Email transfer method for the online protocol and credit mechanism based on scalable message
A technology for sending e-mails and e-mails, applied in the Internet field, can solve problems such as difficulty in promotion and deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
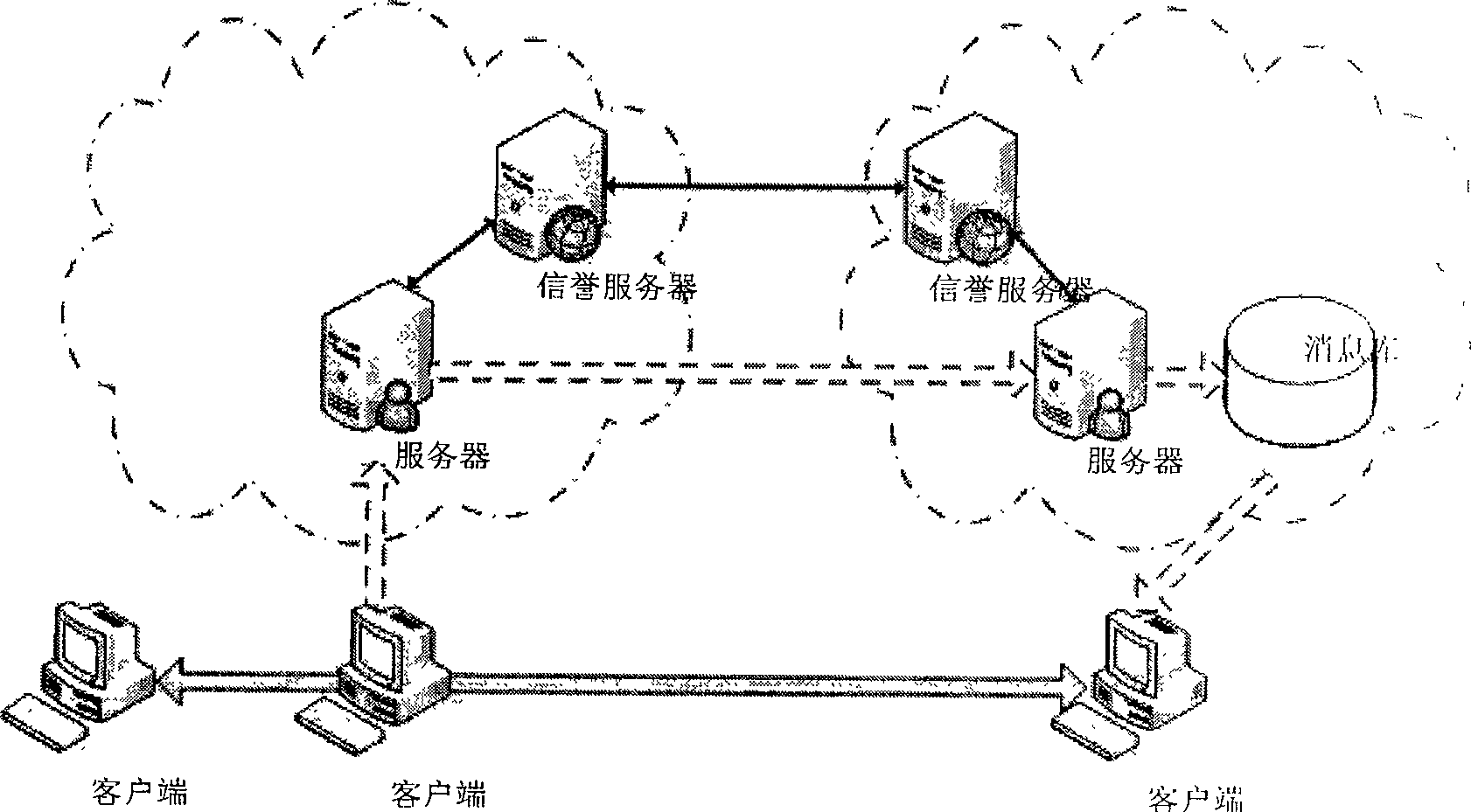
[0048] We mainly introduce a core mechanism of the present invention: the spam filtering method based on the reputation mechanism and the black and white list strategy. For the black and white list information, we can extract the white list information from the contact list information submitted by each IM user; and the black list information, we can use the Privacy Lists mechanism provided by the XMPP protocol to obtain the communication of which users the user rejects. For the reputation mechanism, we need to build a reputation network and a reputation calculation model in order to obtain the user's reputation.
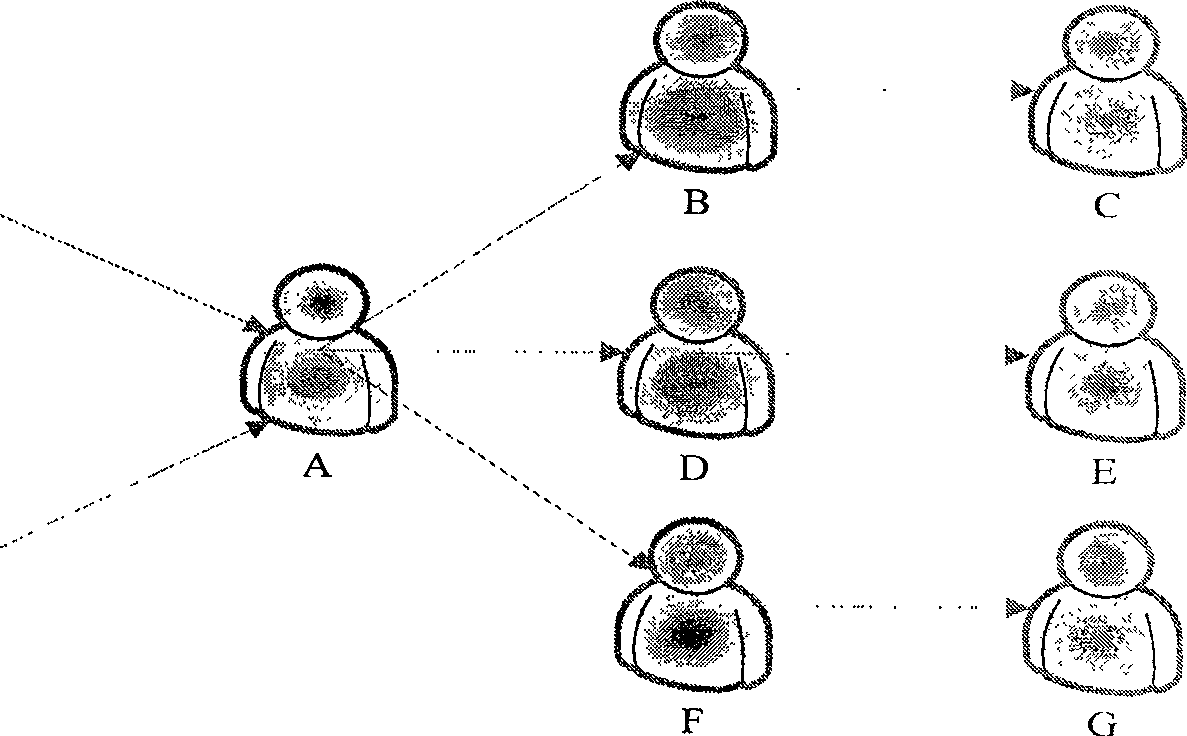
[0049] For the establishment of the reputation network, we use the user whitelist information collected by the server, that is, the contact list information to build a reputation network. Through the contact list, we can get such as figure 2 Such a directed graph G 1 : The directed connection (A → B) between the nodes in the graph indicates that there is a relati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com