Illegal TCP data stream detection method and device, and computer equipment
A detection method and detection device technology, which are applied in security communication devices, digital transmission systems, electrical components, etc., can solve the problems of inability to detect TCP data streams, affect the detection effect of illegal attacks, and achieve the effect of avoiding attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
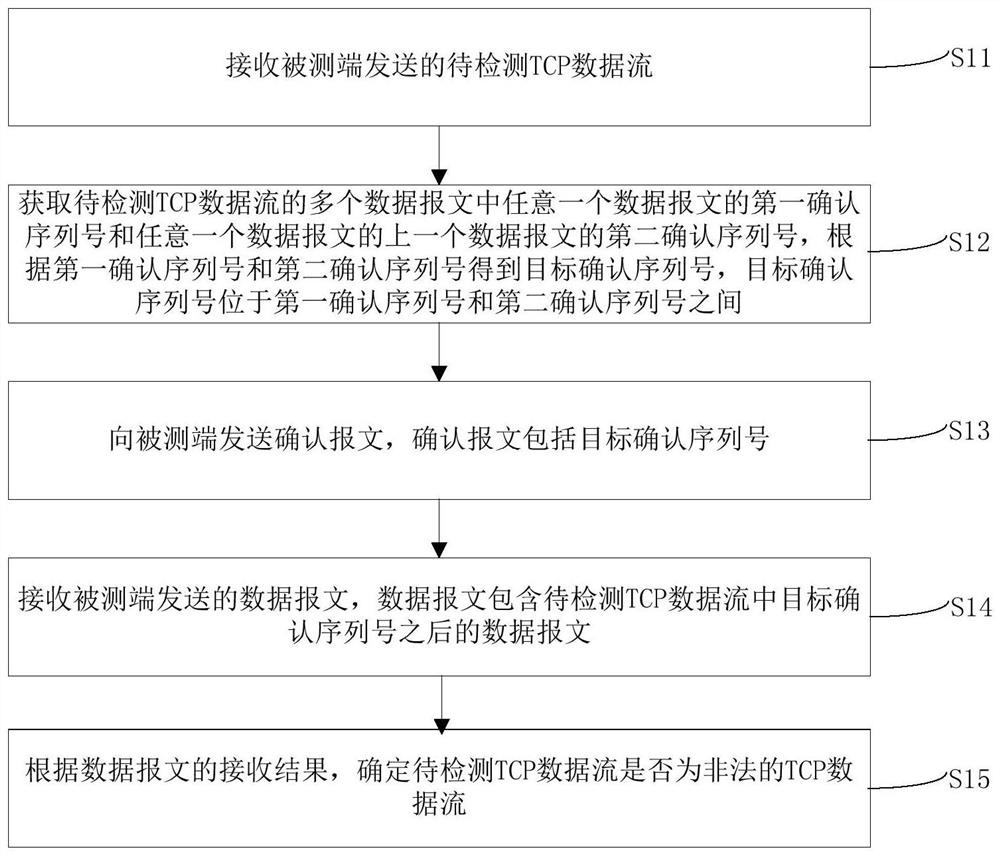
[0031] The embodiment of the present invention provides a detection method for illegal TCP data streams, which is applied to the detection of TCP data streams transmitted in real time by a pair of network ports (such as a pair of network ports of a firewall) of a test terminal, and the test terminal can work in a transparent mode In this way, no matter what bit combination data is transmitted by the terminal under test, the data can be transmitted to the test terminal on the link. Such as figure 1 shown, including the following steps:
[0032] S11: Receive the TCP data stream to be detected sent by the terminal under test.
[0033] Exemplarily, the tested end can be an industrial control system device or a military system device; the TCP data flow to be detected can be an industrial control system device or a military system device , protocol type), the TCP data flow to be detected includes multiple data packets. The TCP data stream can be received directly through a serial...
Embodiment 2
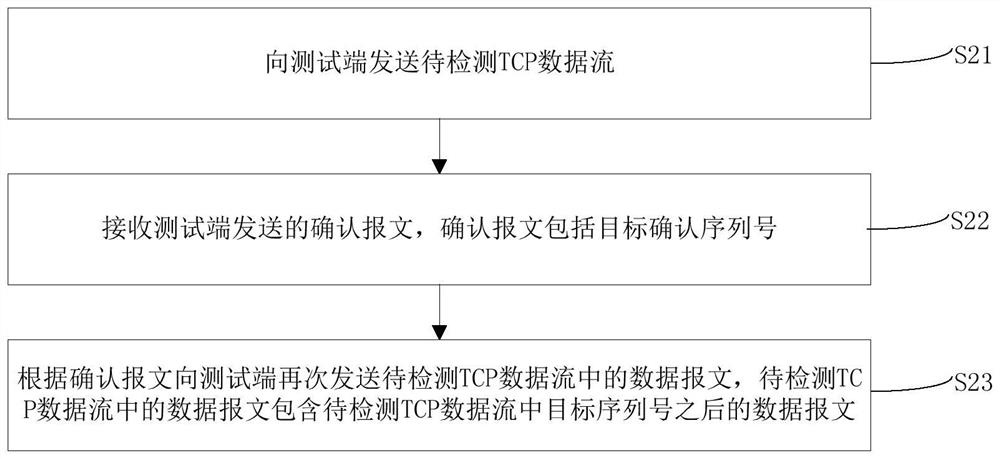
[0053] The embodiment of the present invention provides a detection method of an illegal TCP data stream, which is applied to the tested end, such as figure 2 shown, including the following steps:
[0054] S21: Send the TCP data flow to be detected to the testing end.
[0055] Exemplarily, the TCP data stream to be detected is created according to the method of step S11 in Embodiment 1, and the sending method of the TCP data stream to be detected can be sent through a serial port or wirelessly / wired. The method for sending the TCP data stream to be detected is not limited, and those skilled in the art can set it according to actual conditions.
[0056] S22: Receive an acknowledgment message sent by the test end, where the acknowledgment message includes the target confirmation sequence number. For specific implementation, refer to the description of the corresponding steps in Embodiment 1, which will not be repeated here.
[0057] S23: Send the data message in the TCP data...
Embodiment 3
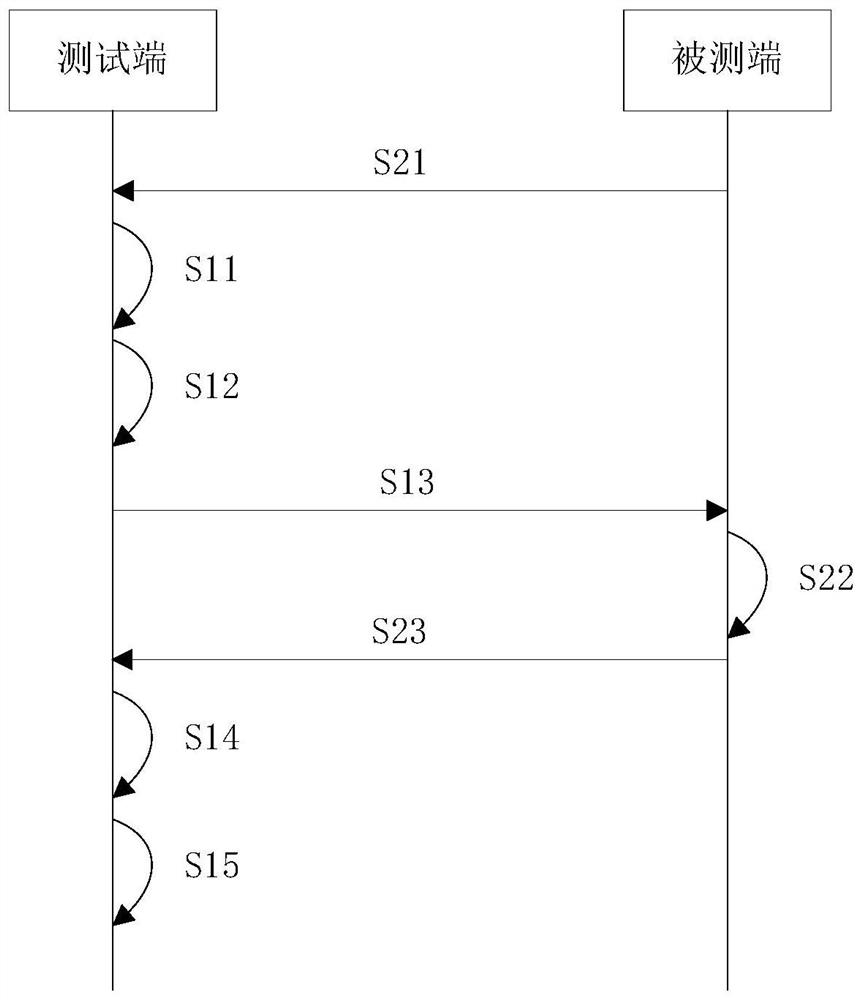
[0061] Embodiments of the present invention provide a detection system for illegal TCP data streams, which is applied to the detection of illegal TCP data streams at the test end and the tested end, and the labels in the figure correspond to the labels in the foregoing embodiments, as image 3 As shown, the specific steps are as follows:
[0062] S21: The terminal under test sends the TCP data flow to be detected to the test terminal.
[0063] S11: The testing end receives the TCP data stream to be detected sent by the tested end.
[0064] S12: The test end obtains the first confirmation sequence number of any one of the data packets of the TCP data flow to be detected and the second confirmation sequence number of the previous data packet of any one data packet, according to the first The confirmation sequence number and the second confirmation sequence number are used to obtain the target confirmation sequence number, and the target confirmation sequence number is located b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com