Validation method and validation device of chip with secure booting function
A technology for secure startup and verification devices, which is applied in the field of communication, can solve problems such as easy leakage, network theft to attack the operator's network, security loopholes in the security startup program, etc., and achieve the effect of ensuring network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
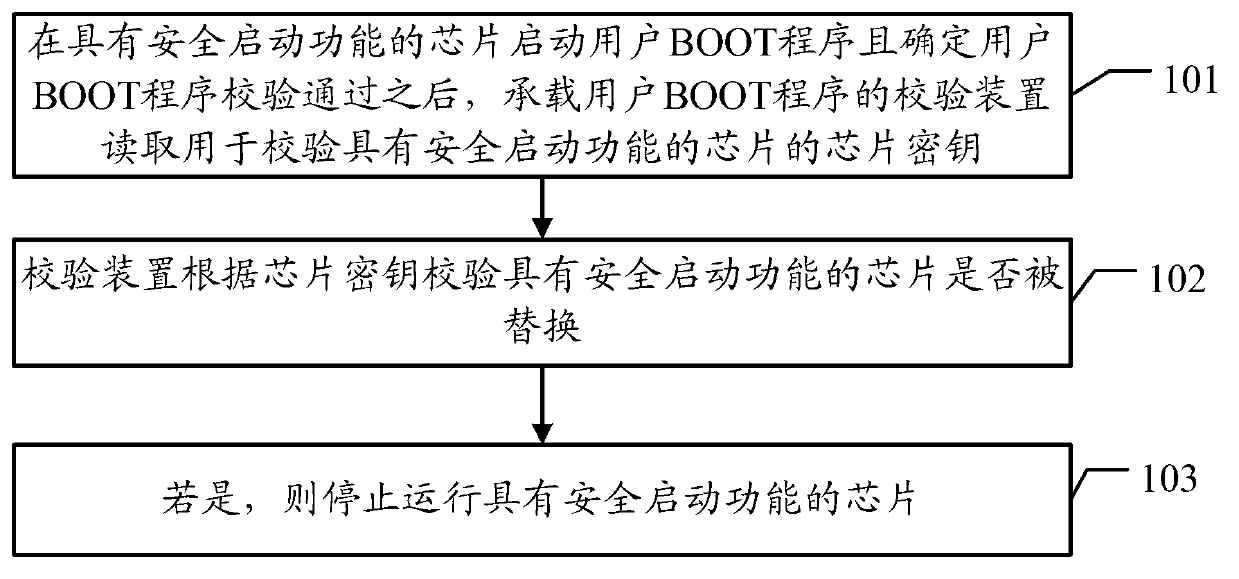
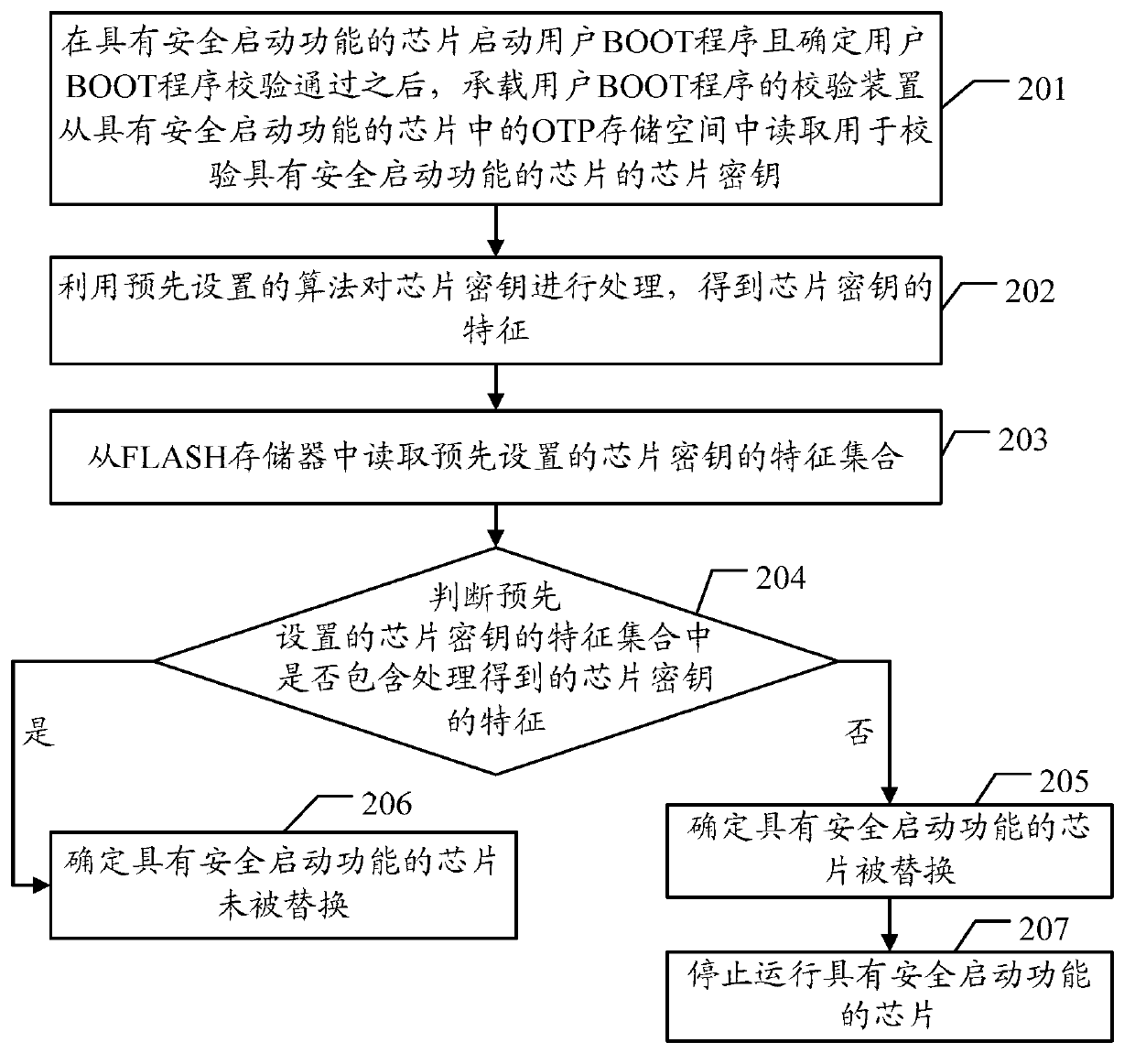
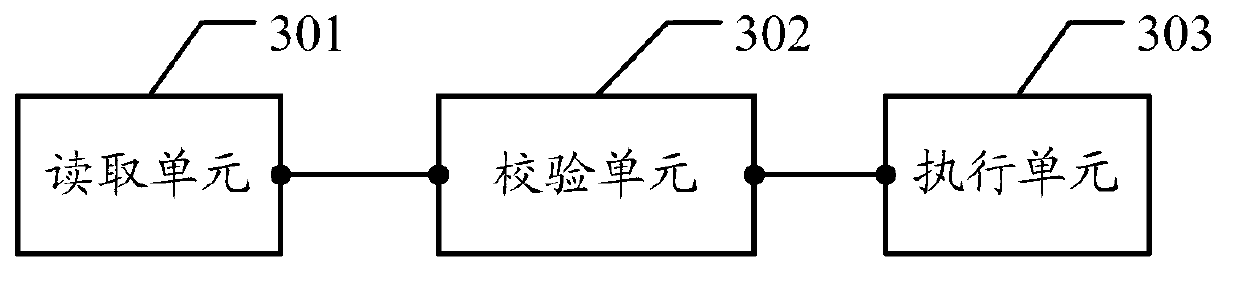
[0037] The embodiment of the present invention provides a verification method and verification device for a chip with a secure boot function, which are used to start a user BOOT program on a chip with a secure boot function on a single board and determine that the user BOOT program has passed the verification , if the verification module carrying the user BOOT program verifies that the chip with the secure boot function has been replaced, it will stop running the chip with the secure boot function to prevent the single board from starting and avoid the damage caused by the chip being replaced. Security issues.
[0038] In the embodiment of the present invention, the startup of the chip control program with secure boot function on the single board mainly relies on three keys, namely PKEY, BOOT KEY, and SMEK, wherein PKEY is used to verify the integrity of the user BOOT program, And under the condition that the user BOOT program is complete, the chip with secure boot function de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com