FPGA (Field Programmable Gate Array)-based network security log processing method and device
A network security and processing device technology, applied in the field of network security, can solve the problems of low overall system efficiency, easy loss of added messages, message loss, etc., to achieve the effect of ensuring network security and avoiding network security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
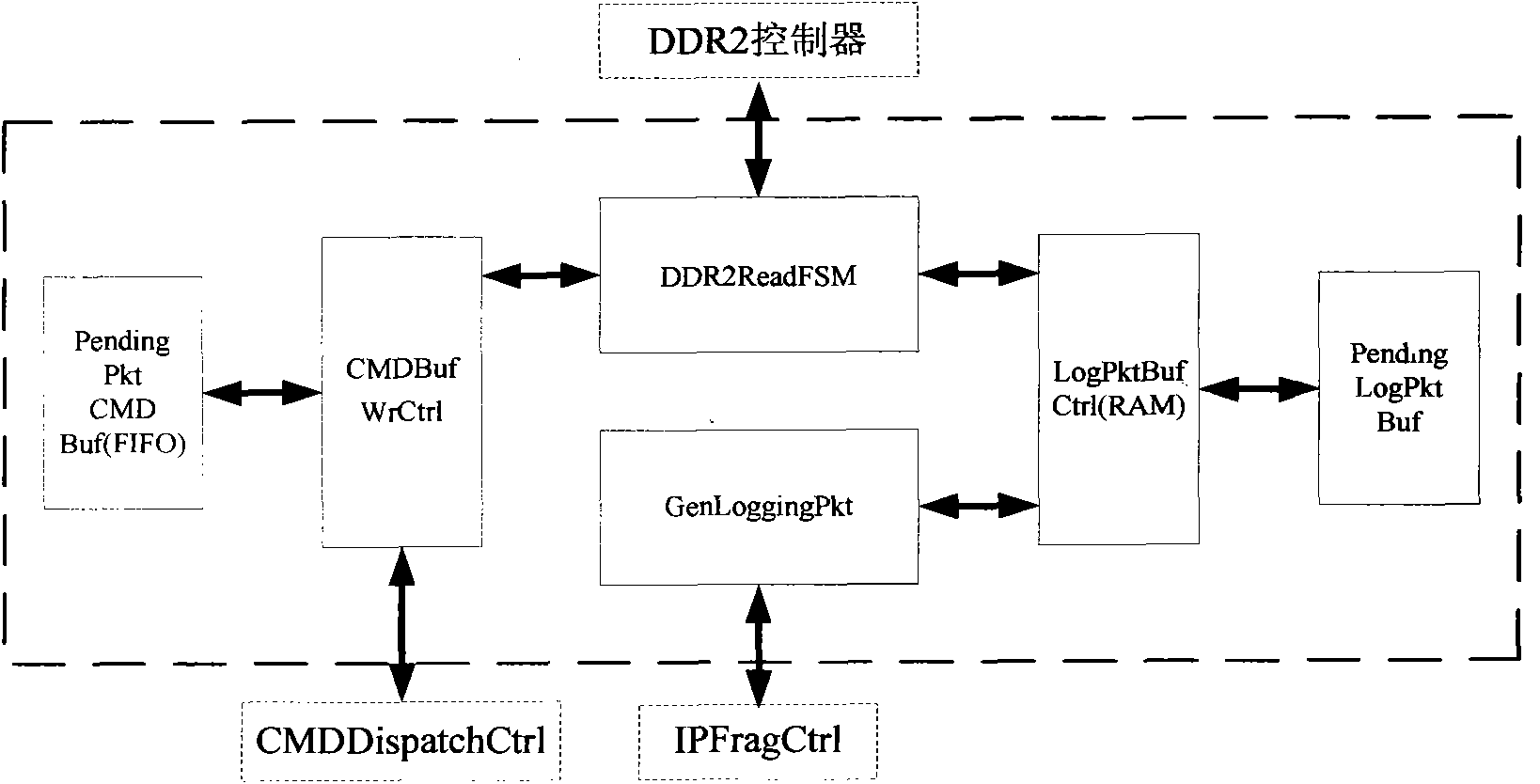
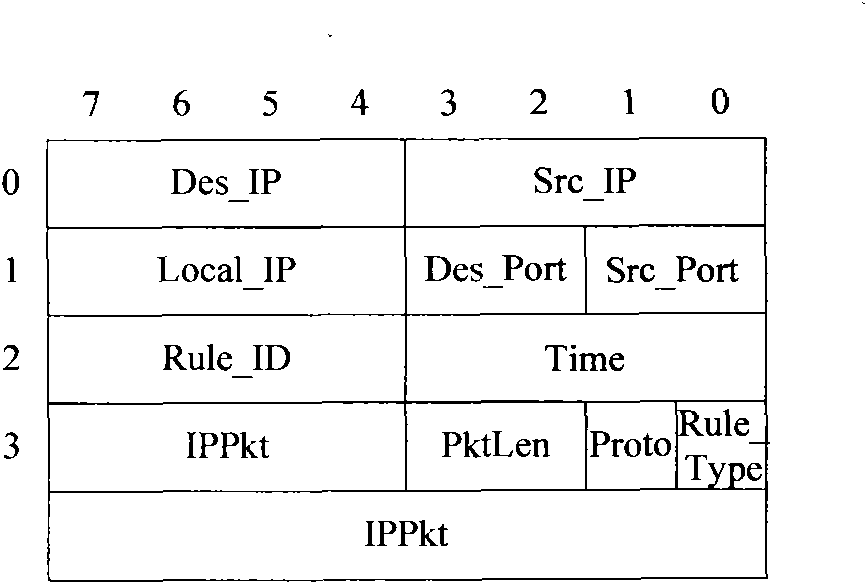
[0027] The present invention includes a network data storage, a user rule storage, and a feature comparator. The method for blocking the network security connection includes the following steps: receiving the data packet sent by the external network; temporarily storing the received data packet in the setting In the network data storage; and extract the characteristic value from the data packet, compare a certain rule in the user rule memory according to a characteristic value of the data packet, judge whether the data packet meets the condition of forwarding the log; when the characteristic value meets the , the network device promptly takes out the data packets from the network data storage, and packs them, and sends the data packets to the main memory of the host that requires storage, so as to facilitate data analysis.
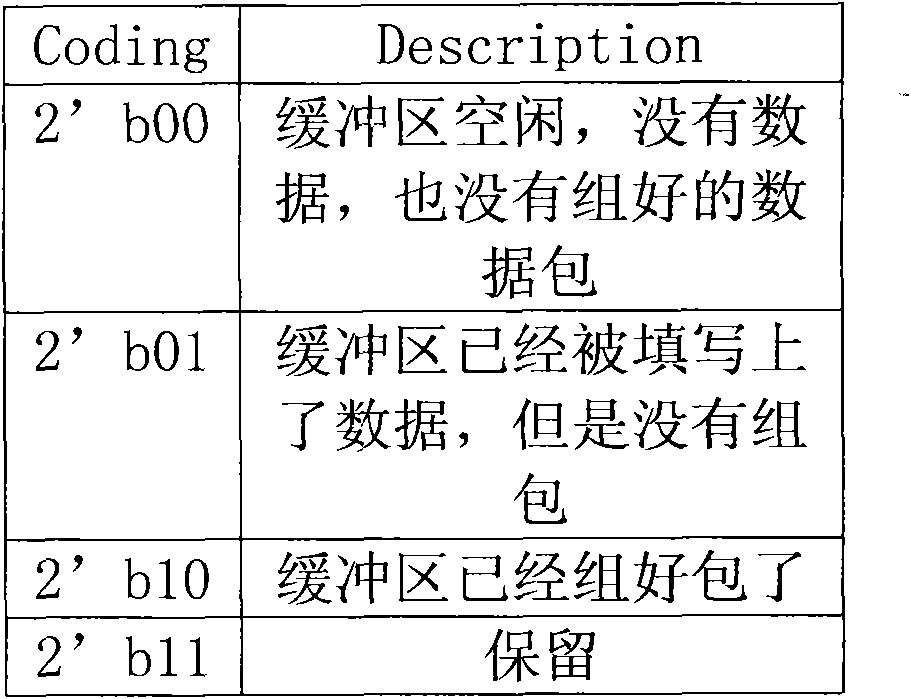
[0028] Figure four It is a state transition diagram of a state machine. The actions of each state are as follows,
[0029] IDLE: In the initial state, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com