Similar sub-image inquiring method and system for protecting privacy under cloud computing environment
A cloud computing environment, privacy protection technology, applied in the field of information security, can solve the problems of infringing the privacy of data owners, infringing the privacy of users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
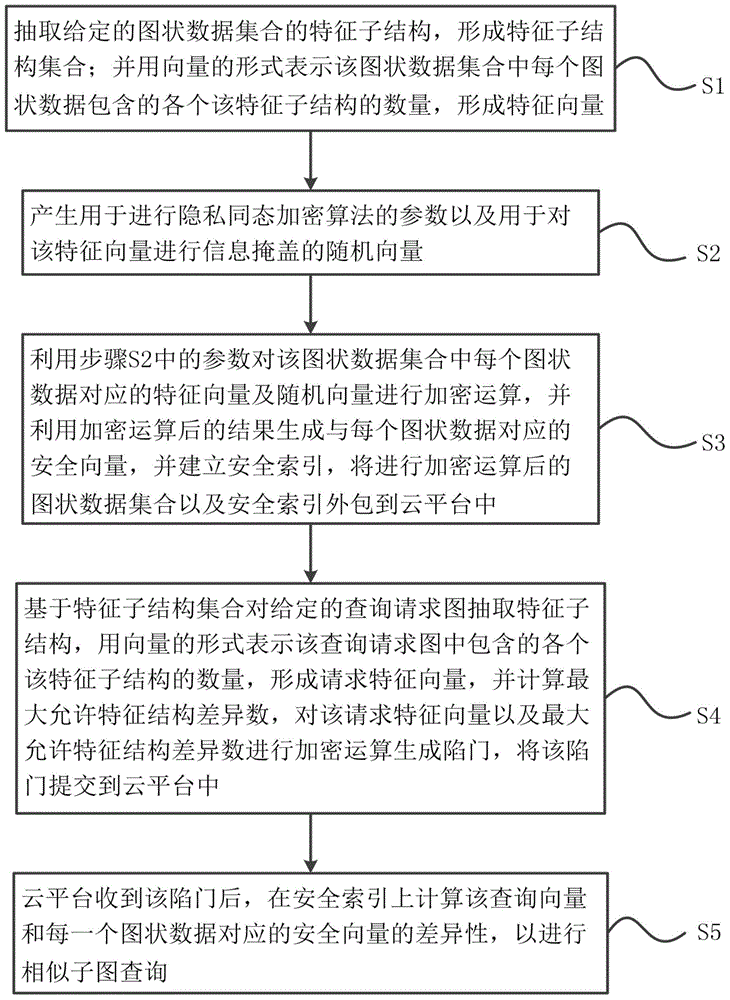
[0046] like figure 1 As shown, the present invention provides a similar subgraph query method for protecting privacy under a cloud computing environment, including:
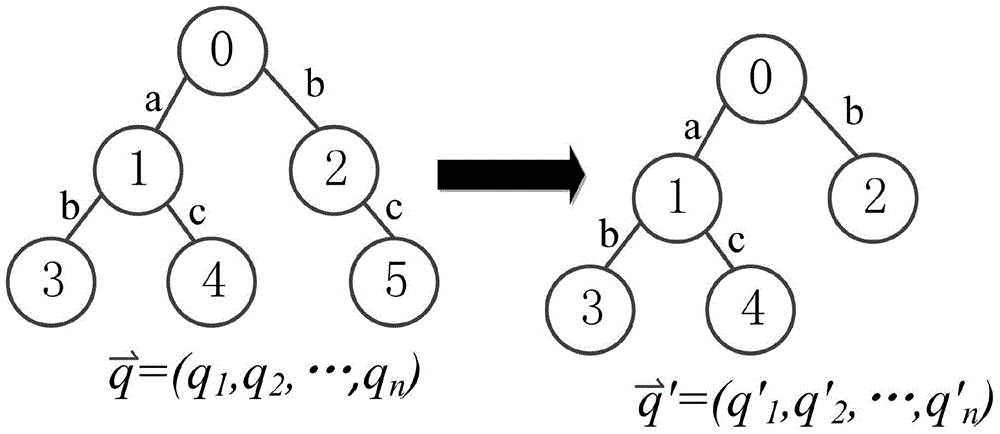
[0047] S1. Extract the feature substructure of a given graph data set to form a feature substructure set; and express the number of each feature substructure contained in each graph data in the graph data set in the form of a vector to form a feature vector ;
[0048] S2. Generate parameters for the privacy homomorphic encryption algorithm and a random vector for information masking of the feature vector;
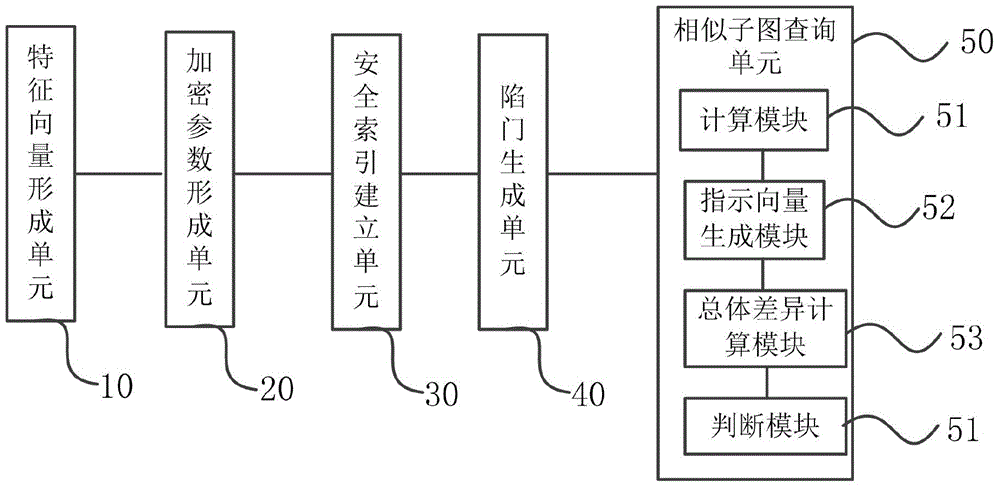
[0049] S3. Use the parameters in step S2 to perform an encryption operation on the feature vector corresponding to each graph data in the graph data set and the random vector, and use the result of the encryption operation to generate a security code corresponding to each graph data. Vector, and establish a security index, and outsource the encrypted graphic data set and the security index to the cloud platf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com