A privacy protection system for transaction data based on blockchain
A privacy protection system and transaction data technology, applied in digital data protection, transmission systems, electronic digital data processing, etc., can solve the problems of high cost, lack of universality, and insufficient convenience, and achieve low cost and high matching efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
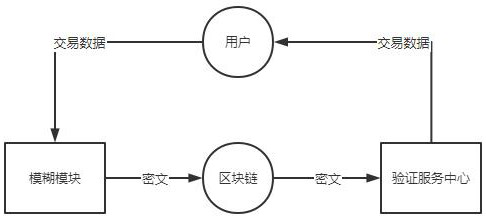
[0031] This embodiment provides a privacy protection system for transaction data based on block chain, combining figure 1 , including a verification service center and a fuzzy module, the fuzzy module is used to fuzzy the transaction data that needs to be recorded in the block chain, and the verification service center is used to help the transaction seller user and the buyer user The fuzzy transaction data in the process is restored to the original transaction data;
[0032] The process of the fuzzy processing is:
[0033] The seller’s user information in the transaction information is used as the first text, the buyer’s user information is used as the second text, and the remaining transaction information is used as the third text. The user's private key is processed to obtain a second key, processed according to the first key and the second key to obtain a third key, and the third key is used to encrypt the third text to obtain ciphertext, The ciphertext is recorded in th...
Embodiment 2
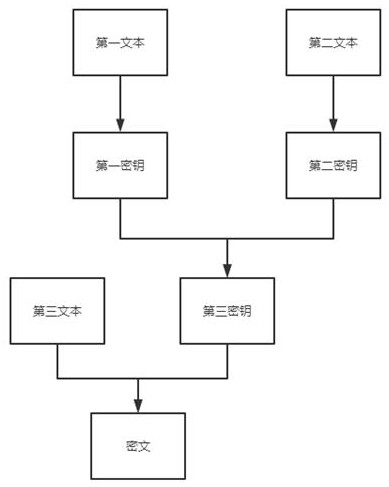
[0047] This embodiment includes all the content of Embodiment 1, combined with figure 2 , the system uses the seller user in the transaction information as the first text, the buyer user as the second text, and the remaining transaction information as the third text, and the first text is encrypted with the seller’s private key to obtain the first key, so The second text is encrypted with the buyer's private key to obtain a second key, the first key and the second key are encrypted with a fuzzy public key to obtain a third key, and the third key is used to pair the Encrypt the third text to obtain the transaction ciphertext, and record the ciphertext and the third key together in the block chain, and the ciphertext and the third key can be obtained by any user;
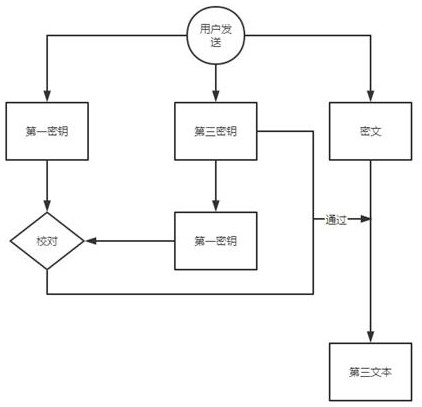
[0048] to combine image 3 , after the seller user obtains the ciphertext and the third key, the ciphertext, the third key and the first key are sent to the verification service center, and the verification service ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com