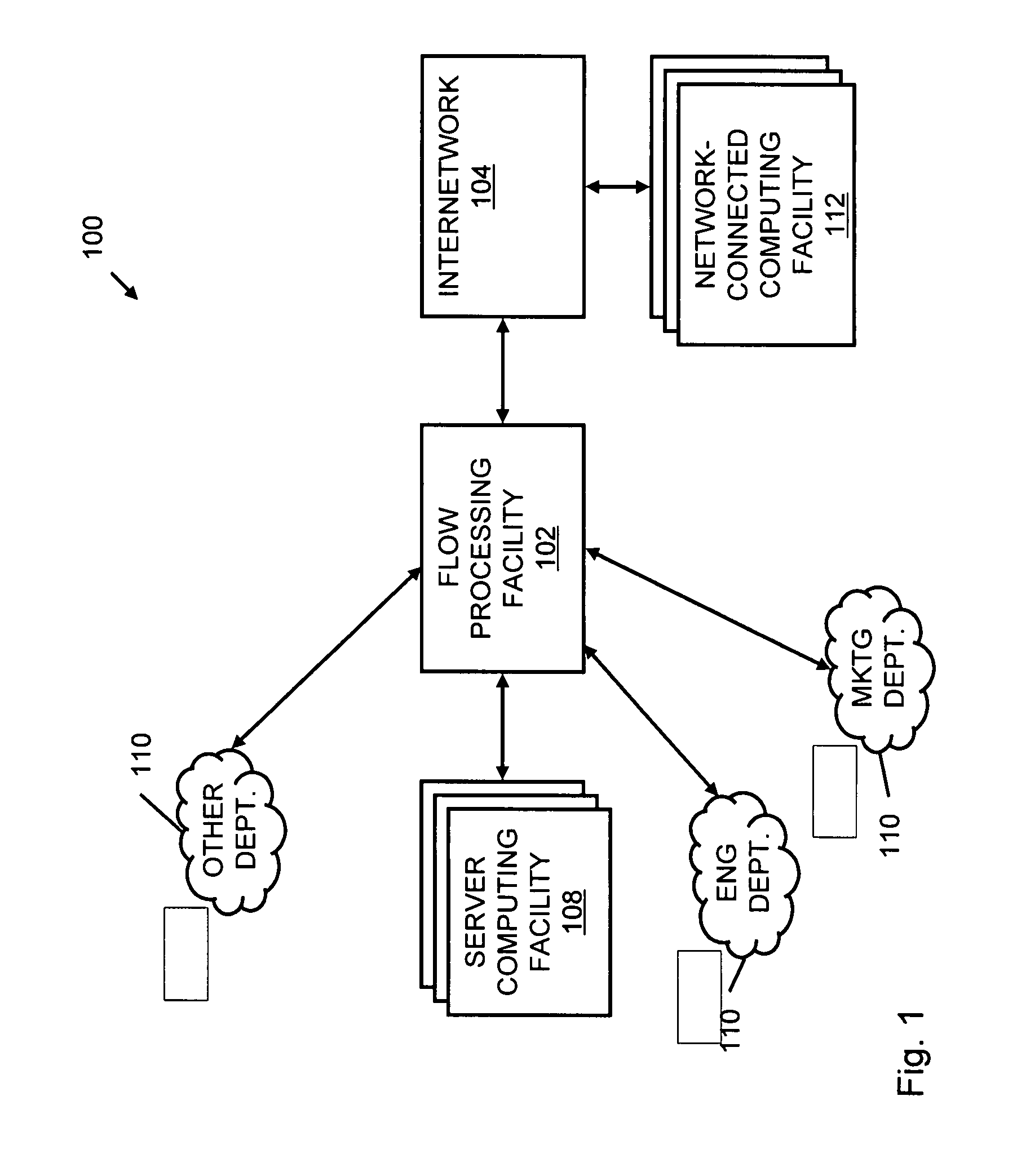
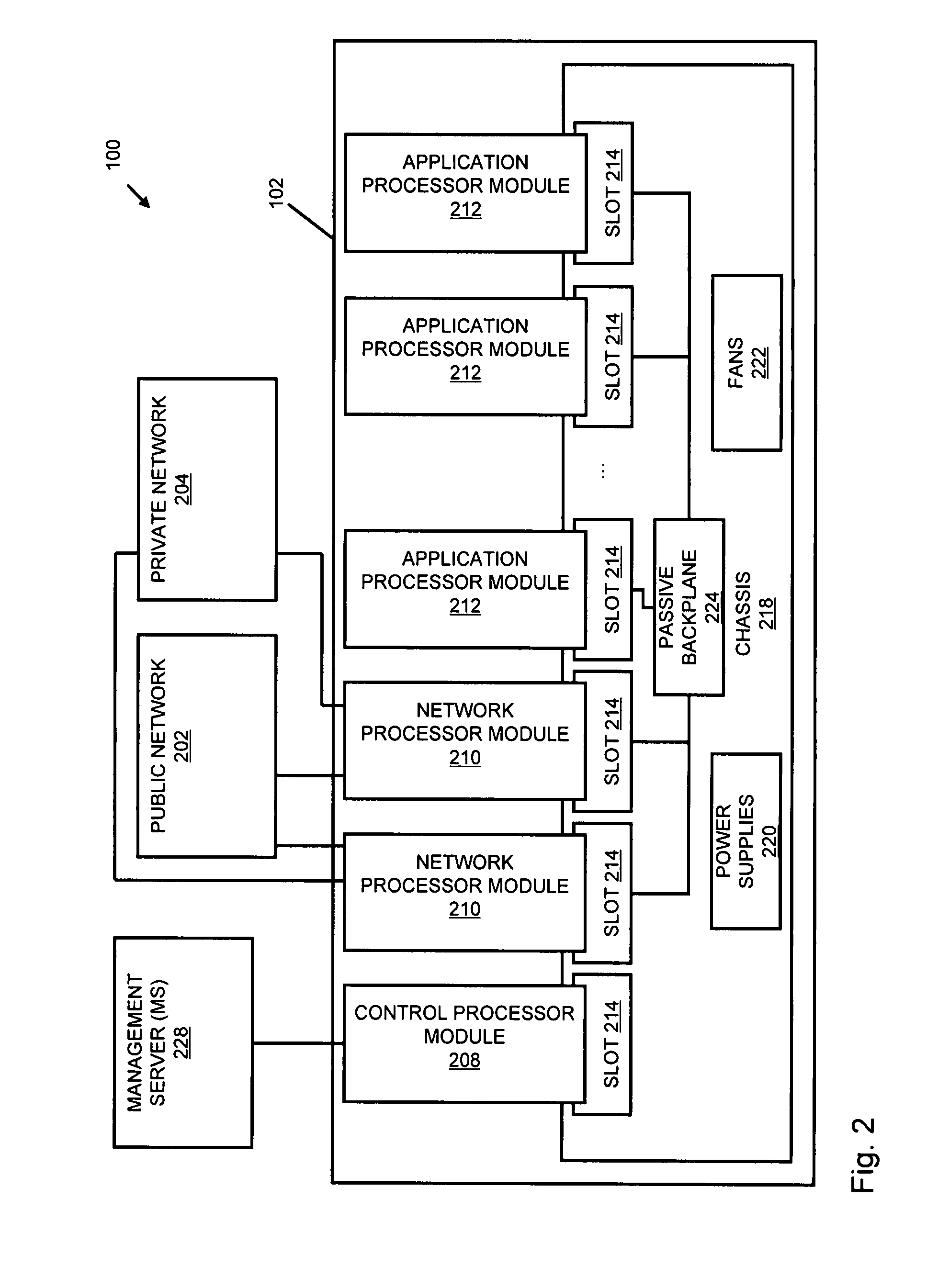
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
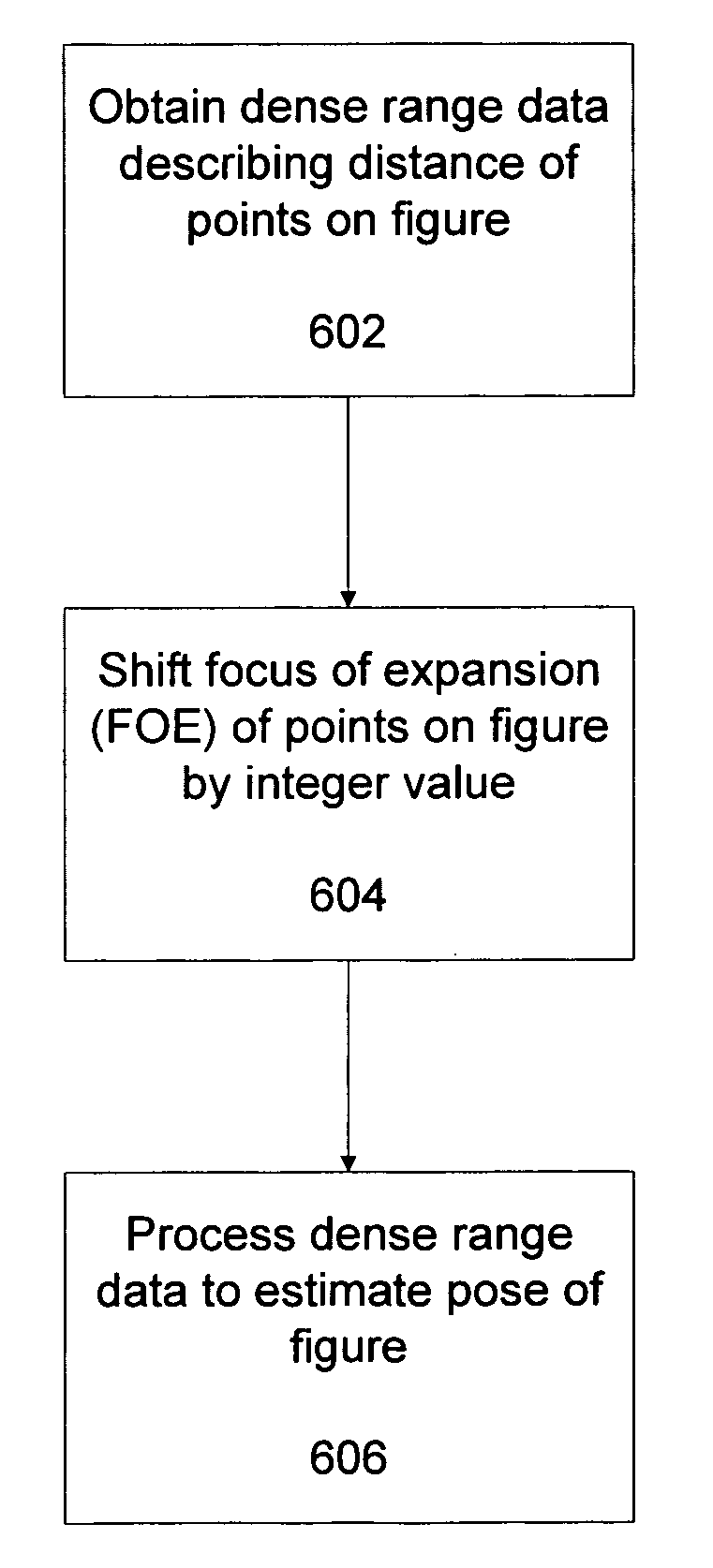
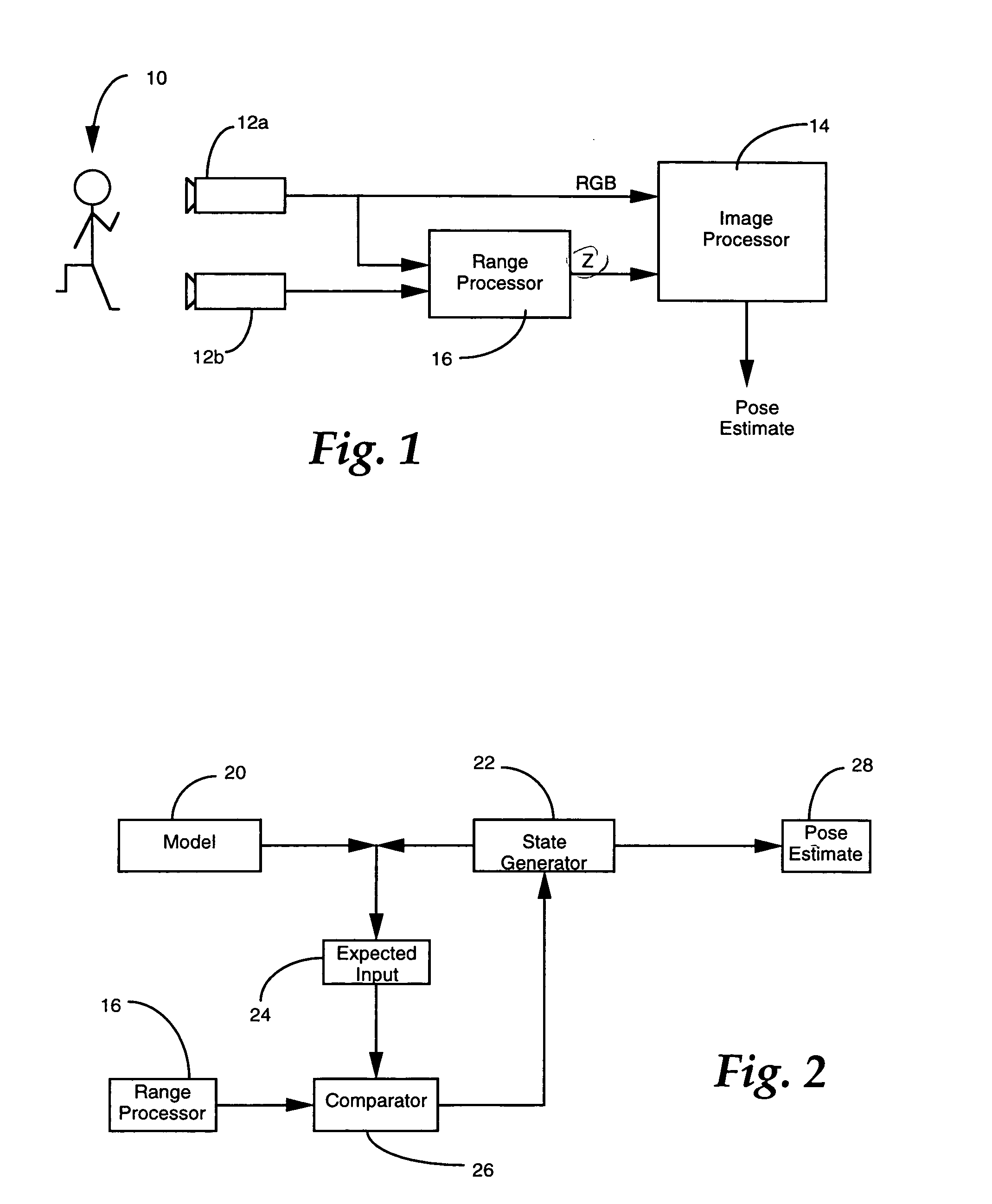
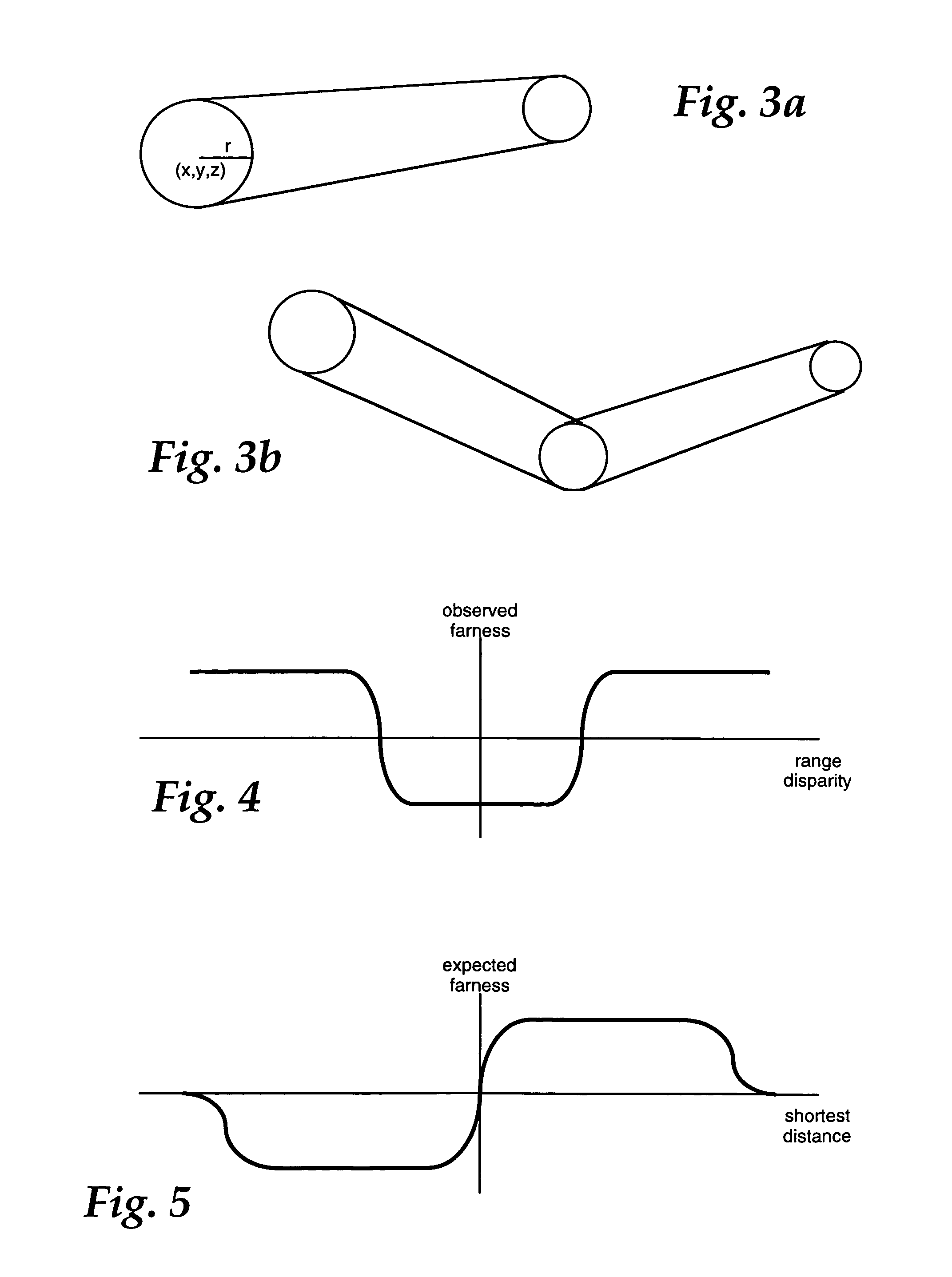
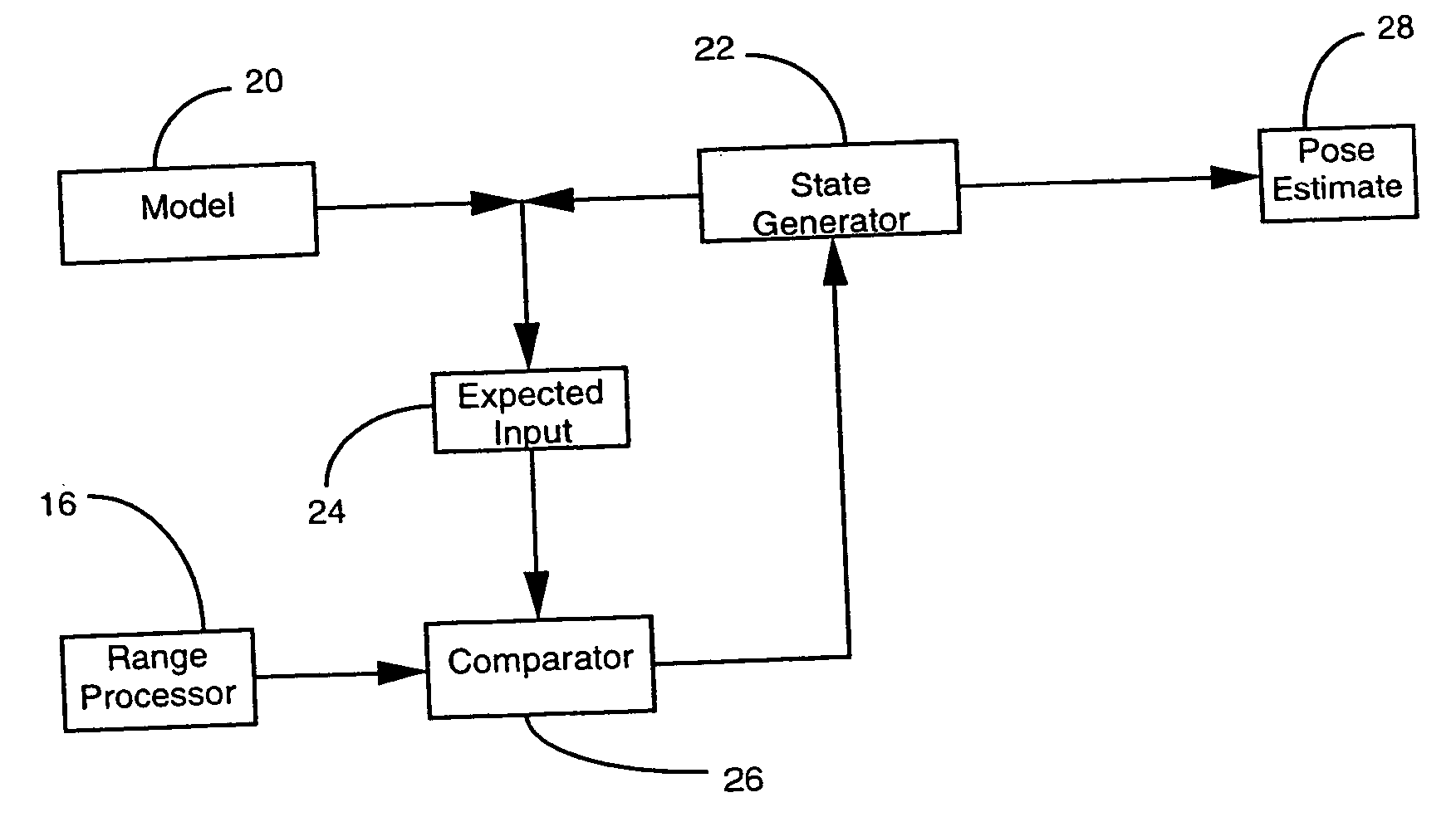
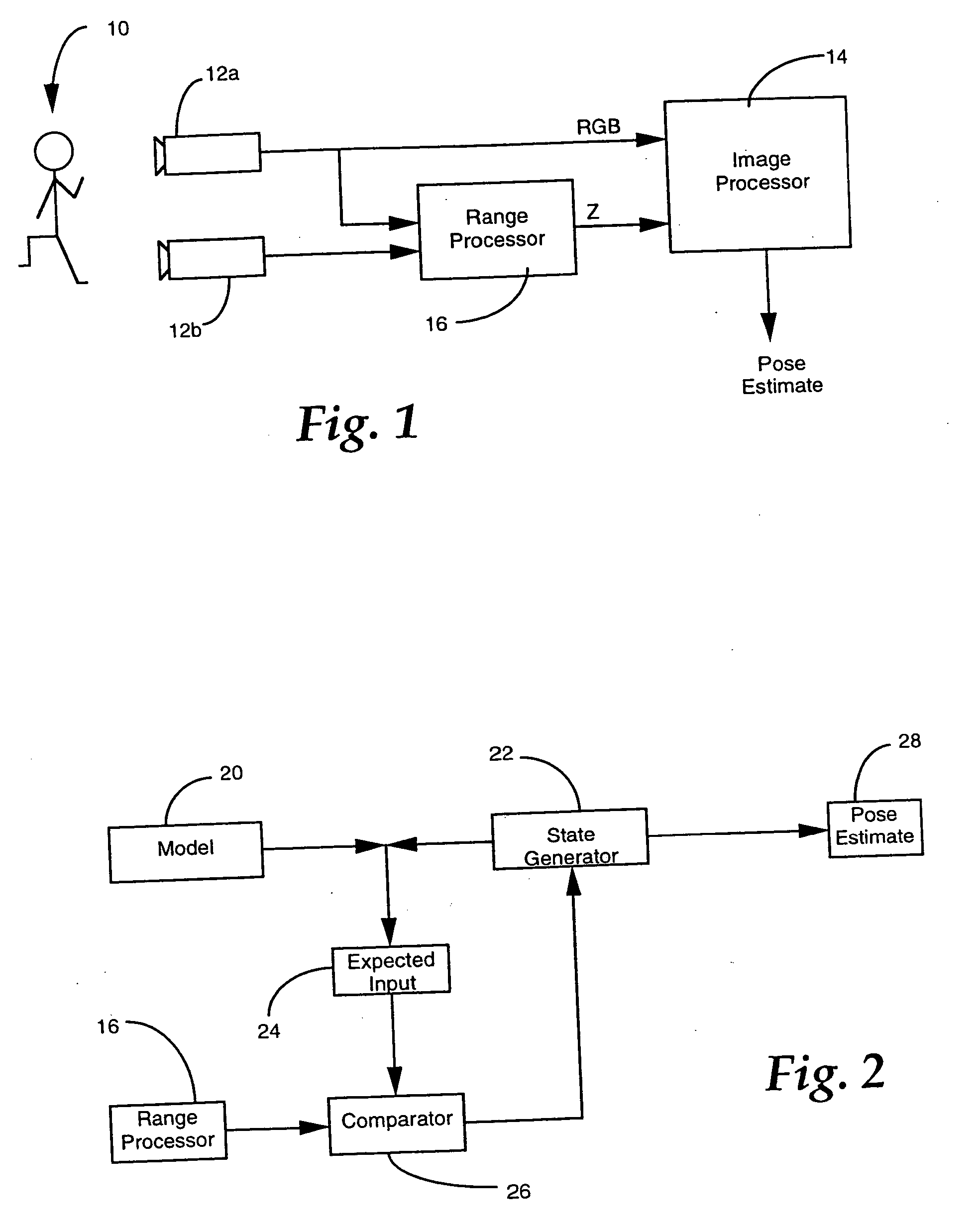
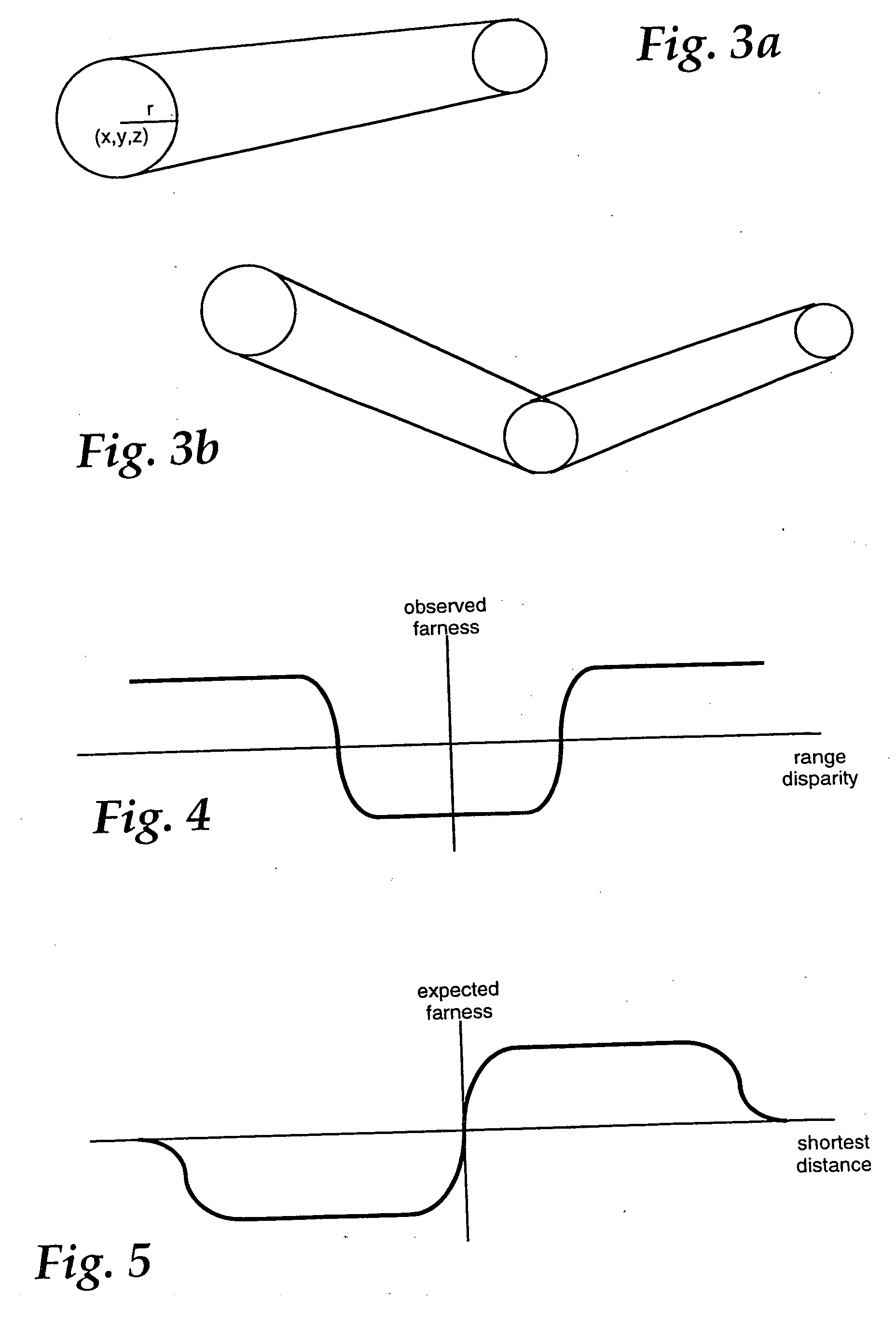
Three dimensional object pose estimation which employs dense depth information
InactiveUS7003134B1Accurate estimateImprove tracking performanceImage enhancementImage analysisGraphicsStructure from motion
Dense range data obtained at real-time rates is employed to estimate the pose of an articulated figure. In one approach, the range data is used in combination with a model of connected patches. Each patch is the planar convex hull of two circles, and a recursive procedure is carried out to determine an estimate of pose which most closely correlates to the range data. In another aspect of the invention, the dense range data is used in conjunction with image intensity information to improve pose tracking performance. The range information is used to determine the shape of an object, rather than assume a generic model or estimate structure from motion. In this aspect of the invention, a depth constraint equation, which is a counterpart to the classic brightness change constraint equation, is employed. Both constraints are used to jointly solve for motion estimates.
Owner:INTEL CORP
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
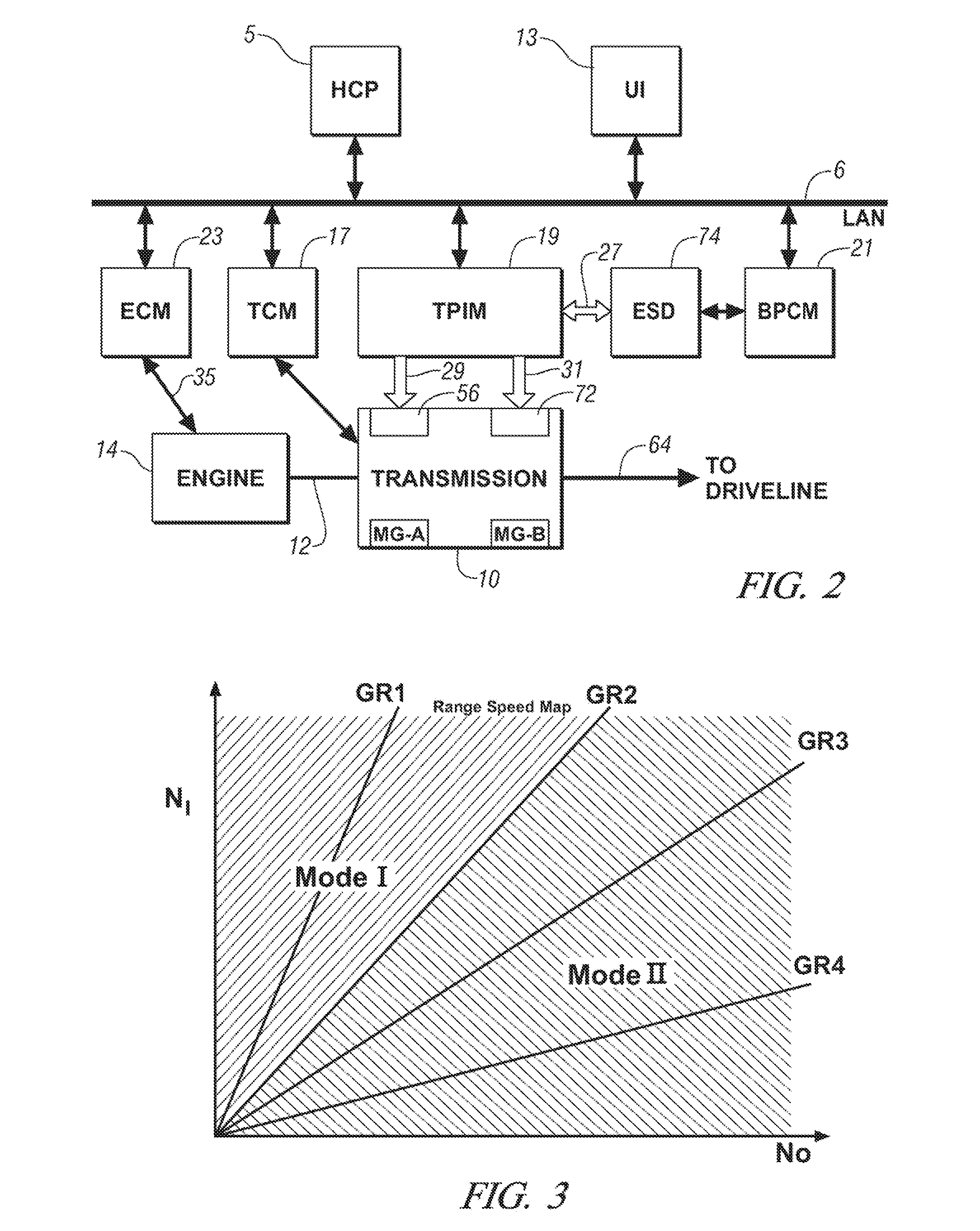
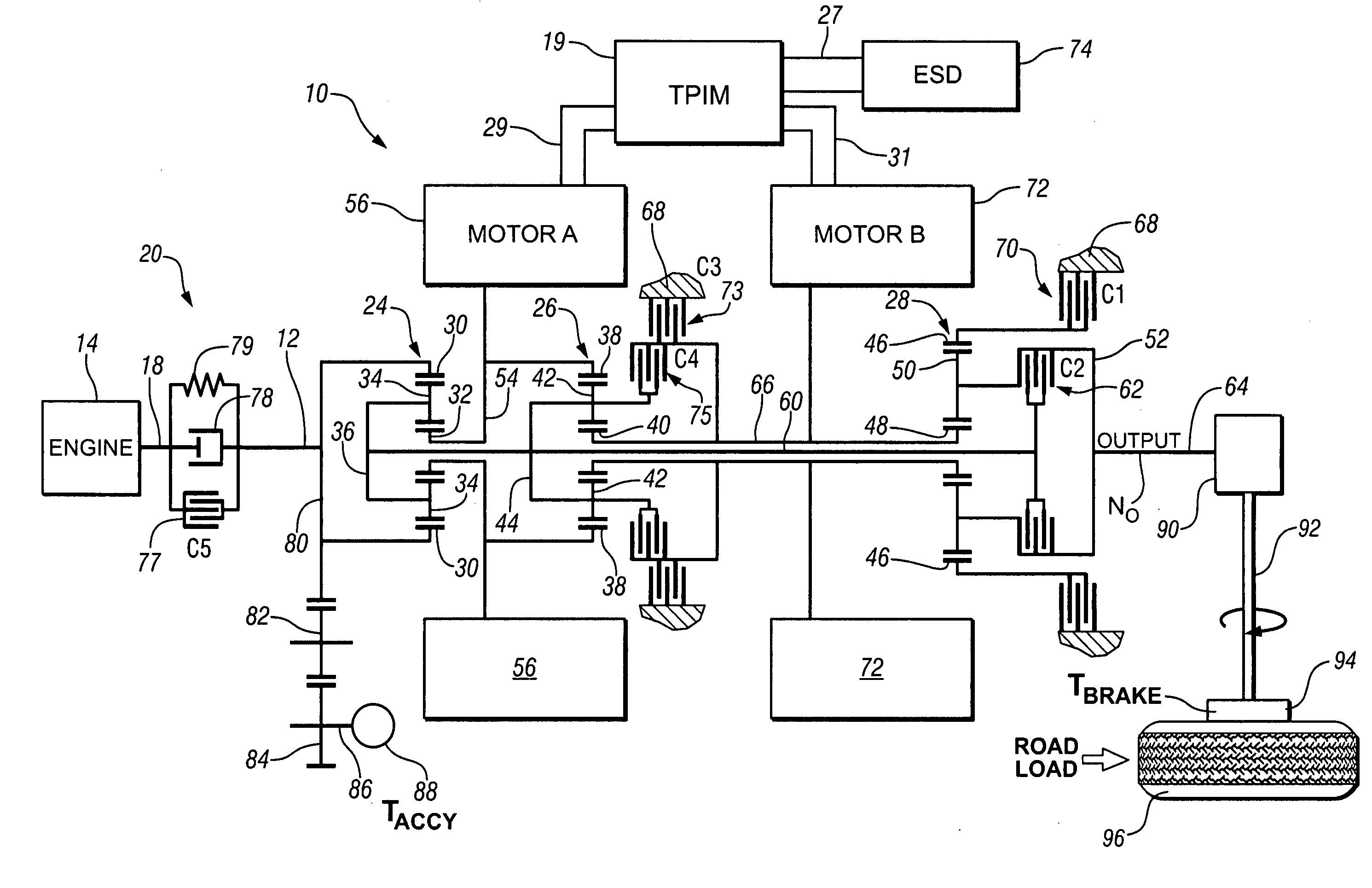
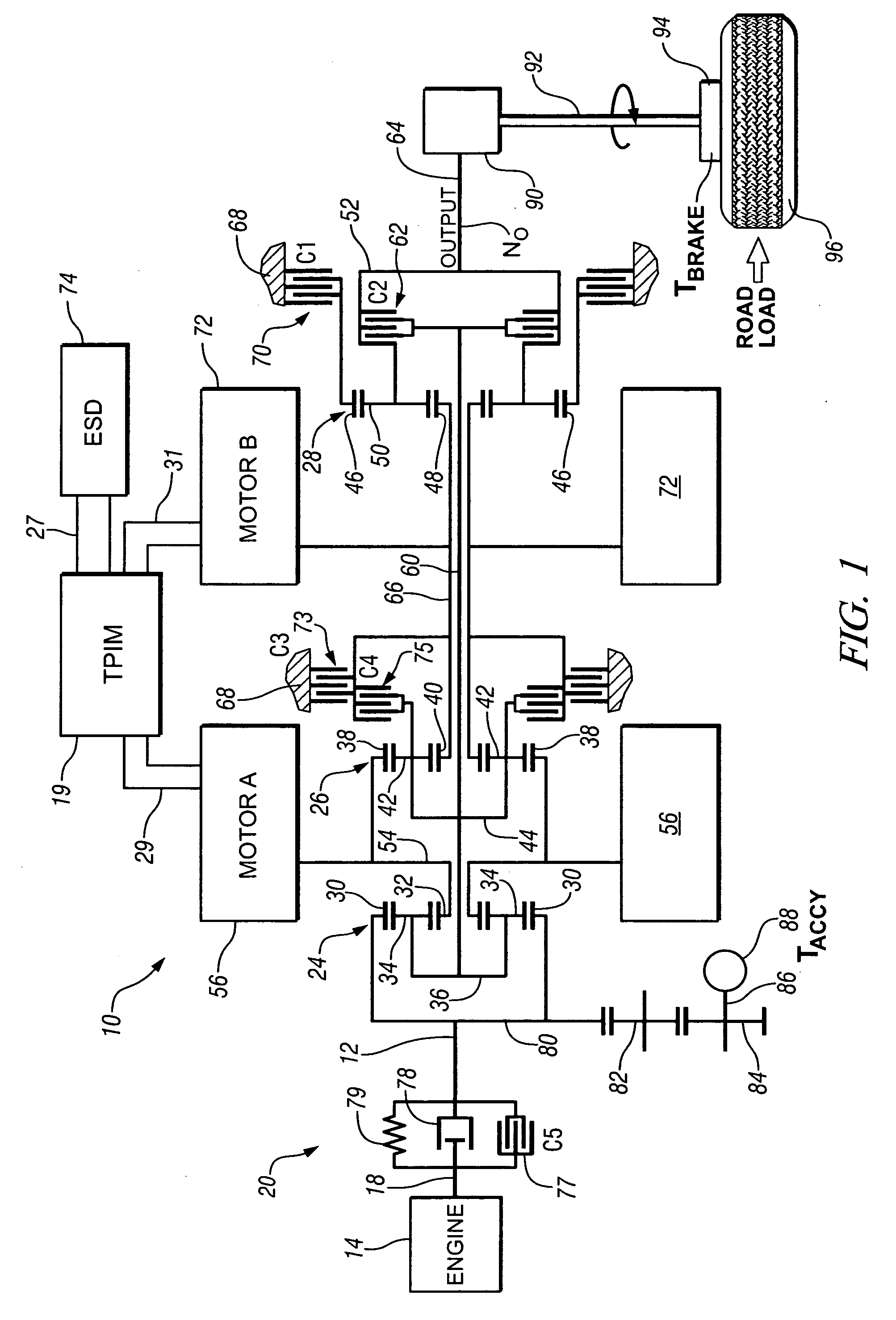
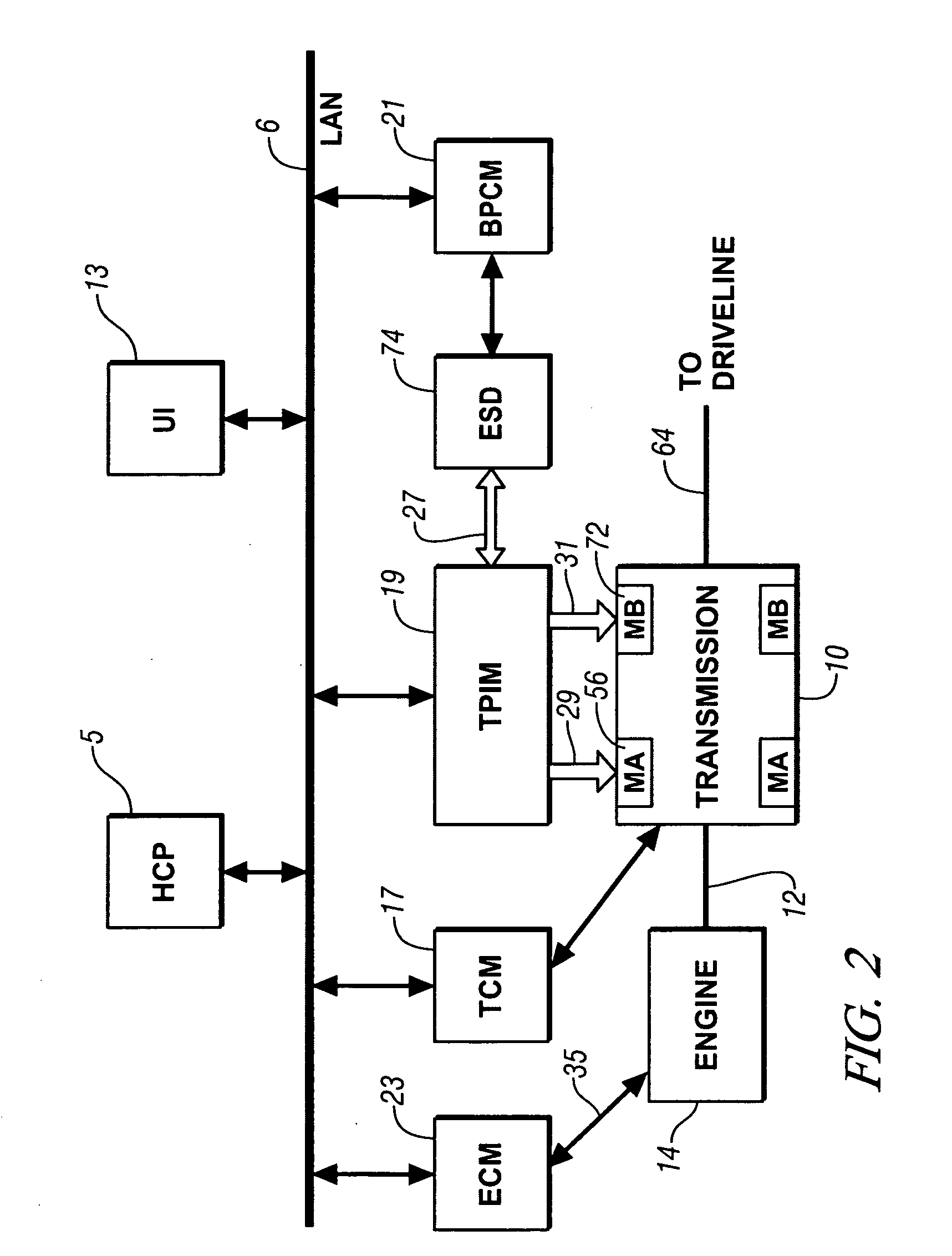
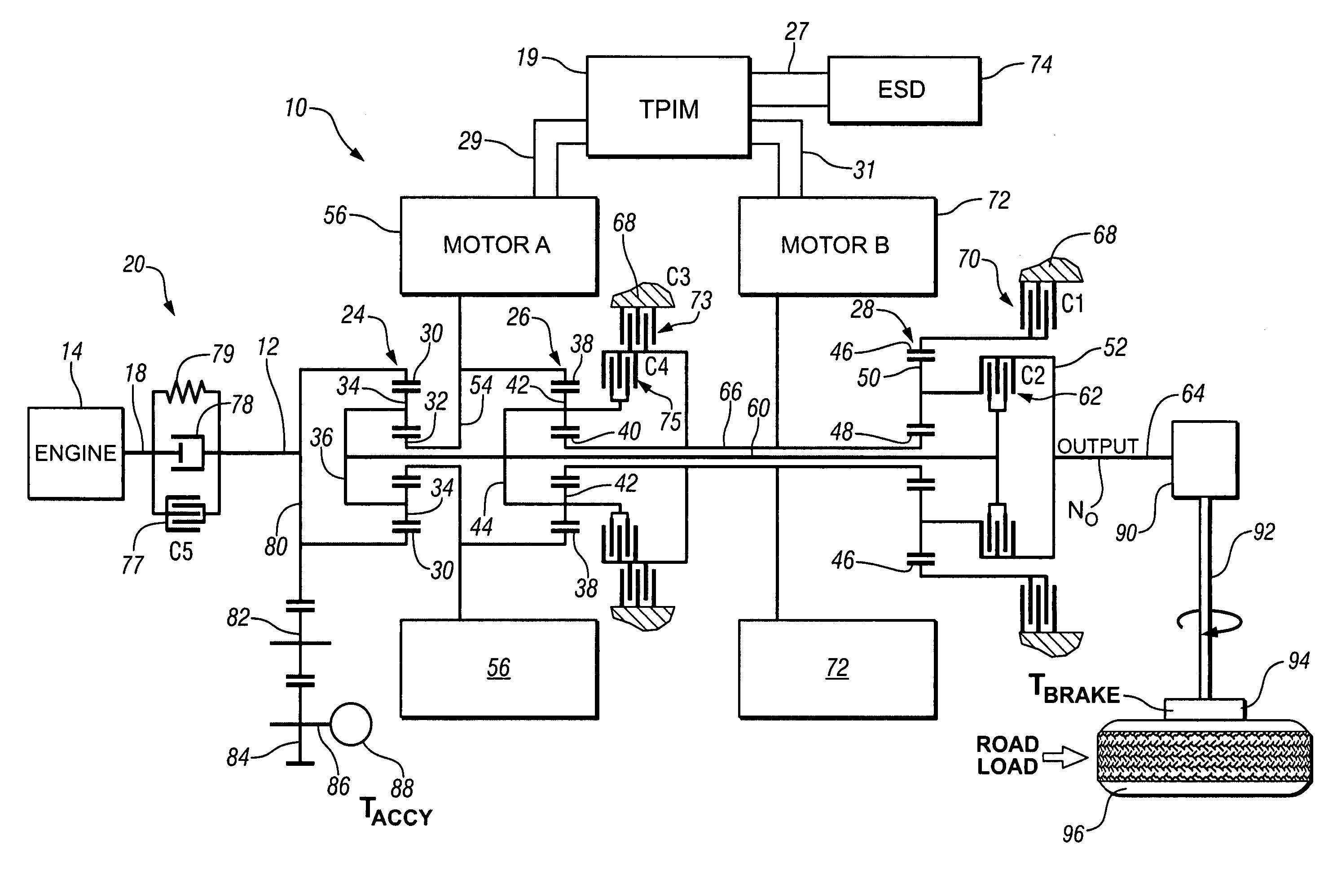
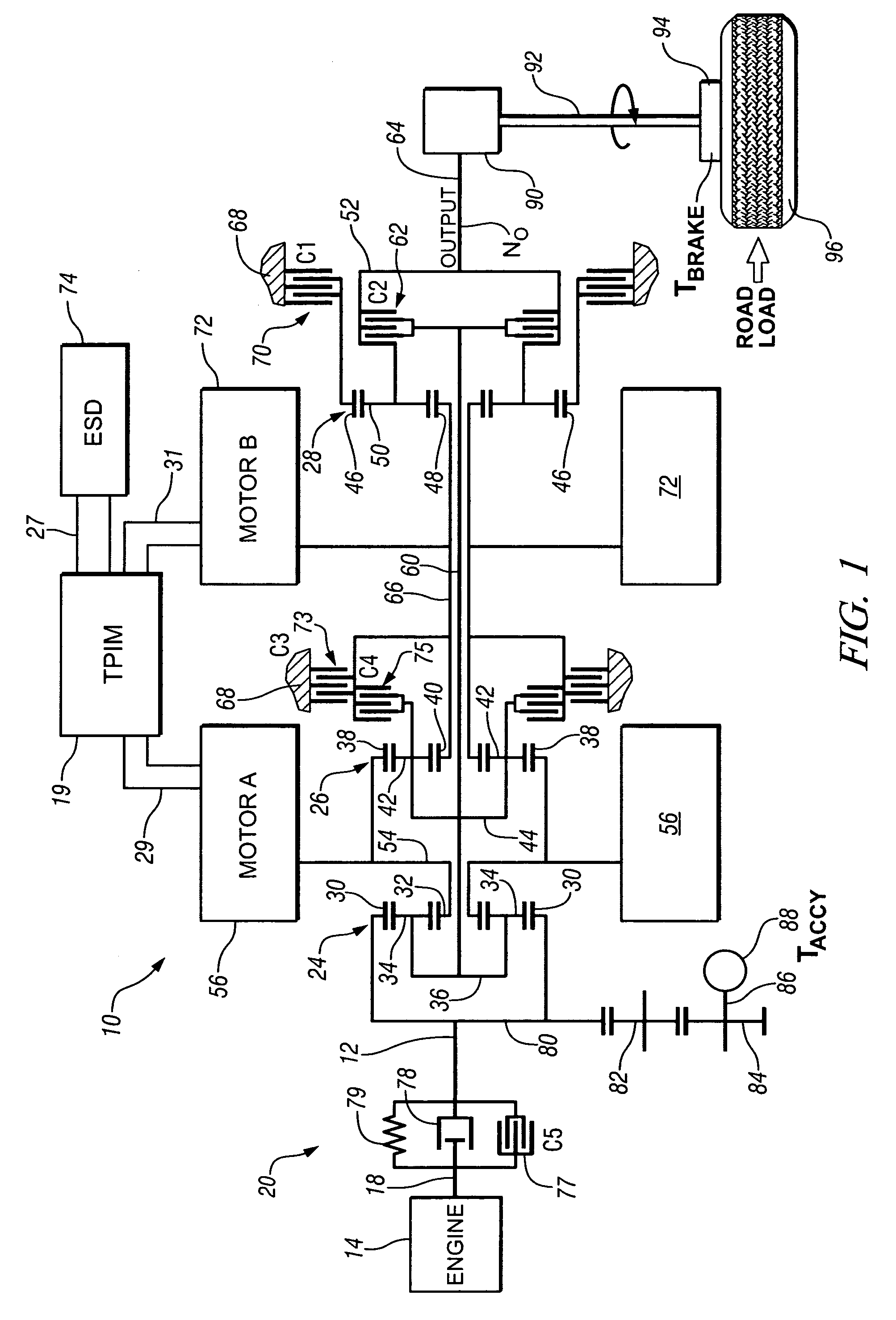
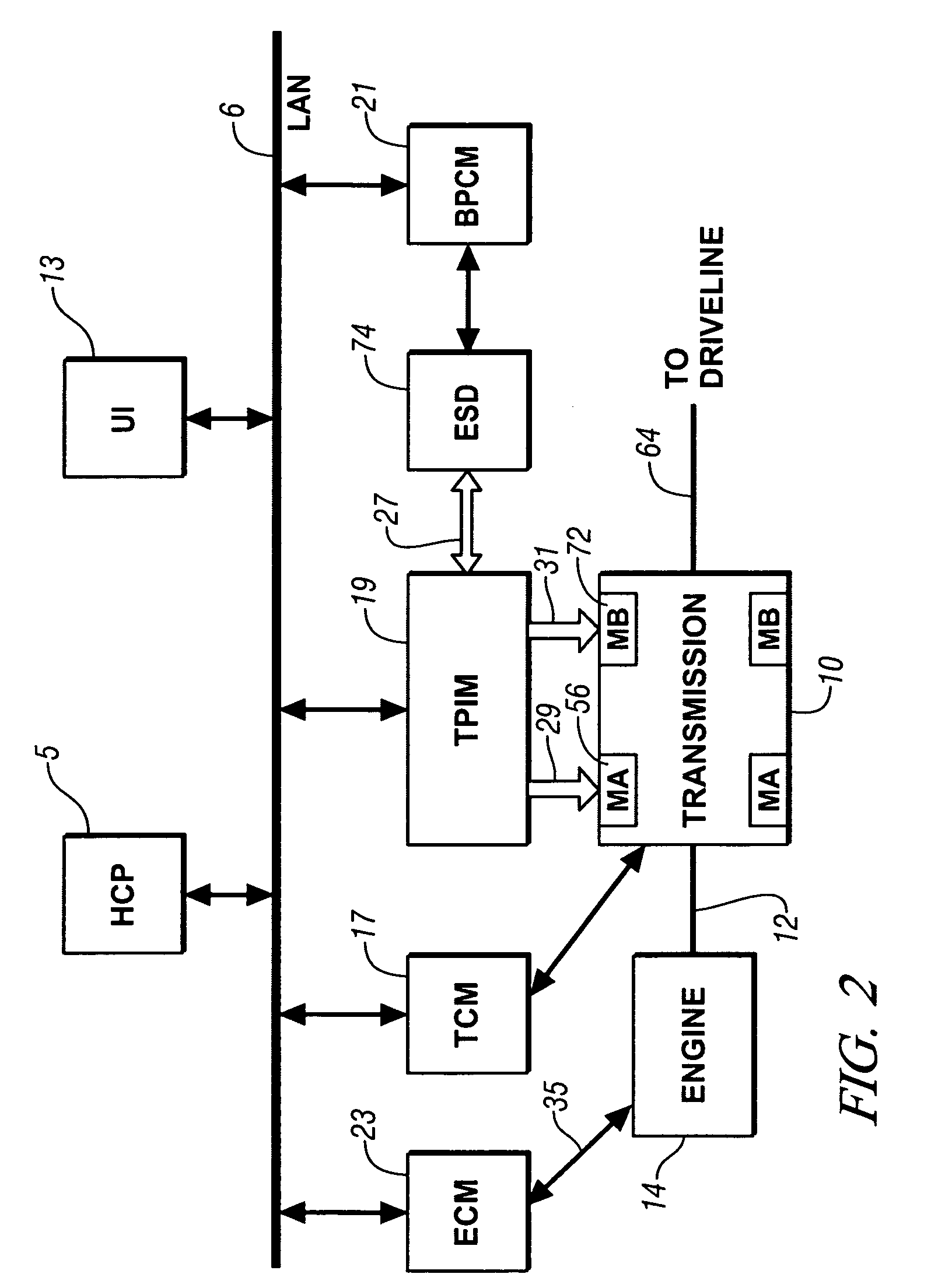
Method and apparatus for controlling an electro-mechanical transmission during a shift execution
InactiveUS20080119320A1Limit output torqueLimit in magnitude of outputElectric propulsion mountingGearing controlElectric machineClutch
A method and apparatus to control an electro-mechanical transmission during a shift event, including identifying a fault in an off-going clutch, is provided. The method includes deactivating an off-going torque-transfer clutch, monitoring slippage of the off-going torque-transfer clutch, and limiting a change in operation of an electrical machine operatively connected to the transmission until the slippage of the off-going torque-transfer clutch exceeds a threshold. Limiting a change in operation of the electrical machine comprises limiting an output torque of the electrical machine, comprising limiting a time-rate change in the output torque and limiting a magnitude of the output torque. The limit of the change Is discontinued when the slippage of the off-going torque-transfer clutch exceeds the threshold.
Owner:GM GLOBAL TECH OPERATIONS LLC
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Jerk management using multivariable active driveline damping
ActiveUS20070225889A1Actively dampen magnitudeMinimize impactHybrid vehiclesDigital data processing detailsDrive wheelEngineering
A multivariable feedback control approach to actively dampen magnitude of jerks in a powertrain system using multiple torque-control devices is offered. To manage jerks, a desired axle torque is restricted when a torque reversal occurs. When the vehicle operator or the system executes a command that requires change in direction of torque, the desired axle torque is limited to a low level until the lash estimate has changed accordingly. During this transition time, active damping controls driveline component speeds so that the effect of lash take-up is minimized. After lash take-up occurs, the desired axle torque proceeds without restriction. The invention includes determining a desired axle torque, an output speed of the transmission, and an output speed of a driven wheel of the driveline. One of the devices is controlled based upon a time-rate change in the desired axle torque.
Owner:GM GLOBAL TECH OPERATIONS LLC
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS8010469B2Increased complexityAvoid problemsMemory loss protectionError detection/correctionData streamSelf-organizing map
Methods and systems for flow processing and switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security are described. Such flow processing facilities may be used for inspecting network traffic packet payloads to detect security threats and intrusions across accessible layers of the network IP stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources.
Owner:CA TECH INC
Three dimensional object pose estimation which employs dense depth information
InactiveUS20050265583A1Improve pose tracking performanceAccurate representationImage enhancementImage analysisGraphicsStructure from motion
Dense range data obtained at real-time rates is employed to estimate the pose of an articulated figure. In one approach, the range data is used in combination with a model of connected patches. Each patch is the planar convex hull of two circles, and a recursive procedure is carried out to determine an estimate of pose which most closely correlates to the range data. In another aspect of the invention, the dense range data is used in conjunction with image intensity information to improve pose tracking performance. The range information is used to determine the shape of an object, rather than assume a generic model or estimate structure from motion. In this aspect of the invention, a depth constraint equation, which is a counterpart to the classic brightness change constraint equation, is employed. Both constraints are used to jointly solve for motion estimates.
Owner:INTEL CORP
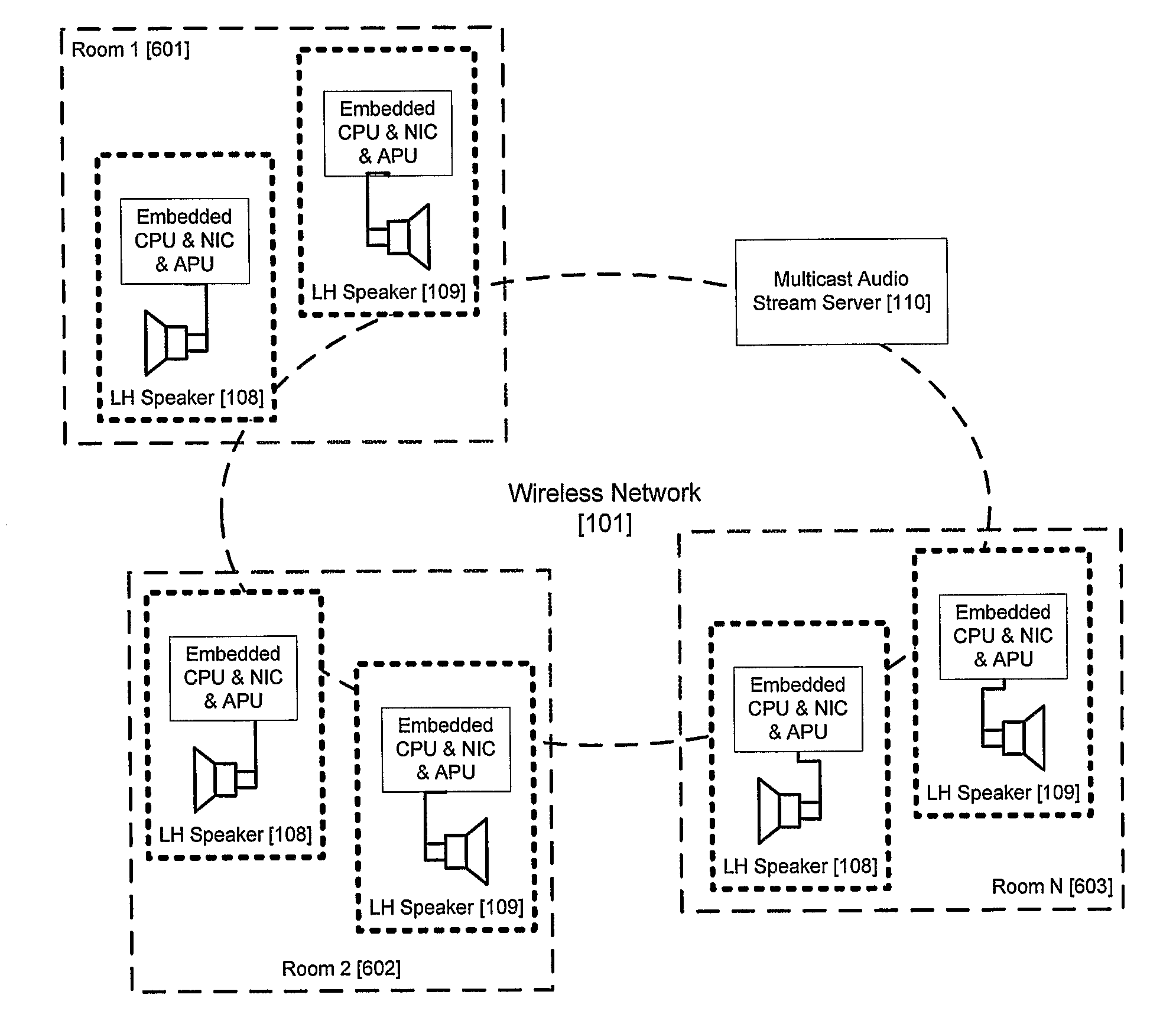
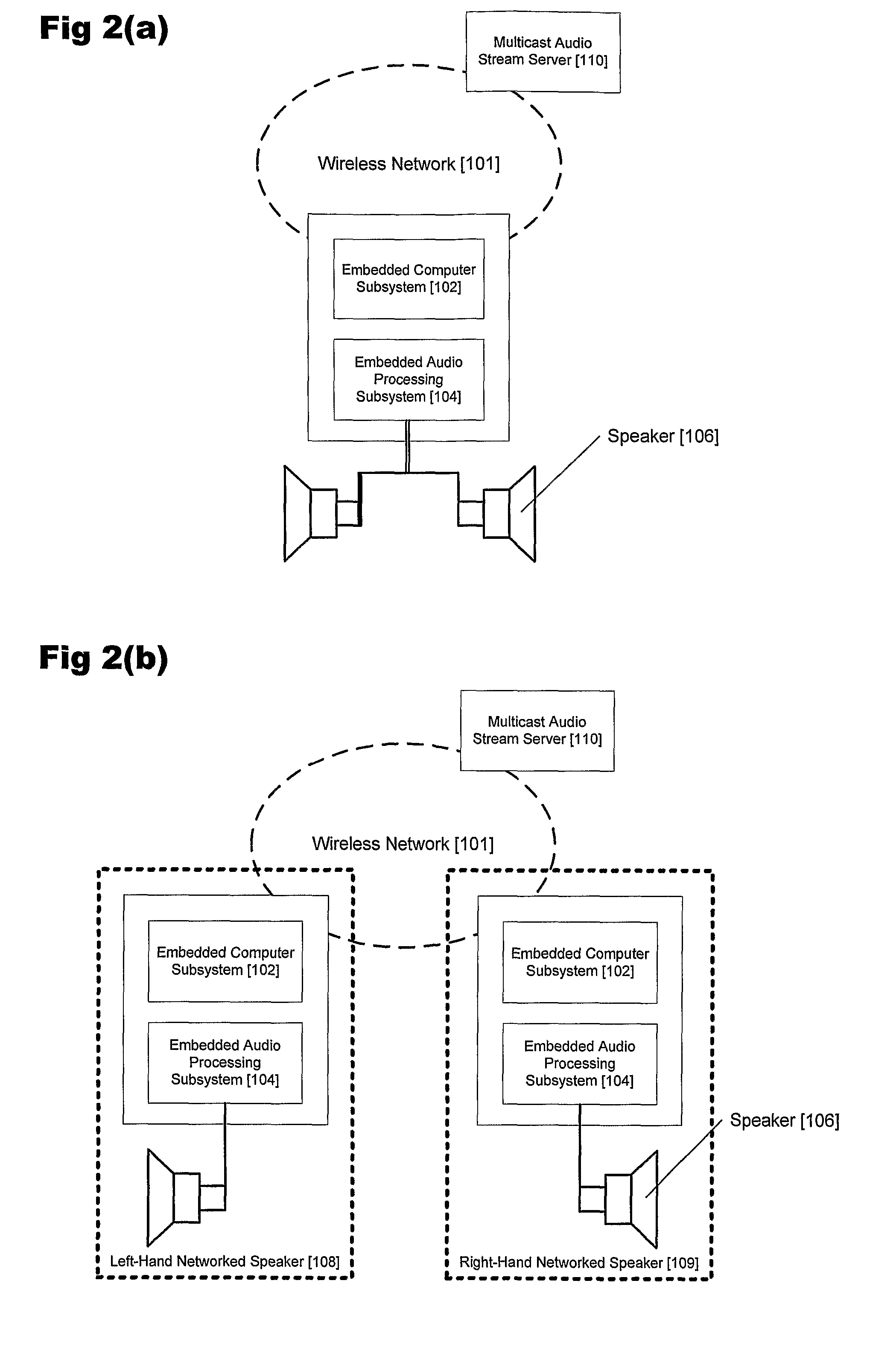
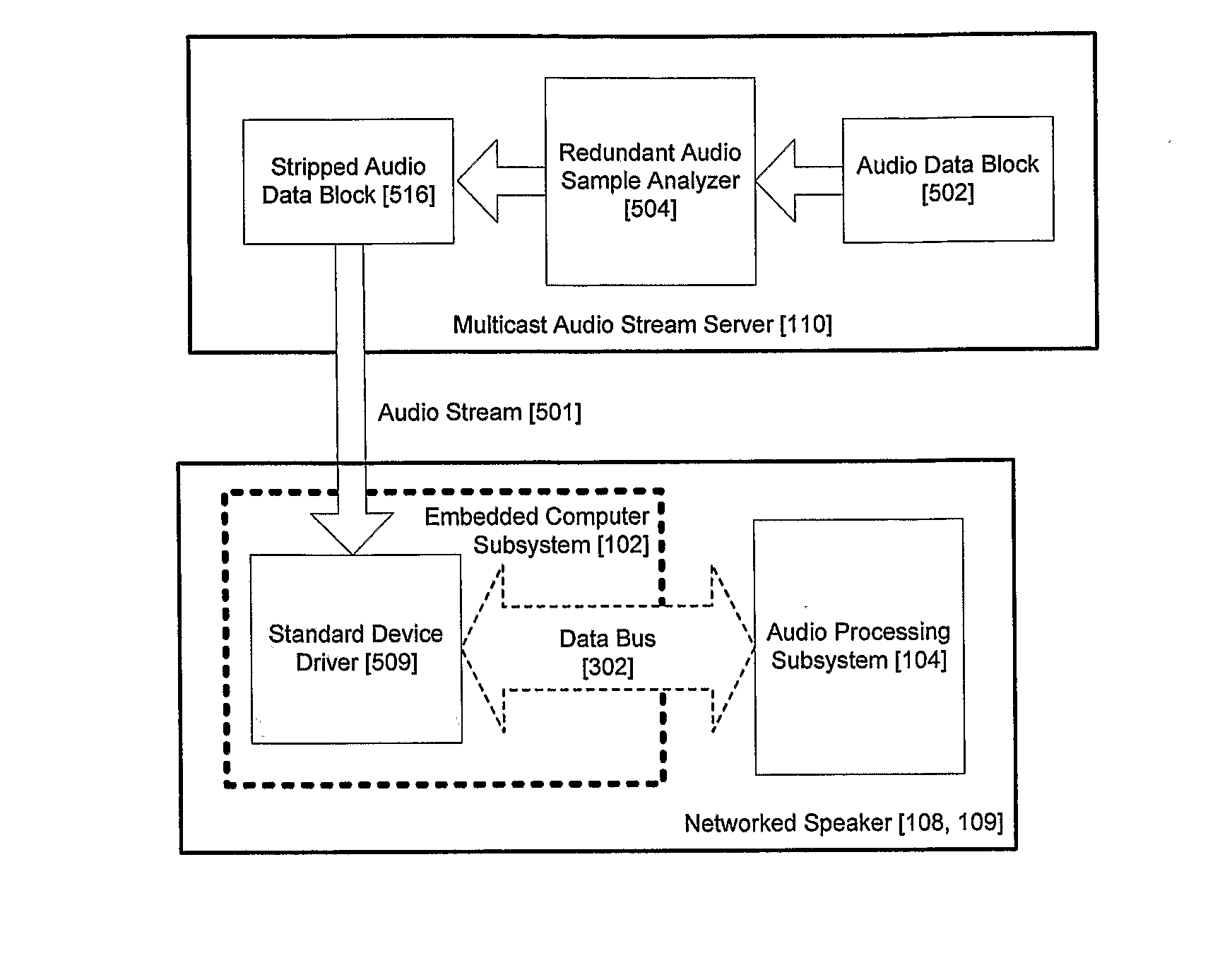
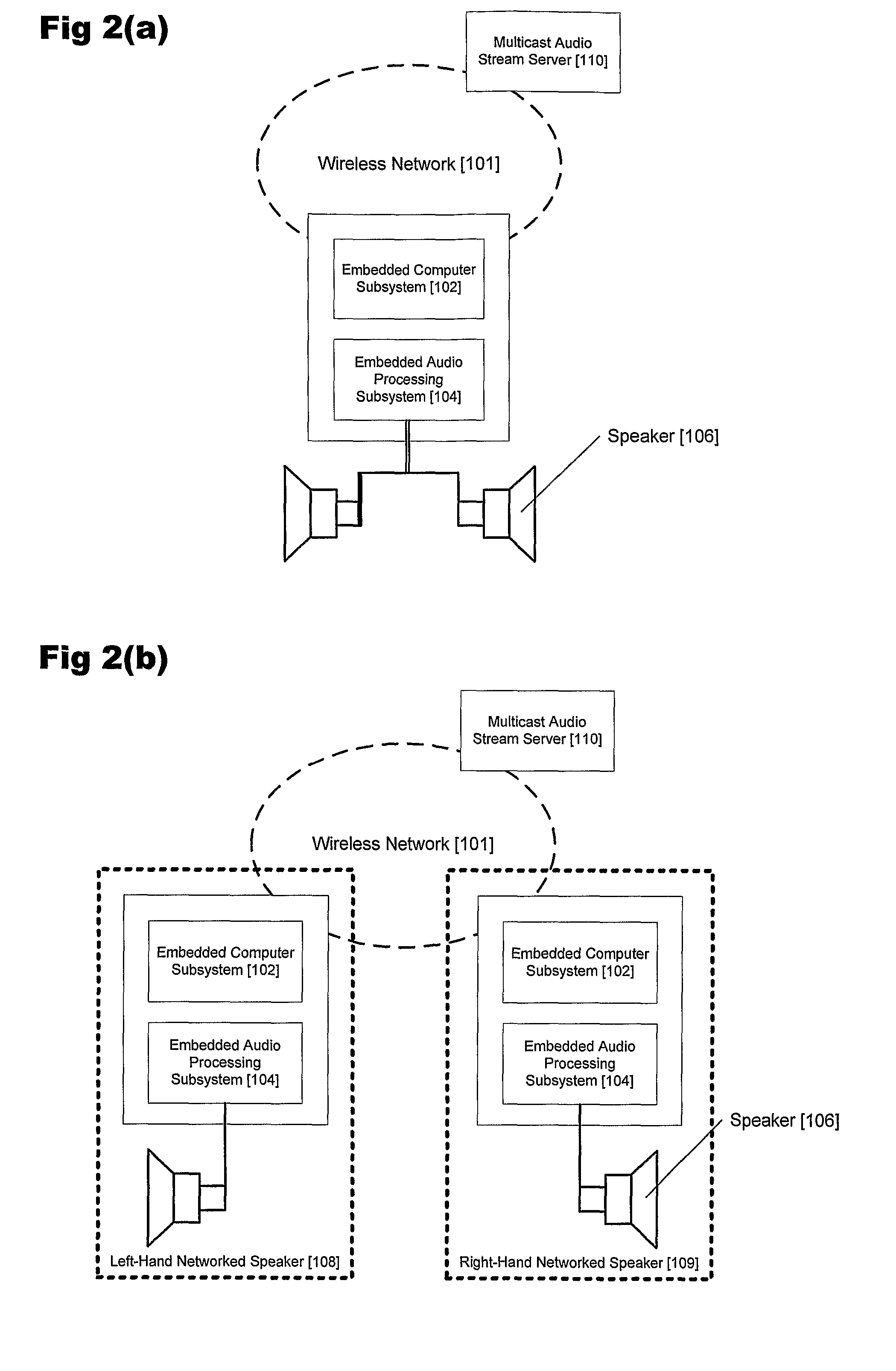
Synchronizing multi-channel speakers over a network
A server is arranged to distribute at least one stream of audio data corresponding to an audio signal to two or more speakers across a network. Each speaker includes a respective clock for regenerating the audio signal from the audio data. For each speaker, the server determines a relative rate of the speaker clock to a real time rate; and for each stream of data provided to a speaker, the server determines from a respective relative rate, respective samples of the audio signal to be altered in accordance with said relative rate. The streams are altered accordingly and transmitted across the network.
Owner:DTS LICENSING
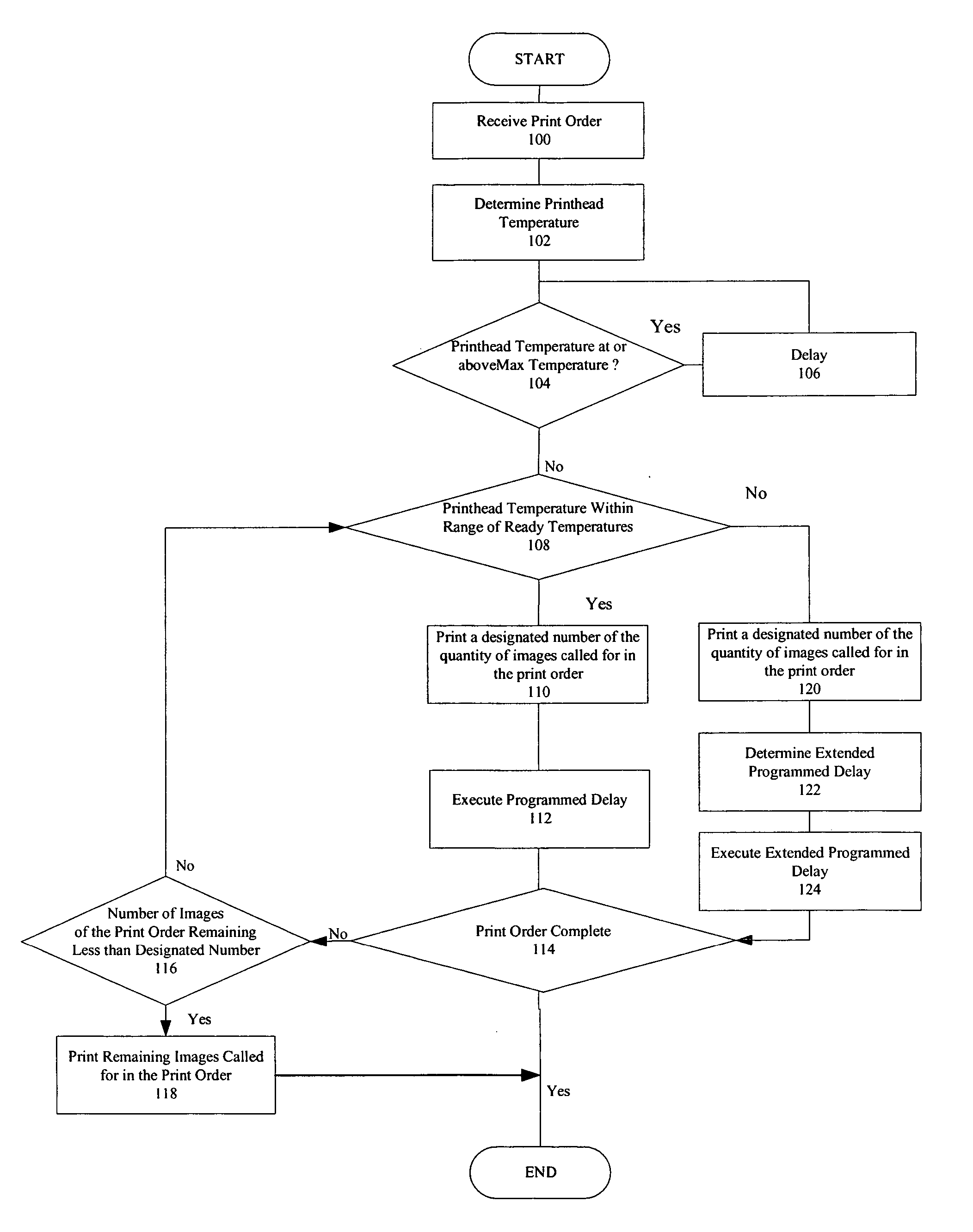
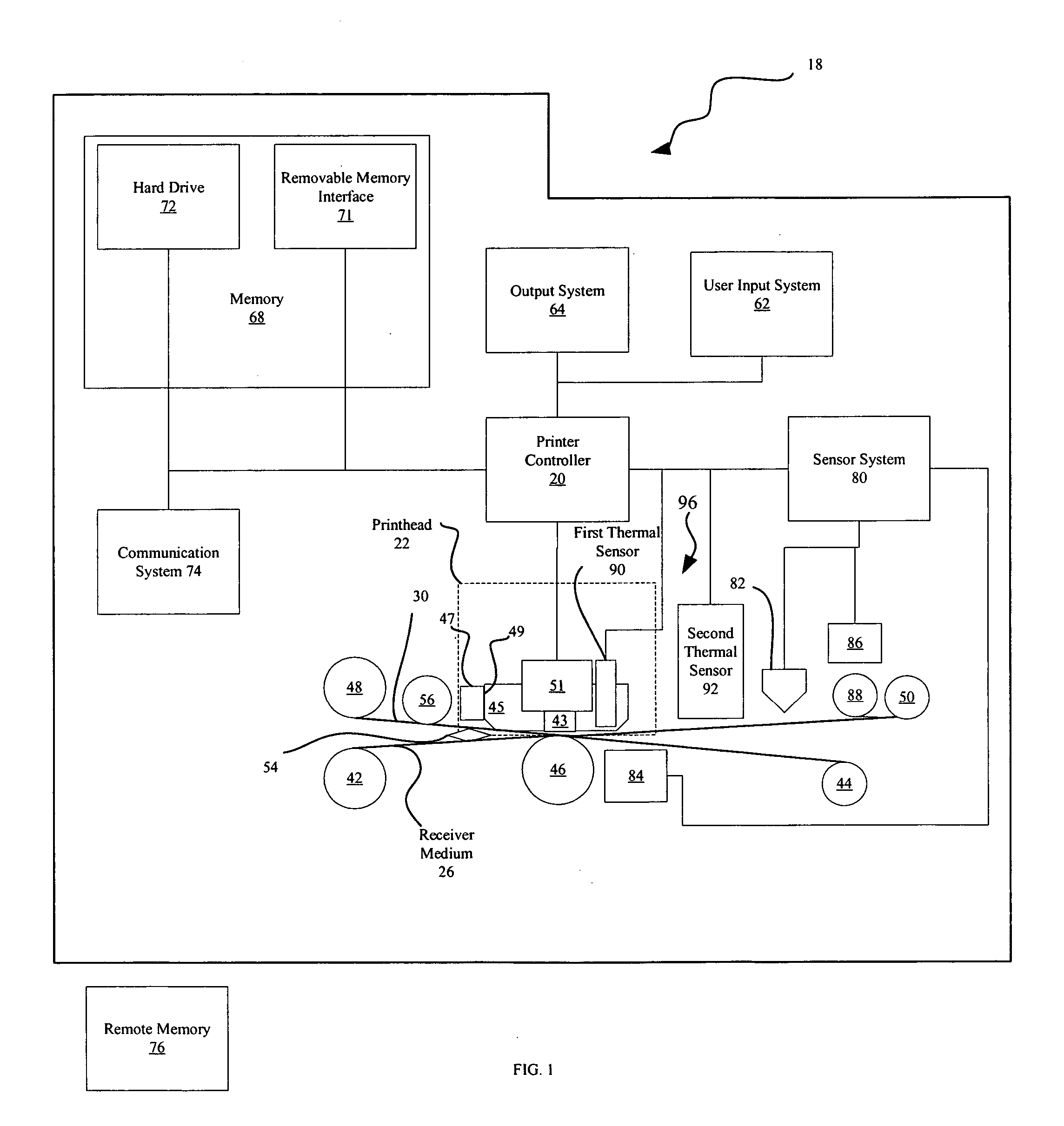
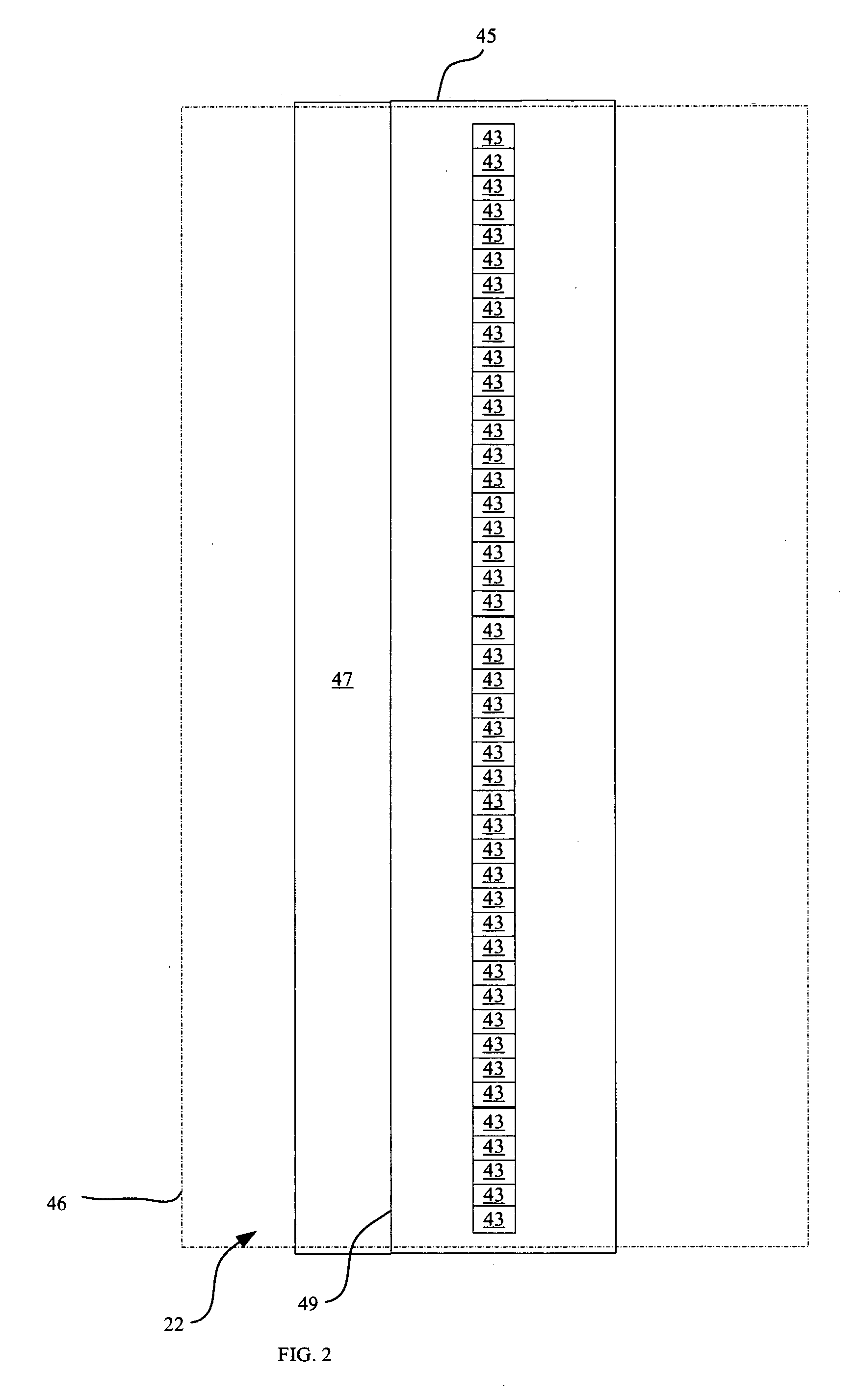
Thermal printer and method for operating same
A printer that applies donor material from donor patches on a donor web to a receiver medium using a thermal printhead that generates heat and a method for operating such a printer are provided. The method comprises the steps of: receiving a print order requesting the printing of a quantity of images; determining a temperature of the printhead; printing a designated number of the quantity of the images in a sequence; determining a length of time of a programmed delay; delaying the printing for the determined length of time of the programmed delay; and printing remaining images from the quantity of images. The length of each programmed delay is determined by using the temperature of the printhead and a time rate of cooling of the printhead and, is determined in a manner that provides a sufficient cooling time to prevent the printhead from reaching a maximum printhead temperature during printing.
Owner:KODAK ALARIS INC
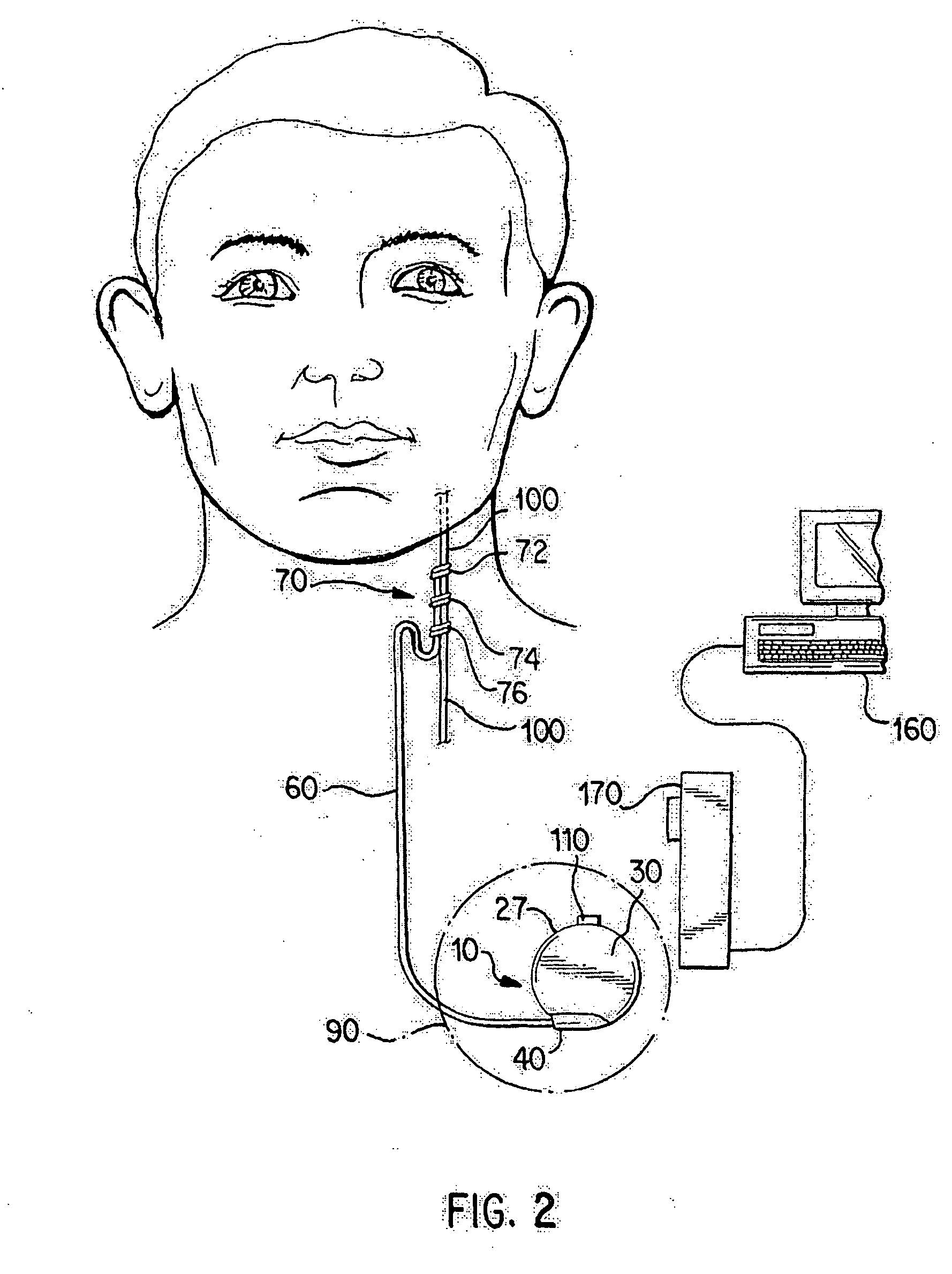
Neurostimulator with activation based on changes in body temperature
InactiveUS20060129202A1Delay detectionReliable indicatorElectrotherapyDiagnostic recording/measuringMoving averageBody Temperature Changes
Improved methods and devices are provided for detecting and / or predicting the onset of an undesirable physiological event or neural state, such as an epileptic seizure, to facilitate rapid intervention with a treatment therapy such as neurostimulation or drug therapy. The methods and devices involve monitoring the patient's body temperature, preferably by an implanted temperature sensor, to detect a sudden change in a body temperature parameter. The temperature parameter change may comprise an increase or decrease in the patient's body temperature, time rate of change of body temperature, or a difference in a moving average temperature for a first period from that of a second period. When a parameter change is detected that exceeds a threshold, neurostimulation therapy is delivered to a neural structure of the patient.
Owner:LIVANOVA USA INC
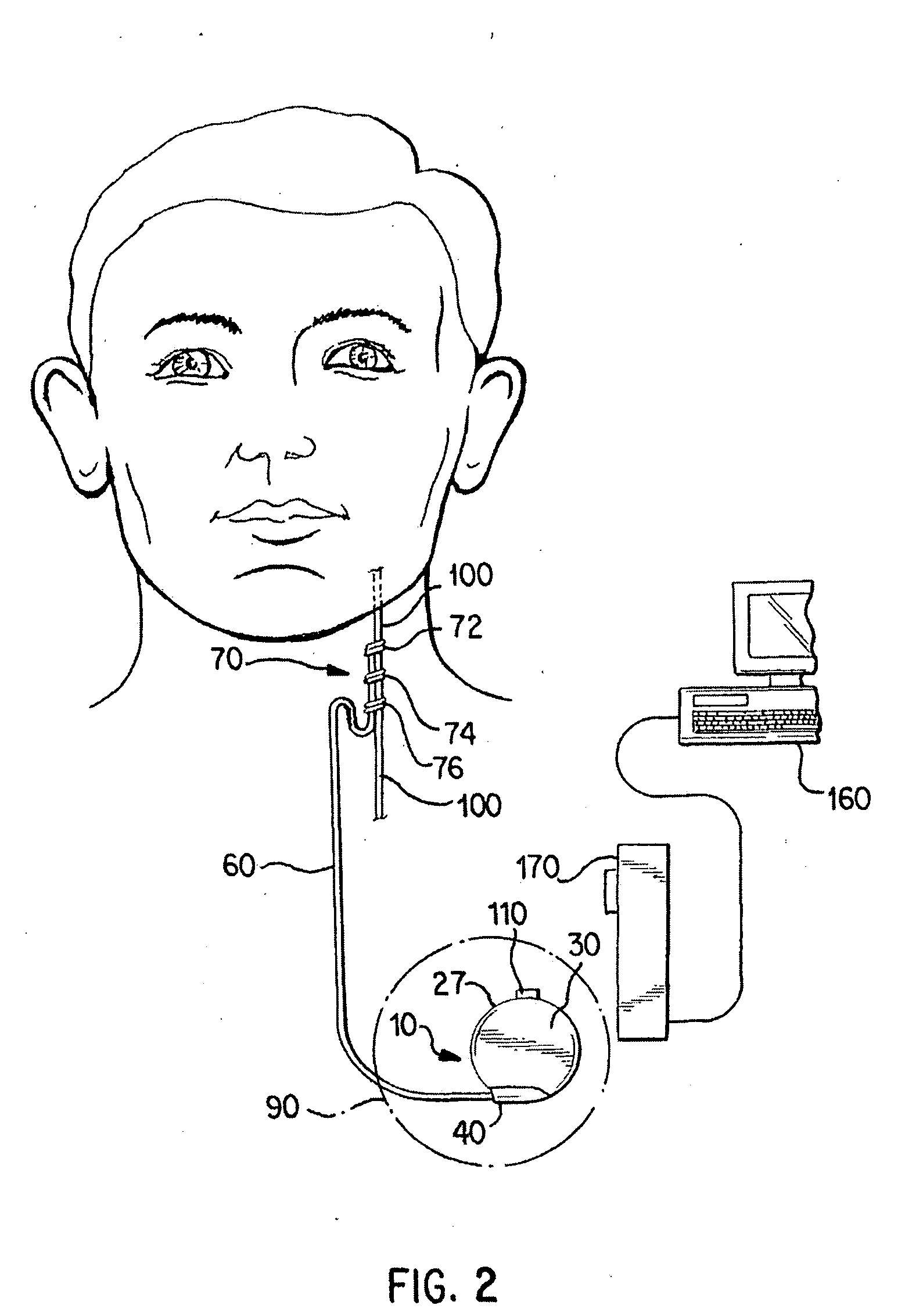
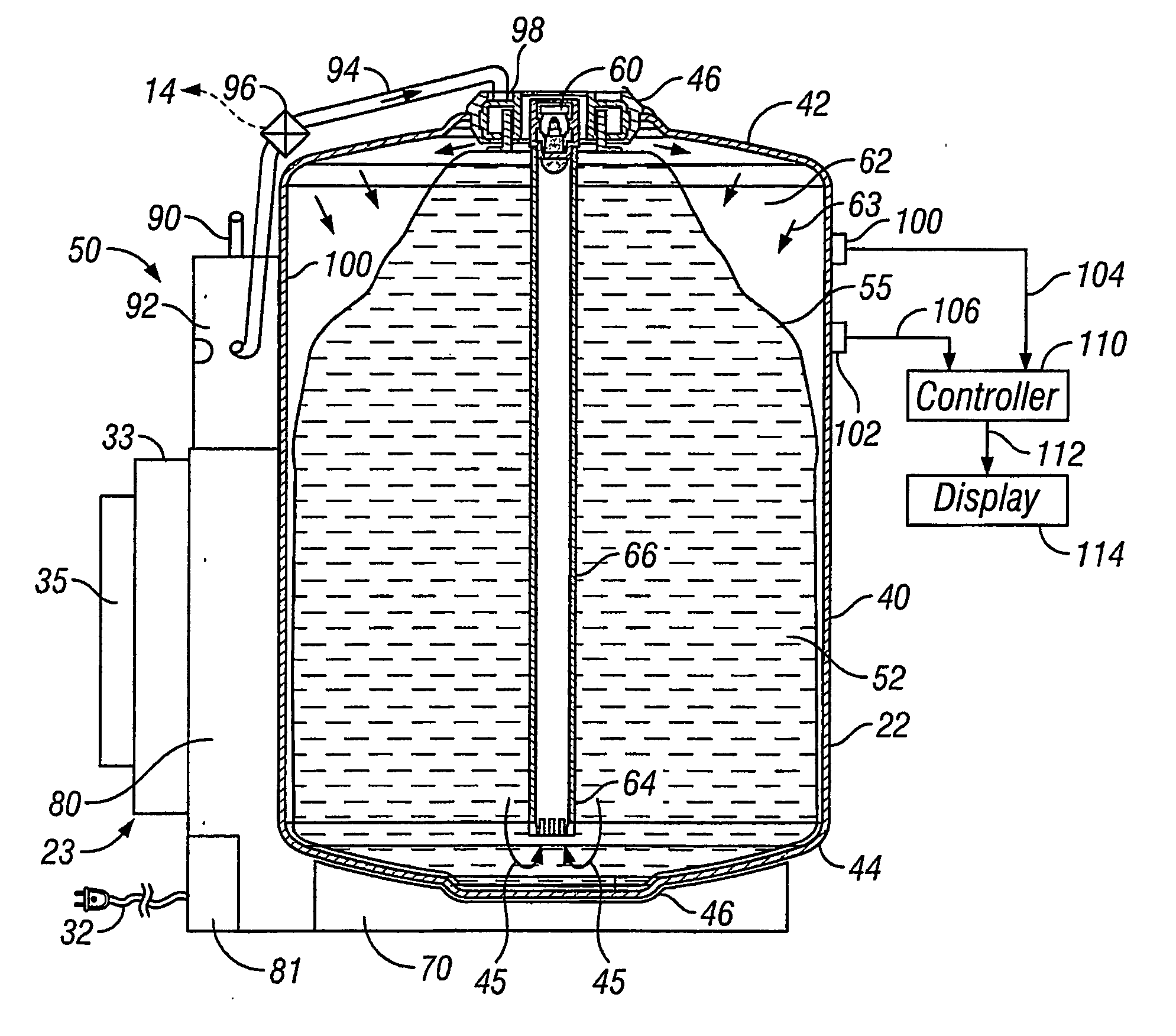
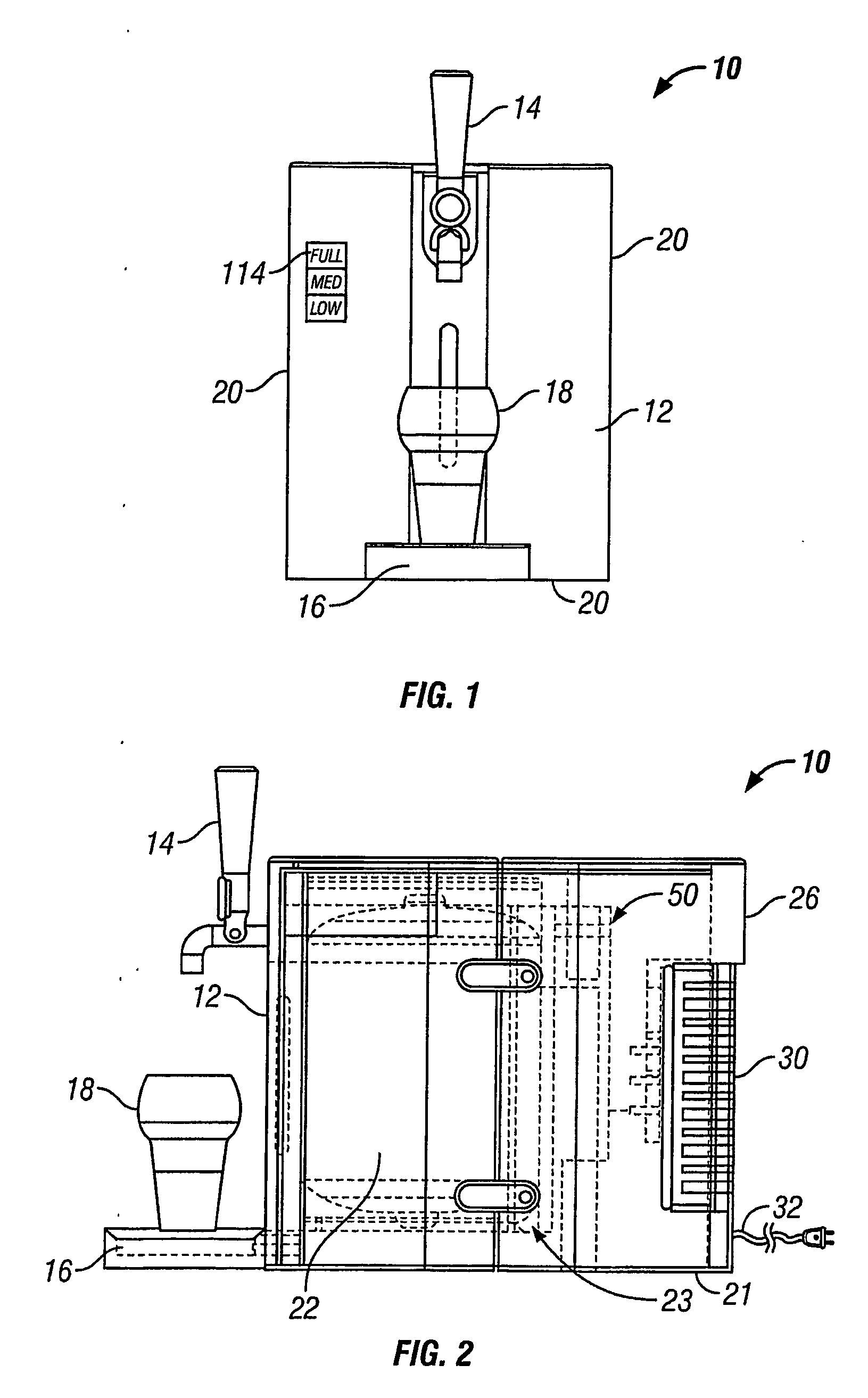
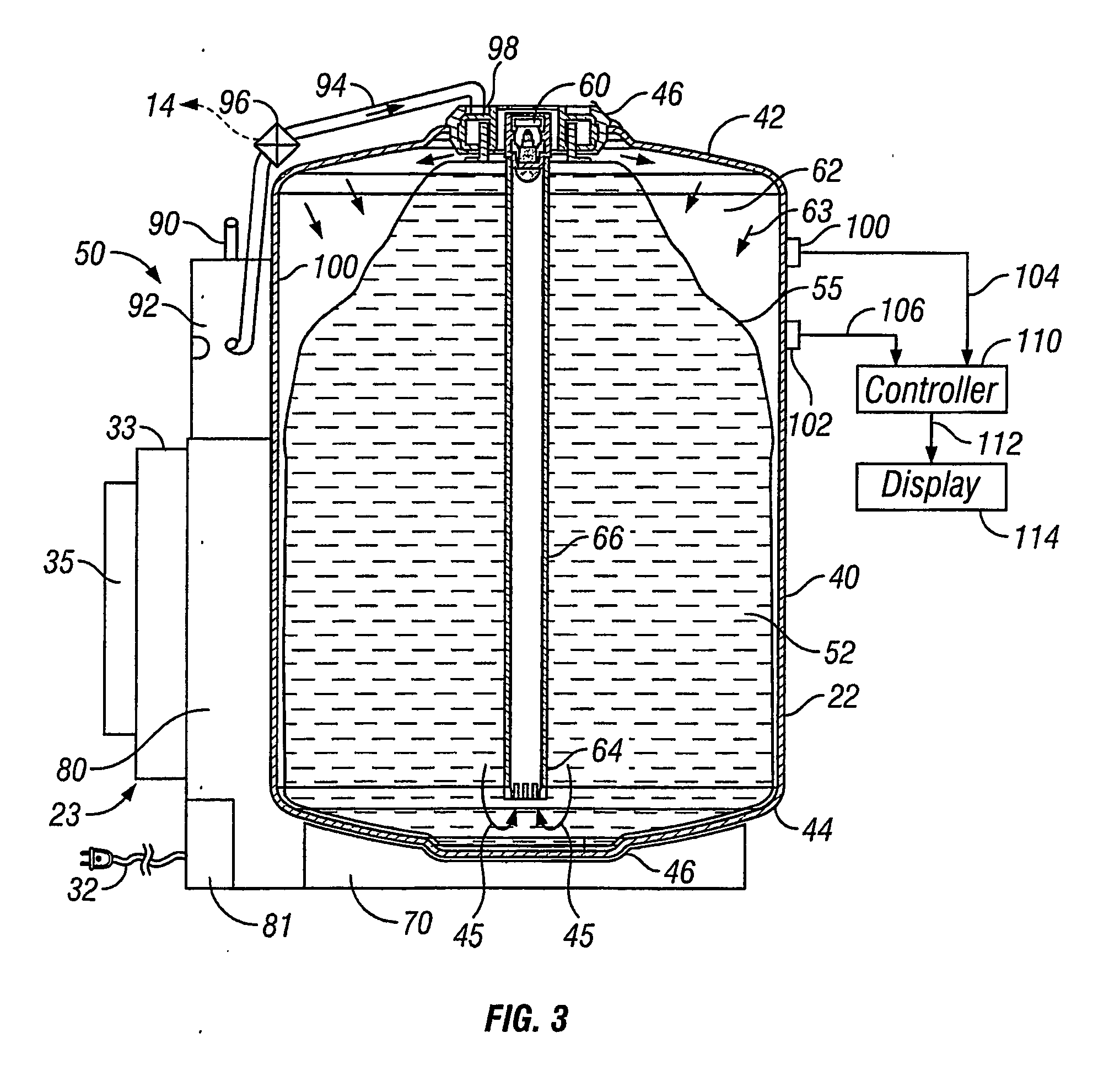
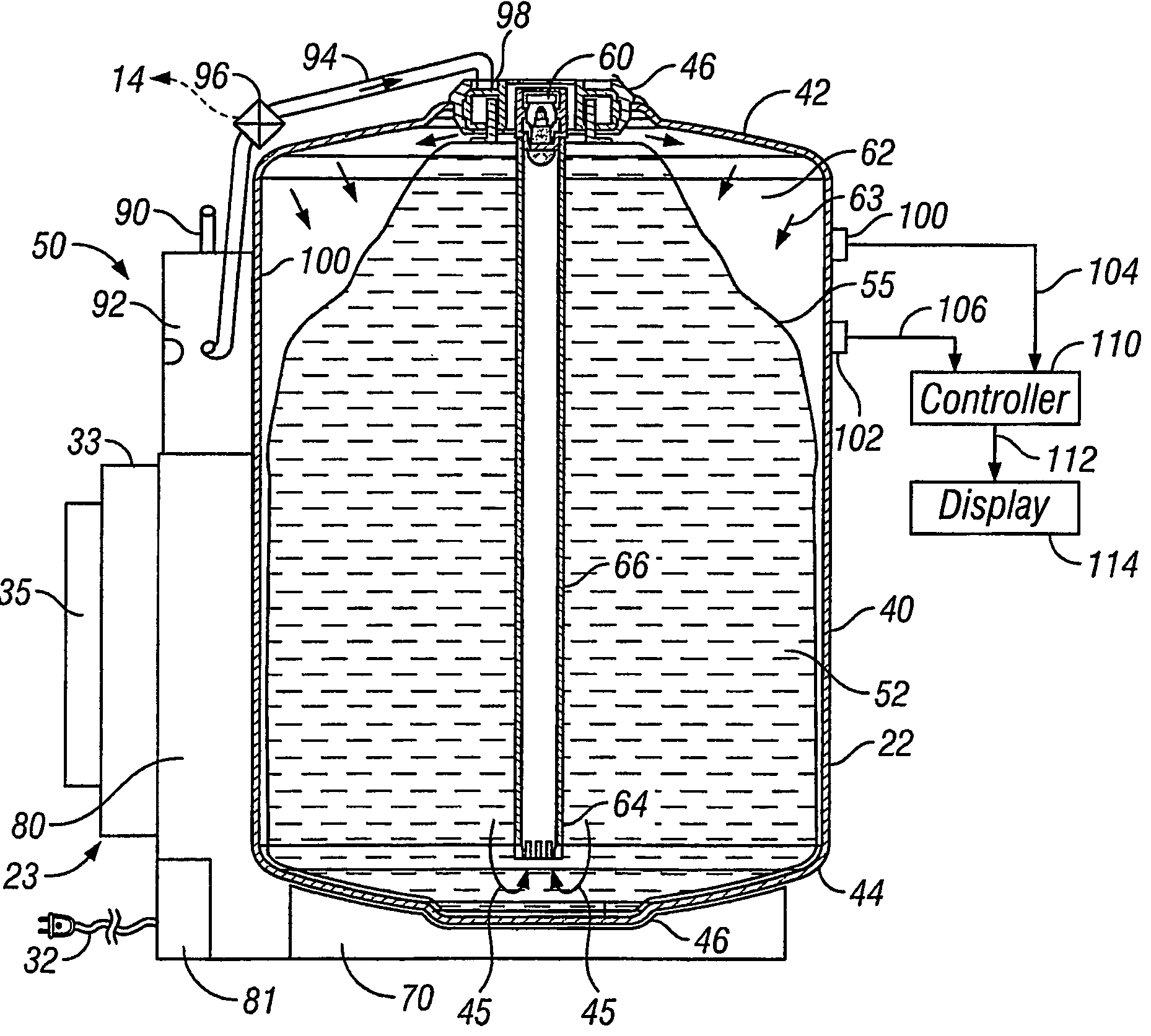
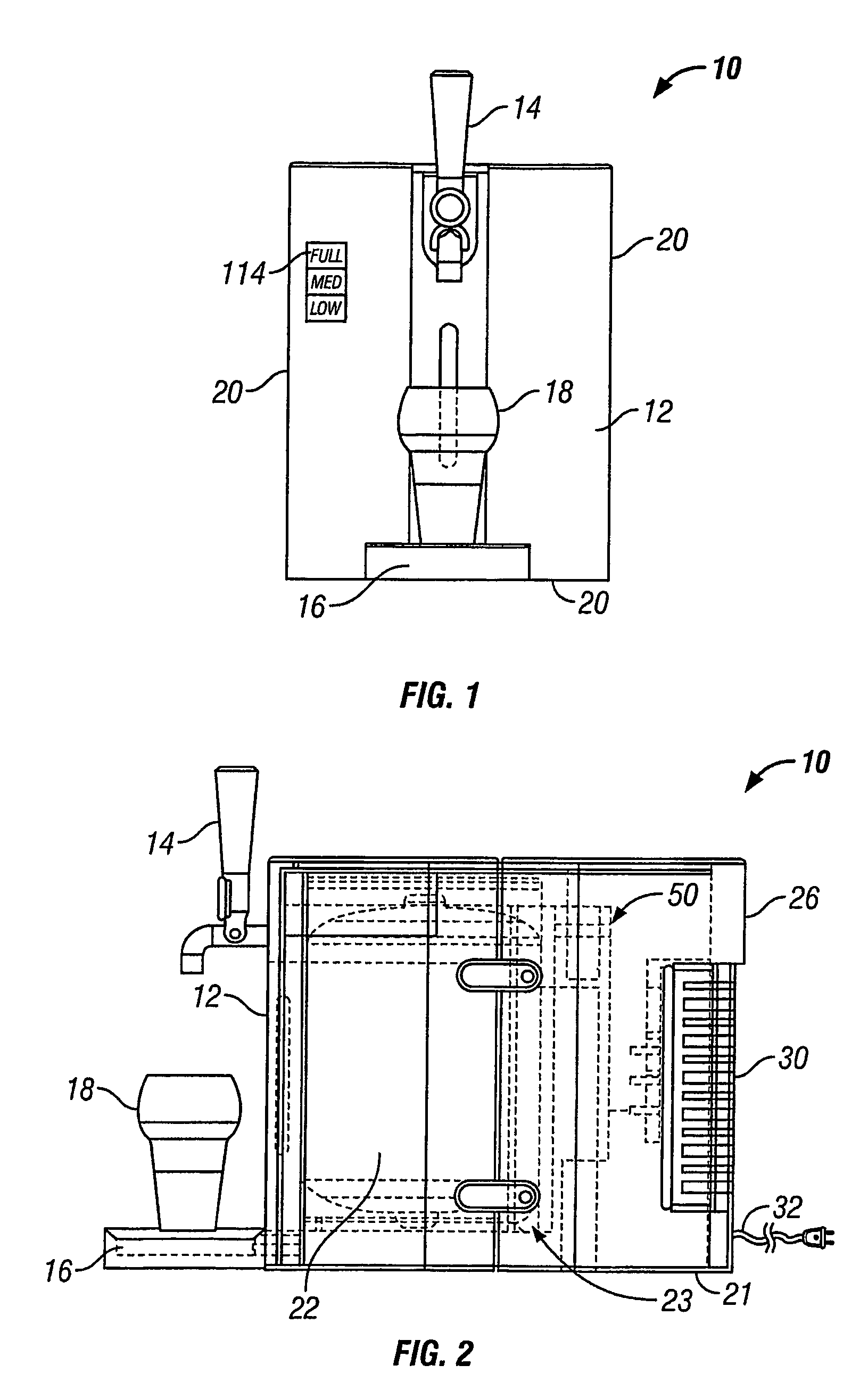
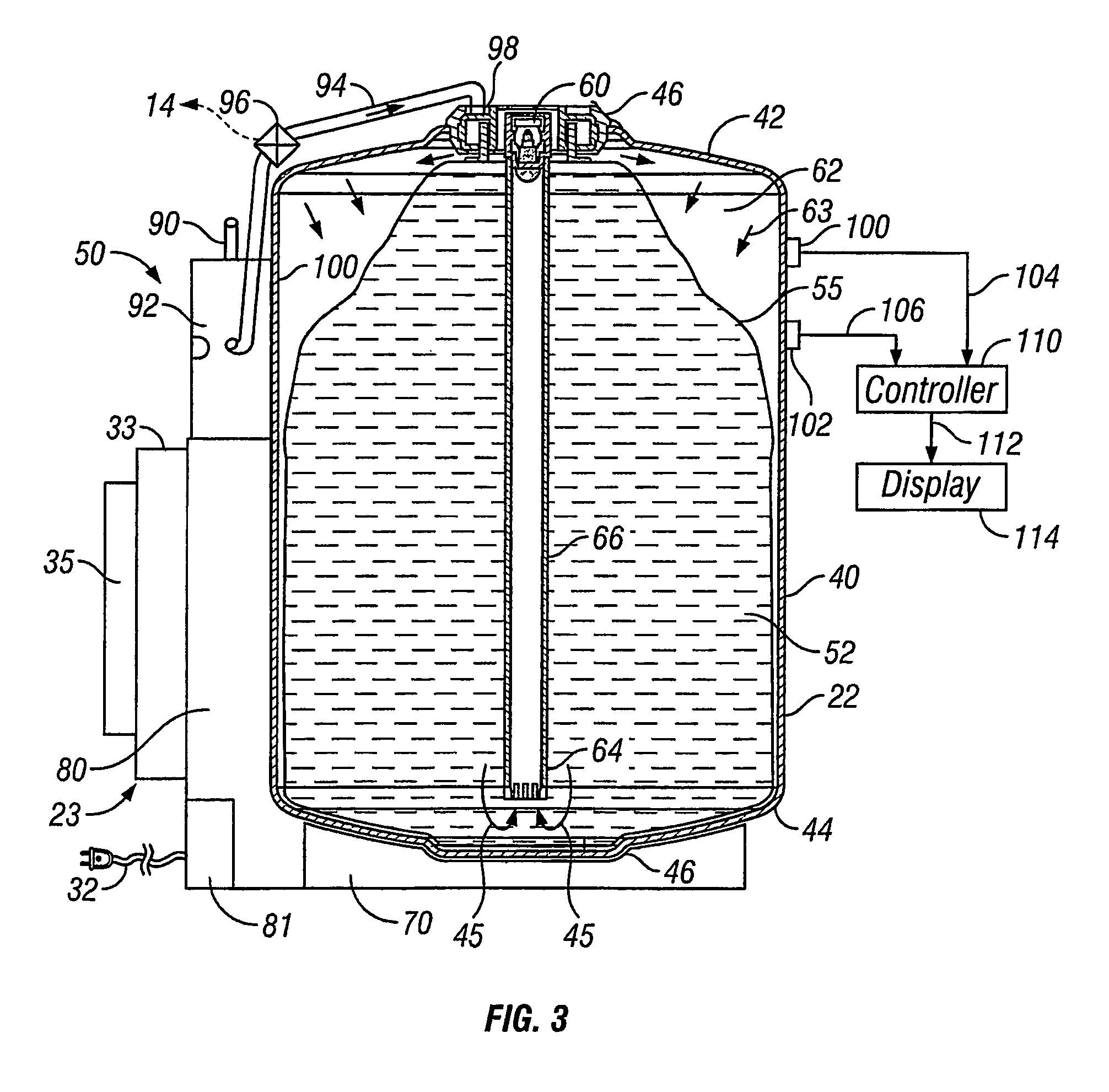
Beer dispensing system with gas pressure reservoir
ActiveUS20060138177A1Reduce dampening pressure fluctuationSufficient pressureLiquid transferring devicesVolume meteringPressure systemPressure sense
A home beer dispensing apparatus has a keg having a self-contained bag filled with a beer and a pressure system. The pressure system creates a pressurized air space between the keg inner walls and the bag to assist in the dispensing of the beer. The pressure system has a keg one-way air valve mounted to a top wall of the keg to permit entry of pressurized air into the keg. The pressure system has a pressure reservoir mounted in the dispensing apparatus outside the keg and in fluid flow communication with the keg one-way valve. The reservoir stores a charge of pressurized air and supplies at least a portion of this charge to the keg through the keg air valve when the dispensing apparatus is operated to dispense the beer. The reservoir provides a reserved charge of pressurized gas that is on hand to reduce dampening pressure fluctuations during beer dispensing which can result in beer frothing, especially during the early stages of beer dispensing when the air head space in the keg is small. Further, the apparatus may also have a pressure sensing system adapted to measure time rate of pressure change in the keg. The apparatus has a signaling device responsive to the time rate of pressure change in the keg to produce a signal related to volume of beer remaining in the bag. Preferably, the signal is displayed visually on the dispensing apparatus.
Owner:ANHEUSER BUSCH INBEV SA
Beer dispensing system with gas pressure reservoir
ActiveUS7810679B2Suppress pressure fluctuationsReduces compressor ratingLiquid transferring devicesVolume meteringPressure systemPressure sense
A home beer dispensing apparatus has a keg having a self-contained bag filled with a beer and a pressure system. The pressure system creates a pressurized air space between the keg inner walls and the bag to assist in the dispensing of the beer. The pressure system has a keg one-way air valve mounted to a top wall of the keg to permit entry of pressurized air into the keg. The pressure system has a pressure reservoir mounted in the dispensing apparatus outside the keg and in fluid flow communication with the keg one-way valve. The reservoir stores a charge of pressurized air and supplies at least a portion of this charge to the keg through the keg air valve when the dispensing apparatus is operated to dispense the beer. The reservoir provides a reserved charge of pressurized gas that is on hand to reduce dampening pressure fluctuations during beer dispensing which can result in beer frothing, especially during the early stages of beer dispensing when the air head space in the keg is small. Further, the apparatus may also have a pressure sensing system adapted to measure time rate of pressure change in the keg. The apparatus has a signaling device responsive to the time rate of pressure change in the keg to produce a signal related to volume of beer remaining in the bag. Preferably, the signal is displayed visually on the dispensing apparatus.
Owner:ANHEUSER BUSCH INBEV SA
Jerk management using multivariable active driveline damping
ActiveUS7315774B2Actively dampen magnitudeMinimize impactHybrid vehiclesDigital data processing detailsDrive wheelFeedback control
A multivariable feedback control approach to actively dampen magnitude of jerks in a powertrain system using multiple torque-control devices is offered. To manage jerks, a desired axle torque is restricted when a torque reversal occurs. When the vehicle operator or the system executes a command that requires change in direction of torque, the desired axle torque is limited to a low level until the lash estimate has changed accordingly. During this transition time, active damping controls driveline component speeds so that the effect of lash take-up is minimized. After lash take-up occurs, the desired axle torque proceeds without restriction. The invention includes determining a desired axle torque, an output speed of the transmission, and an output speed of a driven wheel of the driveline. One of the devices is controlled based upon a time-rate change in the desired axle torque.
Owner:GM GLOBAL TECH OPERATIONS LLC
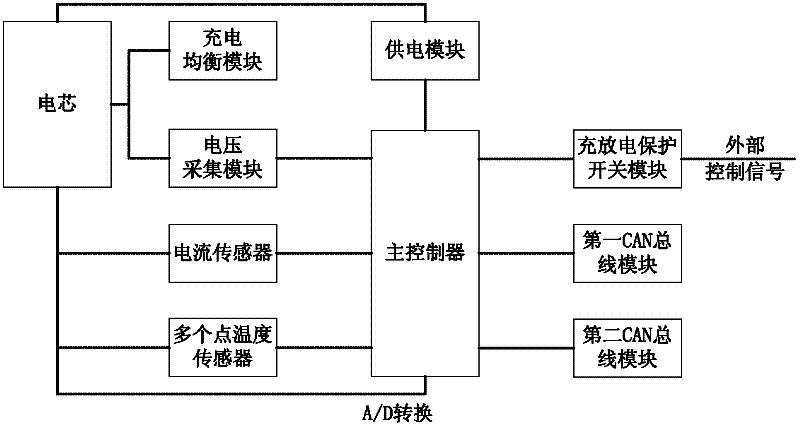
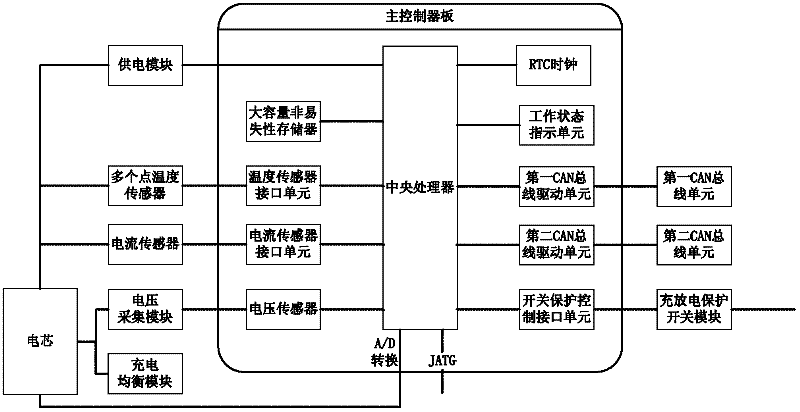
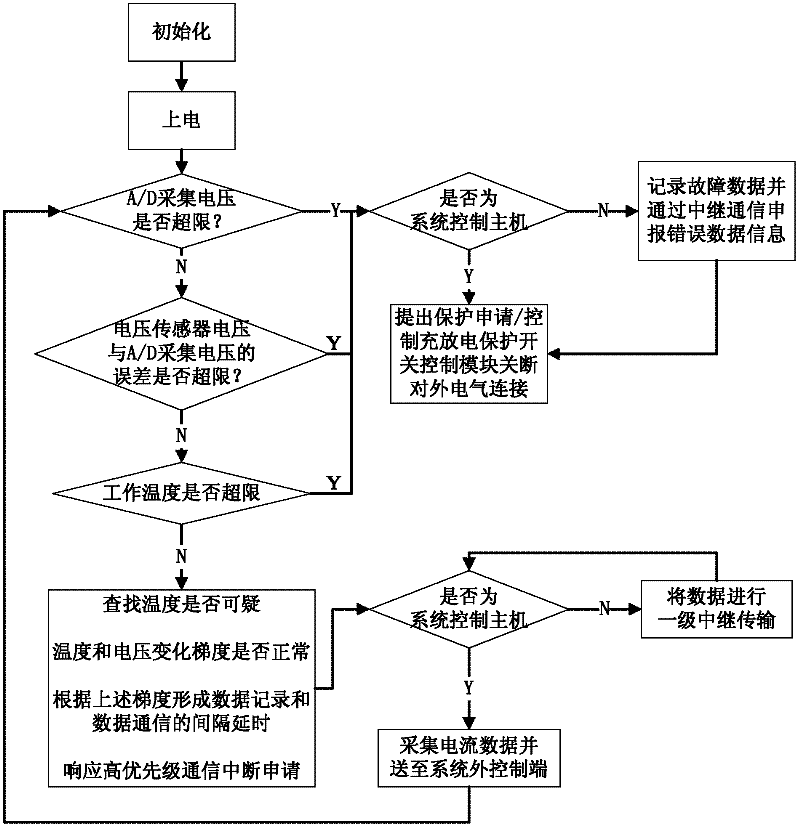
Modular lithium power battery and its management system and management method
InactiveCN102263303AFault-tolerantImprove reliabilityEmergency protective circuit arrangementsElectrical testingFault toleranceElectrical battery
The invention provides a modular lithium power battery and its management system and management method, which collect important cell voltage and current parameters in two independent ways; the charge and discharge protection switch control module adopts two independent paths for transmission , thereby greatly improving system reliability by providing redundancy. In addition, by simultaneously using the parameter threshold and parameter gradient (rate of change per unit time) as the basis for judging the control state, it has certain fault predictability; it has certain fault tolerance by analyzing the obtained parameters according to the correlation between different parameters; CAN bus communication Use relays and algorithms for dynamically setting communication priorities to ensure that fault status is quickly transmitted to the system master. The connection expansion mode of the modular lithium power battery includes the electrical connection and communication connection between the systems.
Owner:福州天和新能电子科技有限公司
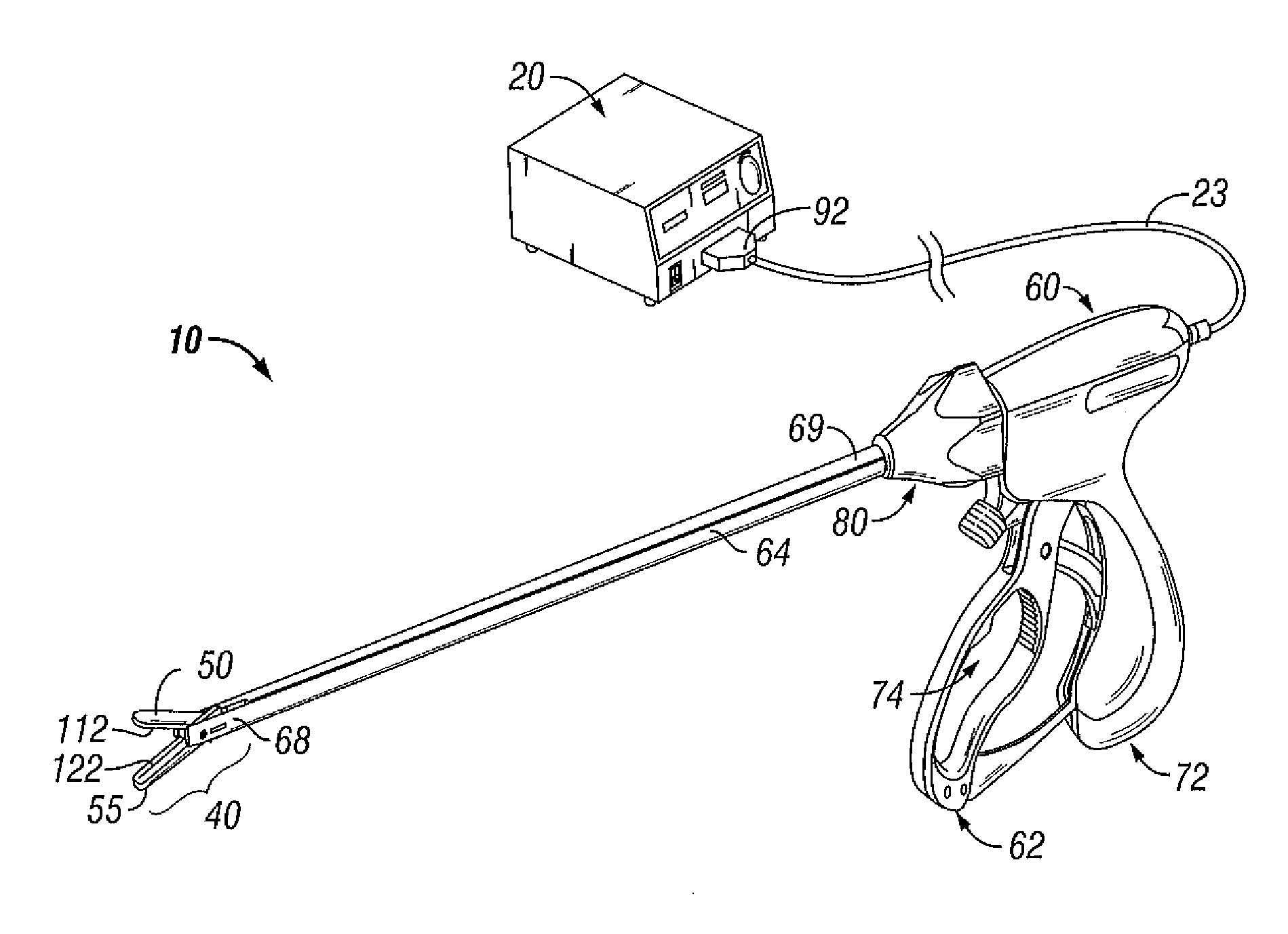
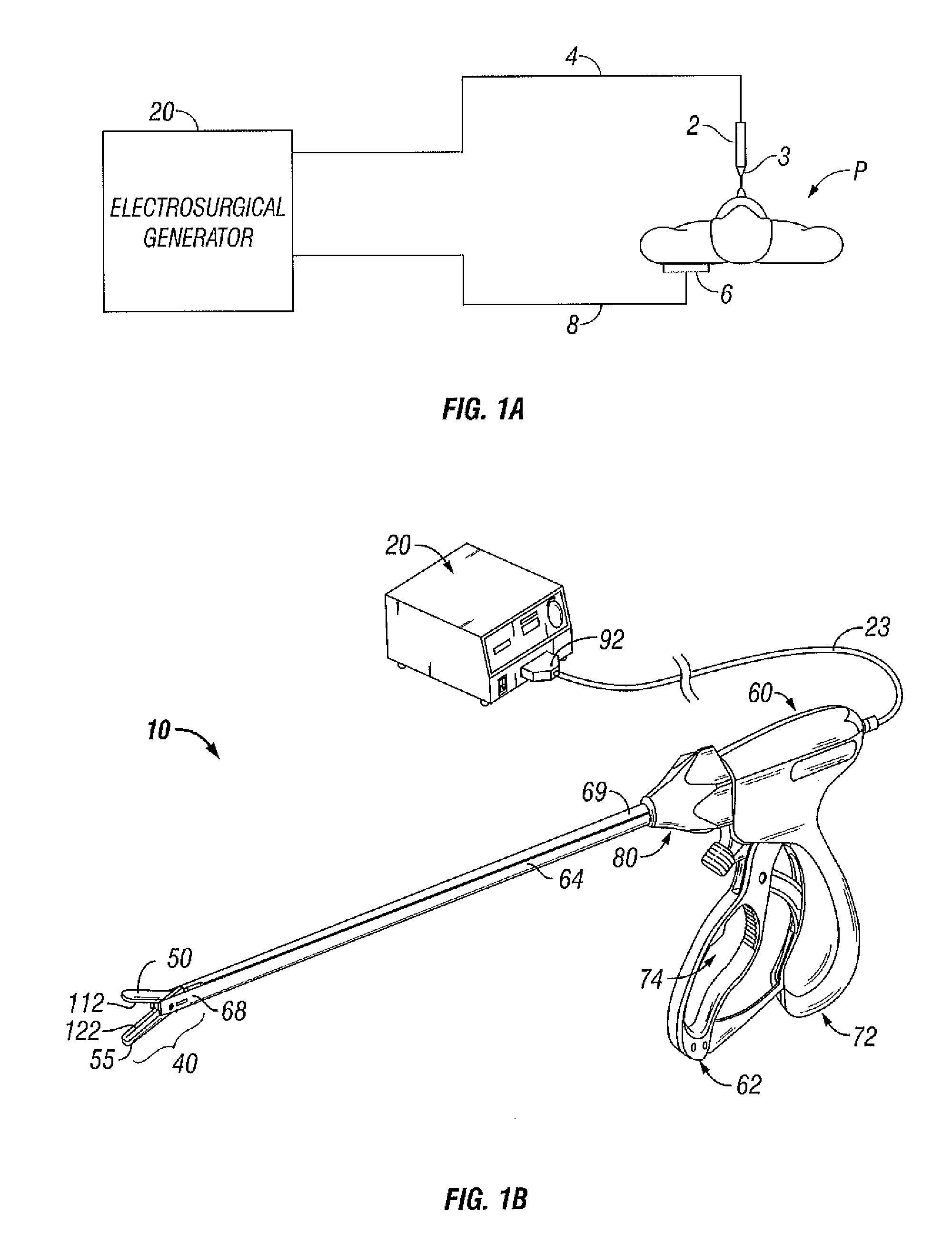
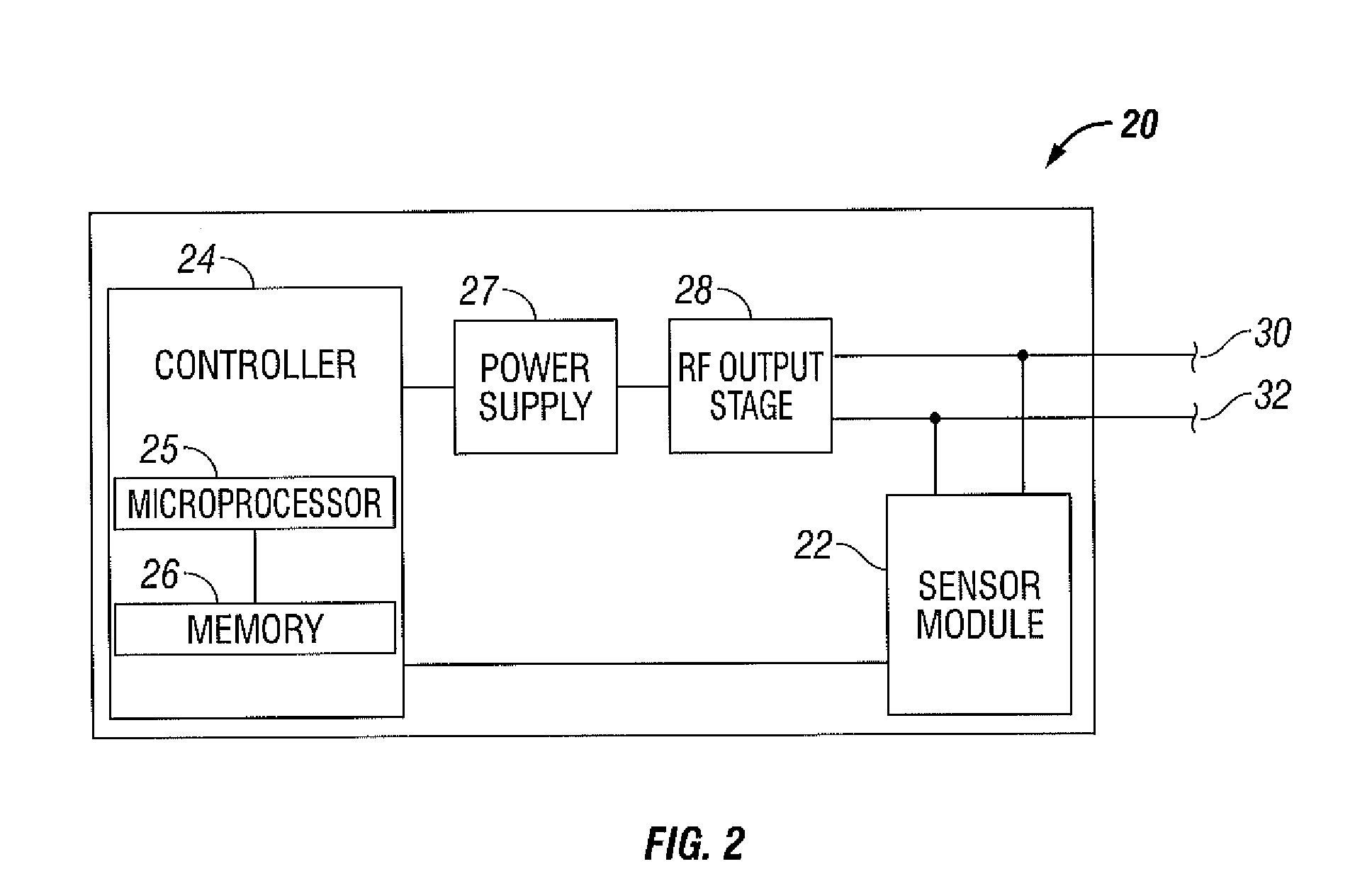
Electrosurgical Apparatus With High Speed Energy Recovery
A circuit for controlling the discharging of stored energy in an electrosurgical generator includes a pulse modulator which controls an output of a power supply. At least one comparator is configured to provide an error signal to the pulse modulator based on a comparison between an output signal generated by the power supply and a feedback signal generated in response to the application of energy to tissue. A discharge circuit is configured to control the discharge of the output of the power supply to an inductive load disposed in parallel with the output of the power supply based on the comparison between the output signal and the feedback signal. The discharge circuit provides a rapid response and time rate control of the delivered electrosurgical energy by controlling the power supply and delivered RF energy in real time, based on a feedback signal generated in response to the application of energy to tissue.
Owner:TYCO HEALTHCARE GRP LP
Method and system of mass and multiple casualty triage
InactiveUS7761309B2Maximize survivabilityMaximize savingMental therapiesDiagnostic recording/measuringTriageDeterioration rate
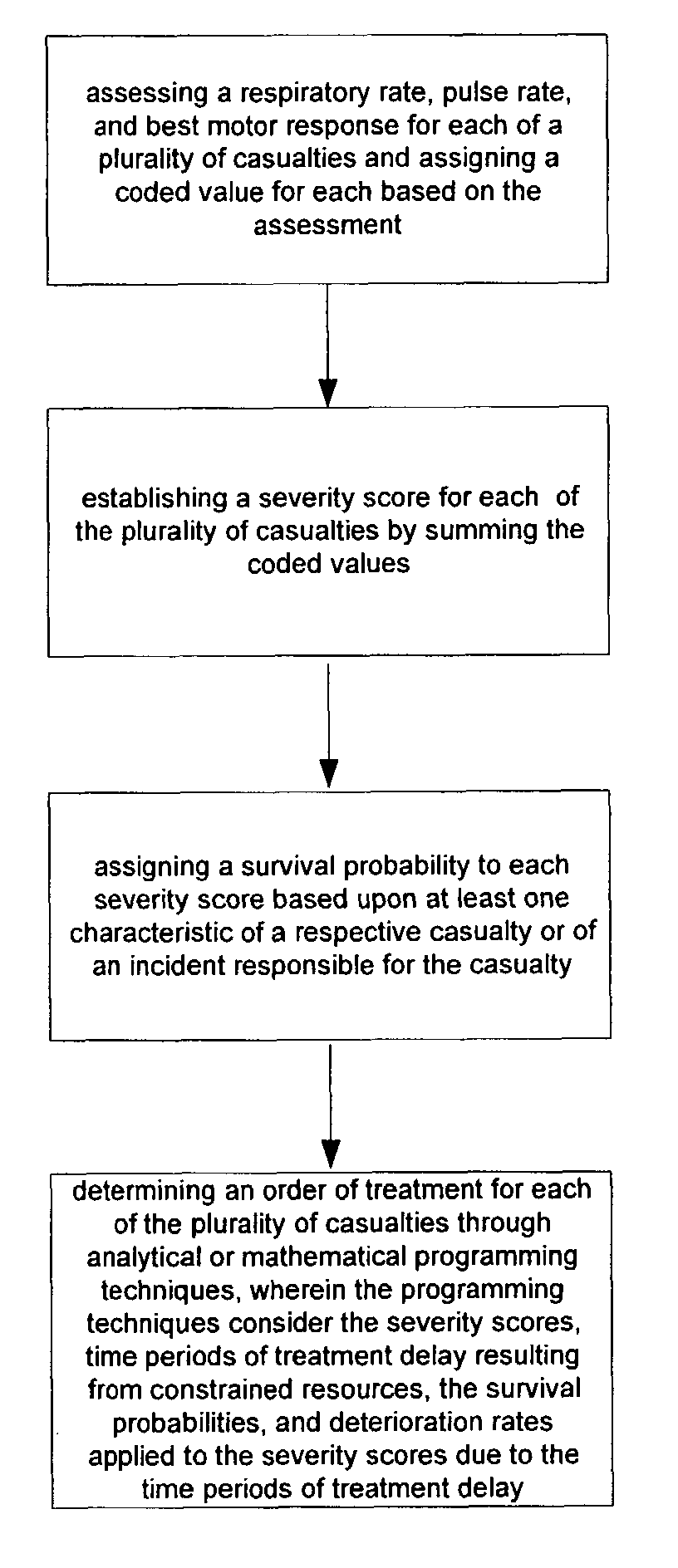
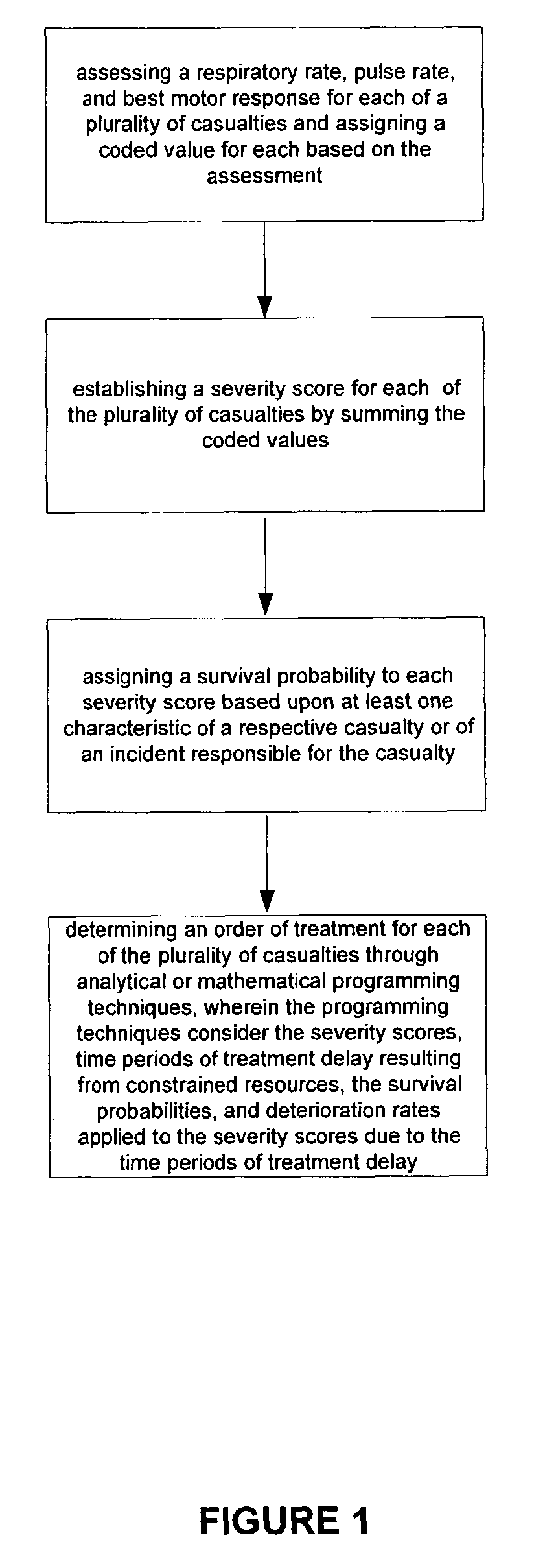
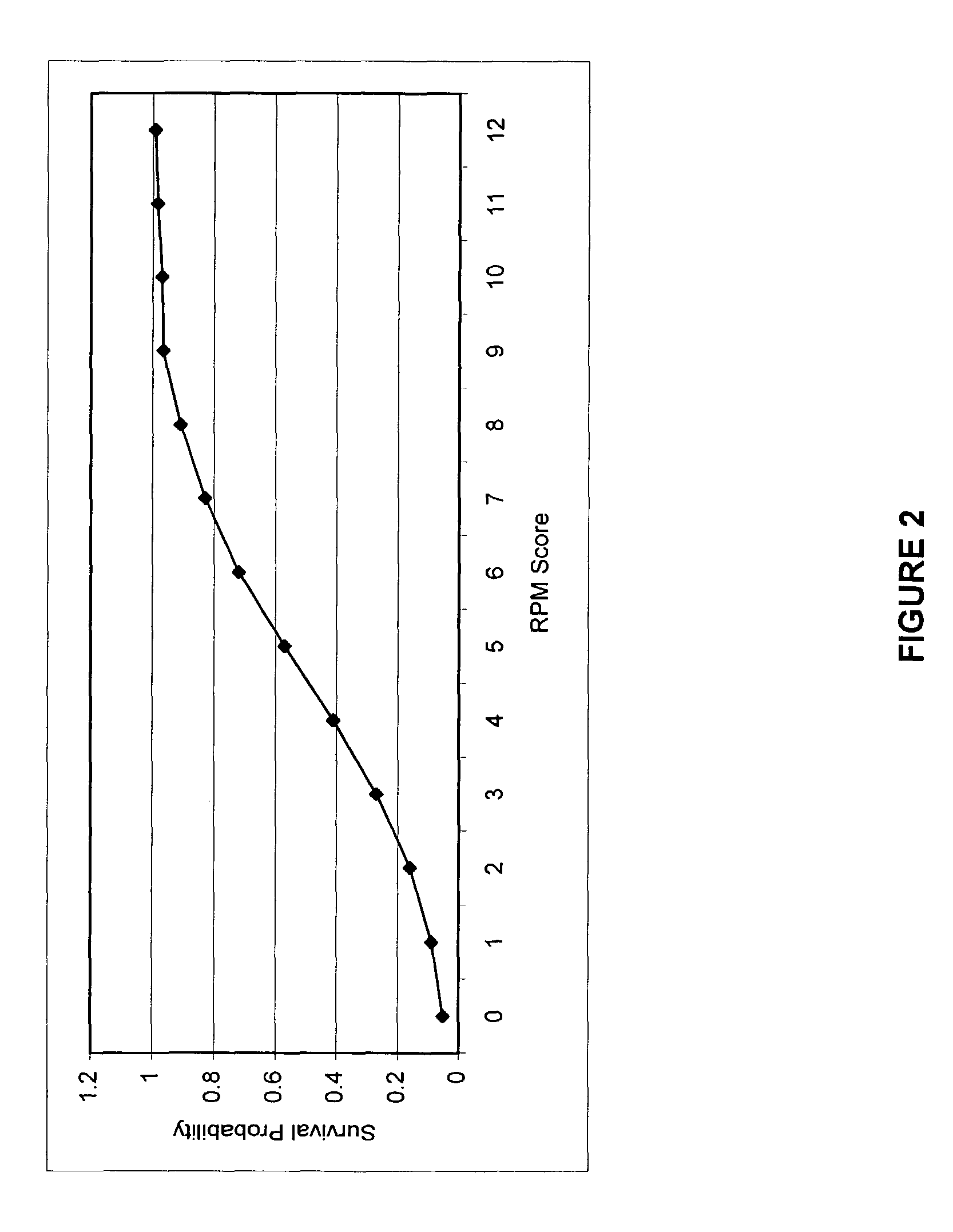
The present invention is a method and system of triage that assesses a severity score for each casualty, and determines a treatment prioritization plan to maximize the number of survivors. The present invention includes a score-based mathematical algorithm for resource-constrained triage, where an optimal number of survivors is determined through a methodology that can be mathematically modeled and solved, a methodology that considers victim survival probabilities, victim deterioration rates, and resource availability. First, each casualty is assessed and an RPM severity score is assigned based upon a sum of coded values for respiratory rate, pulse rate, and best motor response. Next, treatment priorities are determined from analytical or mathematical techniques, such as dynamic or linear programming, in consideration of survival probabilities associated with each RPM score, and deterioration-with-time rates for each RPM score for victims awaiting transport and treatment and the availability and timing of transport and treatment services.
Owner:THINKSHARP
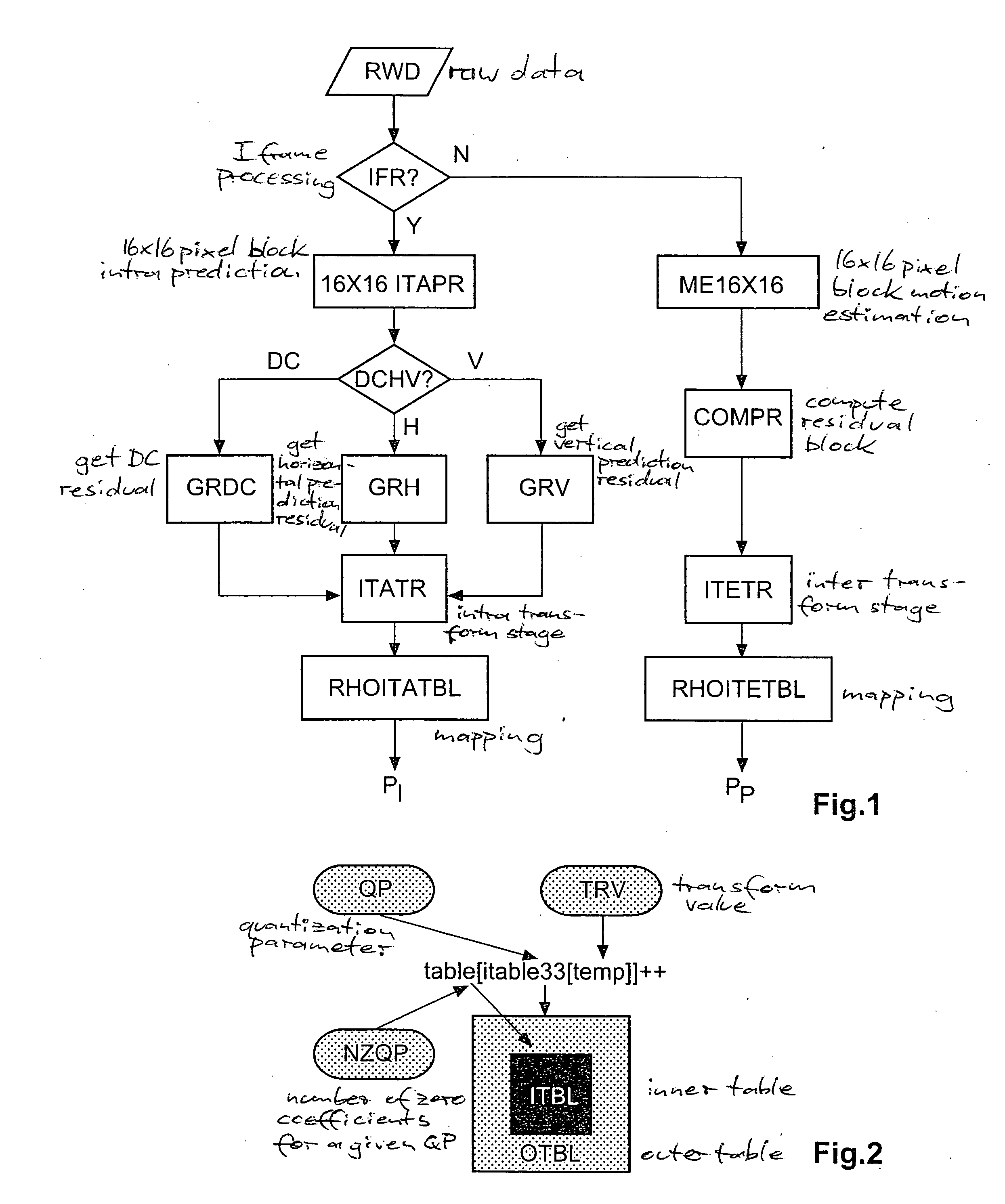
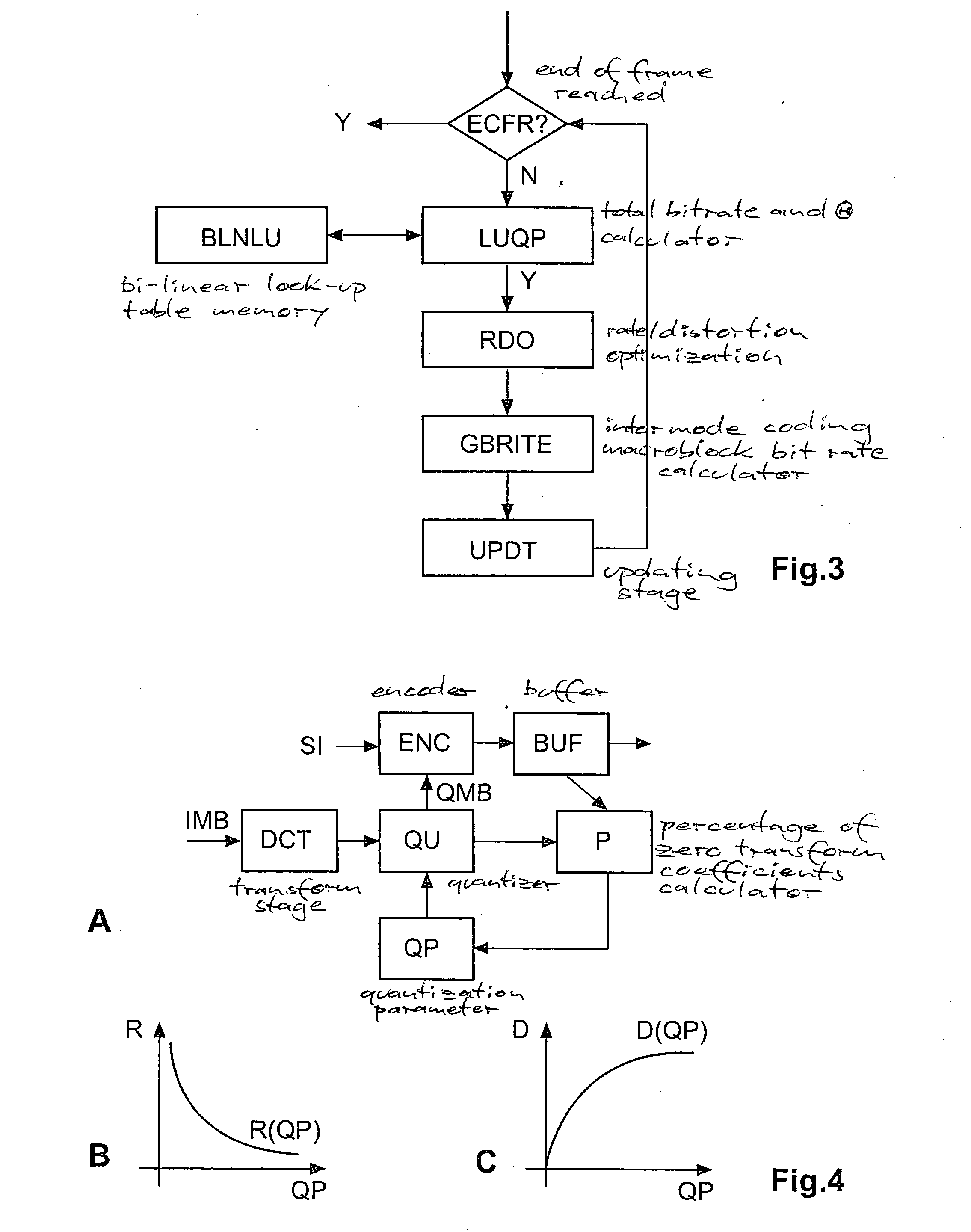
Method for controlling the encoder output bit rate in a block-based video encoder, and corresponding video encoder apparatus
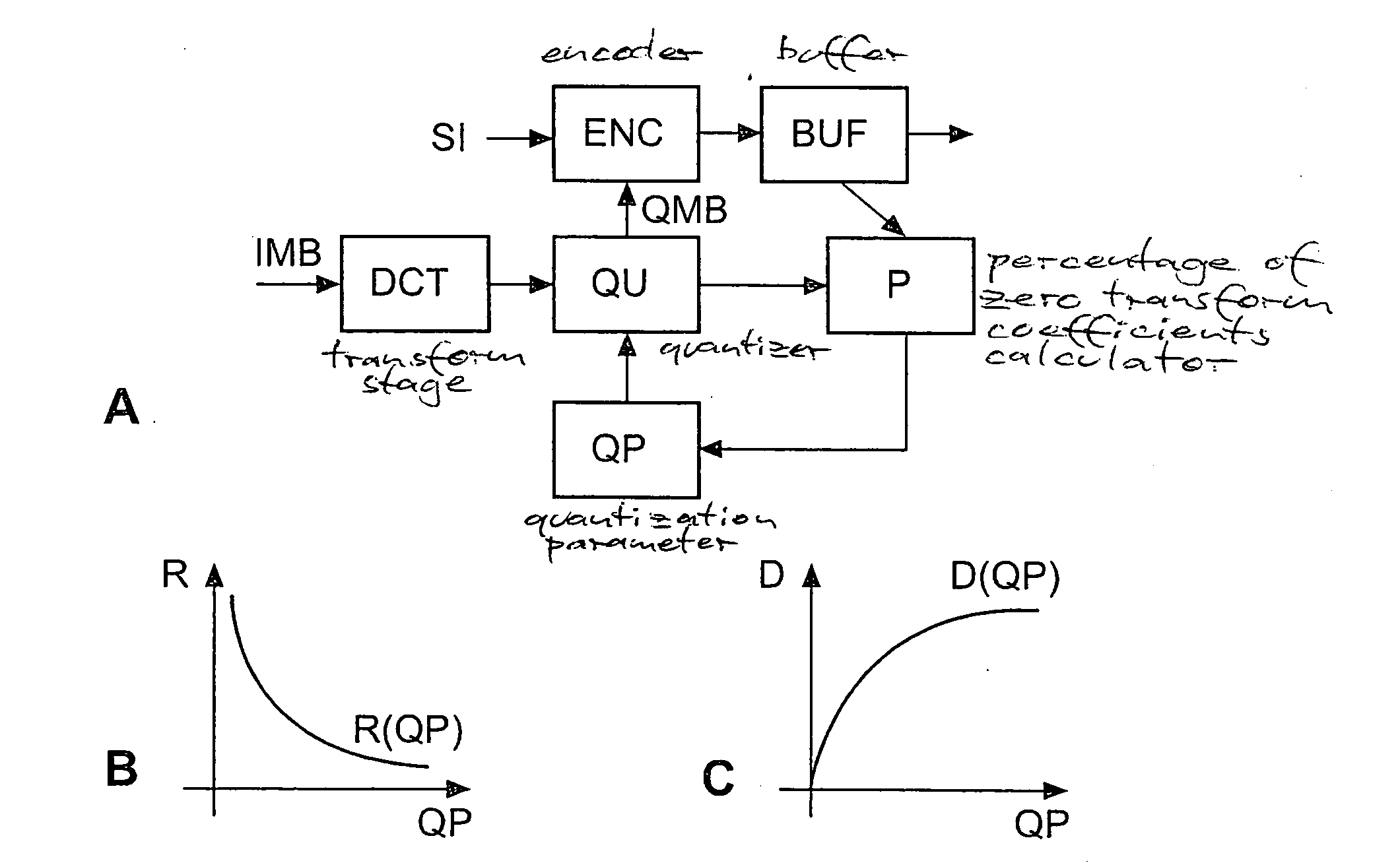
ActiveUS20070009027A1Improve mapping accuracyReduce computing timeColor television with pulse code modulationColor television with bandwidth reductionLinear modelLinearity
Constant-bitrate rate control is very useful for real-time video transmission. However, it is difficult to realize a good CBR rate control in an MPEG4-AVC video codec. According to the invention, an adapted ρ-domain rate control processing for real-time rate control is applied, whereby ρ is the percentage of zero amplitude transform coefficients following quantisation. A couple of tables are used for mapping between the quantization parameters and ρ. A detailed analysis at transform-level is carried out in order to get the slope of the relationship between the bitrate and ρ. The slope of the linear model is constrained by a look-ahead procedure with respect to the neighbour frames or blocks.
Owner:INTERDIGITAL MADISON PATENT HLDG
Neurostimulation with activation based on changes in body temperature
ActiveUS20060142802A1Facilitate rapid interventionRaise the possibilityElectrotherapyDiagnostic recording/measuringMoving averageStability parameter
Improved methods and devices are provided for detecting and / or predicting the onset of an undesirable physiological event or neural state, such as an epileptic seizure, to facilitate rapid intervention with a treatment therapy such as neurostimulation or drug therapy. The methods and devices involve monitoring the patient's body temperature, preferably by an implanted temperature sensor, to detect a change in a body temperature parameter over a first time period. The temperature parameter change may comprise an increase or decrease in the patient's body temperature over a first time period, time rate of change of body temperature over a first time period, a moving average temperature over a first time period, an increase or decrease in body temperature exceeding a target temperature over a first time period, an elevated or reduced body temperature over first time period, or a temperature stability parameter over a first time period. The sampling period at which body temperature measurements are made may be changed manually or depending upon a sensed body parameter, including temperature. When a parameter change is detected that exceeds a threshold, neurostimulation therapy is delivered to a neural structure of the patient.
Owner:LIVANOVA USA INC
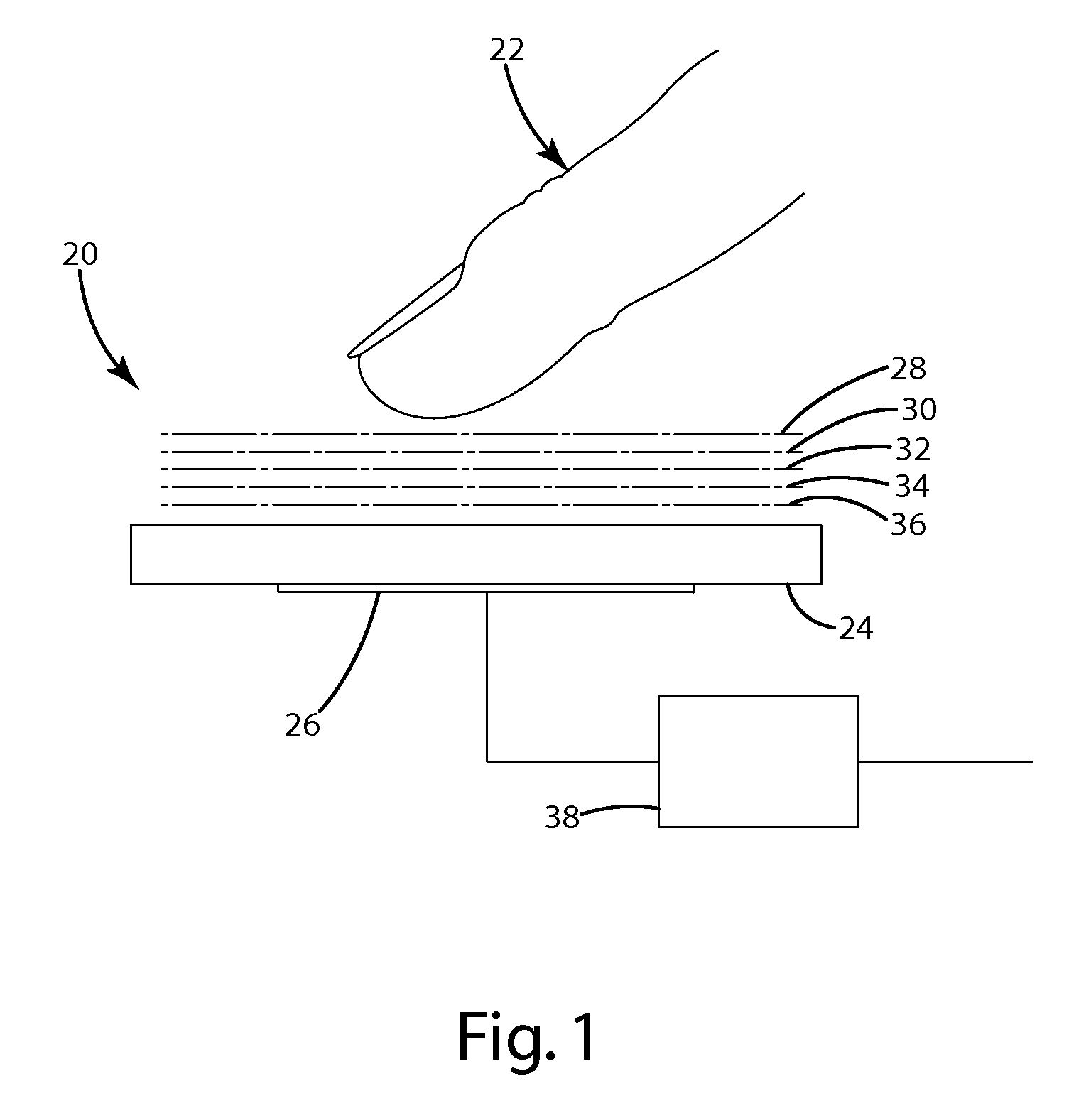
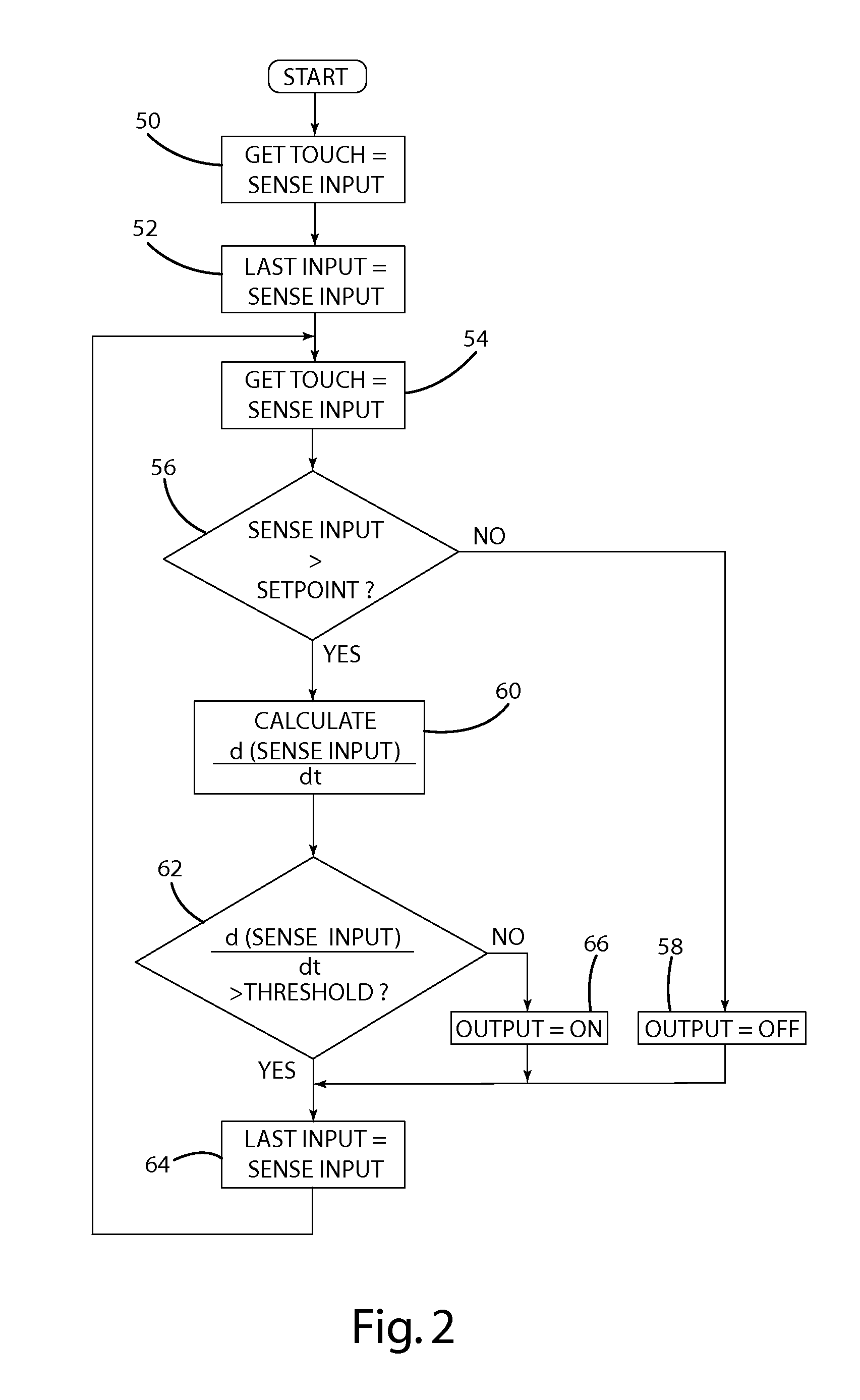
Apparatus and method for determining a touch input
A capacitive sensor for detecting a stimulus. The capacitive sensor includes an electrode and a processing unit electrically coupled to the electrode and configured to determine the presence of a stimulus based on the rate of change of the electrode capacitance. A substrate is positioned adjacent the electrode, wherein the stimulus corresponds to the placement of an object against the substrate. The processing unit is operative to determine a time rate of change based on successive measurements of the electrode capacitance. In addition, the processing unit is operative to determine the presence of a stimulus in response to the time rate of change being less than a reference value.
Owner:ALSENTIS
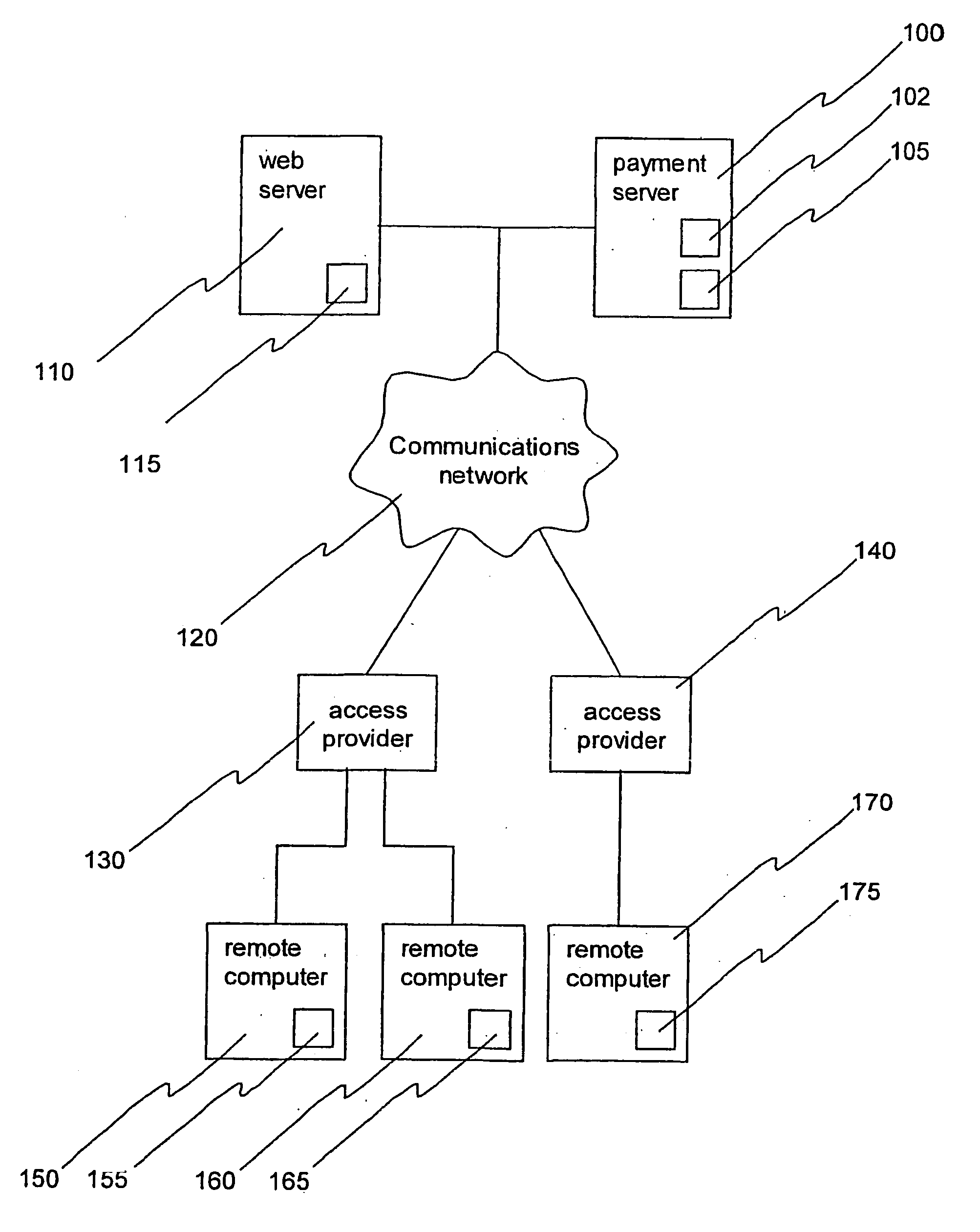
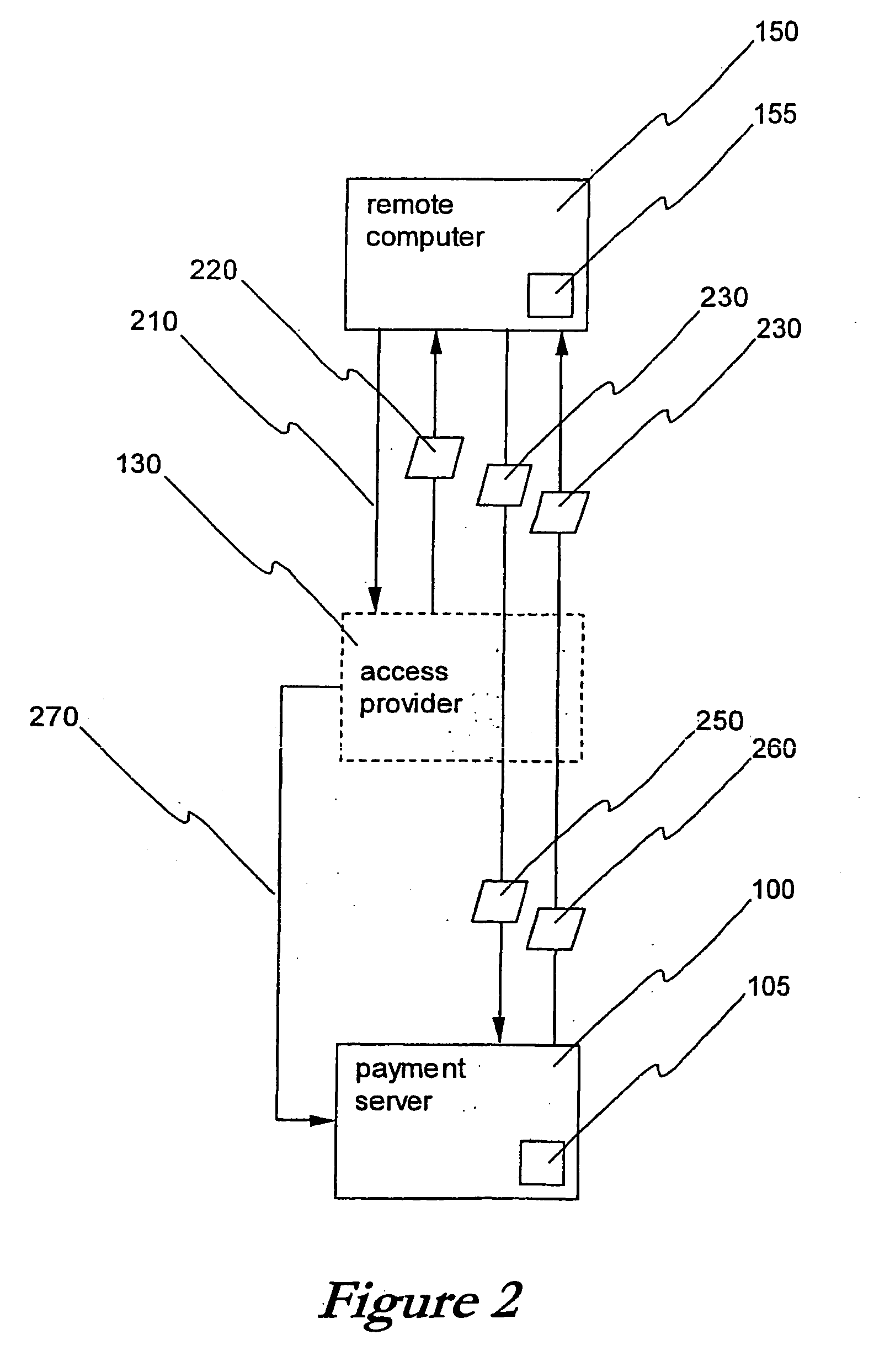
System and method for third party facilitation of electronic payments over a network of computers
InactiveUS20040015413A1Buying/selling/leasing transactionsPayment circuitsThird partyInternet privacy
A facilitator computer for making electronic payments. The first and second parties are a payee and a payer, who maybe a vendor (with a vendor computer) and a purchaser (with a purchaser computer). The method involves a message from the vendor computer, identifying the vendor computer and transaction details, which is received by the facilitator computer (trusted thrid party). Subsequent processing by the facilitator computer, involving interaction with the purchaser computer leads to a secure payment transaction. In coordinating the transaction, the payment server may check as to whether the customer's computer is available (on-line) and / or whether the goods or services are supplied at a timed rate. The identity of the vendor and purchaser computers is verified and authenticated against a known list of computer identities to improve security in the system.
Owner:INTERNET PAY MASTER CORP
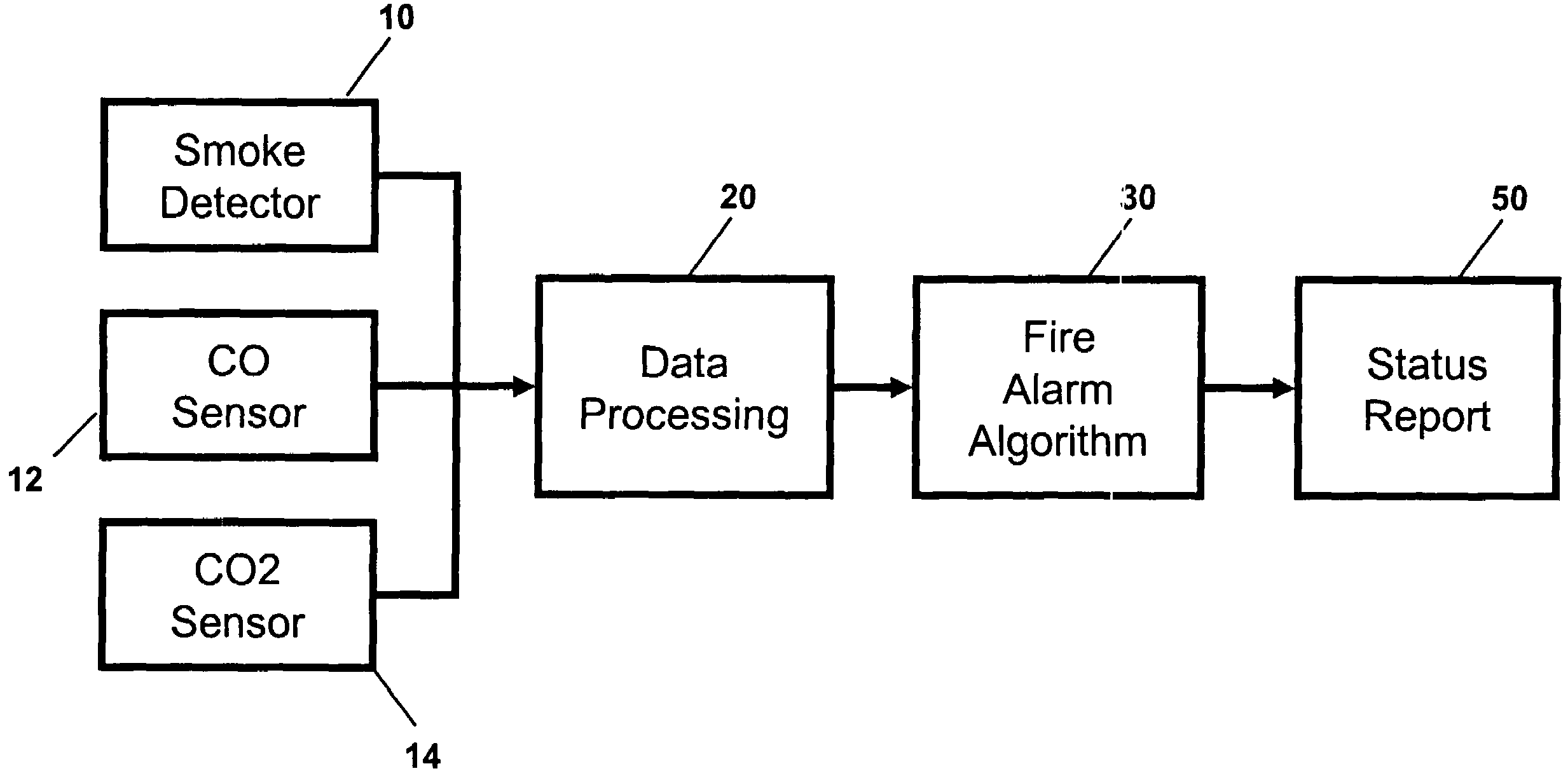
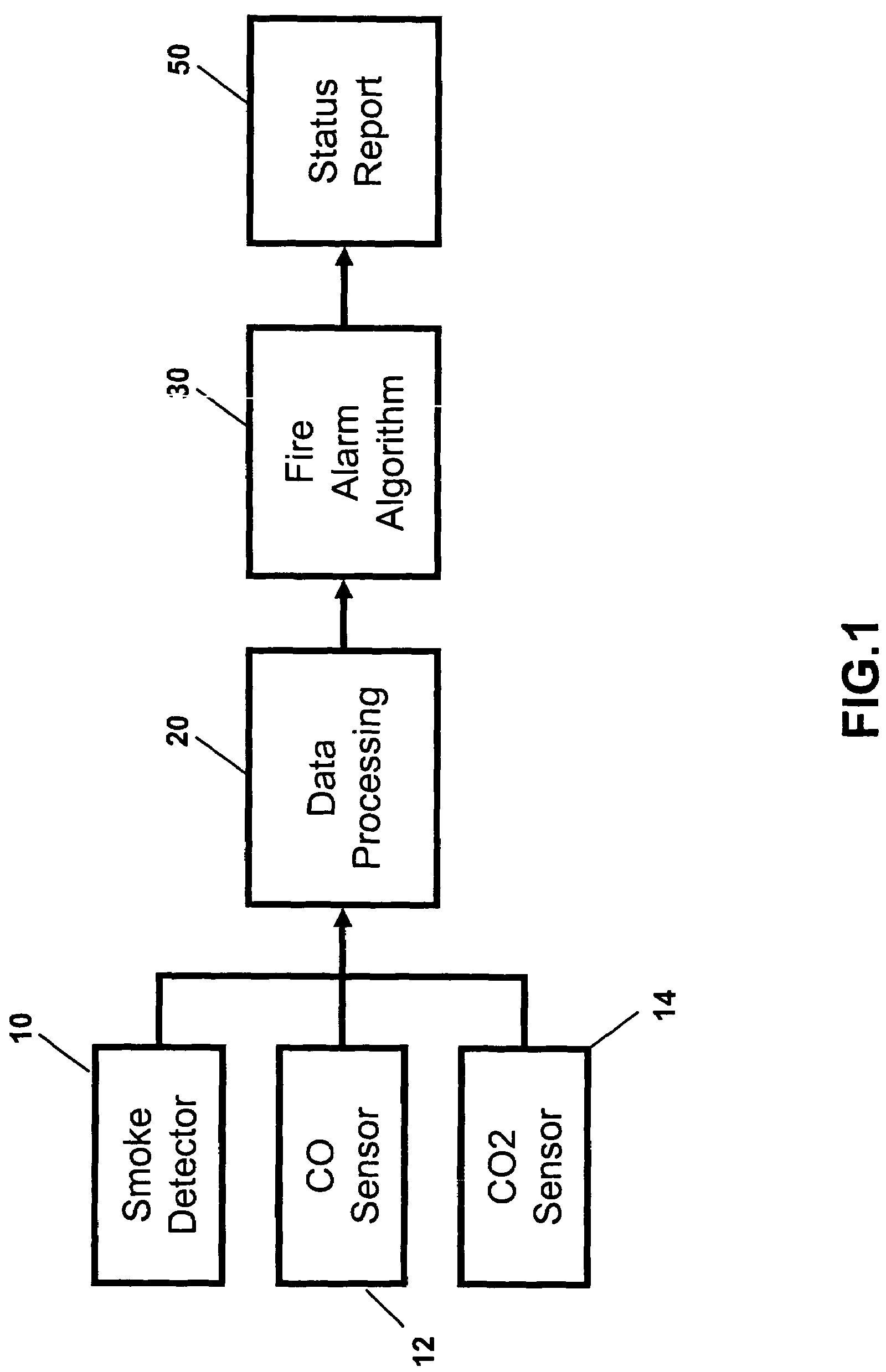
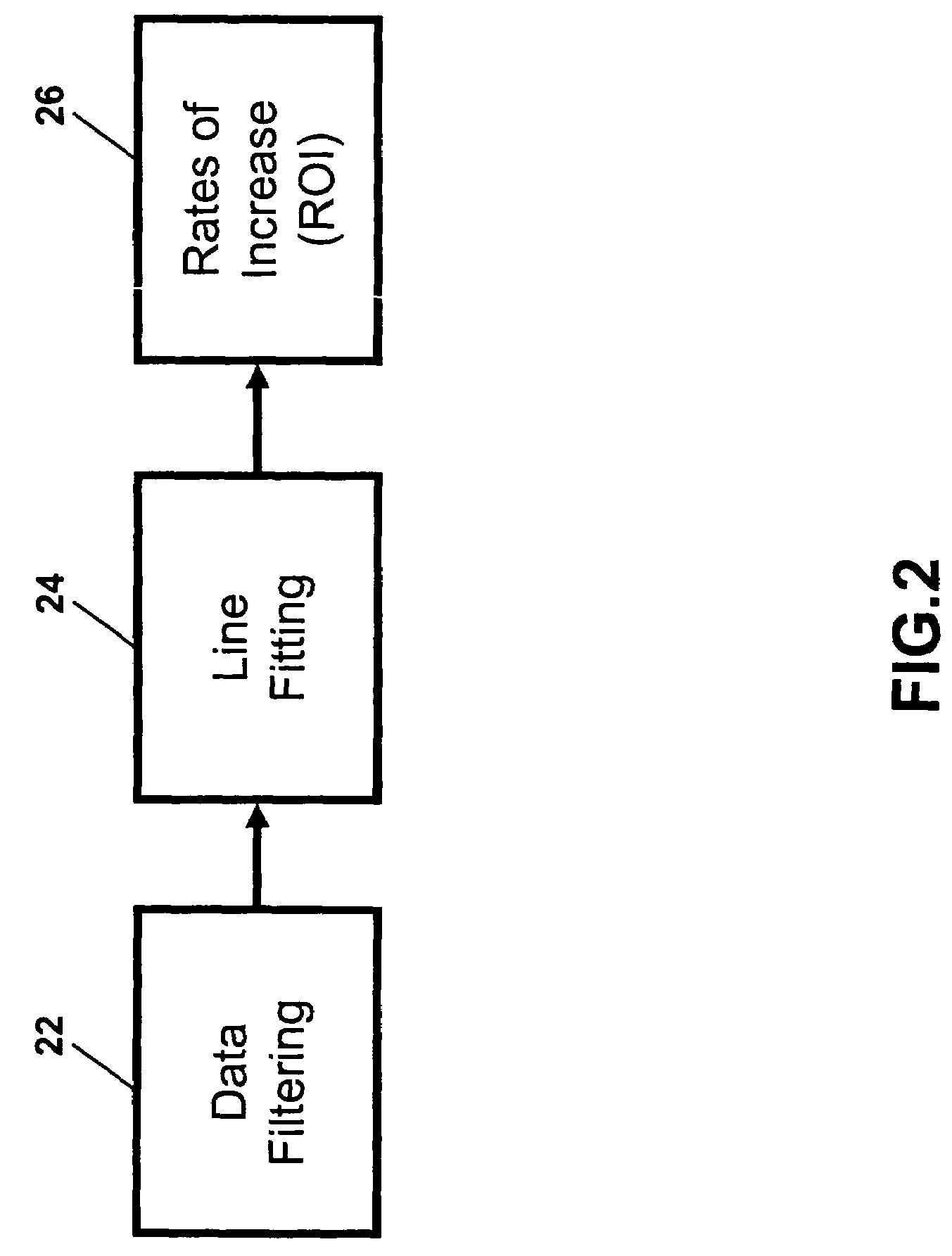
Fire alarm algorithm using smoke and gas sensors
An apparatus for and method of detecting fires comprising detecting (with one or more detectors) levels of carbon monoxide, carbon dioxide, and smoke in an ambient environment, computing (using a processor) over time rates of increase of each of the levels, and generating an alarm if one or more of the rates of increase exceed predetermined threshold rates of increase.
Owner:SOUTHWEST SCI
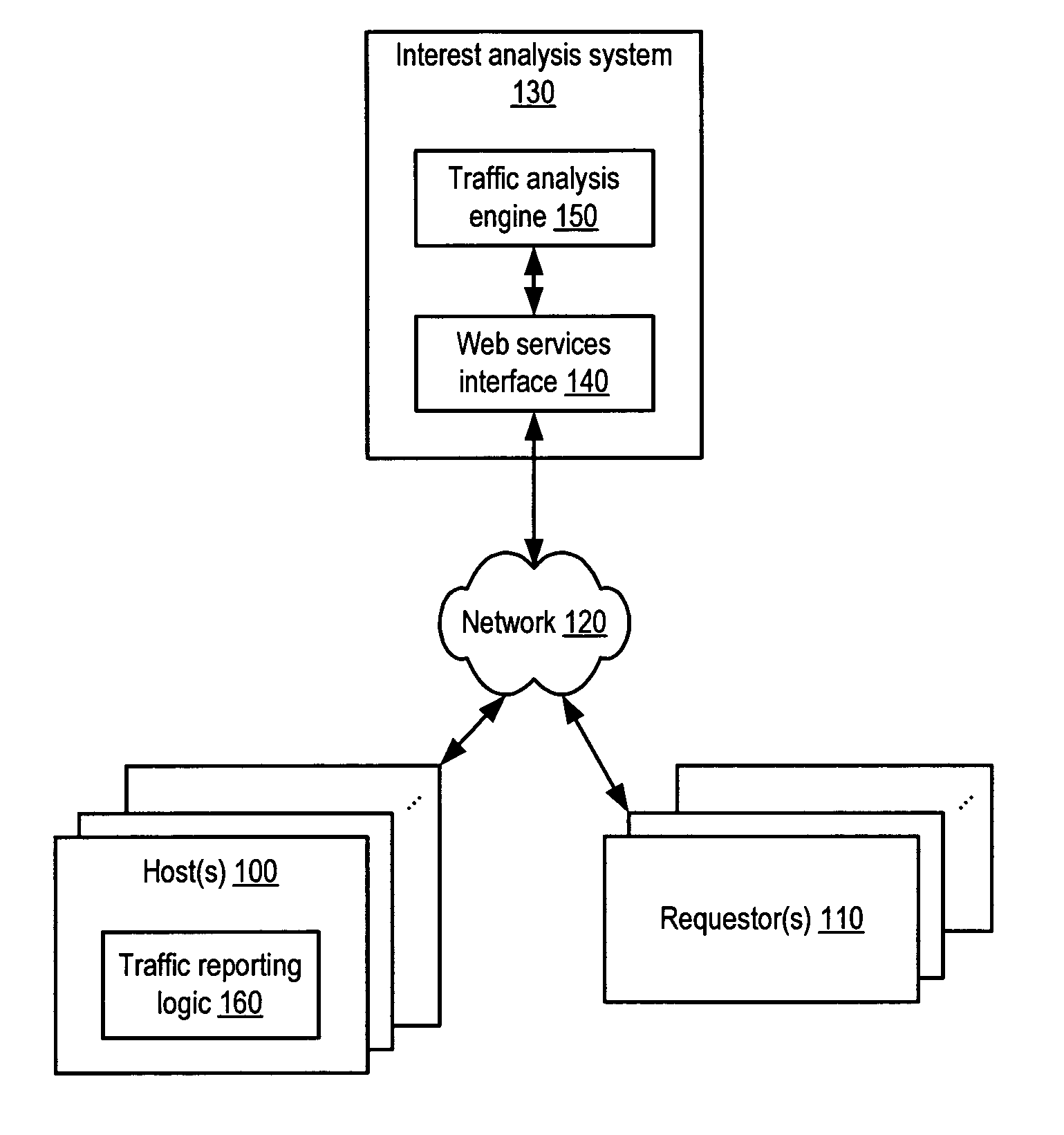
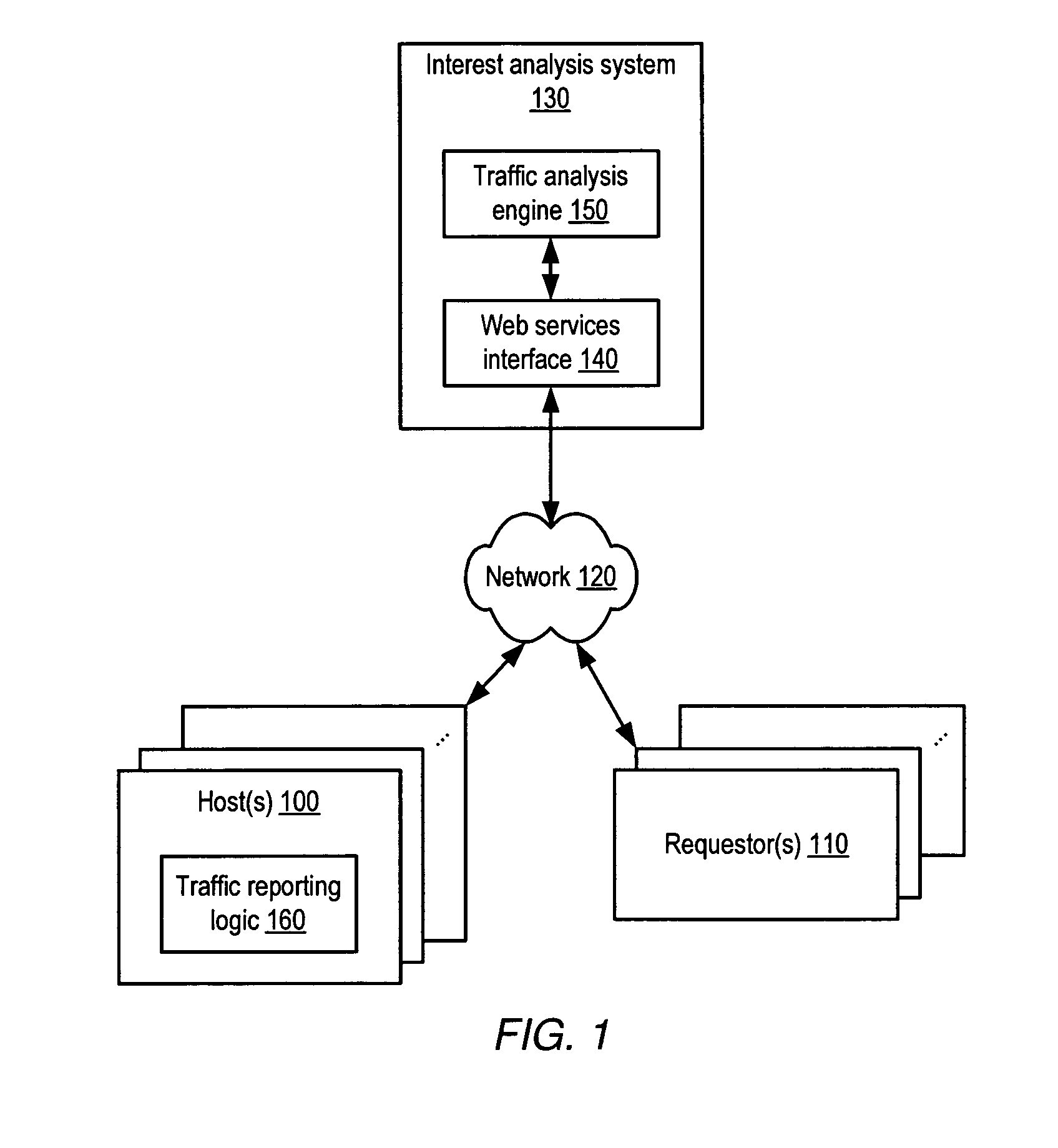
System and method for indicating interest of online content
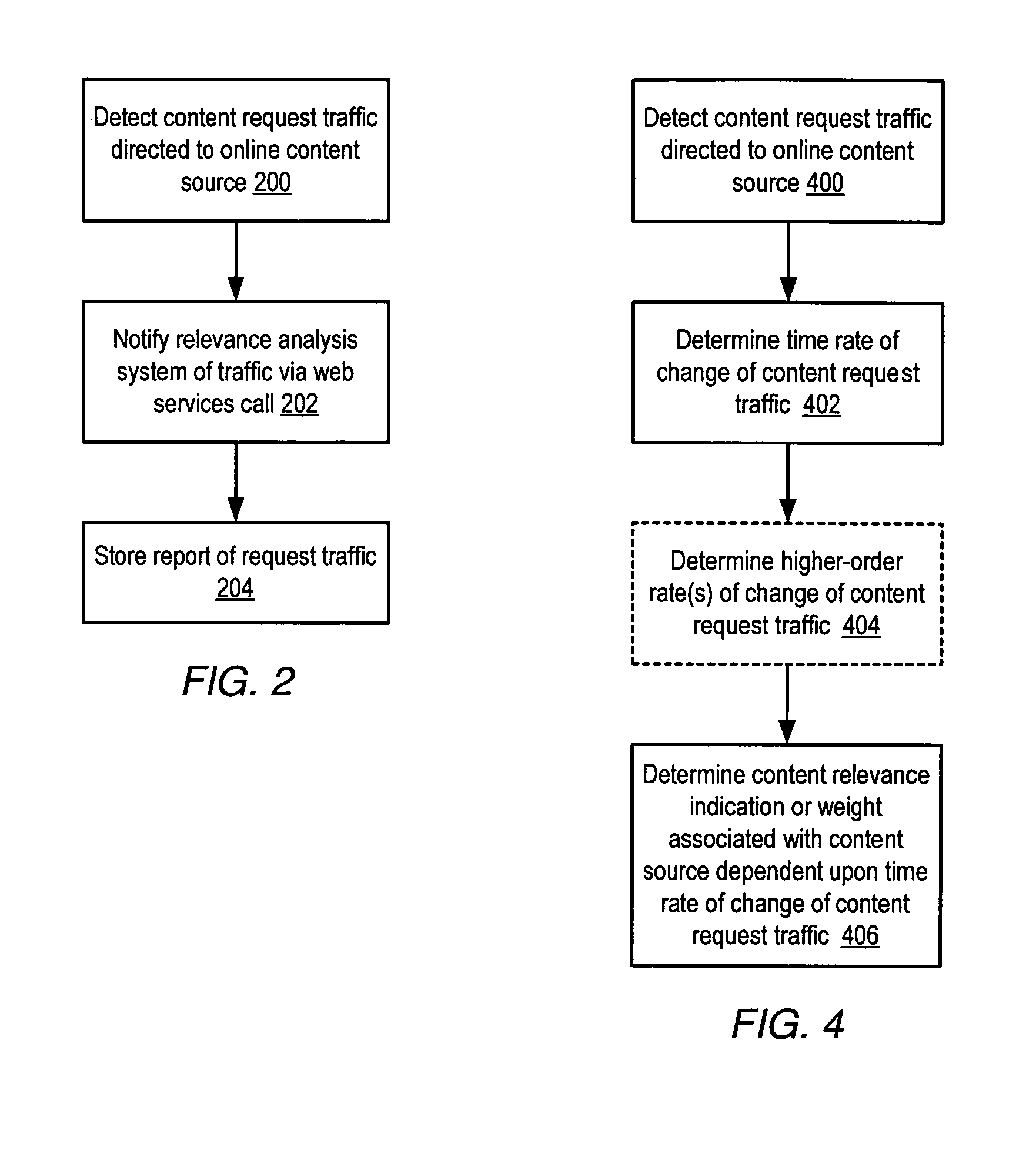
Systems and methods for displaying interest levels of online content. In one embodiment, a system may include a web browser. A badge code module may execute within an execution environment provided by the web browser and may display an indication of content interest associated with a content source, where the indication is dependent upon a time rate of change of content request traffic directed to the content source. In another embodiment, a system may include a web browser configured to generate a web browser window. A plugin module may be integrated with the web browser for execution, may generate a display interface integrated within the browser window, and may display an indication of content interest associated with a content source via the display interface, where the indication is dependent upon a time rate of change of content request traffic directed to the content source.
Owner:AMAZON TECH INC
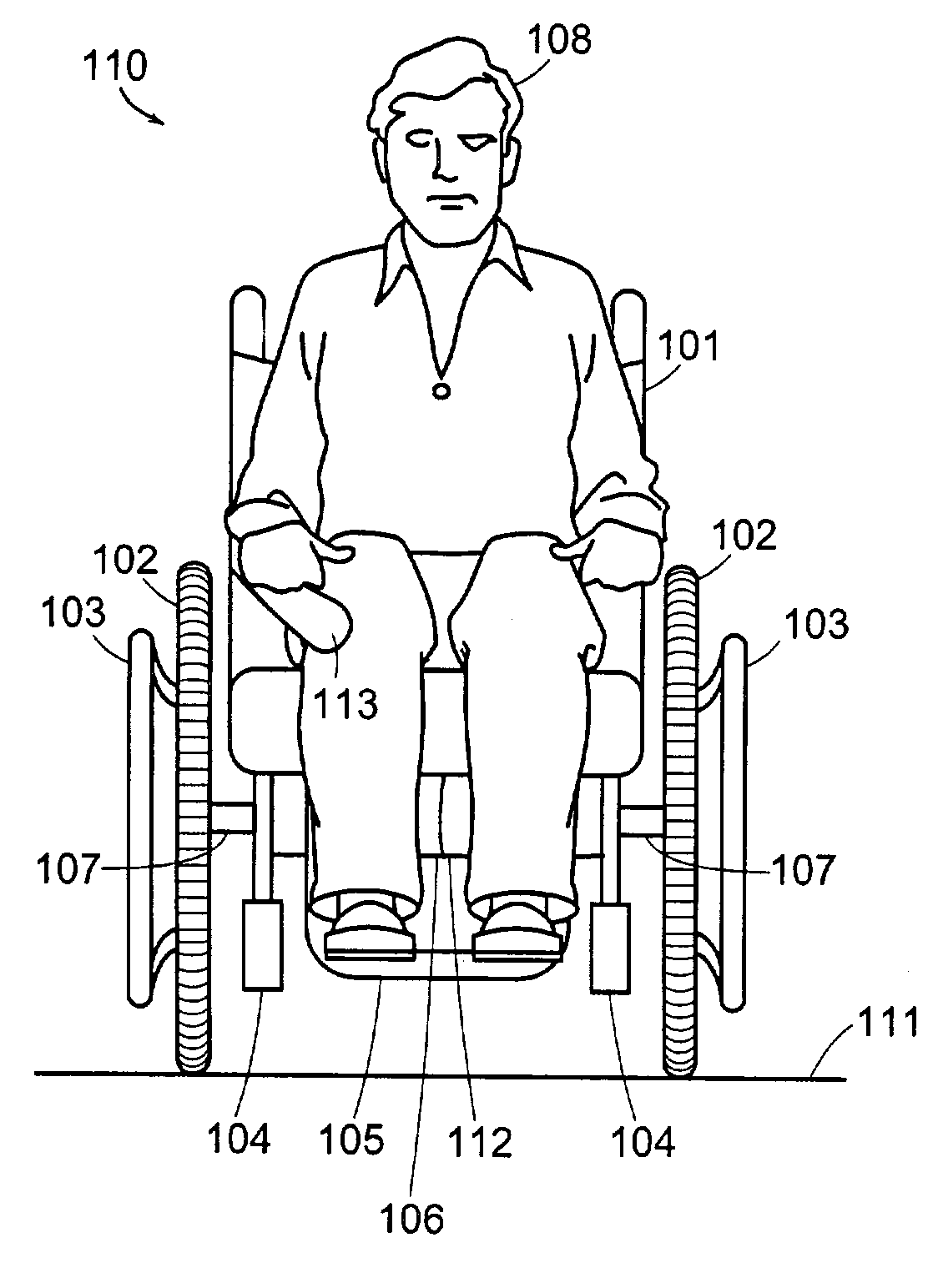
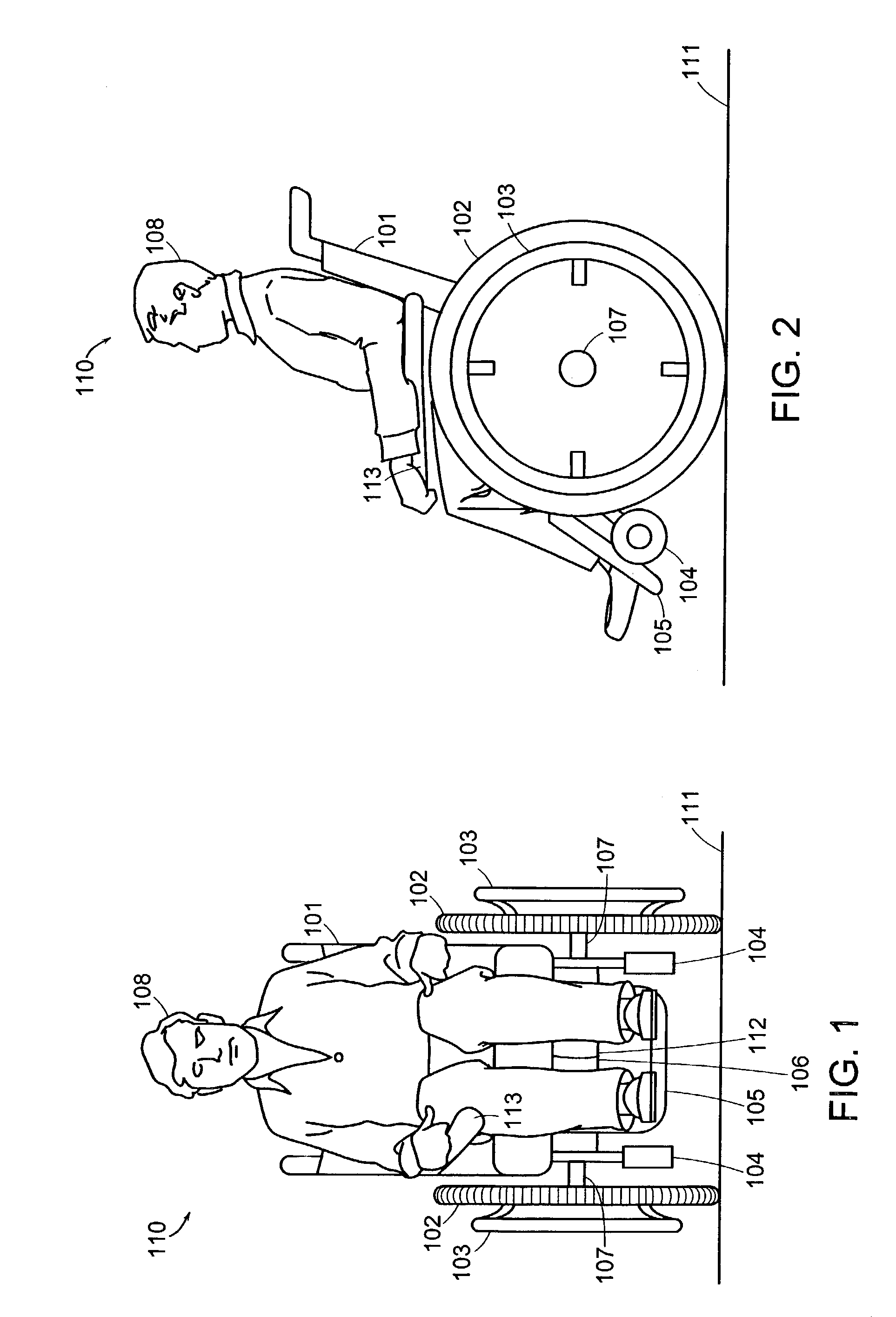
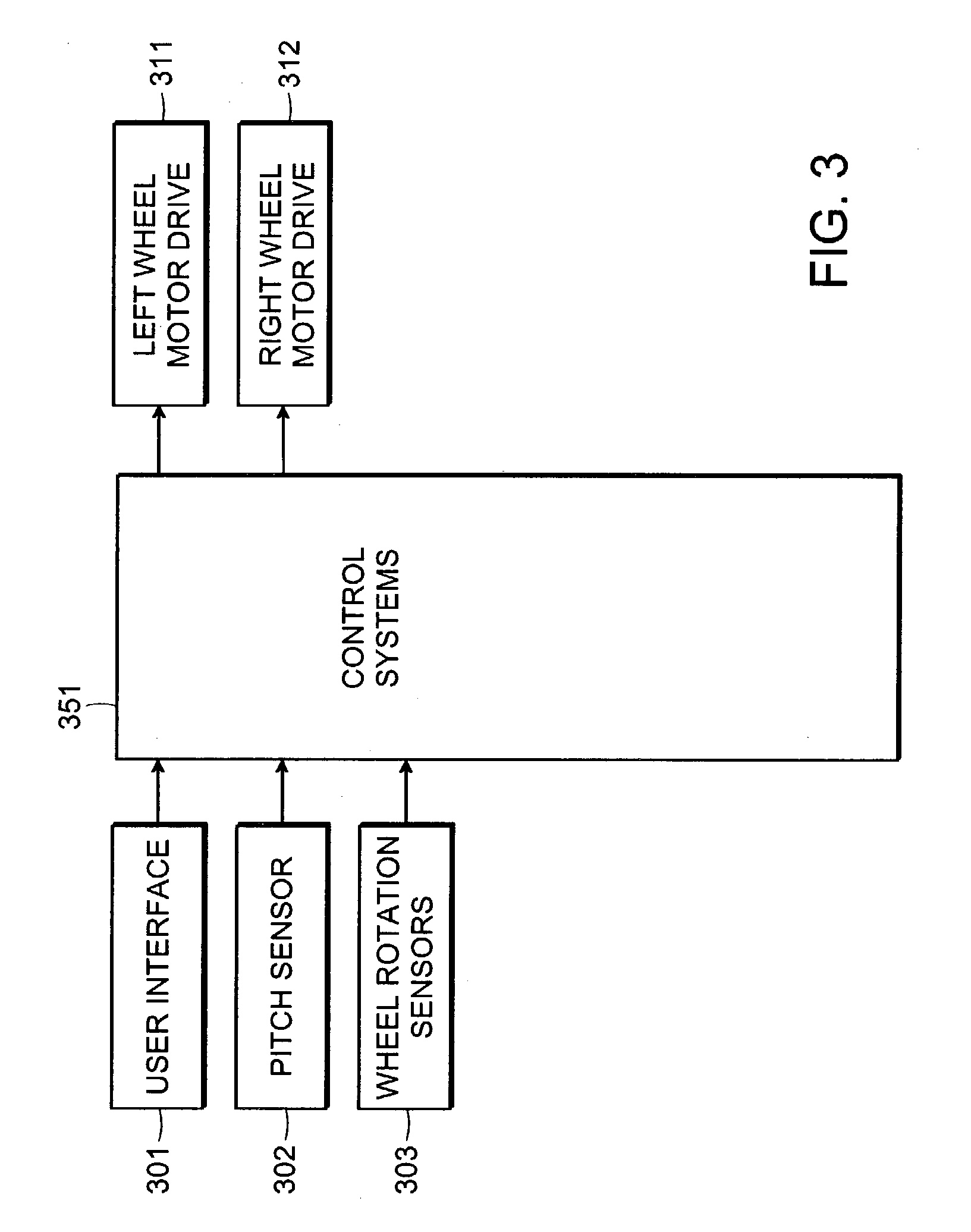
Hybrid human/electric powered vehicle
InactiveUS7017686B2Stable linear operationGuaranteed uptimeWheelchairs/patient conveyanceSpeed measurement using gyroscopic effectsActuatorElectric vehicle
A personal transporter that provides both for propulsion by a user, and, at the same time, for dynamic stabilization by means of a powered actuator. A pitch variable such as pitch or time rate of change of pitch is sensed and used to determine the torque provided to a wheel, whether in a co-rotating or counter-rotating direction, in order to maintain stability of the transporter with respect to tipping in the fore-aft plane.
Owner:DEKA PROD LLP
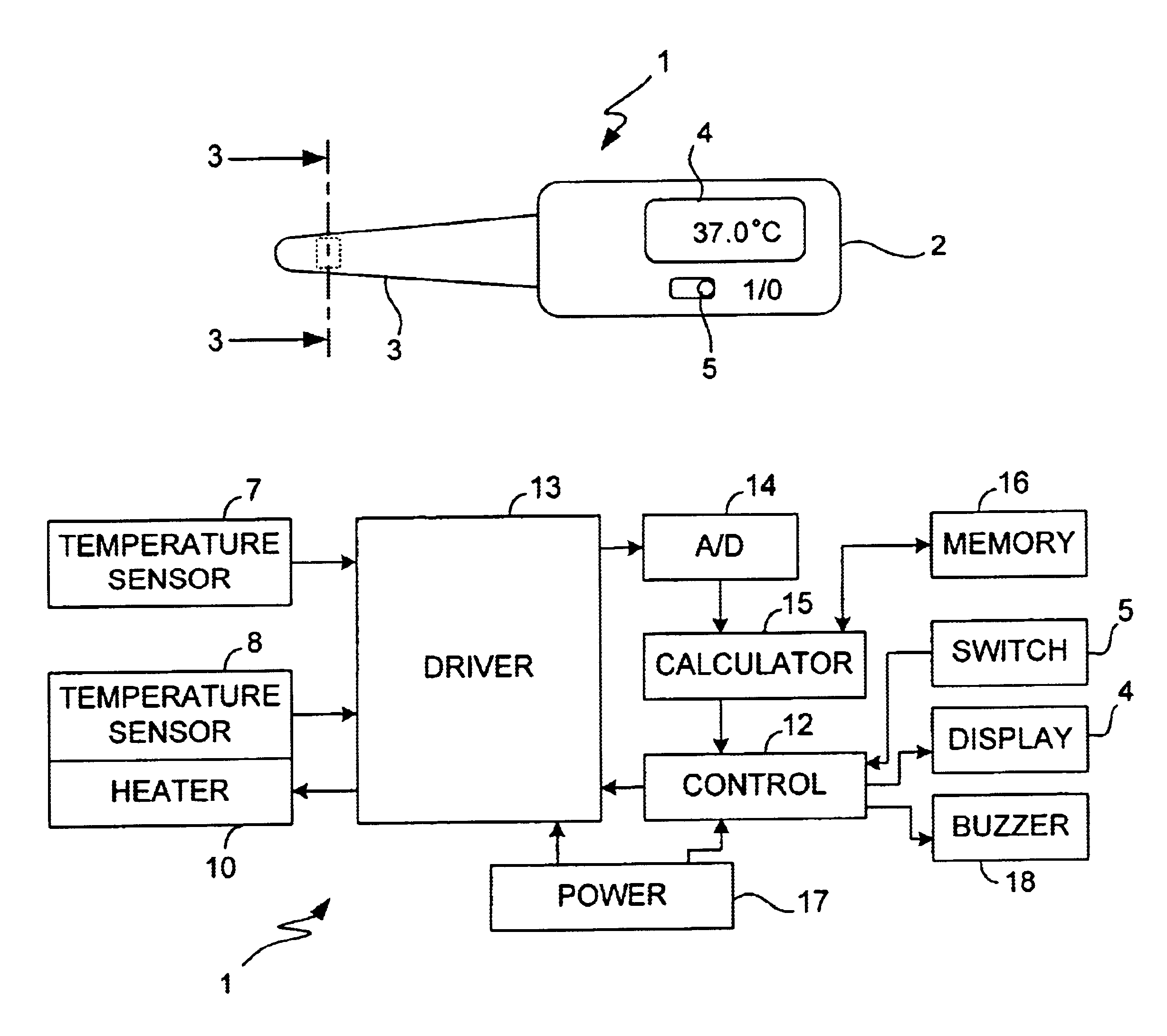
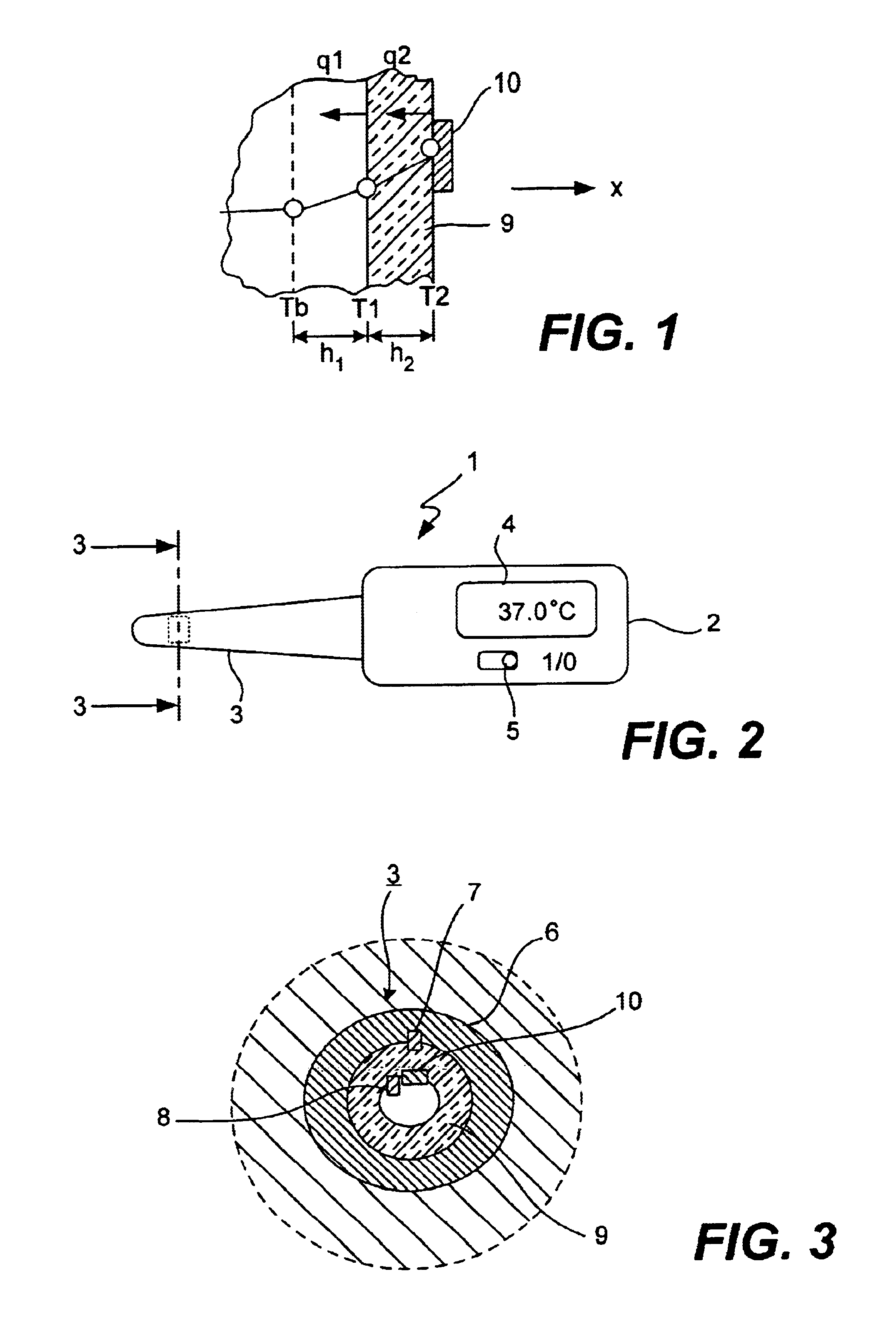
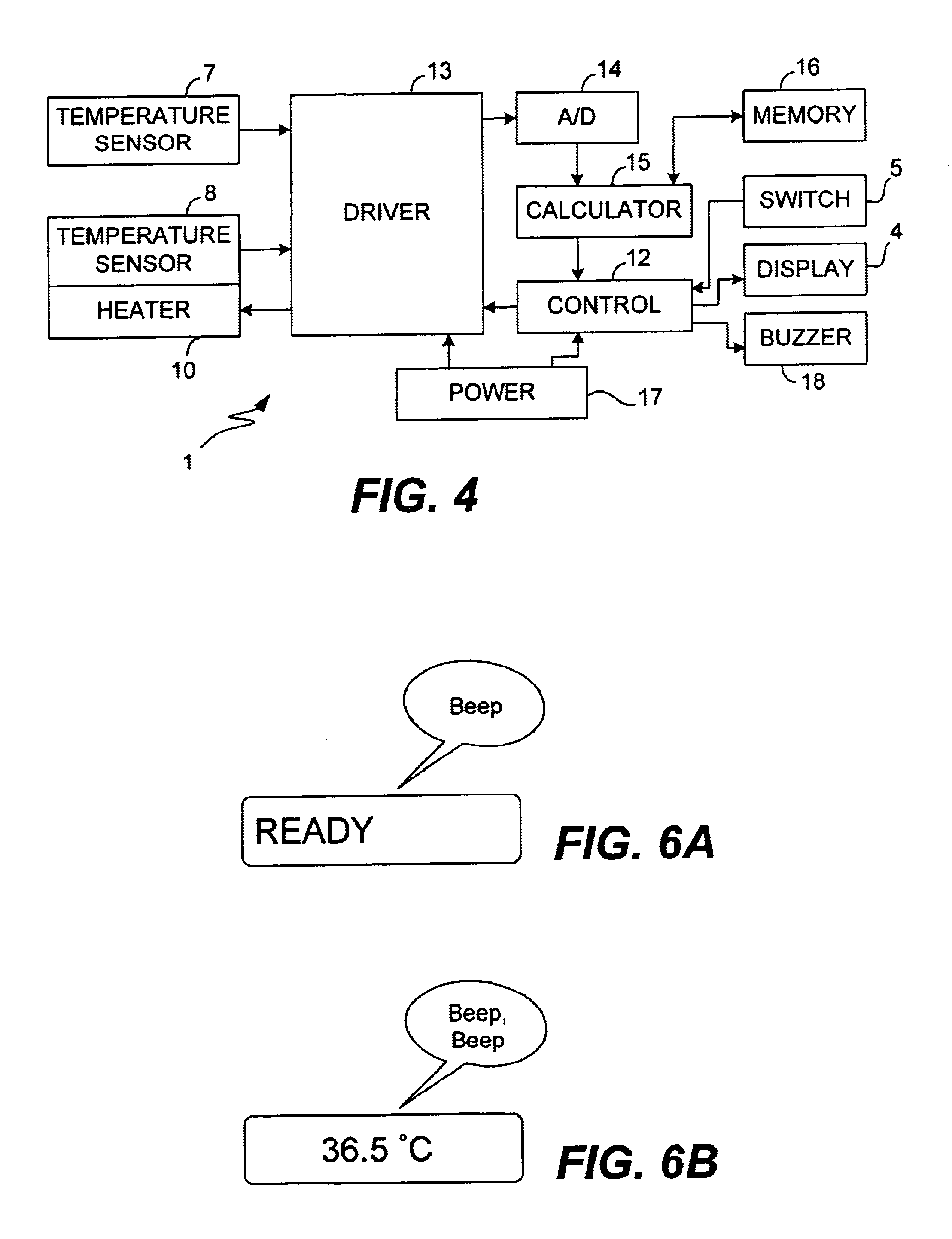
Electronic clinical thermometer
InactiveUS6886978B2Easy to carryAccurately and quickly estimateThermometer detailsThermometers using electric/magnetic elementsHeat flowEngineering
An electronic clinical thermometer has a probe including a variable-temperature heater and one or more temperature sensors and may also include a heat flux sensor. Physical variables such as temperature, time rate of change in temperature and / or heat flow rate are directly measured at positions on the surface of a patient while being heated by the heater through a thermally insulating member. Such measured values are used to solve a heat transfer equation rewritten as lower-order equations. Measurements may be controlled to be taken at a desired timing such as at specified intervals. The probe for contacting the patient's body may be planar or in an elongated bar-shape.
Owner:OMRON HEALTHCARE CO LTD
Synchronizing Multi-Channel Speakers Over a Network
A server is arranged to distribute at least one stream of audio data corresponding to an audio signal to two or more speakers across a network. Each speaker includes a respective clock for regenerating the audio signal from the audio data. For each speaker, the server determines a relative rate of the speaker clock to a real time rate; and for each stream of data provided to a speaker, the server determines from a respective relative rate, respective samples of the audio signal to be altered in accordance with said relative rate. The streams are altered accordingly and transmitted across the network.
Owner:DTS LICENSING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com