Method for preventing neighbor discovery protocol message attack and device
A neighbor discovery protocol and message technology, applied in the field of communication, can solve the problems of high application difficulty, waste of resources, complex configuration, etc., to ensure network security, improve overall robustness, and reduce resource occupation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
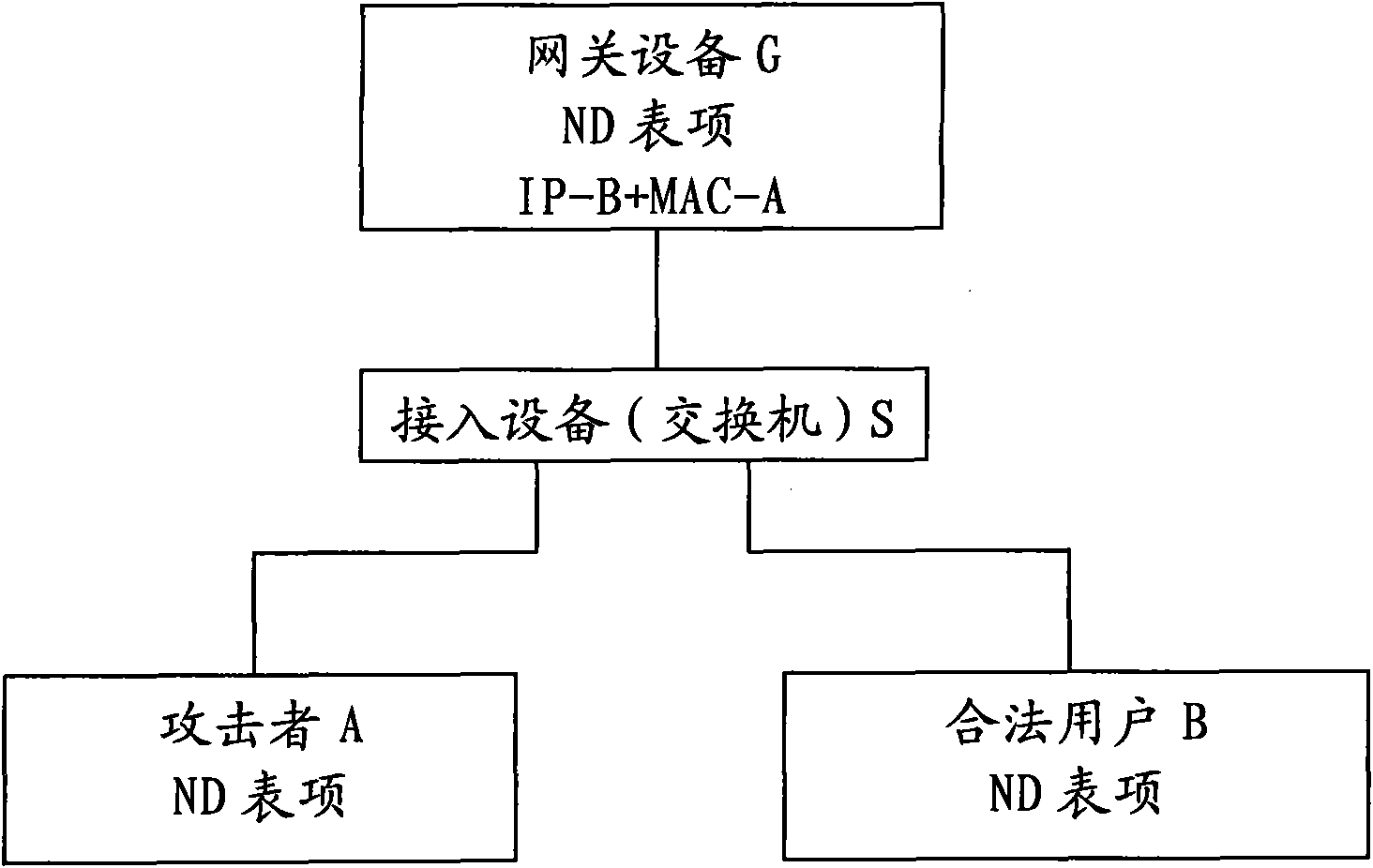
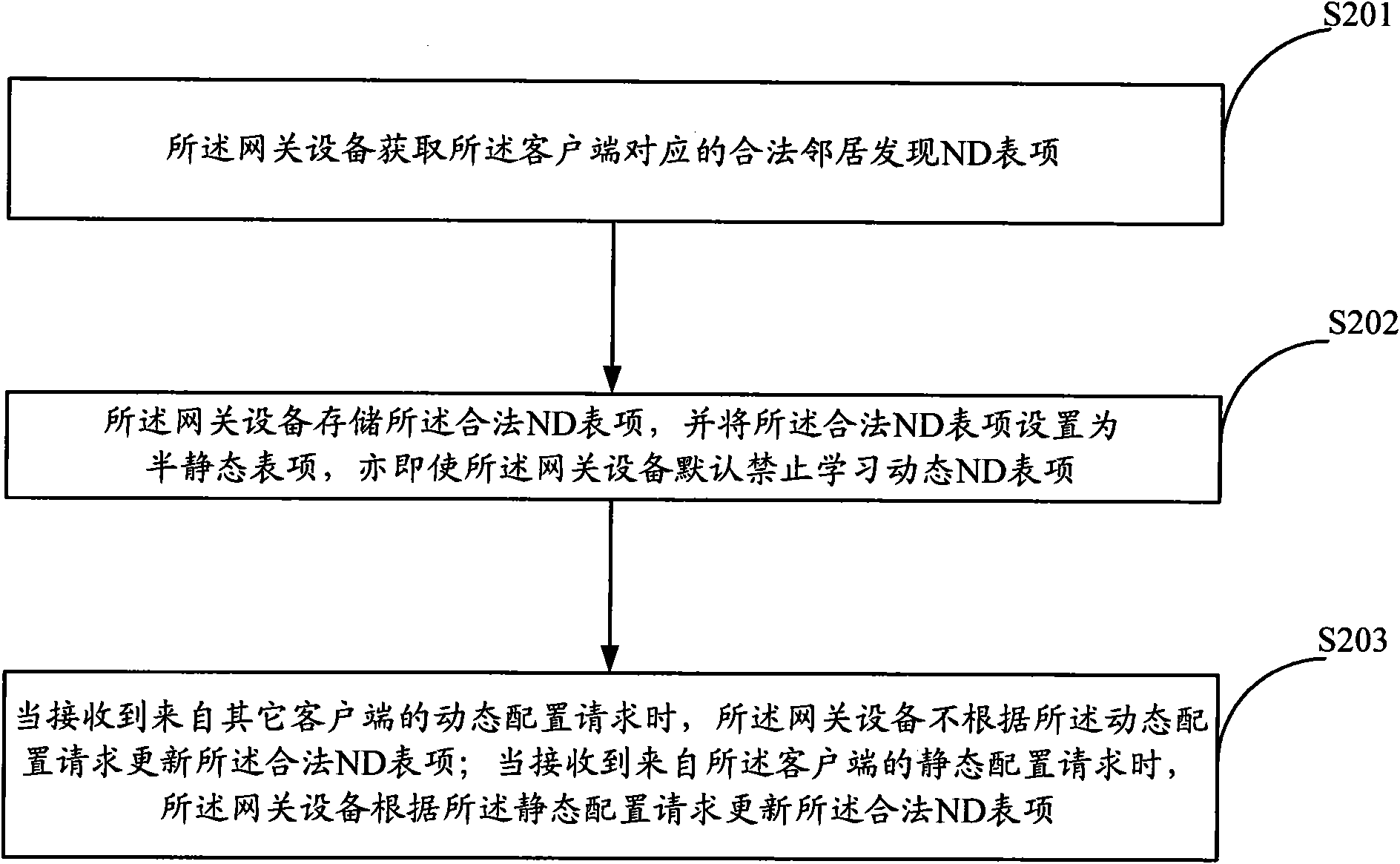
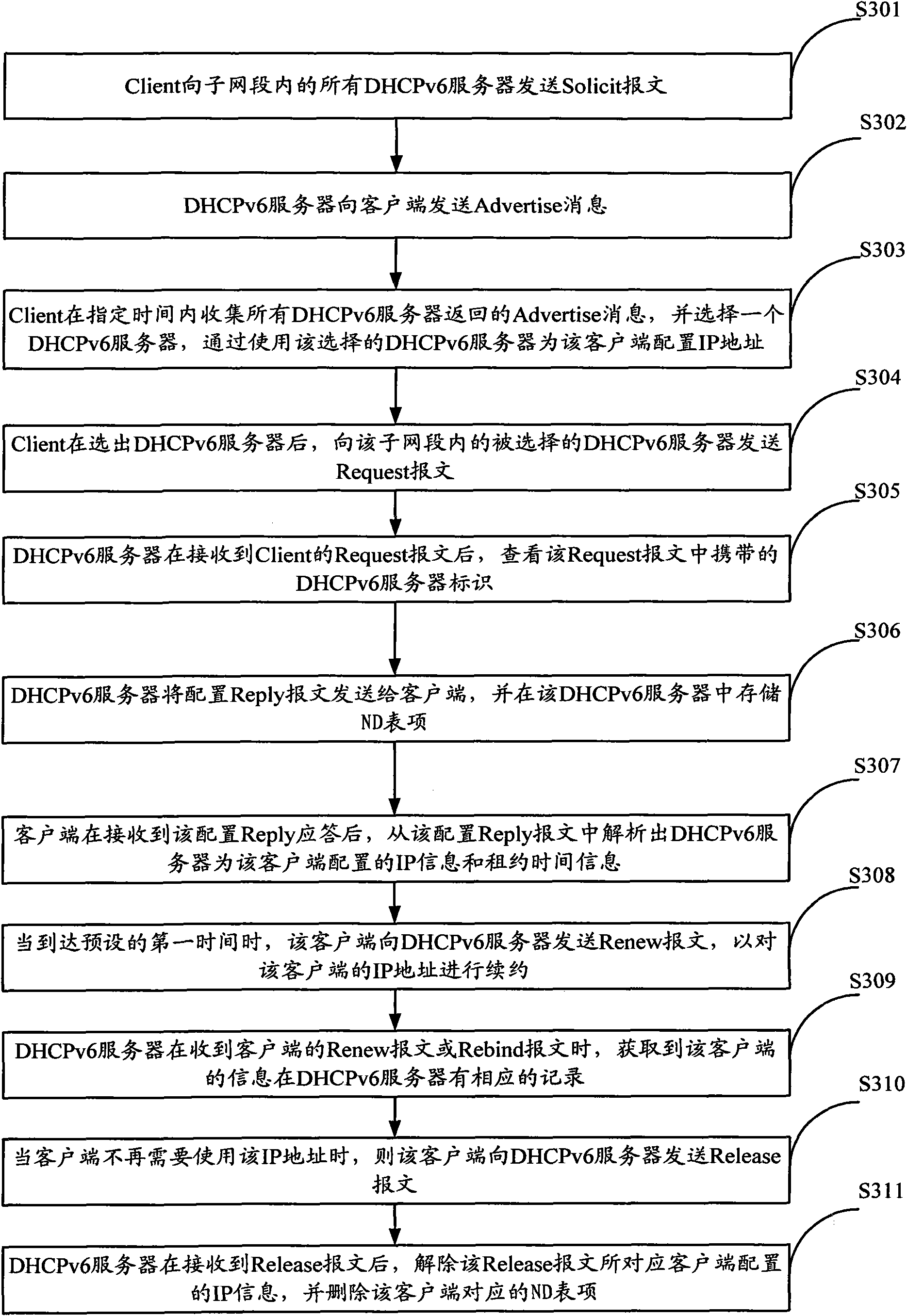
[0060] The core idea of the present invention is by configuring the DHCPv6 server in the network with the gateway device, after the DHCPv6 server configures the IP address for the client successfully, store the legal ND entry of the client in the gateway device (comprising at least the legal IP address and Correspondence between legitimate MAC addresses), and set the legal ND entry as a semi-static entry. When receiving an NS packet from a user (or an attacker) that needs to dynamically update an ND entry, the ND entry will not be updated. Update, the ND entry is updated only when the user notifies the administrator to update the ND entry statically, thereby preventing the attack of the attacker's NS packet and enhancing the security of the network.
[0061] A method for preventing neighbor discovery protocol message attacks proposed by the present invention is applied to a system including at least a client, a DHCP server and a gateway device, wherein the DHCP server can be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com