A k-anonymity-based Location and Data Privacy Protection Method in Population Intelligence Perception
A crowd-sensing, data privacy technology, applied in digital data protection, electronic digital data processing, platform integrity maintenance, etc., to resist collusion attacks and ensure ownership privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The specific implementation manner of the present invention will be described in further detail below by describing the best embodiment with reference to the accompanying drawings.
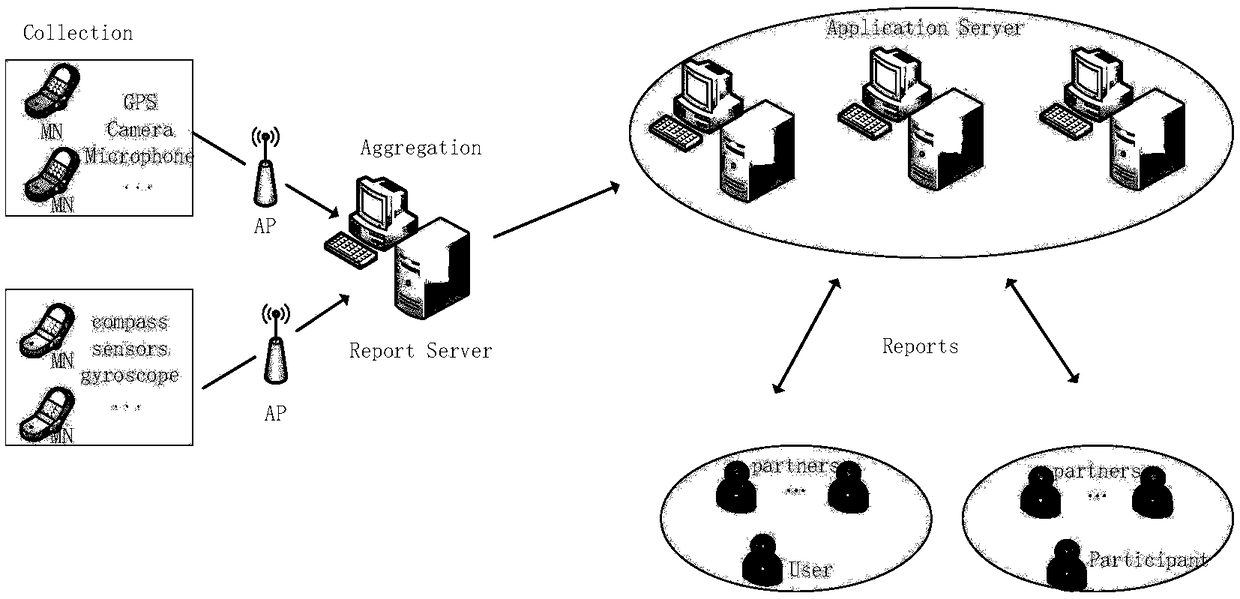
[0041] Crowd perception system: such as figure 2 As shown, a large-scale data collection system that uses a large number of mobile terminal sensing data, the crowd sensing system is composed of a crowd sensing application server in the cloud and a group of mobile terminal users.
[0042] Participants: Users added to the equivalence class are the final participants of the group intelligence sensing system.
[0043] Application server: A server that obtains the participant's perception data without exposing the participant's location and data privacy.
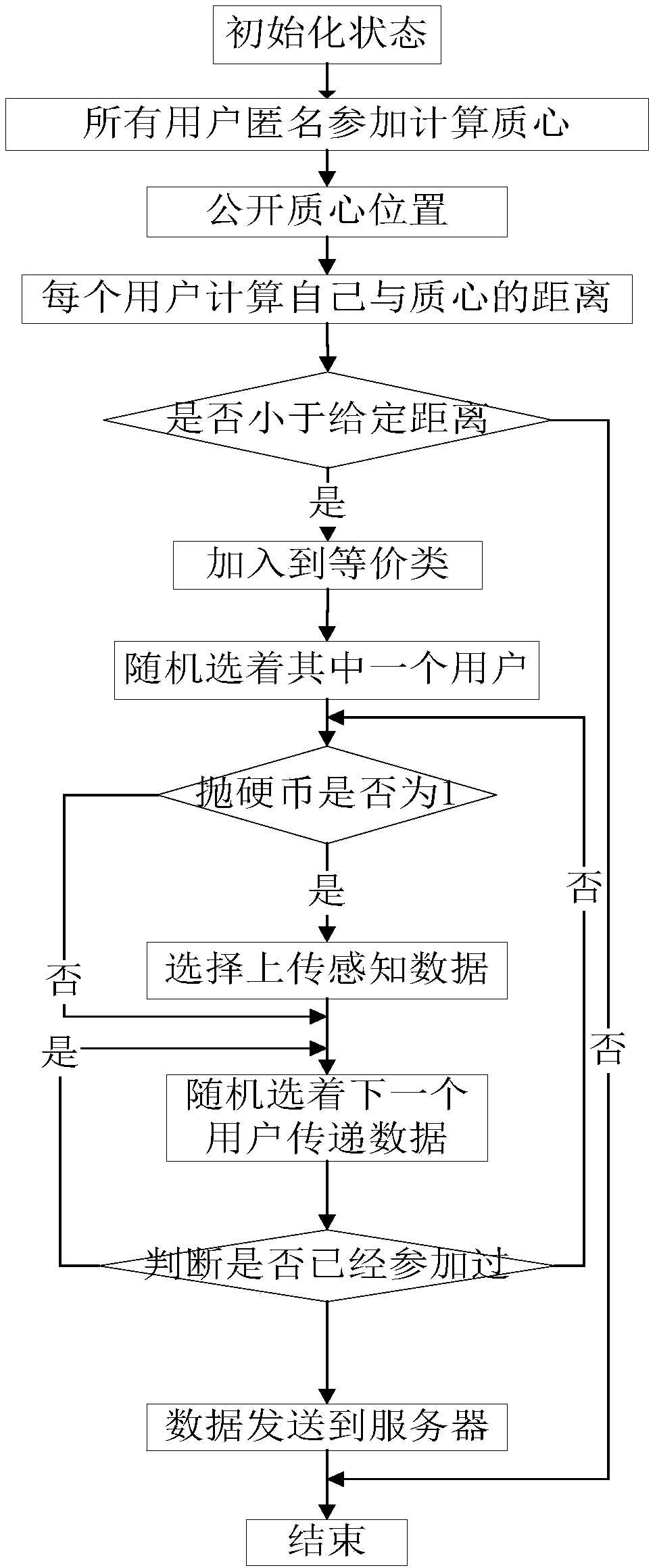
[0044] A k-anonymous location and data privacy protection method based on group intelligence in the present invention, the execution process is as follows figure 1 As shown, the steps are as follows:
[0045] (1) Construct an equivalence ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com