Personalized dual hiding method based on location-based service privacy protection
A privacy protection and location-based service technology, applied in the field of personalized dual stealth based on location-based service privacy protection, can solve problems such as security risks, security and performance bottlenecks, and query content security issues that do not consider moving objects, and achieve balanced services. Quality, the realization of personalized needs, the effect of high privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described below in conjunction with the drawings.
[0049] Reference attached figure 1 The specific steps of the present invention are as follows.
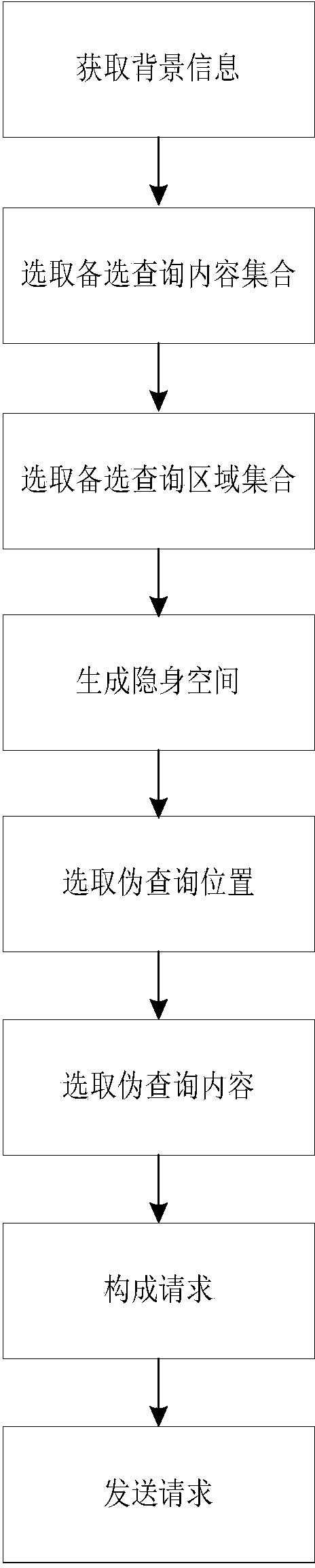
[0050] Step 1. Obtain background information.
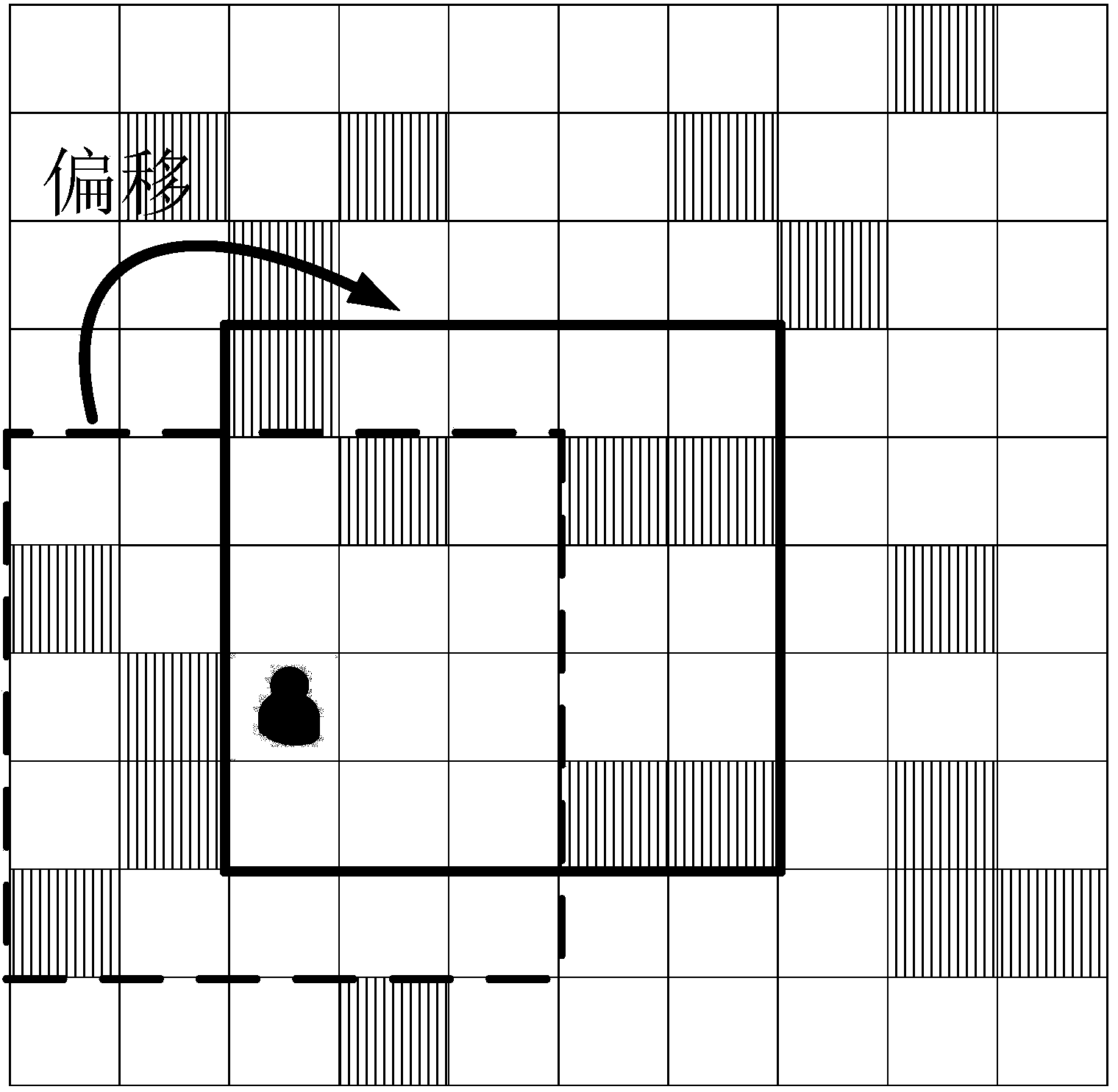
[0051] The mobile object uses the Internet to obtain the location map of the local city and the query probability of each location in the location map, and divide the location map into n areas of equal size, and each area has m types of query content , Each query content has its own query probability. The mobile object uses the GPS of the mobile device to obtain the location coordinates of the mobile object on the location map, and the location coordinates determine the area where the mobile object is located.
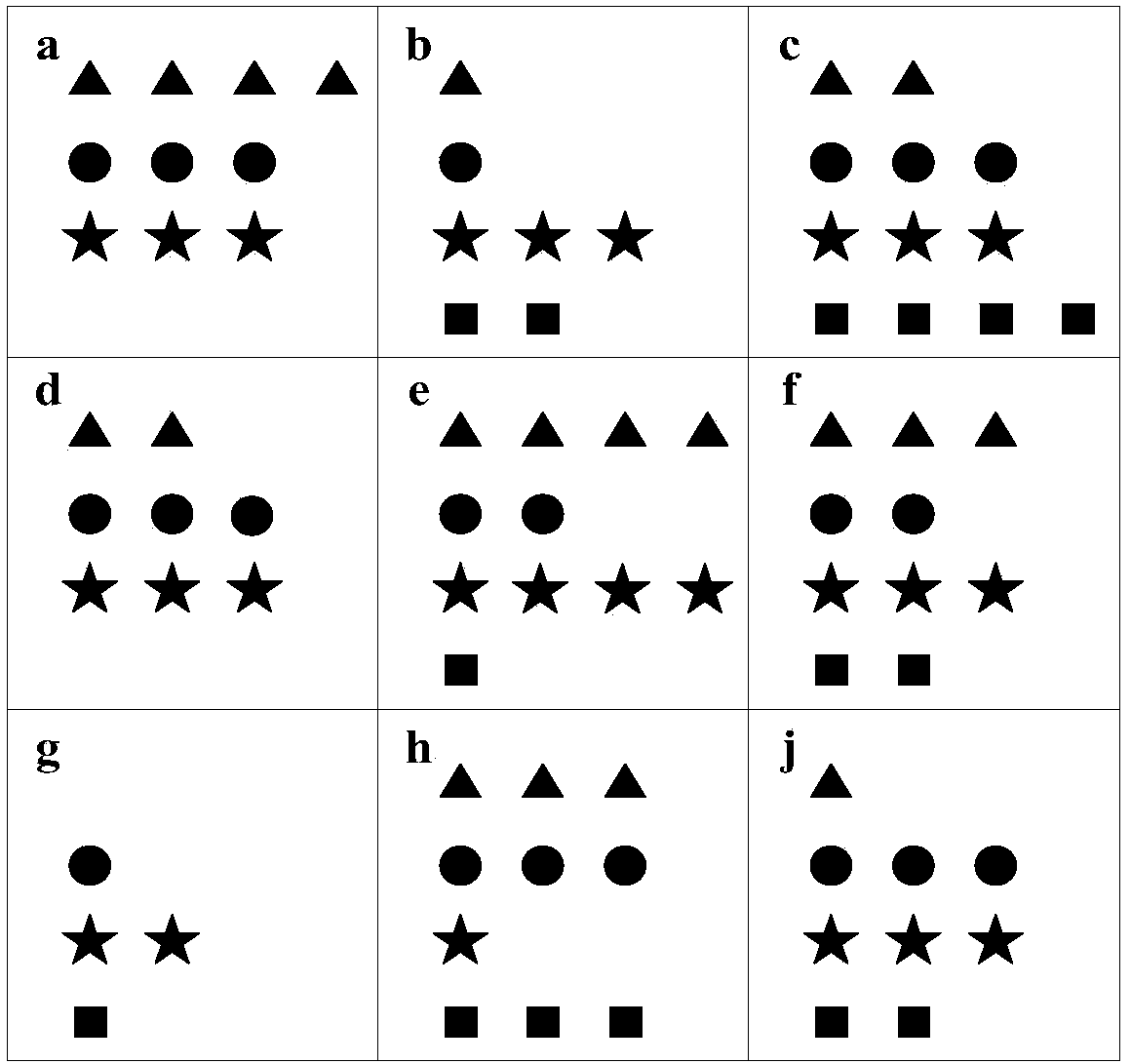
[0052] Reference attached figure 2 In the embodiment of the present invention, the location map is divided into 9 areas, figure 2 The four types of query content in each area are represented by triangles, circles, five-pointed stars, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com