Phrase-based searchable symmetric encryption method
A symmetric encryption and phrase technology, applied in the field of searchable encryption of phrases, can solve problems such as increasing network overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
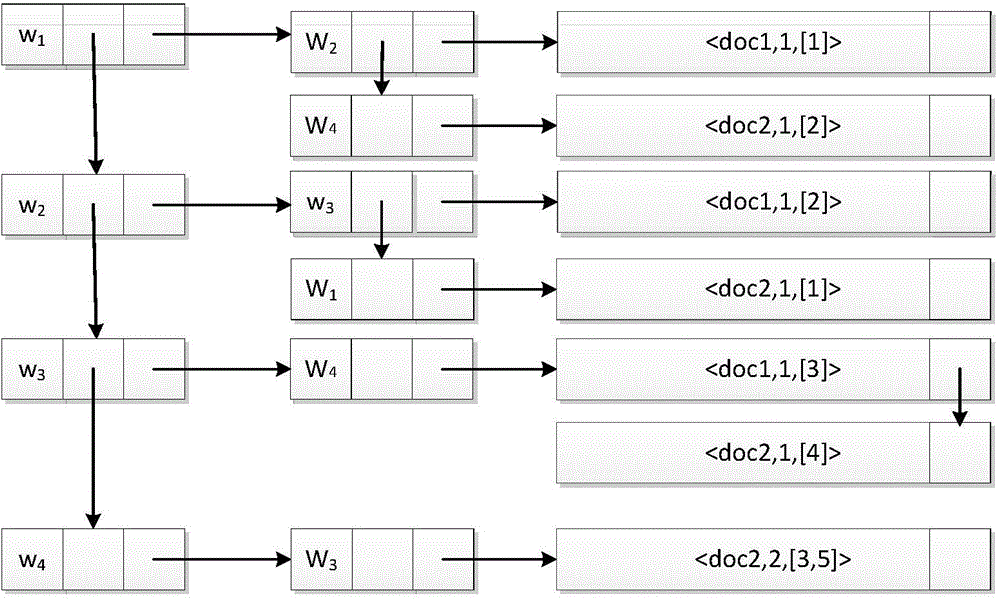
[0052] The content of file 1 to be encrypted is: w 1 ,w 2 ,w 3 ,w 4 ;The contents of file 2 to be encrypted are: w 2 ,w 1 ,w 4 ,w 3 ,w 4 ,w 3 As an example, the phrase-based searchable symmetric encryption method consists of the following steps:
[0053] 1. Client initialization
[0054] Generate global keys x, y, z; select three pseudo-random permutations ω, θ, ρ; select two pseudo-random functions g, The three pseudo-random permutations ω, θ, ρ are:
[0055] ω:{0,1} k ×{0,1} p →{0,1} p
[0056] θ:{0,1} k ×{0,1} lg(m|Δ|) →{0,1} lg(m|Δ|)
[0057] ρ : { 0,1 } k × { 0,1 } log ( m | Δ | max i { ...
Embodiment 2
[0090] The content of file 1 to be encrypted is: w 1 ,w 2 ,w 3 ,w 4 ;The contents of file 2 to be encrypted are: w 2 ,w 1 ,w 4 ,w 3 ,w 4 ,w 3 As an example, the phrase-based searchable symmetric encryption method consists of the following steps:
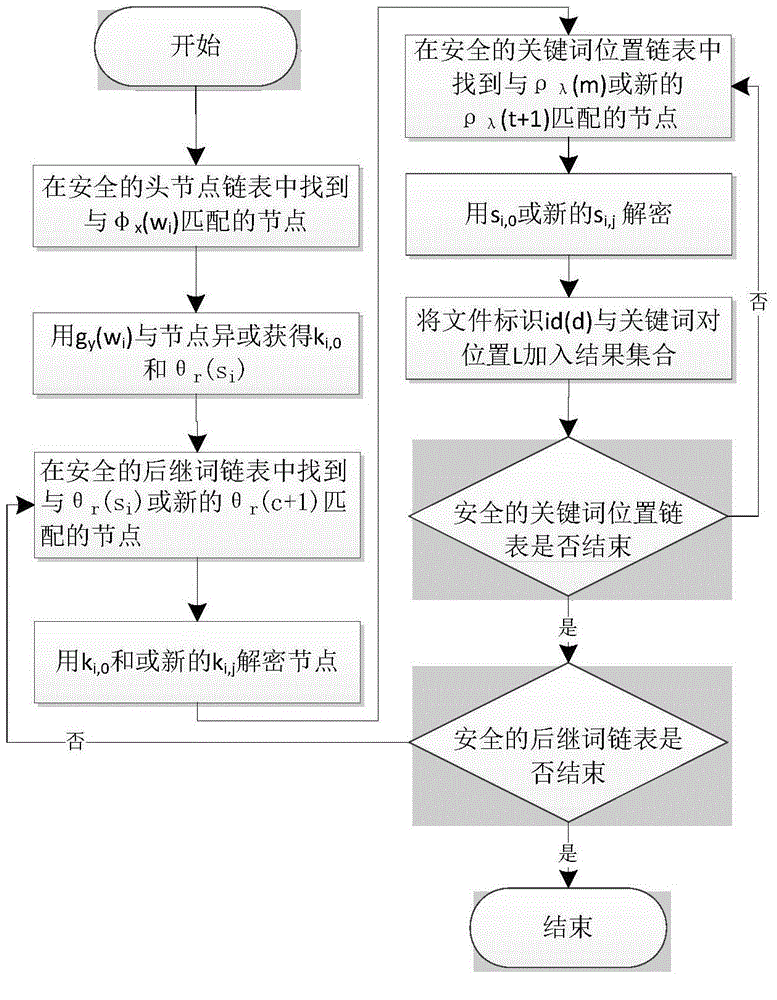
[0091] exist image 3 In this embodiment, steps 1 to 4 are the same as those in Embodiment 1. In step 5, when the cloud server executes the query and returns the result, after the cloud server receives the query trapdoor, it uses the set of triples in the query trapdoor to traverse the above security index. word query.
[0092] The double keyword query phrase of the present embodiment is {w 1 ,w 2}, the generated query trapdoor is The method of double keyword query is: use Find the corresponding node in the secure head node linked list, use g y (w 1 ) and the found node XOR operation to obtain θ r (s 1 ) and key k 1,0 , get θ r (s 1 ) to find the corresponding node in the secure successor list, and use the key...
Embodiment 3
[0094] The content of file 1 to be encrypted is: w 1 ,w 2 ,w 3 ,w 4 ;The contents of file 2 to be encrypted are: w 2 ,w 1 ,w 4 ,w 3 ,w 4 ,w 3 As an example, the phrase-based searchable symmetric encryption method consists of the following steps:
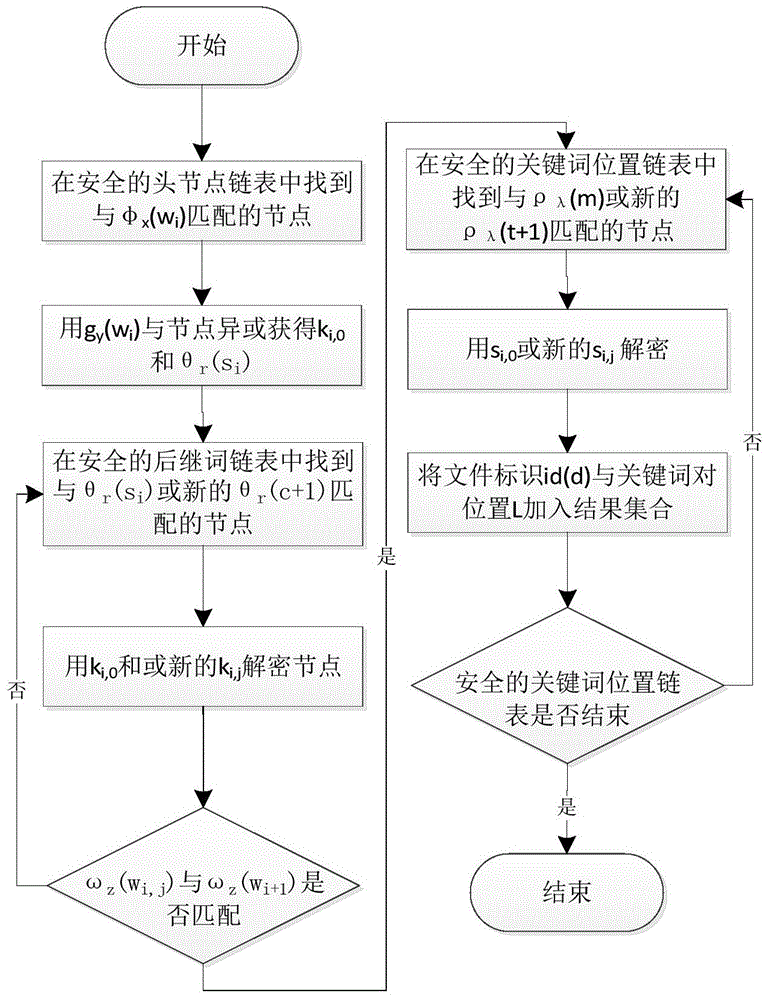
[0095] exist Figure 4 In this embodiment, steps 1 to 4 are the same as those in Embodiment 1. In step 5, when the cloud server executes the query and returns the result, after the cloud server receives the query trapdoor, it traverses the above-mentioned security index with the set of triples in the query trapdoor. The length of the query trapdoor is 3 triples, and three Keyword search.
[0096] The 3 keyword query phrases of the present embodiment are {w 1 ,w 2 ,w 3}, the generated query trapdoor is The method of querying 3 keywords is: use the first triple in the query trapdoor and the second triplet Perform a double-keyword query, and subtract 0 from all the position information obtained, and the result is ((i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com