Method, apparatus and system for identifying access device of industrial control network
A technology of industrial control network and access equipment, applied in the field of information security, can solve problems such as obsolete protocol stack and unsupported protocol options, and achieve effective management and convenient supervision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
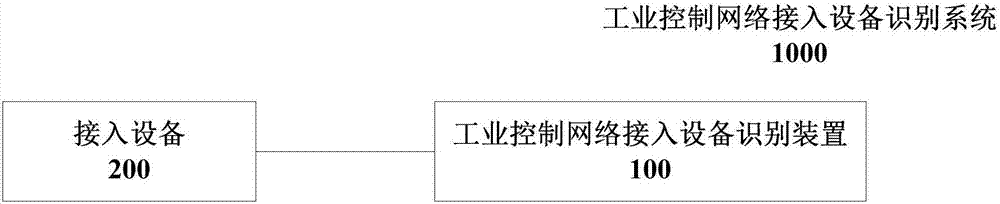
[0020] figure 1 It is a block diagram of an industrial control network access device identification system 1000 shown according to an exemplary embodiment, refer to figure 1 , the system can be used in an industrial control network, the industrial control network access device identification system 1000 can include an access device 200; and the industrial control network access device identification device 100 provided in the present disclosure, the industrial control network The access device identification apparatus 100 is connected with the access device 200 . The access device 200 may be a host computer, PLC (Programmable Logic Controller, Programmable Logic Controller) and other equipment, and the industrial control network access device identification device 100 may be connected directly or through a bypass (for example, a switch, etc.) device connection path) is connected to the access device 200 to acquire the device information of the access device.
[0021] Afterwa...
Embodiment 2
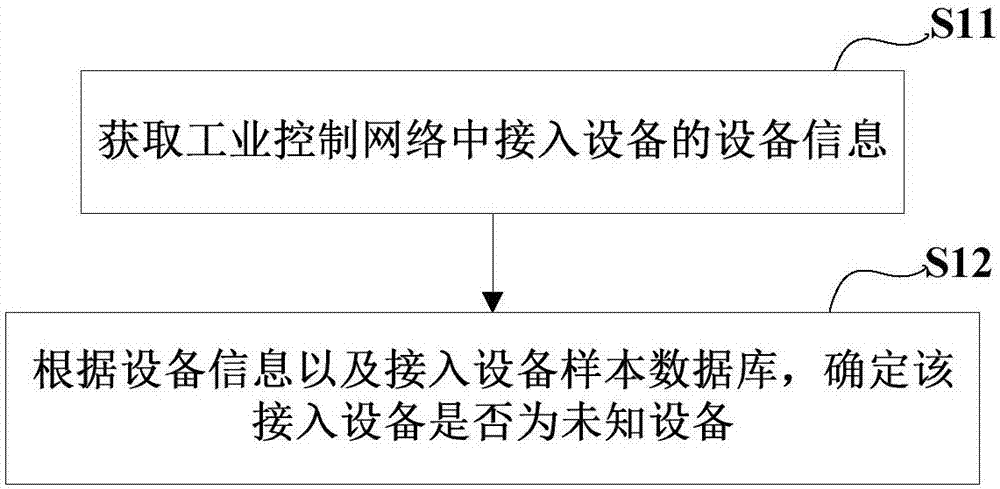
[0026] figure 2 It is a flow chart of a method for identifying industrial control network access equipment according to an exemplary embodiment. The method can be applied to the identification device for industrial control network access equipment in the above system, such as figure 2 As shown, the method includes the following steps.
[0027] In step S11, the device information of the access device in the industrial control network is obtained.
[0028] For example, obtain the device information of the access device in the above-mentioned industrial control network, wherein the device information may include the device status data and flow data of the access device, and the device status data may include IP address, MAC address, protocol number, and applications.
[0029] In step S12, it is determined whether the access device is an unknown device according to the device information and the access device sample database.
[0030] For example, according to the above devic...
Embodiment 3
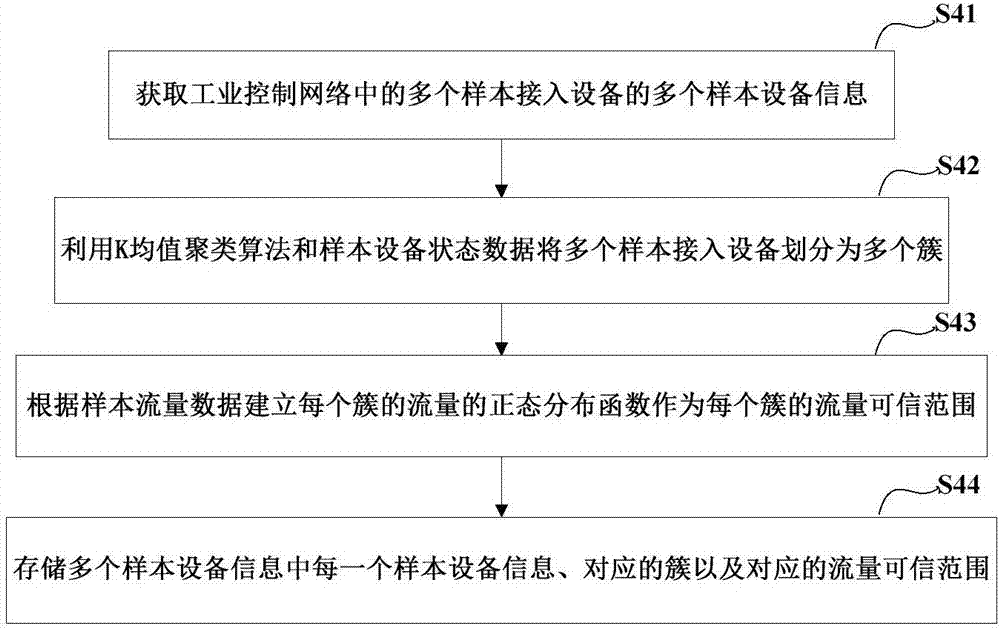
[0033] image 3 It is a flow chart of a method for identifying an industrial control network access device according to an exemplary embodiment, refer to image 3 , in this embodiment 3, an example method step for establishing the access device sample database in step S12 is further provided, which may further include the following steps:
[0034] In step S41, a plurality of sample device information of a plurality of sample access devices in the industrial control network is acquired, and each sample device information includes sample device status data and sample flow data of a sample access device.
[0035] For example, a plurality of sample device state data and sample flow data may be acquired by using deep packet inspection (DPI) technology, and the device state data may include IP address, MAC address, protocol number, and application. For example, the address of the host computer is 192.168.1.2, the mac address is 01:02:03:04:05:06, use http to access the Internet, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com