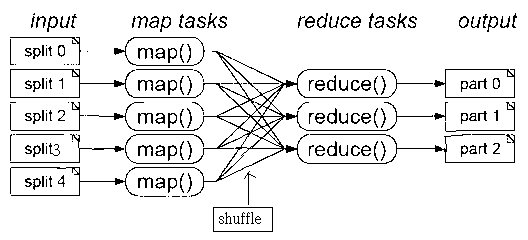
Patents
Literature
209 results about "Self-organizing map" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
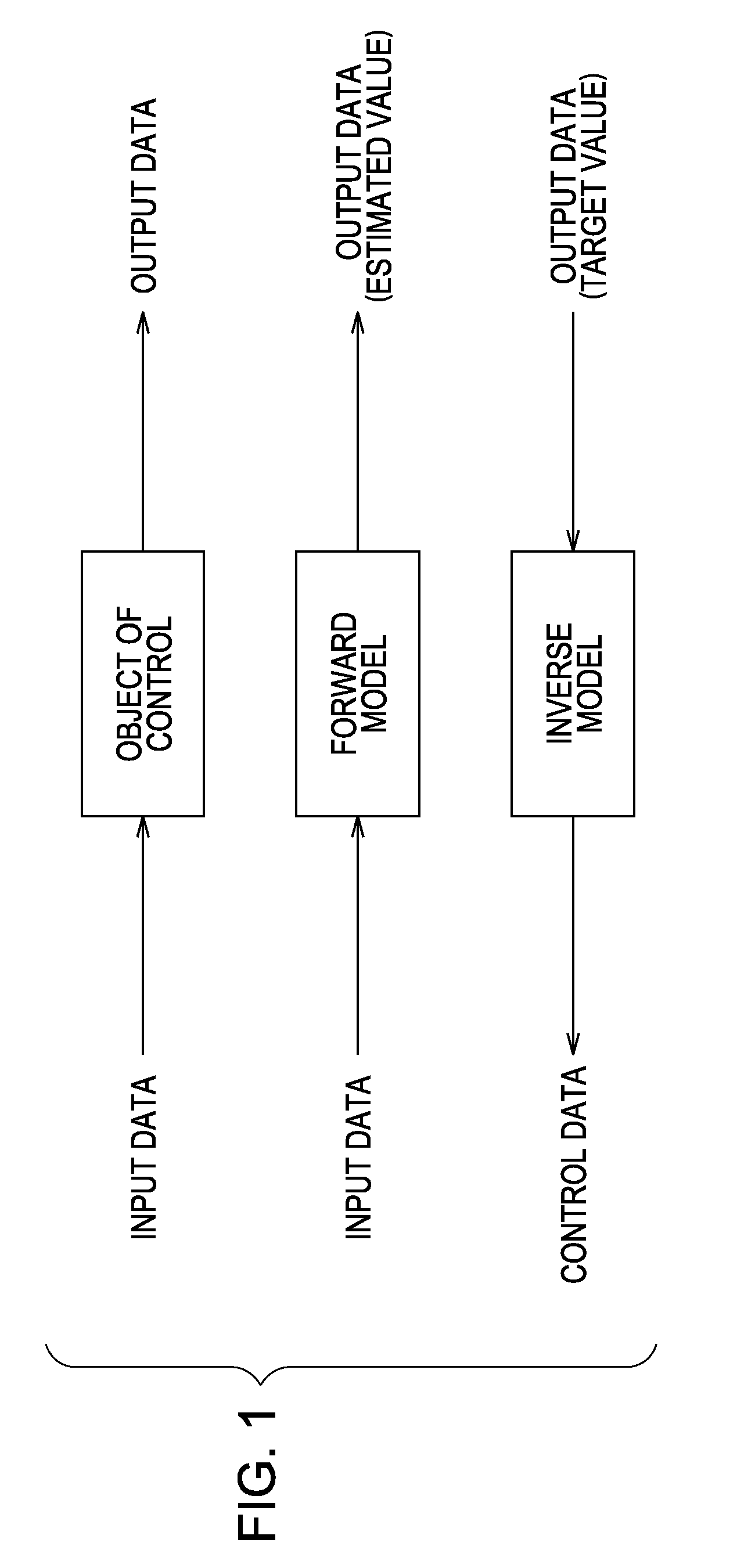
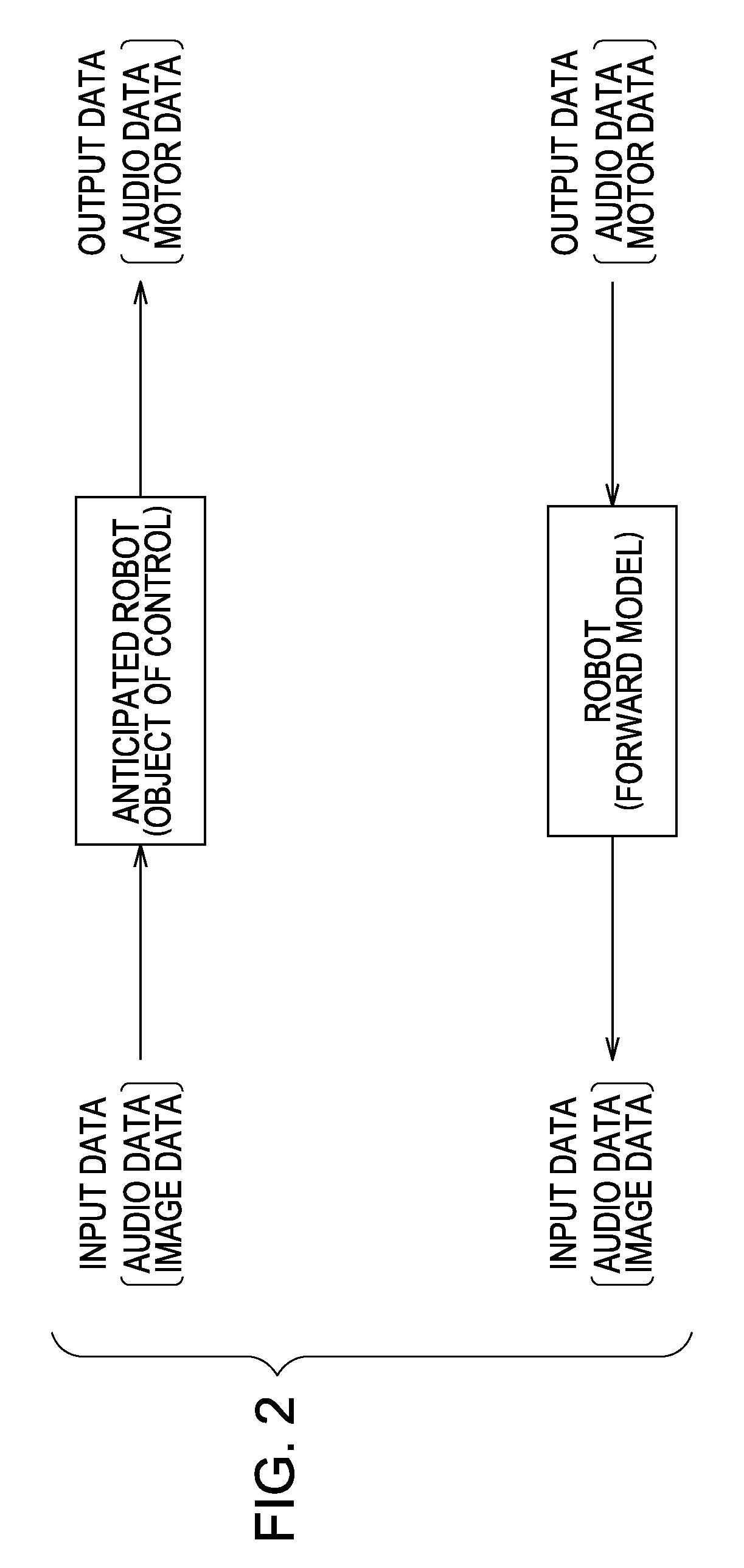
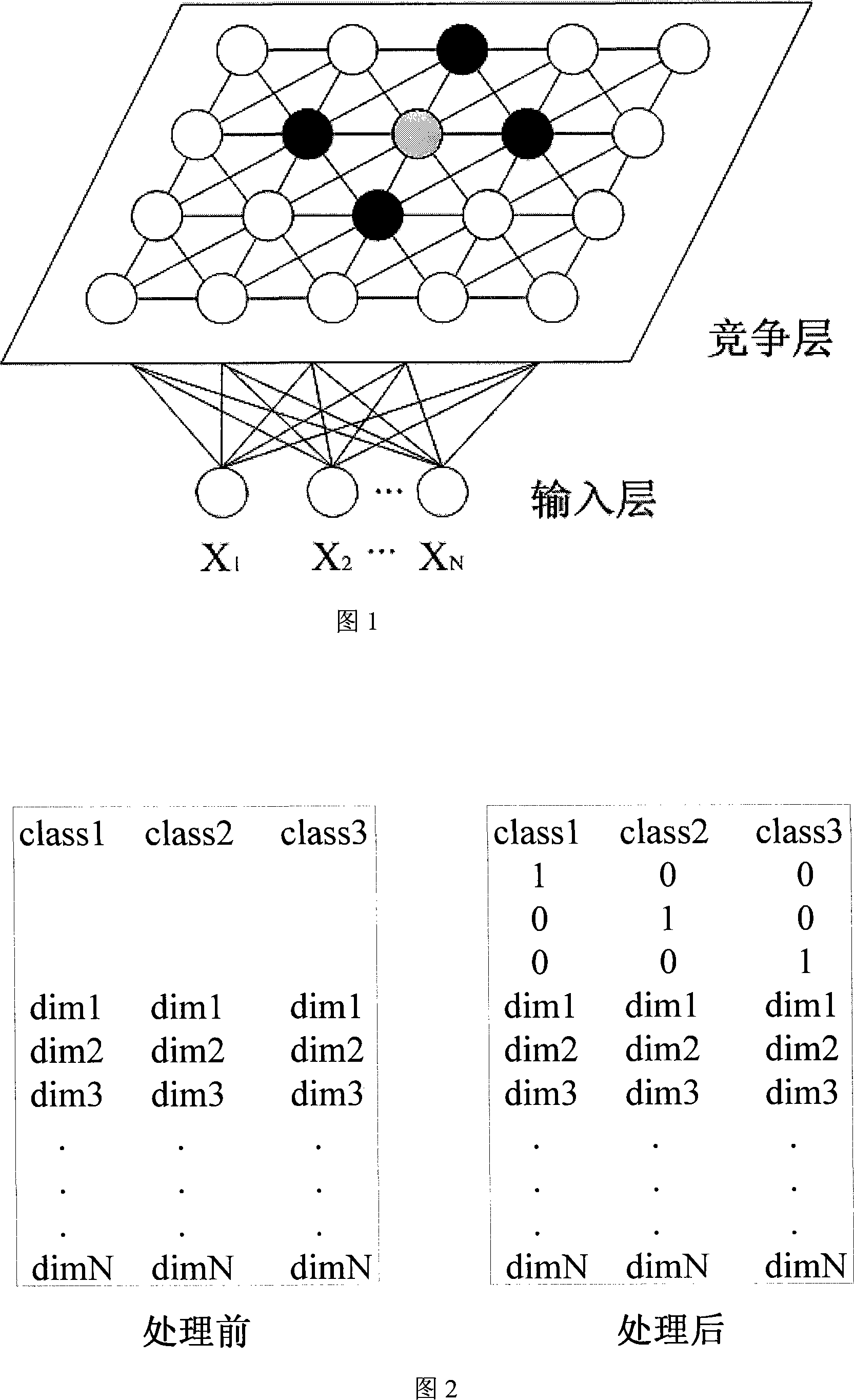
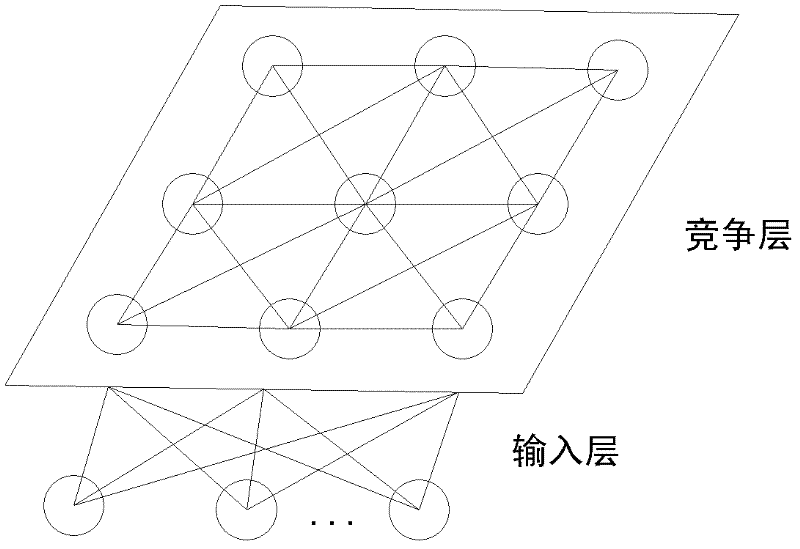
A self-organizing map (SOM) or self-organizing feature map (SOFM) is a type of artificial neural network (ANN) that is trained using unsupervised learning to produce a low-dimensional (typically two-dimensional), discretized representation of the input space of the training samples, called a map, and is therefore a method to do dimensionality reduction. Self-organizing maps differ from other artificial neural networks as they apply competitive learning as opposed to error-correction learning (such as backpropagation with gradient descent), and in the sense that they use a neighborhood function to preserve the topological properties of the input space.
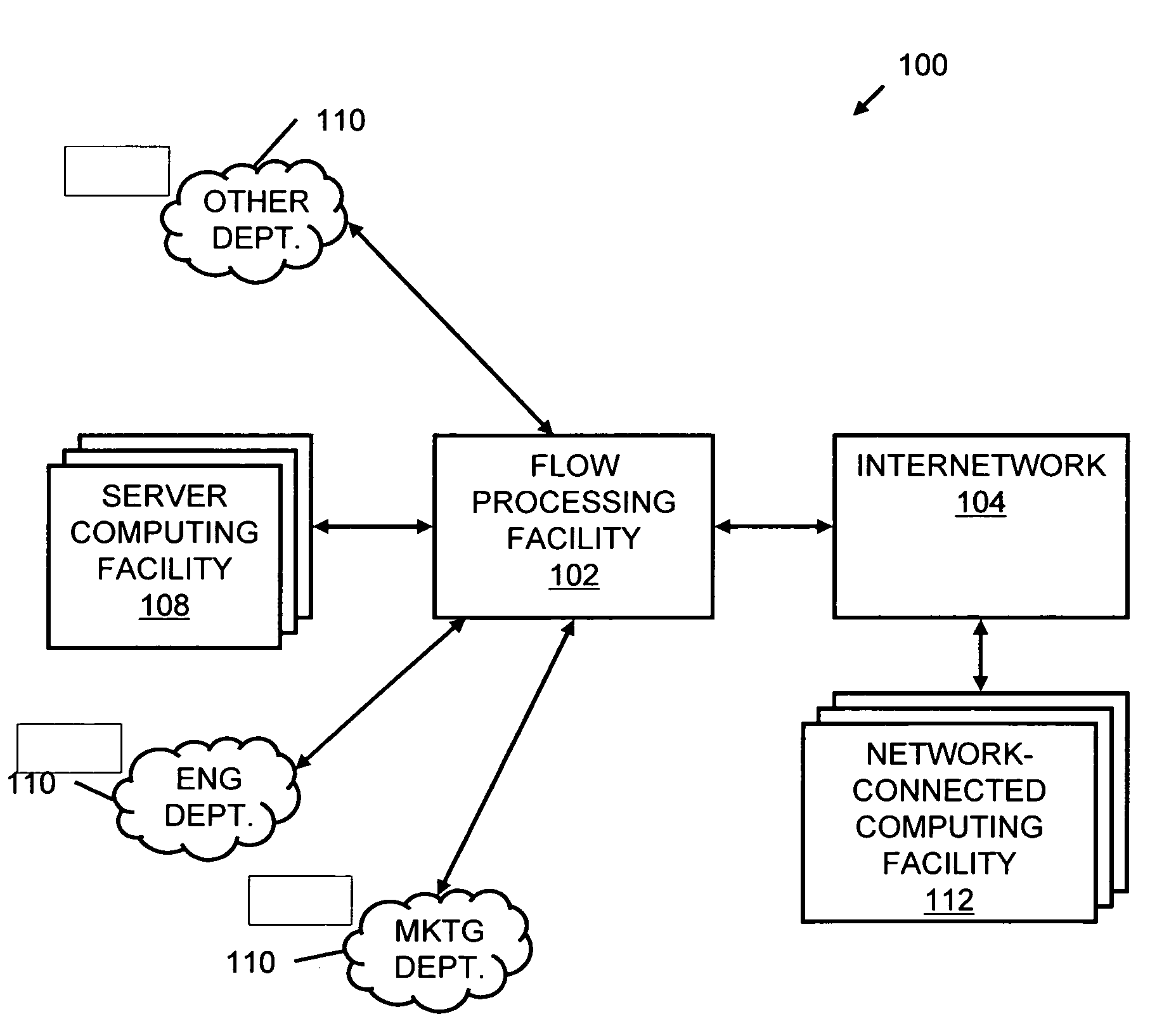
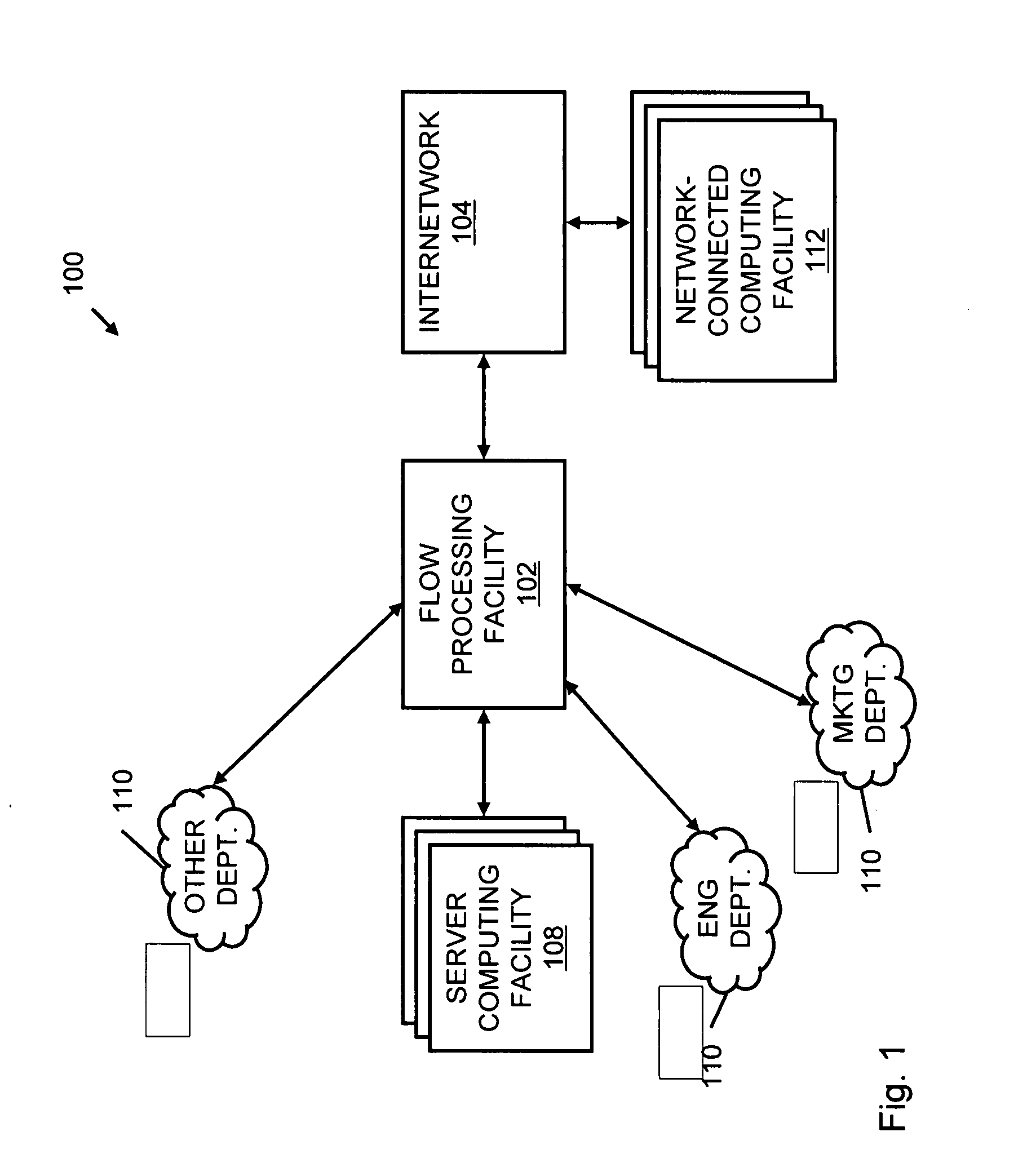
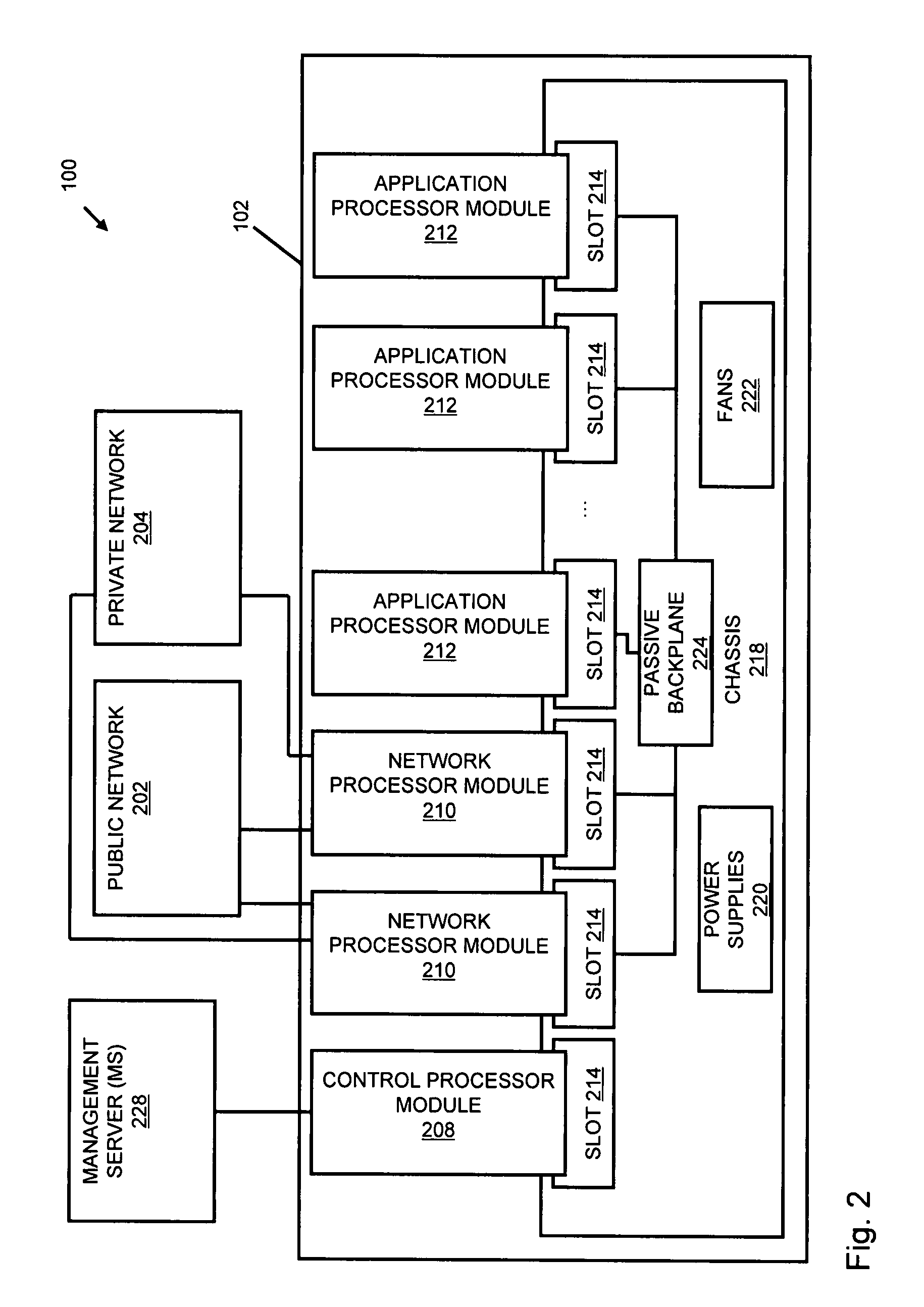
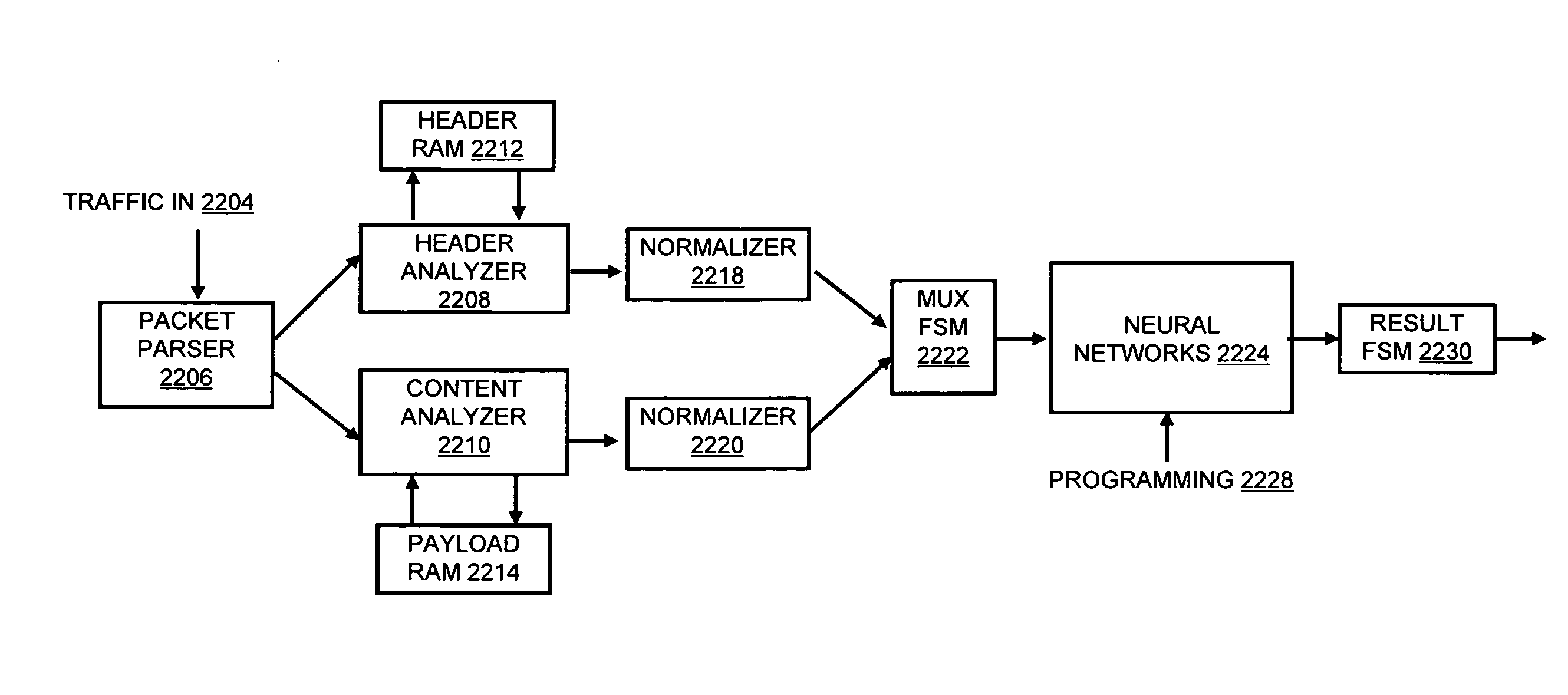
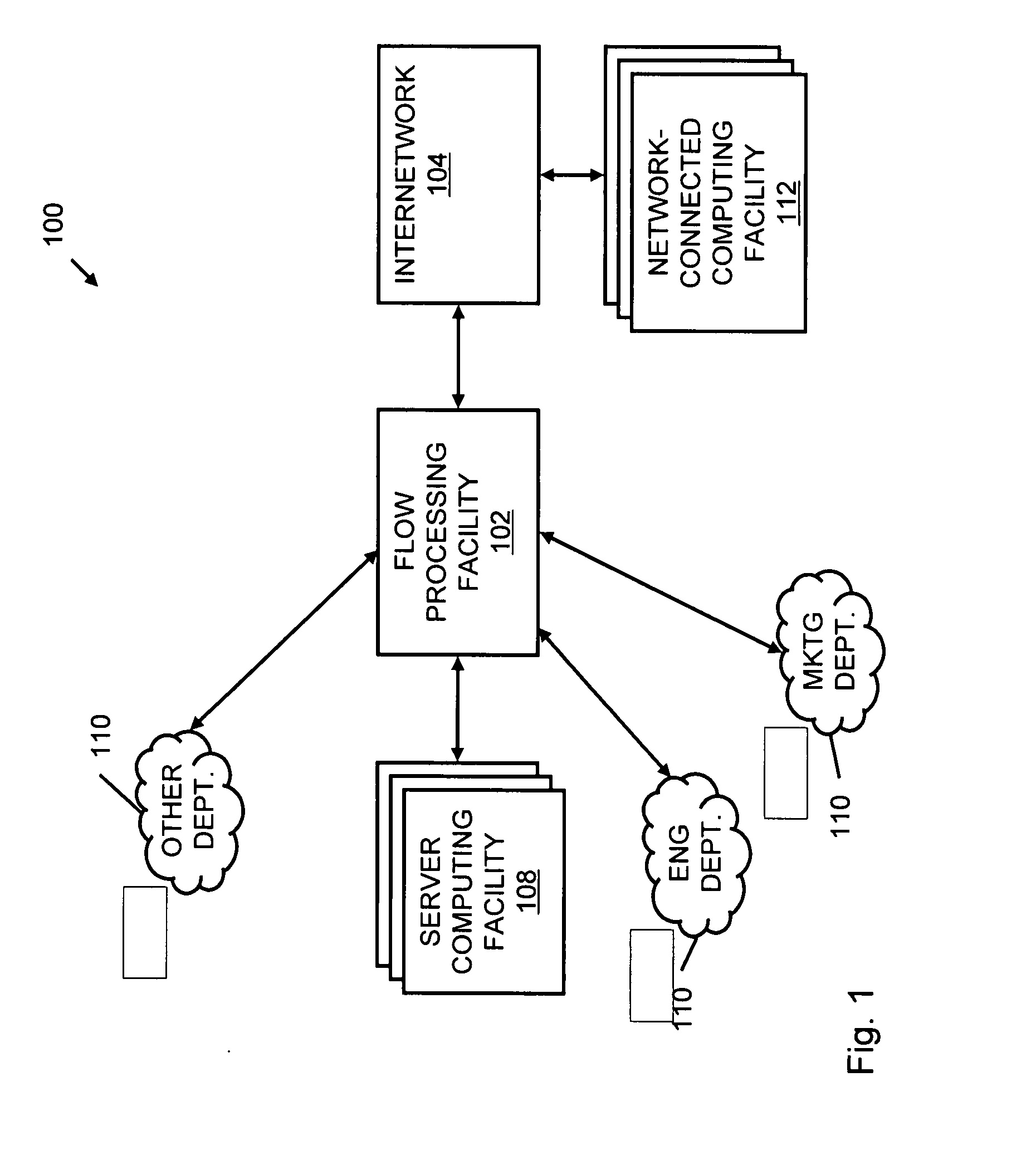
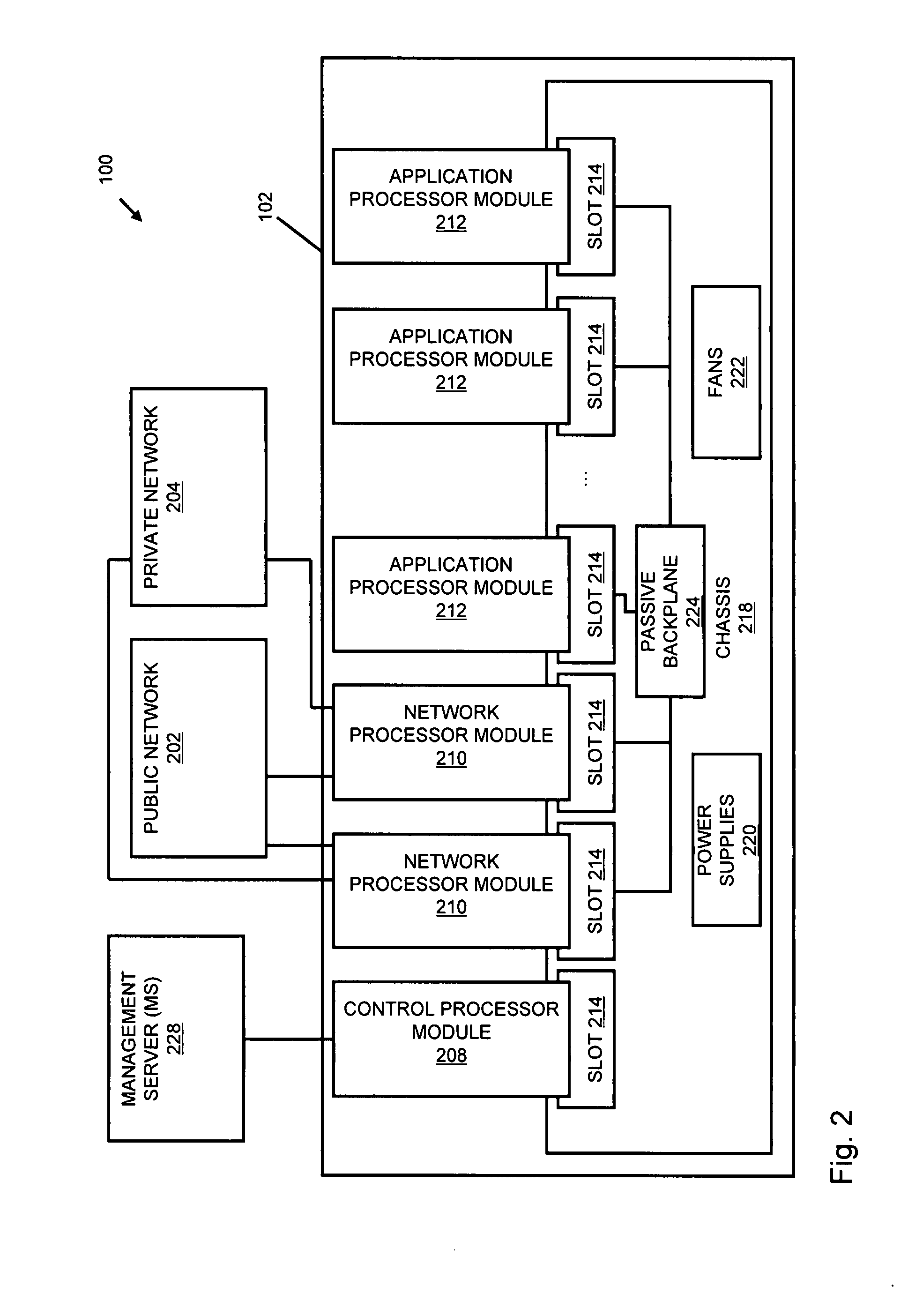
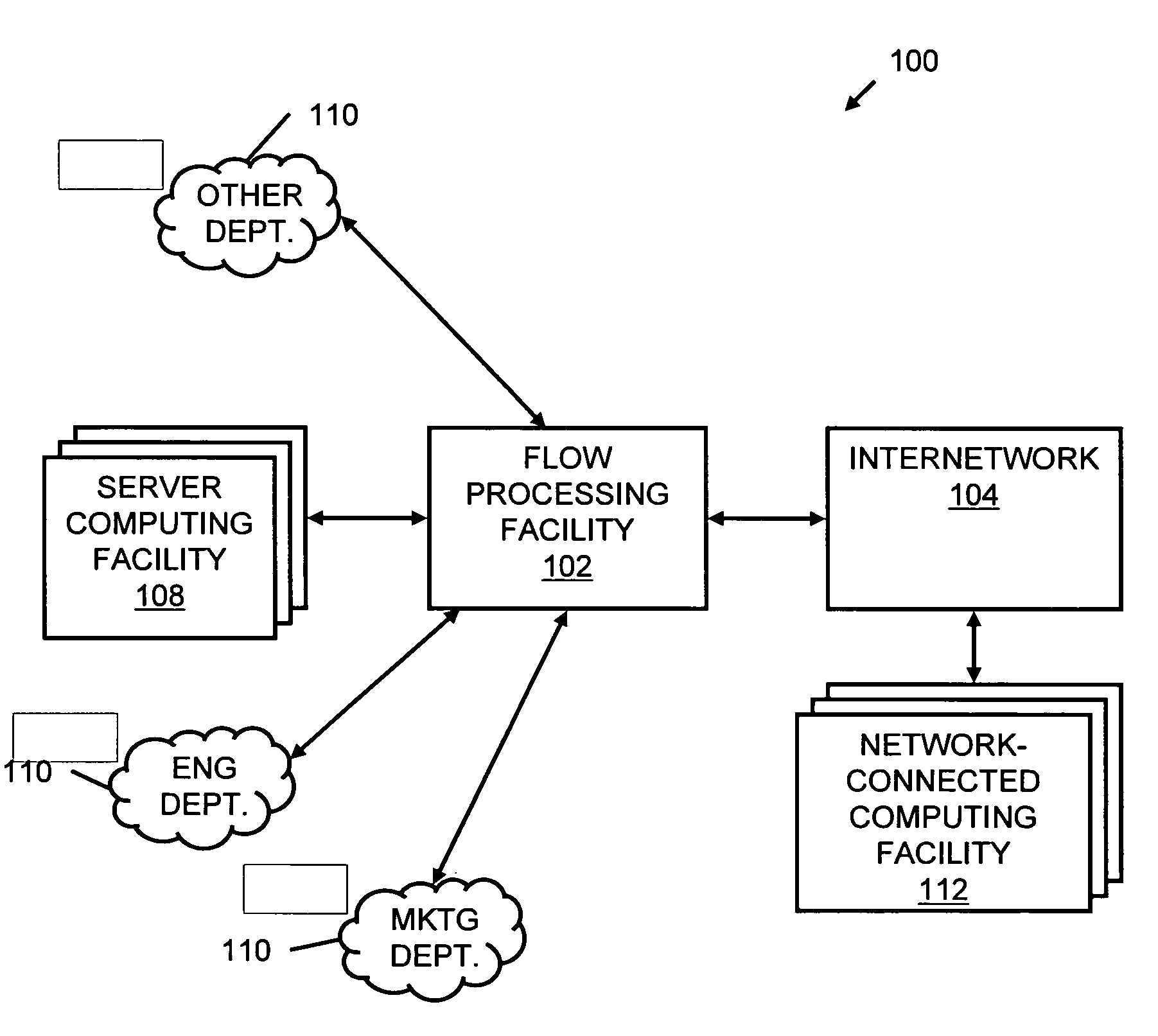
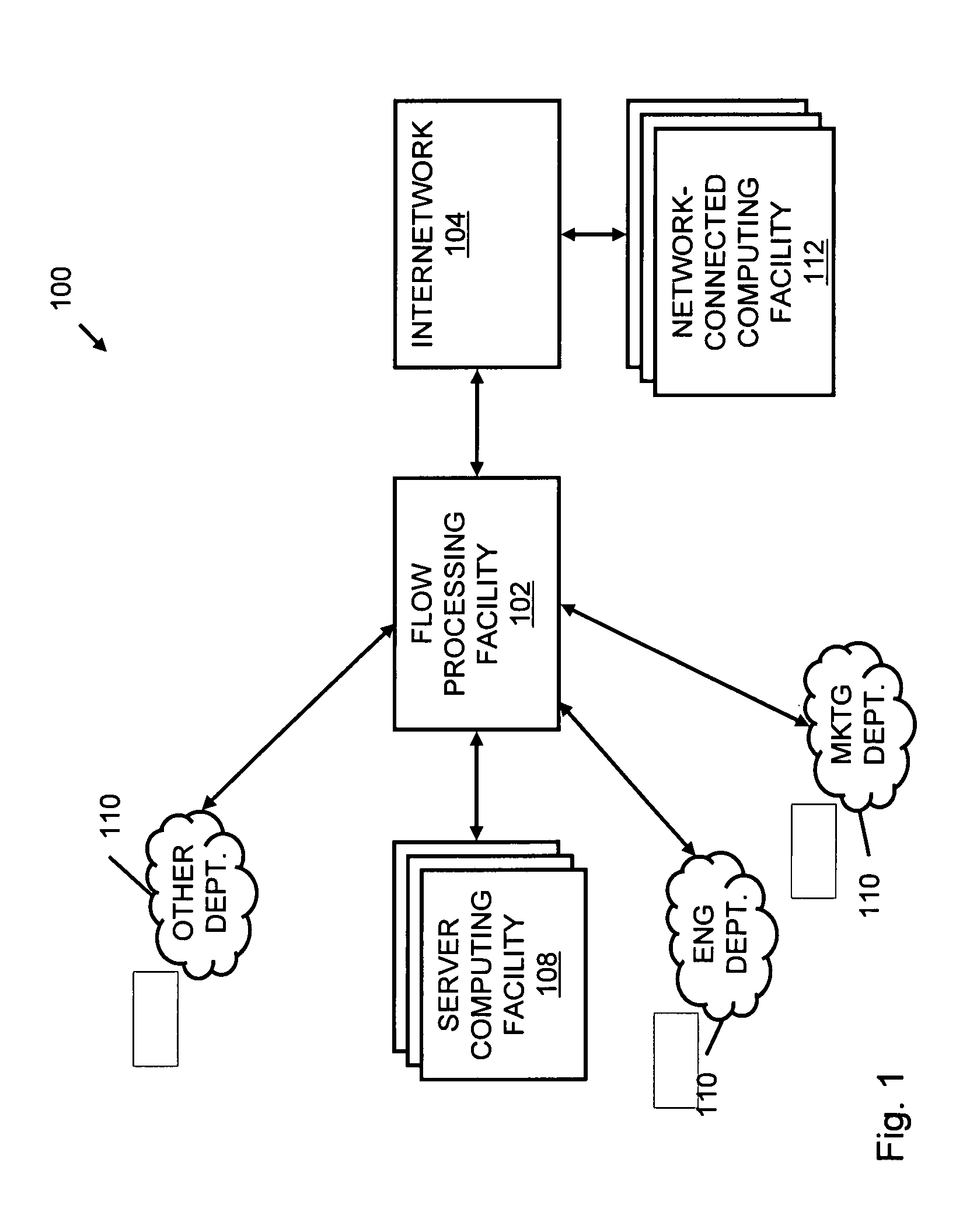
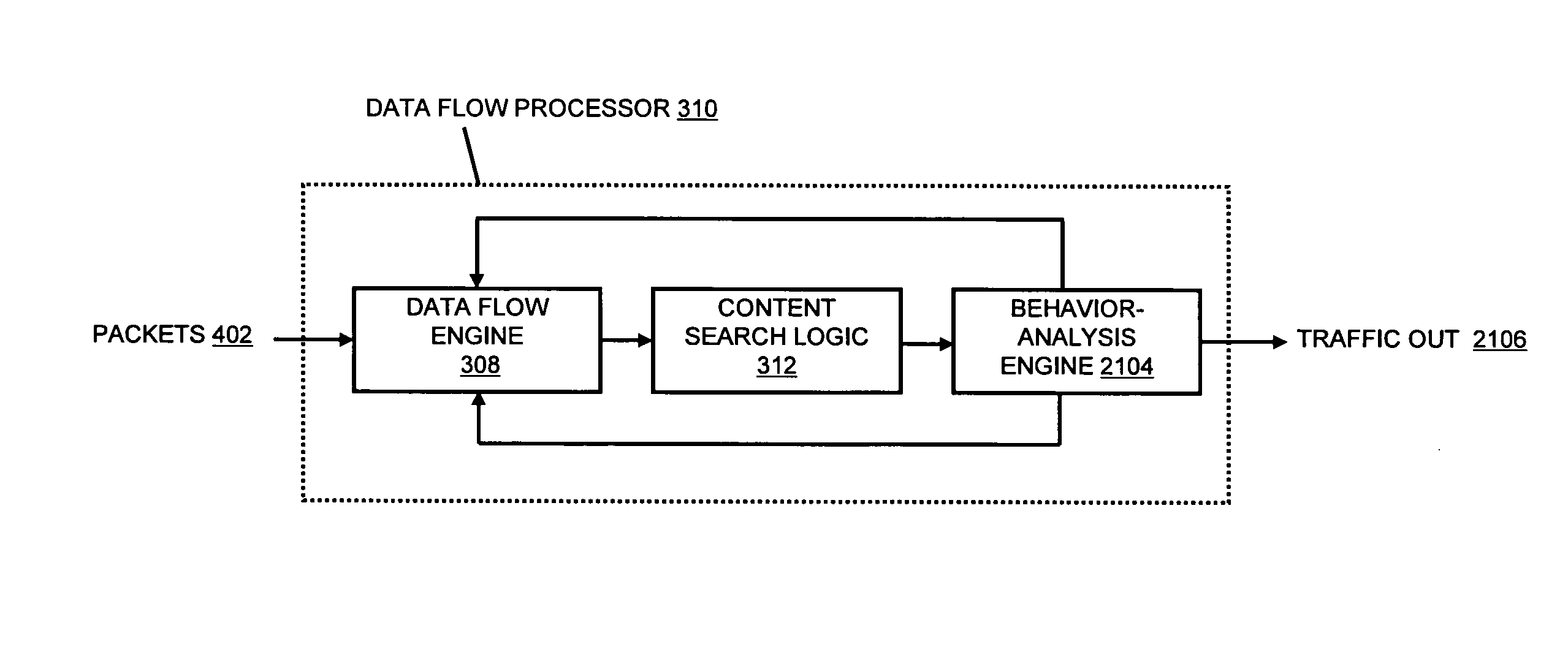
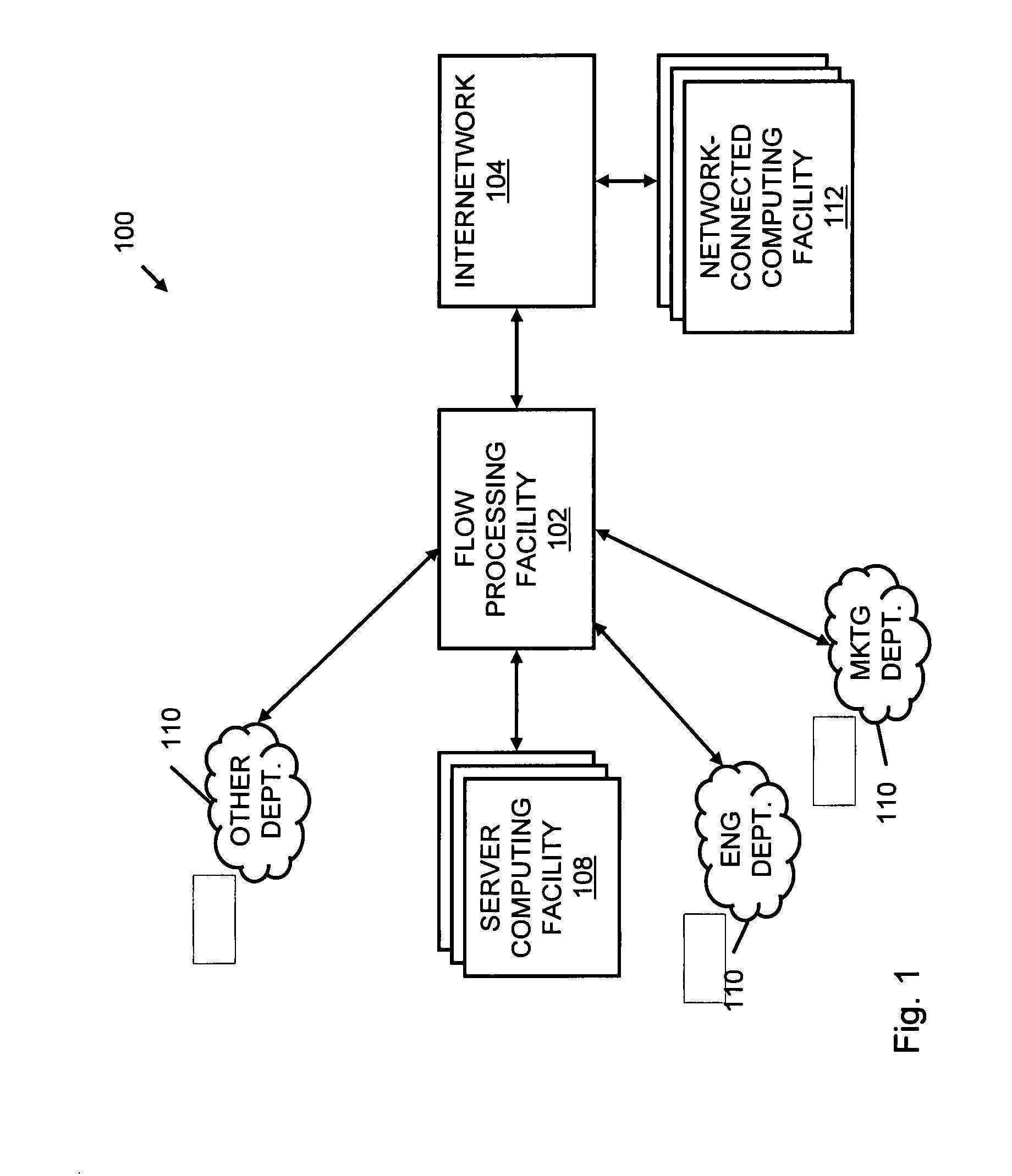
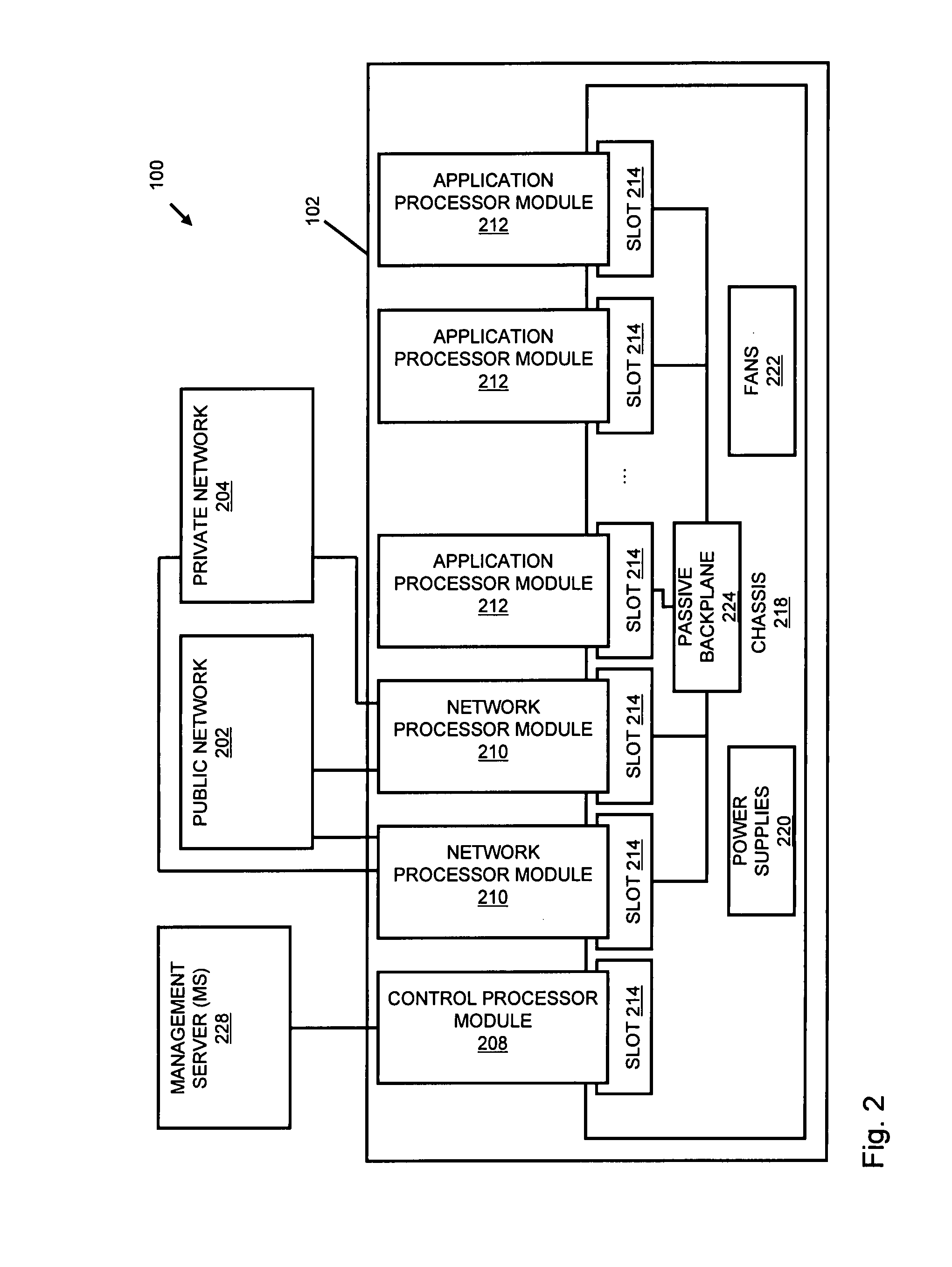
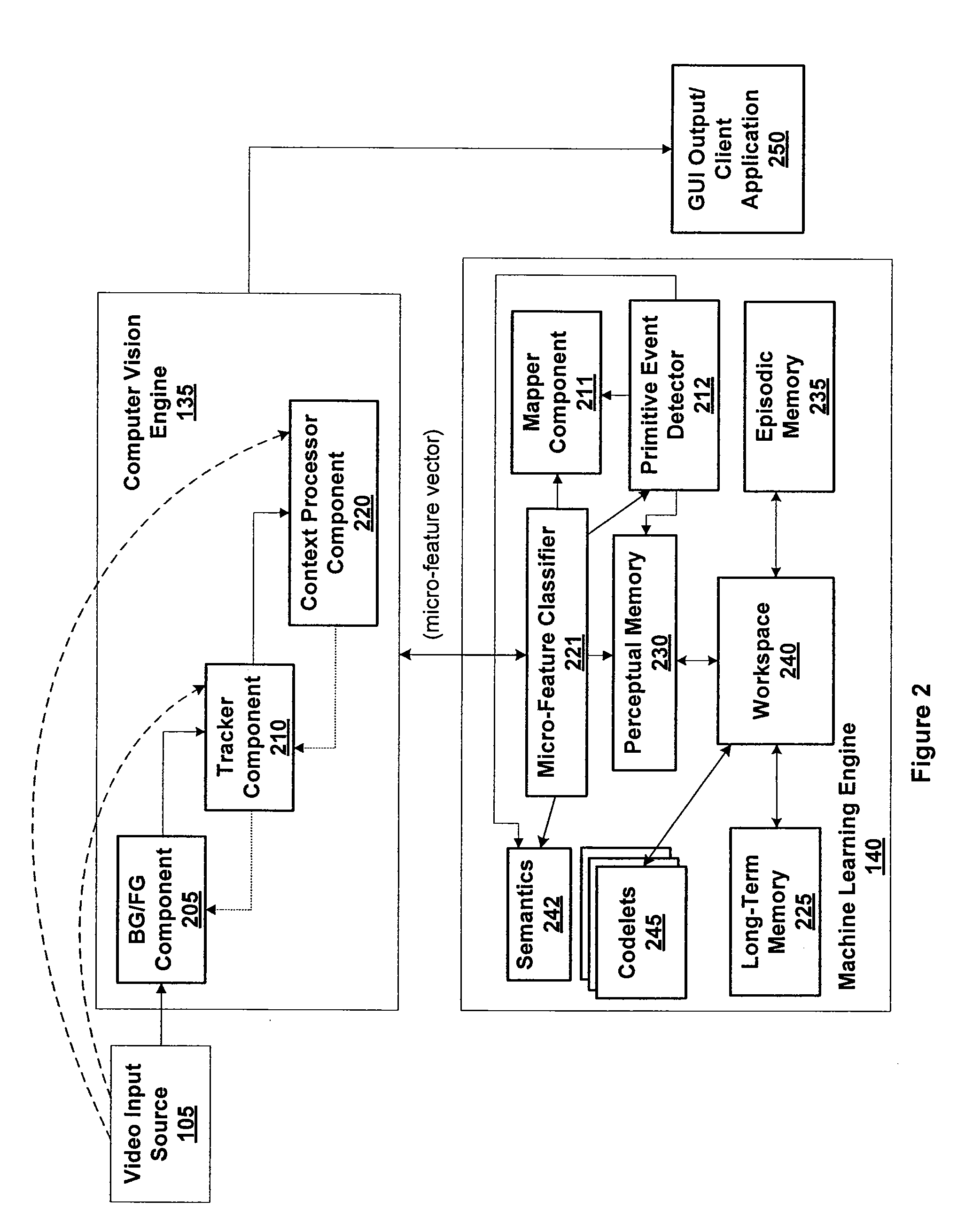
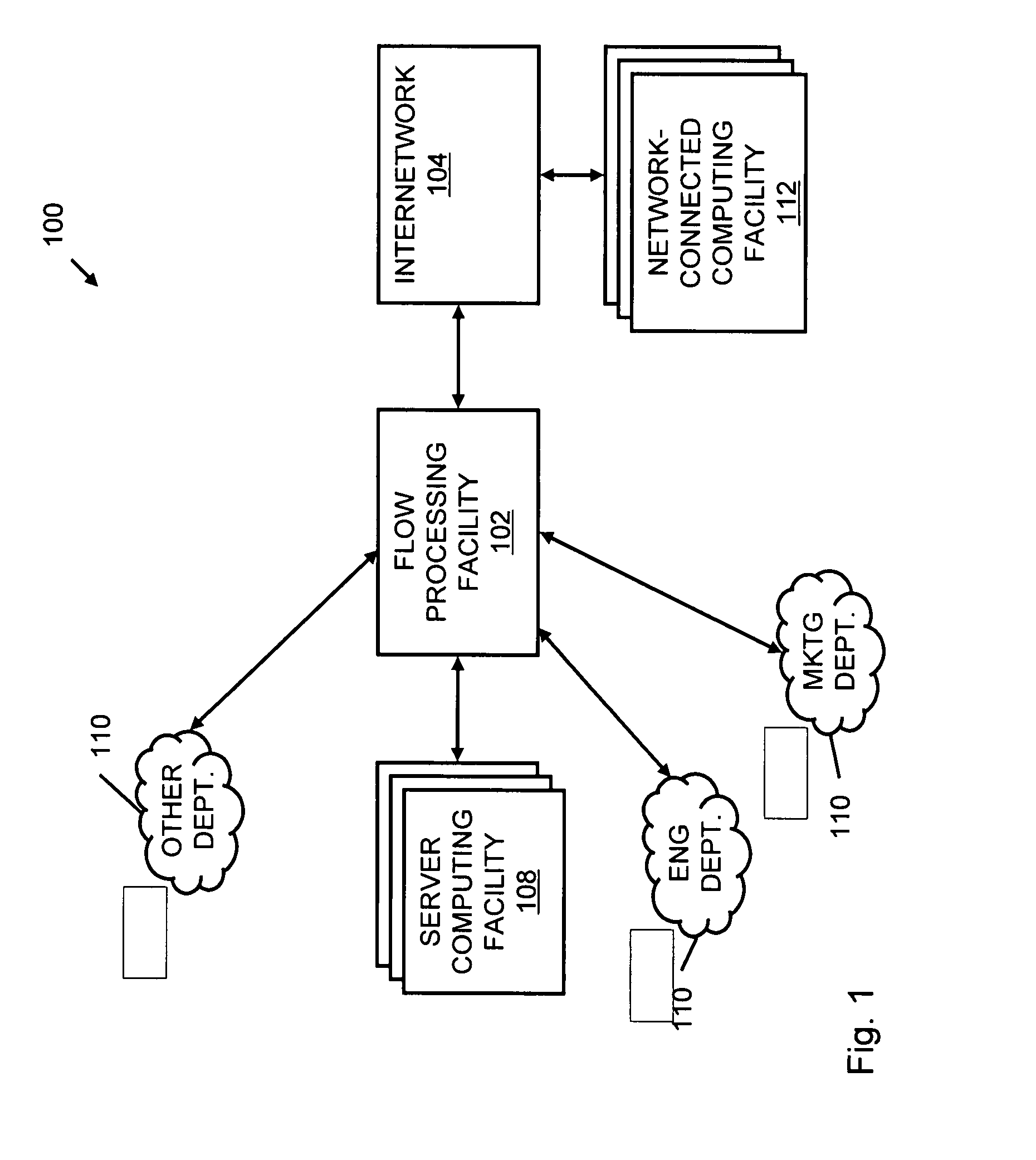
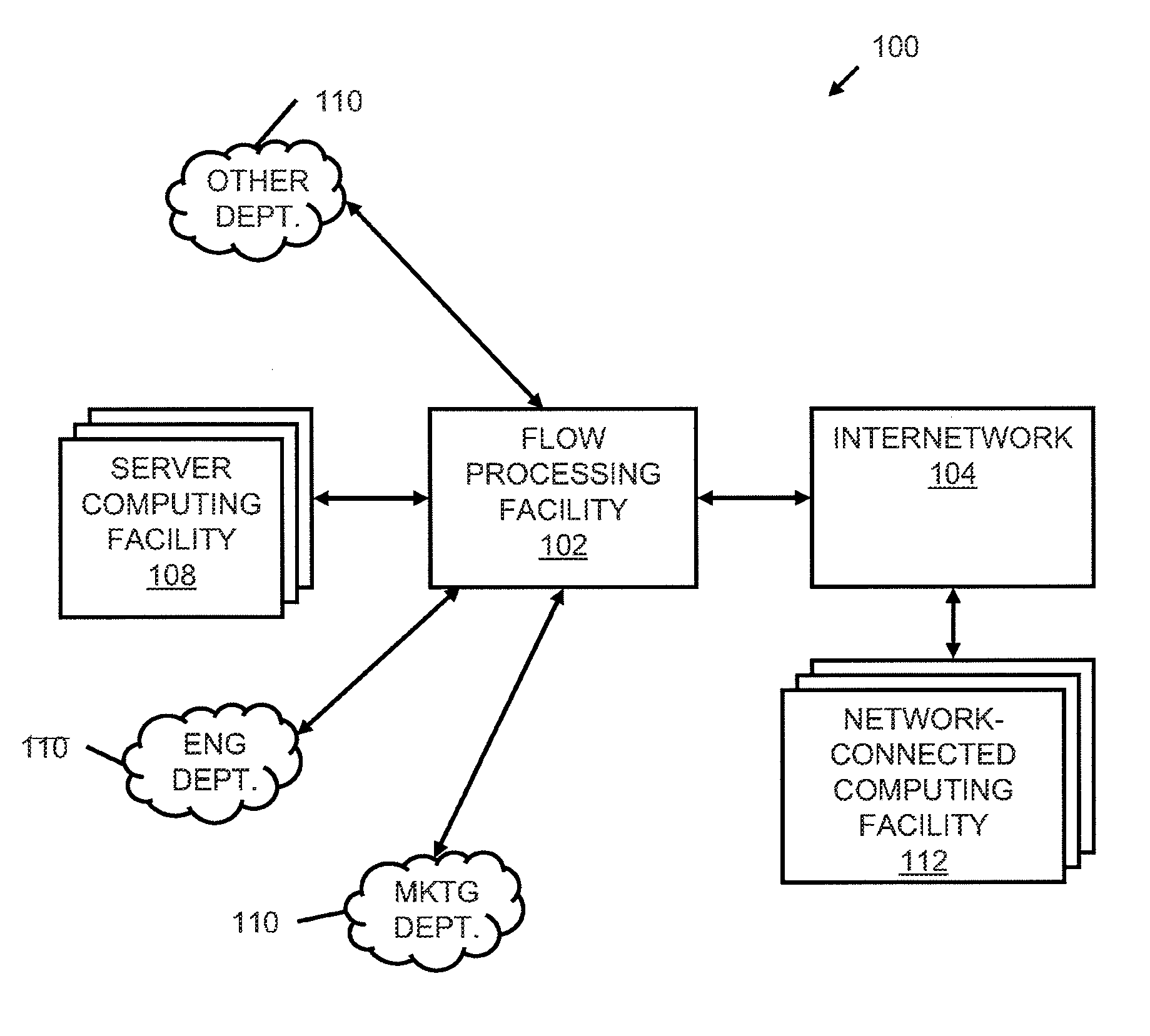
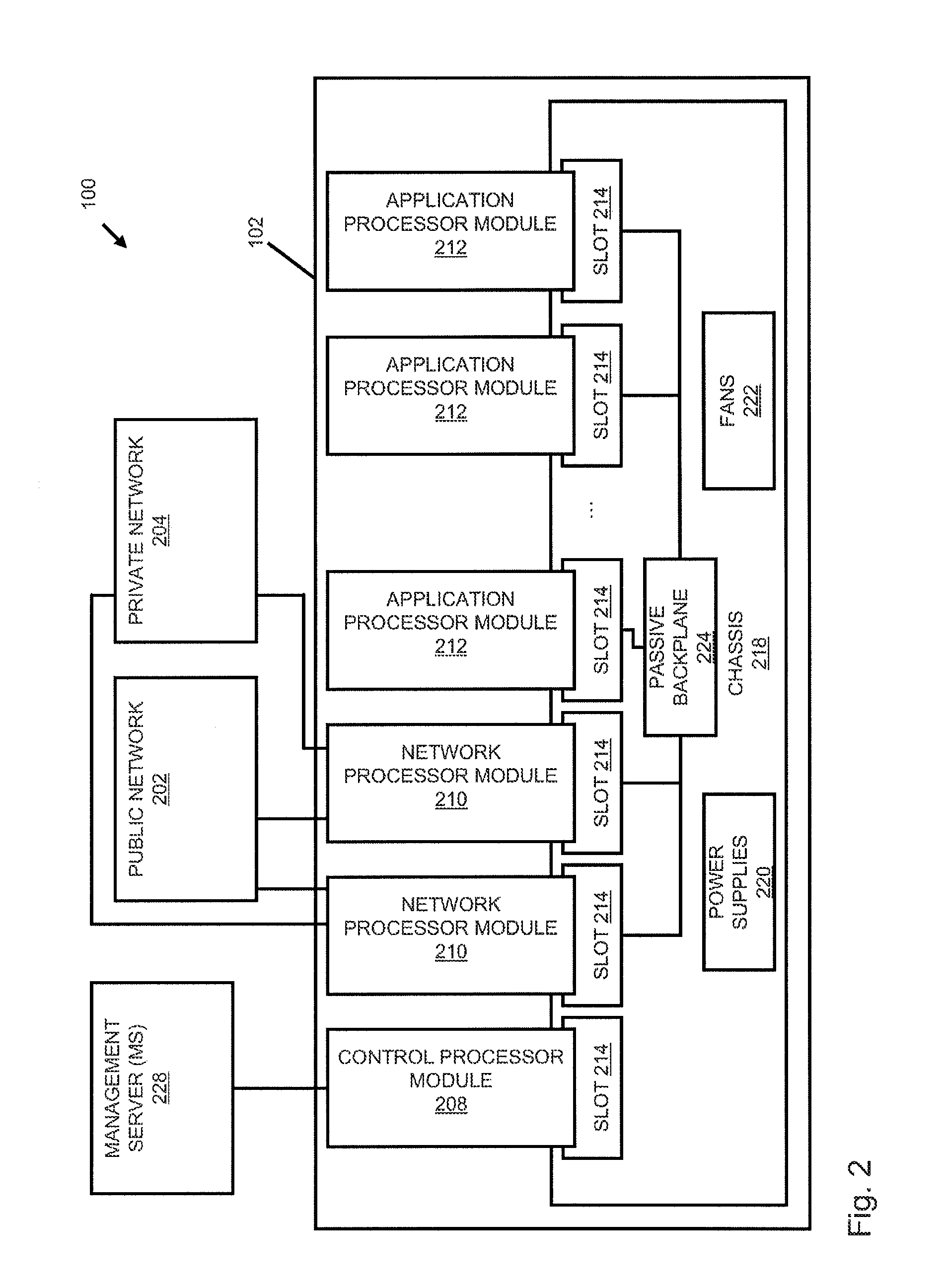
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
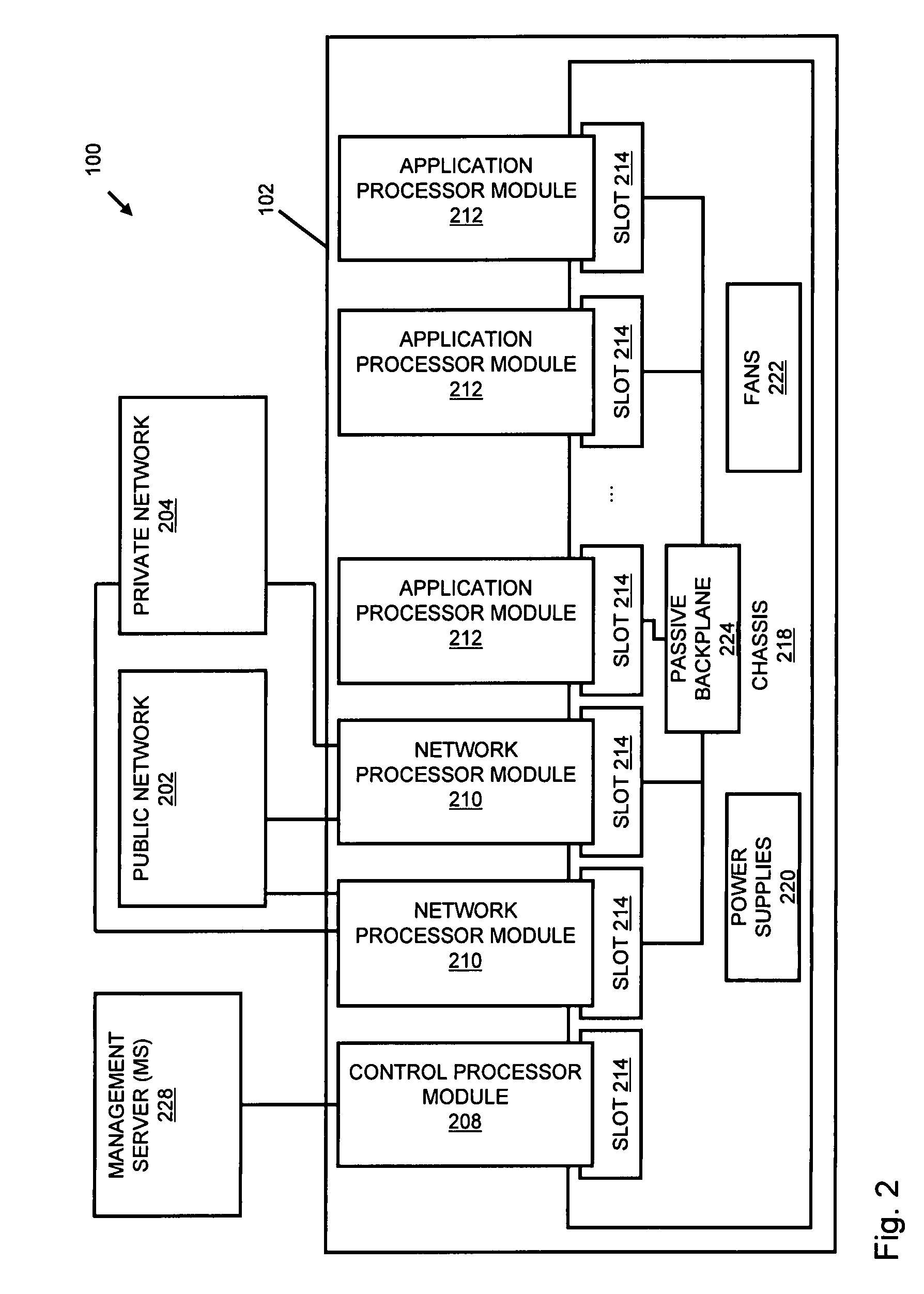
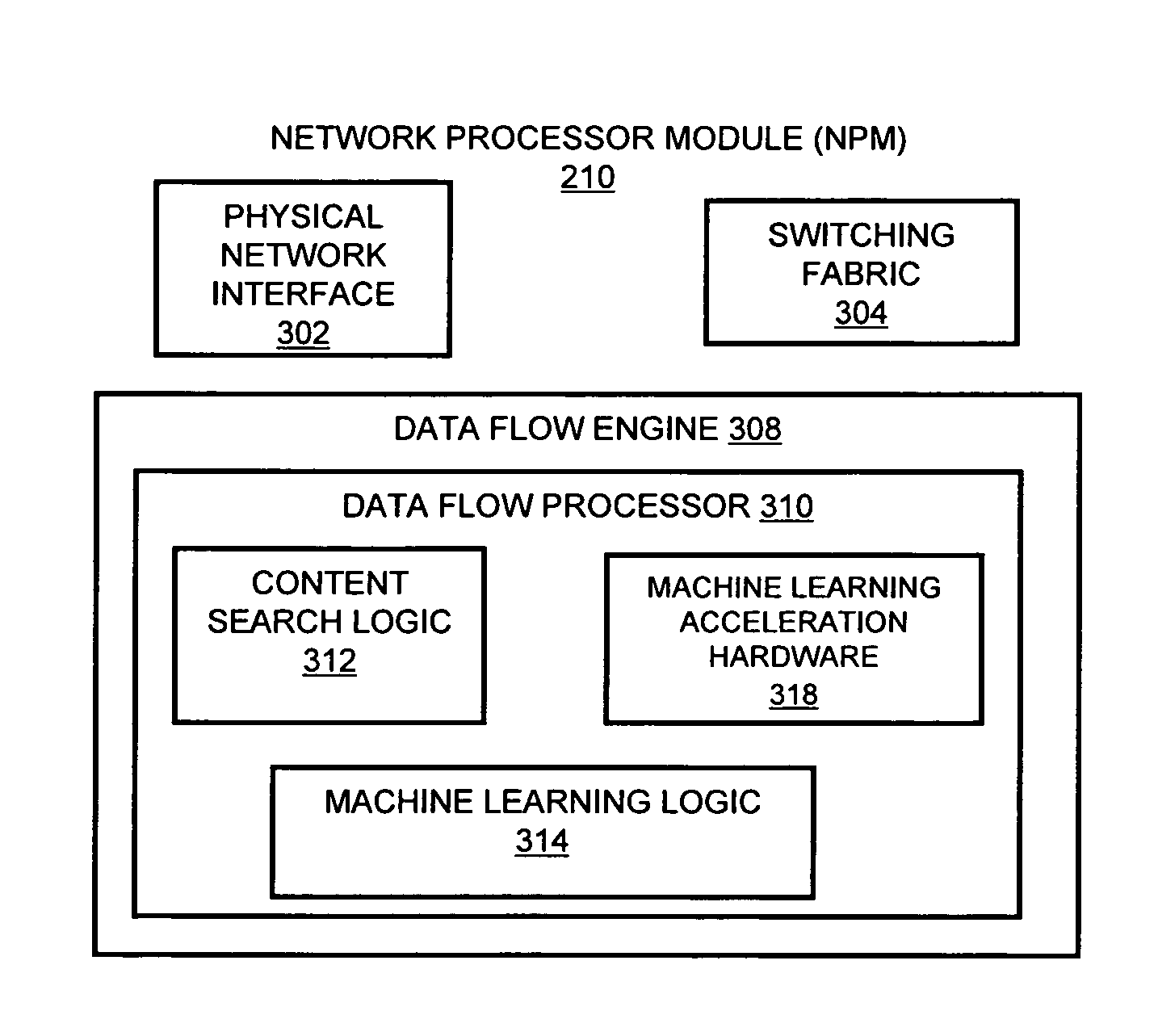
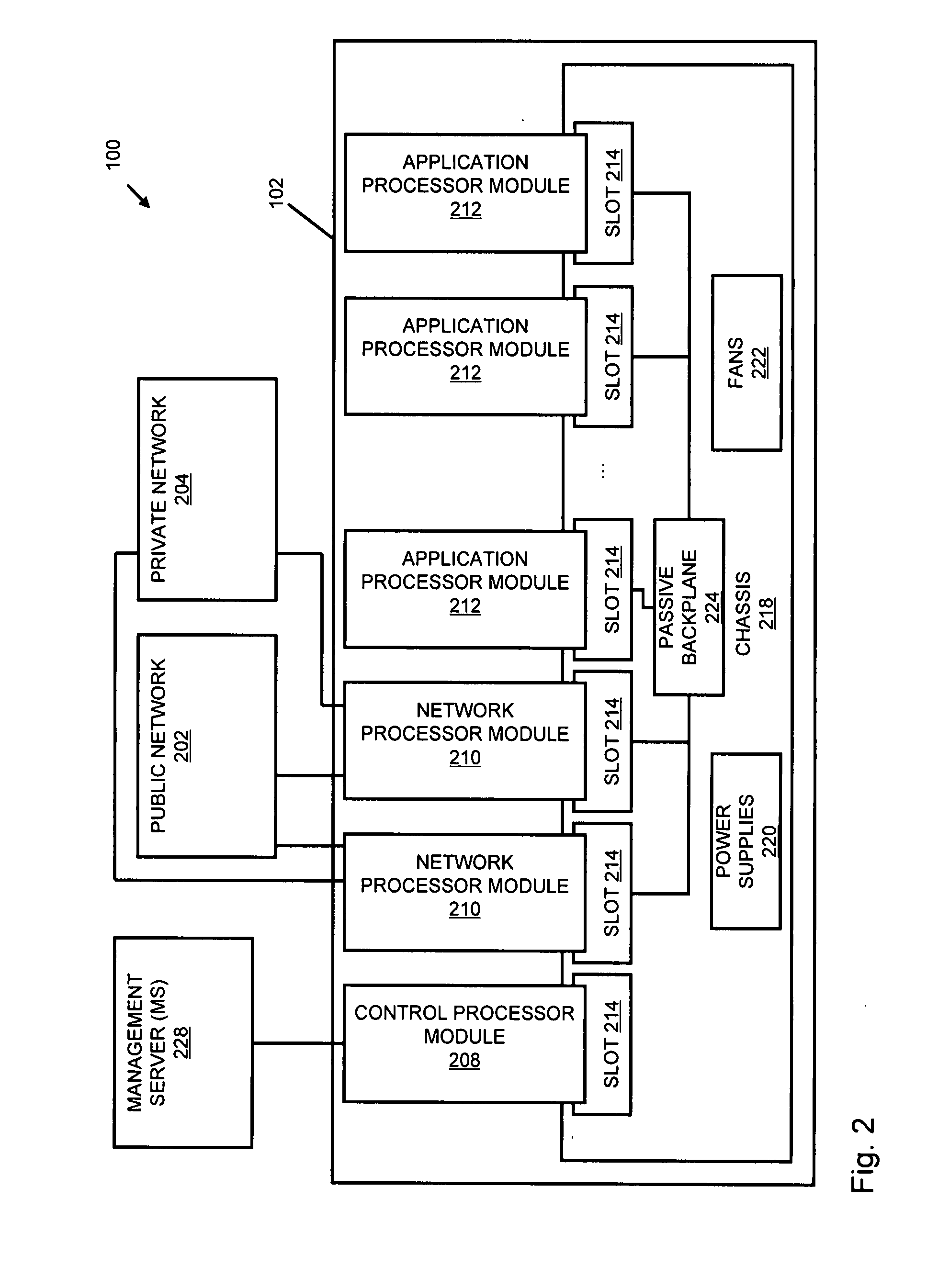
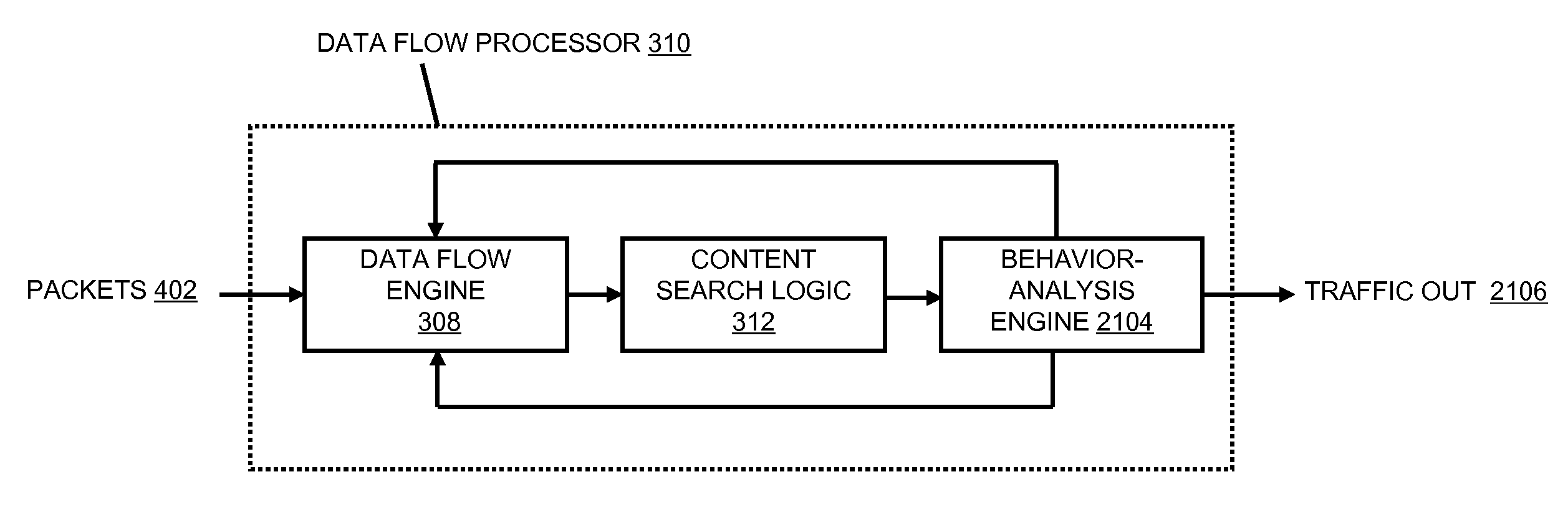
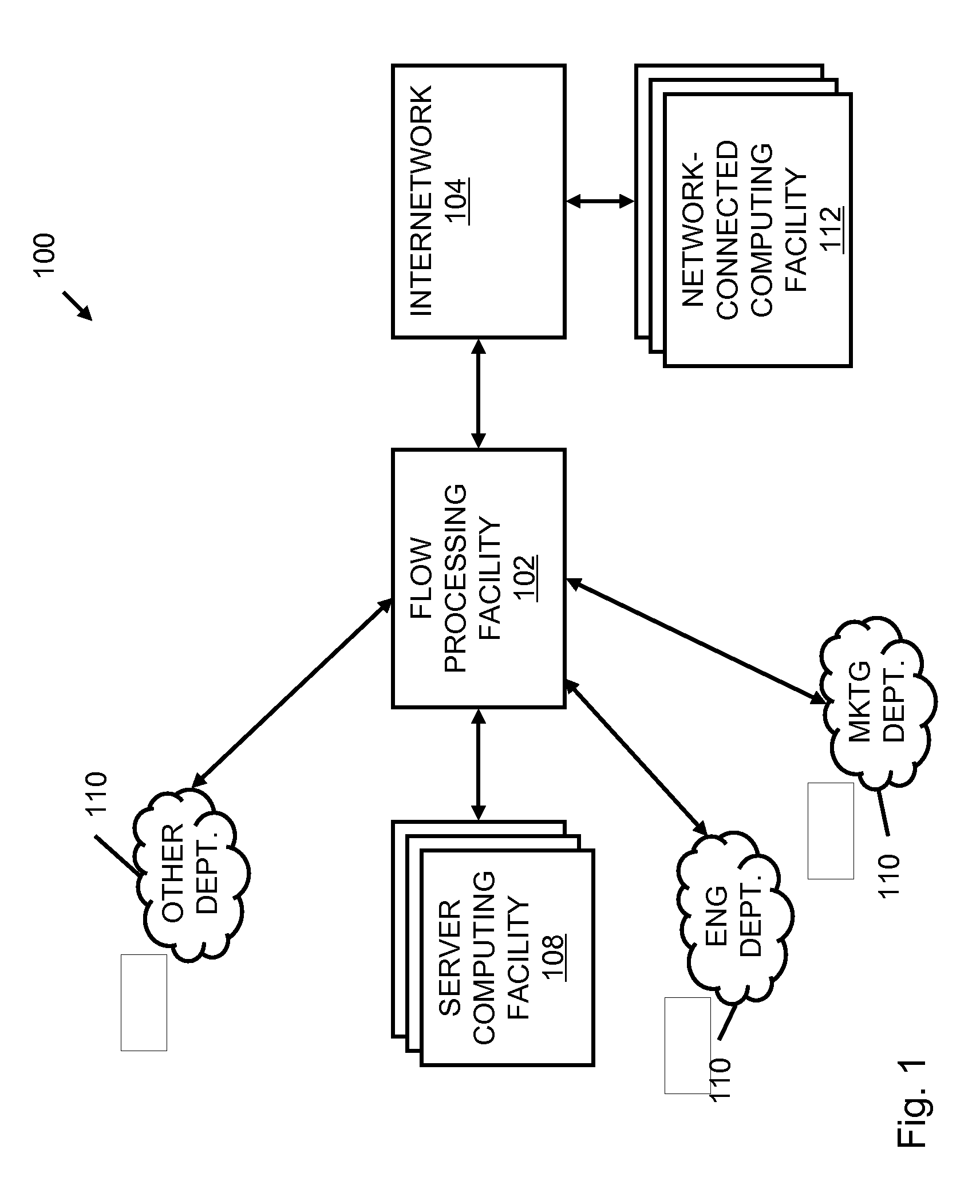
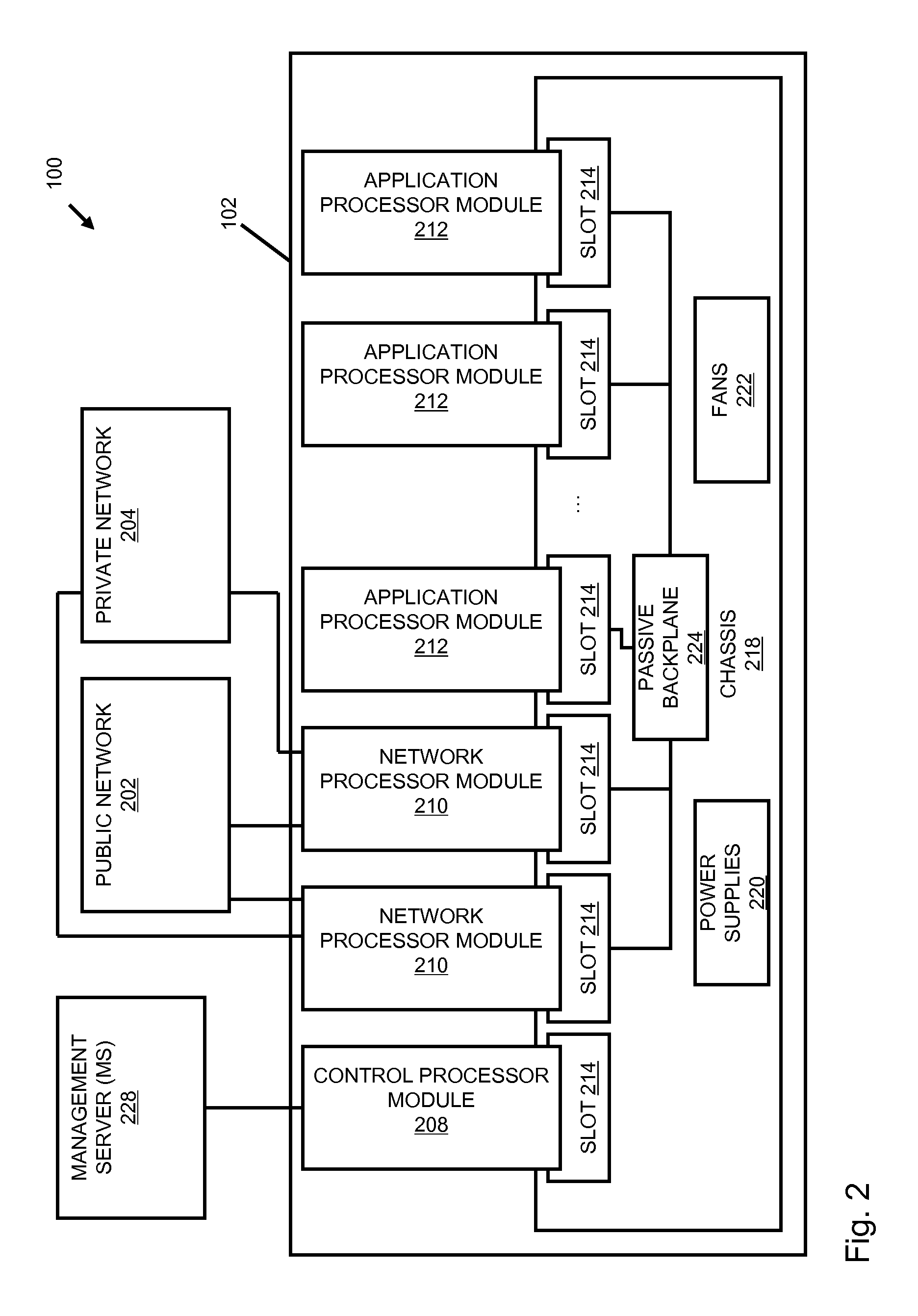
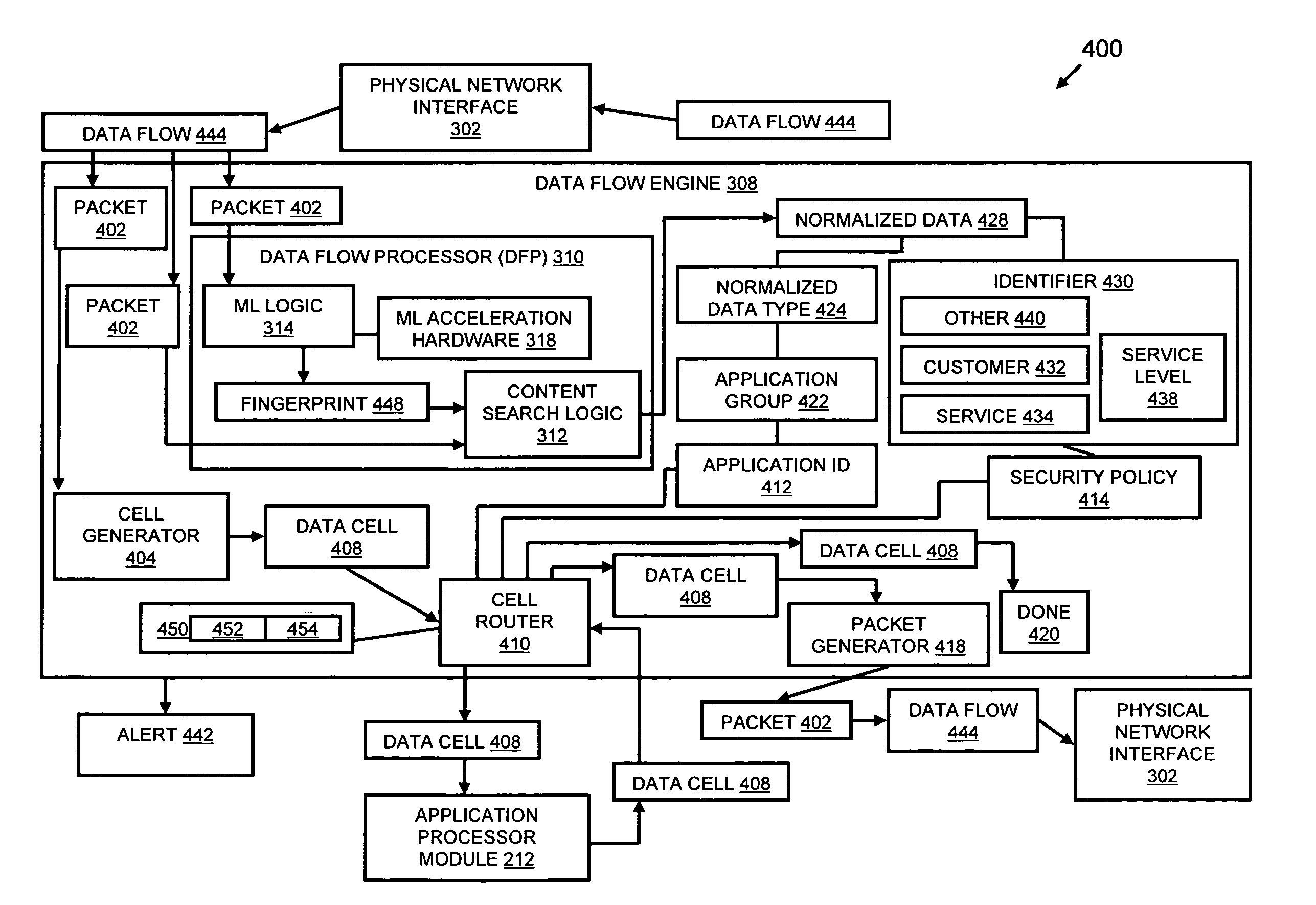
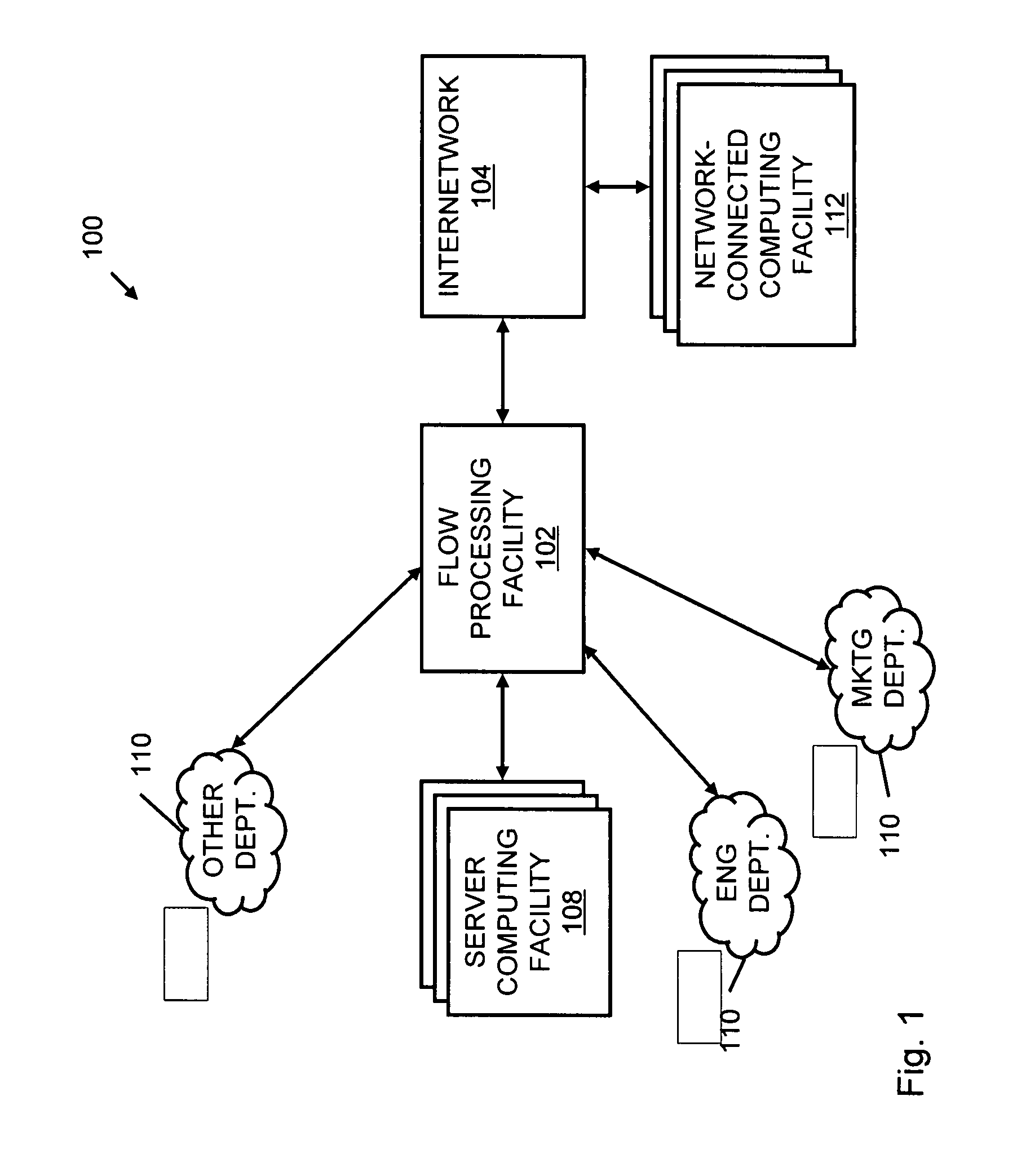
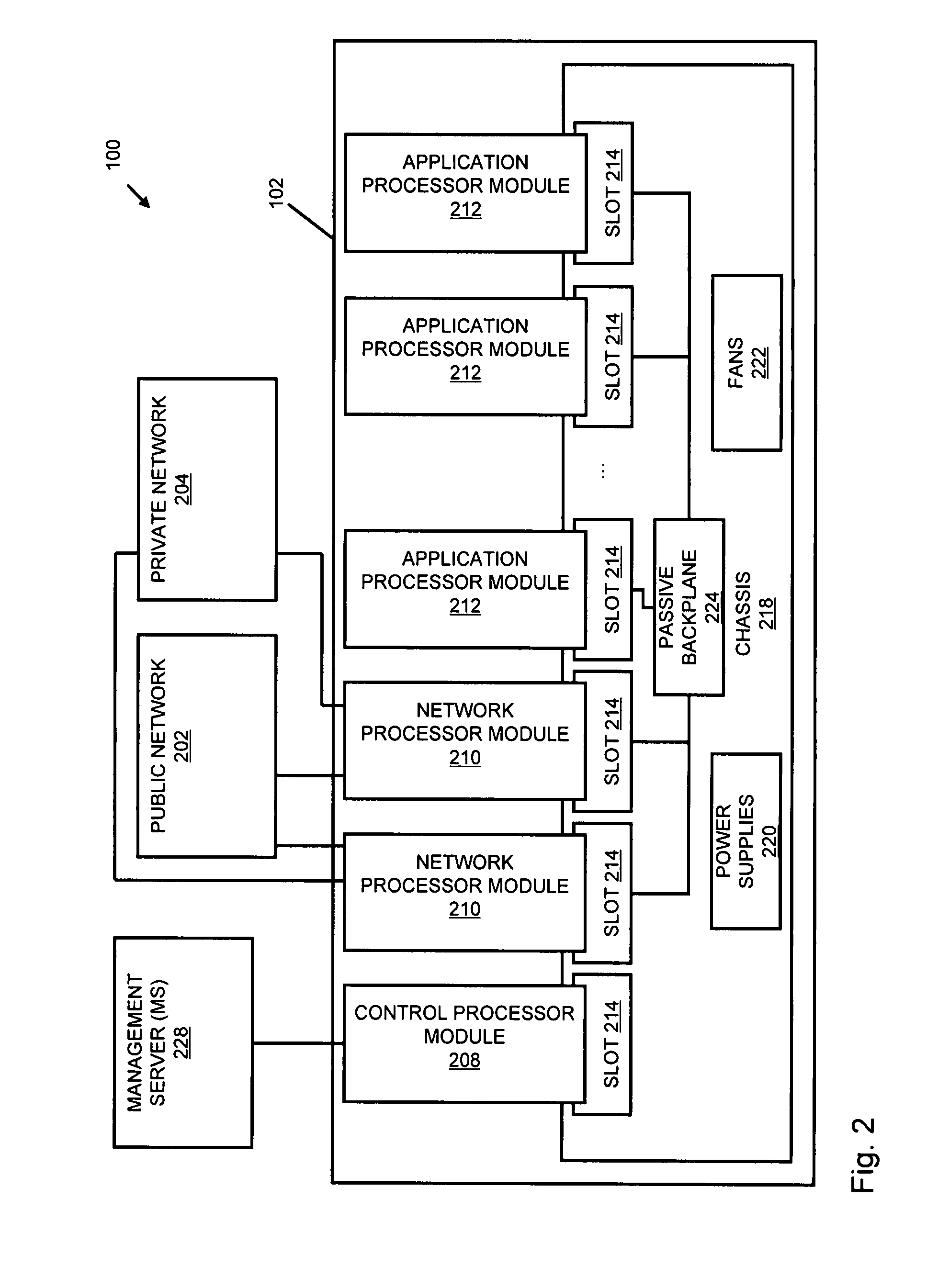
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Method and system for probabilistically quantifying and visualizing relevance between two or more citationally or contextually related data objects
InactiveUS7716226B2Easy to understand intuitivelyData processing applicationsWeb data indexingDocumentation procedureDocument preparation
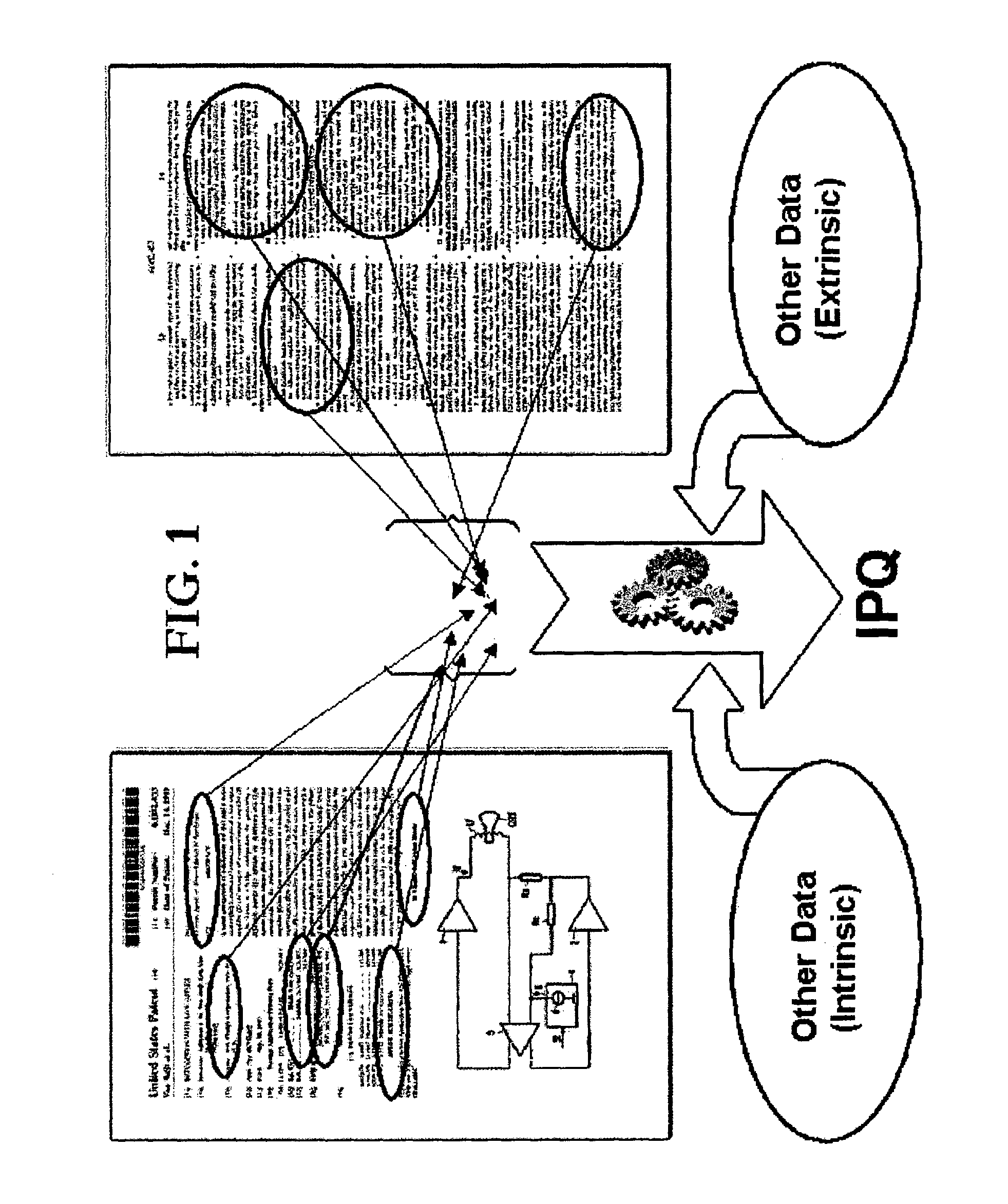
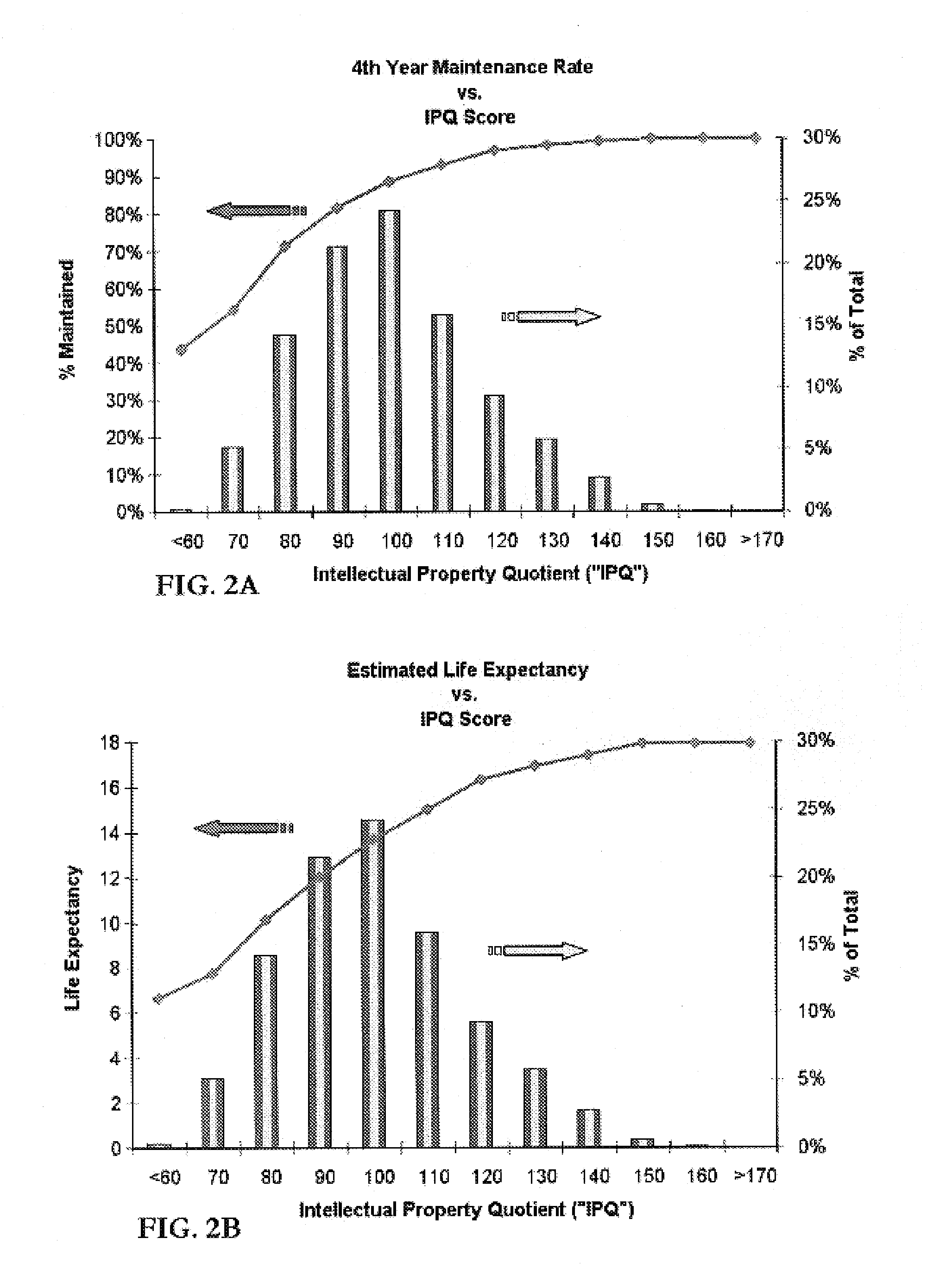
In one embodiment the present invention provides a novel method for probabilistically quantifying a degree of relevance between two or more citationally or contextually related data objects, such as patent documents, non-patent documents, web pages, personal and corporate contacts information, product information, consumer behavior, technical or scientific information, address information, and the like. In another embodiment the present invention provides a novel method for visualizing and displaying relevance between two or more citationally or contextually related data objects. In another embodiment the present invention provides a novel search input / output interface that utilizes an iterative self-organizing mapping (“SOM”) technique to automatically generate a visual map of relevant patents and / or other related documents desired to be explored, searched or analyzed. In another embodiment the present invention provides a novel search input / output interface that displays and / or communicates search input criteria and corresponding search results in a way that facilitates intuitive understanding and visualization of the logical relationships between two or more related concepts being searched.
Owner:PATENTRATINGS
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS8010469B2Increased complexityAvoid problemsMemory loss protectionError detection/correctionData streamSelf-organizing map
Methods and systems for flow processing and switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security are described. Such flow processing facilities may be used for inspecting network traffic packet payloads to detect security threats and intrusions across accessible layers of the network IP stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources.
Owner:CA TECH INC
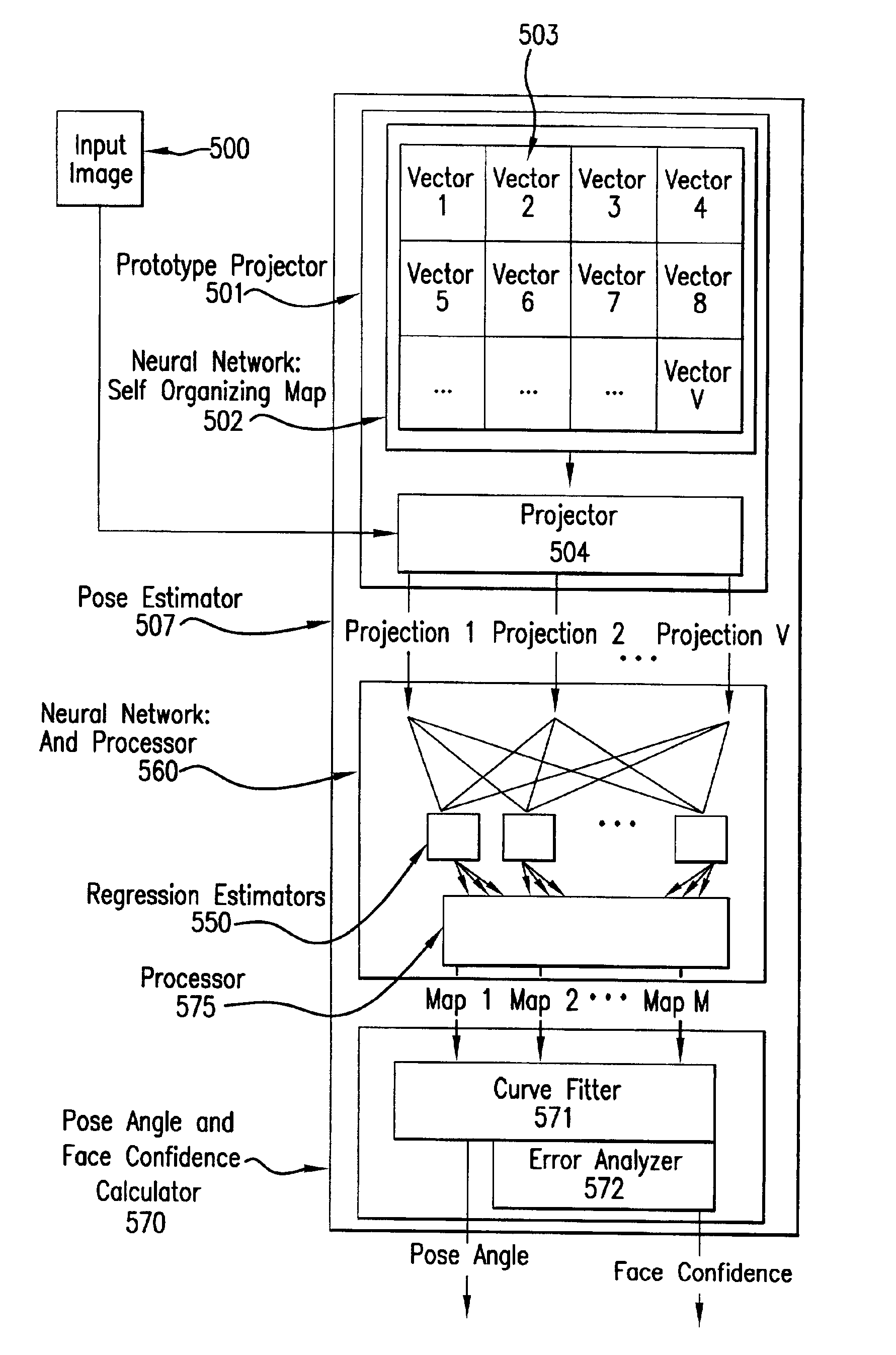
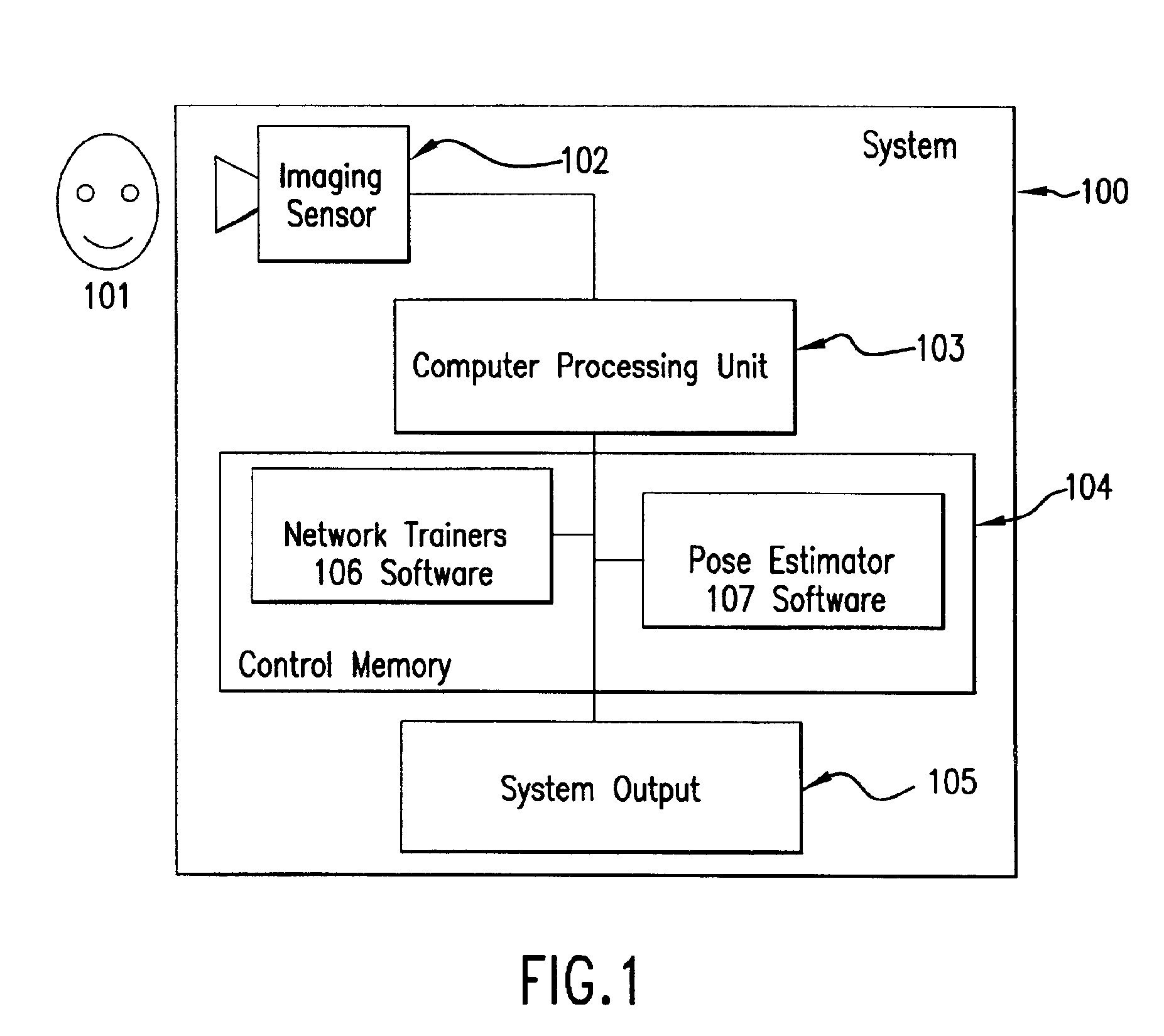
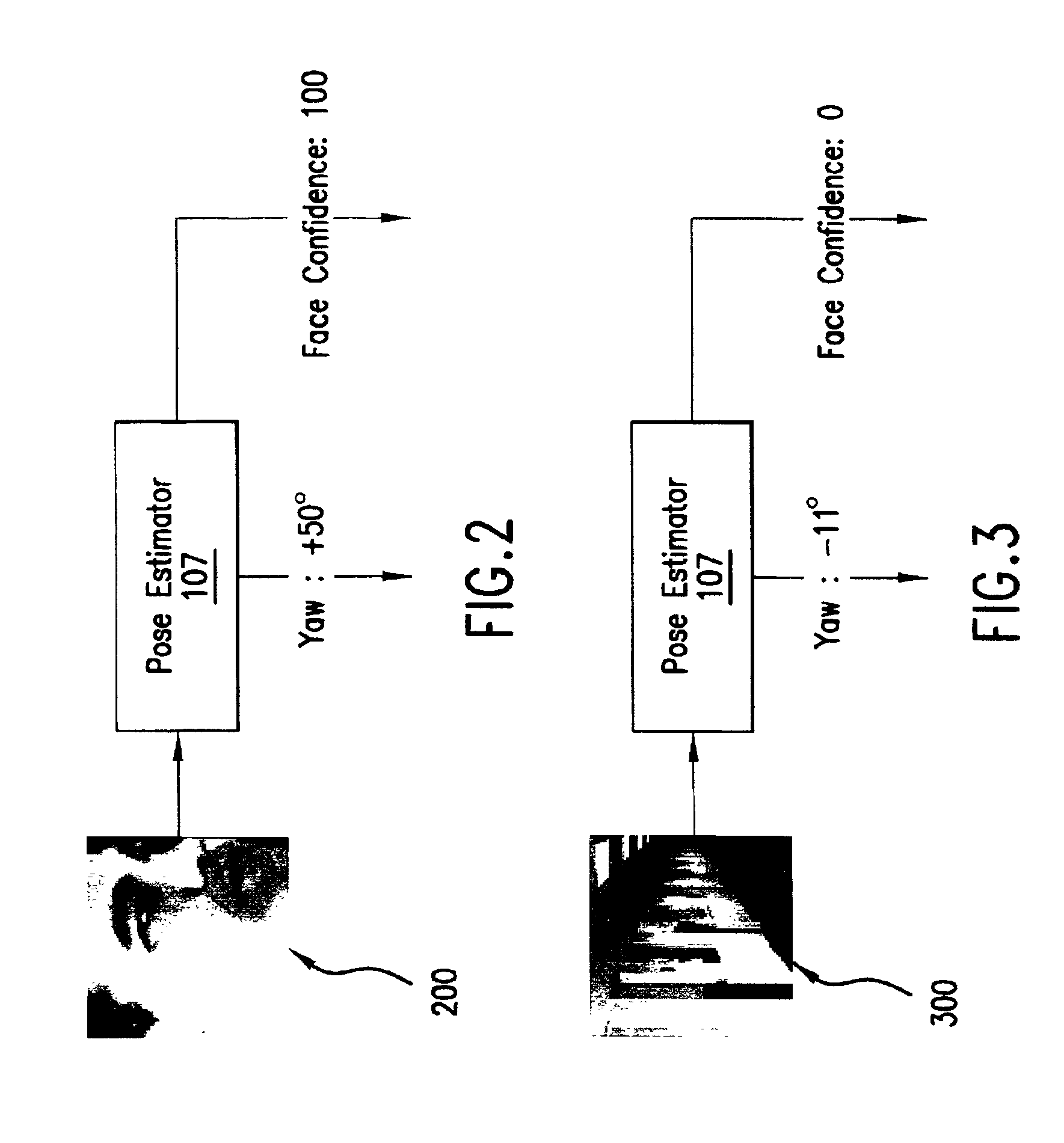
System and method for pose-angle estimation
InactiveUS6959109B2Reduces input image dimensionalityElectric signal transmission systemsImage analysisPattern recognitionComputer graphics (images)
A system and method are disclosed for determining the pose angle of an object in an input image. In a preferred embodiment, the present system comprises a pose estimator having a prototype projector, a regression estimator, and an angle calculator. The prototype projector is preferably adapted to reduce the input image dimensionality for faster further processing by projecting the input pixels of the image onto a Self-Organizing Map (SOM) neural network. The regression estimator is preferably implemented as a neural network and adapted to map the projections to a pattern unique to each pose. The angle calculator preferably includes a curve fitter and an error analyzer. The curve fitter is preferably adapted to estimate the pose angle from the mapping pattern. The error analyzer is preferably adapted to produce a confidence signal representing the likelihood of the input image being a face at the calculated pose. The system also preferably includes two network trainers responsible for synthesizing the neural networks.
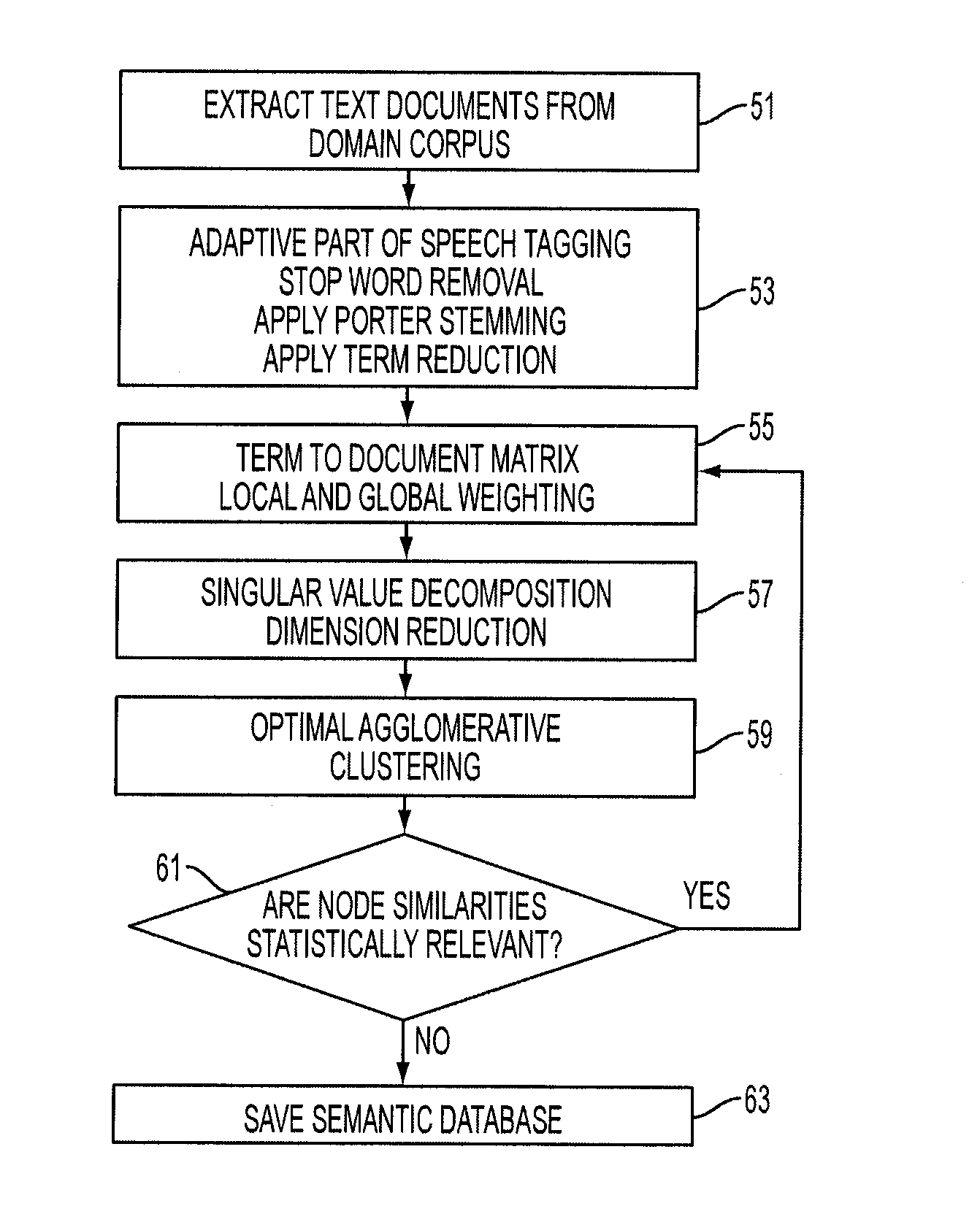
Owner:MORPHOTRUST USA
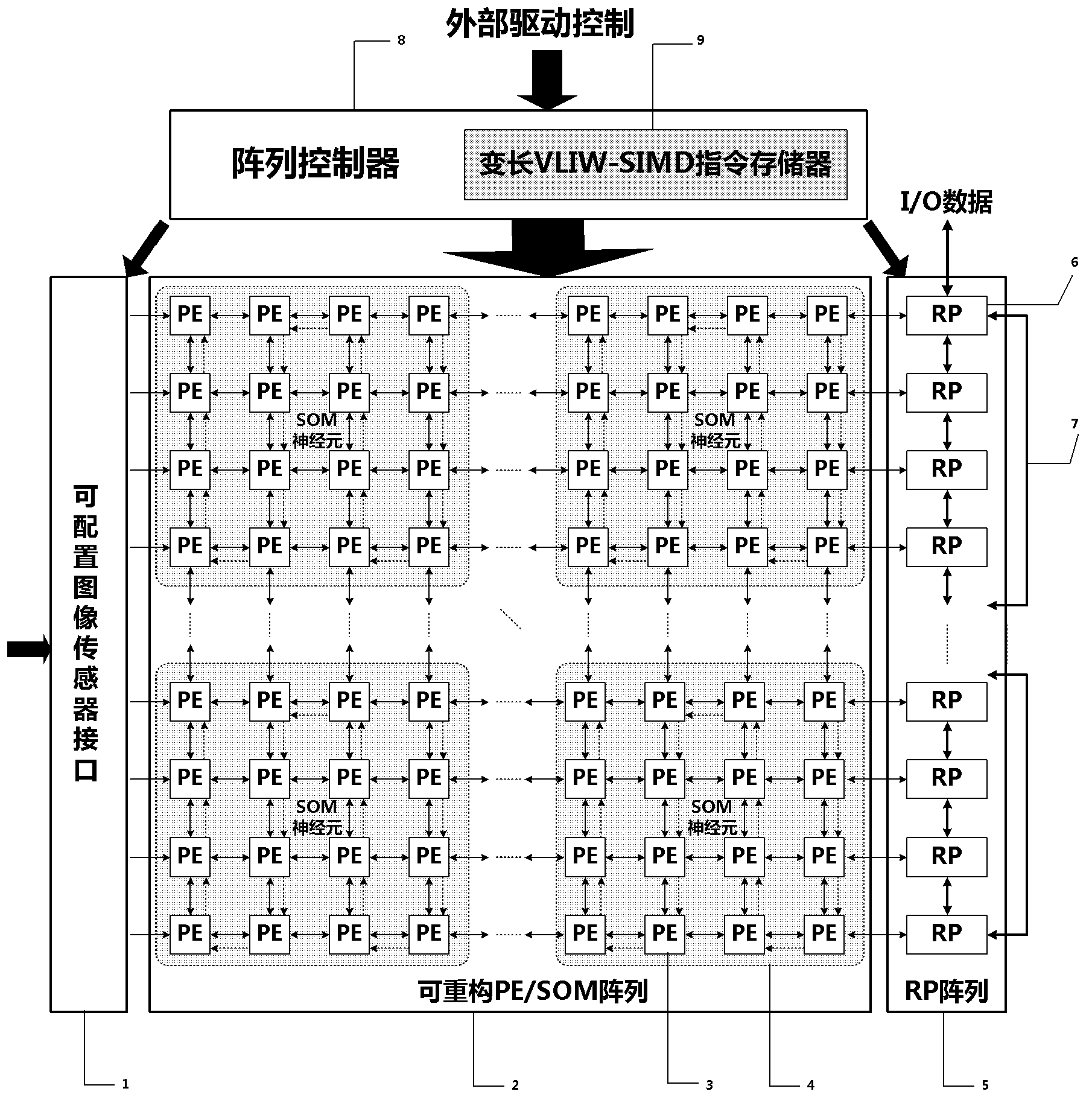
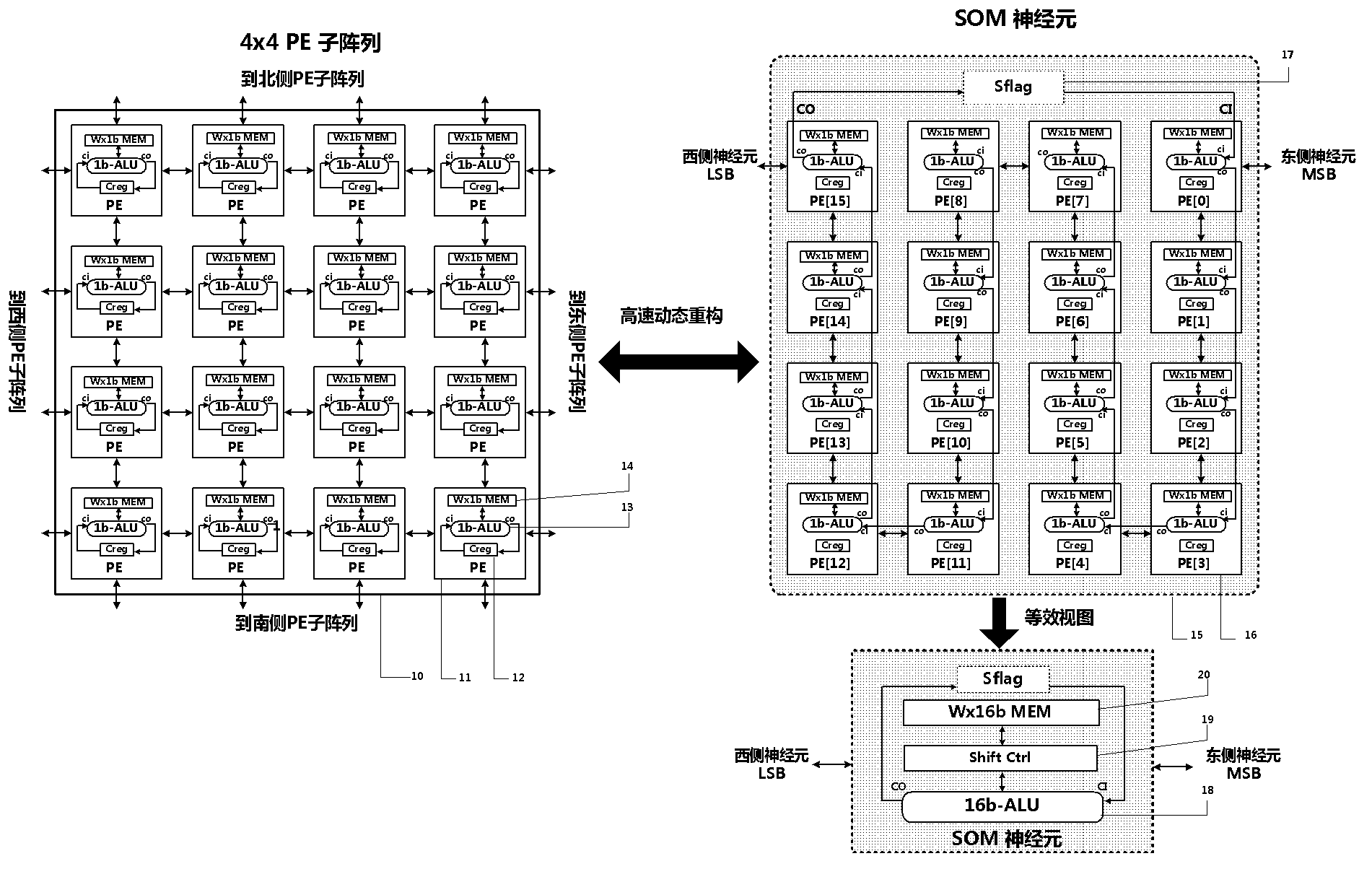
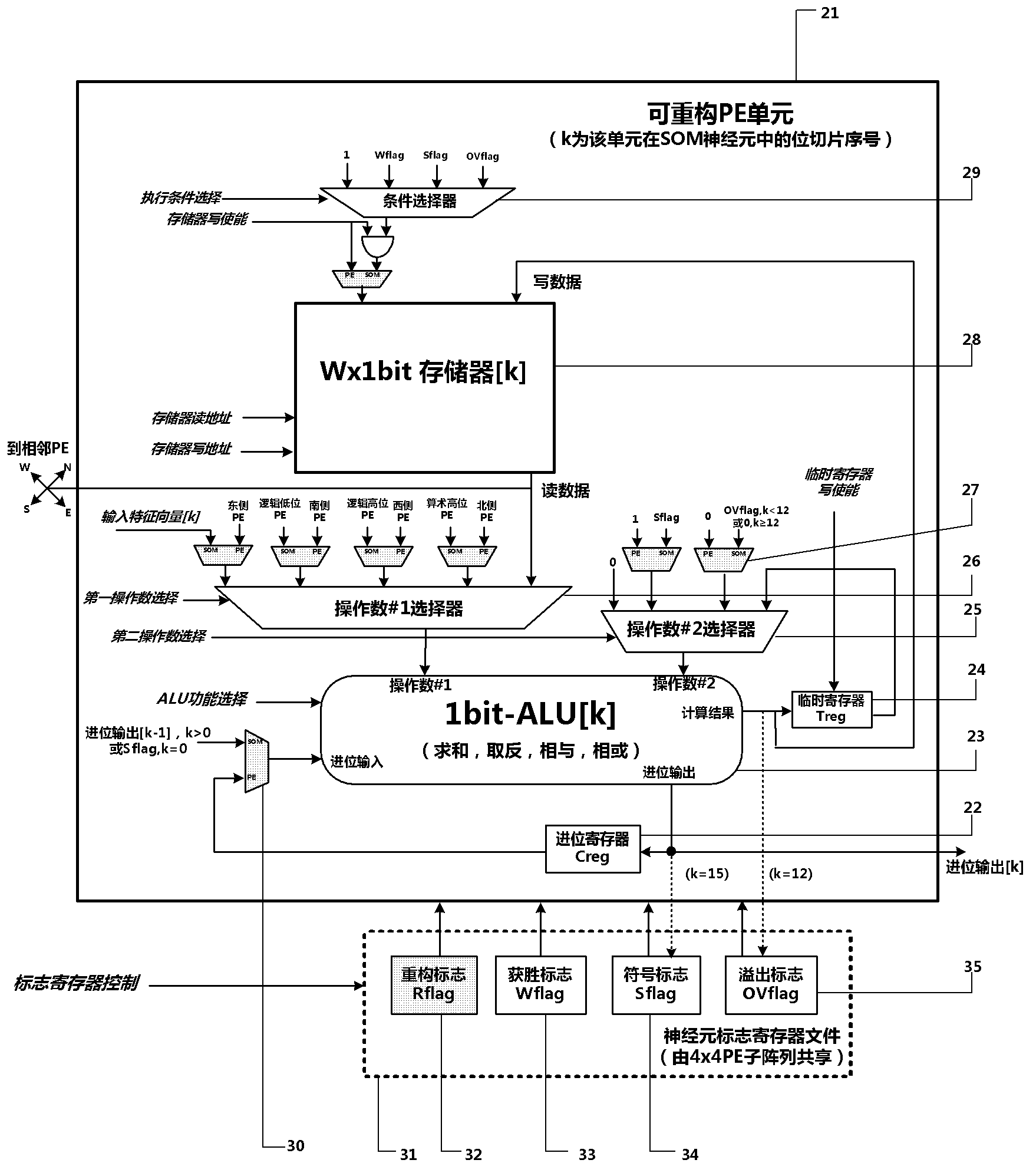
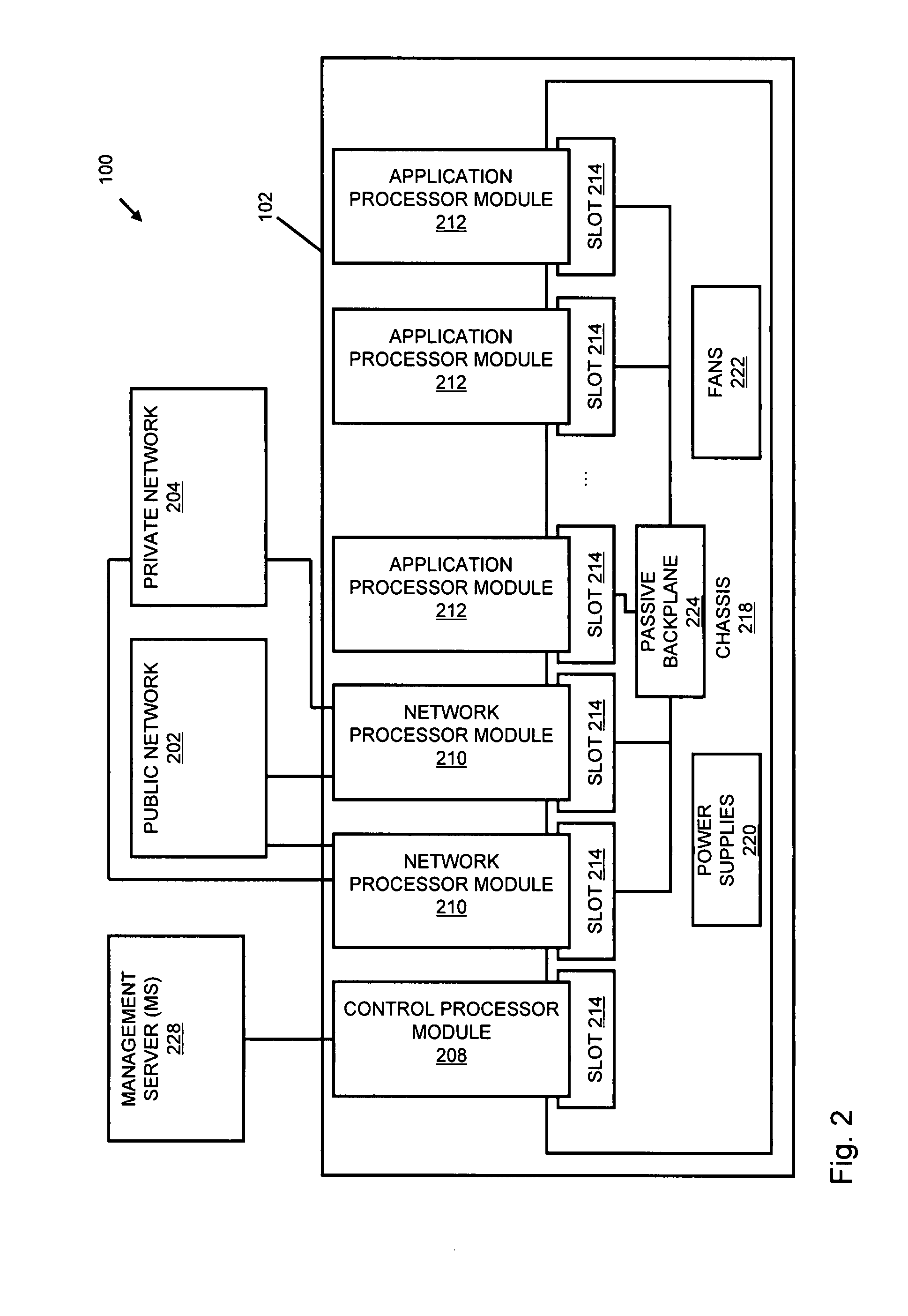
Dynamically reconfigurable multi-stage parallel single instruction multiple data array processing system
ActiveCN103019656AFunctionalImplement image feature extractionConcurrent instruction executionImaging processingReconfigurable computing
The invention discloses a dynamically reconfigurable multi-stage parallel single instruction multiple data array processing system, which comprises a pixel level parallel processing element (PE) array and a row parallel row processor (RP) array, wherein the PE array is mainly used for finishing a linear operation part suitable for the parallel execution of all pixels in low-level and intermediate-level image processing; the RP array is used for operation suitable to be finished in a row parallel way or complex nonlinear operation in the low-level and intermediate-level processing; and particularly, the PE array can also be dynamically reconfigured into a two-dimensional self-organizing map (SOM) neural network with extremely low performance and area overhead, and the neural network can realize advanced image processing functions of high-speed parallel online training, feature recognition and the like with the coordination of RPs. The shortcoming that advanced image processing cannot be used for pixel level parallel RP arrays in the conventional programmable vision chip and the conventional parallel vision processor is completely overcome, and the implementation of a fully-functional, low-cost, low-power consumption, intelligent and portable high-speed real-time visual image system on chip is facilitated.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Methods, Apparatus and Products for Semantic Processing of Text
ActiveUS20130246322A1Exploit analyzing powerSimple interfaceNatural language translationSemantic analysisSemantic contextSemantic clustering
A computer-implemented method of training a neural network includes training a first neural network of a self organizing map type with a first set of first text documents each containing one or more keywords in a semantic context to map each document to a point in the self organizing map y semantic clustering; determining, for each keyword in the first set, all points in the self organizing map to which first documents containing said keyword are mapped, as a pattern and storing said pattern for said keyword in a pattern dictionary; forming at least one sequence of keywords from a second set of second text documents each containing one or more keywords in a semantic context; translating said at least one sequence of keywords into at least one sequence of patterns using the pattern dictionary; and training a second neural network with the at least one sequence of patterns.
Owner:CORTICAL IO
System and method of structuring data for search using latent semantic analysis techniques
ActiveUS20110225159A1Digital data information retrievalDigital data processing detailsDocument preparationA domain
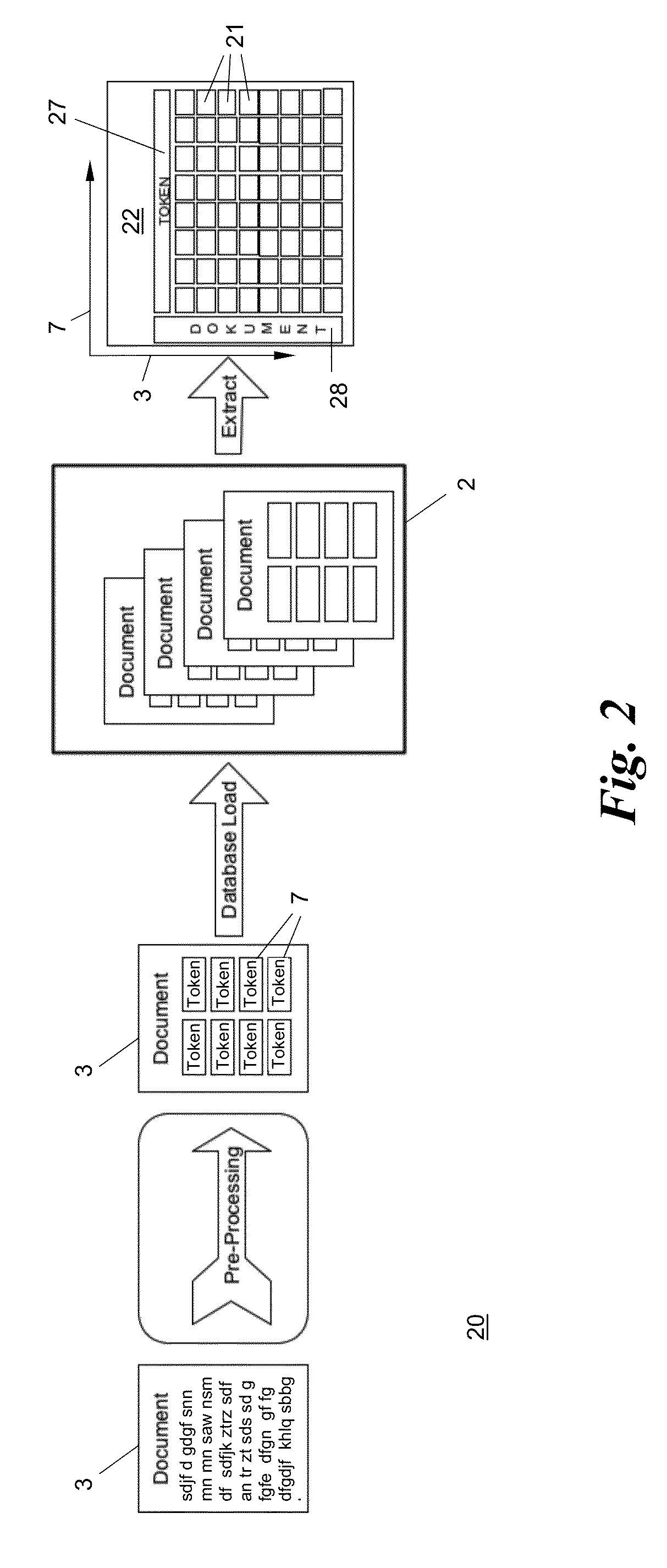
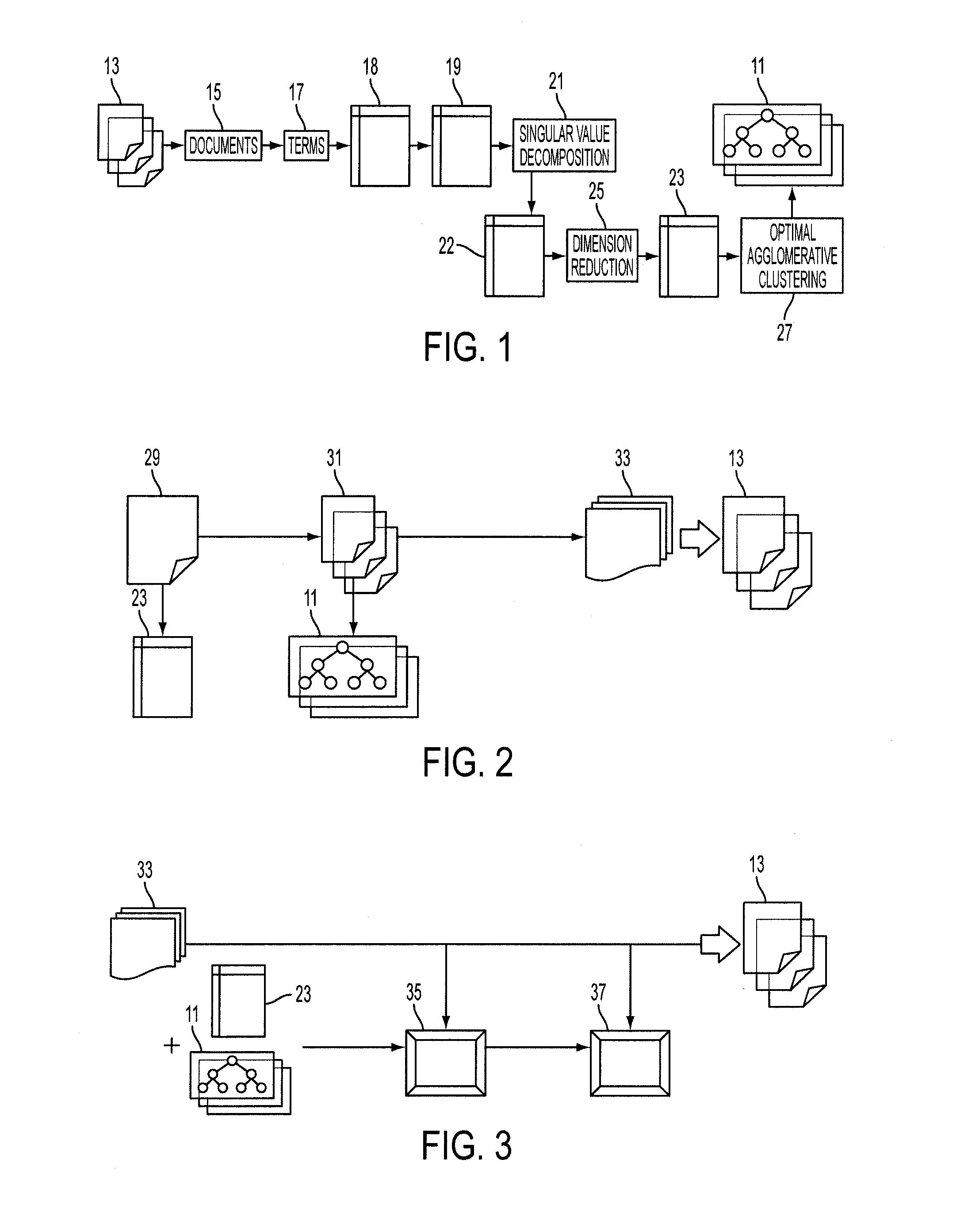
The disclosed embodiments provide a system and method for using modified Latent Semantic Analysis techniques to structure data for efficient search and display. The present invention creates a hierarchy of clustered documents, representing the topics of a domain corpus, through a process of optimal agglomerative clustering. The output from a search query is displayed in a fisheye view corresponding to the hierarchy of clustered documents. The fisheye view may link to a two-dimensional self-organizing map that represents semantic relationships between documents.
Owner:SYNTORG INC
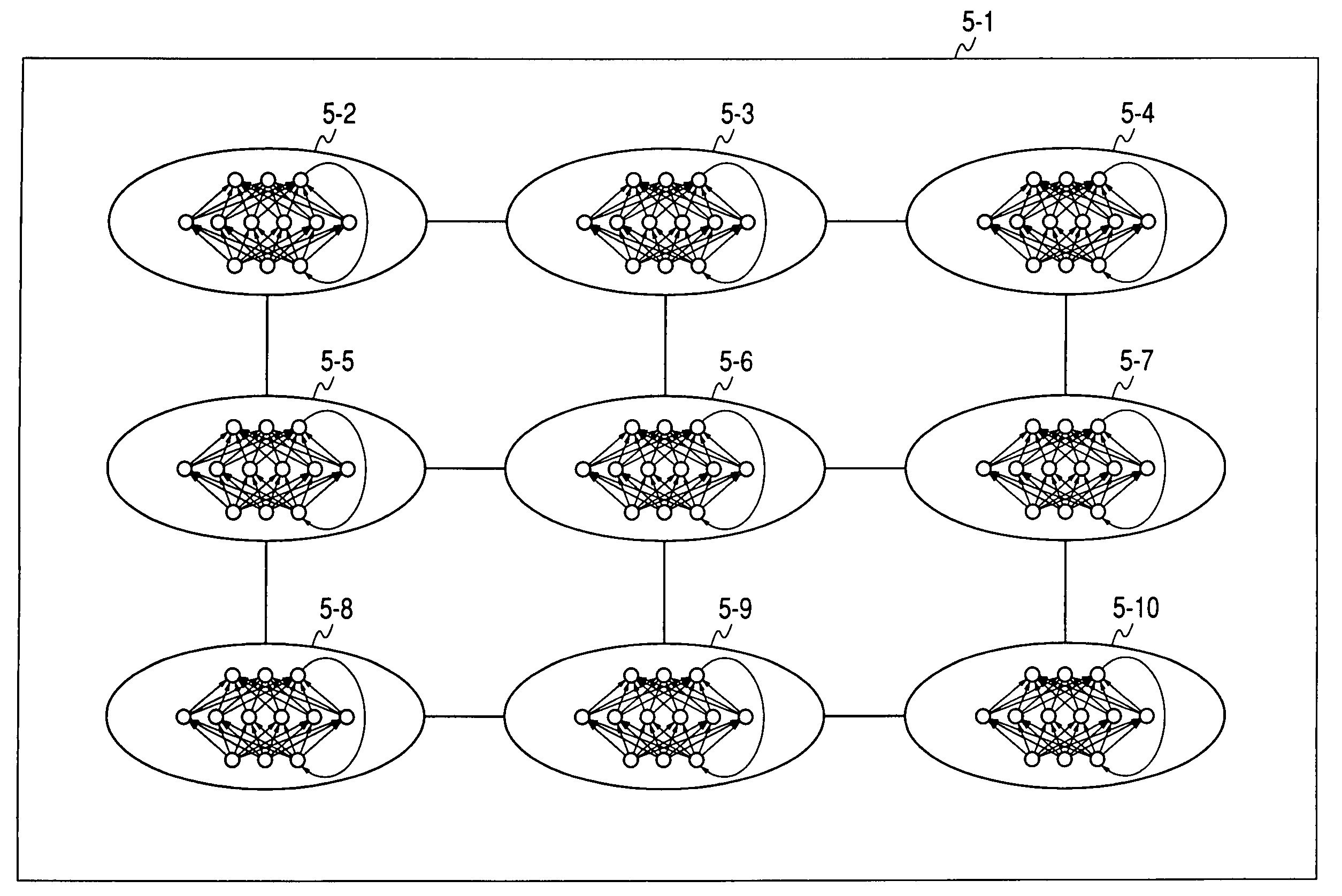
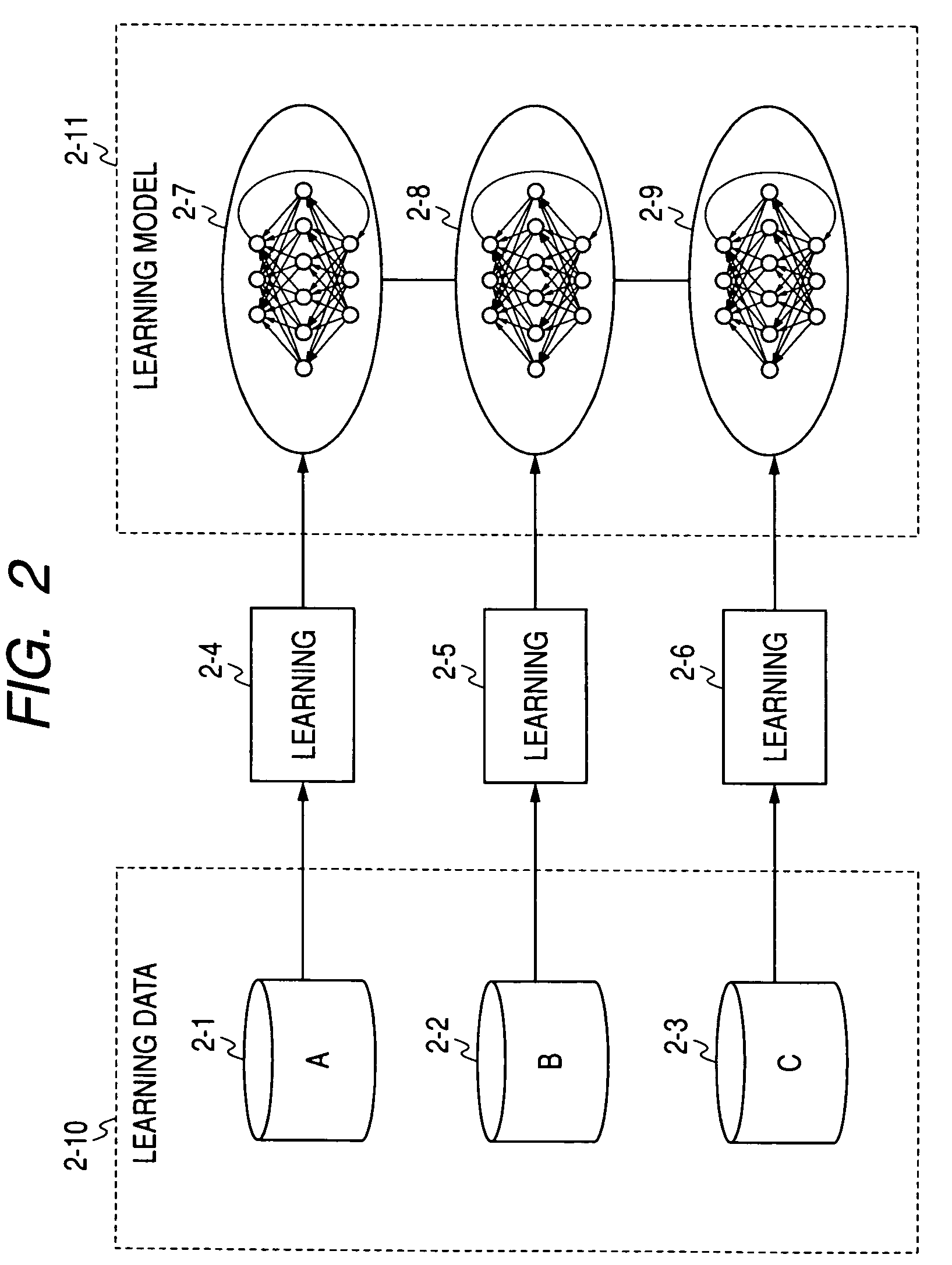
Apparatus and method for embedding recurrent neural networks into the nodes of a self-organizing map
InactiveUS7672920B2Digital computer detailsCharacter and pattern recognitionNetwork onMachine learning
A learning system is provided, which includes network storage means for storing a network including a plurality of nodes, each of which holds a dynamics; and learning means for self-organizationally updating the dynamics of the network on the basis of measured time-series data.
Owner:SONY CORP
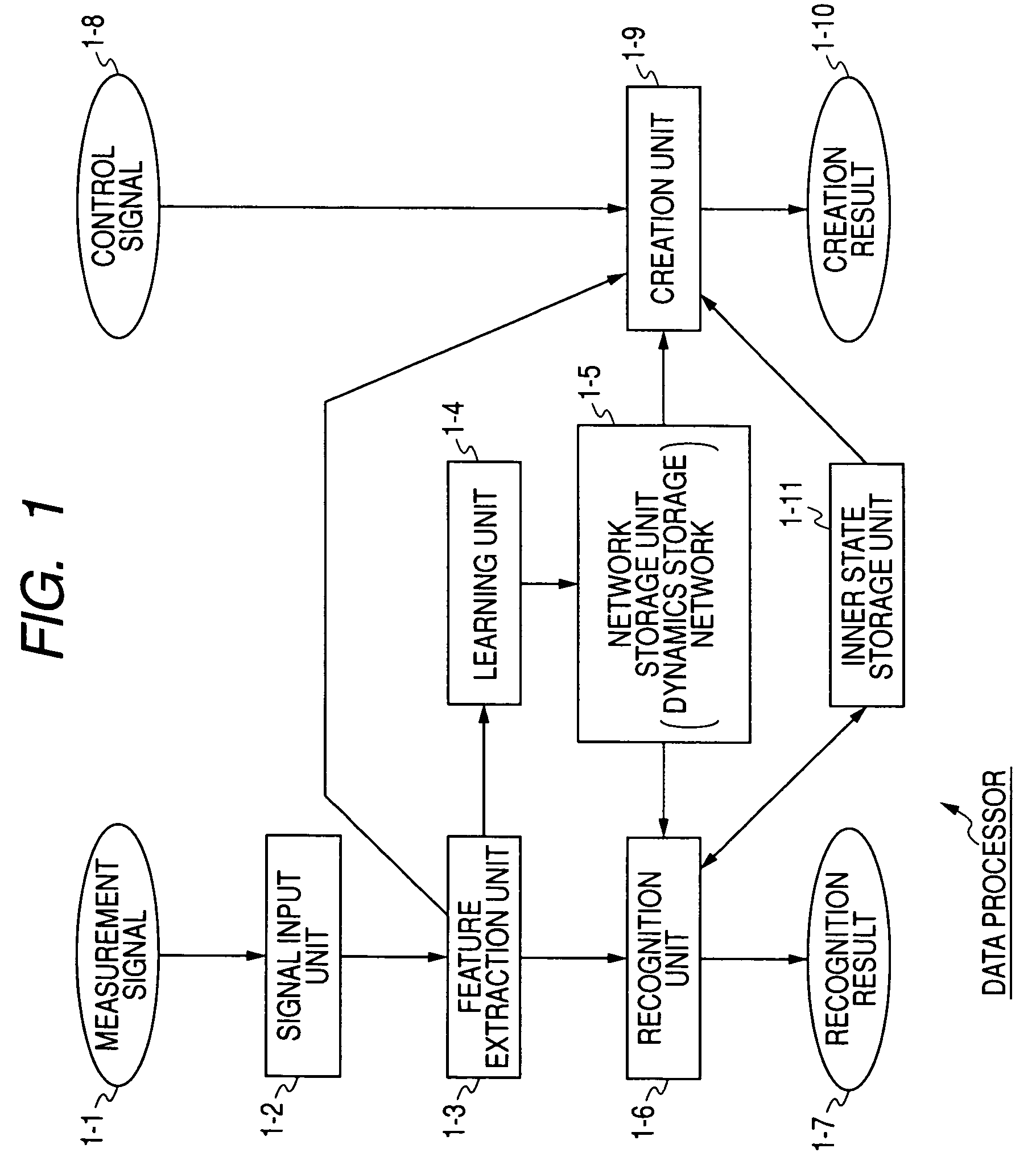
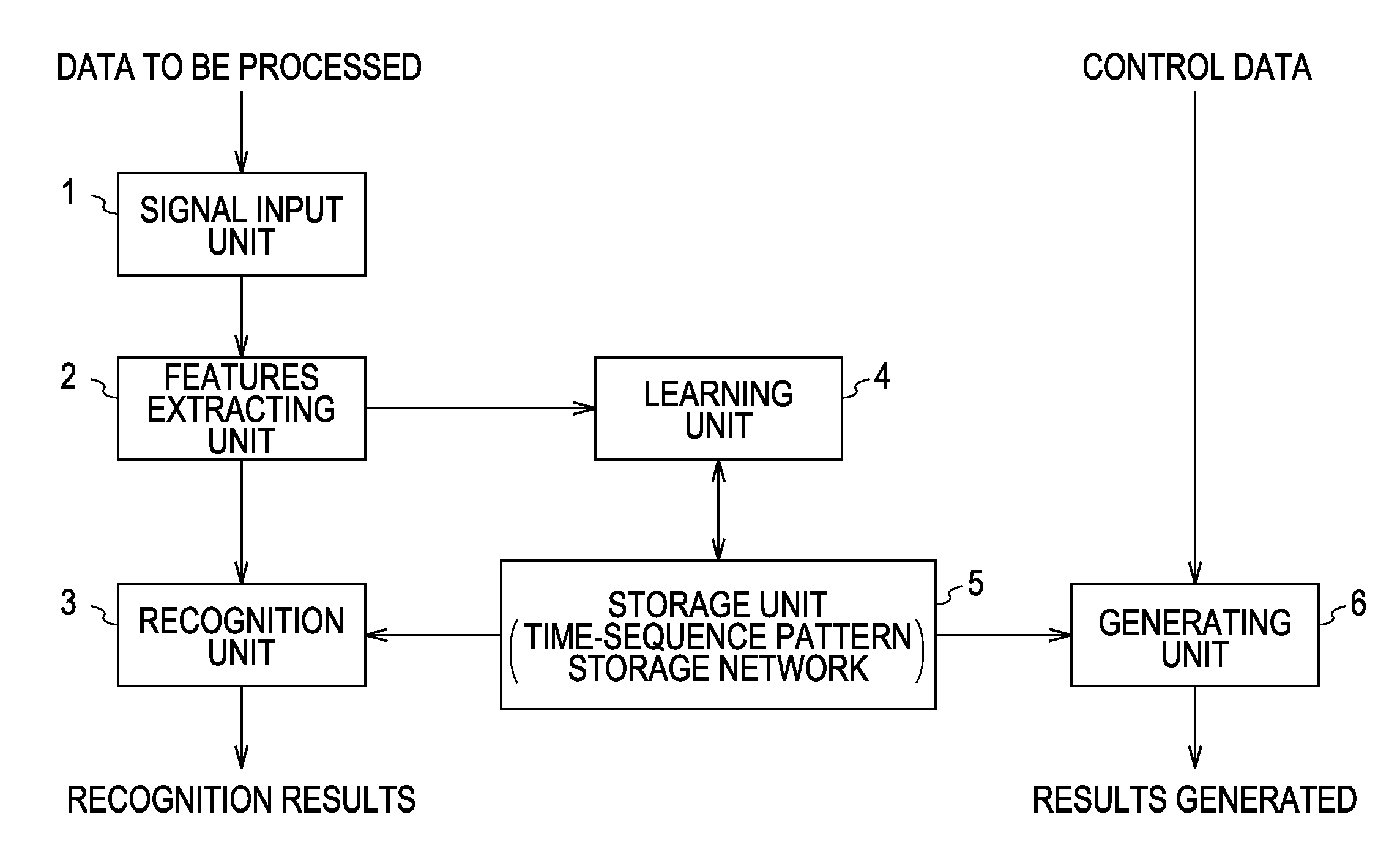
Data Processing Device, Data Processing Method, and Program
InactiveUS20070250461A1Increase in amount of computationProgramme-controlled manipulatorDigital computer detailsLearning unitData mining
A data processing device for processing time-sequence data includes a learning unit for performing self-organizing learning of a SOM (self-organization map) making up a hierarchical SOM in which a plurality of SOMs are connected so as to construct a hierarchical structure, using, as SOM input data which is input to the SOM, a time-sequence of node information representing a winning node of a lower-order SOM which is at a lower hierarchical level from the SOM.
Owner:SONY CORP
Identifying anomalous object types during classification
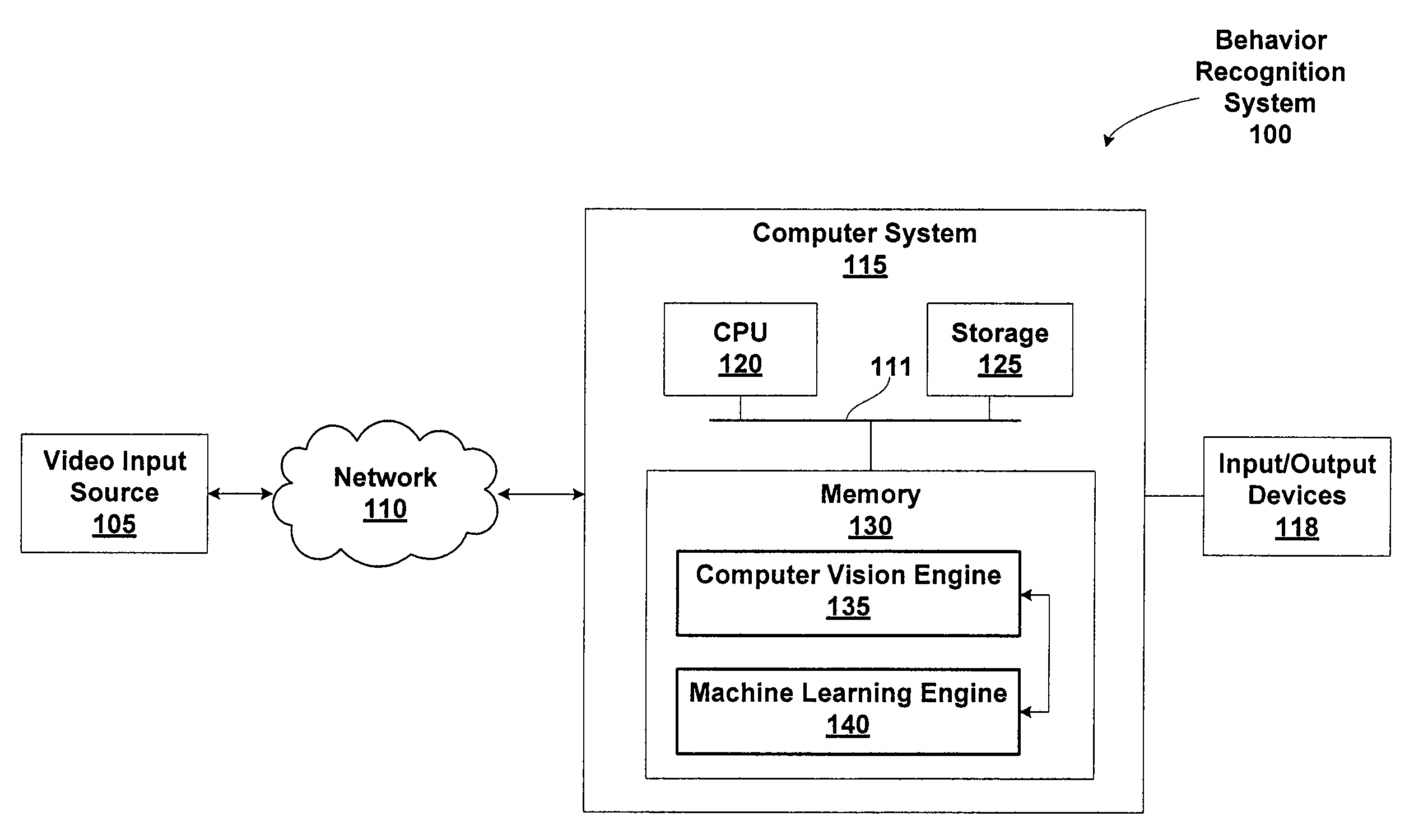
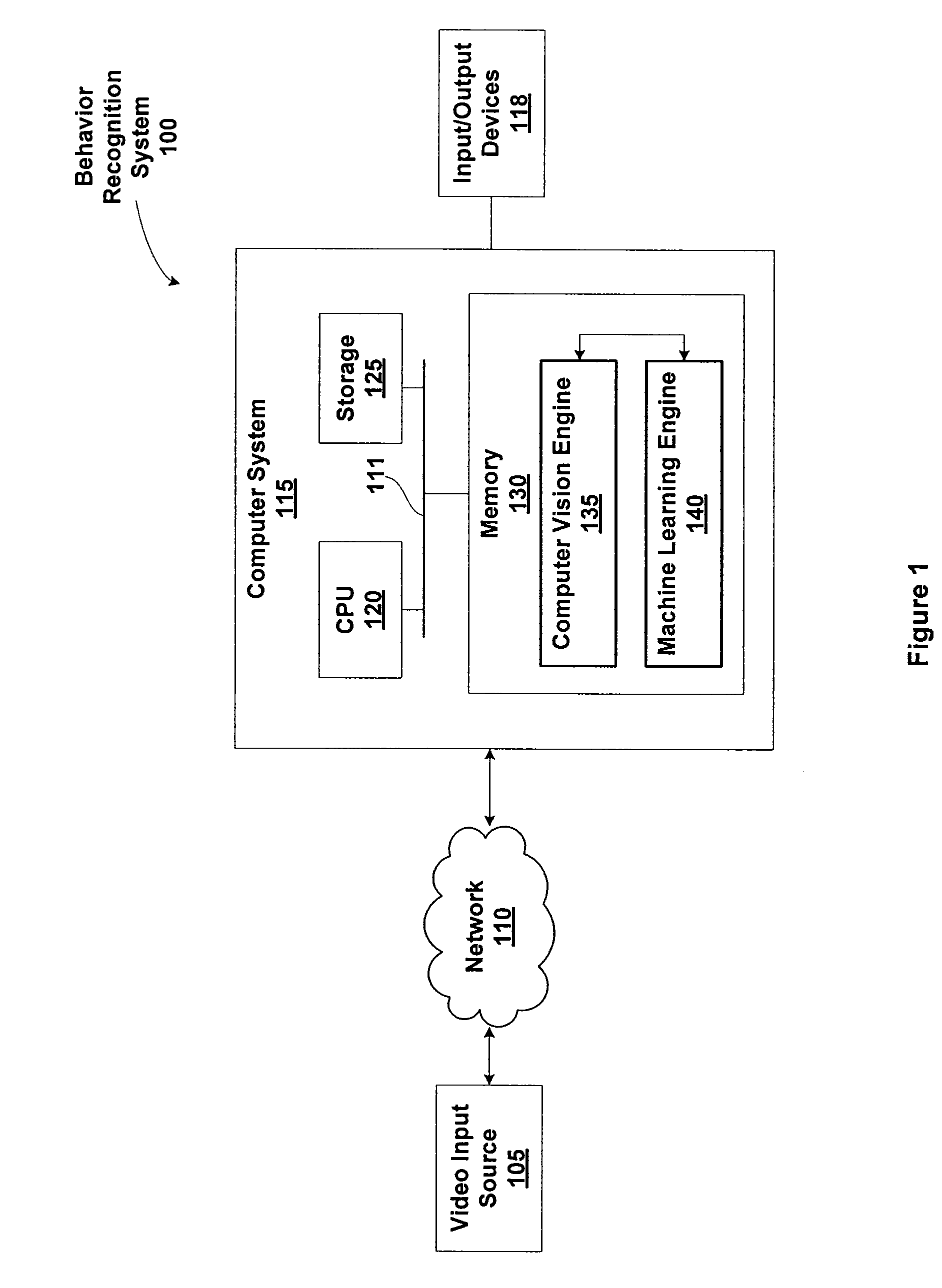
ActiveUS20110052068A1Character and pattern recognitionElectric/magnetic detectionTraining phaseObject definition
Techniques are disclosed for identifying anomaly object types during classification of foreground objects extracted from image data. A self-organizing map and adaptive resonance theory (SOM-ART) network is used to discover object type clusters and classify objects depicted in the image data based on pixel-level micro-features that are extracted from the image data. Importantly, the discovery of the object type clusters is unsupervised, i.e., performed independent of any training data that defines particular objects, allowing a behavior-recognition system to forgo a training phase and for object classification to proceed without being constrained by specific object definitions. The SOM-ART network is adaptive and able to learn while discovering the object type clusters and classifying objects and identifying anomaly object types.
Owner:MOTOROLA SOLUTIONS INC
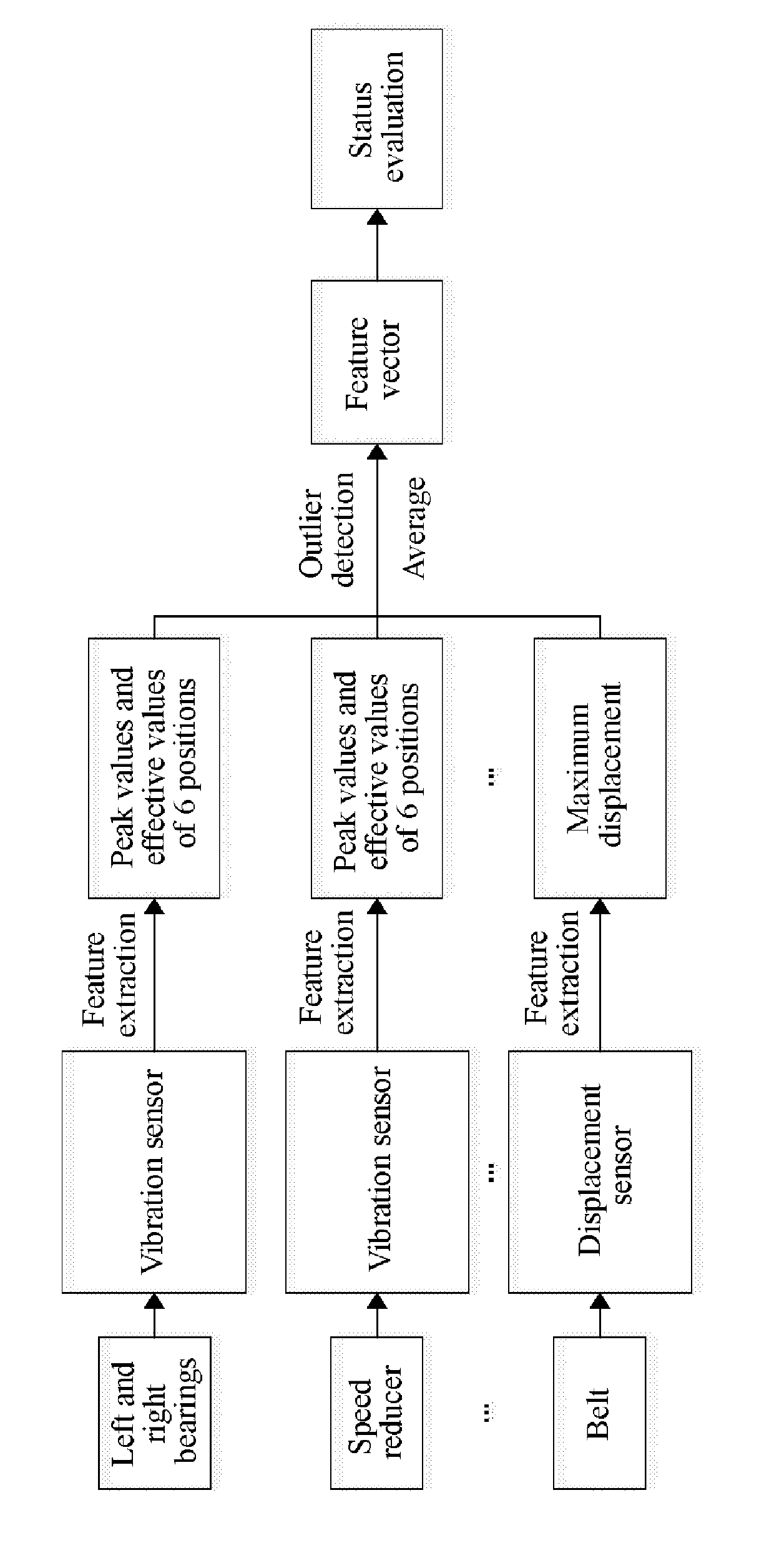
Method for evaluating health status of mechanical equipment
InactiveUS20190285517A1Testing/monitoring control systemsStructural/machines measurementSelf organizing map neural networkNerve network
Disclosed is a method for evaluating a health status of mechanical equipment. Firstly, status data of main components on mechanical equipment are collected by a sensor, and feature extraction is performed to obtain feature parameters. Then, noise data and fault data are extracted by an outlier detection algorithm, and only the fault data are retained. Subsequently, dimension reduction processing is performed to obtain a feature vector for final evaluation. Finally, equipment status evaluation is performed, a self-organizing map neural network model is established by health status data and failure status data, rate impact factors of each group of data to be evaluated are calculated by an entropy weight theory, and the rate impact factors are introduced into a neural network to perform health factor calculation. The present invention implements overall status evaluation for mechanical equipment, provides a basis for health maintenance of the mechanical equipment, and avoids unnecessary economic losses.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS +1
Systems and methods for processing data flows
InactiveUS7979368B2Increased complexityAvoid problemsDigital computer detailsDigital dataData packData stream
Owner:CA TECH INC
Use of machine learning for classification of magneto cardiograms
InactiveUS20070167846A1Exceeding quality of classificationCharacter and pattern recognitionMedical automated diagnosisMagnetocardiographyKernel method
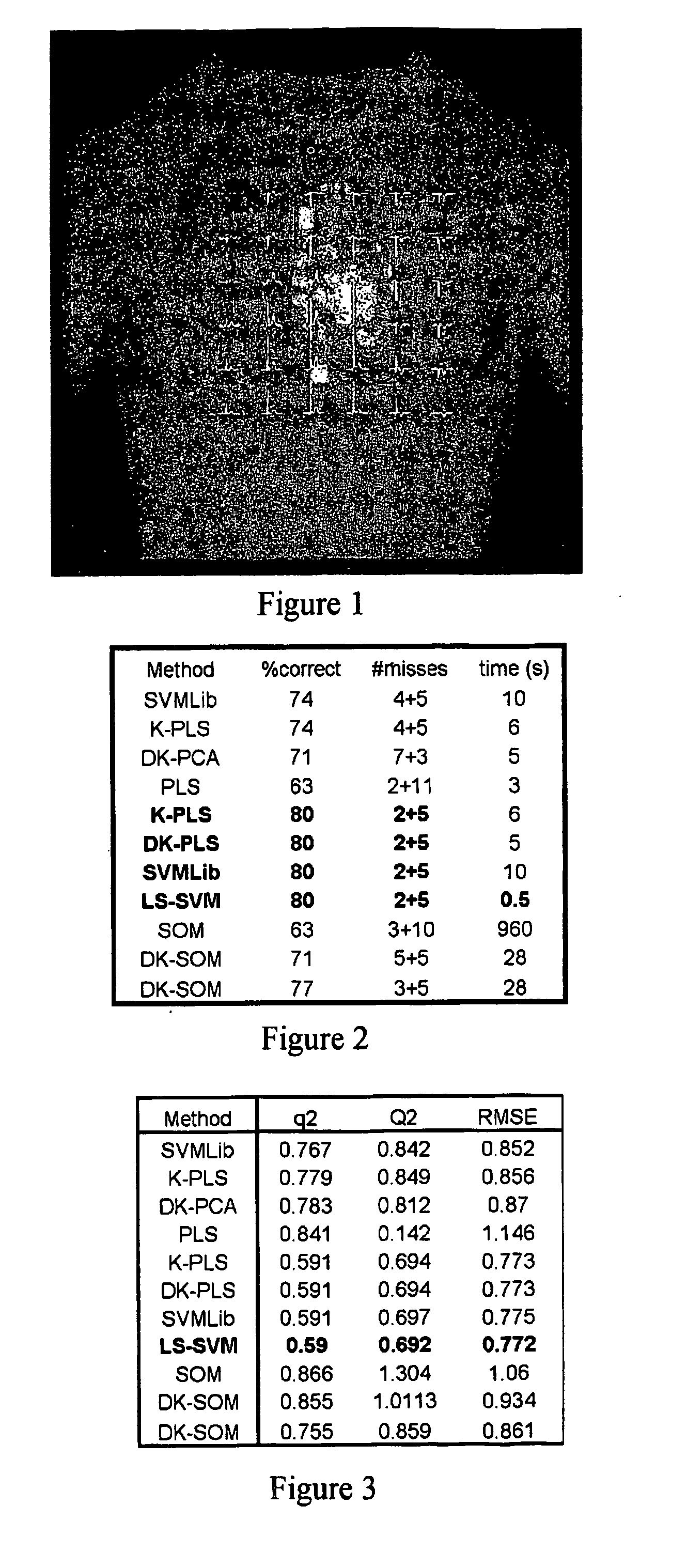
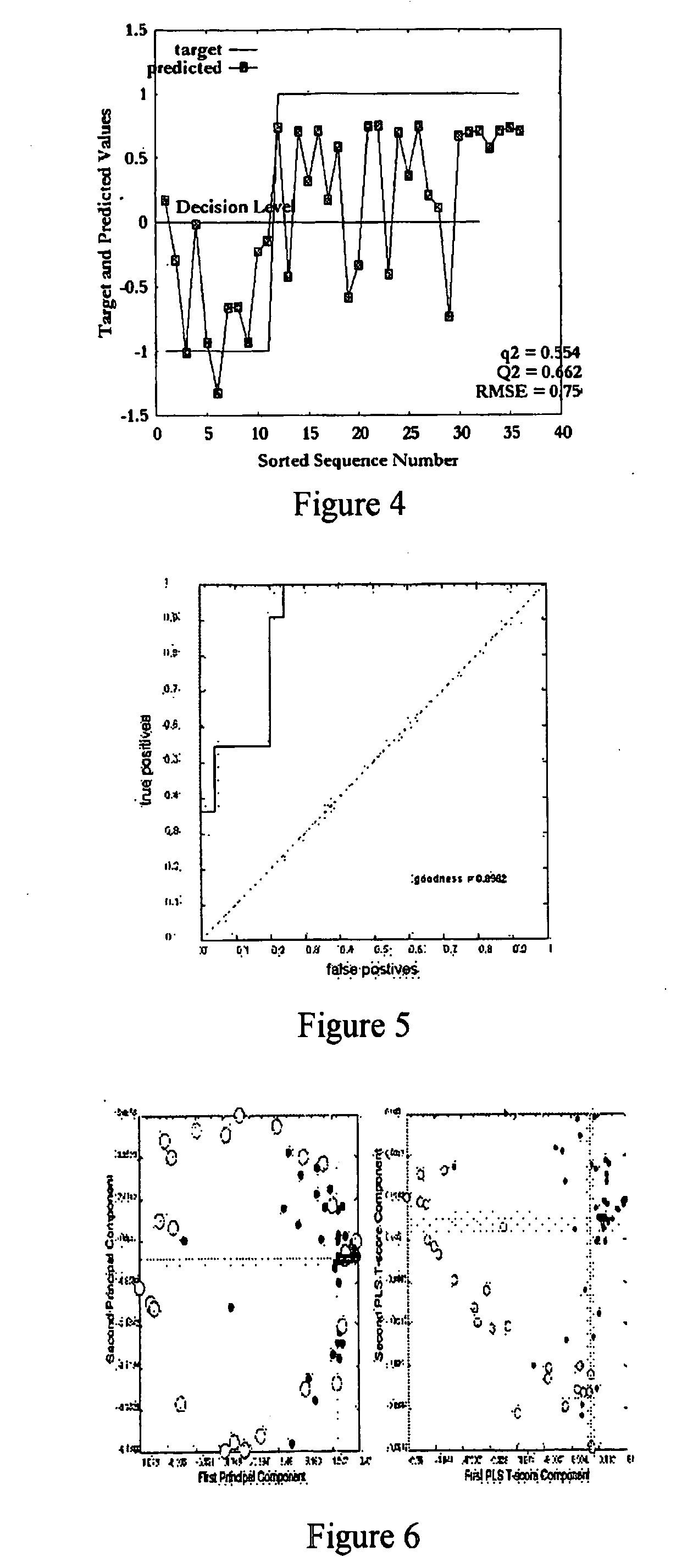
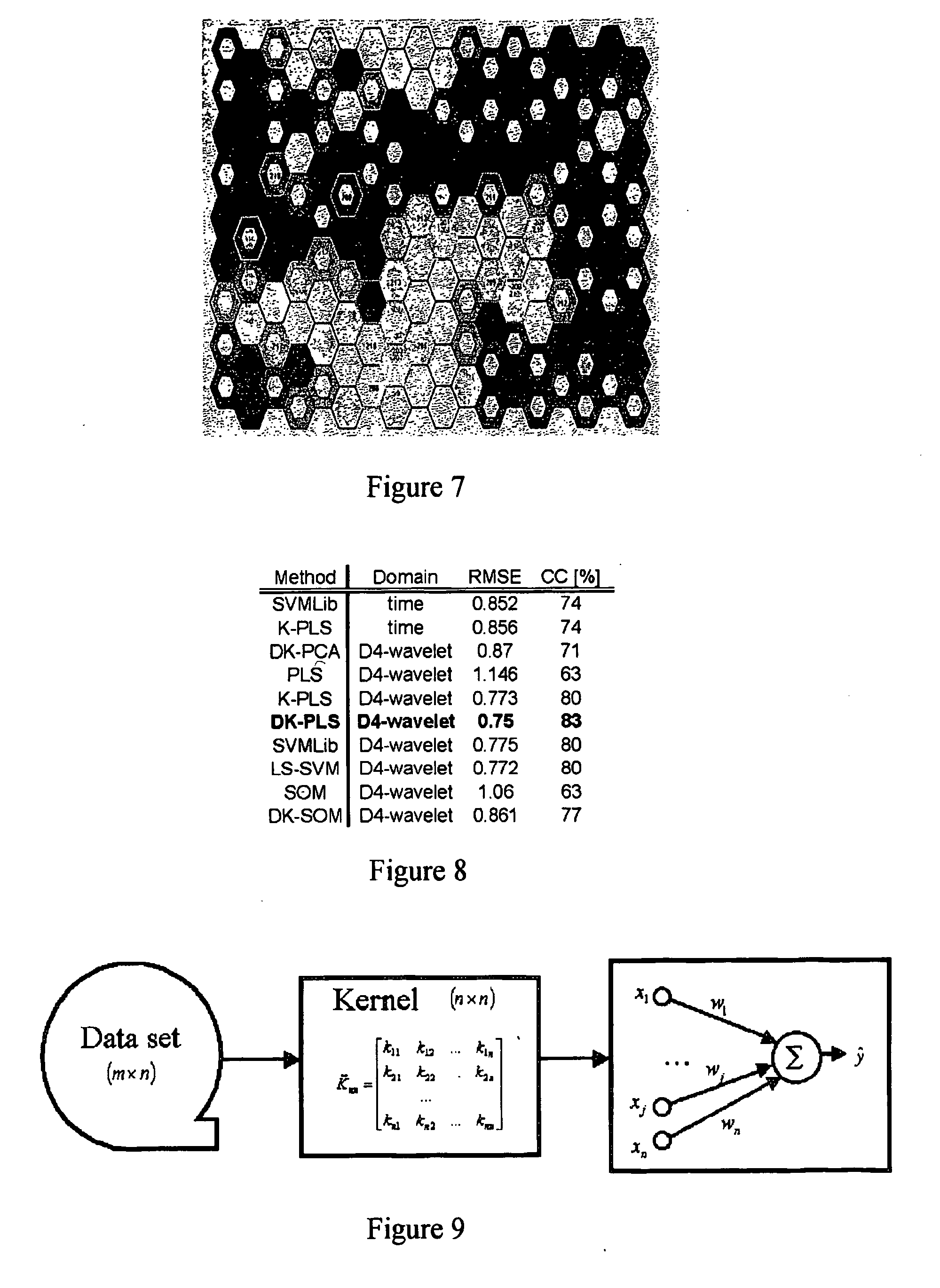
The use of machine learning for pattern recognition in magnetocardiography (MCG) that measures magnetic fields emitted by the electrophysiological activity of the heart is disclosed herein. Direct kernel methods are used to separate abnormal MCG heart patterns from normal ones. For unsupervised learning, Direct Kernel based Self-Organizing Maps are introduced. For supervised learning Direct Kernel Partial Least Squares and (Direct) Kernel Ridge Regression are used. These results are then compared with classical Support Vector Machines and Kernel Partial Least Squares. The hyper-parameters for these methods are tuned on a validation subset of the training data before testing. Also investigated is the most effective pre-processing, using local, vertical, horizontal and two-dimensional (global) Mahanalobis scaling, wavelet transforms, and variable selection by filtering. The results, similar for all three methods, were encouraging, exceeding the quality of classification achieved by the trained experts. Thus, a device and associated method for classifying cardiography data is disclosed, comprising applying a kernel transform to sensed data acquired from sensors sensing electromagnetic heart activity, resulting in transformed data, prior to classifying the transformed data using machine learning.
Owner:CARDIOMAG IMAGING
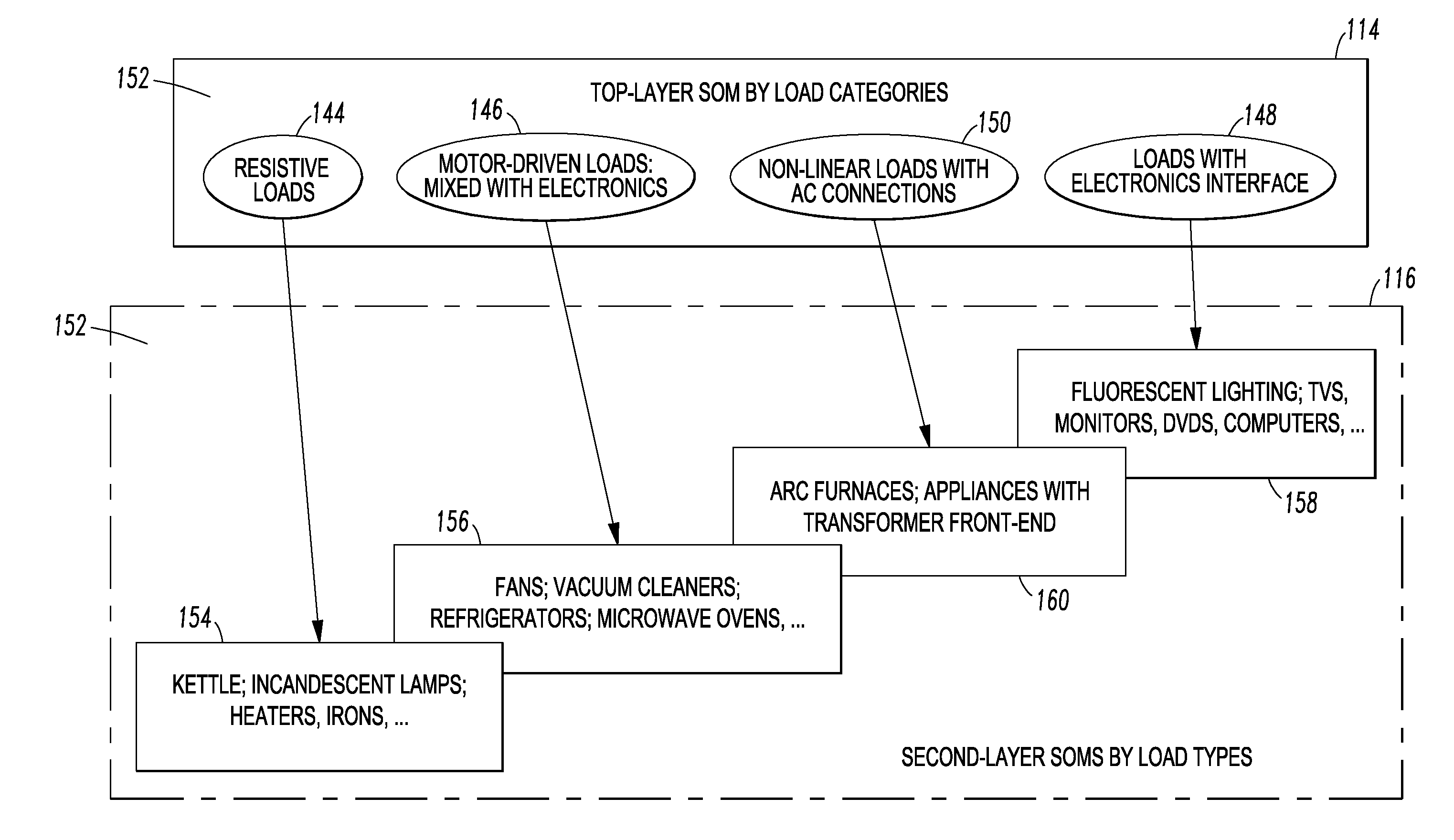
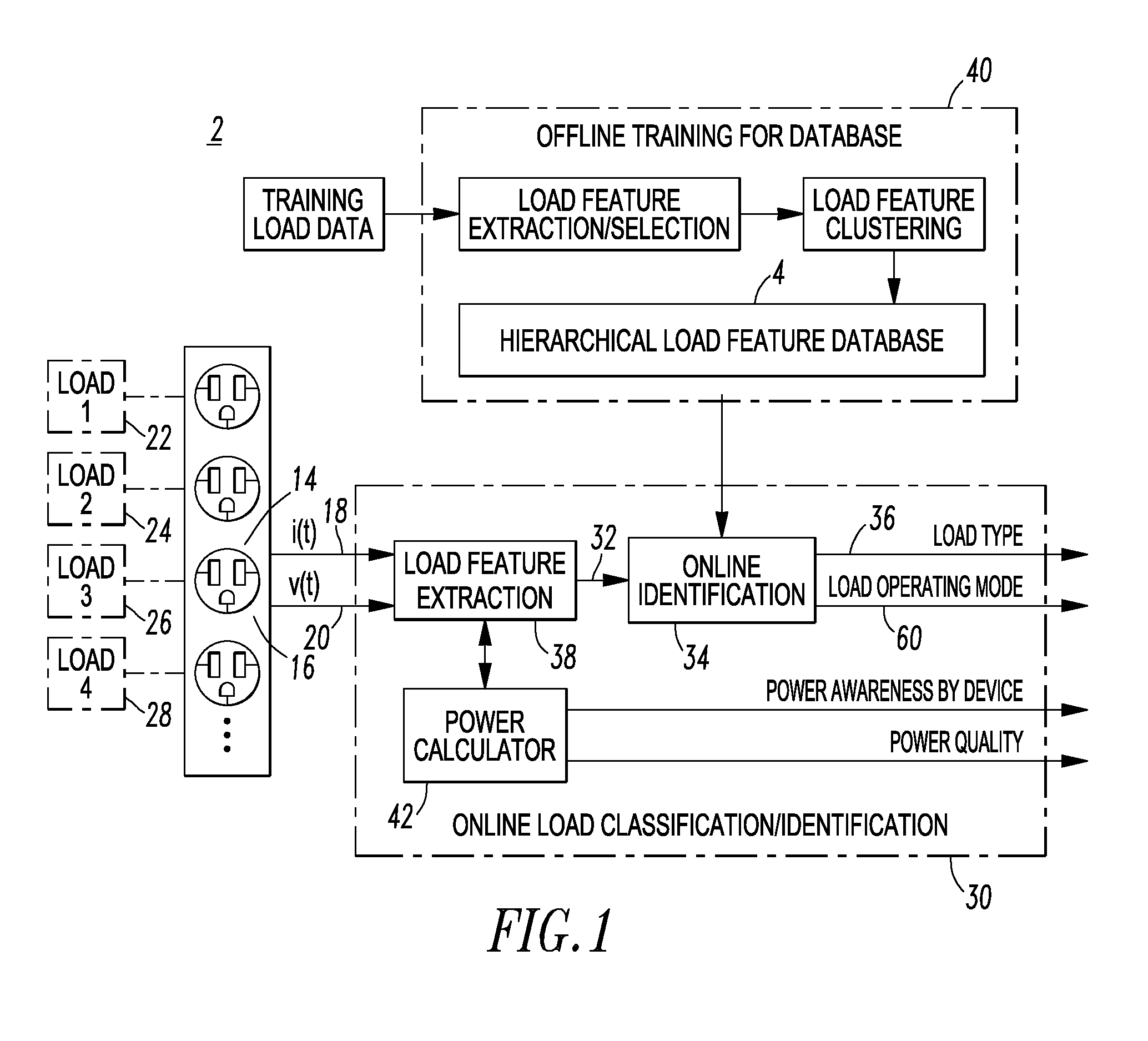
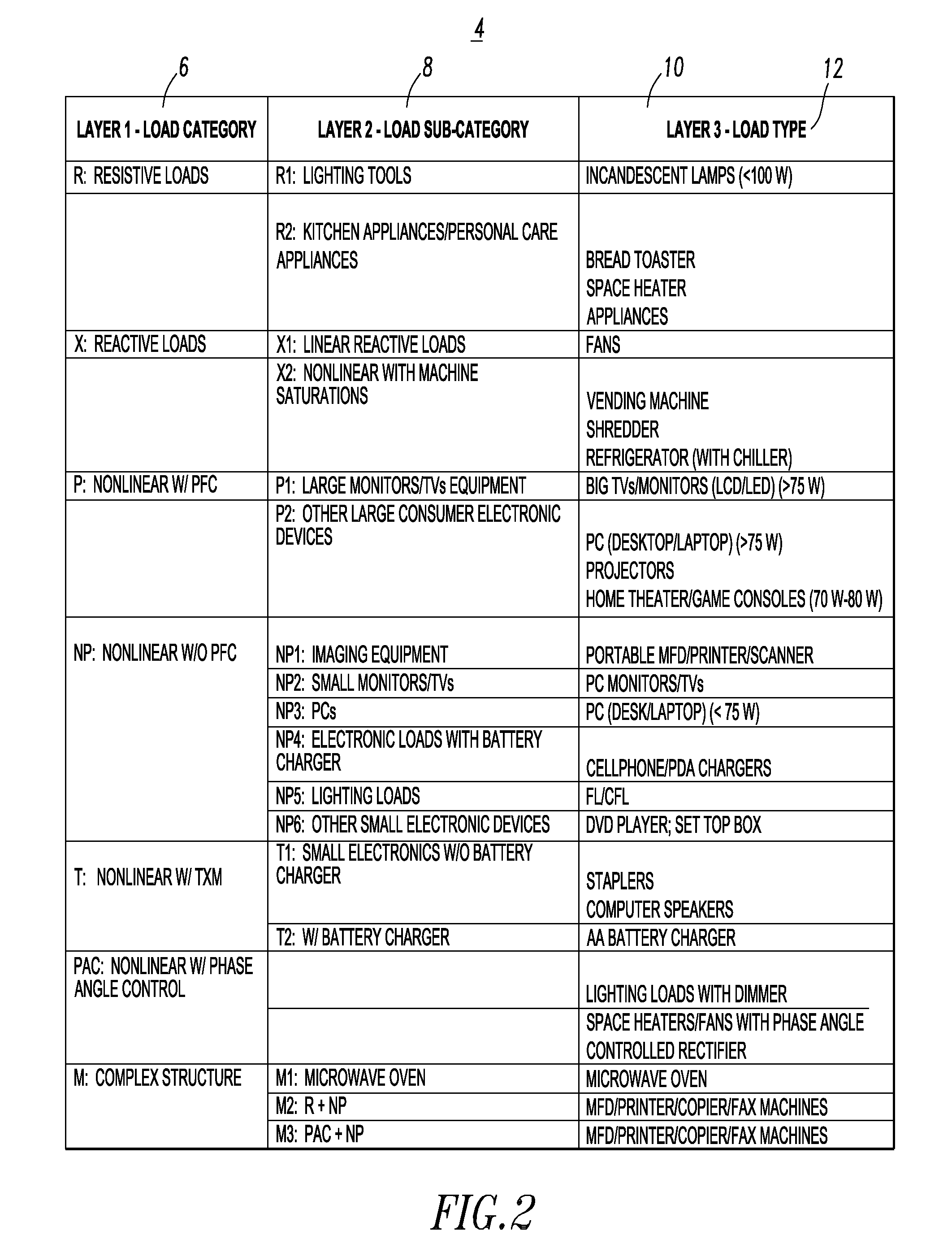
System and method employing a self-organizing map load feature database to identify electric load types of different electric loads
ActiveUS20130138651A1Digital data processing detailsSpecial data processing applicationsFeature vectorElectricity
A method identifies electric load types of a plurality of different electric loads. The method includes providing a self-organizing map load feature database of a plurality of different electric load types and a plurality of neurons, each of the load types corresponding to a number of the neurons; employing a weight vector for each of the neurons; sensing a voltage signal and a current signal for each of the loads; determining a load feature vector including at least four different load features from the sensed voltage signal and the sensed current signal for a corresponding one of the loads; and identifying by a processor one of the load types by relating the load feature vector to the neurons of the database by identifying the weight vector of one of the neurons corresponding to the one of the load types that is a minimal distance to the load feature vector.
Owner:GEORGIA TECH RES CORP +1
Cloud cluster extraction method of network information
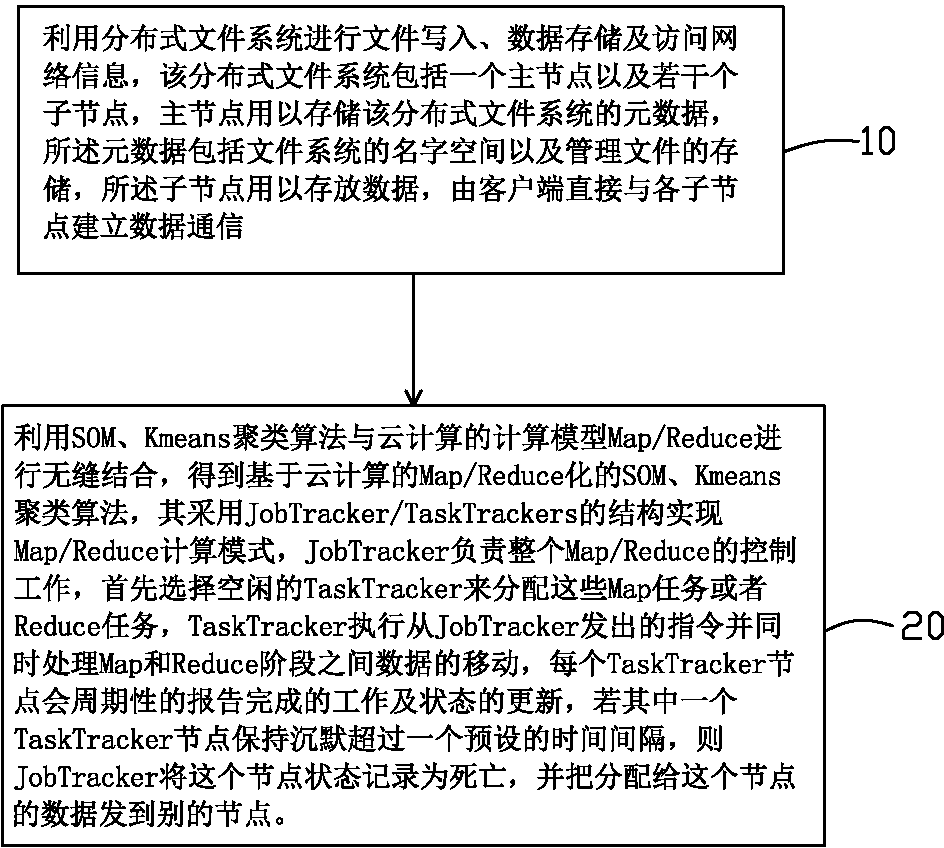
InactiveCN102999633ASolve the shortcomings of too much subjectivityImprove feature extractionTransmissionSpecial data processing applicationsPrediction algorithmsData store
The invention provides a cloud cluster extraction method of network information. The cloud cluster extraction method comprises the following steps of: performing file writing, data storage and access to network information by a distributed file system; performing seamless combination on calculation models Map / Reduce of SOM (Self-Organizing Maps), a Kmeans clustering algorithm and cloud calculation to obtain a Map / Reduce SOM and Kmeans clustering algorithm based on the cloud calculation; performing control on the whole Map / Reduce by JobTracker, and distributing Map tasks or Reduce tasks by free TaskTracker; executing an instruction sent from the JobTracker and processing movement of data between Map and Reduce phases at the same time by the TaskTracker; periodically reporting finished work and state updating by each TaskTracker node; and if one TaskTracker node keeps silent for longer than a pre-set time interval, recording that the state of the node is dead and sending data distributed to the node to the other nodes by the JobTracker. The cloud cluster extraction method of the network information has good characteristic extracting performance and overcomes the disadvantage of too strong subjectivity in the existing network flow time sequence analyzing and predicating algorithm.
Owner:BEIJING NORMAL UNIV ZHUHAI
Clustering method and system of parallelized self-organizing mapping neural network based on graphic processing unit
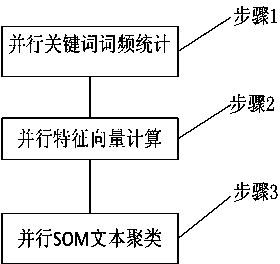
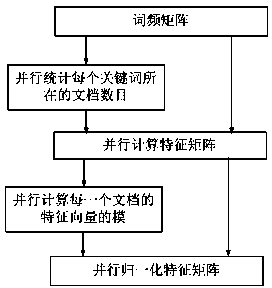
InactiveCN103488662AClustering fastFast implementation of clusteringWeb data indexingSpecial data processing applicationsData setGraphics processing unit
The invention relates to a clustering method and system of a parallelized self-organizing mapping neural network based on a graphic processing unit. Compared with the traditional serialized clustering method, the invention can realize large-scale data clustering in a faster manner by parallelization of an algorithm and a parallel processing system of the graphic processing unit. The invention mainly relates to two aspects of contents: (1) firstly, designing the clustering method of the parallelized self-organizing mapping neural network according to the characteristic of high parallelized calculating capability of the graphic processing unit, wherein the method comprises the following steps of obtaining a word-frequency matrix by carrying out parallelized statistics on the word frequency of keywords in a document, calculating feature vectors of a text by parallelization to generate a feature matrix of data sets, and obtaining a cluster structure of massive data objects by the parallelized self-organizing mapping neural network; and (2) secondly, designing a parallelized text clustering system based on a CPU / GPU cooperation framework by utilizing the complementarity of the calculating capability between the graphic processing unit (GPU) and the central processing unit (CPU).
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
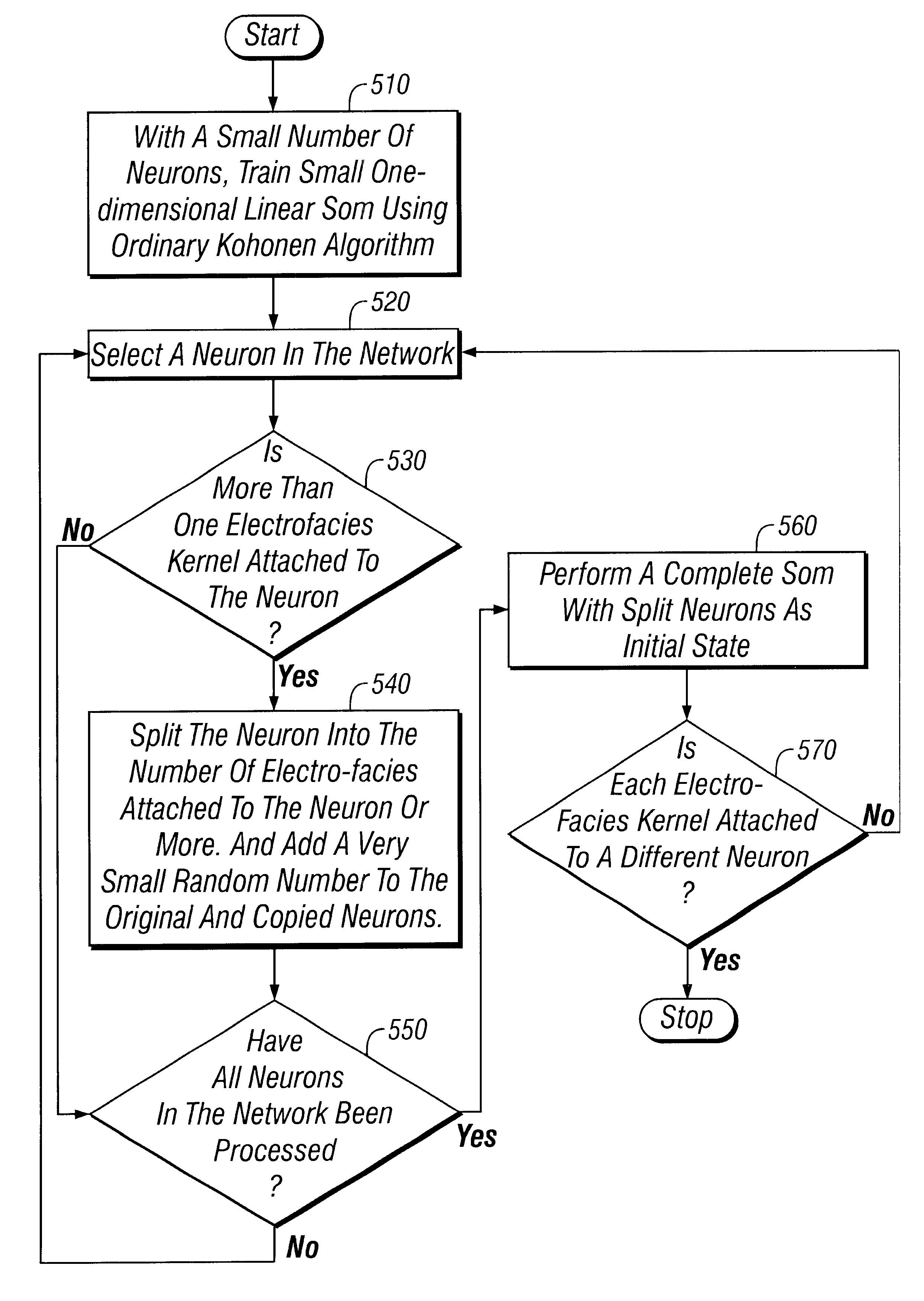
Coarse-to-fine self-organizing map for automatic electrofacies ordering
InactiveUS6477469B2Electric/magnetic detection for well-loggingDigital computer detailsElectricityOutcrop
A method for ordering electrofacies to assist in identification of mineral deposits is disclosed. Automated ordering of electrofacies allows geologists to draw inferences about the geological settings in which sediment deposit occurred without directly examining core samples or outcrops. The electrofacies order is determined by (a) training a one-dimensional linear self-organizing map to form an initial neural network that includes a plurality of neurons. The number of neurons is small in comparison to the number of electrofacies kernels (i.e., not greater than one-third the number of electrofacies kernels). (b1) A neuron is selected from the initial neural network. In the next step (b2), the processor determines if more than one electrofacies kernel is attached to the neuron. (b3) If more than one electrofacies kernel is attached to the neuron, then the neuron is split into the number of electrofacies kernels attached to the neuron. (c) Steps (b1)-(b3) are repeated until all neurons in the initial neural network have been processed. In the next step, (d) a self-organizing map is trained to form a final neural network using the split neurons in the initial neural network as initial state. (e) Steps (b1)-(d) are repeated if more than one electrofacies kernel is attached to a neuron with the initial neural network equal to the final neural network. In the last step (f), each electrofacies kernel corresponding to a neuron in the final neural network is correlated to an order number.
Owner:HALLIBURTON ENERGY SERVICES INC +1
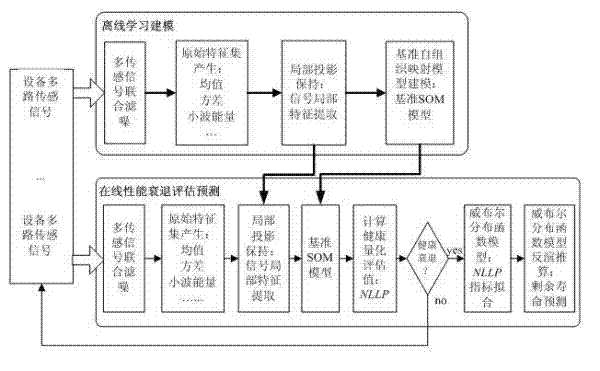
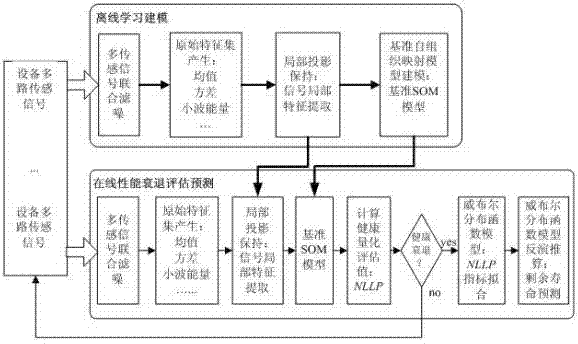
Equipment health state evaluation and recession prediction method based on multi-channel sensing signals
InactiveCN102313577AReduce dimensionalityReduce complexityMeasurement devicesSpecial data processing applicationsFiltrationEngineering
The invention relates to an equipment health state evaluation and recession prediction method based on multi-channel sensing signals. The operation steps of the method are as follows: the first step: joint noise filtration of the multiple sensing signals: adopting a multi-scale wavelet filtering algorithm to perform the joint noise filtration on the multi-channel sensing signal collected from equipment so as to improve the quality of the multiple sensing signals; the second step: generation of an original characteristic set; the third step: extraction of local characteristics of the signals; the fourth step: modeling of a reference self-organizing mapping model; and the fifth step: health quantitative evaluation and residual life prediction. By adopting the method, the quantitative evaluation and the life prediction of performance recession of the equipment can be realized, the operation reliability of the equipment can be further improved and the maintenance cost can be reduced.
Owner:SHANGHAI UNIV
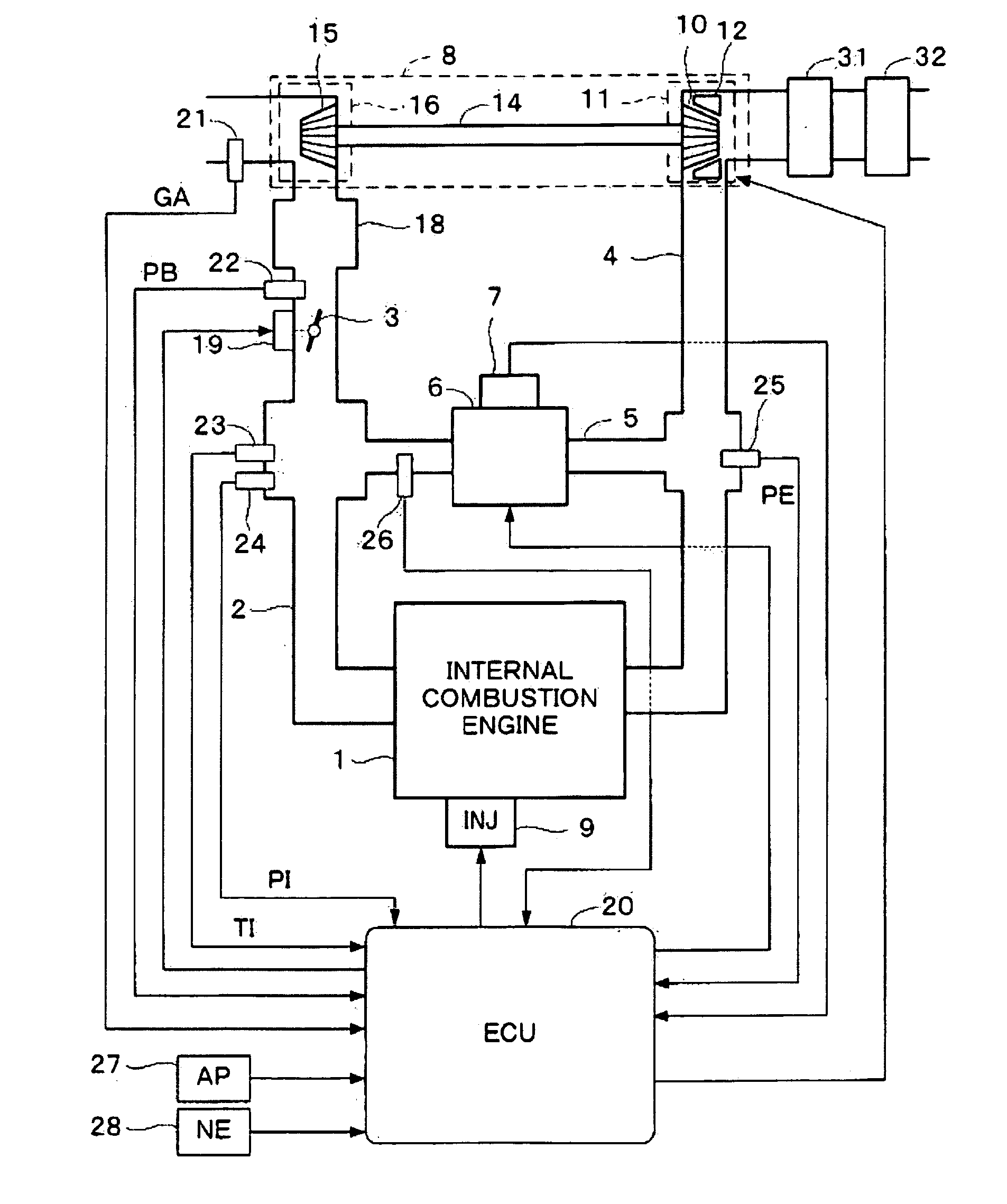
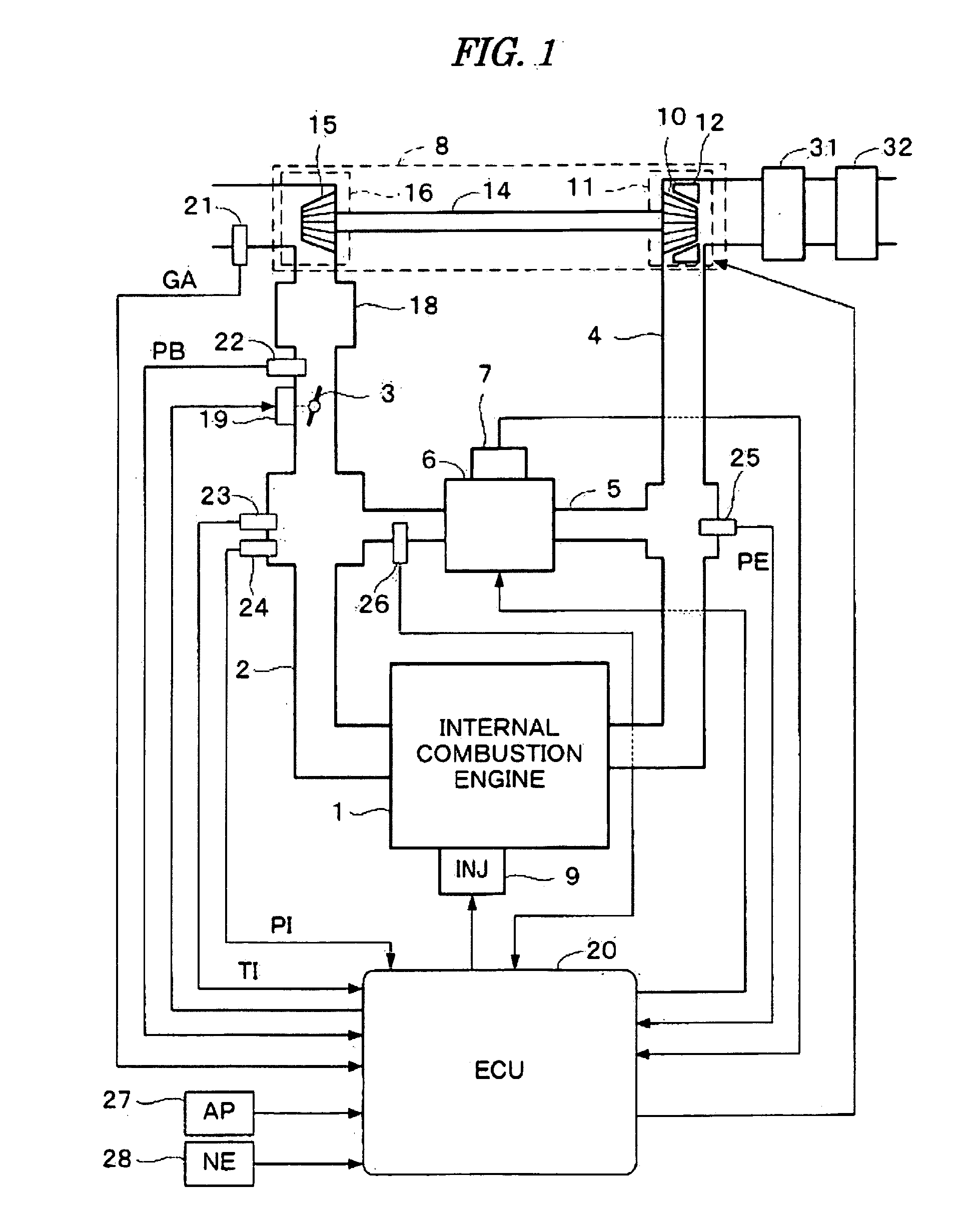
Control system for internal combustion engine
ActiveUS20090192693A1Improve robustnessAccurately determineAnalogue computers for vehiclesElectrical controlState parameterControl system
A control system for an internal combustion engine is disclosed. In the control system, an engine state parameter is calculated using a self-organizing map for calculating a predetermined output parameter according to at least one engine operating parameter which indicates an operating condition of said engine. The engine state parameter indicates an engine state which is relevant to the predetermined output parameter.
Owner:HONDA MOTOR CO LTD
Fault detection, diagnosis and performance evaluation method for redundant aileron actuator
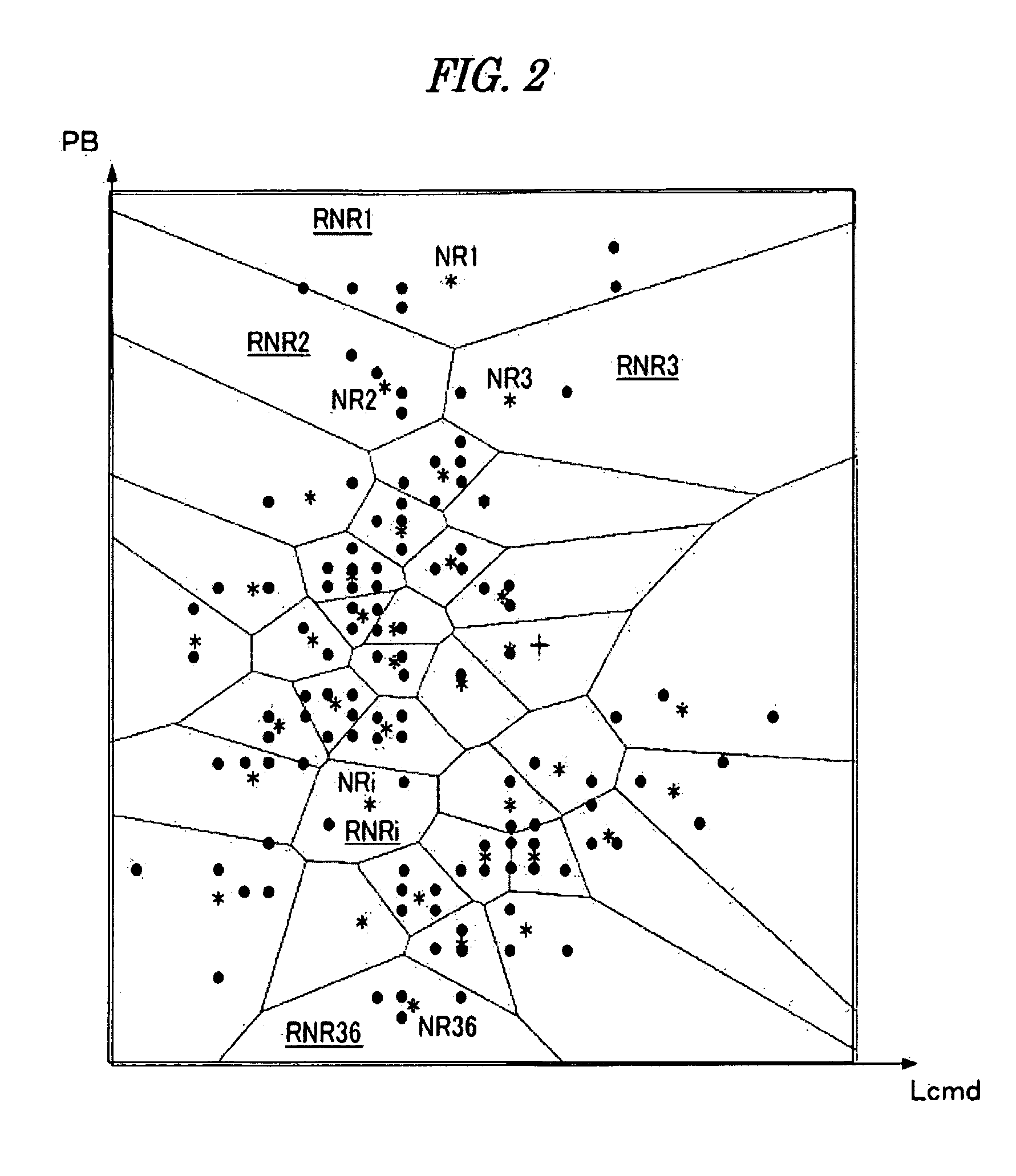
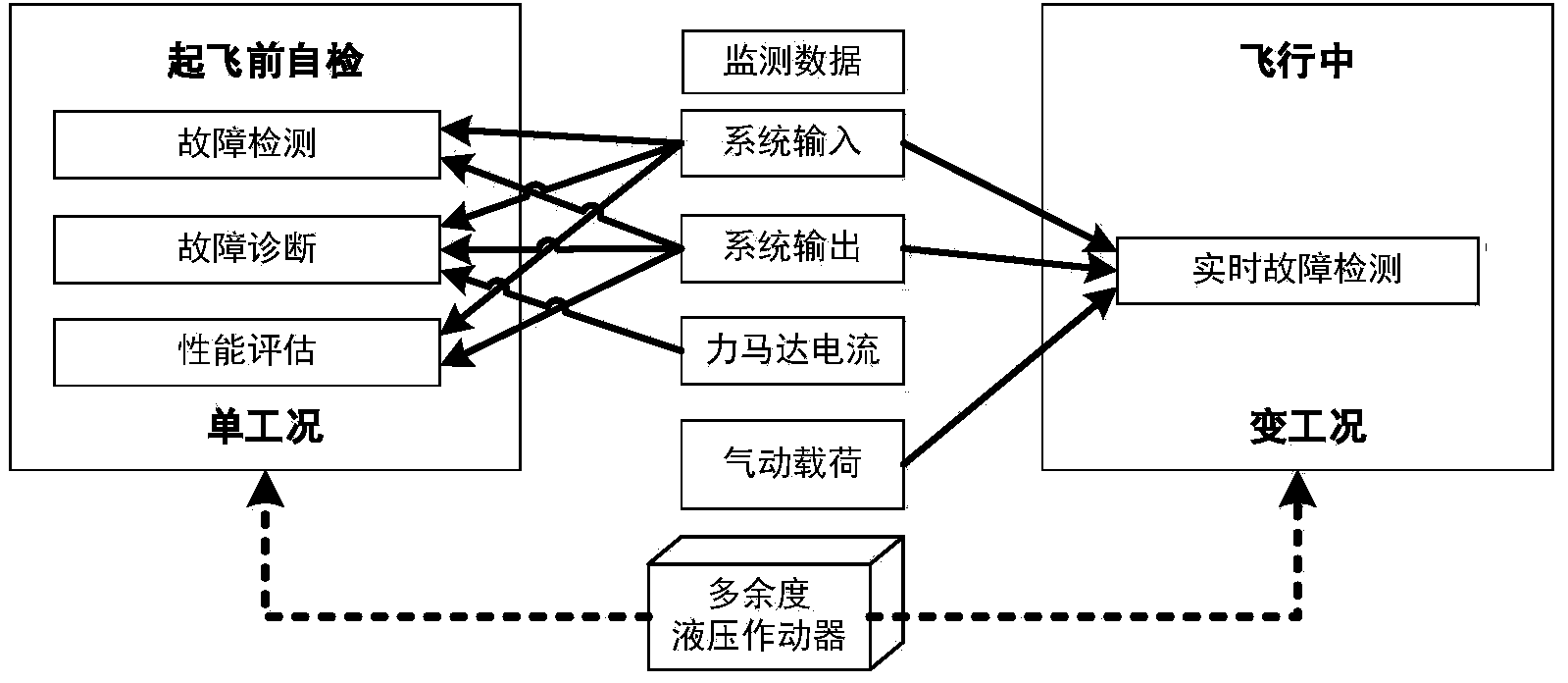
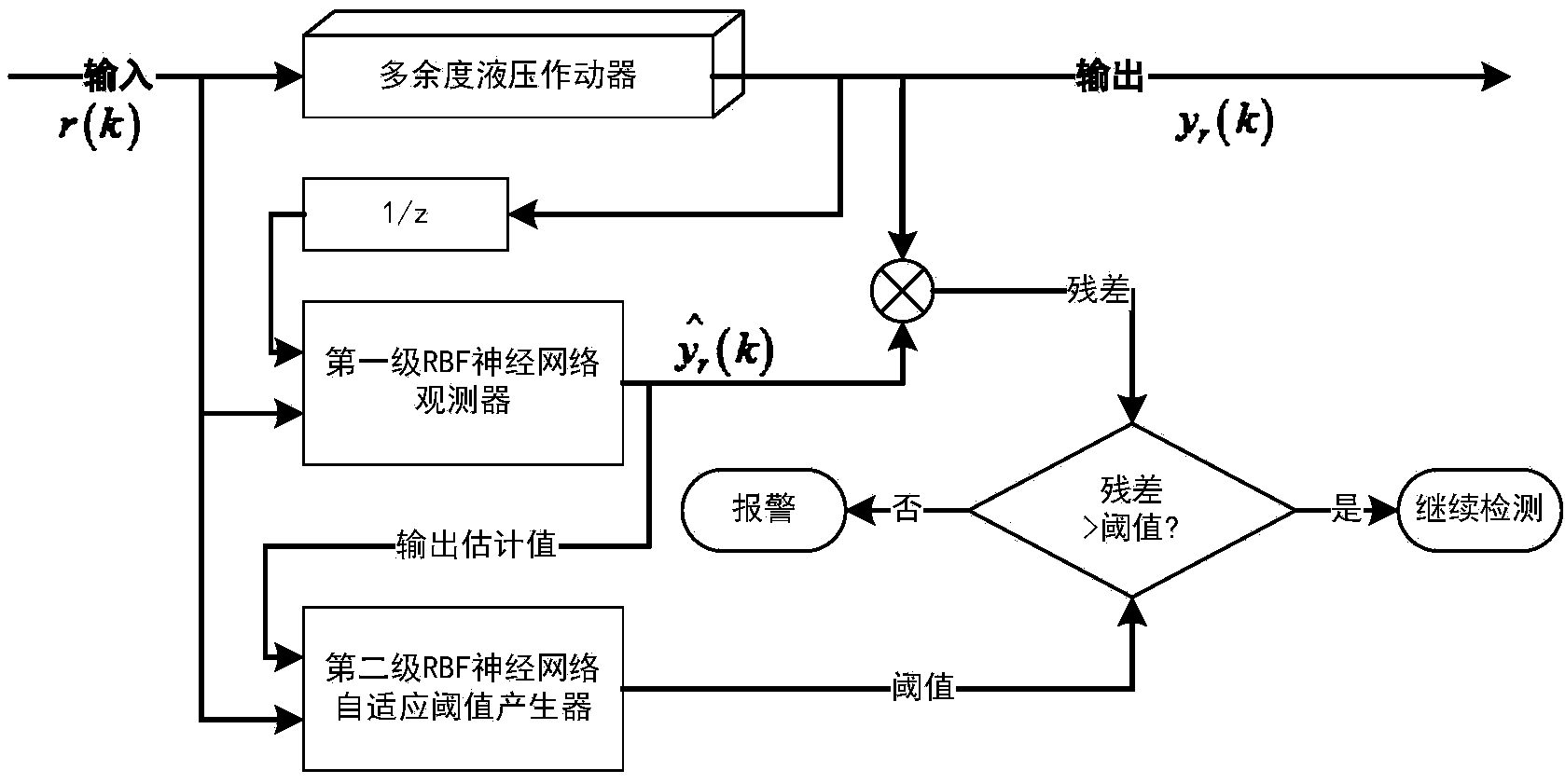
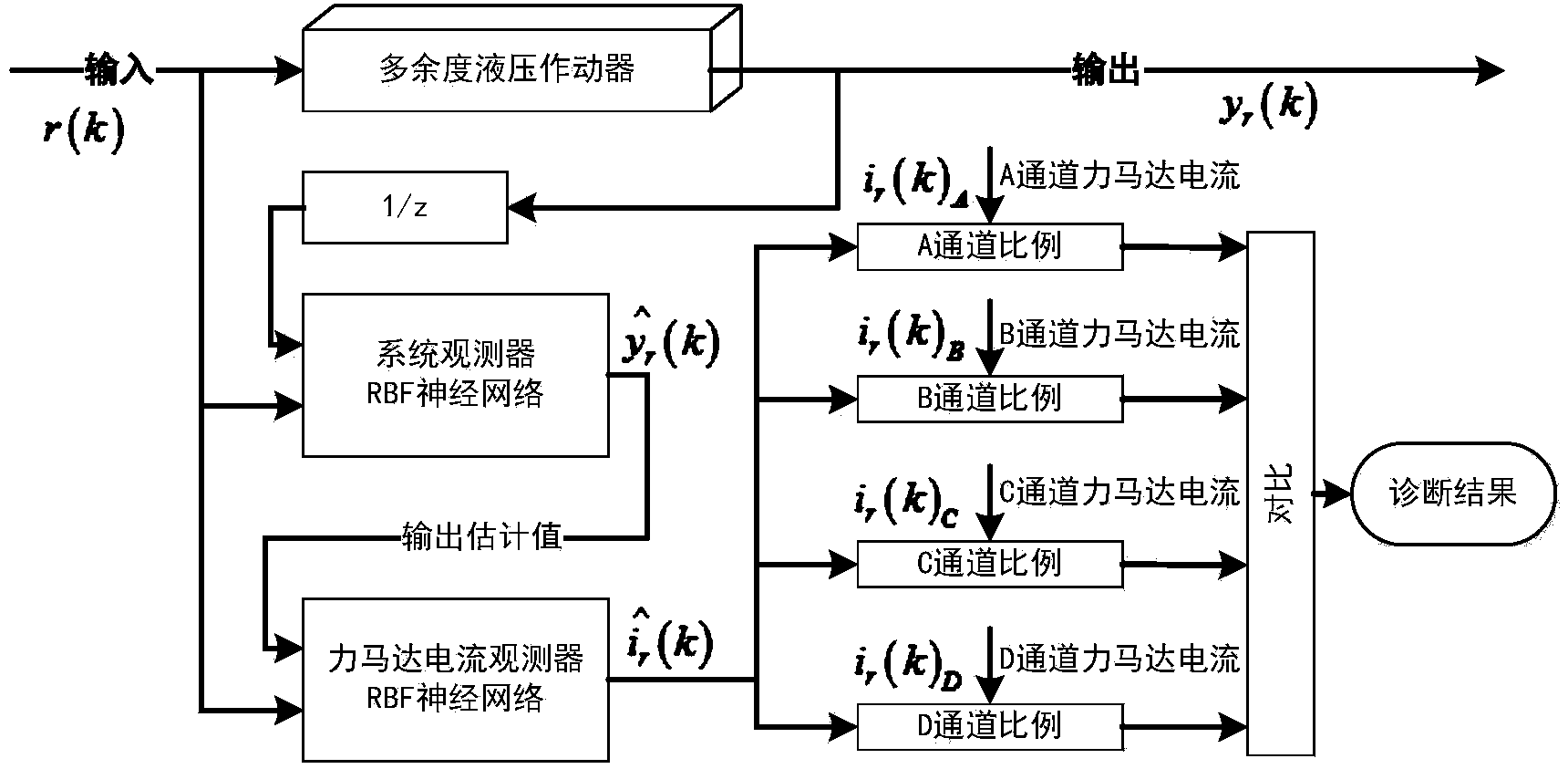
ActiveCN104390776AImprove accuracyReduce the false alarm rate of detectionMachine part testingFluid-pressure actuator testingTime domainNetwork output
The invention discloses a fault detection, diagnosis and performance evaluation method for a redundant aileron actuator. According to the method, fault detection, diagnosis, evaluation and real-time detection of the actuator are performed by means of an input order signal, an output displacement signal, a force motor current signal and aerodynamic loading data of the actuator; the fault detection is realized by a two-stage neural network, a first neural network is used as a system observer and is matched with actual output to acquire a residual error, and a second neural network outputs a self-adaptive threshold value synchronously; the fault detection is realized by the system observer and a force motor current observer; a time domain feature is extracted from a residual error signal and output to a self-organizing mapping neural network, and a minimum quantization error is acquired and normalized to a health degree, so that the actuator performance is evaluated; and on the basis of fault detection, the aerodynamic loading data is introduced, by means of a specific input order spectrum, the system observer and the neural network with the self-adaptive threshold value are trained, and the real-time fault detection is realized.
Owner:北京恒兴易康科技有限公司
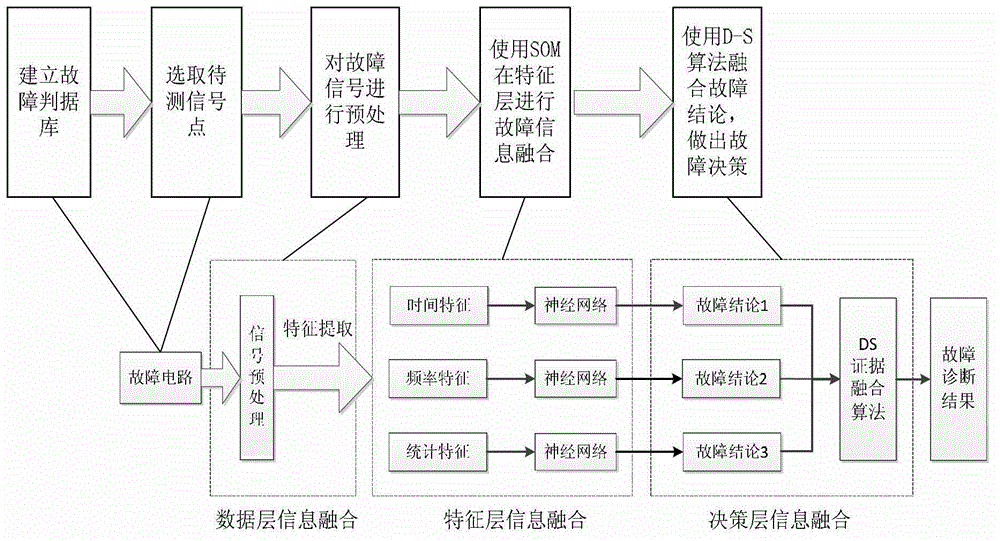
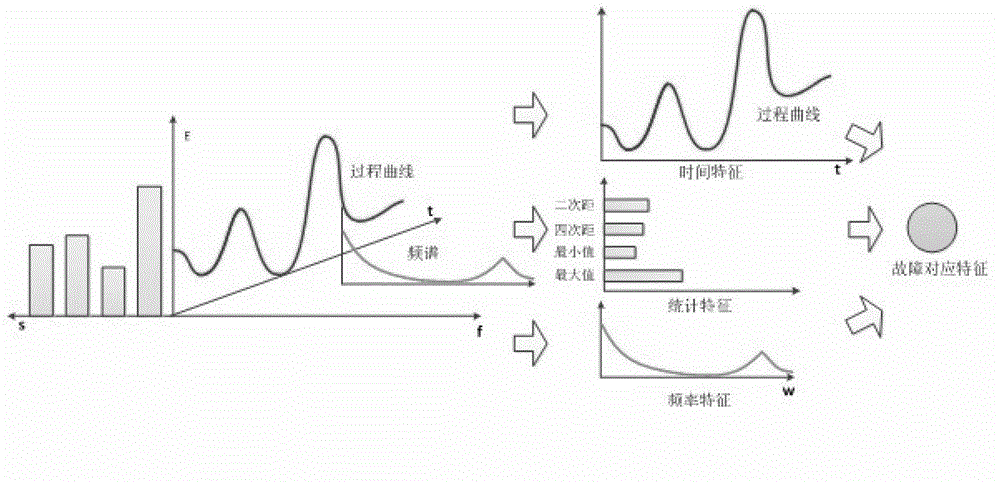
Method for fusing and diagnosing fault information of circuit of electric meter on basis of SOM (self-organized mapping) and D-S (Dempster-Shafer) theories
ActiveCN102721941AIncrease trustReduce uncertaintyElectrical measurementsDecision takingSelf-organizing map
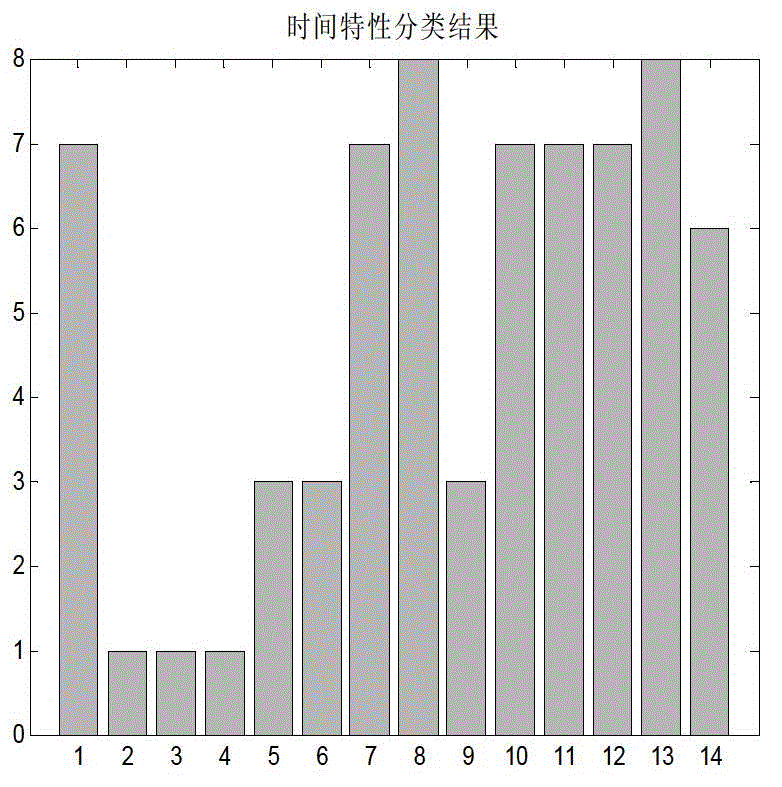
A method for fusing and diagnosing fault information of a circuit of an electric meter on the basis of SOM (self-organized mapping) and D-S (Dempster-Shafer) theories includes firstly, creating a fault mode set for the faulty circuit according to circuit analysis of the faulty circuit of the electric energy meter and fault modes specified by GJB299C; secondly, selecting to-be-observed fault signal points corresponding to fault modes in the set according to the fault mode set created in the first step and using the to-be-observed fault signal points as test points for functions and states of the circuit; thirdly, preprocessing fault signals acquired at the fault signal points selected in the second step; fourthly, fusing fault information by the aid of the SOM theory, outputting fault conclusions, selecting 70% of data for training and selecting 30% of the data for testing; and fifthly, fusing the fault conclusions by the aid of the D-S theory and making a decision for faults. By the aid of the method, confidence degree of a fault diagnostic result is further increased, integral uncertainty caused by errors is reduced, accuracy of fault diagnosis is greatly improved, and the method is an extremely important means in the field of information fusion.
Owner:苏州航大科创发展有限公司
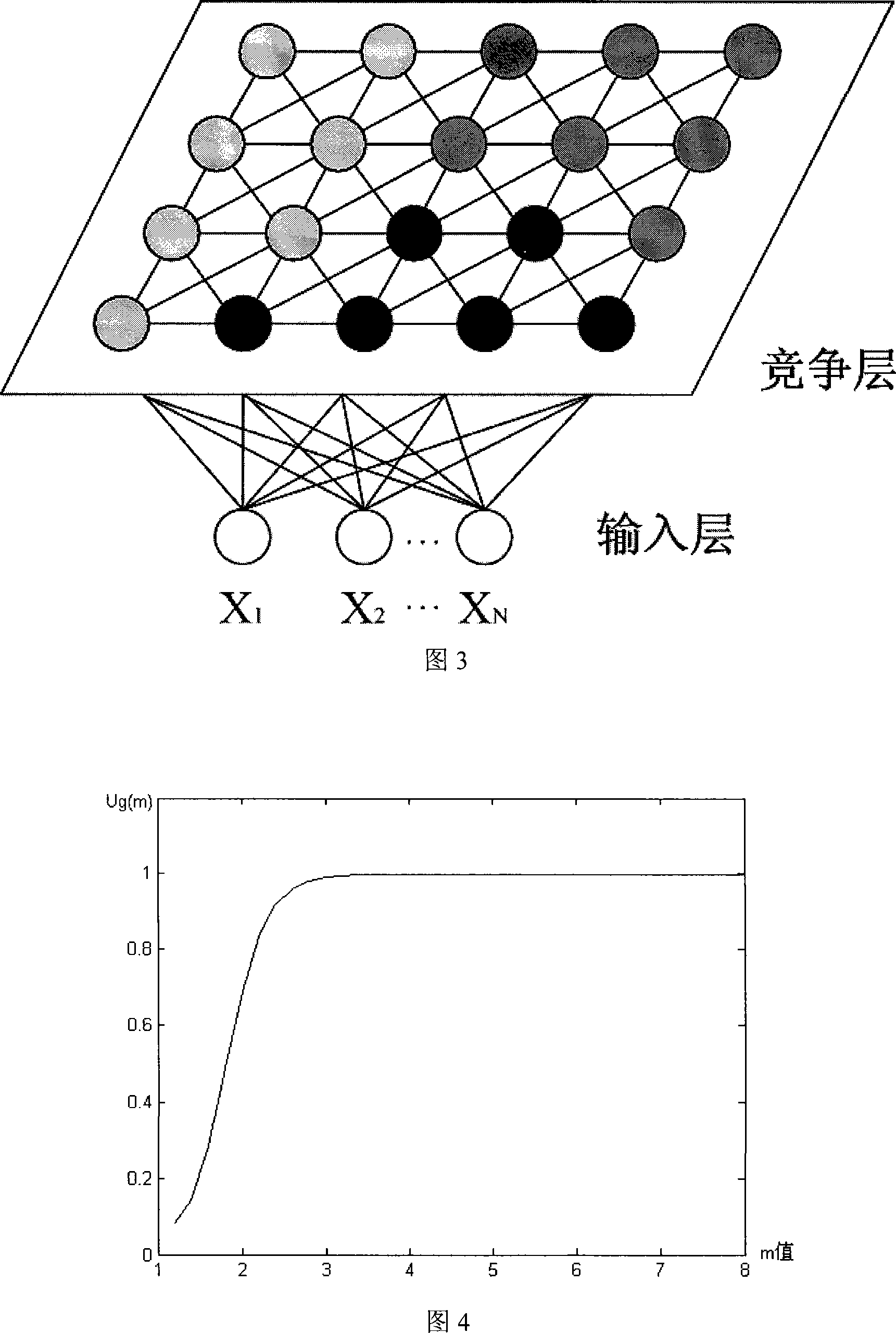
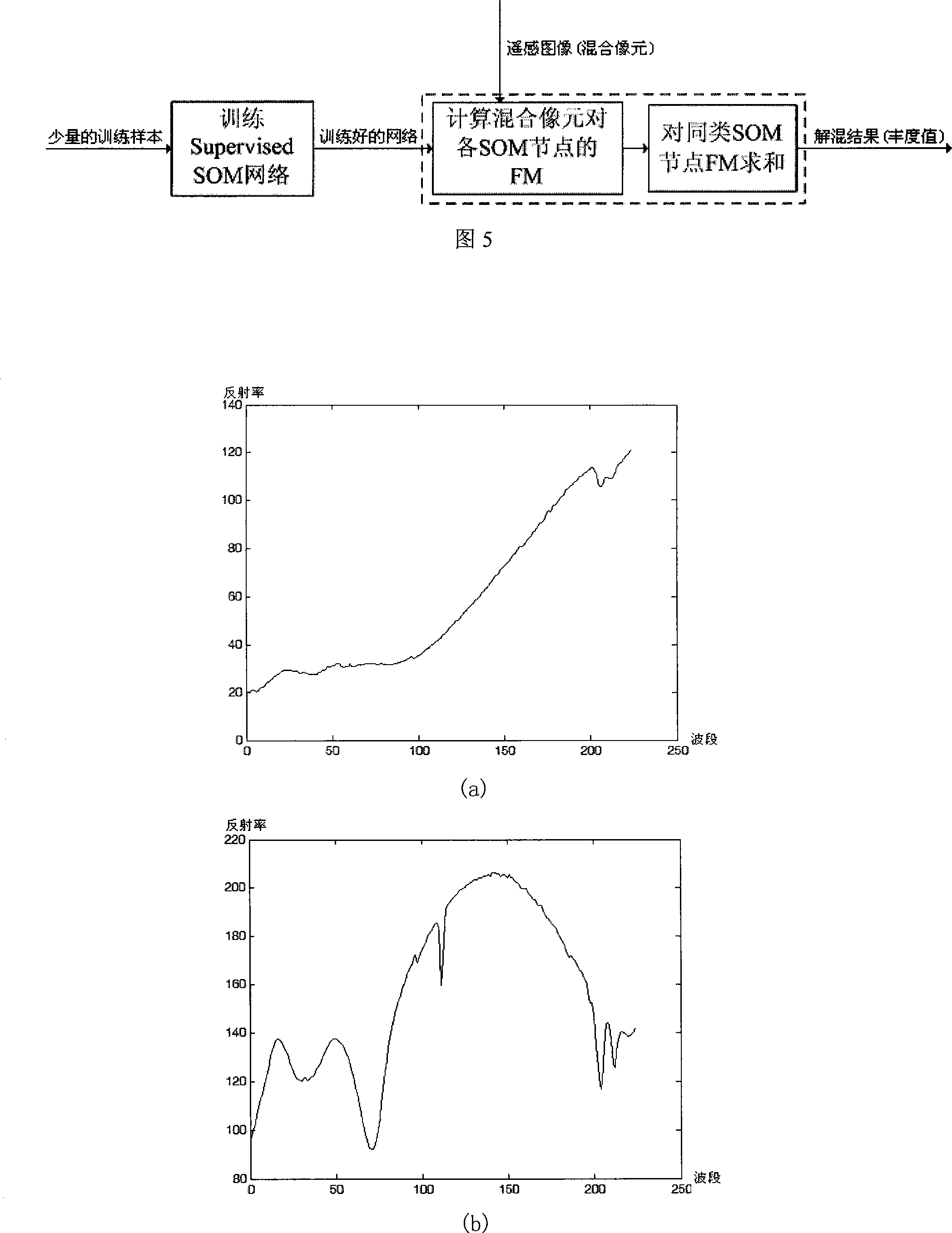
Remote sensing image mixed image element decomposition method based on self-organizing mapping neural network
InactiveCN101221662AGuaranteed robustnessGuaranteed speedImage analysisDecomposition problemDecomposition
The invention belongs to the remote sensing image processing technical field, in particular to a remote sensing image mixed pixel decomposition method based on self-organization mapping neural network. The method integrates the self-organization mapping neural network and the fuzzy grade of membership in the fuzzy theory to work out abundance values after decomposition. Simultaneously, as the self-organization mapping neural network does not has the competitive learning characteristic of an objective function, the method is free from the problem of local extremum. In addition, the invention automatically meets the two bindings required by the mixed pixel decomposition problem, wherein the two binds are respectively the binding of non-negative abundance values and the binding of the sum of the abundance values being 1. The invention has a better mixed pixel decomposition effect and a higher anti-noise capacity. The new method has a particularly important application value concerning the high-accuracy ground object separation and ground target detection and identification based on multi-spectrum and high spectrum remote sensing image.
Owner:FUDAN UNIV
Systems and Methods for Processing Data Flows
InactiveUS20160366160A1Increased complexitySignificant expenseData switching networksNeural learning methodsData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
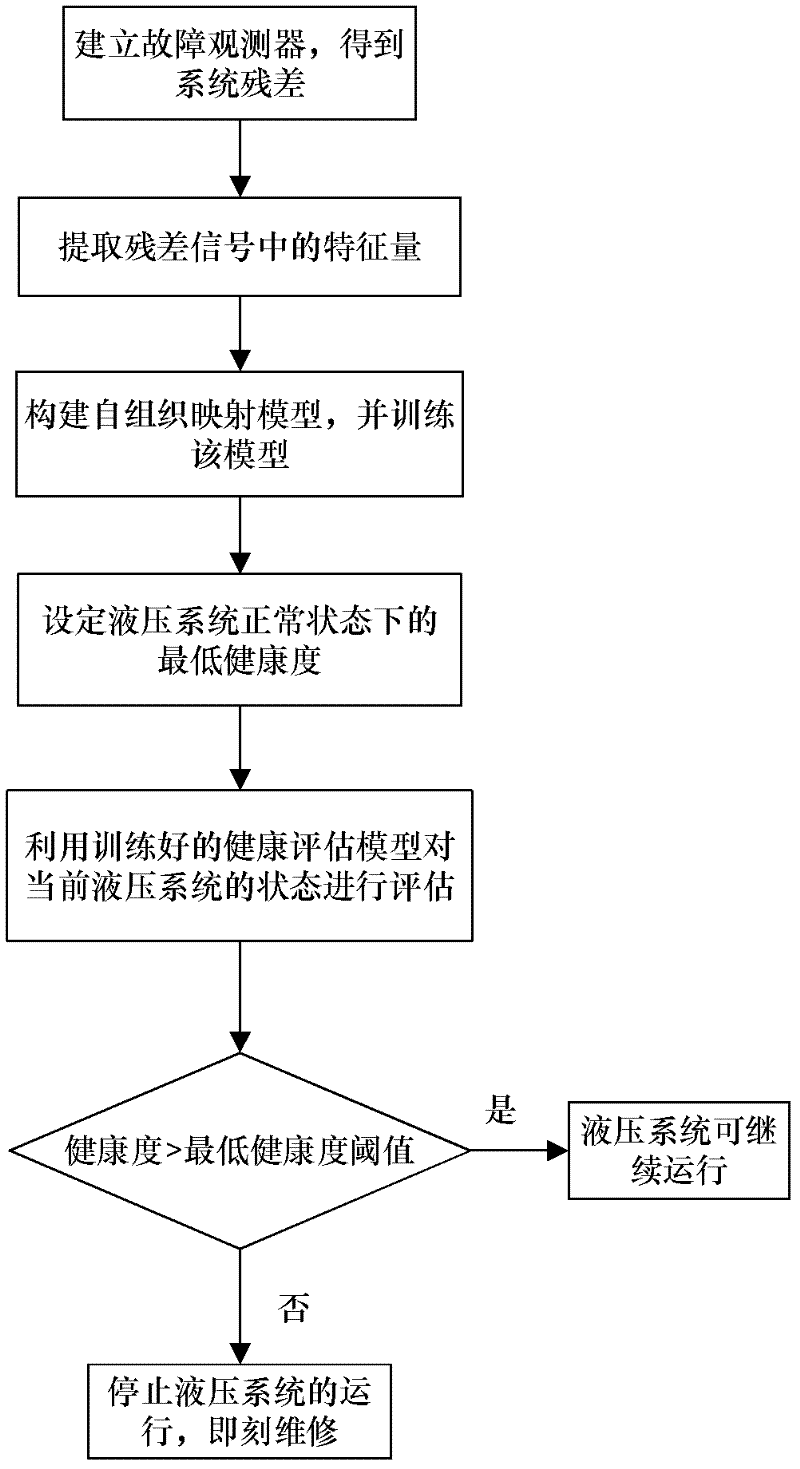
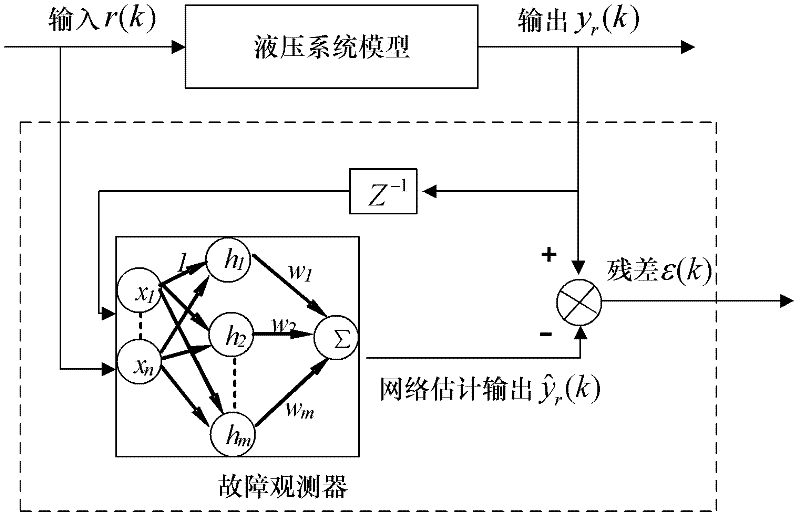
Health evaluation method for hydraulic system based on fault observer and SOM (self-organized mapping)
InactiveCN102606557AImprove robustnessEase of evaluationFluid-pressure actuator safetyFluid-pressure actuator testingTime domainControl system
The invention provides a health evaluation method for a hydraulic system based on a fault observer and SOM (self-organized mapping). The method includes: firstly, training the fault observer by the aid of input and output signals of the hydraulic system in a normal operation state to acquire residual signals in the normal state; secondly, acquiring residual signals of a certain component in a degenerate state through the fault observer by the aid of input and output signals of the degenerate component in the system; thirdly, extracting time-domain features of the residual signals in the two states and building a self-organized mapping model by the aid of residual features in the normal state; and finally, inputting residual features of the degenerate component to the self-organized mapping model to acquire the health degree of the hydraulic system in the corresponding states, and judging whether the current hydraulic system can continue running or not by the aid of the lowest health threshold value. The health evaluation method is used for evaluating health of the hydraulic control system in real time, is fine in evaluation effect, reduces dependency on historical data, and has engineering practicability.
Owner:BEIHANG UNIV
Apparatus and program for learning data and apparatus for deciding meaning of image
InactiveUS20050125368A1Improve accuracyHigh content accuracyImage analysisDigital computer detailsPattern recognitionLearning data
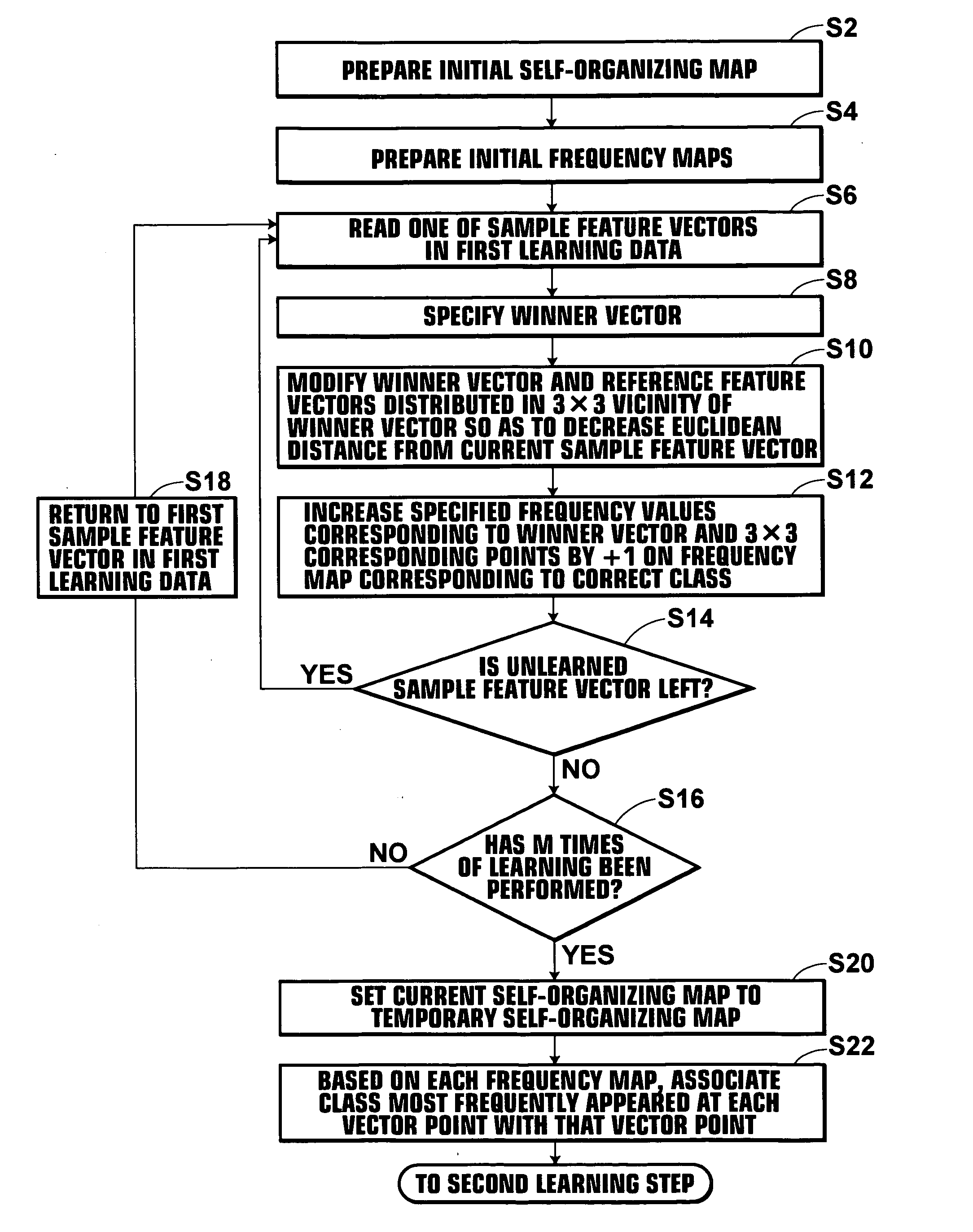
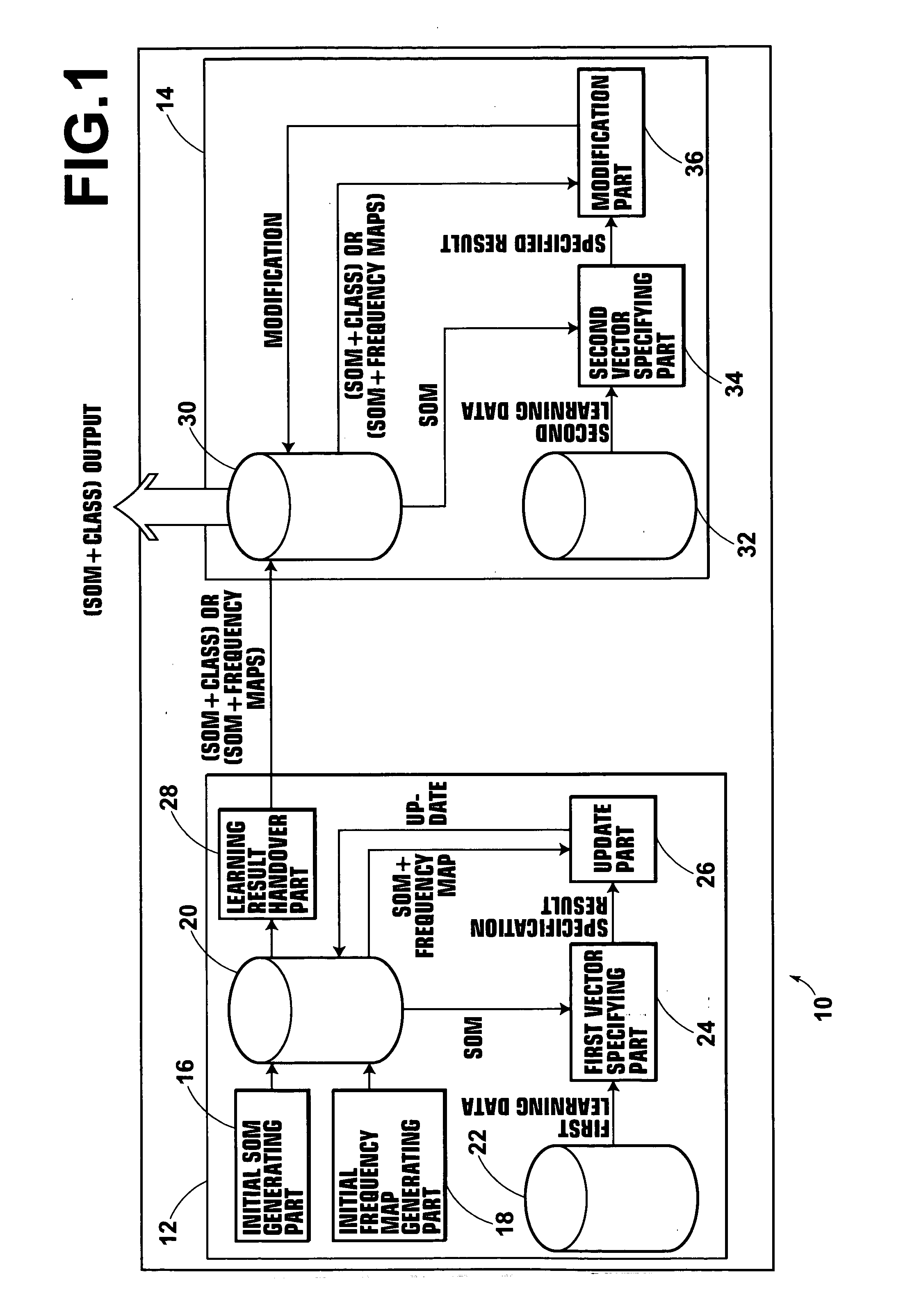
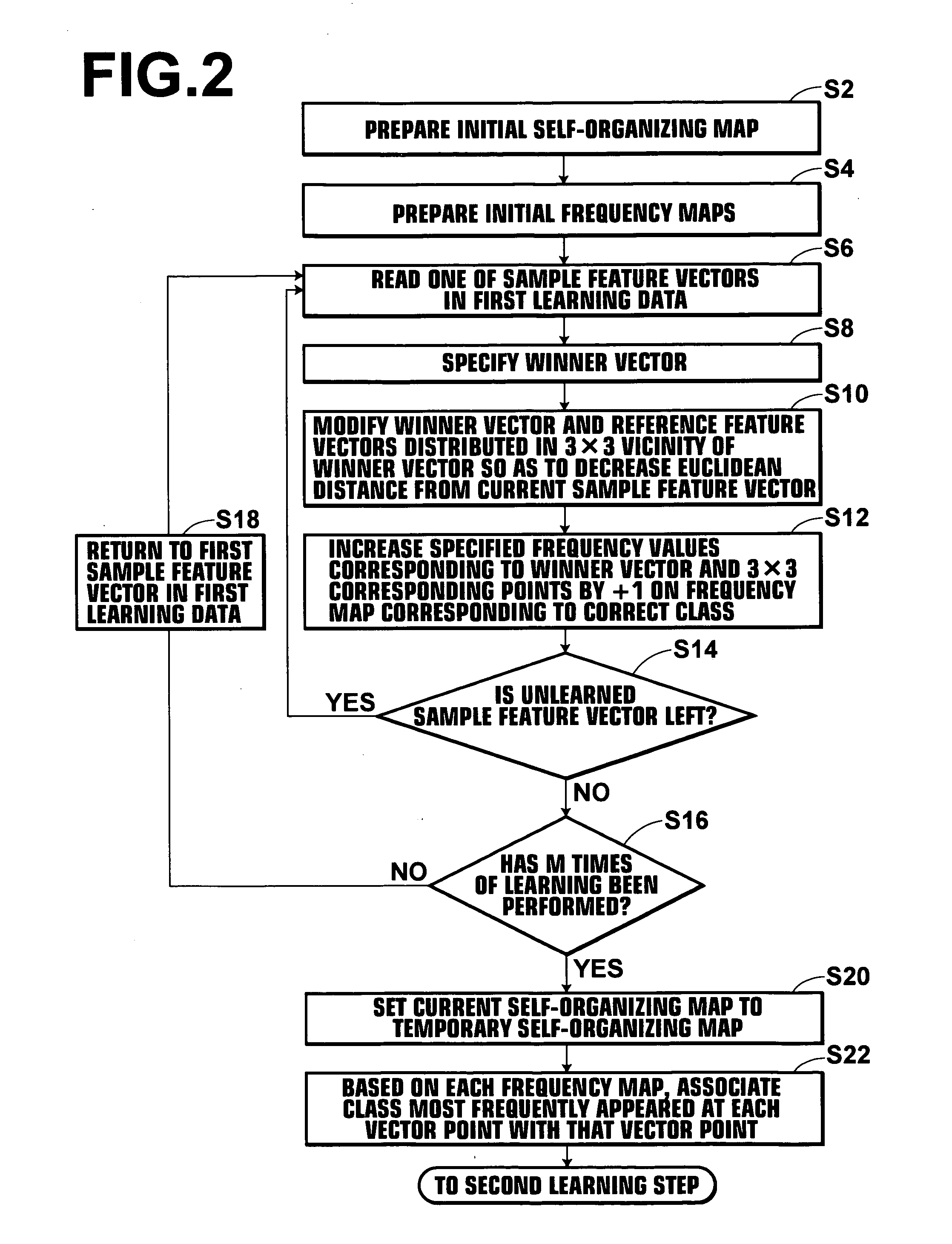
A temporary self-organizing map in which classes are associated with respective vector points is first derived by a first learning section of a data learning apparatus. Thereafter, by use of, for example, an improved method incorporating concept of vicinity learning intp learning vector quantization, a second learning section modifies the temporary self-organizing map and obtains a final self-organizing map. By use of the final self-organizing map thus derived, image meaning determining processing is performed.
Owner:FUJIFILM HLDG CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com