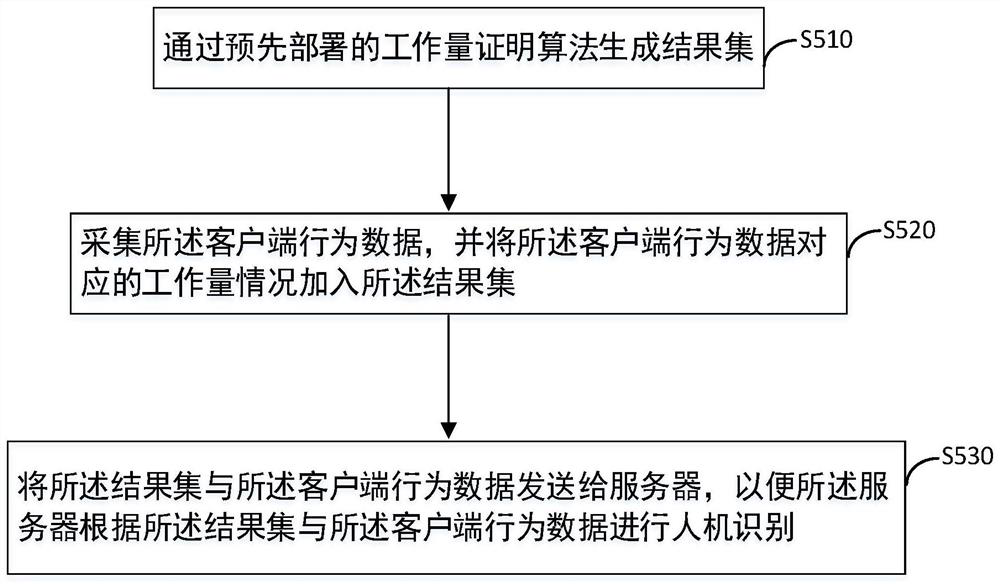
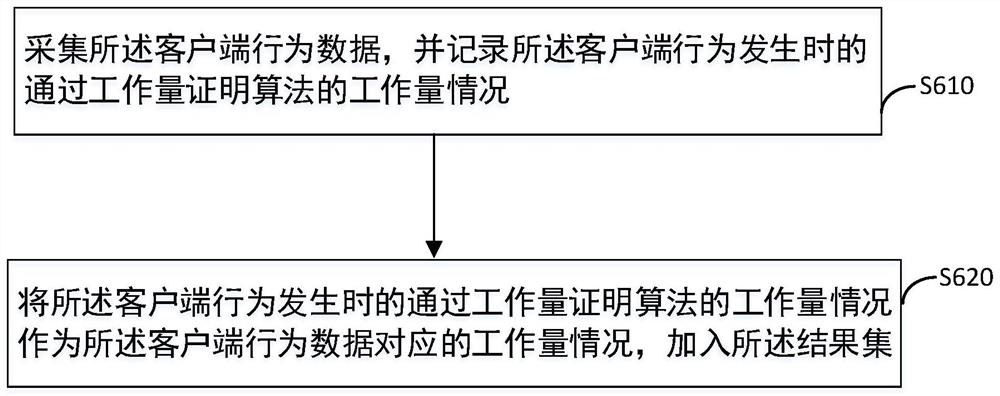
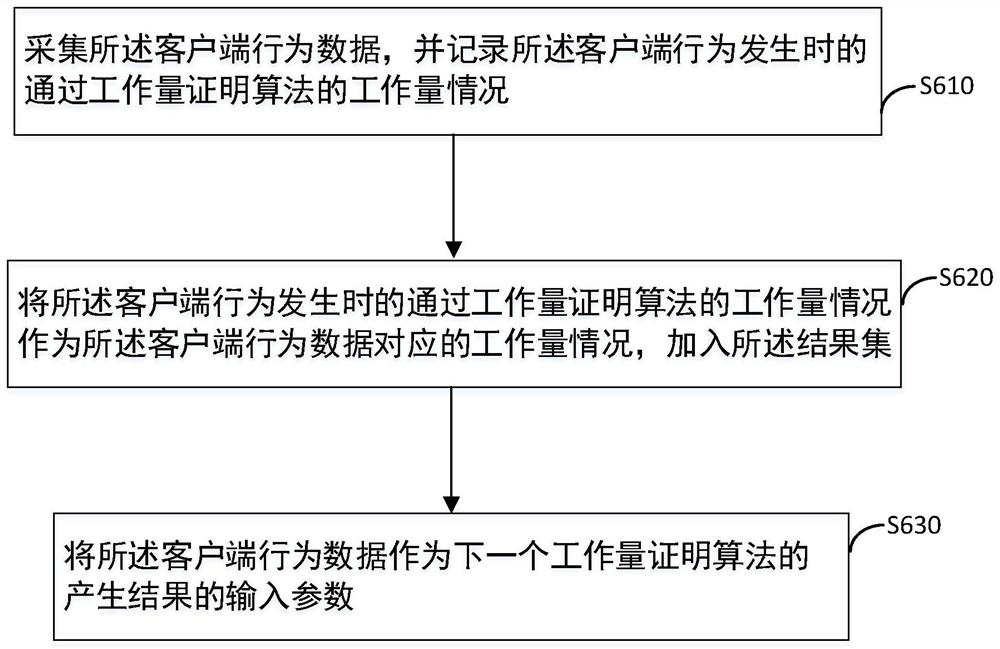
Patents
Literature
50results about How to "Avoid aggressive behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
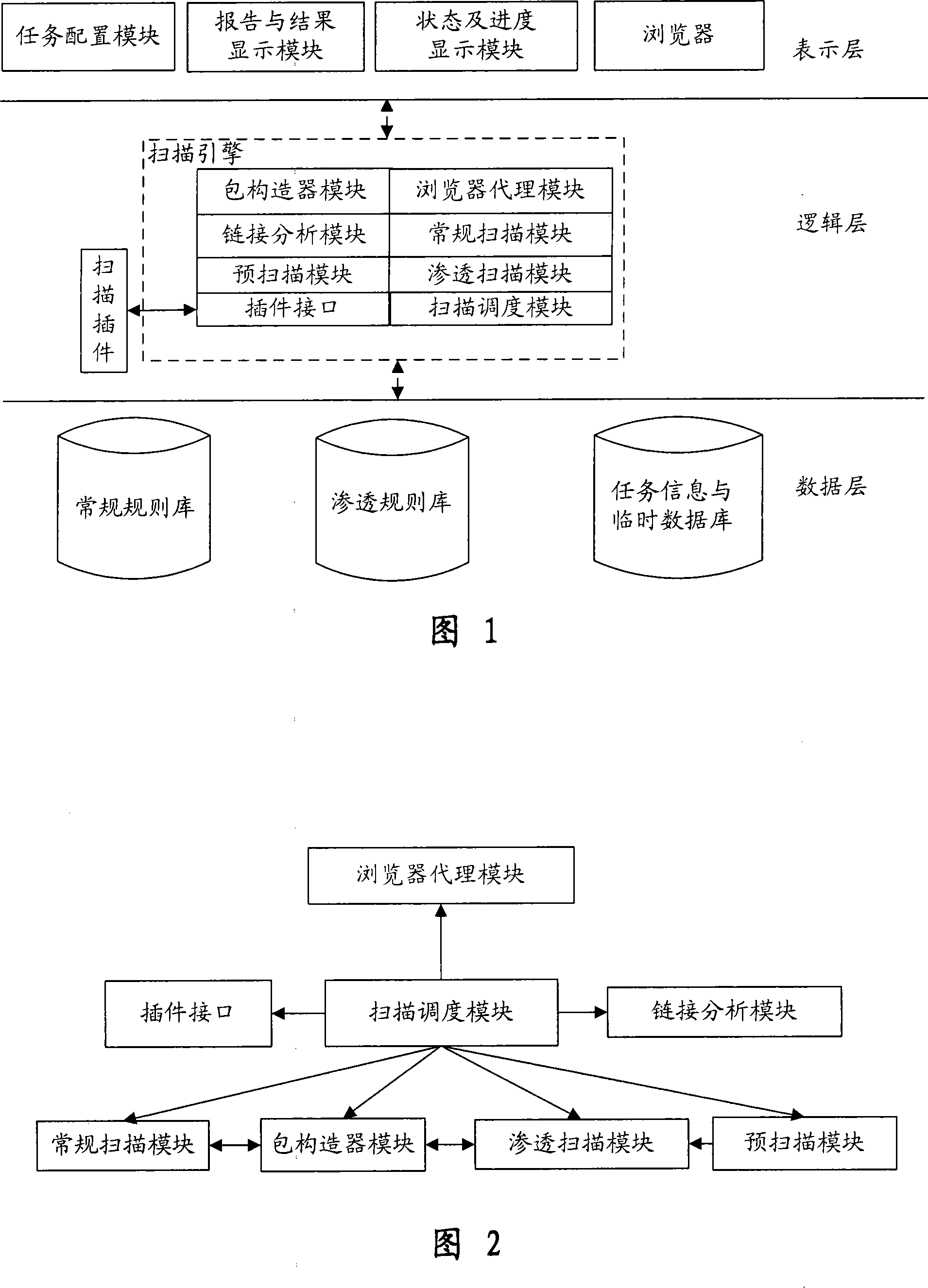
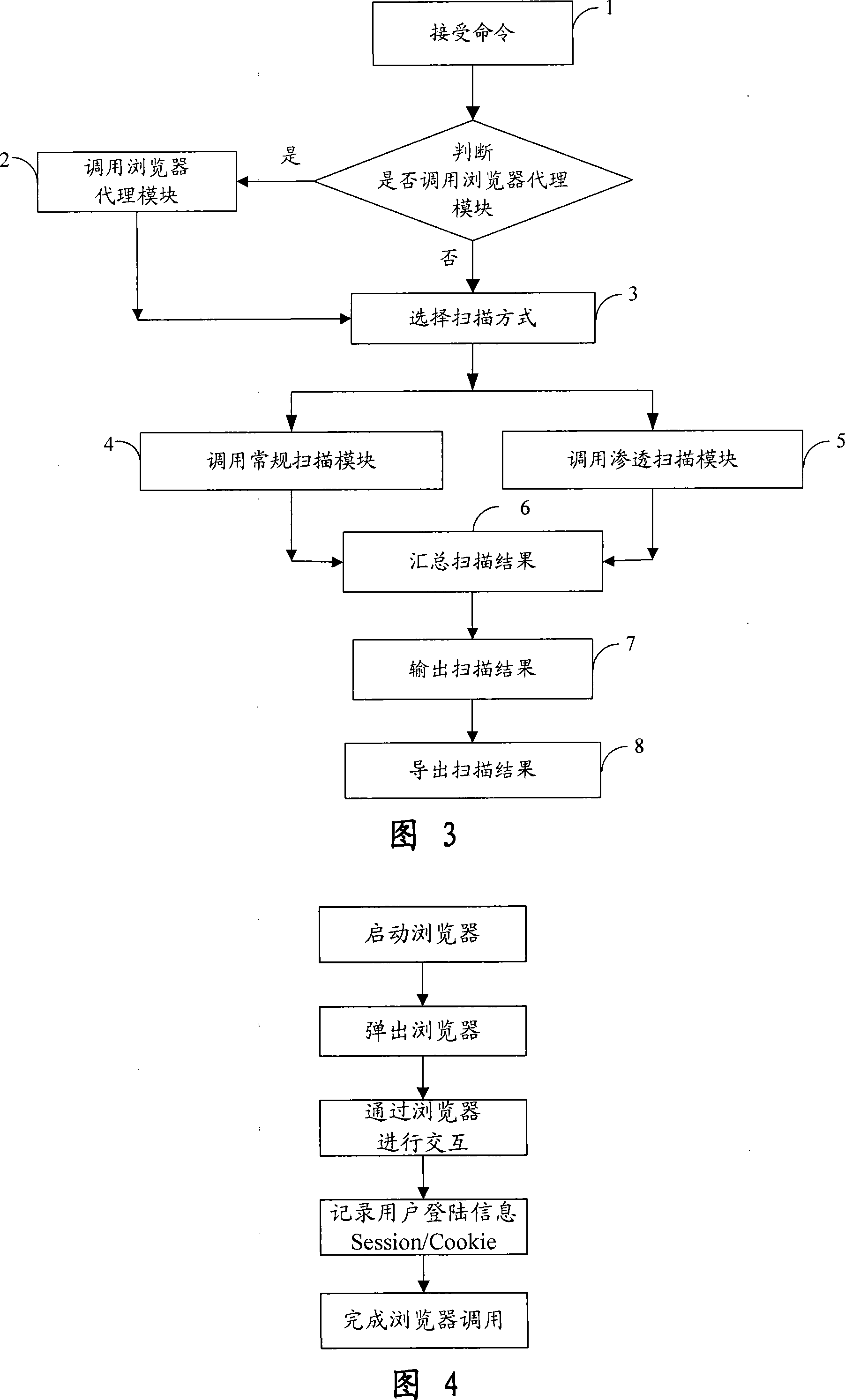
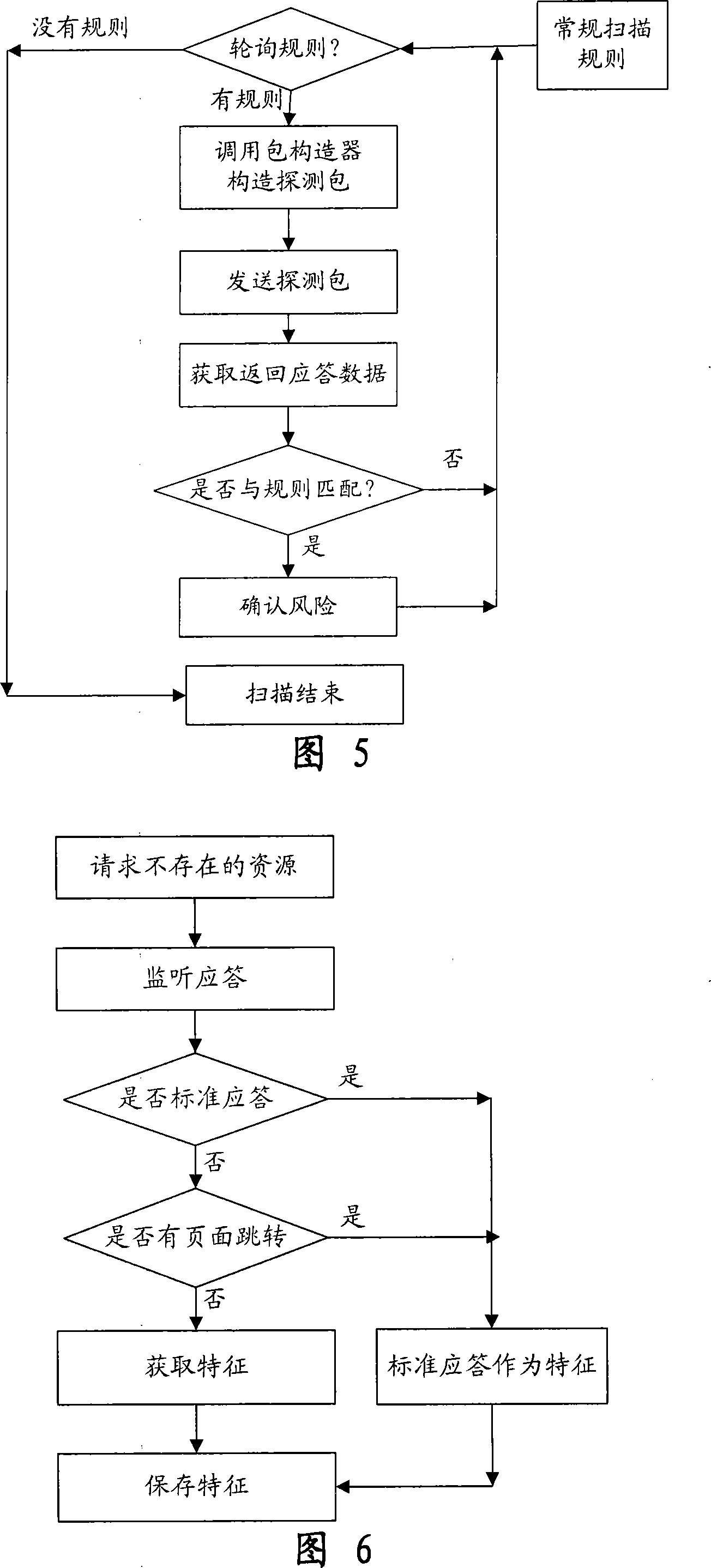
Automatic penetration testing system and method for WEB system
InactiveCN101242279AImprove functional efficiencyImprove work efficiencySpecial data processing applicationsSecuring communicationComputer hardwareSecurity testing
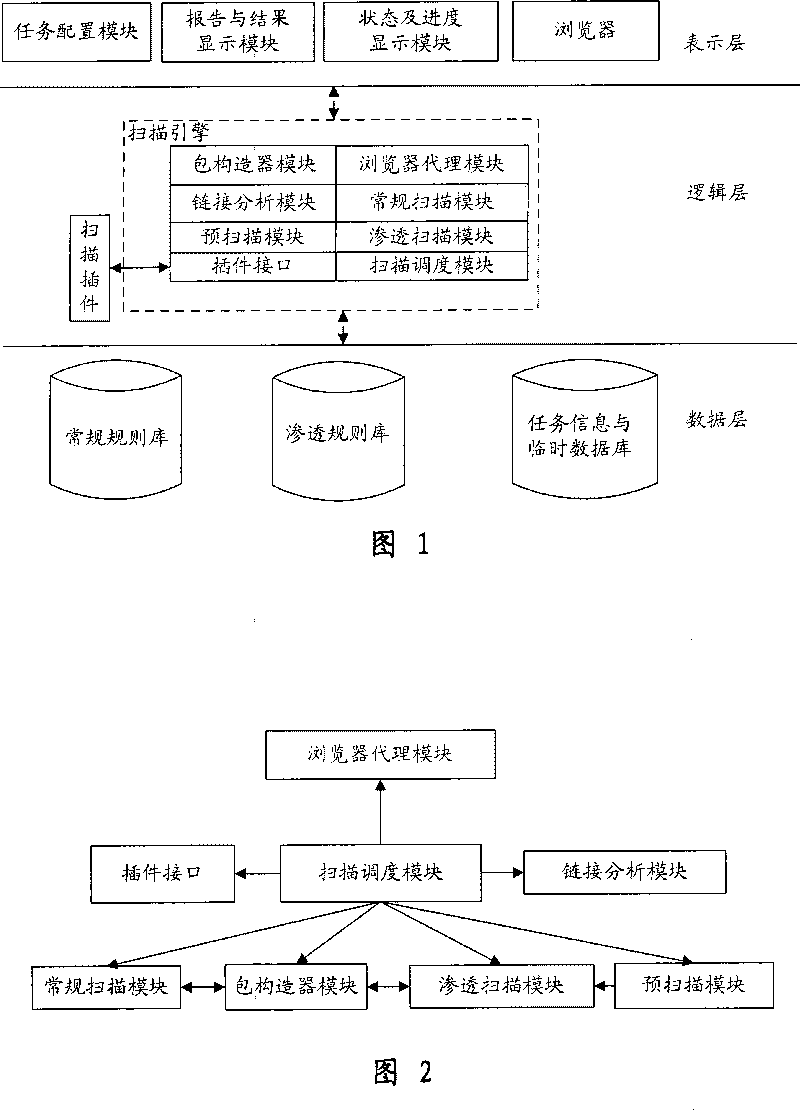
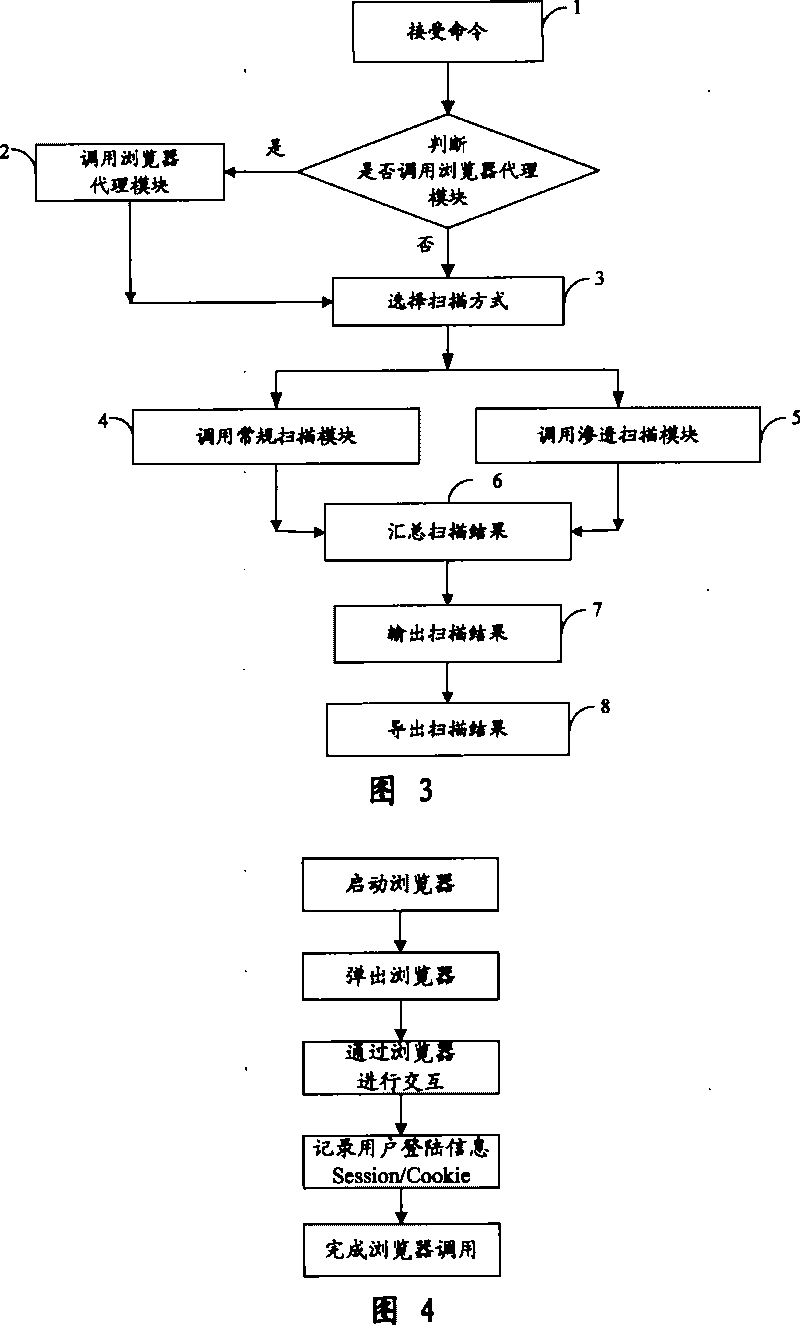
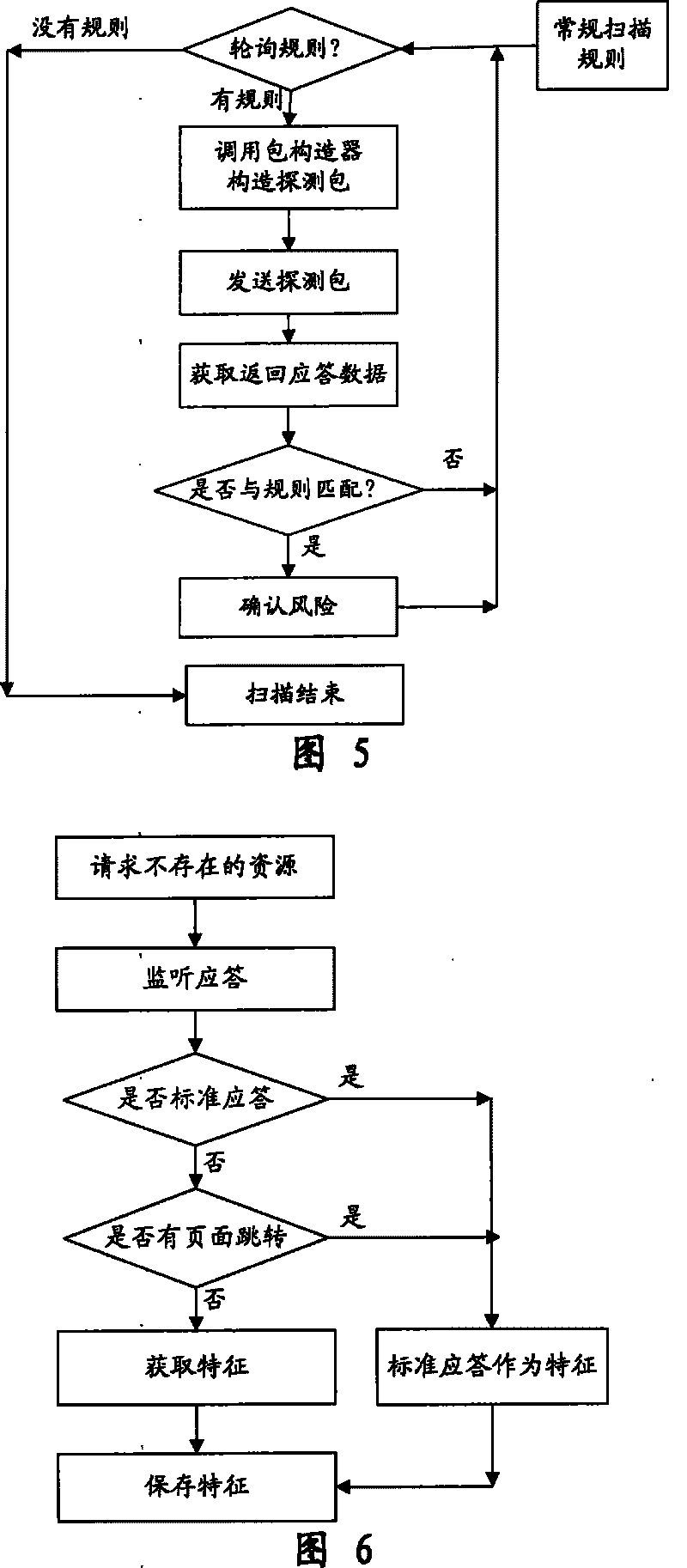
The invention provides an automatic permeability test system for a WEB system, comprising three layers: a GUI presentation layer for alternating interface with a user, a logical layer as runs of control core, executing scanning and confidence program of the system and associative functions, and a data layer for storing and maintaining kinds of scan rules and configuration information in a task execution process. The system can automatically carry out a penetrating scan or a conventional scan to a WEB station based on a WEB scan task in the GUI layer, analyzing the scan result combined with the relative inserters, finds the possible security problems of the WEB station, and then generates a detecting report for reporting a formed aggregate risk list. The invention is used to perform an automatic security test, is capable of replacing the present manual security test and permeability test, greatly reduces the cost of software security test in software develop at present, and also greatly increases accuracy of security test.
Owner:BEIJING UNIV OF POSTS & TELECOMM
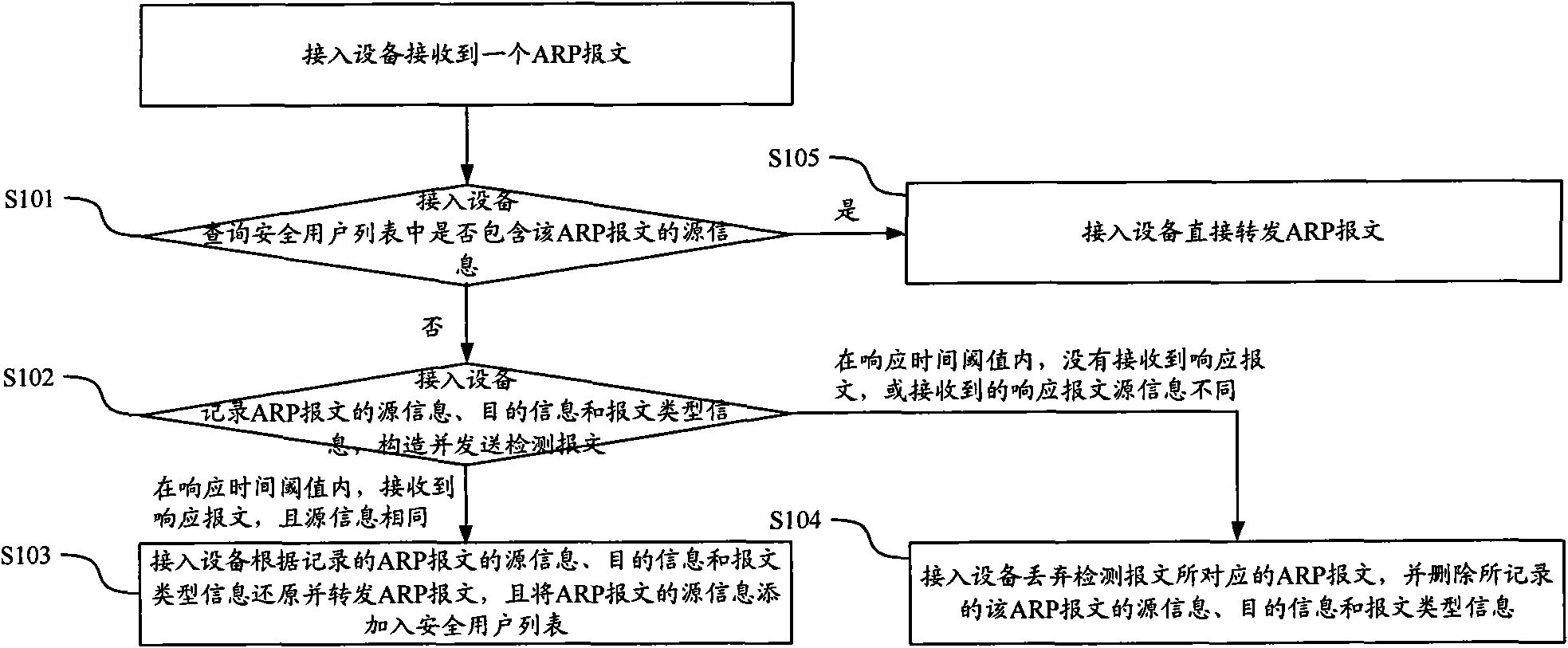
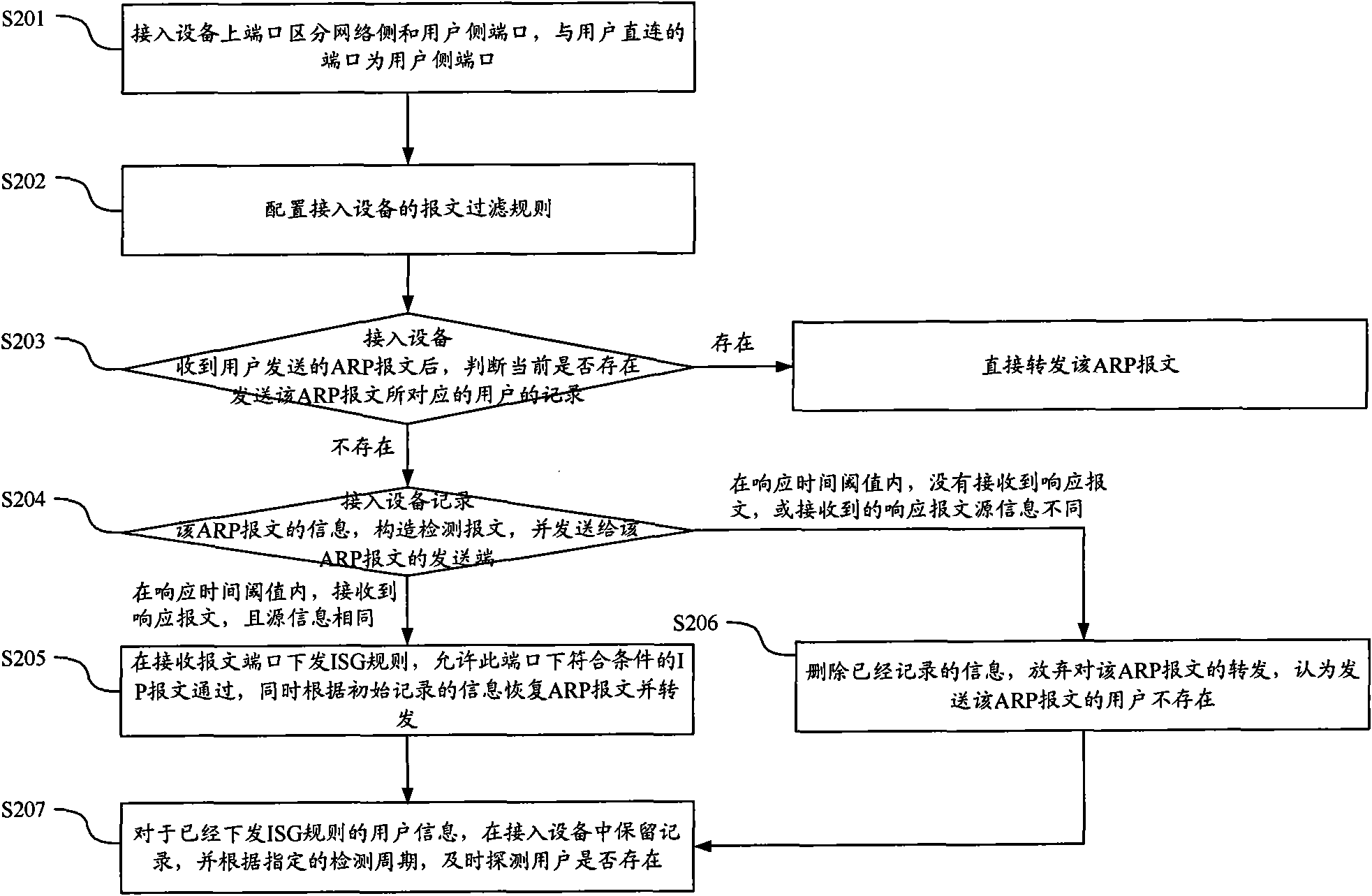
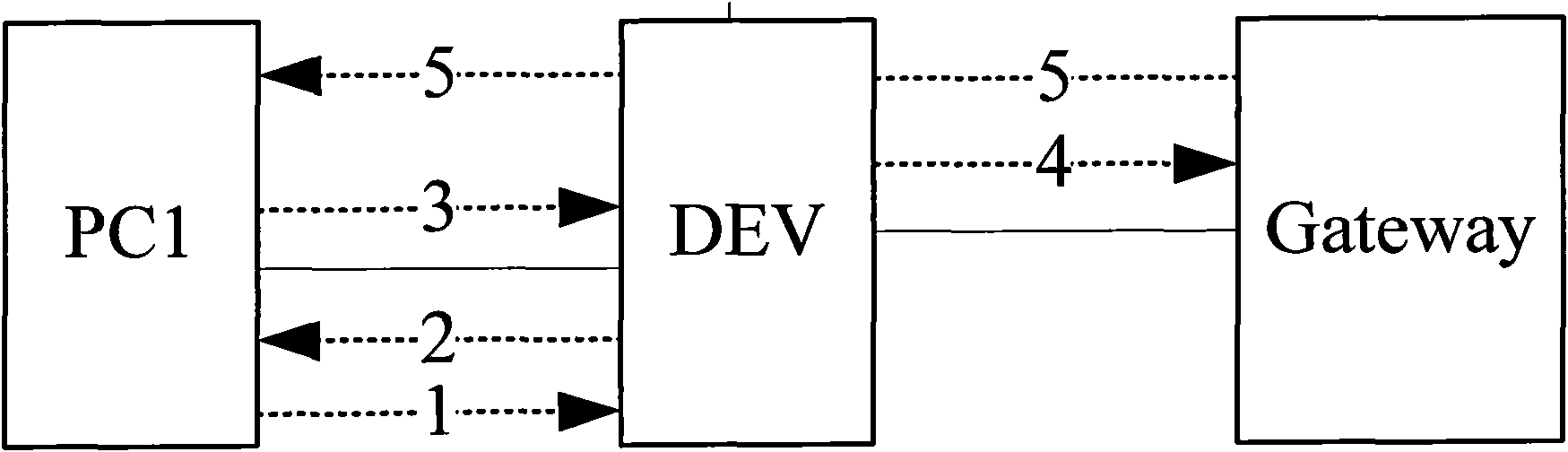
Method and device for verifying message safety
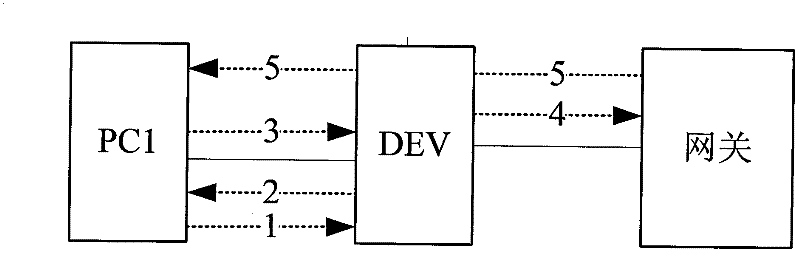
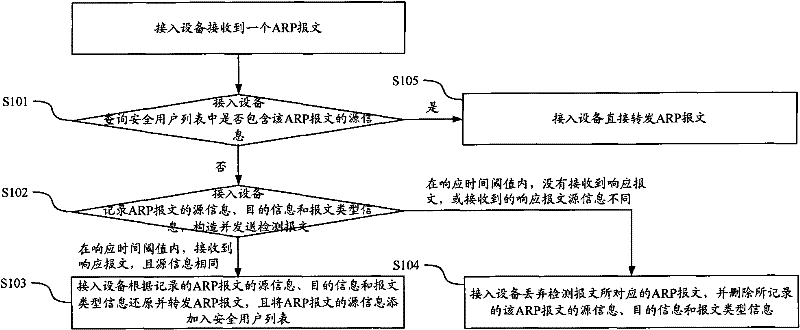
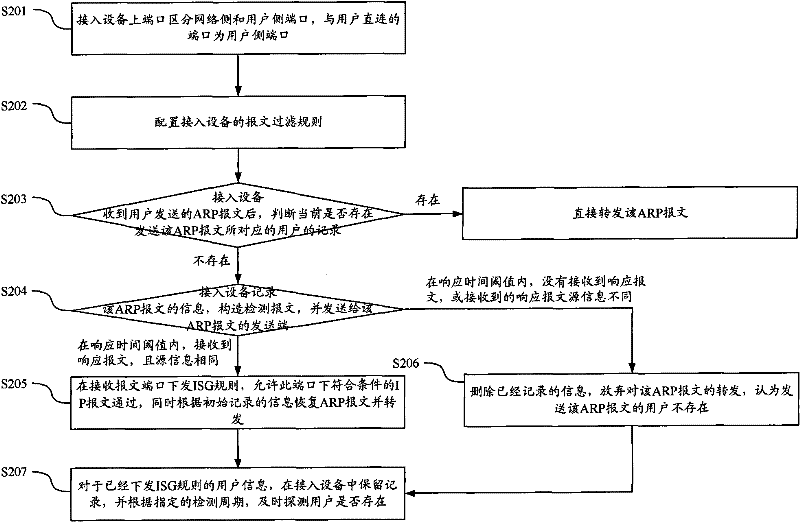
ActiveCN101820396AVerify legitimacyAvoid aggressive behaviorData switching networksComputer securityComputer science
The invention discloses a method and a device for verifying message safety. By using the technical scheme of the invention, simple user validation judgment can be carried out on an access device to effectively verify the user validation at a position closest to a user, thereby preventing the attack of a message with a user-forged IP on an uplink network at an end point.
Owner:NEW H3C TECH CO LTD
Email transfer method for the online protocol and credit mechanism based on scalable message
ActiveCN101056281AAvoid aggressive behaviorReduce the burden onUser identity/authority verificationData switching networksTransfer procedureTransfer mode
Email sending method based on the scalable message online protocol and credit mechanism belongs to the network security area. Its features are as follows: this method utilizes the IM platform based on the XMPP protocol to effectively guarantee the true source identity. The 'pull mode' transmission mode is used in the Email sending. The IM platform is used to maintain the characteristics of the online status of the user and the block transfer mode is combined with the direct transfer mode between the sender and receiver in the message transfer. The method invents the distinct combination mechanism of the credit mechanism and blacklist policy and can real time prevent the rubbish message attack. The method can be deployed on the IM platform based on the XMPP protocol which is extensively used now. The method adopts the server forwarding and end-to-end direct message transfer solution, so it can alleviate the load of the old server and can not affect the performance of the old IM service.
Owner:TSINGHUA UNIV
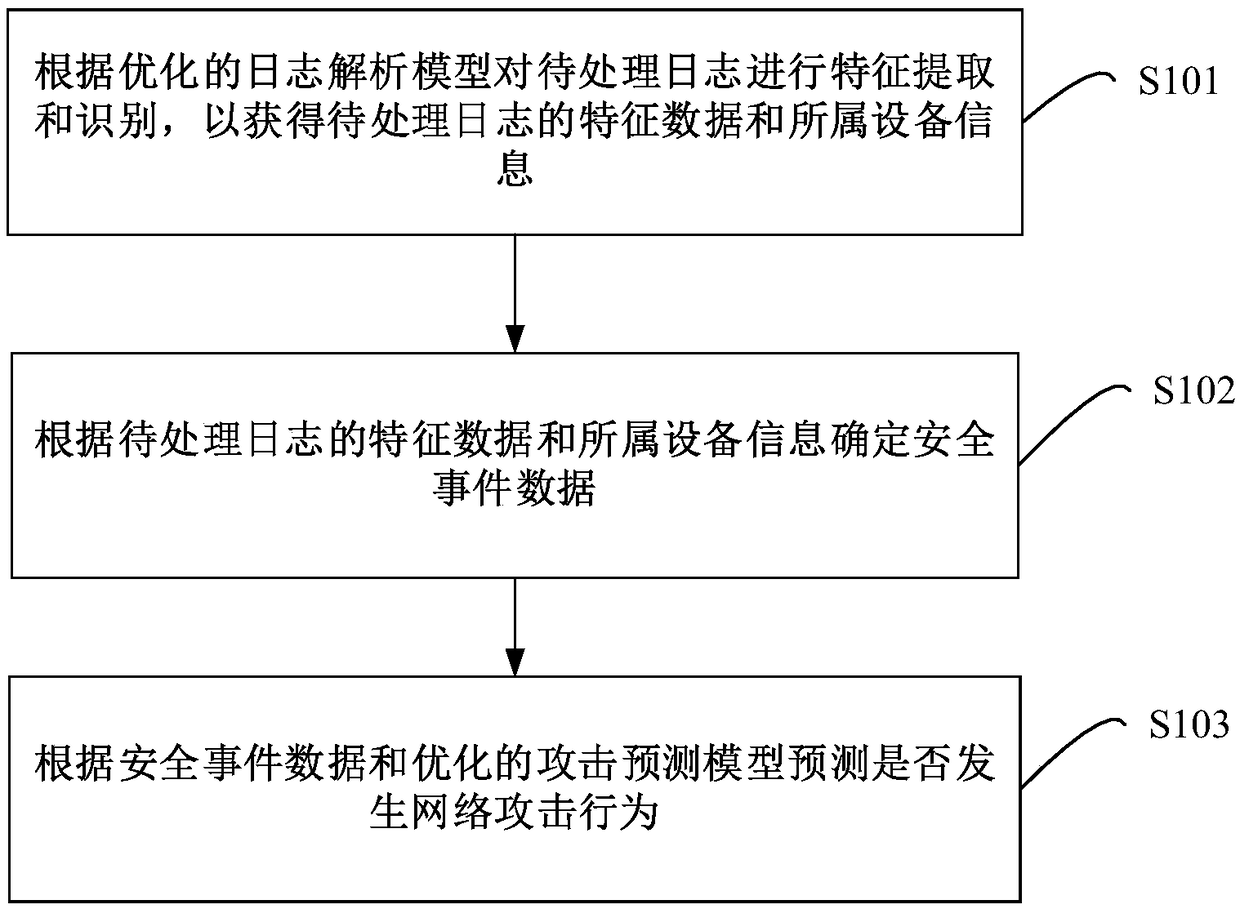
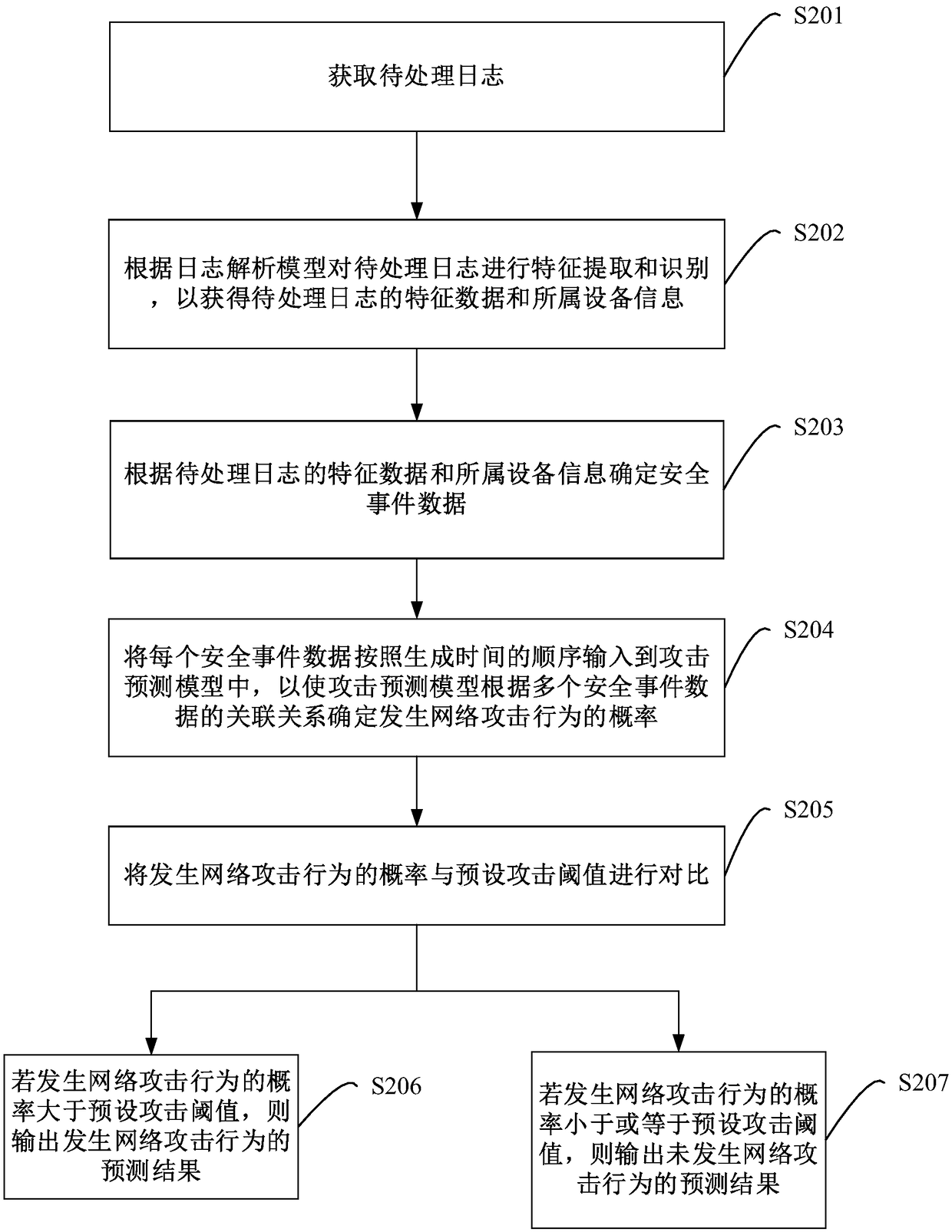
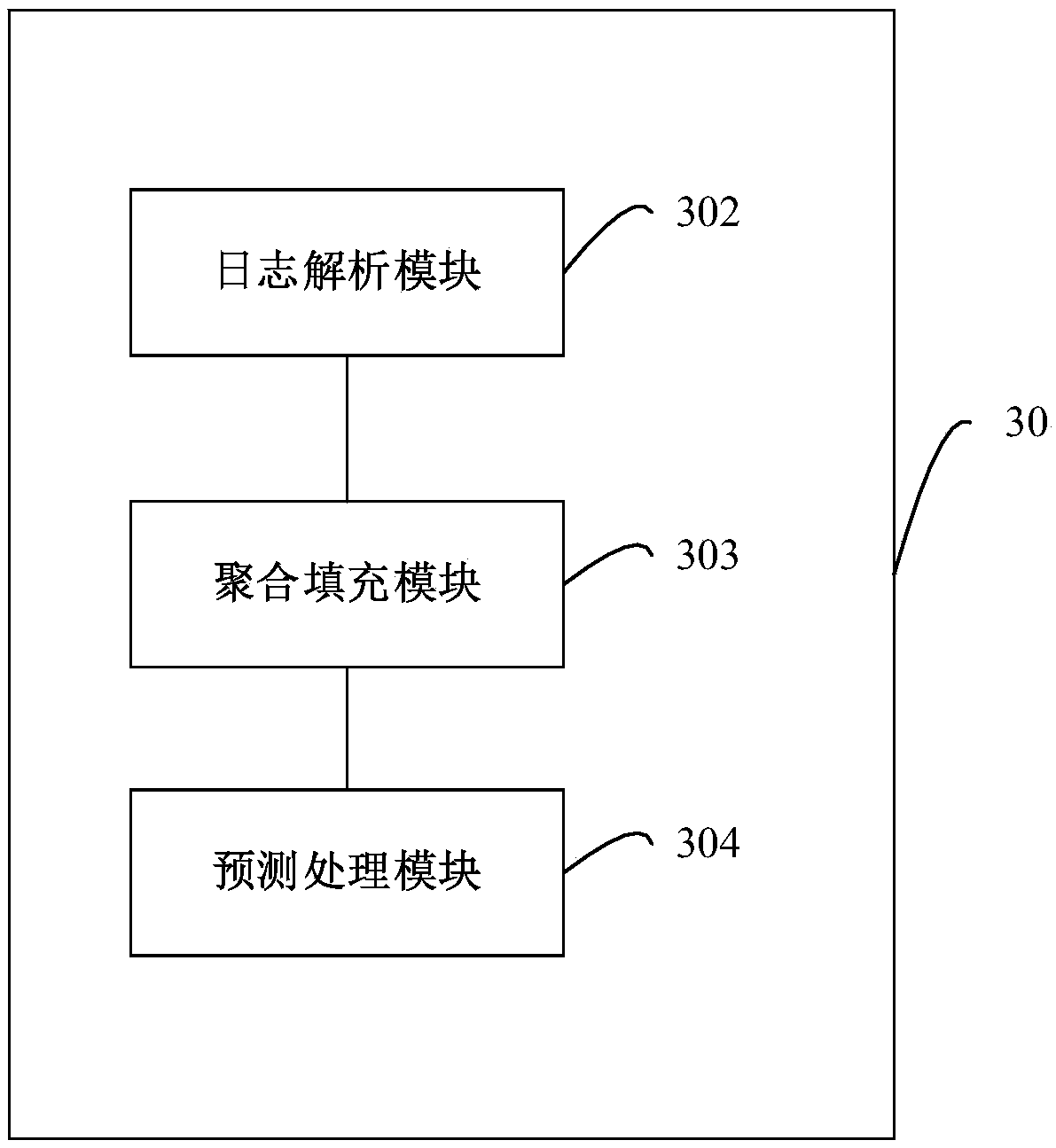
Method, apparatus and device for network attack behaviors prediction, and storage medium
ActiveCN109347827AImprove analysis efficiencyImprove recognition efficiencyTransmissionFeature extractionEvent data
The embodiment of the invention provides a method, an apparatus and a device for network attack behaviors prediction, and a storage medium. The method provided by the embodiment of the invention comprises the following steps: performing feature extraction and identification for a to-be-processed log according to a log parsing model, thereby obtaining feature data of the to-be-processed log and information of the device to which the to-be-processed log; according to the feature data of the to-be-processed log and the information of the device to which the to-be-processed log, determining security event data; and according to the security event data and an attack prediction model, predicting whether network attack behaviors happen. Thus, parsing and identification efficiency for the log is improved, the network attack behaviors which are going to happen can be predicted before the network attack behaviors happen, a base is provided for effectively avoiding the network attack behaviors, and security of a network device can be guaranteed effectively.
Owner:NEUSOFT CORP
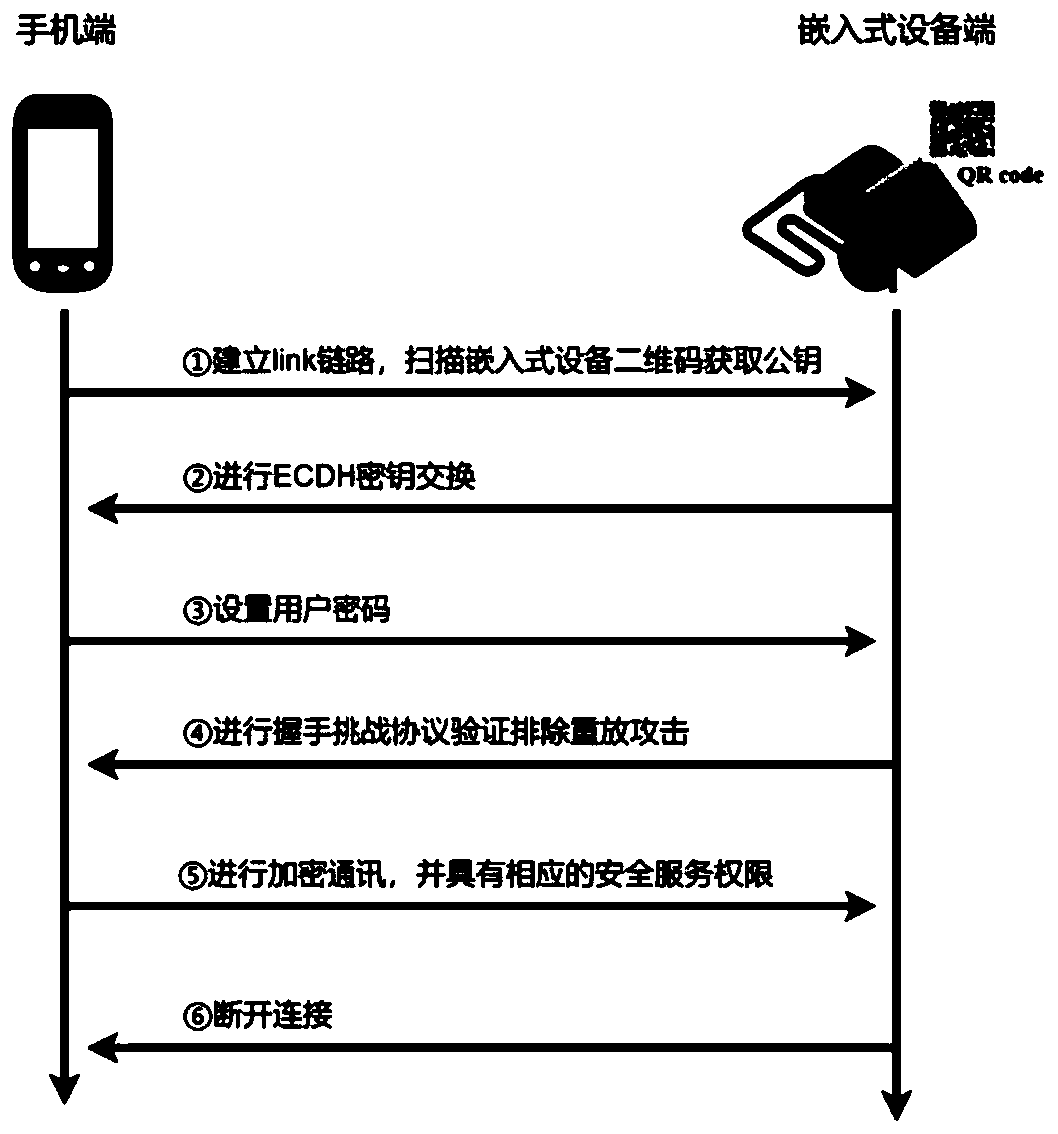
Bluetooth communication authentication request, receiving and communication method, mobile terminal and equipment terminal
ActiveCN110572804AWill not visitEnsure safetyShort range communication serviceSecurity arrangementKey exchangeTelecommunications link
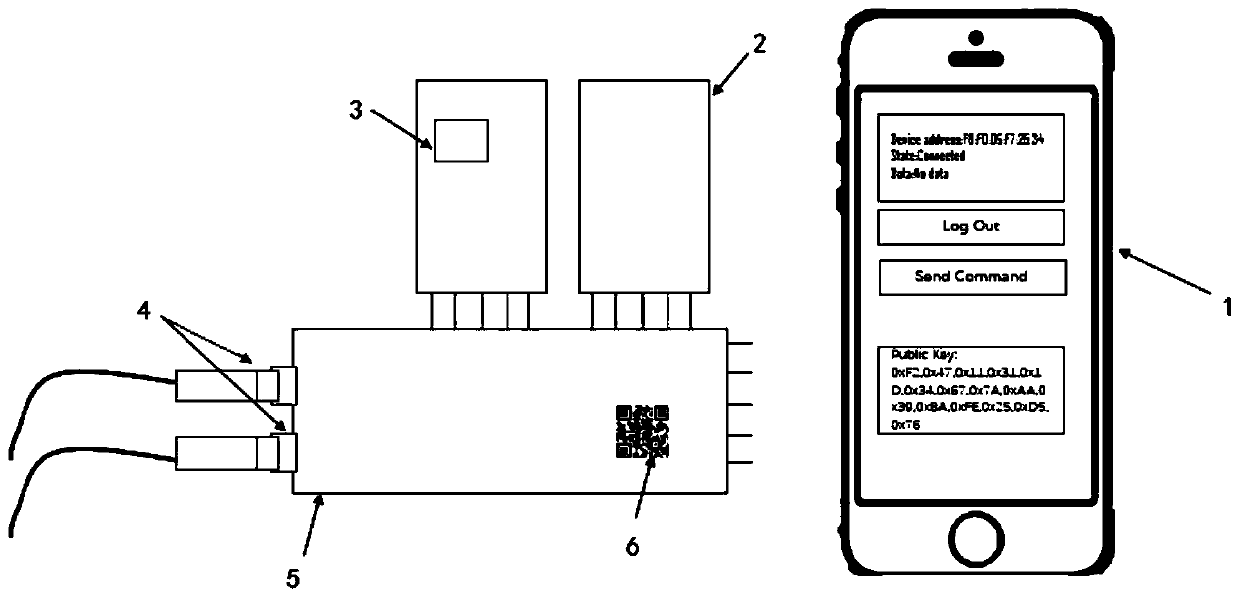
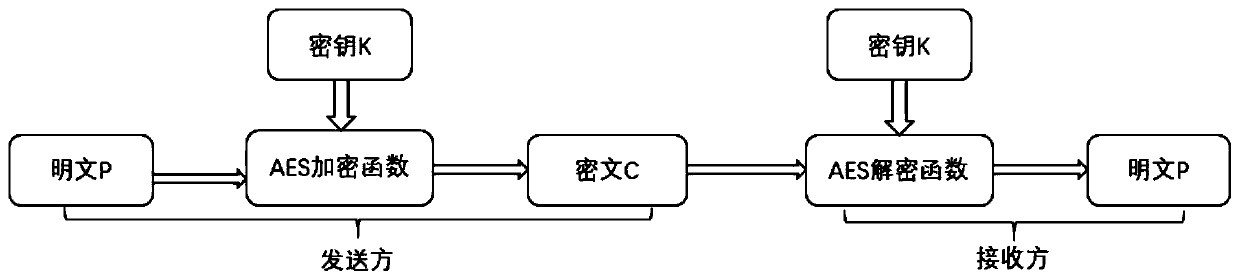
The invention discloses a Bluetooth communication authentication request, receiving and communication method, a mobile terminal and an equipment terminal, and the Bluetooth communication authentication request and communication method comprises the steps: carrying out the Bluetooth scanning with the equipment terminal, and establishing a communication link on a link layer; obtaining an equipment end public key; performing ECDH key exchange, and generating an ECDH Base AES Key symmetric key K; acquiring a user password, and sending the user password to the equipment end; after the equipment terminal passes user authentication, performing data communication with the equipment terminal, and disconnecting connection after communication is completed; in the user password sending process and thedata communication process, an AES encryption channel is adopted for encryption and decryption transmission, and a secret key of an AES encryption function is a symmetric secret key K. According to the method, the secret keys of the two communication parties are stored in the application layer, detection and verification are carried out on the application layer through the ECDH secret key exchange technology, it is guaranteed that the secret keys are stored in a protected thread, and data cannot be accessed by other malicious programs.
Owner:JINAN UNIVERSITY
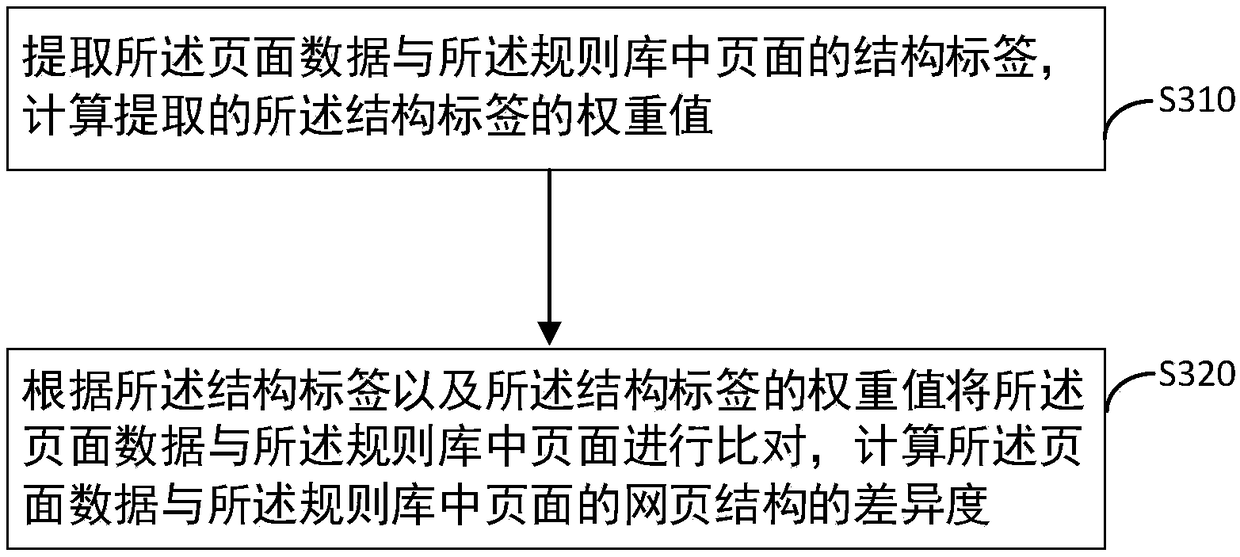
Illegal-page detection method and device, intrusion detection system and storage medium
InactiveCN108304584AImprove the detection rateReduce false alarm rateWebsite content managementSpecial data processing applicationsPattern recognitionWeb page
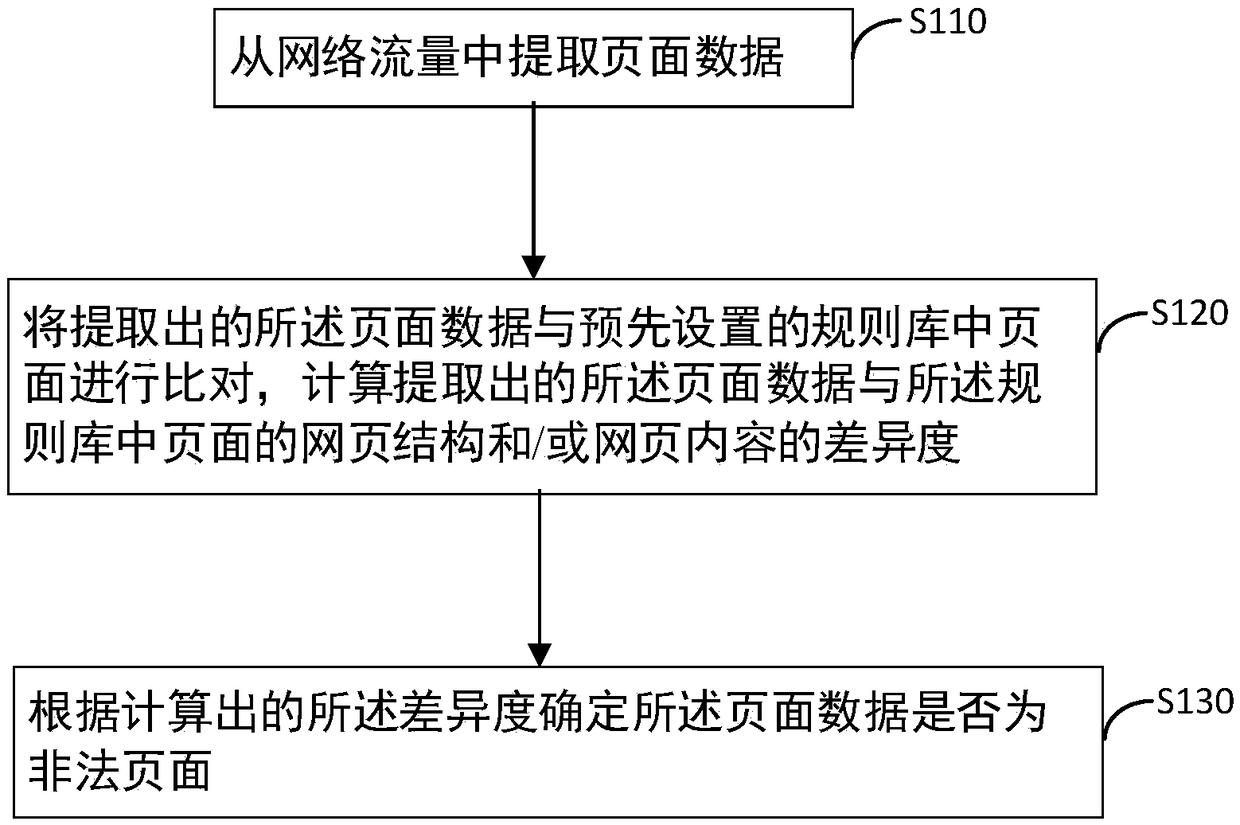
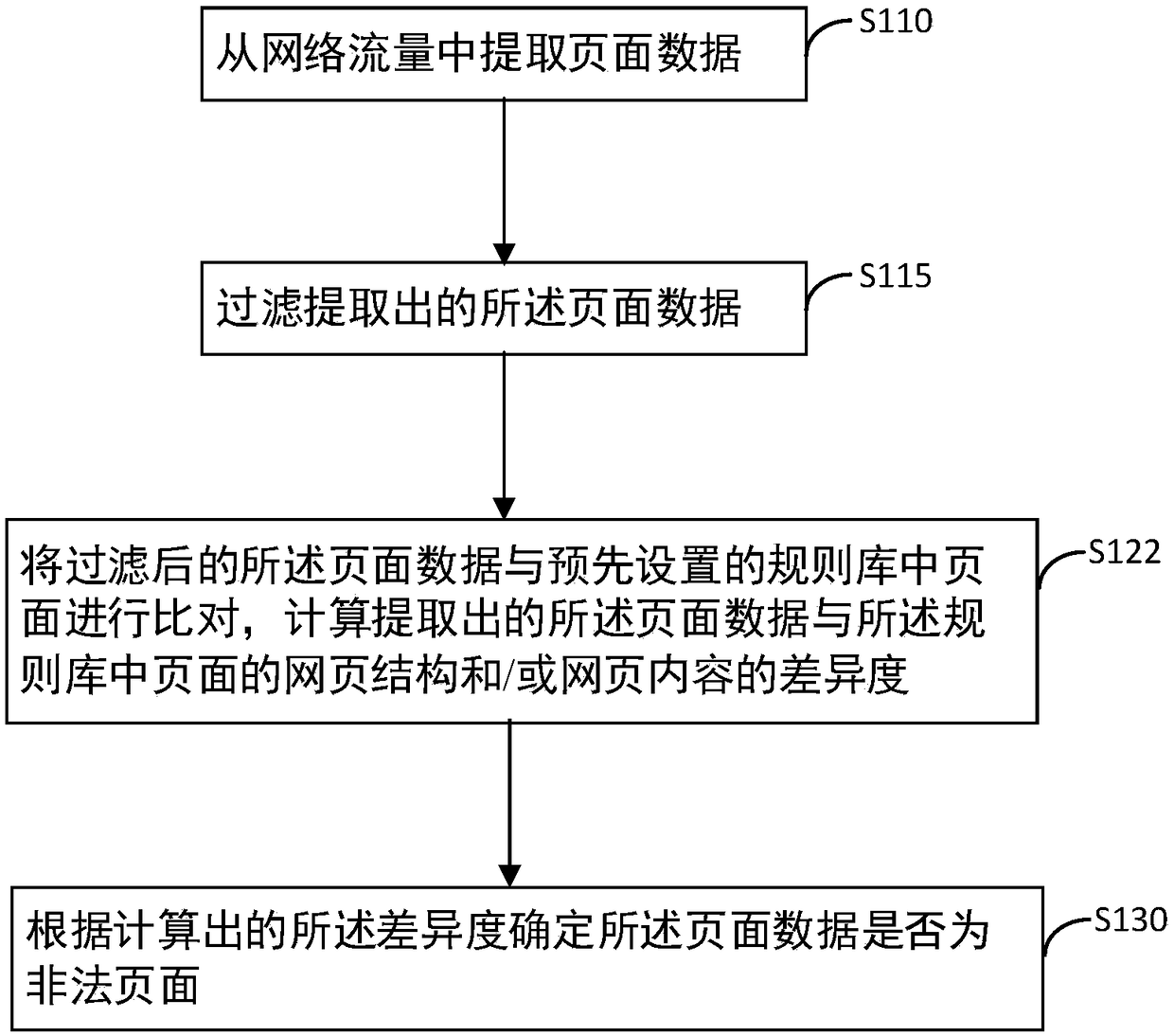
The invention provides an illegal-page detection method and device, an intrusion detection system and a computer readable storage medium. The illegal-page detection method includes the steps that pagedata is extracted from network flow; the extracted page data is compared with pages in a preset rule base, and the difference degree between the extracted page data and webpage structures and / or thewebpage content of the pages in the rule base is computed; according to the computed different degree, whether the page data is abnormal pages or not is determined. According to the illegal-page detection method and device, the intrusion detection system and the computer readable storage medium in the embodiment, the abnormal pages are determined from two dimensionalities of the structure and thecontent, the relevance ratio is greatly increased, and the false alarm rate is reduced; the abnormal pages are detected based on the fuzzy similarity degree, variety pages and unknown pages can be better detected, aggressive behaviors can be effectively avoided, and illegal websites are blown.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
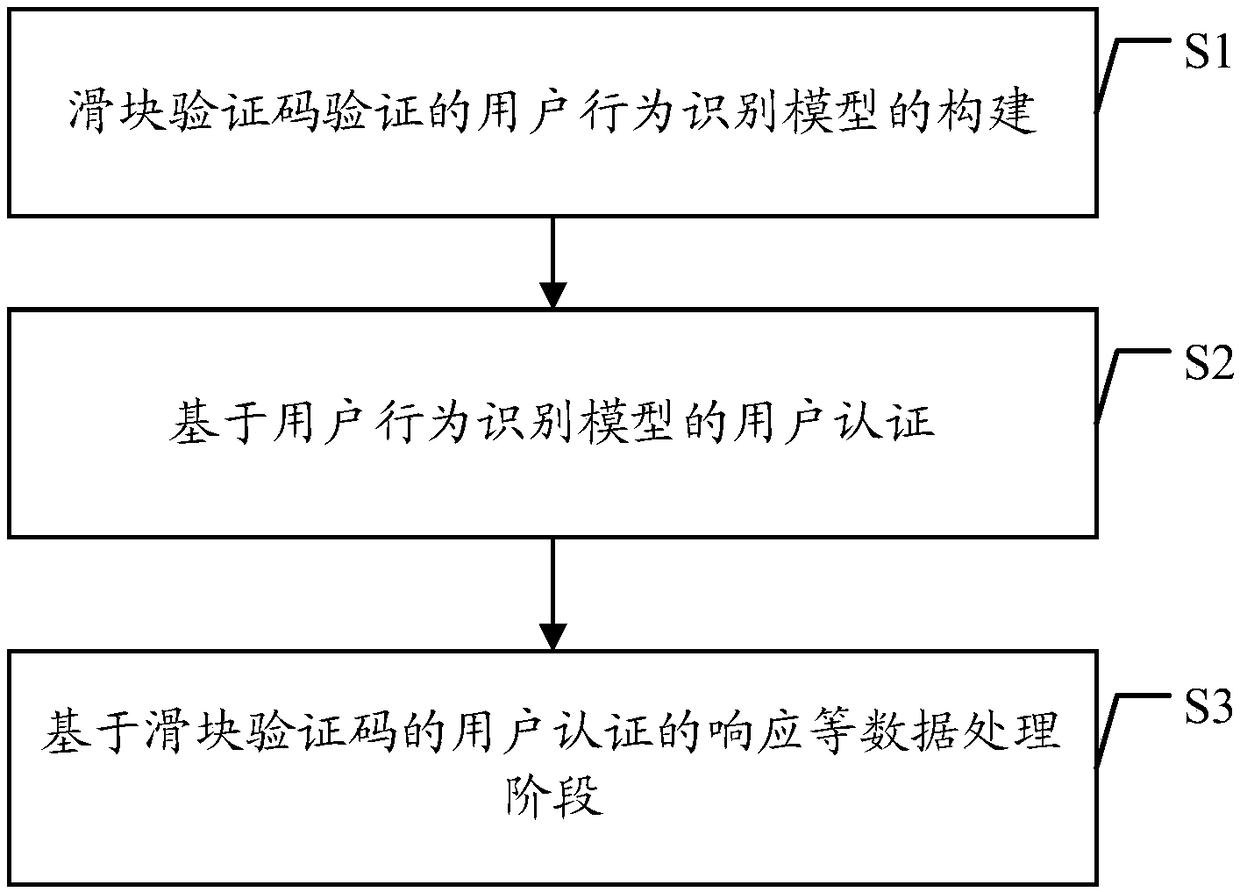
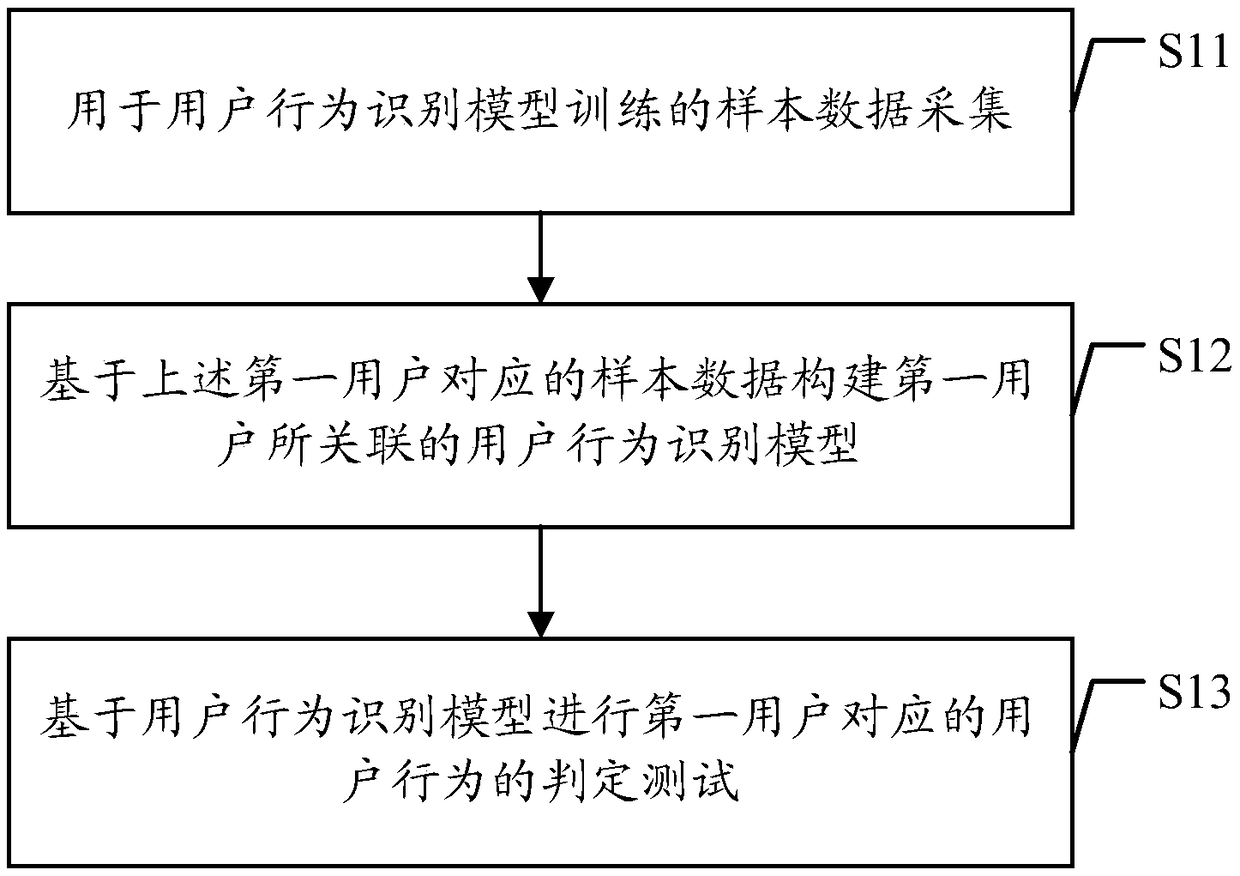
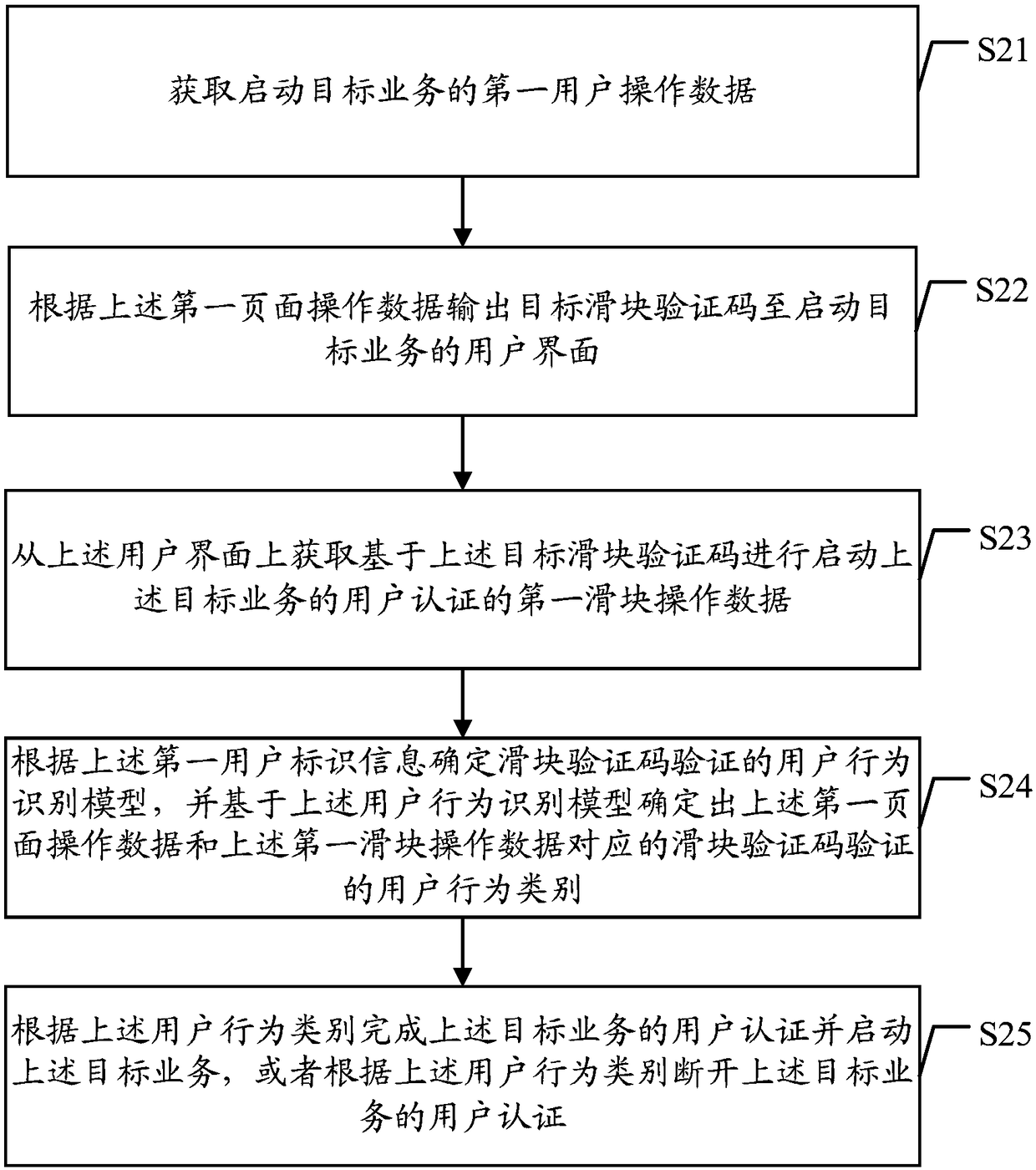
User behavior recognition method and device based on slider verification code verification
ActiveCN109241709AImprove authentication securityAvoid attackDigital data authenticationEnergy efficient computingInternet privacyUser authentication
The embodiment of the application discloses a method and a device for identifying user behavior based on slider authentication code verification. The method comprises the following steps: first user operation data for starting a target service is obtained, the first user operation data including first user identification information and first page operation data; A target slider verification codeis output to the user interface according to the first page operation data, and first slider operation data for user authentication based on the target slider verification code is obtained from the user interface; The user behavior identification model verified by the slider authentication code is determined according to the first user identification information, and a user behavior category corresponding to the first page operation data and the first slider operation data is determined based on the user behavior identification model; user authentication is completed or user authentication isdisconnected according to the user behavior category. By adopting the embodiment of the application, the user authentication security based on the slider authentication code authentication can be improved, the network attack of the slider authentication code authentication can be effectively prevented, and the security is higher.
Owner:PING AN TECH (SHENZHEN) CO LTD
Distributed key management system applied to urban rail transit
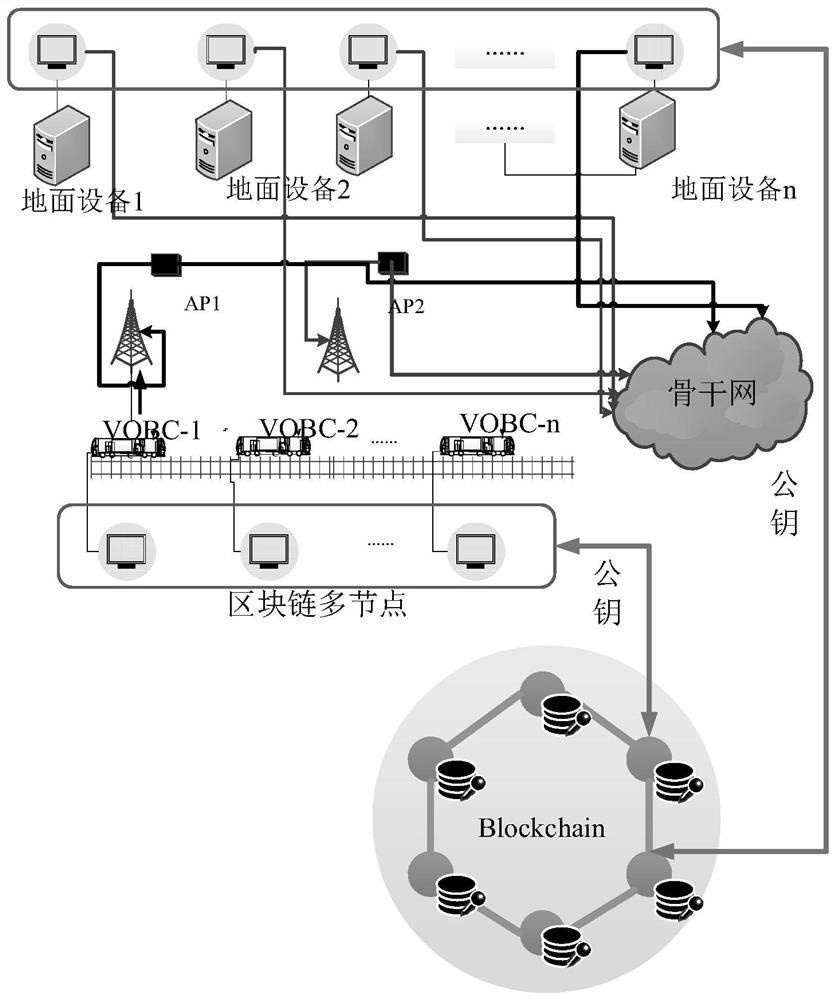
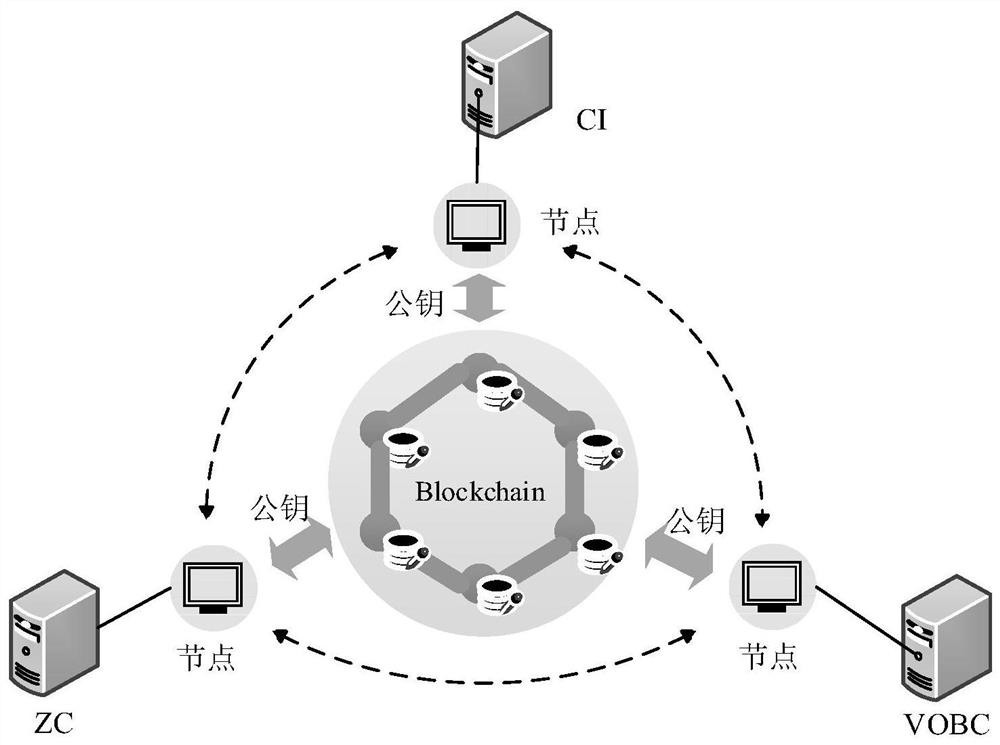
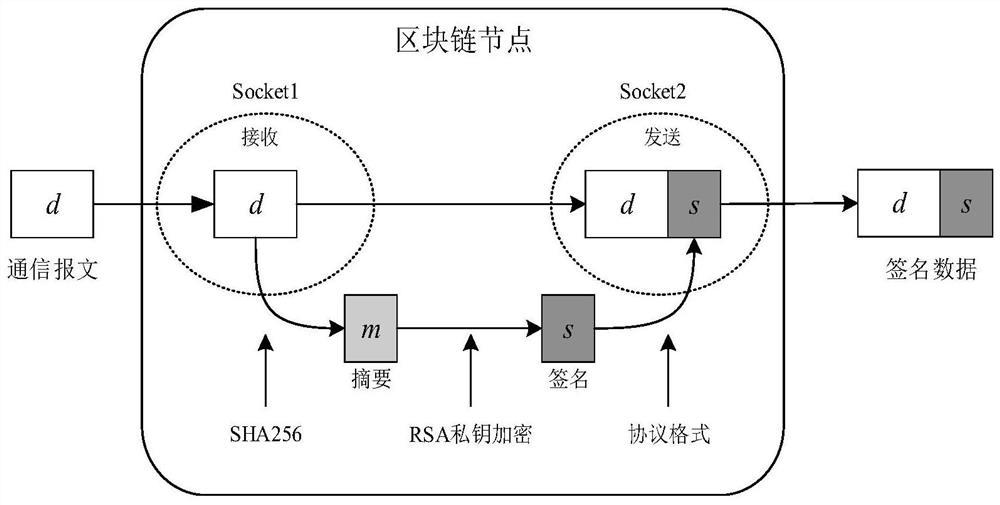
ActiveCN112003691AAvoid aggressive behaviorReduce lossesKey distribution for secure communicationFinanceComputer networkControl system
The invention discloses a distributed key management system applied to urban rail transit. The system comprises a block chain network composed of a plurality of block chain nodes and a plurality of train operation control subsystems, each train operation control subsystem is configured to be connected with one block chain node; for the train operation control subsystems connected with the block chain nodes, the block chain nodes connected with the train operation control subsystems realize communication with other external train operation control subsystems and realize signature and authentication of communication data packets among the train operation control subsystems. According to the invention, a distributed secret key management mechanism of the urban rail transit is realized, and the safety and the anti-attack capability of an urban rail transit control system are improved.
Owner:BEIJING JIAOTONG UNIV
Multi-information fusion human exoskeleton robot control protection system
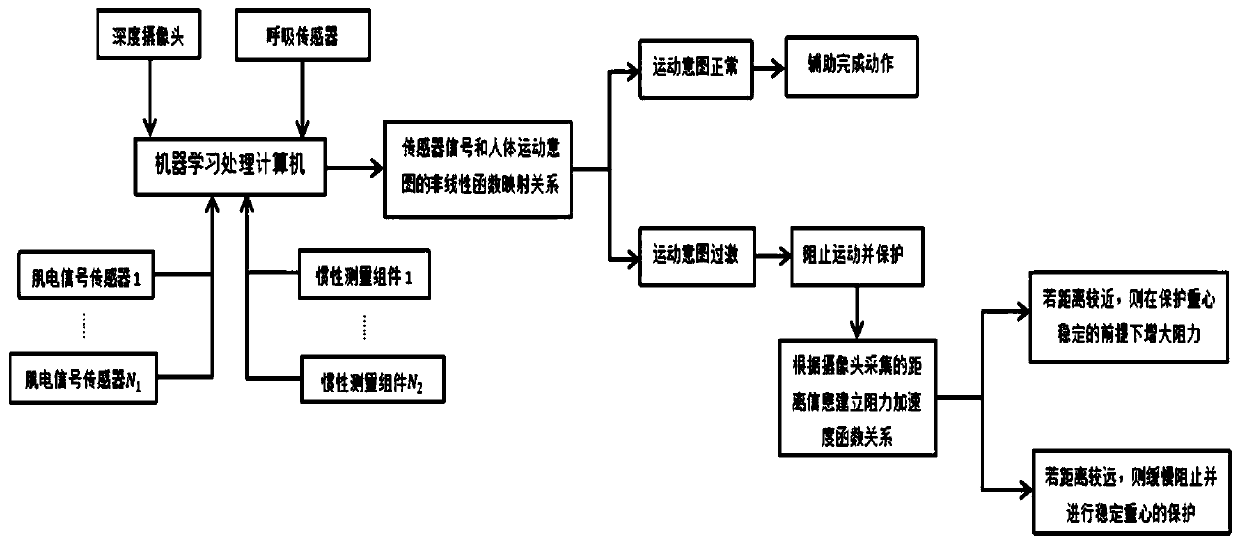
ActiveCN110125909AAvoid aggressive behaviorProtect against damageProgramme-controlled manipulatorRespiratory organ evaluationHuman bodyExoskeleton robot
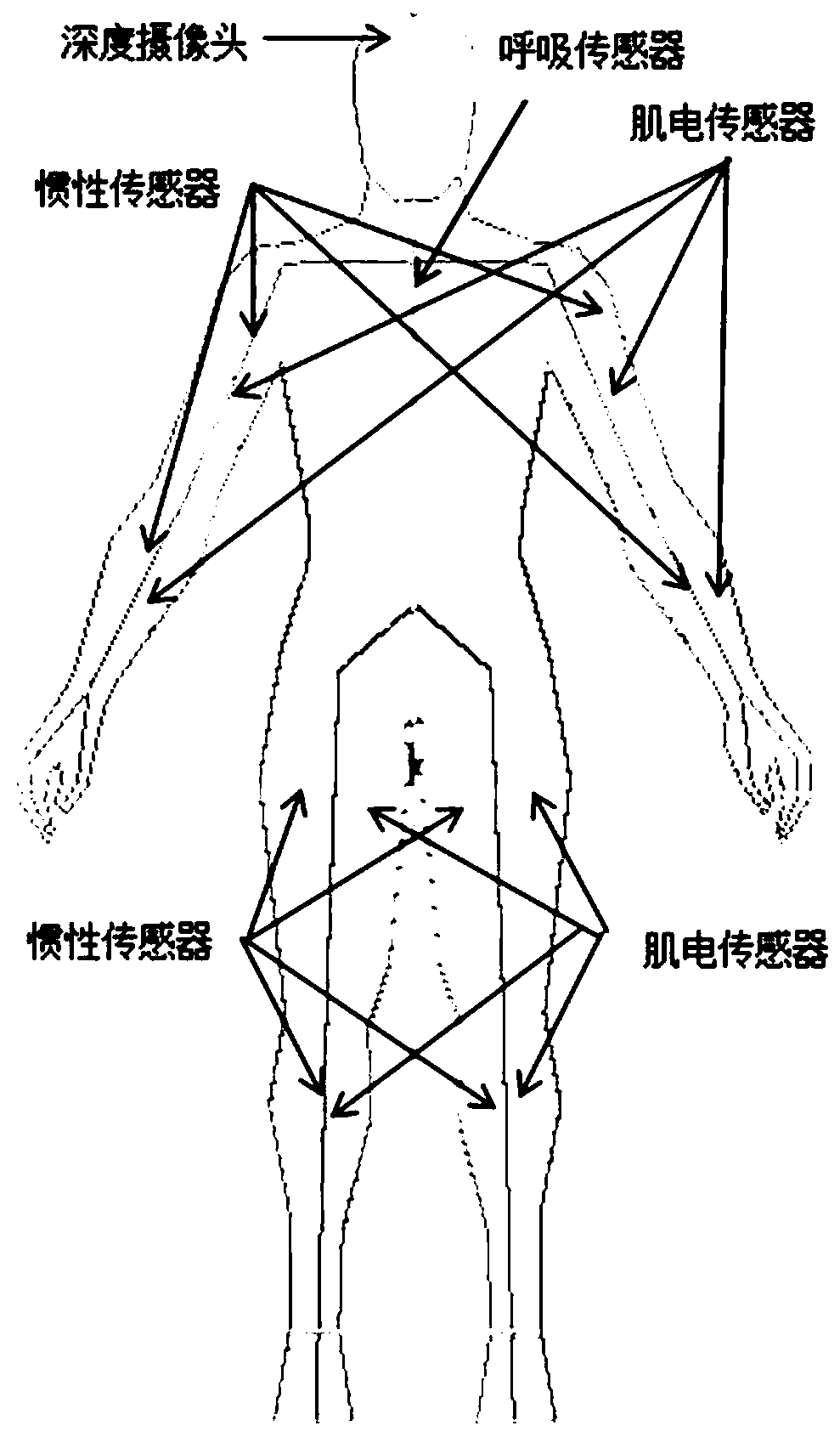
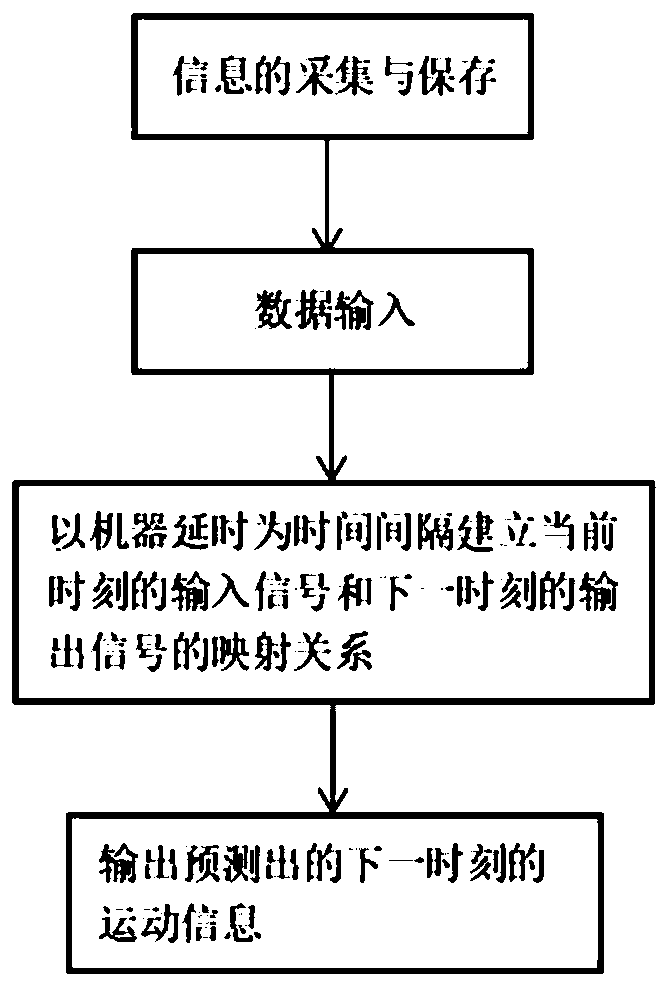
The invention discloses a multi-information fusion human exoskeleton robot control protection system. The system comprises a plurality of inertia measurement assemblies, a plurality of electromyogramsensors, respiration sensors, a depth camera and machine learning processing computers, wherein the inertia measurement assemblies and the electromyogram sensors are installed at arms and legs of a human body, the respiration sensors are installed on a chest, the depth camera is worn on a head, and the machine learning processing computers are installed at any position of the human body; effectivedata acquired by all the sensors at a certain moment are used as input of an LSTM neural network based on a BPTT algorithm, the sum of time consumed by processing a machine learning algorithm throughthe computers and the maximum delay time of receiving control signals by a steering engine at each position of the robot from the moment is used as a time interval, a control signal representing a movement intention of the human body at the moment after the time interval is used as output, a nonlinear function mapping relation which is difficult to express through an analytic expression in engineering is established through neural network training, the movement intention of the human body at the next moment is judged through the action at the moment, so that a function that the correspondingcontrol signal is output is achieved.
Owner:南京师范大学镇江创新发展研究院
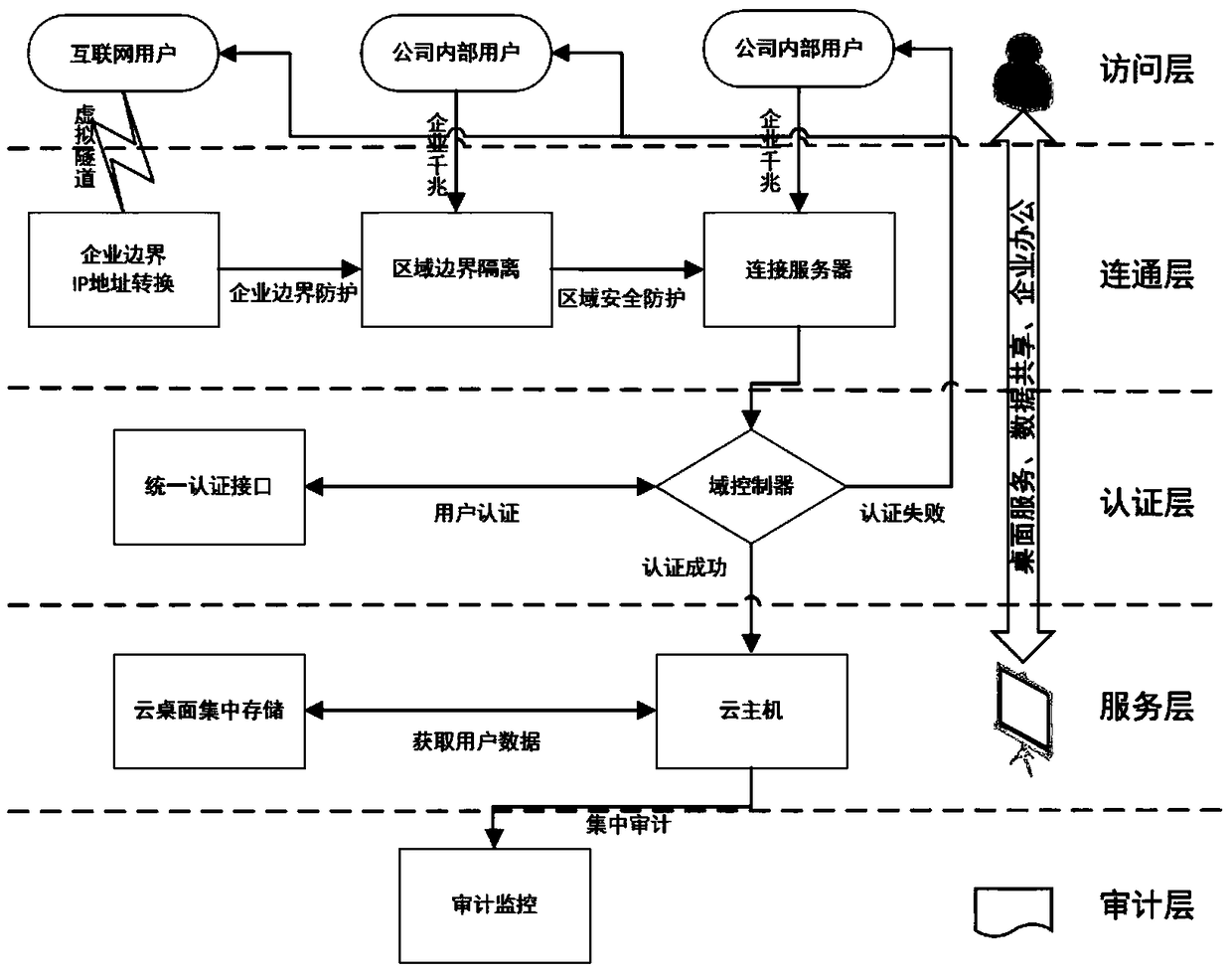
A virtual cloud desktop security access method based on deep protection
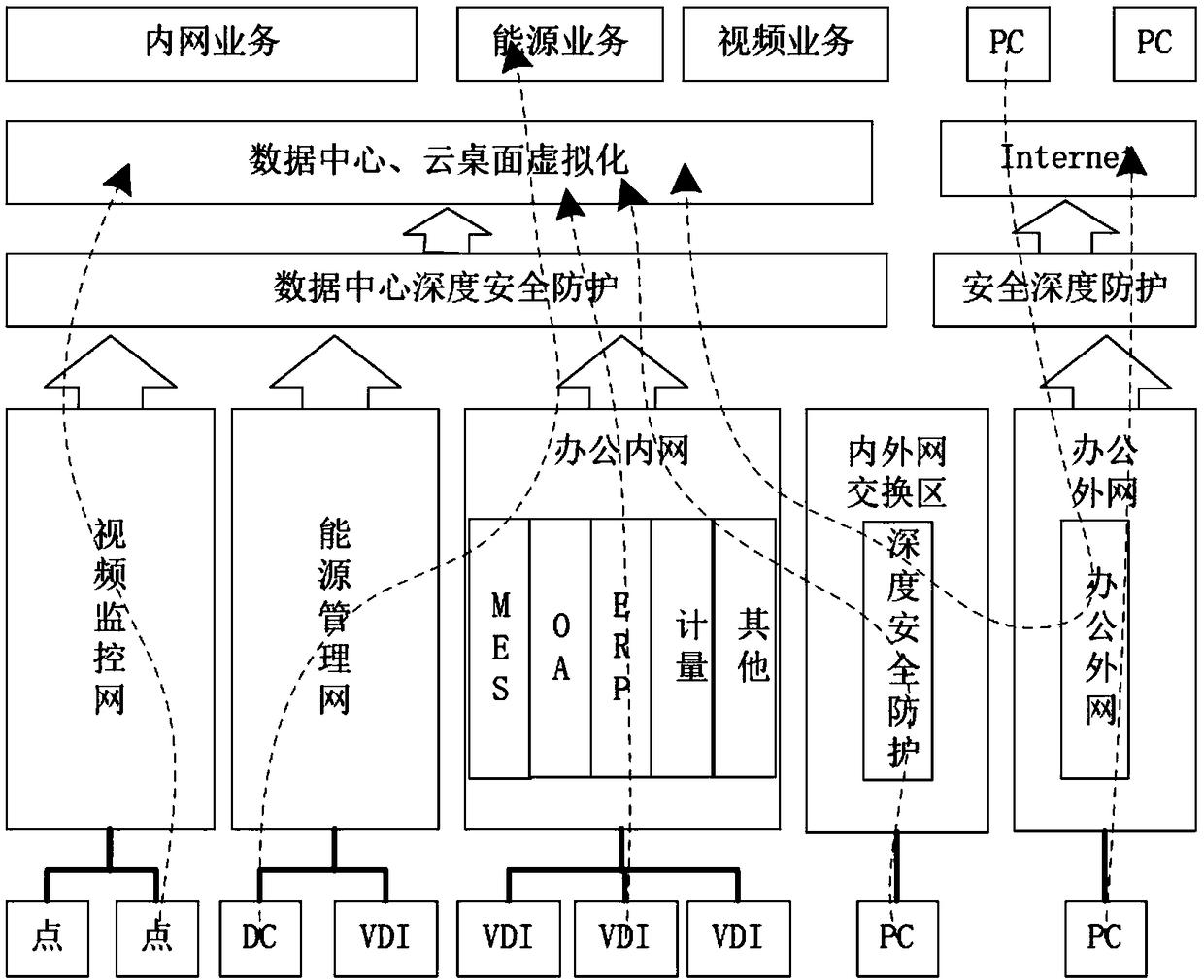
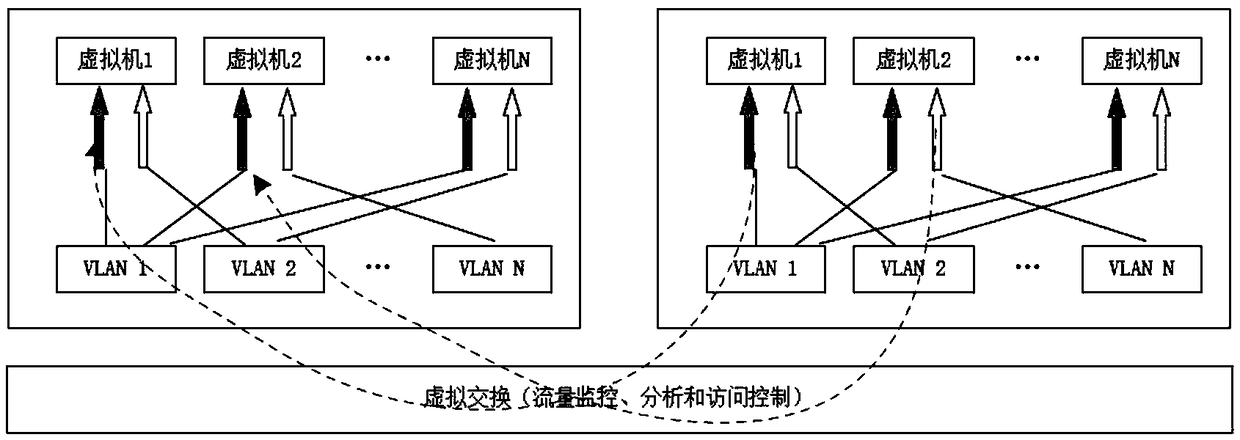
InactiveCN109472136AComprehensive audit monitoringNon-stop operationPlatform integrity maintainanceExecution for user interfacesVirtualizationAccess method
The invention relates to a virtual cloud desktop security access method based on deep protection, which comprises the following steps of: analyzing according to a business flow direction, reasonably dividing security areas, analyzing according to the business flow direction, establishing a security area model, and dividing the security area model into five security areas, namely a security servicearea, a wired access area, a wireless access area, a security support area and a security interconnection area; And performing virtual deep protection, and for security threats faced by a virtualization layer, realizing isolation of a virtual network by designing a virtual network identifier to route and forward a data frame. Through the functions of virus prevention, access control, intrusion detection / intrusion protection, virtual patches, host integrity monitoring, log auditing and the like, comprehensive protection of a virtual host and a virtual system is achieved, different regional networks, different users and different applications are achieved, and different depth protection strategies are adopted to achieve deep-level safety protection of the virtual cloud desktop.
Owner:SD STEEL RIZHAO CO LTD
Attack detection method of spanning tree protocol based on credible switchboard
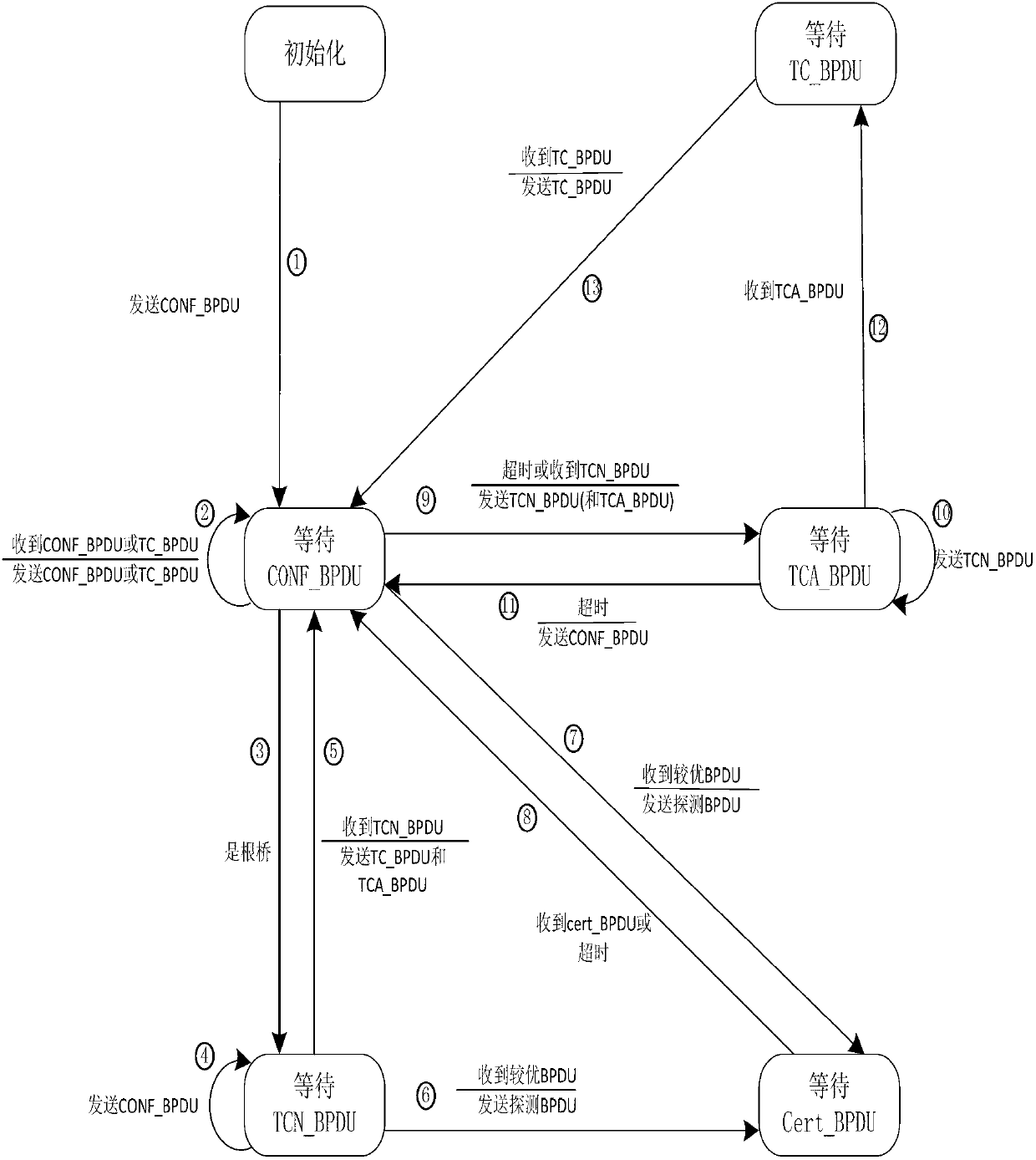
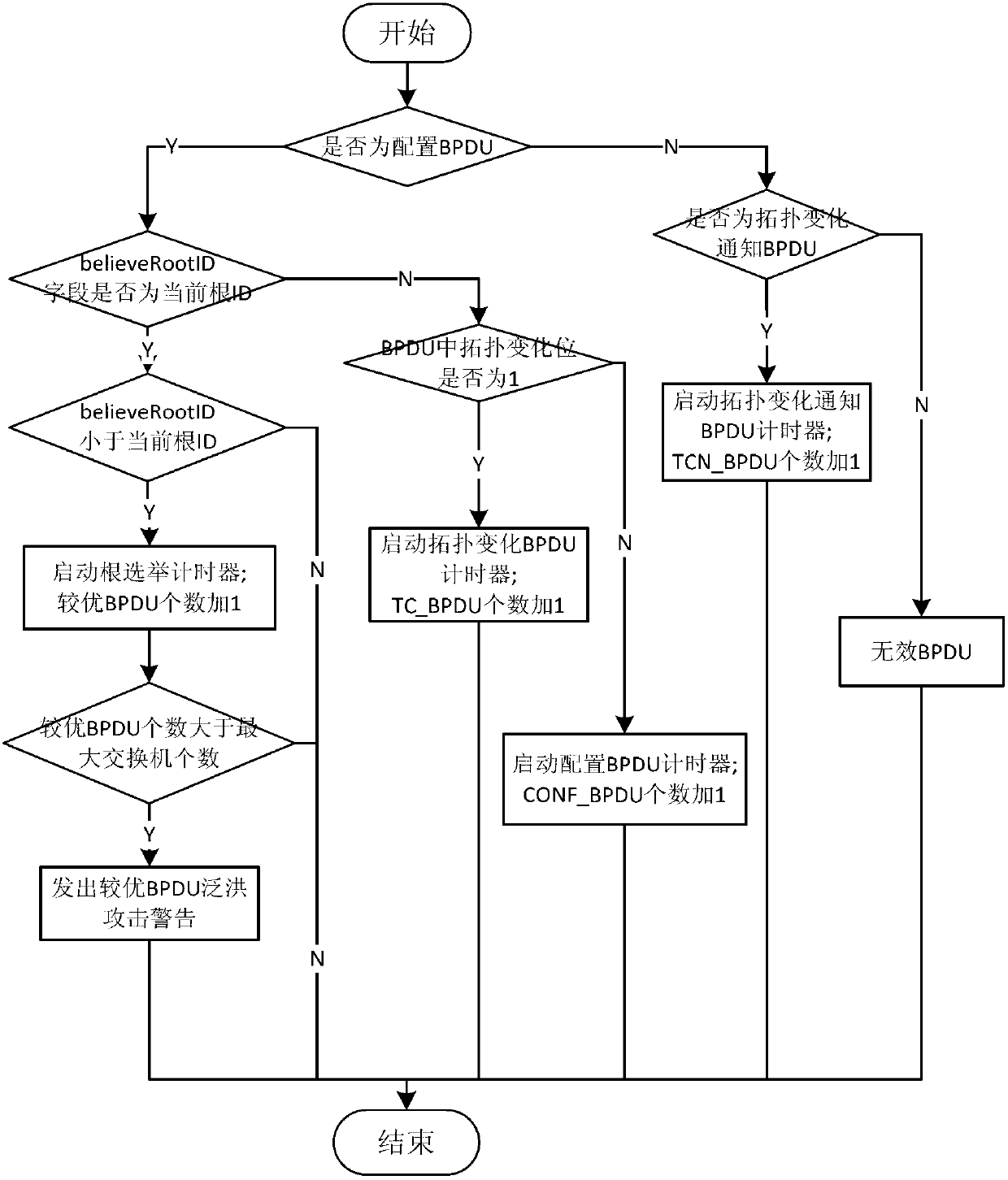
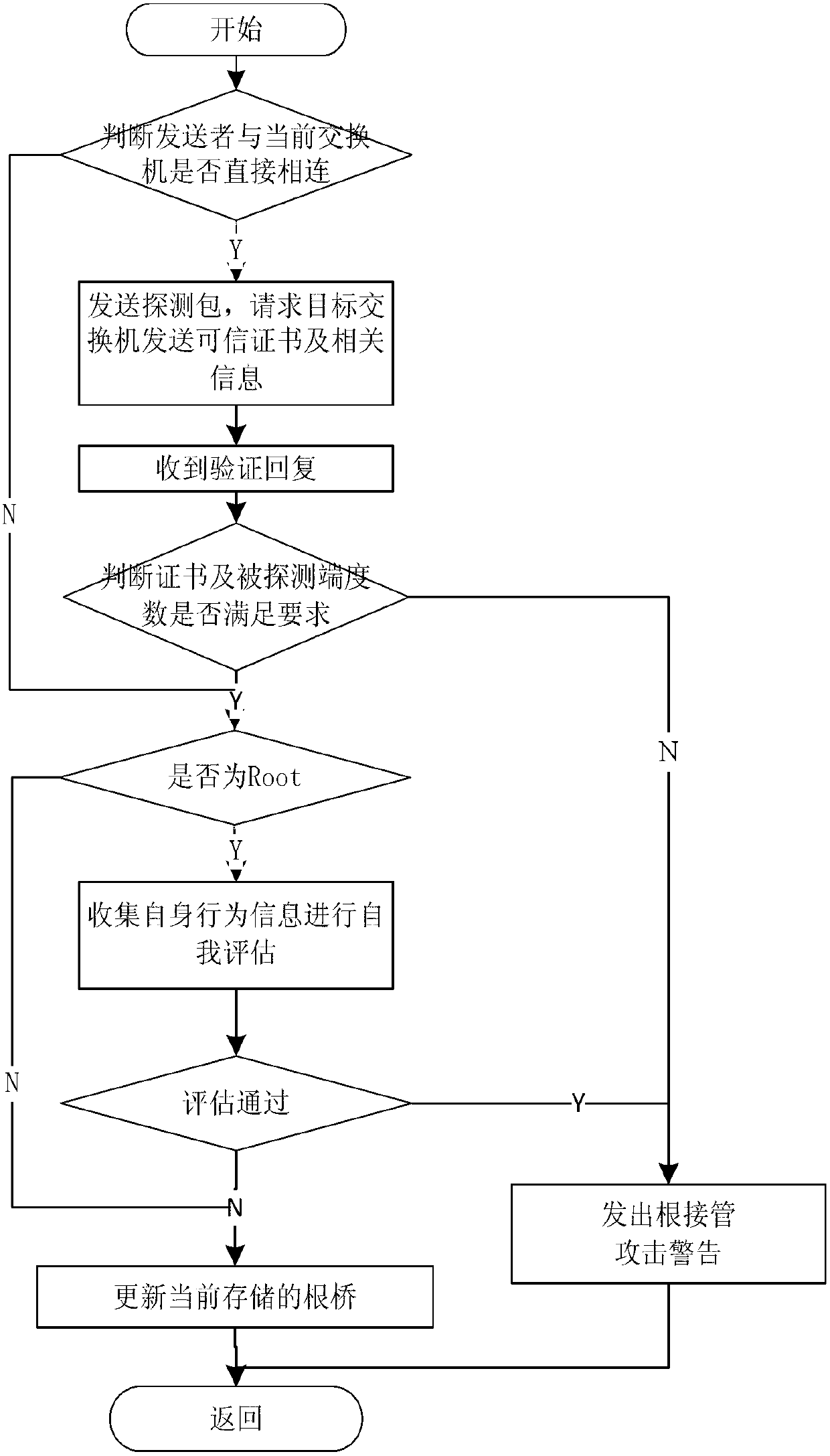
ActiveCN103139219AReduce workloadAvoid aggressive behaviorData switching networksTimerProtocol data unit
The invention discloses an attack detection method of a spanning tree protocol based on a credible switchboard. An interior monitoring module is utilized to conduct monitoring for an attack behavior which is generated by the switchboard, an exterior protection module is utilized to conduct detecting for an attack threat from the exterior of the switchboard, and therefore, full attach detection of the spanning tree protocol is achieved. The method includes that firstly, according to the condition that in different stages, the switchboard waits different bridge protocol data units (BPDU), a state image is drawn, according to a state transfer condition, whole operation behavior of the switchboard is monitored so as to detect an attach behavior generated by the equipment, then the BPDU from the exterior is classified, a timer and a counting method are adopted to detect flooding attack, finally, when received BID is less than the BPDU of a current root BID, an explorer packet is sent to conduct validity checking on a target switchboard, and if the BPDU is a root bridge, whether the root bridge needs changing is decided after self-assessment so as to detect whether a root connection pipe is attached.
Owner:BEIJING UNIV OF TECH
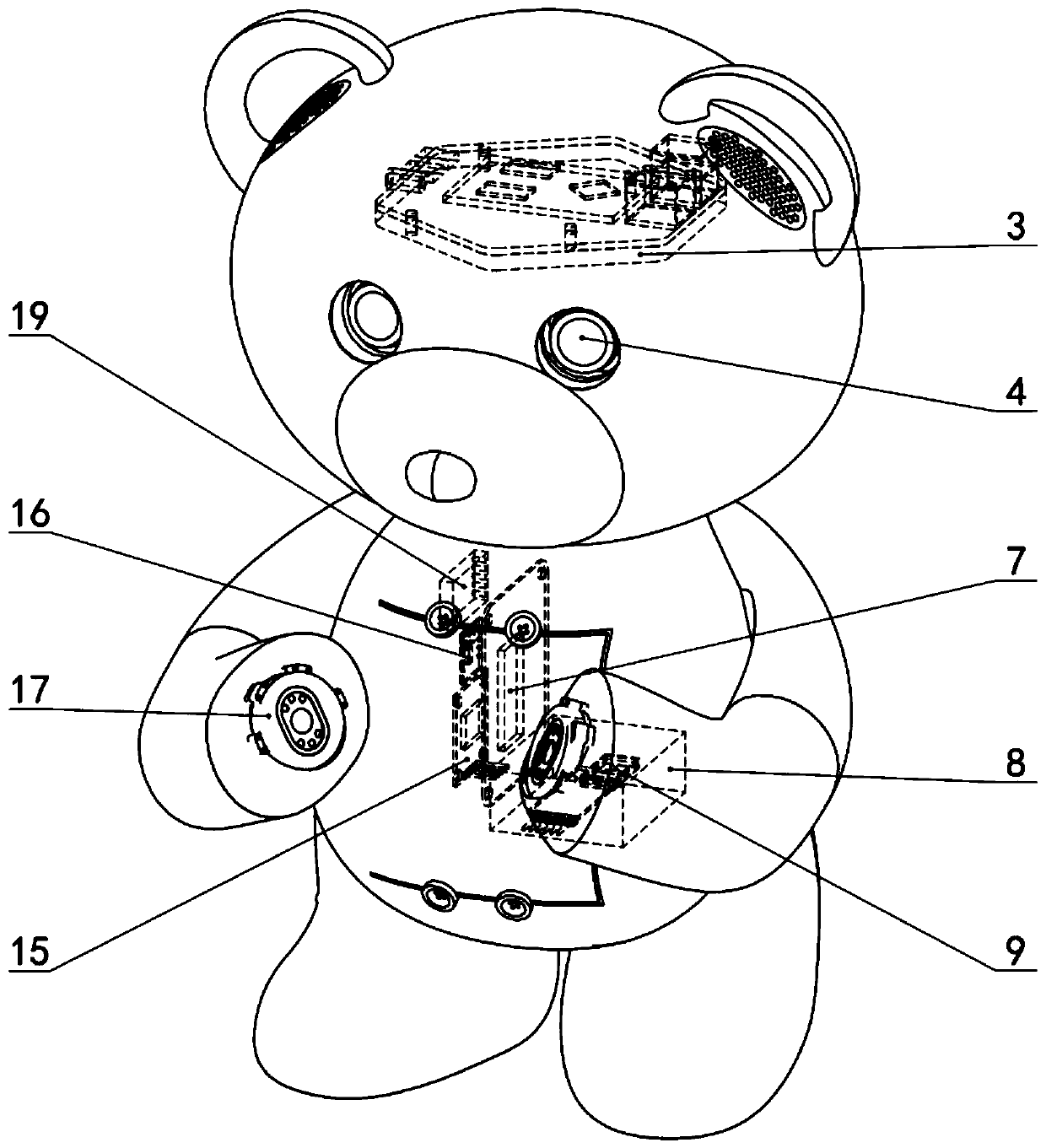
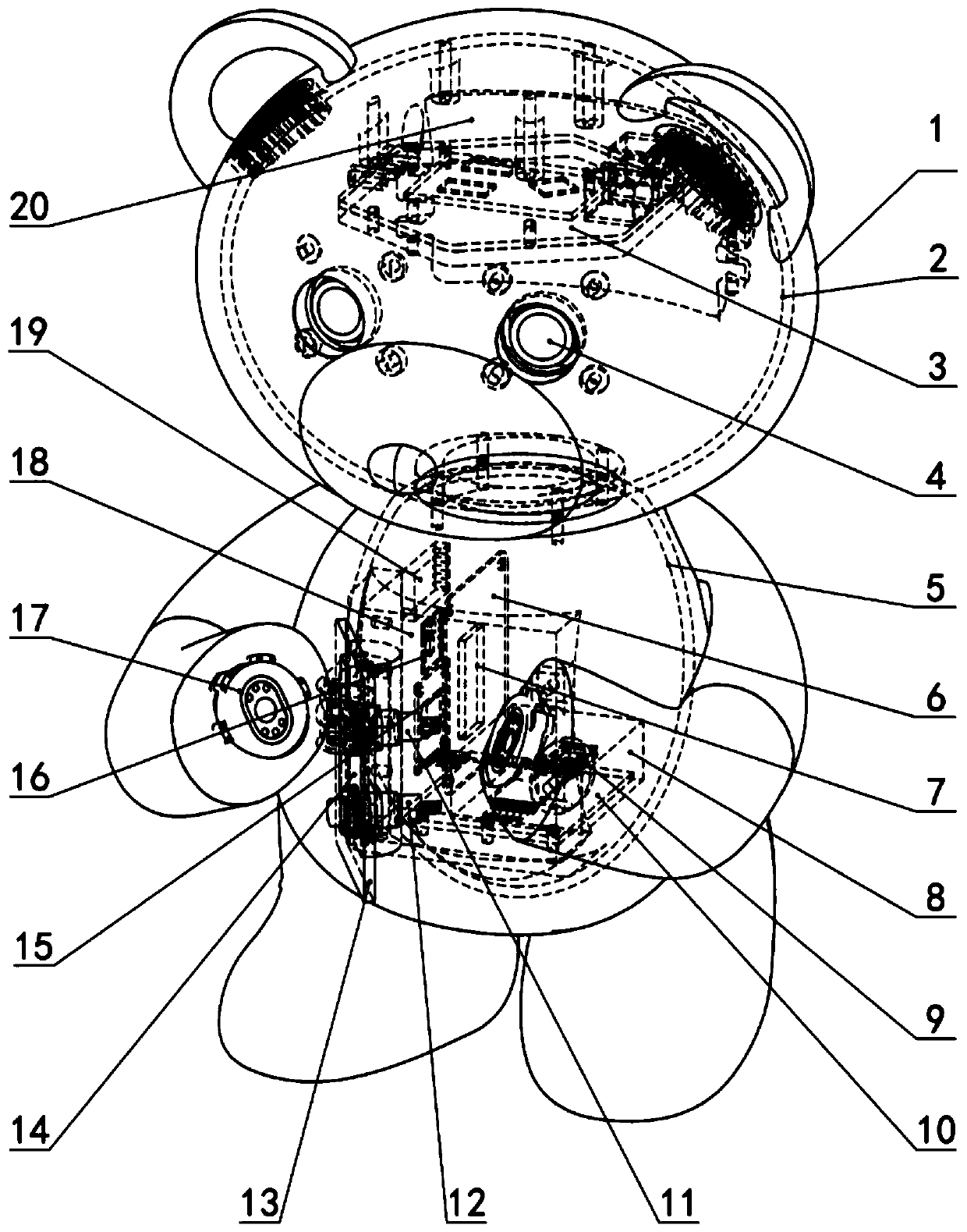
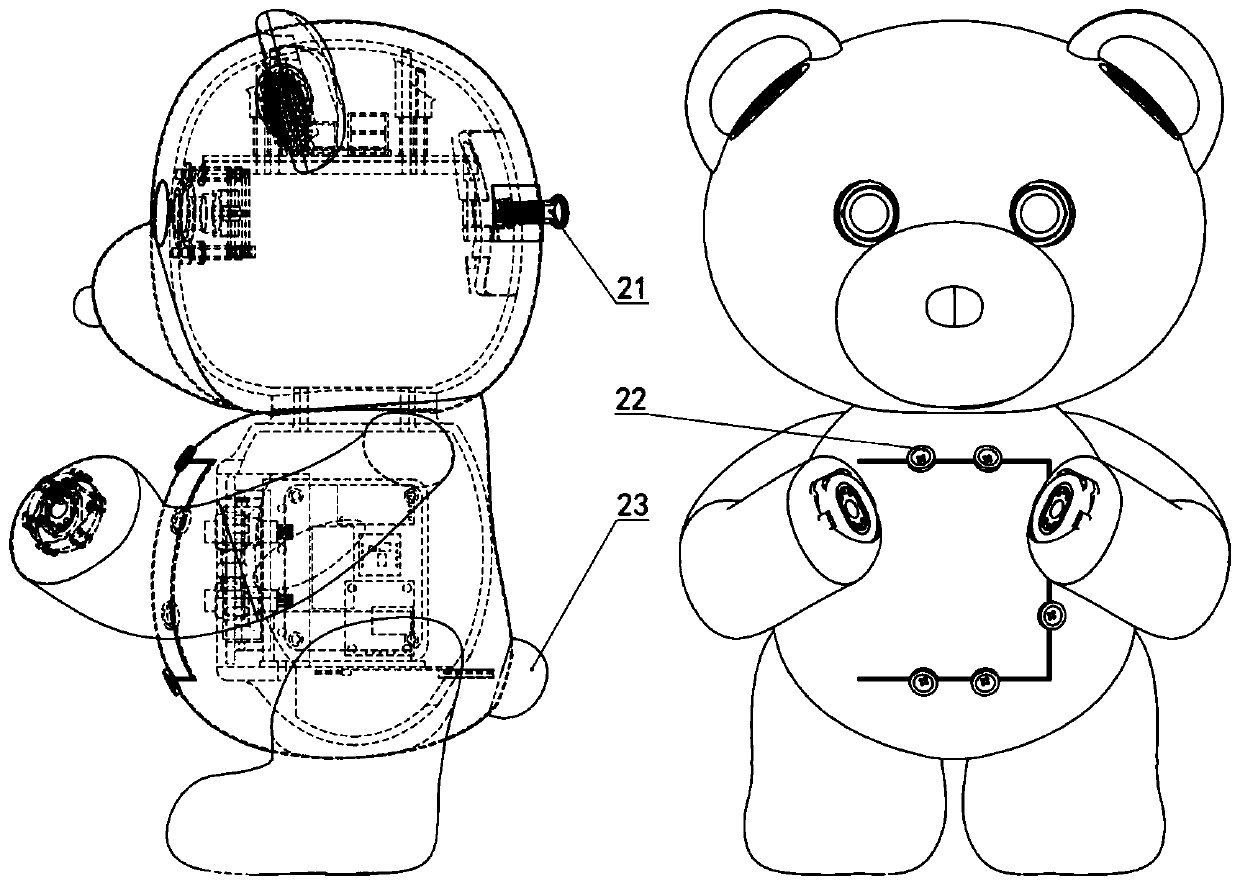
Psychological accompanying robot and emotion supporting method
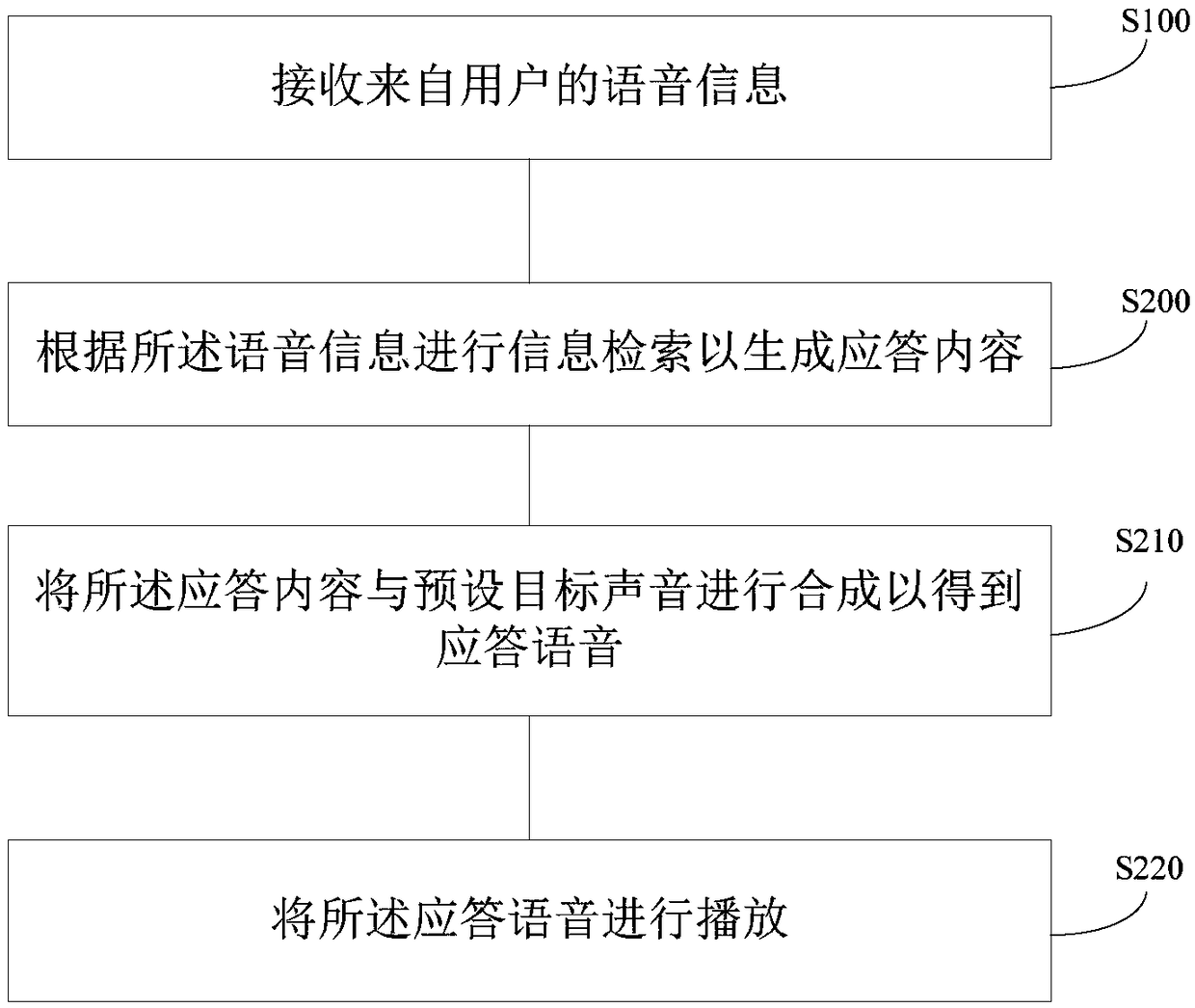
The invention discloses a psychological accompanying robot and an emotion supporting method. The psychological accompanying robot comprises an emotion recognizing module, an emotion comforting and supporting module, an operational analysis control module and a data transmission module, wherein all the modules are integrated to a mechanical shell and are arranged in a doll cotton cover. The psychological accompanying robot acquires the information such as the expressions, actions and languages of a user through the emotion recognizing module, analyzes and judges the emotions through the operational analysis control module, generates an emotion supporting strategy and then achieves psychological accompanying through the emotion comforting and supporting module. Communication between the robot doll and a mobile phone can be achieved through the data transmission module, and integration of all the information and sharing of equipment hardware can be achieved. According to the psychologicalaccompanying robot and the emotion supporting method, the psychological accompanying robot can be carried along as a mascot or a pendant, interaction can be achieved through the modes such as the expressions, actions and sounds to carry out psychological accompanying and emotion comforting, and the psychological accompanying robot can become a most faithful friend and a companion of the user.
Owner:SOUTH CHINA UNIV OF TECH
Method for preventing Dos aggression of business support system
ActiveCN101415000AImprove securityAccurately process the requestFinanceData switching networksSupporting systemUser identifier
The invention discloses a method of a service supporting system used for preventing Dos attack; when the user initiates service transaction request, the user ID is used to generate a user transaction behavior index counter at the upstream link of request disposal of the service supporting system; during one counting period, when the user transacts the service once by the service supporting system, the corresponding user transaction behavior index counter is counted and then compared with the user transaction behavior threshold; if the count of the counter exceeds the allowance of the threshold, the service request is refused in the link; if the count of the counter does not exceed the allowance of the threshold, the service request is allowed to continue to be processed in the downstream link of the service supporting system. The method starts from the application layer, analyses the normal operation index of the user, utilizes the unusual threshold to judge the attack behavior at the upstream link of the service supporting system, blocks the attack request to be transmitted to the downward request processing system when the Dos attack occurs, thus achieving the purpose of preventing the Dos attacks.
Owner:CHINA MOBILE GROUP SICHUAN
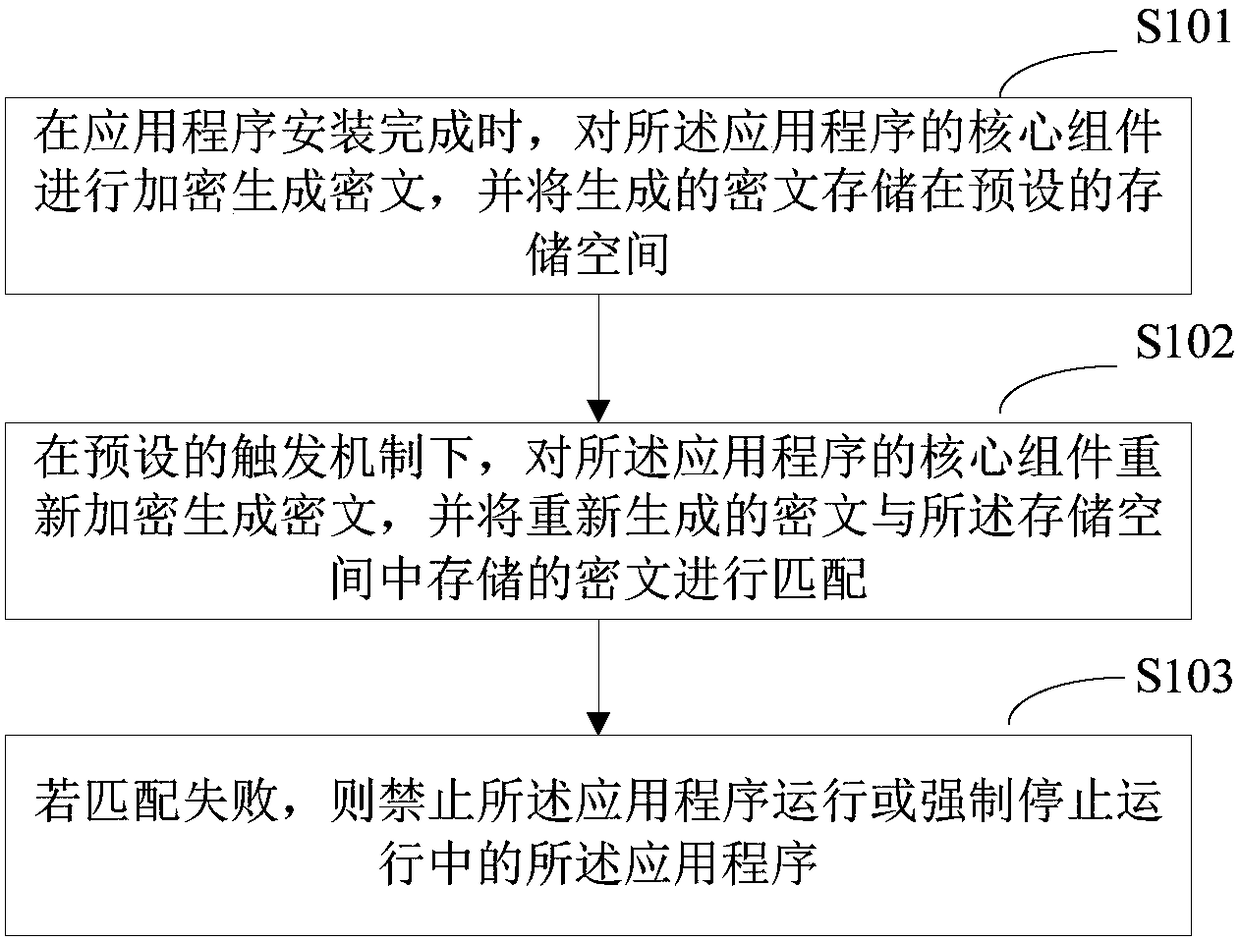
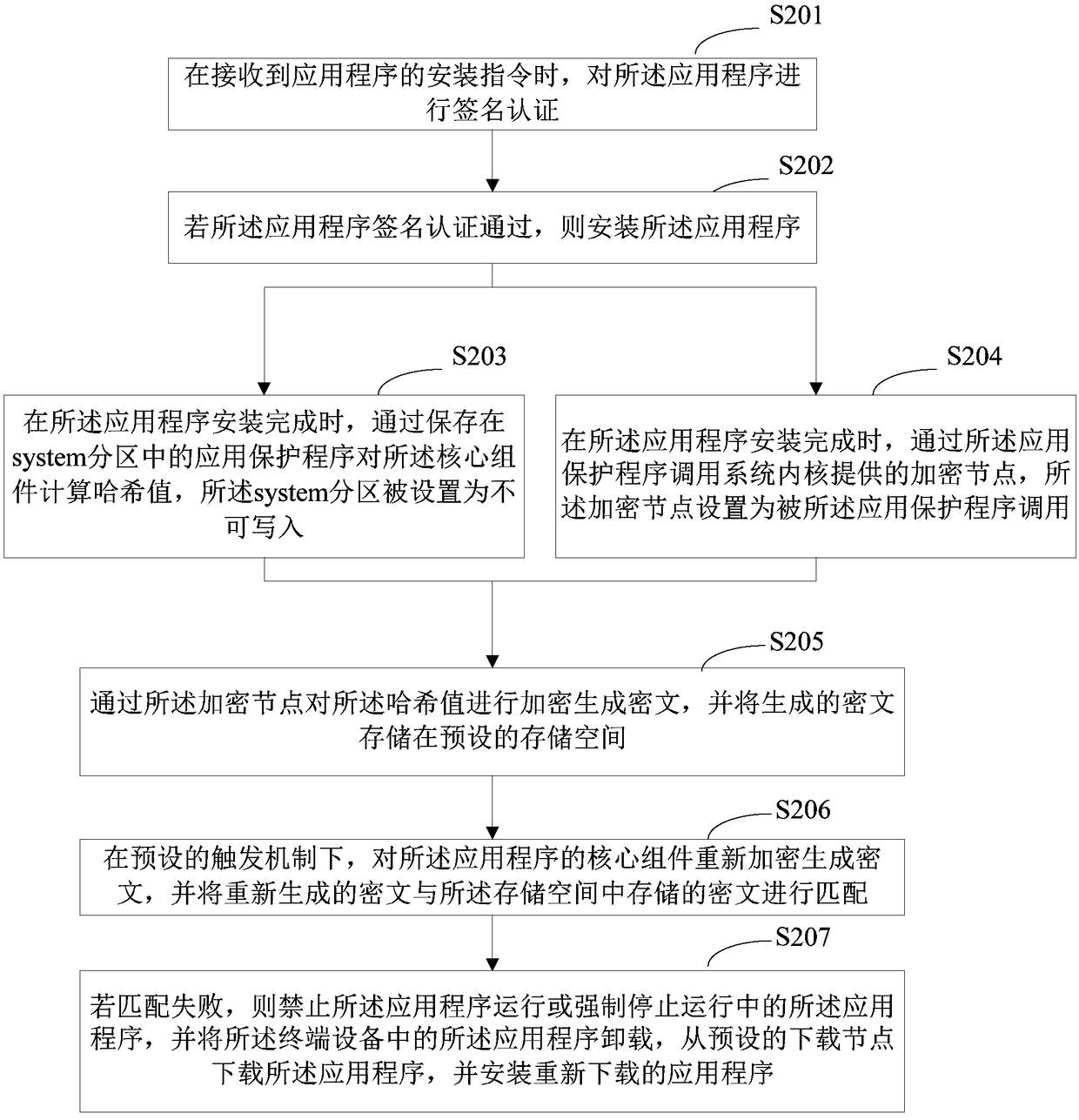
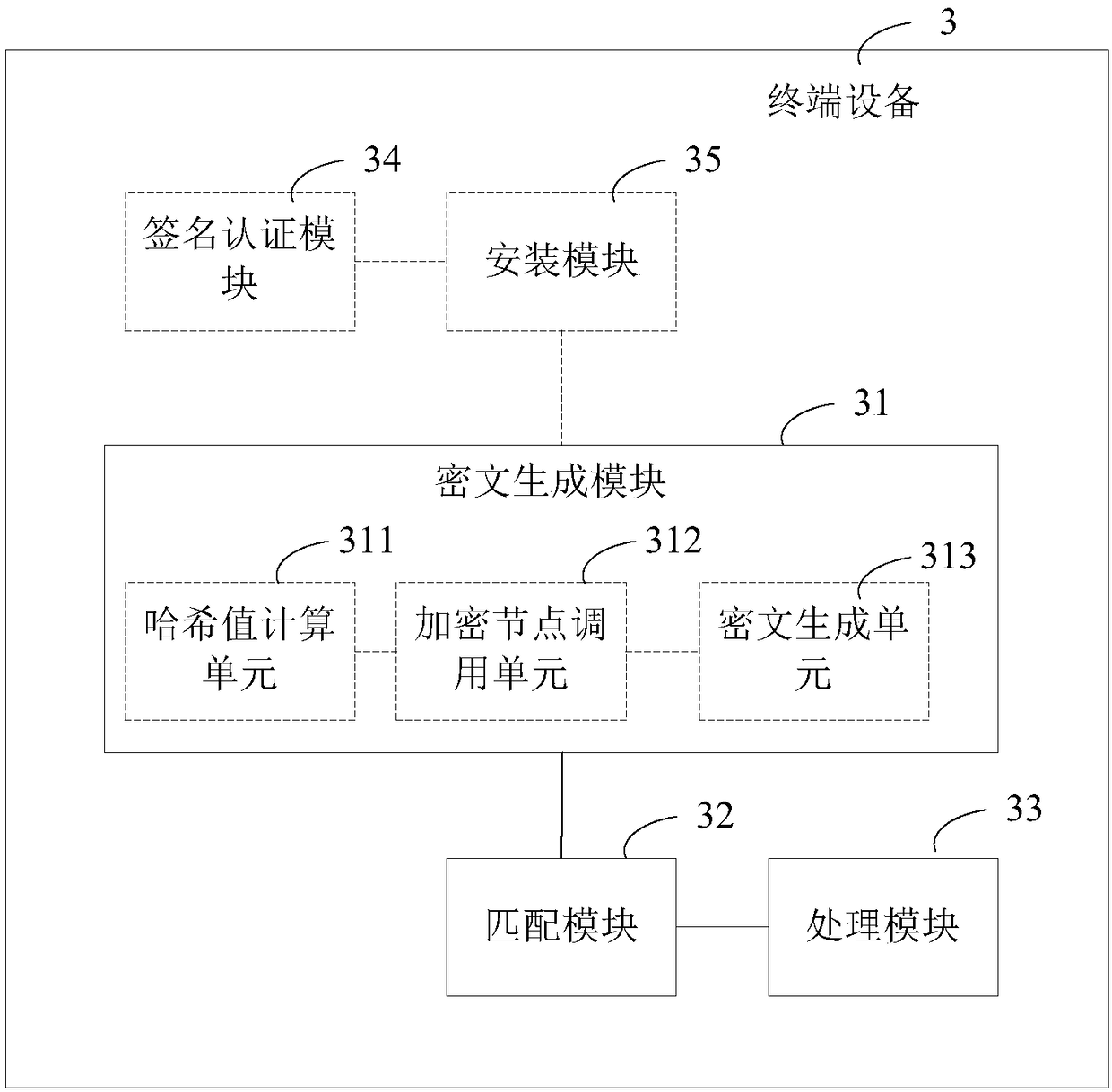
Verification method for application program, terminal equipment and storage medium
ActiveCN108229144AGuaranteed legalityAvoid aggressive behaviorPlatform integrity maintainanceCiphertextValidation methods
The invention relates to the technical field of information security and provides a verification method for an application program, terminal equipment and a storage medium. The method comprises the steps that after the application program is installed, a core assembly of the application program is encrypted to generate ciphertext, the generated ciphertext is stored in a preset storage space, undera preset trigger mechanism, the core assembly of the application program is encrypted again to generate the ciphertext, the newly-generated ciphertext is matched with the ciphertext stored in the storage space, and if matching fails, the application program is forbidden from running or the running application program is forced to be stopped. According to the verification method, the legality of the installed application program can be verified.
Owner:PAX COMP TECH SHENZHEN
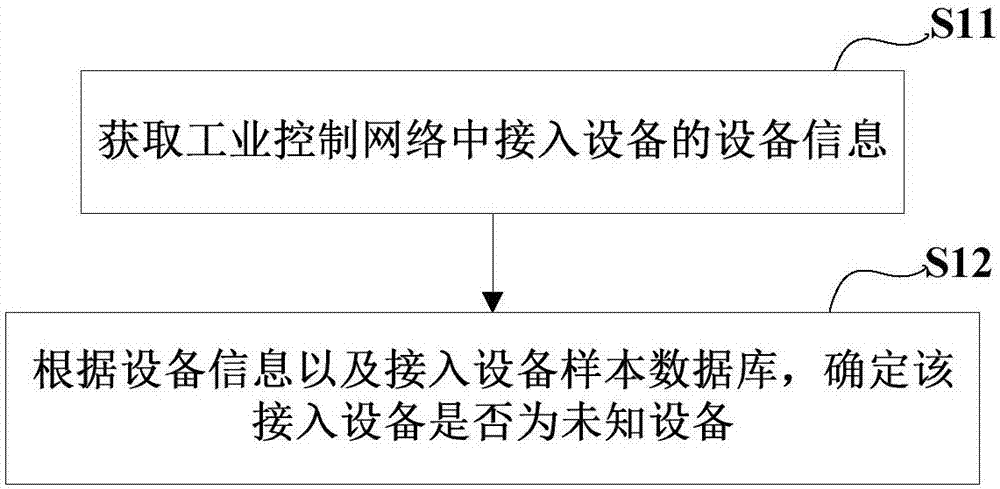
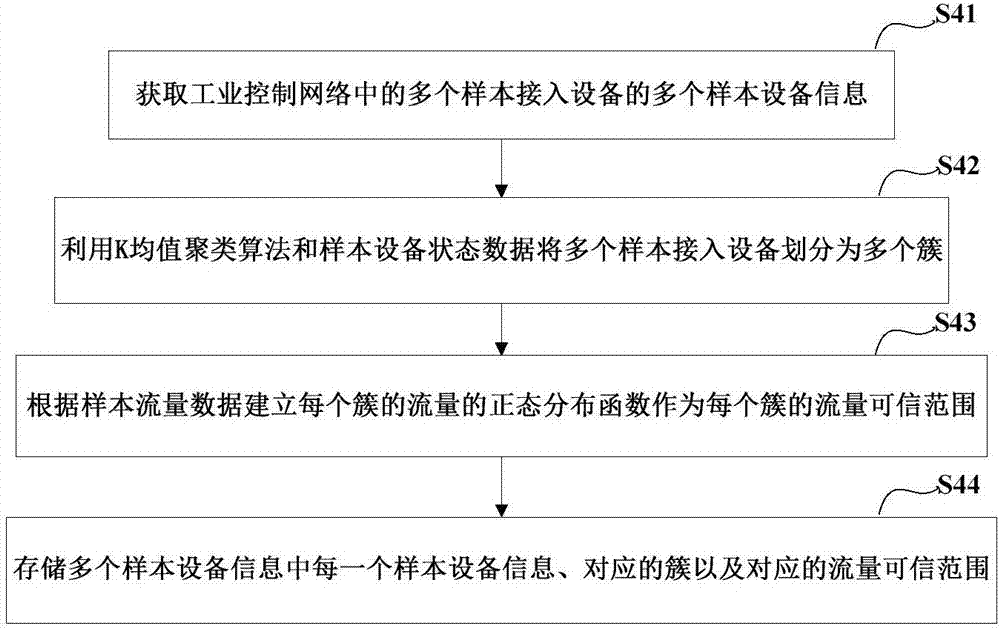
Method, apparatus and system for identifying access device of industrial control network
PendingCN106982209AEfficient identificationAccurate identificationCharacter and pattern recognitionDigital data authenticationComputer networkNetwork attack
Owner:BEIJING KUANGEN NETWORK TECH
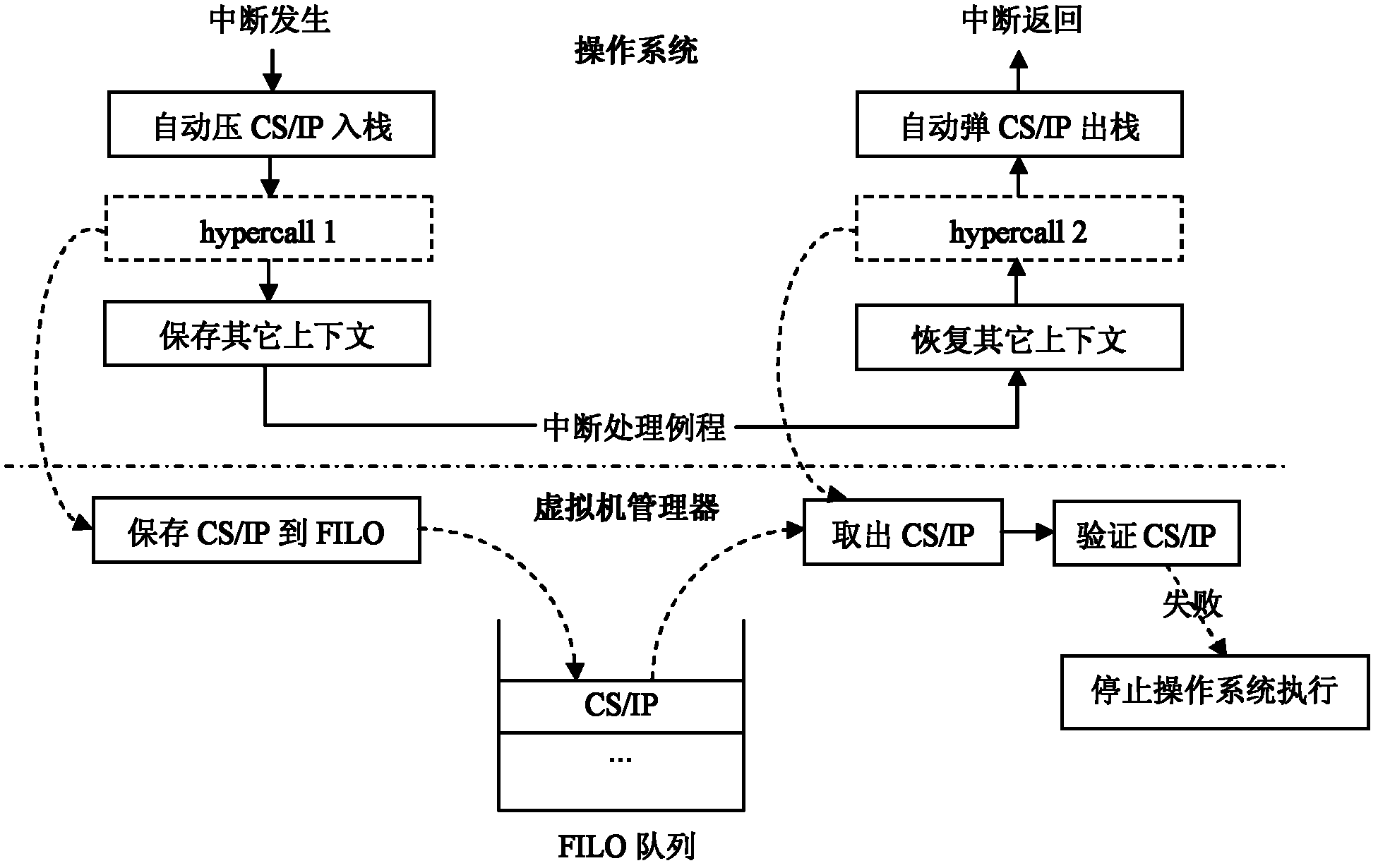
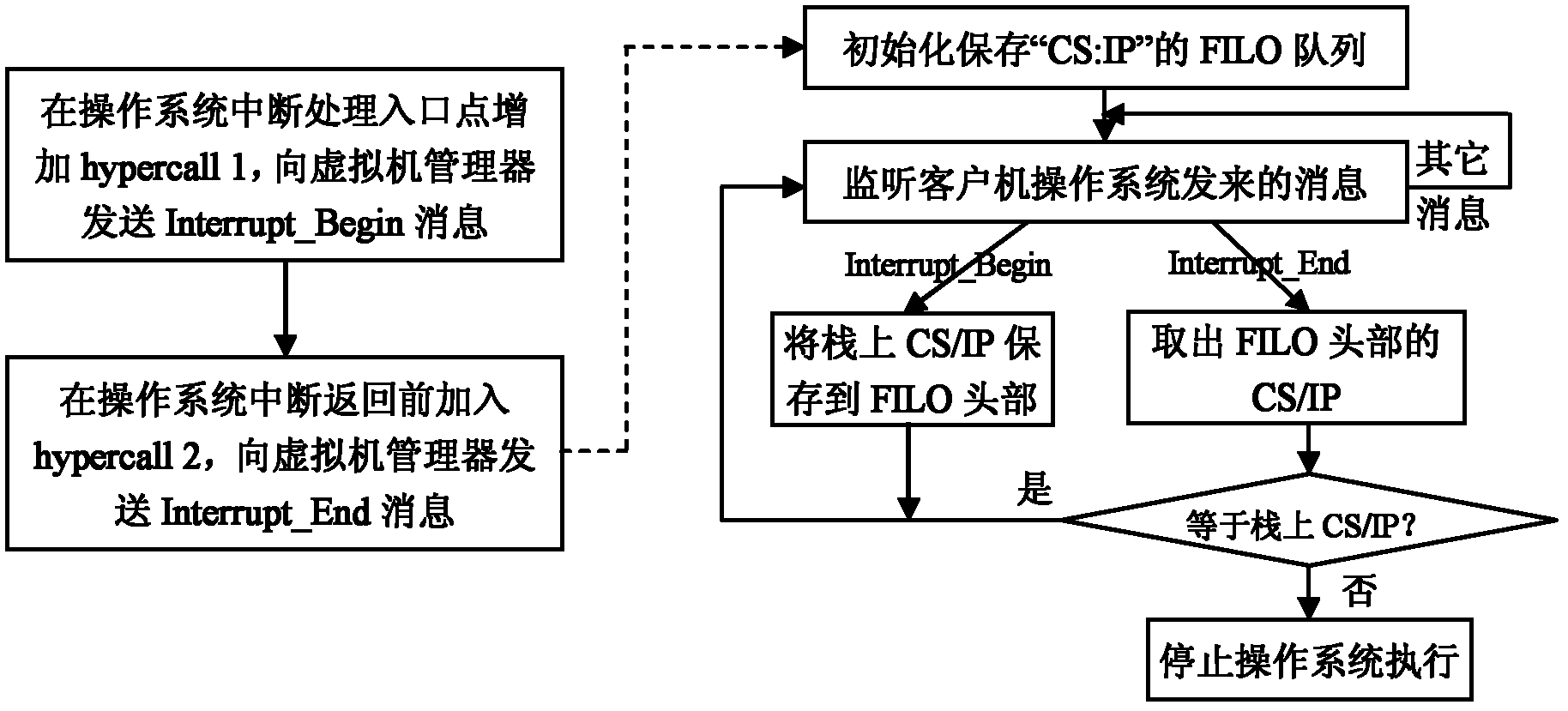
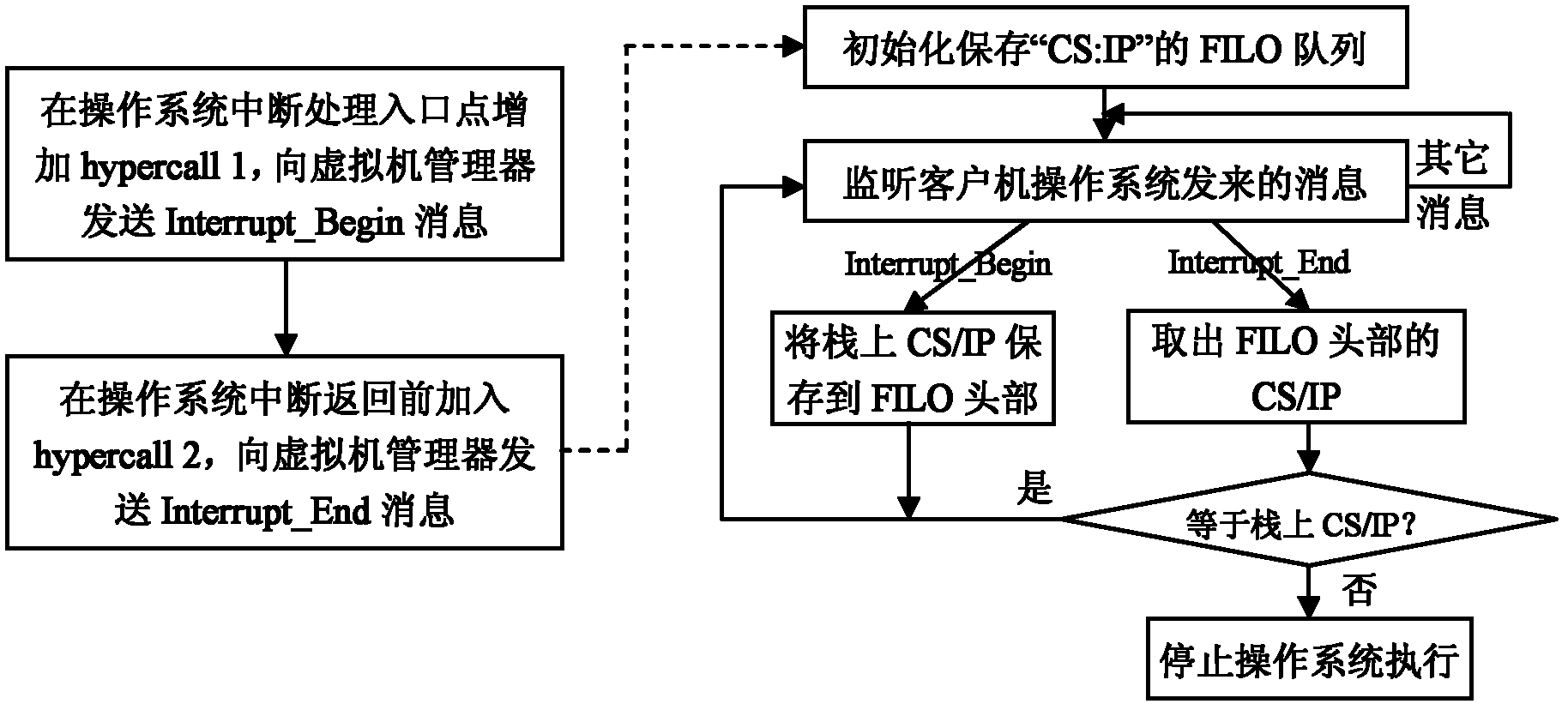
Method for preventing illegal transferring of interruption procedures of operating system
InactiveCN102509048AIllegal transfer of interrupt processing flowAvoid aggressive behaviorProgram initiation/switchingPlatform integrity maintainanceOperational systemControl data
The invention discloses a method for preventing illegal transferring of interruption procedures of an operating system, which mainly solves the problem that illegal transferring of the interruption procedures of the operating system by attackers cannot be prevented in the prior art. The method for preventing illegal transferring includes steps of modifying the interruption procedures of the operating system, transmitting specific information to a virtual machine manager when the interruption starts and stops; and modifying the virtual machine manager. When the virtual machine manager receives information of interruption starting, values of a CS (client / server) and an IP (internet protocol) register on current stacks of the operating system can be stored into an FILO (first in later out) array; when the virtual machine manager receives information of interruption stopping, the values of the CS and the IP register stored at the head of the FILO array can be extracted to be compared with the values on the current stacks of the operating system, if the values of the CS and the IP register are different from those of the current stacks of the operating system, execution of the operating system is stopped so as to prevent illegal transferring of the attackers. By the aid of the virtual machine manager, control data in interruption context are protected, so that the attackers cannot transfer the executive procedures of the operating system by distorting the control data, and the method can be used for protecting safety of the operating system.
Owner:XIDIAN UNIV
Method and device for verifying message safety
ActiveCN101820396BVerify legitimacyAvoid aggressive behaviorData switching networksComputer security
The invention discloses a method and a device for verifying message safety. By using the technical scheme of the invention, simple user validation judgment can be carried out on an access device to effectively verify the user validation at a position closest to a user, thereby preventing the attack of a message with a user-forged IP on an uplink network at an end point.
Owner:NEW H3C TECH CO LTD
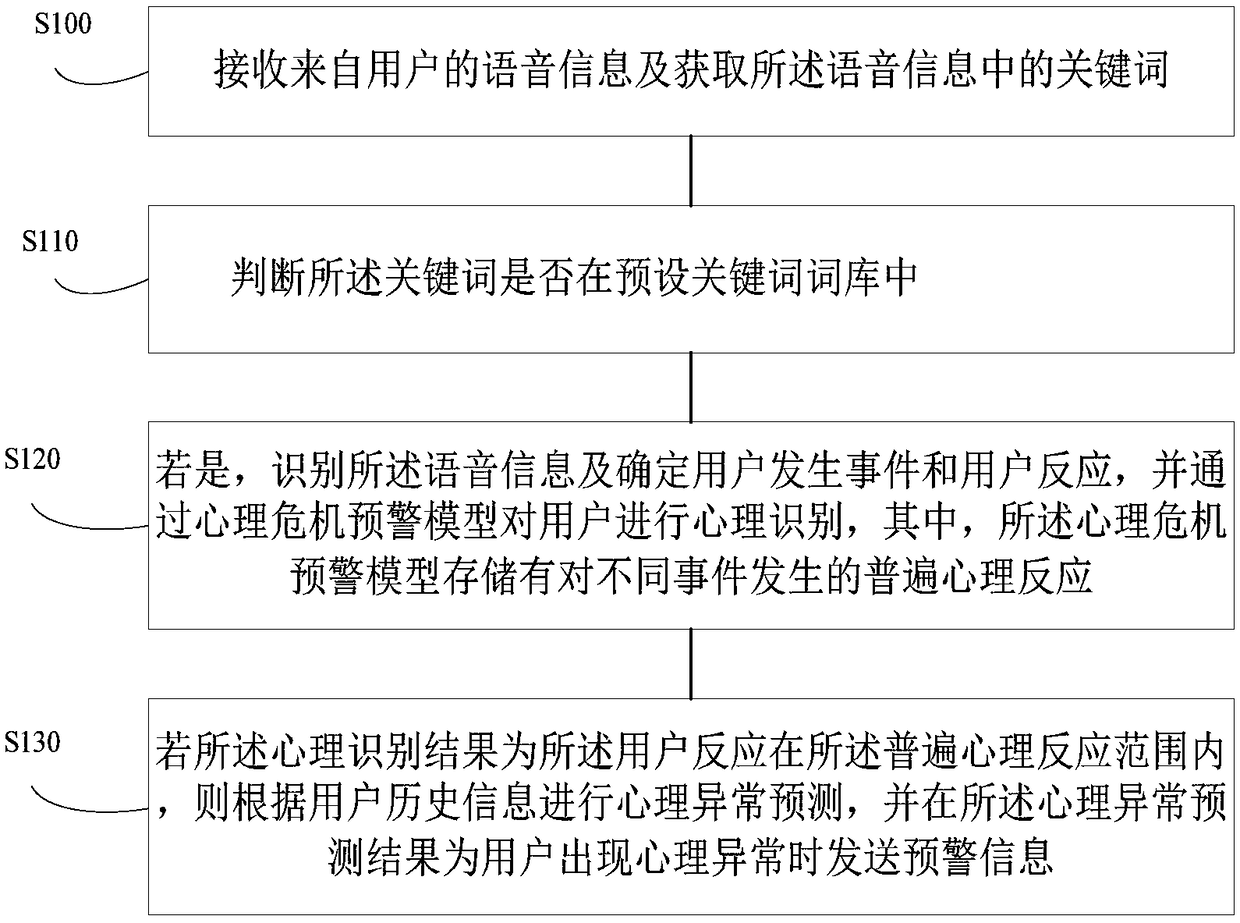
Mind companion method and device, robot and computer storage medium
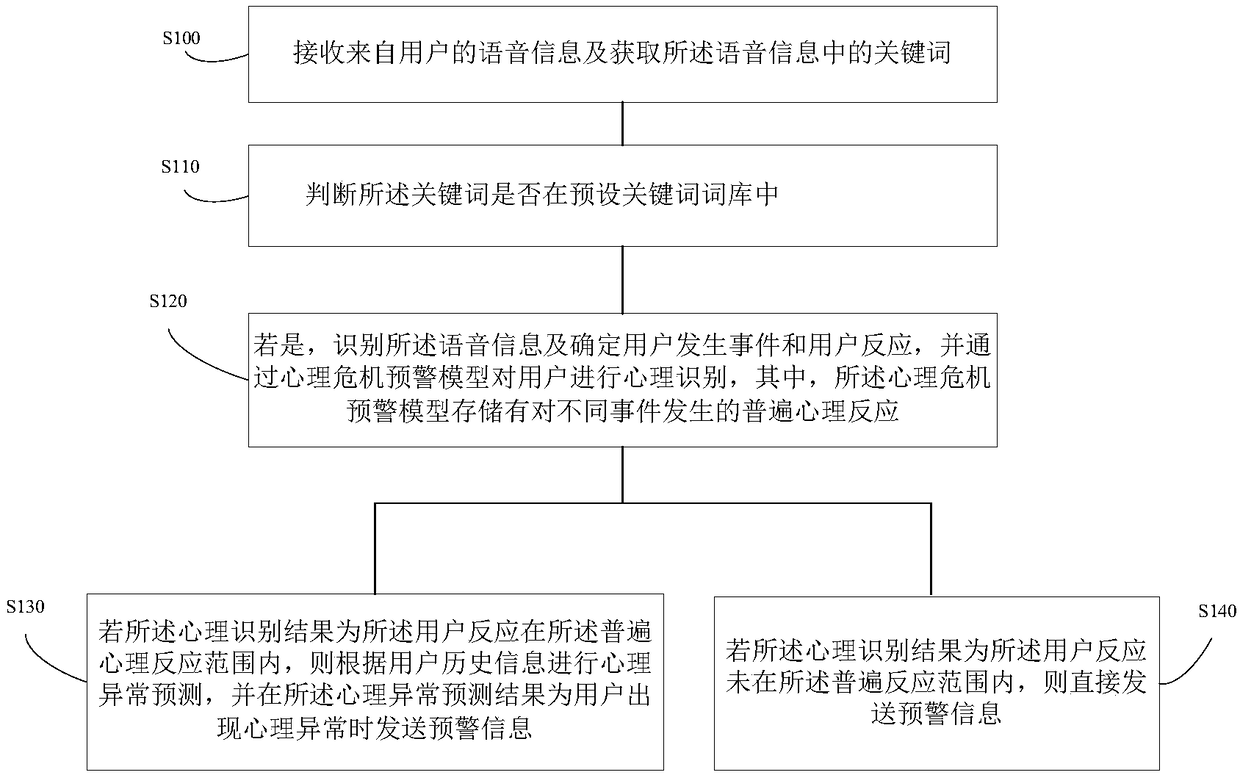
The invention provides a mind companion method and device, a robot and a computer storage medium. The method comprises: receiving voice information from a user and acquiring a keyword in the voice information; determining whether the keyword is in a preset keyword bank; and identifying the voice information and determining the user's event and a user reaction if so, and psychologically identifyingthe user through a psychological crisis early warning model. The invention can identify the psychological abnormality of the user according to the voice information of the user and perform abnormality early warning, can find the psychological problems of the user as early as possible so as to take corresponding measures timely, and can prevent the user from over-excited behaviors due to the neglect of the psychological abnormality.
Owner:广东蔚海数问大数据科技有限公司
Account risk evaluation method based on geographic position
PendingCN114140111AAvoid lostAvoid aggressive behaviorFinanceProtocol authorisationPayment transactionData mining
The invention provides an account risk evaluation method based on a geographic position, and the method comprises the steps: S1, storing an account profile in an account database, and enabling the account profile to comprise data related to a transaction account, the account profile at least comprises a first profile rule associated with a first geographic position and a second profile rule associated with a second geographic position, and the second geographic position is different from the first geographic position; s2, receiving, by the receiving device, an authorization request involving a first payment transaction associated with a related transaction account. According to the account risk evaluation method based on the geographic position, the account risk is judged according to the geographic position migration, so that the account with the risk is accurately identified and locked, and the loss caused by the fact that the account is utilized by a hacker gang is prevented.
Owner:WUHAN JIYI NETWORK TECH CO LTD
Emotion recognition and guidance method, device and equipment and readable storage medium
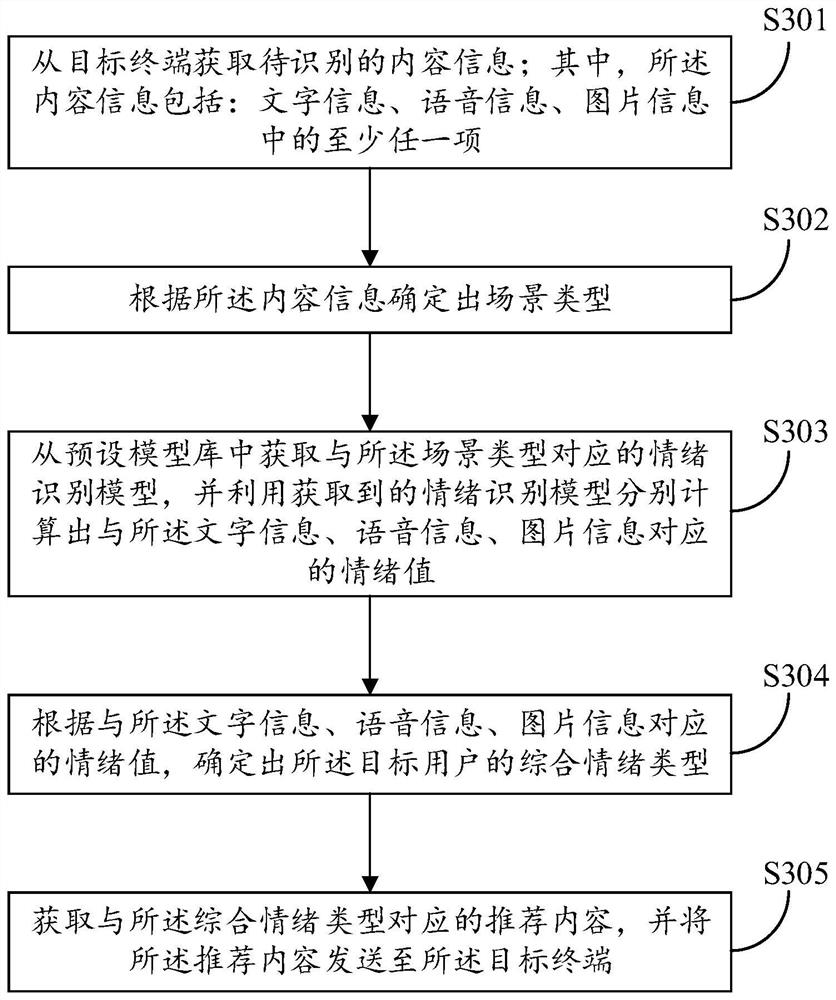
PendingCN114254136AAvoid aggressive behaviorComprehensive recognitionDigital data information retrievalSemantic analysisEmotion identificationHuman–computer interaction
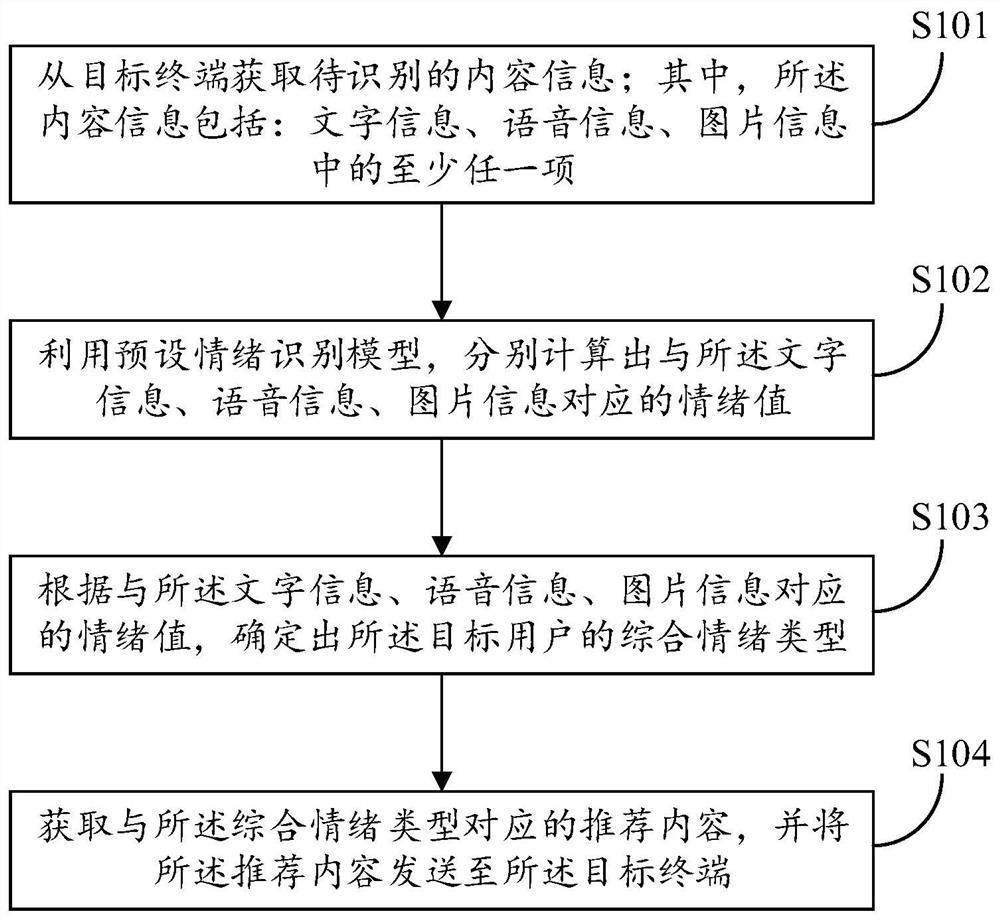
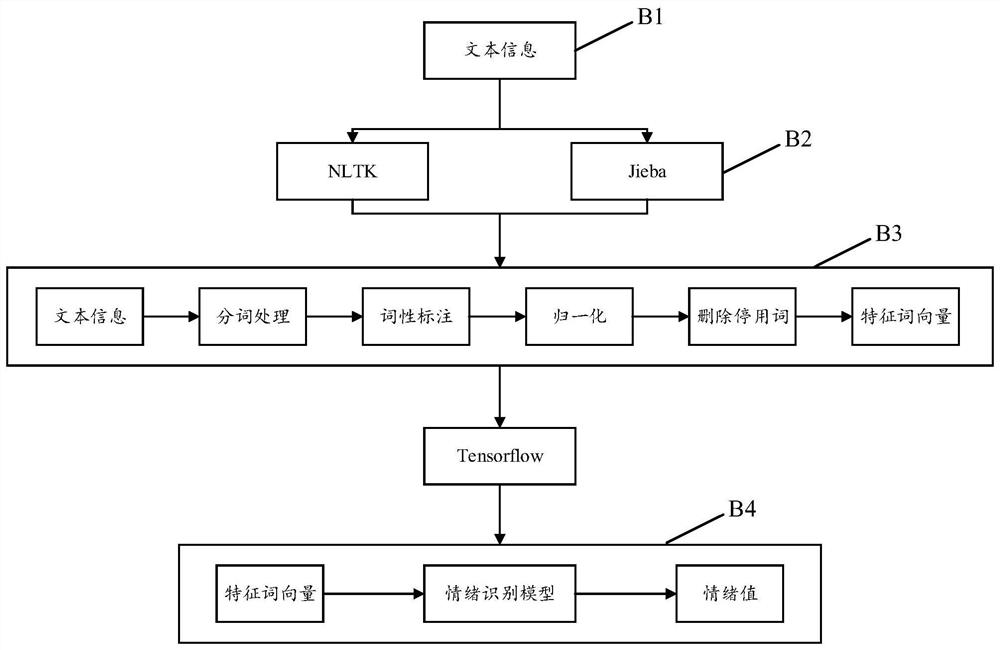
The invention discloses an emotion recognition and guiding method, device and equipment and a readable storage medium. The method comprises the steps that to-be-recognized content information is acquired from a target terminal; wherein the content information comprises at least any one of character information, voice information and picture information; utilizing a preset emotion recognition model to respectively calculate emotion values corresponding to the character information, the voice information and the picture information; determining a comprehensive emotion type of the target user according to emotion values corresponding to the text information, the voice information and the picture information; obtaining recommended content corresponding to the comprehensive emotion type, and sending the recommended content to the target terminal; according to the invention, the current emotion information of the user can be identified more accurately, and the emotion of the user can be guided frontally.
Owner:SHANGHAI BILIBILI TECH CO LTD
Automatic penetration testing system and method for WEB system
InactiveCN101242279BImprove functional efficiencyImprove work efficiencySpecial data processing applicationsSecuring communicationComputer hardwareLogical layer
The invention provides an automatic permeability test system for a WEB system, comprising three layers: a GUI presentation layer for alternating interface with a user, a logical layer as runs of control core, executing scanning and confidence program of the system and associative functions, and a data layer for storing and maintaining kinds of scan rules and configuration information in a task execution process. The system can automatically carry out a penetrating scan or a conventional scan to a WEB station based on a WEB scan task in the GUI layer, analyzing the scan result combined with therelative inserters, finds the possible security problems of the WEB station, and then generates a detecting report for reporting a formed aggregate risk list. The invention is used to perform an automatic security test, is capable of replacing the present manual security test and permeability test, greatly reduces the cost of software security test in software develop at present, and also greatlyincreases accuracy of security test.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Data processing method and device, electronic equipment and computer readable storage medium
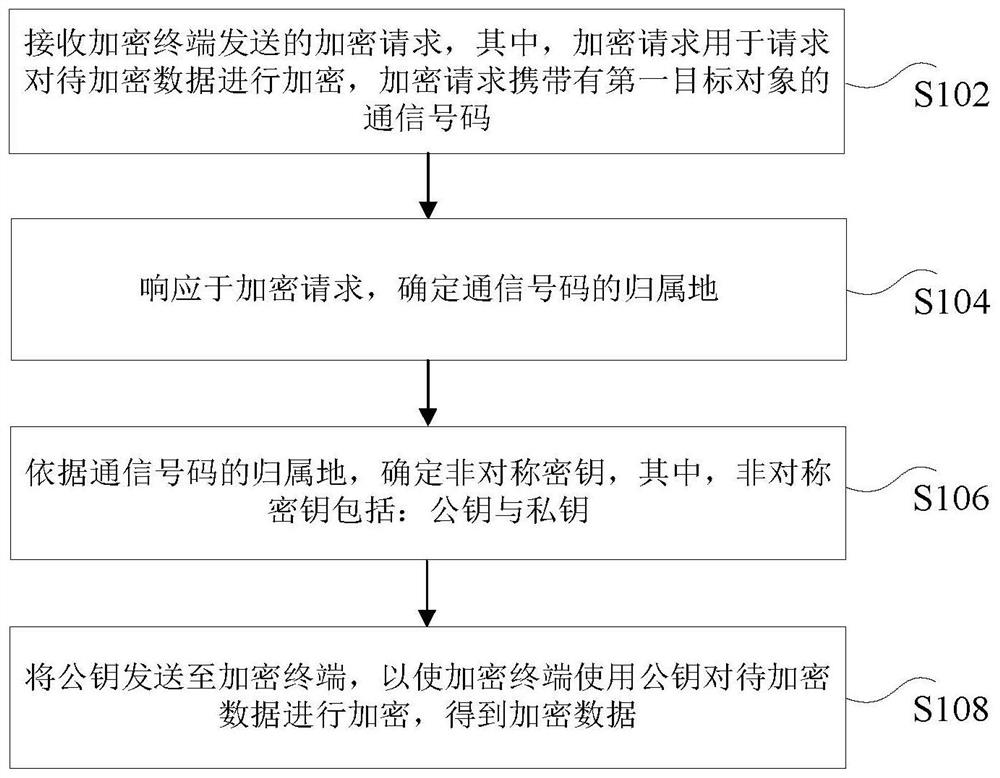
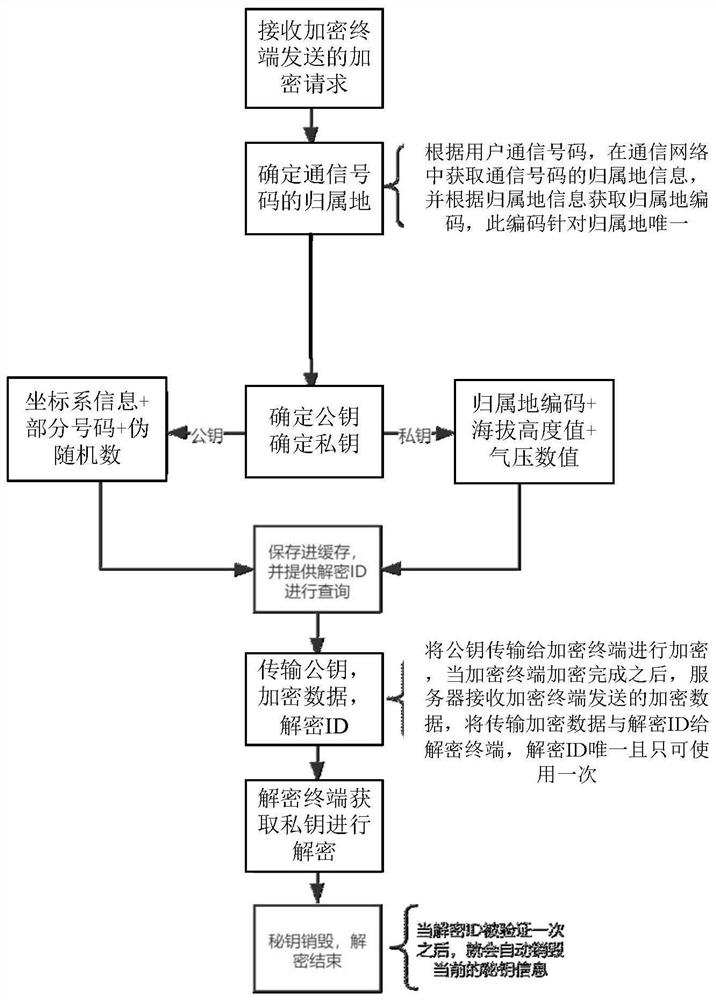
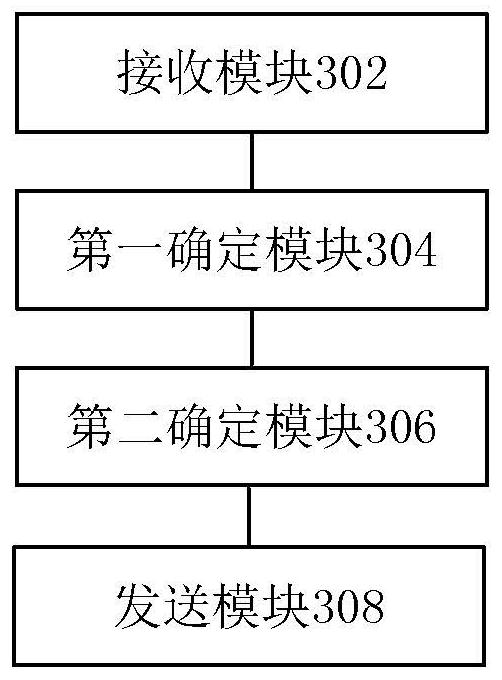
PendingCN114301663AIncrease randomnessProtection securityKey distribution for secure communicationData breachEngineering
The invention discloses a data processing method and device, electronic equipment and a computer readable storage medium. The method comprises the steps that an encryption request sent by an encryption terminal is received, the encryption request is used for requesting to encrypt data to be encrypted, and the encryption request carries a communication number of a first target object; determining an attribution of the communication number in response to the encryption request; an asymmetric key is determined according to the attribution of the communication number, and the asymmetric key comprises a public key and a private key; and sending the public key to the encryption terminal, so that the encryption terminal encrypts the to-be-encrypted data by using the public key to obtain encrypted data. According to the method and the device, the technical problem of data leakage caused by the fact that the secret key is easy to crack when the data is encrypted and transmitted by using the static secret key in the related technology is solved.
Owner:CHINA TELECOM CORP LTD
Wheelchair special for prisoners
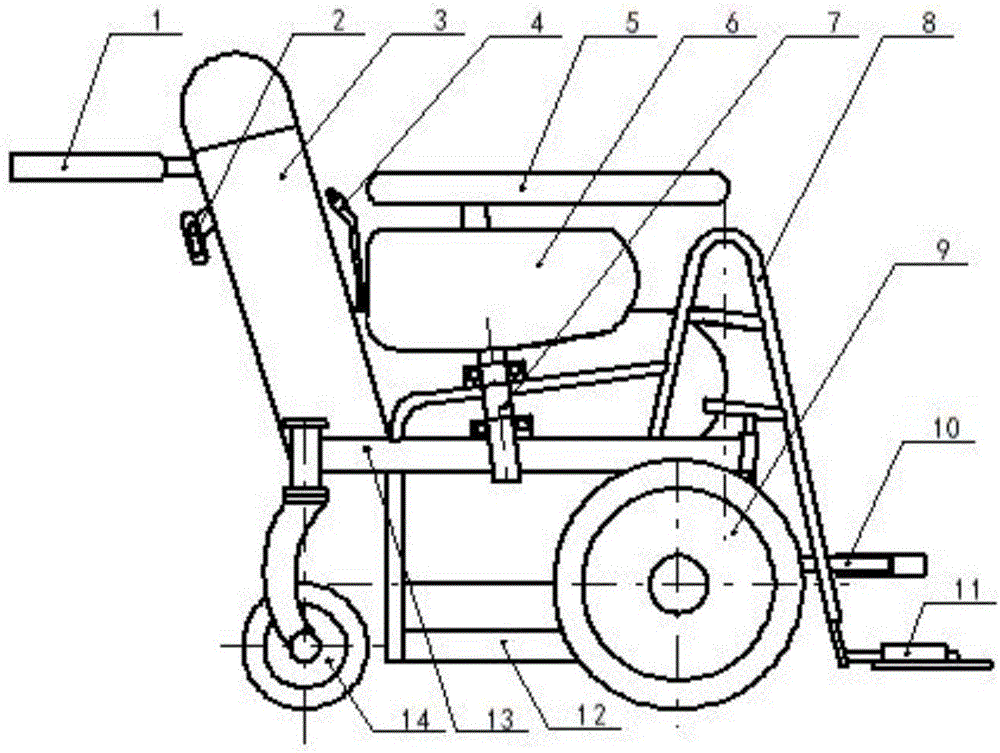
InactiveCN106038095AAvoid aggressive behaviorSimple structureWheelchairs/patient conveyanceVehicle frameEngineering
The present invention relates to a wheelchair special for prisoners. An ejection rod motor is longitudinally fixedly arranged on one side of the part, below a chair seat and chair back portion, of a frame; a rotating rod is laterally mounted on the middle part of the frame; the two ends of the rotating rod sleeve inside sleeves fixedly arranged on the frame; foot ring rods are fixedly arranged on the parts, on both sides of the frame front part, of the frame in a longitudinally symmetric manner, and a foot ring is arranged at the front end of each foot ring rod; a pair of mounting clamping plates are fixedly arranged on the parts, corresponding to the end parts of an ejection rod of the ejection rod motor, at the lower part of the rotating rod, and the mounting clamping plates are fixedly arranged on the ejection rod ends of the ejection rod motor by bolts; and vertical plates are fixedly arranged on the upper parts of the both sides of the rotating rod, each of the two vertical plates is fixedly provided with a longitudinal pull rod by bolts, and the front ends of the pull rods are fixedly arranged on the foot rings. The wheelchair is simple in structure, scientific in design and clever in conception, and can control the action of upper and lower limbs of the prisoners in the wheelchair and avoid the occurrence of malignant accidents, thus belonging to one of indispensable facilities in prison.
Owner:TIANJIN XINCHENG NEW SCI TRADE
Email transfer method for the online protocol and credit mechanism based on scalable message
ActiveCN100539555CAvoid aggressive behaviorReduce the burden onUser identity/authority verificationData switching networksTransfer procedureTransfer mode
The e-mail transmission method based on the extensible message online protocol and reputation mechanism belongs to the field of network security. It is characterized in that: in the method, the IM platform based on the XMPP protocol is used to effectively guarantee the authenticity of the source identity. The "pull mode" transmission mode is adopted for sending Email messages. In the process of message transmission, the IM platform is used to maintain the characteristics of the user's online status, and a transmission method combining block transmission and direct connection transmission between the sender and the receiver is adopted. Moreover, in the method, a unique combination of the reputation mechanism and the black and white list strategy is invented to prevent spam attacks in real time. The method can be deployed on the widely used IM platform based on the XMPP protocol at present. The method adopts the transmission scheme of server forwarding and end-to-end direct connection to transmit messages, which reduces the burden on the original server and will not affect the performance of the original IM service.
Owner:TSINGHUA UNIV
Man-machine identification method, device, server, client and storage medium
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
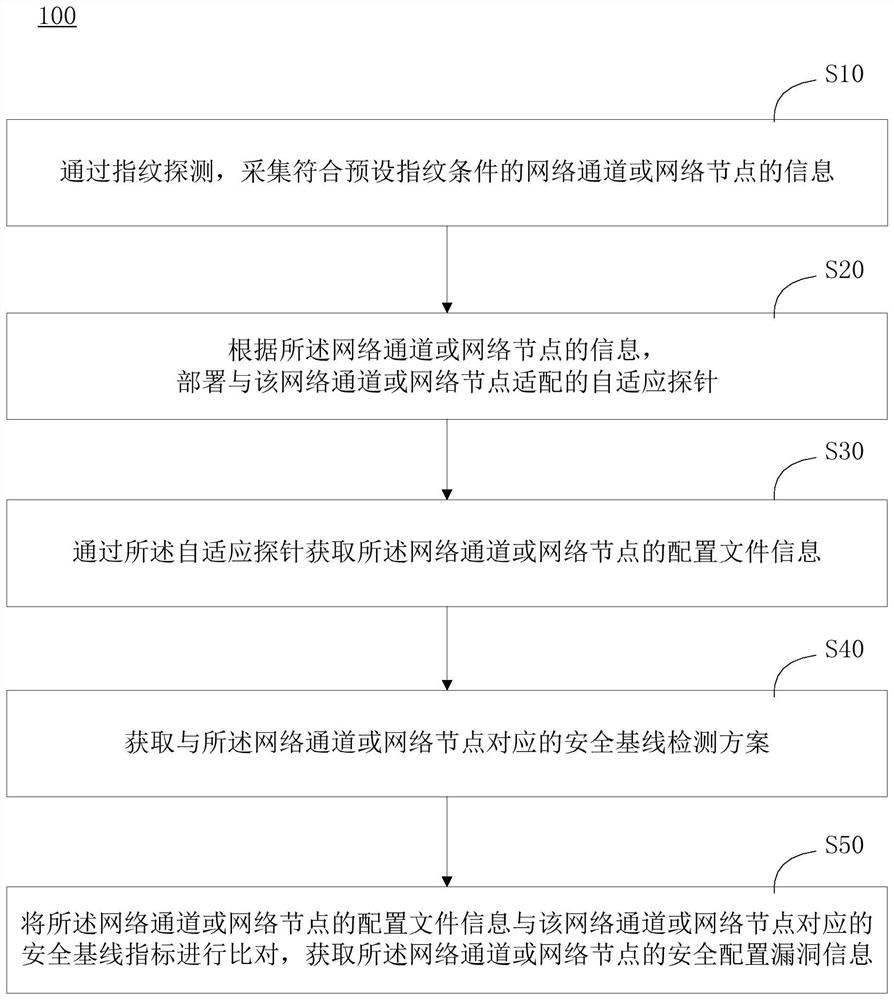
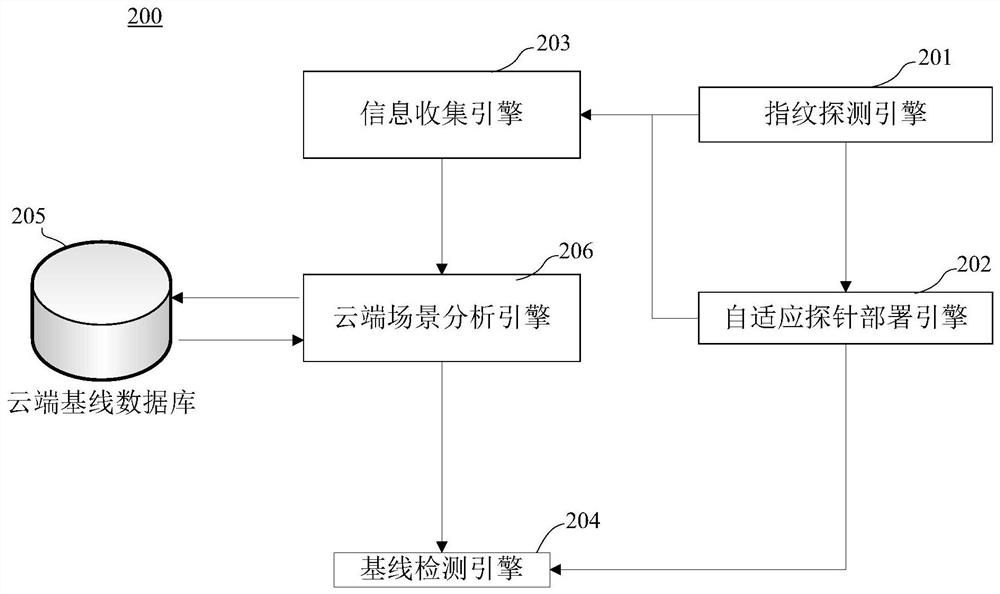
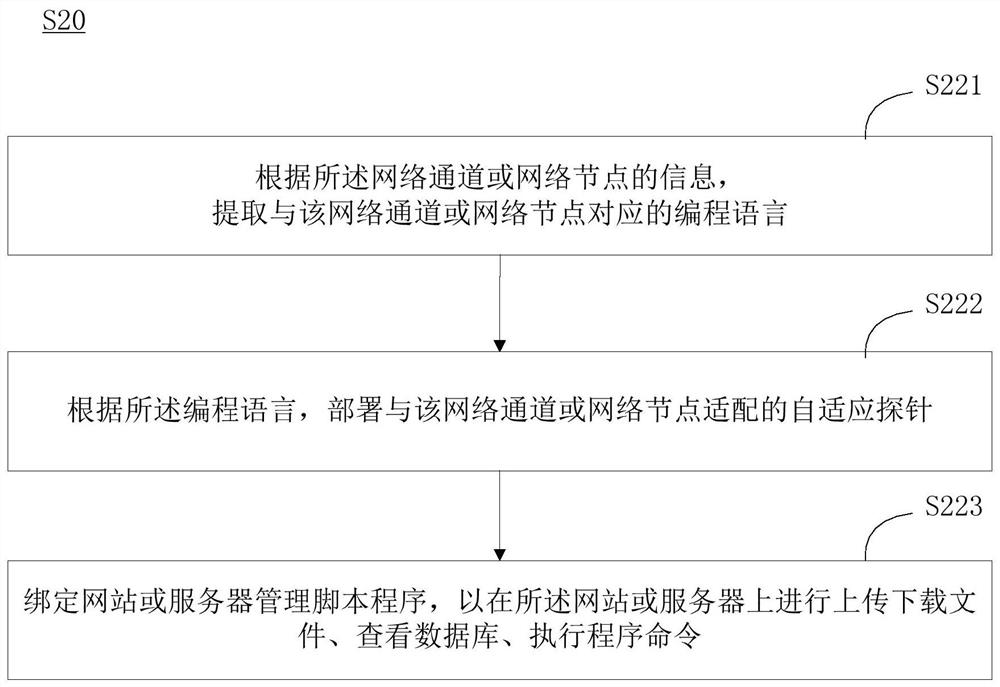
Security configuration vulnerability monitoring method, device, and computer-readable storage medium
The invention discloses a security configuration vulnerability monitoring method. The method includes the following steps: through fingerprint detection, collecting information of network channels ornetwork nodes that accord with preset fingerprint conditions; arranging self-adaptive probes that fit the network channels or the network nodes; obtaining configuration file information of the networkchannels or the network nodes through the self-adaptive probes; and comparing the configuration file information of the network channels or the network nodes with security baseline indexes corresponding to the network channels or the network nodes, and obtaining security configuration vulnerability information of the network channels or the network nodes. The security configuration vulnerabilitymonitoring method can comprehensively detect security configuration vulnerability information of network channels or network nodes in an Internet system to prevent attacks of hackers at the source. The invention also provides a security configuration vulnerability monitoring device configured in the Internet and a computer readable storage medium.
Owner:SANGFOR TECH INC
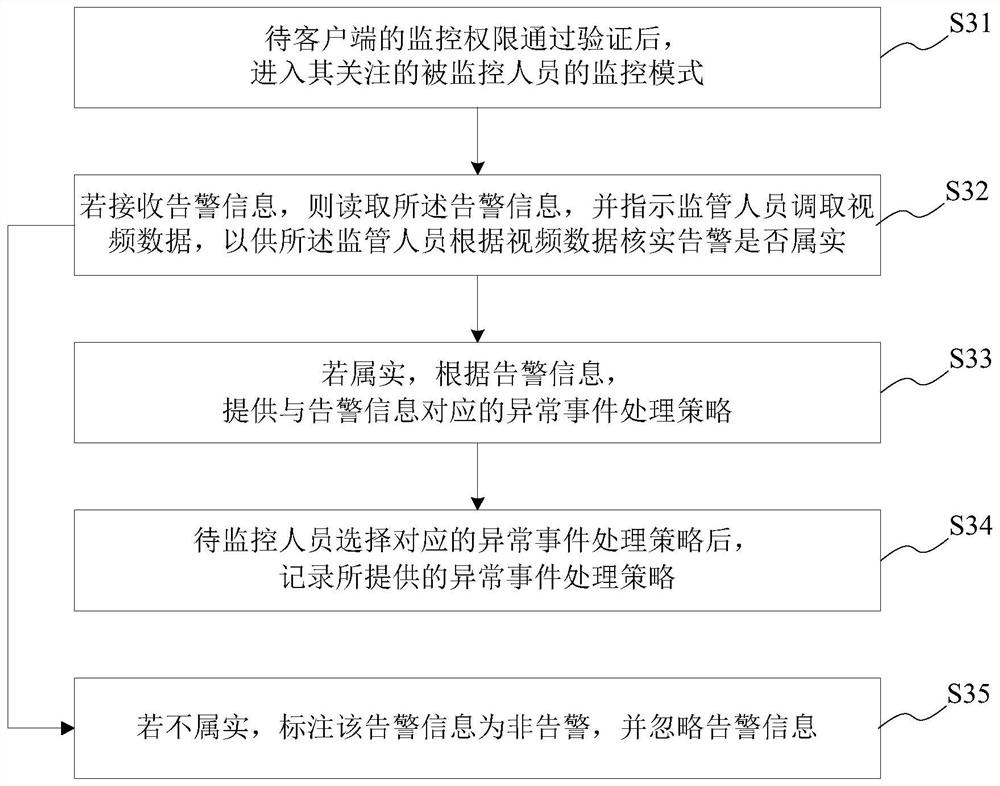
To-be-monitored data analysis/processing method/system, medium and service/client
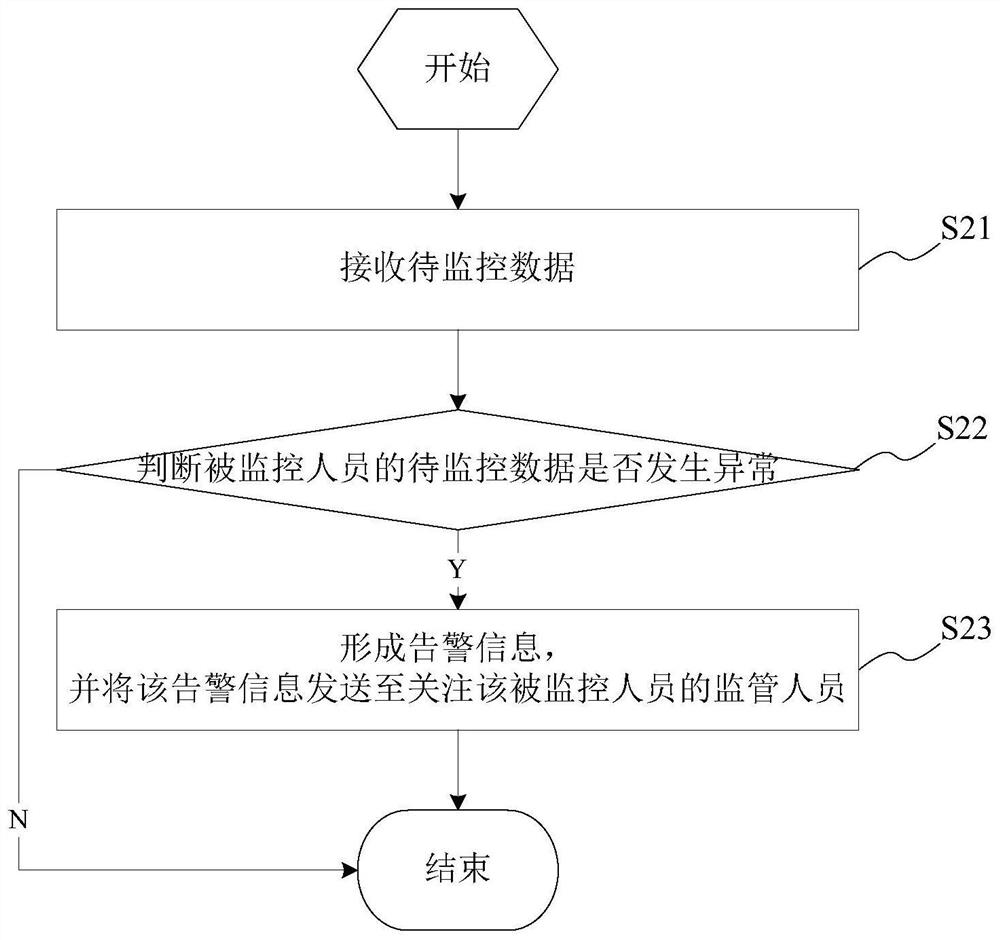
InactiveCN111935057AAvoid aggressive behaviorImprove the level of refined managementCharacter and pattern recognitionClosed circuit television systemsEngineeringData model
The invention provides a to-be-monitored data analysis / processing method / system, a medium and a service / client. The to-be-monitored data analysis method of a monitored person comprises the following steps: receiving to-be-monitored data; analyzing the to-be-monitored data according to a pre-built data model so as to judge whether the to-be-monitored data of the monitored person is abnormal or not,if yes, forming alarm information, and sending the alarm information to a supervisor paying attention to the monitored person; after the supervisor verifies the alarm information, providing an abnormal event processing strategy corresponding to the alarm information; and if not, ending the process. According to the invention, daily action behavior data and vital sign data of a monitored person are collected, a big data analysis technology is used, the data is compared with daily data, abnormal conditions are found in time through quantitative data, the overshoot behavior of the monitored person is prevented, and the fine management level of supervisors in a special area is improved.
Owner:上海云思智慧信息技术有限公司
Psychological intervention rehabilitation assistive device based on VR technology
PendingCN114588470AInstalled and disassembledImprove comfortRestraining devicesSleep inducing/ending devicesEyewearMechanical engineering
The invention relates to the technical field of psychological intervention rehabilitation assistive devices, in particular to a psychological intervention rehabilitation assistive device based on VR technology, which comprises a seat, a fixing rod is fixedly connected to the upper side of the rear end of the seat, a universal pipe is fixedly connected to the outer surface of the front end of the fixing rod, and VR glasses are fixedly connected to one side, away from the fixing rod, of the universal pipe. The VR glasses and the universal pipe are connected through a connecting mechanism; the connecting mechanism comprises a connector. By arranging the universal pipe, the position of the VR glasses can be freely adjusted according to the height condition of a user, the VR glasses do not need to be worn on the head through a bandage, the use comfort of a patient is improved, the VR glasses and the universal pipe are connected through the connecting mechanism, the VR glasses are convenient to mount and dismount, and the use is convenient. And the hand binding mechanism is arranged to bind the hands of the patient, so that overexertion during mood excitation of the patient is prevented, and the personal safety of the patient is guaranteed.
Owner:安徽阳光心健科技发展有限公司
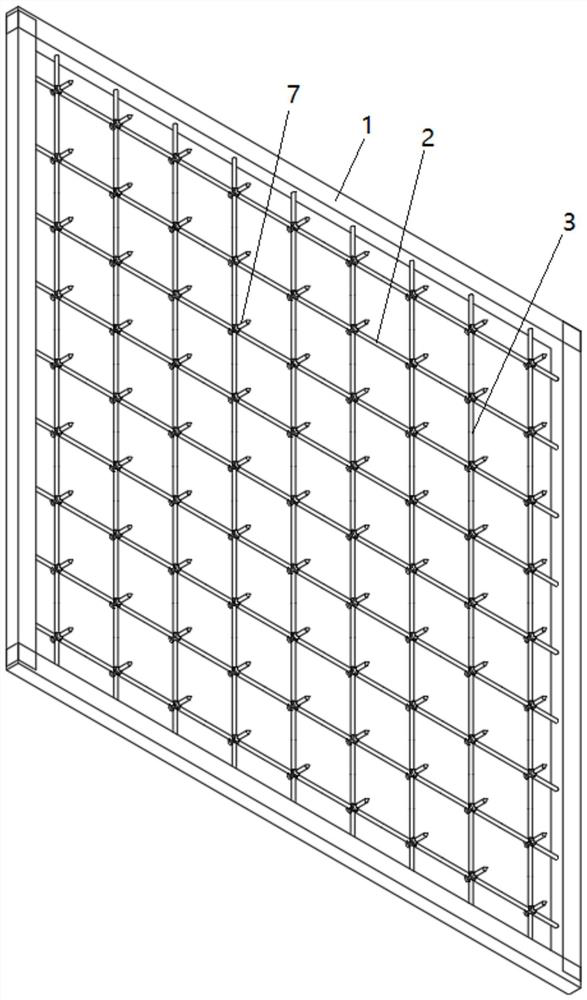
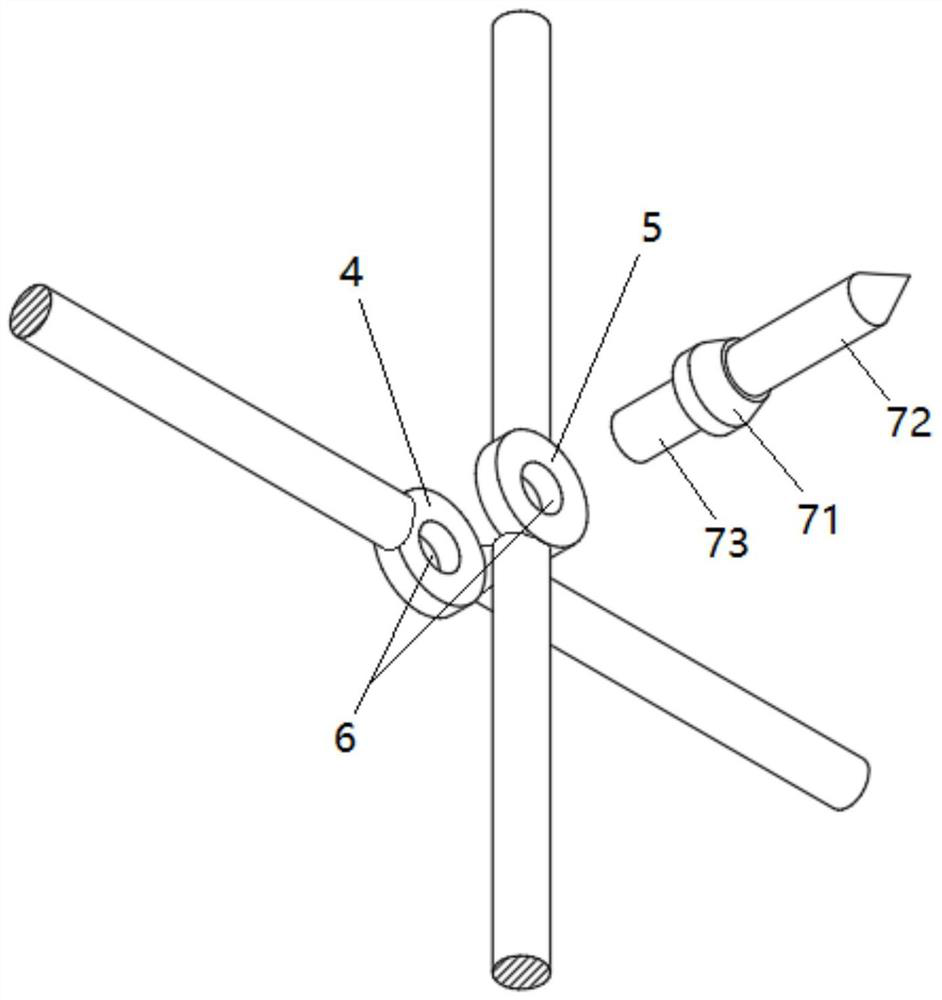
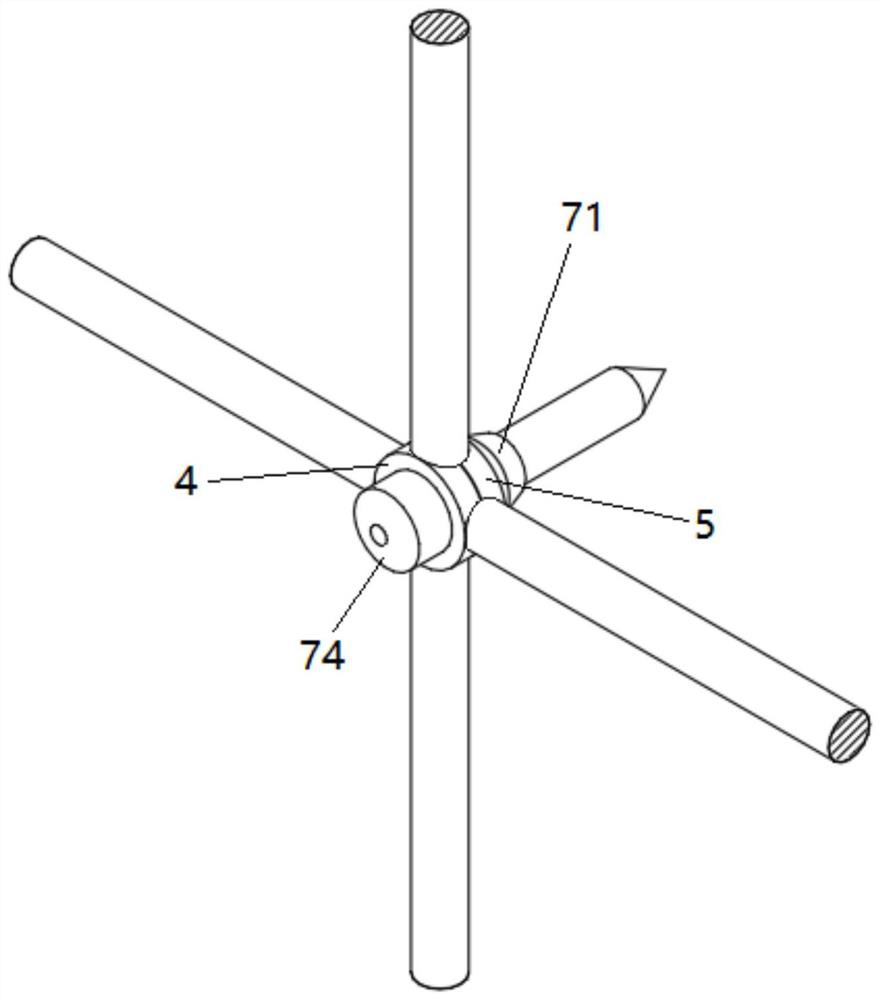
Protective isolation fence and processing method thereof
PendingCN114776136AImprove the protective effectAvoid pollutionFencingWire networkStampingHuman health
The protective separation fence comprises an outer frame, a plurality of transverse reinforcing steel bars and a plurality of longitudinal reinforcing steel bars, the transverse reinforcing steel bars and the longitudinal reinforcing steel bars are arranged in a crossed mode, and a first flat part and a second flat part are correspondingly formed at the crossed position of each transverse reinforcing steel bar and each longitudinal reinforcing steel bar through stamping. The first flat part and the second flat part are provided with through holes which are communicated with each other, barbed nails penetrate through the through holes and extend out, and the first flat part and the second flat part are pressed together through riveting, so that the transverse steel bars and the longitudinal steel bars are fixedly connected. The mesh is formed in a steel bar stamping and barbed nail riveting mode, a traditional steel wire welding mode is replaced, pollution of electric welding to the environment and damage to human health are avoided, the strength of the separation fence is enhanced, the service life is long, and the separation fence is not prone to damage; in addition, after the mesh is formed, barbed nails on the mesh can play a good protection role, and attack behaviors of animals can be effectively avoided.
Owner:北京市中凯路达交通技术有限责任公司
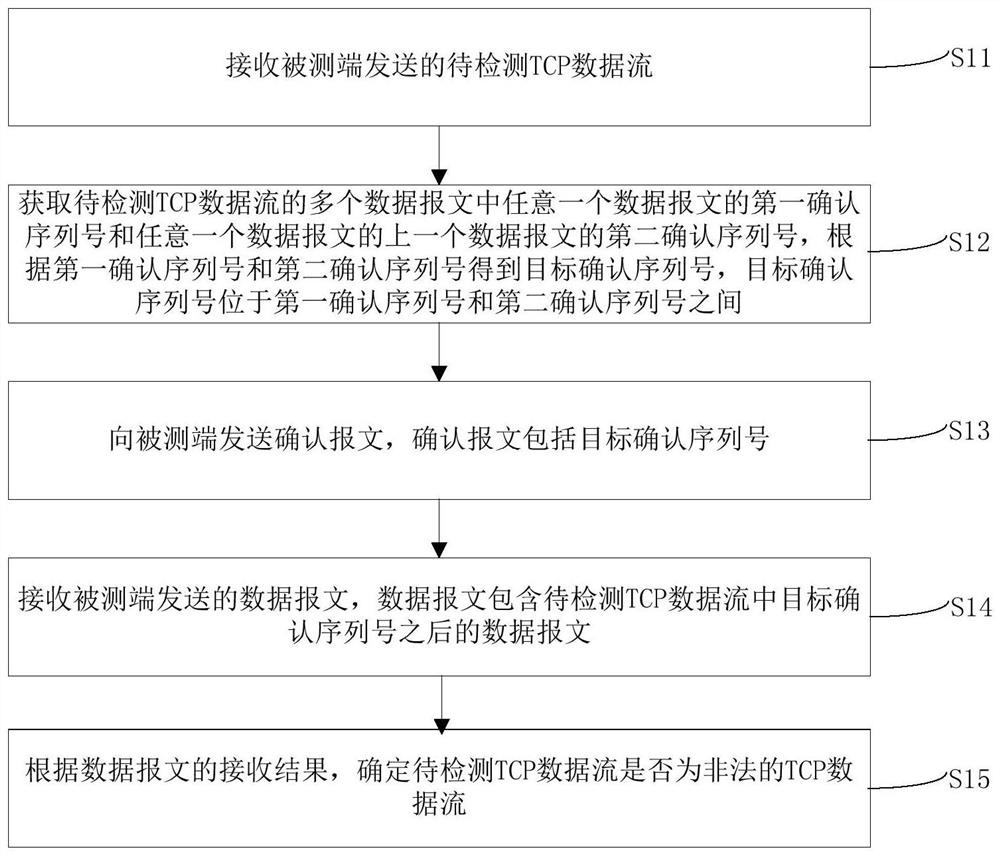
Illegal TCP data stream detection method and device, and computer equipment
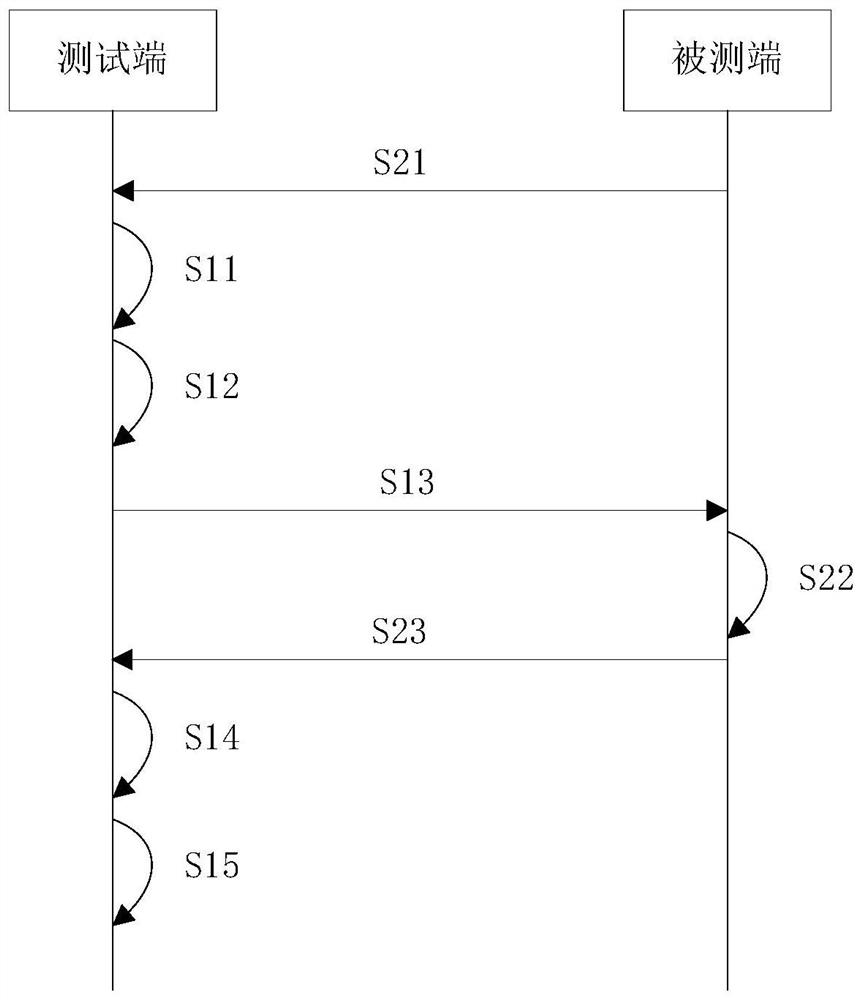
PendingCN114070572AAccurate detection statusAvoid aggressive behaviorSecuring communicationData streamAttack
The invention discloses an illegal TCP data stream detection method and device, and computer equipment. The method comprises the following steps of: receiving a to-be-detected TCP data stream sent by a detected end; acquiring a first confirmation serial number of any one data message in a plurality of data messages and a second confirmation serial number of a previous data message of the any one data message in the to-be-detected TCP data stream, and acquiring a target confirmation serial number between the first confirmation serial number and the second confirmation serial number according to the first confirmation serial number and the second confirmation serial number; sending a confirmation message comprising the target confirmation serial number to the detected end; receiving a data message sent by the detected end, wherein the data message comprises a data message after the target confirmation serial number in the to-be-detected TCP data stream; and determining whether the to-be-detected TCP data stream is an illegal TCP data stream or not according to a receiving result of the data message. By implementing the illegal TCP data stream detection method, the state of the whole TCP data stream can be accurately detected, and attack behaviors of illegal TCP data streams on an industrial control system and a military system are avoided.
Owner:北京威努特技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com