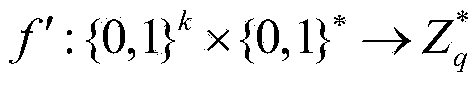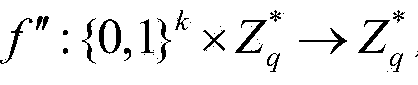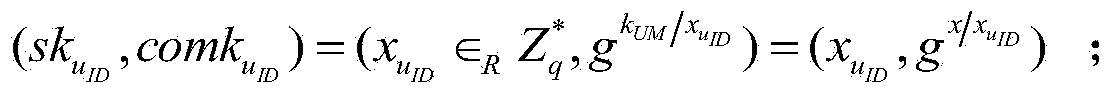Multi-user multi-keyword searchable encryption method in cloud storage
An encryption method and keyword technology, applied in the field of information security, can solve problems such as inability to realize keyword retrieval
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0073] Assuming that the file encryptor Ent wants to convert the document collection D=(D 1 ,...,D n ) is encrypted and stored in the storage server Serv, set the document D i The keyword list is W i =(w i,1 ,...,w i,m ), 1≤i≤n, n is the number of files to be stored, m is the document D i The number of keywords in w i,j , 1≤j≤m, for D i The keyword in the j-th keyword field of , the construction scheme hopes that after the document is encrypted, the keyword can be searched, and the goal of security and confidentiality is achieved. The algorithm includes seven polynomial time algorithms, which are described in detail as follows:
[0074] Step 1, system parameter initialization, namely step Init(1 k )
[0075] The algorithm is executed by the user management organization UM to initialize the system, and the security parameter k is input. Generally, k=160 or larger can be set, and the larger the k, the higher the security. The output order is the cyclic group G of prime nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com